VPN Security: Authentication, Confidentiality, and Integrity Report
VerifiedAdded on 2023/06/07
|12
|2219
|342
Report
AI Summary
This report provides a comprehensive analysis of Virtual Private Network (VPN) security. It begins by exploring how internet browsers ensure communication with the correct servers and delves into the authentication process, including the role of digital signatures. The report then examines the importance of ensuring communication with the right client through protocols like L2TP/IPSec. A significant portion is dedicated to confidentiality and integrity processes, particularly within SSL communication, explaining how these are achieved through symmetric encryption, hash algorithms, and cipher suites. Furthermore, the report addresses the mitigation of replay attacks, detailing strategies employed in SSL communication. The conclusion emphasizes the critical role VPNs play in securing data across less secure networks such as the internet, highlighting the importance of authentication, confidentiality, integrity, and anti-replay mechanisms.

Running head: VIRTUAL PRIVATE NETWORKS
Virtual Private Networks
Name of the Student
Student ID
Name of the Subject
Name of the University
Submission Date
Author Note
Virtual Private Networks
Name of the Student
Student ID
Name of the Subject
Name of the University
Submission Date
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VIRTUAL PRIVATE NETWORKS
Executive Summary
Virtual Private networks or VPN provides effective security over the networks that are mostly
considered as unsecured, such as the internet. VPN allows remote users and branch offices to
have secured access over the applications they use as well as the resources. However, it is still a
dicey situation from the perspective of a user on the other end. Therefore, the following report as
described below has put forward an idea on how the internet browser ensures that the link
provided is being communicated to the correct server, the authentication process of digital
signatures and the communication to the right client. Further, the report had provided a detailed
confidentiality and integrity process for the Virtual Private network Processes and the Protection
against the replay attacks. The report had clearly stated how SSL communication provides
confidentiality and integrity to transferred messages and how proper anti-replay attacks are
mitigated in these kinds of communications.
Executive Summary
Virtual Private networks or VPN provides effective security over the networks that are mostly
considered as unsecured, such as the internet. VPN allows remote users and branch offices to
have secured access over the applications they use as well as the resources. However, it is still a
dicey situation from the perspective of a user on the other end. Therefore, the following report as
described below has put forward an idea on how the internet browser ensures that the link
provided is being communicated to the correct server, the authentication process of digital
signatures and the communication to the right client. Further, the report had provided a detailed
confidentiality and integrity process for the Virtual Private network Processes and the Protection
against the replay attacks. The report had clearly stated how SSL communication provides
confidentiality and integrity to transferred messages and how proper anti-replay attacks are
mitigated in these kinds of communications.

2VIRTUAL PRIVATE NETWORKS
Table of Contents
Introduction......................................................................................................................................3
Authentication Process................................................................................................................3
Ensuring communication to the right server............................................................................3
Digital Signatures and their role in authentication process.....................................................4
Ensuring communication to the right client.................................................................................6
Confidentiality and Integrity Processes.......................................................................................7
Confidentiality and integrity is achieved in SSL communication...........................................7
Server & client agreeing on one cipher suite...........................................................................8
Role of symmetric encryption and hash algorithms in SSL communication..........................8
Protection against Replay Attacks...............................................................................................9
Anti-replay attacks mitigation in SSL communication...........................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................3
Authentication Process................................................................................................................3
Ensuring communication to the right server............................................................................3
Digital Signatures and their role in authentication process.....................................................4
Ensuring communication to the right client.................................................................................6
Confidentiality and Integrity Processes.......................................................................................7
Confidentiality and integrity is achieved in SSL communication...........................................7
Server & client agreeing on one cipher suite...........................................................................8
Role of symmetric encryption and hash algorithms in SSL communication..........................8
Protection against Replay Attacks...............................................................................................9
Anti-replay attacks mitigation in SSL communication...........................................................9
Conclusion.......................................................................................................................................9
References......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VIRTUAL PRIVATE NETWORKS
Introduction
The enormous world of internet is often considered as one of the most unsafe when it
comes to securing the integrity of data and information. This is why the technology of VPN or
Virtual Private Networks was developed to provide a safe and intricately encrypted connection
on the internet, which is considered as an otherwise less secured network [3]. VPN allows
remote users and branch offices to have secured access over the applications they use as well as
the resources. However, it is still a dicey situation from the perspective of a user on the other
end. Therefore, the following report would put forward an idea on how the internet browser
ensures that the link provided is being communicated to the correct server, the authentication
process of digital signatures and the communication to the right client. Further, the report would
provide a detailed confidentiality and integrity process for the Virtual Private network Processes
and the Protection against the replay attacks. Thus, a clear view about the security models of the
VPN would be attainable with the report.
