Comprehensive Report: VPN Technologies and Security - University
VerifiedAdded on 2023/02/01
|9
|2031
|99
Report
AI Summary
This report provides a comprehensive overview of VPN technologies and their associated security aspects. It delves into the significance of VPNs in organizations, highlighting their role in providing end-to-end encryption and secure connections, especially in environments with internet censorship. The report explores various VPN authentication methods, including SSL and TLS, digital signatures, and centralized access control. It analyzes the confidentiality and integrity aspects of SSL/TLS, discussing symmetric encryption and hash algorithms. The report also examines VPN client software options, OS support, and support for simultaneous users. Furthermore, it addresses anti-replay attacks and mitigation strategies. References to relevant research papers and publications support the analysis. The report offers a practical understanding of VPN implementation and security considerations, making it a valuable resource for anyone seeking to understand and implement secure network connections.
Running head: VPN TECHNOLOGIES AND SECURITY
VPN Technologies and Security
Name of the Student
Name of the University
Author Note
VPN Technologies and Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VPN TECHNOLOGIES AND SECURITY
Question A: Significance in Organizations
VPN is used to provide end to end encryption for internet connection to devices and components
of business organizations. Through encryption, VPN enables secure web connections to these devices,
irrespective of the location the employee uses the internet. Many regions have censorship imposed on the
internet. This significantly affects production of company members when working away from office or
working while out of station. Lists of several locations are shared by VPN service providers from where
countries can be chosen for ensuring fast and reliable connections to company network without blocked
content.
Pre-shared keys are required by IPSec connections for existing in client as well as server for
encrypting and sending network traffic with one another [11]. This enables attackers with opportunities to
hijack this exchanging process and crack the pre shared key.
Such problems don’t exist for SSL VPNs as public key based cryptography is used here for
negotiating any handshake or secure exchanging of encrypting keys [7]. Yet, there exists a range of
vulnerabilities in TLS/SSL a typical example of which can be Heartbleed.
Question B: Role of VPN in securing Businesses
VPNs provide security from hackers, competitors and advertisers, governments as well as fake Wi-
Fi. VPNs enable to remotely connect with a secured server which is hosting data required by the user.
Even the most advanced antivirus and firewall solutions used for securing network connections fail
to provide concrete security from hacking, intrusions and exploits. Only about one-third the malware and
viruses can be prevented by these security applications since they are largely inefficient when not regularly
updated.
The advantages that SSL VPNs have over IPsec VPNs is in security as key sharing process cannot be
hijacked. Bypassing firewalls is another advantage of SSL VPNs over IPsec VPNs as SSL is capable of
travelling over port 443 which is always allowed by most of the networks.
Question A: Significance in Organizations
VPN is used to provide end to end encryption for internet connection to devices and components
of business organizations. Through encryption, VPN enables secure web connections to these devices,
irrespective of the location the employee uses the internet. Many regions have censorship imposed on the
internet. This significantly affects production of company members when working away from office or
working while out of station. Lists of several locations are shared by VPN service providers from where
countries can be chosen for ensuring fast and reliable connections to company network without blocked
content.
Pre-shared keys are required by IPSec connections for existing in client as well as server for
encrypting and sending network traffic with one another [11]. This enables attackers with opportunities to
hijack this exchanging process and crack the pre shared key.
Such problems don’t exist for SSL VPNs as public key based cryptography is used here for
negotiating any handshake or secure exchanging of encrypting keys [7]. Yet, there exists a range of
vulnerabilities in TLS/SSL a typical example of which can be Heartbleed.
Question B: Role of VPN in securing Businesses
VPNs provide security from hackers, competitors and advertisers, governments as well as fake Wi-
Fi. VPNs enable to remotely connect with a secured server which is hosting data required by the user.
Even the most advanced antivirus and firewall solutions used for securing network connections fail
to provide concrete security from hacking, intrusions and exploits. Only about one-third the malware and
viruses can be prevented by these security applications since they are largely inefficient when not regularly
updated.