Authentication Process
Ensuring communication to the right server
Generally, a browser uses the functions for the fundamental operating systems as well as
their infrastructure for looking up on the IP addresses for the domain as provided by the user in
the URL or the Universal Resource Locator. The connection is then established to the IP address
for exchanging data. However, this process has a tendency to falter in several ways [4]. It can
even be a case where any malicious attacker can interfere with the DNS lookup, therefore
Introduction
The enormous world of internet is often considered as one of the most unsafe when it
comes to securing the integrity of data and information. This is why the technology of VPN or
Virtual Private Networks was developed to provide a safe and intricately encrypted connection
on the internet, which is considered as an otherwise less secured network [3]. VPN allows
remote users and branch offices to have secured access over the applications they use as well as
the resources. However, it is still a dicey situation from the perspective of a user on the other
end. Therefore, the following report would put forward an idea on how the internet browser
ensures that the link provided is being communicated to the correct server, the authentication
process of digital signatures and the communication to the right client. Further, the report would
provide a detailed confidentiality and integrity process for the Virtual Private network Processes
and the Protection against the replay attacks. Thus, a clear view about the security models of the
VPN would be attainable with the report.
Authentication Process
Ensuring communication to the right server
Generally, a browser uses the functions for the fundamental operating systems as well as
their infrastructure for looking up on the IP addresses for the domain as provided by the user in
the URL or the Universal Resource Locator. The connection is then established to the IP address
for exchanging data. However, this process has a tendency to falter in several ways [4]. It can
even be a case where any malicious attacker can interfere with the DNS lookup, therefore
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VIRTUAL PRIVATE NETWORKS
changing the IP lookup to the IP address that the attacker wishes the user to be redirected to. In
addition to this HTTPs also do not provide much security to the IP communications.
Thus, Virtual Private Network or VPN introduces IPSec, an Internet Protocol security
service that ensures that a user is redirected to the correct web server. IPSec enables that the
services that are requested by a user selects as well as negotiates between the correct security
protocols, secret keys and single or multiple algorithms. It provides a user with the basic set of
authentication and data integrity models with state of the art encryption services that ensures that
a user does not end up redirected to unprotected viewing of websites by hackers and experience
data modifications. An IPSec secured website can be identified with the security lock image
followed by the word “Secure” located the extreme left hand of the address bar, following with
the URL beginning with HTTPS notation instead of the HTTP.
Figure 1: Secured IP via Google Chrome
(Source: Google Homepage)
Digital Signatures and their role in authentication process
Working process of digital signatures in maintaining authenticity of messages: The
mathematical scheme that is used for presenting the authenticity of a document containing digital
messages is called digital signature. Digital signature protects the dignity of a digital message
sent via the network services providing a full protection by authenticating the sender,
characterizing the messages as non-repudiate such that the sender cannot deny the sending of the
changing the IP lookup to the IP address that the attacker wishes the user to be redirected to. In
addition to this HTTPs also do not provide much security to the IP communications.
Thus, Virtual Private Network or VPN introduces IPSec, an Internet Protocol security
service that ensures that a user is redirected to the correct web server. IPSec enables that the
services that are requested by a user selects as well as negotiates between the correct security
protocols, secret keys and single or multiple algorithms. It provides a user with the basic set of
authentication and data integrity models with state of the art encryption services that ensures that
a user does not end up redirected to unprotected viewing of websites by hackers and experience
data modifications. An IPSec secured website can be identified with the security lock image
followed by the word “Secure” located the extreme left hand of the address bar, following with
the URL beginning with HTTPS notation instead of the HTTP.
Figure 1: Secured IP via Google Chrome
(Source: Google Homepage)
Digital Signatures and their role in authentication process
Working process of digital signatures in maintaining authenticity of messages: The
mathematical scheme that is used for presenting the authenticity of a document containing digital
messages is called digital signature. Digital signature protects the dignity of a digital message
sent via the network services providing a full protection by authenticating the sender,
characterizing the messages as non-repudiate such that the sender cannot deny the sending of the

5VIRTUAL PRIVATE NETWORKS
message, and protecting the integrity of the message by making it unalterable within transit [6].
The ways by which the digital messages are authenticated can be described in the following
ways:
Data Integrity: Generally, it is found that the digital signatures include hashing
algorithms in the digital messages. The integrity of the data is verified with the
help of digital signatures by proofing the correct hash over the data as signed by
the sender [3]. For example, cryptographic message syntax is used to verify that
both the receiver and sender have the same hash data signed by both the parties to
check for the data integrity.
Non-repudiation: This is a process by which the sender of a digital message
cannot deny sending the message since a digital signature has the ability to find
out the exact data signed by the sender at the very beginning.
Unalterable within transit: The property of a digital signature is to authenticate
even the signing of the digital message by the person controlling the private key.
Therefore, with this property, the digital message in a signed file cannot be altered
while transition; thus maintaining the integrity of the contents of an encrypted
file.
message, and protecting the integrity of the message by making it unalterable within transit [6].
The ways by which the digital messages are authenticated can be described in the following
ways:
Data Integrity: Generally, it is found that the digital signatures include hashing
algorithms in the digital messages. The integrity of the data is verified with the
help of digital signatures by proofing the correct hash over the data as signed by
the sender [3]. For example, cryptographic message syntax is used to verify that
both the receiver and sender have the same hash data signed by both the parties to
check for the data integrity.
Non-repudiation: This is a process by which the sender of a digital message
cannot deny sending the message since a digital signature has the ability to find
out the exact data signed by the sender at the very beginning.
Unalterable within transit: The property of a digital signature is to authenticate
even the signing of the digital message by the person controlling the private key.
Therefore, with this property, the digital message in a signed file cannot be altered
while transition; thus maintaining the integrity of the contents of an encrypted
file.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6VIRTUAL PRIVATE NETWORKS
Figure 2: Details of Digital Signature
(Source: Making digital signatures with a browser, 2018)
Ensuring communication to the right client
The property of a Virtual Private Network or VPN adopts security protocols that ensure
that varied ranges of security protocols are provided to the servers as well as the client. A VPN
always ensures two-way or three-way security protocol. The protocol by which VPN ensures that
the communication is being established to the right client is known as the Layer 2 Tunnelling
Protocol (L2TP)/IPSec. This protocol is the combination of the L2TP and IPSec protocols that
Figure 2: Details of Digital Signature
(Source: Making digital signatures with a browser, 2018)
Ensuring communication to the right client
The property of a Virtual Private Network or VPN adopts security protocols that ensure
that varied ranges of security protocols are provided to the servers as well as the client. A VPN
always ensures two-way or three-way security protocol. The protocol by which VPN ensures that
the communication is being established to the right client is known as the Layer 2 Tunnelling
Protocol (L2TP)/IPSec. This protocol is the combination of the L2TP and IPSec protocols that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VIRTUAL PRIVATE NETWORKS
ensures that a VPN client is highly secured [5]. The L2TP protocol cannot ensure encryption;
however, it generates a tunnel providing the IPSec protocol to generate the encryption,
integration of data and security of channels. This ensures that all the packets are sent and
received in equal quantities having a proof that none of them were compromised, thus proving
that the clients are authentic in nature.
Confidentiality and Integrity Processes
Confidentiality and integrity is achieved in SSL communication
Confidentiality in SSL communications: The SSL communication makes use of
asymmetric and symmetric encryption to make sure that the privacy of the messages sent or
received can be maintained. SSL communication follows a handshake algorithm methodology
and a shared secret key, which is valid just for a single session [6]. The SSL communication
makes sure that all the messages are encrypted using the secret key and algorithm shared
between the client and the server, thus even when the communication is intercepted, the
confidentiality would not be compromised. In addition to that, the secret keys used for the SSL
communication are supported by asymmetric encryption to ensure no distribution problem.