The advantages that SSL VPNs have over IPsec VPNs is in security as key sharing process cannot be
hijacked. Bypassing firewalls is another advantage of SSL VPNs over IPsec VPNs as SSL is capable of
travelling over port 443 which is always allowed by most of the networks.
2VPN TECHNOLOGIES AND SECURITY
Authentication and Access Control
Question 1: SSL and TLS authentication
Communications to the right server is ensured by browsers by checking SSL certificates of the
website visited. TSL uses a very efficient authentication protocol for messaging, generation of keys and
cipher suites. TSL offers backwards compatibility with SSL systems. In the recent versions of TSL, perfect
forward secrecy is necessary while RC4 negotiations are restricted.
Authentication and Access Control
Question 1: SSL and TLS authentication
Communications to the right server is ensured by browsers by checking SSL certificates of the
website visited. TSL uses a very efficient authentication protocol for messaging, generation of keys and
cipher suites. TSL offers backwards compatibility with SSL systems. In the recent versions of TSL, perfect
forward secrecy is necessary while RC4 negotiations are restricted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3VPN TECHNOLOGIES AND SECURITY
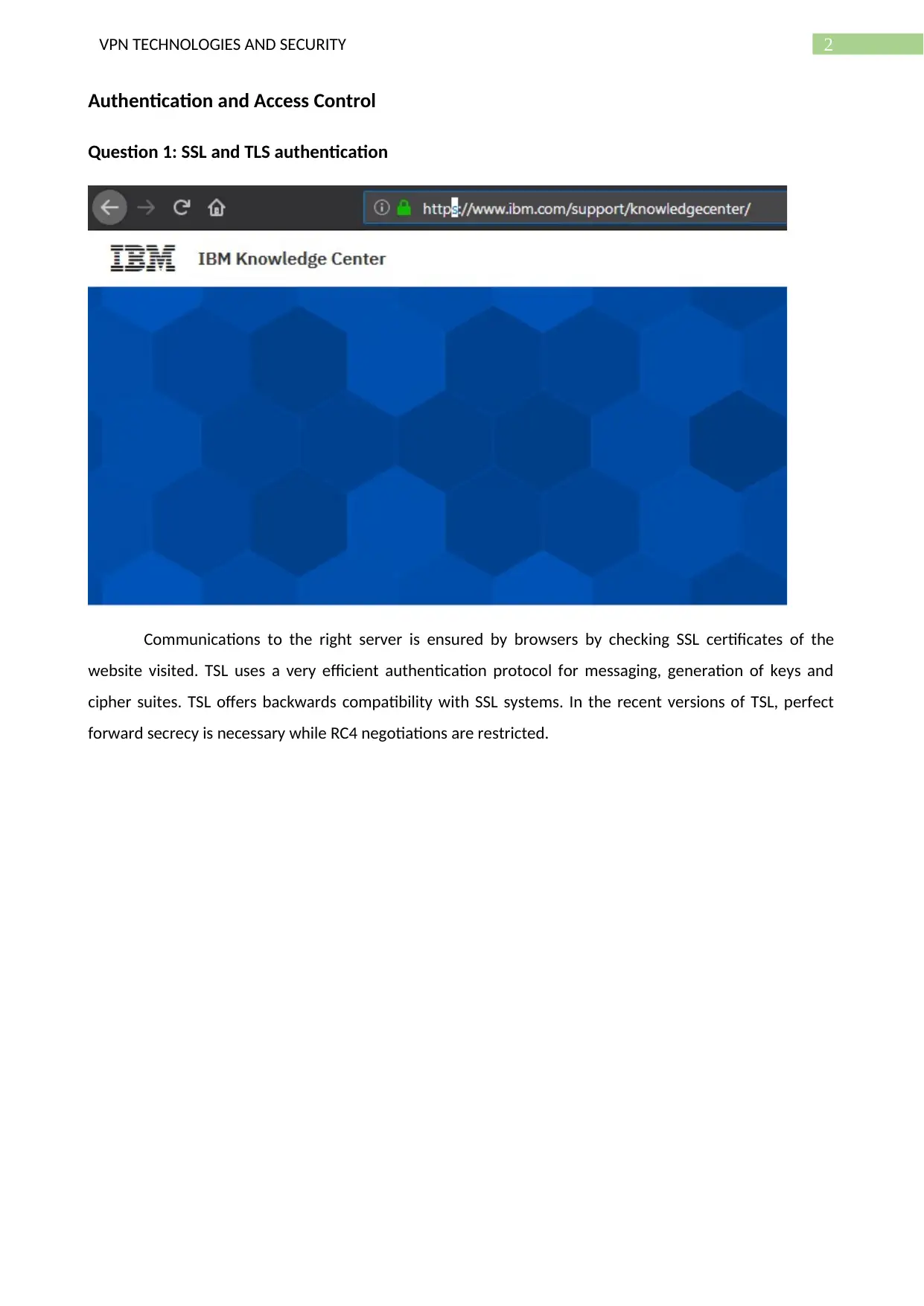
Question 2: Digital Signatures and Authentication
Digital signatures enable authentication of messaging using public key encryption. Digital signatures
refer to cryptographic values which get calculated from residing data along with secret keys only known to
the signer.
Question 3: How servers communicate with right client
In Moodle web service multiple functions are requested by clients from the provider servers. Here
Moodle serves as provider which means clients always initiate requests. Clients provide tokens or
credentials like set of username and password for authentication with all requests as also name of required
function and other necessary data. Moode then returns the data along with confirmation.
Question 4: Centralized access control and SSL/VPN
Centralized access control is another useful feature obtained from SSL VPNs. In the absence of
centralized access control, authentication and access controls over every resource in the deployed SSL need
to be done separately [6]. By eliminating this duplication of request to resources is significantly reduced.
Operations are also greatly streamlined. Users from different groups can be linked to common
authentication mechanisms and used for granting different access levels. Other common resources thus