Integrity provision in SSL communication: The SSL communication protects the
integrity of a sent or received by with the help of the calculation of the message digest. However,
it has to be made sure that the CipherSpec in the channel definition makes use of a hash
algorithm.
ensures that a VPN client is highly secured [5]. The L2TP protocol cannot ensure encryption;
however, it generates a tunnel providing the IPSec protocol to generate the encryption,
integration of data and security of channels. This ensures that all the packets are sent and
received in equal quantities having a proof that none of them were compromised, thus proving
that the clients are authentic in nature.
Confidentiality and Integrity Processes
Confidentiality and integrity is achieved in SSL communication
Confidentiality in SSL communications: The SSL communication makes use of
asymmetric and symmetric encryption to make sure that the privacy of the messages sent or
received can be maintained. SSL communication follows a handshake algorithm methodology
and a shared secret key, which is valid just for a single session [6]. The SSL communication
makes sure that all the messages are encrypted using the secret key and algorithm shared
between the client and the server, thus even when the communication is intercepted, the
confidentiality would not be compromised. In addition to that, the secret keys used for the SSL
communication are supported by asymmetric encryption to ensure no distribution problem.
Integrity provision in SSL communication: The SSL communication protects the
integrity of a sent or received by with the help of the calculation of the message digest. However,
it has to be made sure that the CipherSpec in the channel definition makes use of a hash
algorithm.

8VIRTUAL PRIVATE NETWORKS
Server & client agreeing on one cipher suite
The server and the client agree on the use of one single cipher suite to be negotiated
while establishing a secure channel connection (HTTPS) by being familiar with the
specifications of the SSL or Secret Socket Layers and the TSL or the Transport Socket Layer [2].
Role of symmetric encryption and hash algorithms in SSL communication
It is quite difficult to understand the functions of a symmetric encryption and the hash
algorithms during an SSL communication. Each of these has specific functionalities and can be
implemented with the help of robust communication encryption solution [5]. The role of
symmetric encryption and hash algorithm in SSL or Secret Socket Layer communication can be
described as below:
Symmetric Encryption: The property of the shared secret encryption or shared key of
Symmetric Encryption has the potential of being extremely fast and they are also comparatively
less complex than the other encryption formats. Therefore, it allows an easier implementation in
the hardware; although, it ensures proper implementation only after all configured hosts have
participated to the secret key through external means.
Hash Algorithms: A hash algorithm is different from the encryption process as this is a
form of cryptographic security, which provides a two-step process defining encryption and
decryption of a message [4]. It provides condensation of a message into a fixed length value of
irreversible format known as hash. This process is used in SSL for the verification of data.
Server & client agreeing on one cipher suite
The server and the client agree on the use of one single cipher suite to be negotiated
while establishing a secure channel connection (HTTPS) by being familiar with the
specifications of the SSL or Secret Socket Layers and the TSL or the Transport Socket Layer [2].
Role of symmetric encryption and hash algorithms in SSL communication
It is quite difficult to understand the functions of a symmetric encryption and the hash
algorithms during an SSL communication. Each of these has specific functionalities and can be
implemented with the help of robust communication encryption solution [5]. The role of
symmetric encryption and hash algorithm in SSL or Secret Socket Layer communication can be
described as below:
Symmetric Encryption: The property of the shared secret encryption or shared key of
Symmetric Encryption has the potential of being extremely fast and they are also comparatively
less complex than the other encryption formats. Therefore, it allows an easier implementation in
the hardware; although, it ensures proper implementation only after all configured hosts have
participated to the secret key through external means.
Hash Algorithms: A hash algorithm is different from the encryption process as this is a
form of cryptographic security, which provides a two-step process defining encryption and
decryption of a message [4]. It provides condensation of a message into a fixed length value of
irreversible format known as hash. This process is used in SSL for the verification of data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
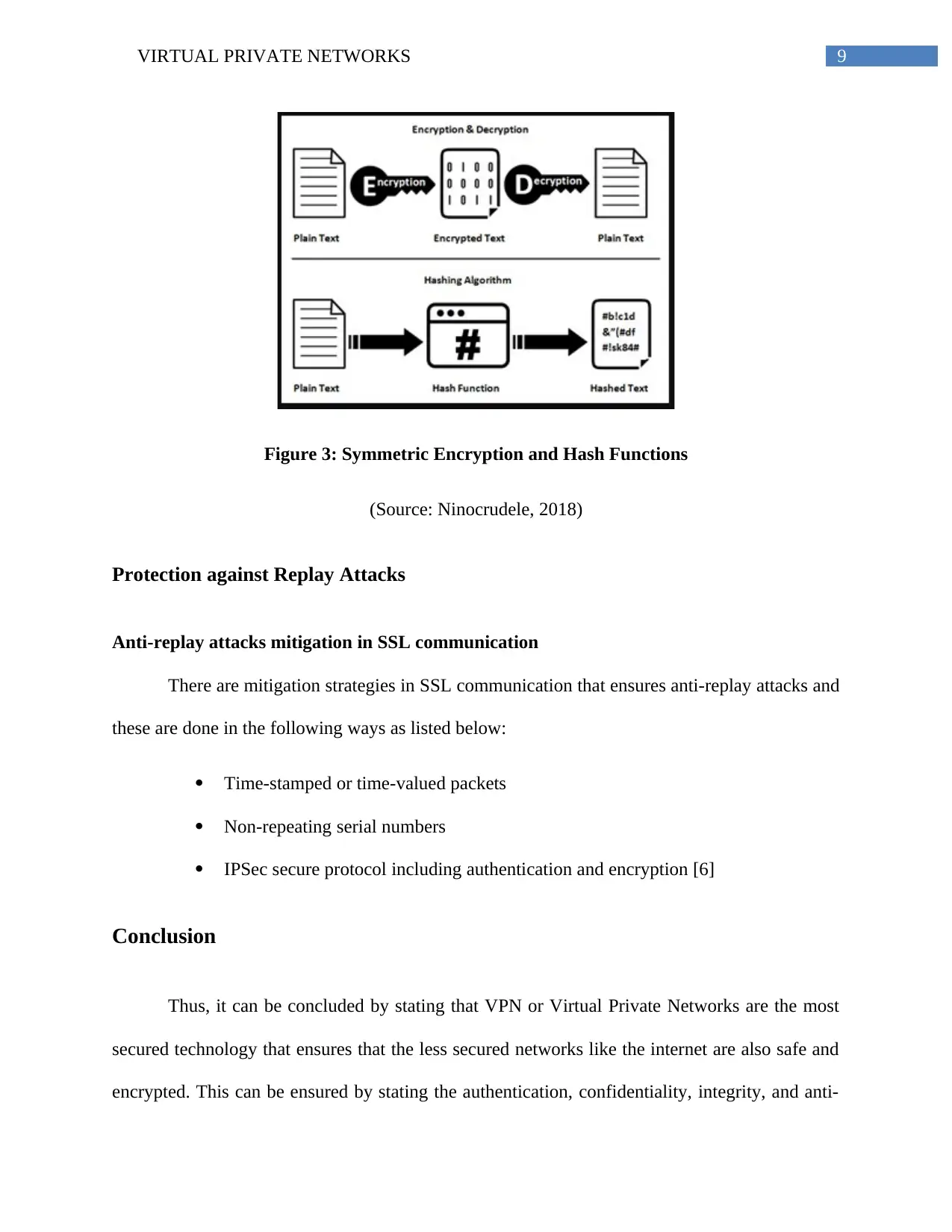
9VIRTUAL PRIVATE NETWORKS
Figure 3: Symmetric Encryption and Hash Functions
(Source: Ninocrudele, 2018)
Protection against Replay Attacks
Anti-replay attacks mitigation in SSL communication
There are mitigation strategies in SSL communication that ensures anti-replay attacks and
these are done in the following ways as listed below:
Time-stamped or time-valued packets
Non-repeating serial numbers
IPSec secure protocol including authentication and encryption [6]
Conclusion
Thus, it can be concluded by stating that VPN or Virtual Private Networks are the most
secured technology that ensures that the less secured networks like the internet are also safe and
encrypted. This can be ensured by stating the authentication, confidentiality, integrity, and anti-
Figure 3: Symmetric Encryption and Hash Functions
(Source: Ninocrudele, 2018)
Protection against Replay Attacks
Anti-replay attacks mitigation in SSL communication
There are mitigation strategies in SSL communication that ensures anti-replay attacks and
these are done in the following ways as listed below:
Time-stamped or time-valued packets
Non-repeating serial numbers
IPSec secure protocol including authentication and encryption [6]
Conclusion
Thus, it can be concluded by stating that VPN or Virtual Private Networks are the most
secured technology that ensures that the less secured networks like the internet are also safe and
encrypted. This can be ensured by stating the authentication, confidentiality, integrity, and anti-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10VIRTUAL PRIVATE NETWORKS
replay mitigation process provided by the technology. The following report thus puts forward an
idea on how the internet browser ensures that the link provided is being communicated to the
correct server, the authentication process of digital signatures and the communication to the right
client. Further, the report would provide a detailed confidentiality and integrity process for the
Virtual Private network Processes and the Protection against the replay attacks. The report also
clearly states how SSL communications provide confidentiality and integrity to transferred
messages and how proper anti-replay attacks are mitigated in these kinds of communications.
Thus, a clear view about the security models of the VPN would be attainable with the report.
replay mitigation process provided by the technology. The following report thus puts forward an
idea on how the internet browser ensures that the link provided is being communicated to the
correct server, the authentication process of digital signatures and the communication to the right
client. Further, the report would provide a detailed confidentiality and integrity process for the
Virtual Private network Processes and the Protection against the replay attacks. The report also
clearly states how SSL communications provide confidentiality and integrity to transferred
messages and how proper anti-replay attacks are mitigated in these kinds of communications.
Thus, a clear view about the security models of the VPN would be attainable with the report.

11VIRTUAL PRIVATE NETWORKS
References
[1] Making digital signatures with a browser.. Retrieved September 03, 2018, from Federal
Public Service Finances:
https://ccff02.minfin.fgov.be/CCFF_Authentication/views/login/signature/signatureHelp.html,
2018.
[2] Ninocrudele. AzureLeap – AES encryption and Hash algorithm concepts and best practices
in cloud. Retrieved September 03, 2018, from AzureLeap: http://ninocrudele.com/azureleap-aes-
encryption-and-hash-algorithm-concepts-and-best-practices-in-cloud. 2018, April 03.
[3] Gallo, Crescenzio, Michelangelo De Bonis, and Michele Perilli. "Virtual Private
Networks." Encyclopedia of Information Science and Technology, Third Edition. IGI Global,
2015. 6347-6356.
[4] Jyothi, K. Karuna, and B. Indira Reddy. "Study on Virtual Private Network (VPN), VPN’s
Protocols And Security." (2018).
[5] Jalalzai, M. H., W. B. Shahid, and M. M. W. Iqbal. "DNS security challenges and best
practices to deploy secure DNS with digital signatures." Applied Sciences and Technology
(IBCAST), 2015 12th International Bhurban Conference on. IEEE, 2015.
[6] Dragomir, Dan, et al. "A Survey on Secure Communication Protocols for IoT
Systems." Secure Internet of Things (SIoT), 2016 International Workshop on. IEEE, 2016.
References
[1] Making digital signatures with a browser.. Retrieved September 03, 2018, from Federal
Public Service Finances:
https://ccff02.minfin.fgov.be/CCFF_Authentication/views/login/signature/signatureHelp.html,
2018.
[2] Ninocrudele. AzureLeap – AES encryption and Hash algorithm concepts and best practices
in cloud. Retrieved September 03, 2018, from AzureLeap: http://ninocrudele.com/azureleap-aes-
encryption-and-hash-algorithm-concepts-and-best-practices-in-cloud. 2018, April 03.
[3] Gallo, Crescenzio, Michelangelo De Bonis, and Michele Perilli. "Virtual Private
Networks." Encyclopedia of Information Science and Technology, Third Edition. IGI Global,
2015. 6347-6356.
[4] Jyothi, K. Karuna, and B. Indira Reddy. "Study on Virtual Private Network (VPN), VPN’s
Protocols And Security." (2018).
[5] Jalalzai, M. H., W. B. Shahid, and M. M. W. Iqbal. "DNS security challenges and best
practices to deploy secure DNS with digital signatures." Applied Sciences and Technology
(IBCAST), 2015 12th International Bhurban Conference on. IEEE, 2015.
[6] Dragomir, Dan, et al. "A Survey on Secure Communication Protocols for IoT
Systems." Secure Internet of Things (SIoT), 2016 International Workshop on. IEEE, 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