Question 2: Digital Signatures and Authentication
Digital signatures enable authentication of messaging using public key encryption. Digital signatures
refer to cryptographic values which get calculated from residing data along with secret keys only known to
the signer.
Question 3: How servers communicate with right client
In Moodle web service multiple functions are requested by clients from the provider servers. Here
Moodle serves as provider which means clients always initiate requests. Clients provide tokens or
credentials like set of username and password for authentication with all requests as also name of required
function and other necessary data. Moode then returns the data along with confirmation.
Question 4: Centralized access control and SSL/VPN
Centralized access control is another useful feature obtained from SSL VPNs. In the absence of
centralized access control, authentication and access controls over every resource in the deployed SSL need
to be done separately [6]. By eliminating this duplication of request to resources is significantly reduced.
Operations are also greatly streamlined. Users from different groups can be linked to common
authentication mechanisms and used for granting different access levels. Other common resources thus
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4VPN TECHNOLOGIES AND SECURITY
made available for organizational members are email, intranet, calendaring and some key company
resources.
Question 5: Network access control and SSL/VPN
NAC or Network Access Control allows administrators in controlling if users can log into SSL VPN
based on an array of parameters like operating system, antivirus software, Java version among others. If
users cannot meet the specific requirements, they get not allowed to sign in.
Options of Network Access Control is accessible from SSL VPN interfaces through Access Control
NAC. Most options in NAC page operate closely with exceptions in NAC for providing actual specifications to
NAC rules.
Confidentiality and Integrity
Question 1: Analysis of Confidentiality and Integrity in SSL
A mix of symmetric and asymmetric encryptions is used by SSL and TLS for ensuring privacy of
messages. During the handshaking in SSL or in TLS, the client as well as the server agrees upon a shared
secret key and specific encryption algorithm for use on a single session only [10]. Every message
transmitted amongst the SSL client and SSL server get encrypted with this algorithm and by the key which
ensures the message is kept confidential even when intercepted. Multiple encryption algorithms are
supported by SSL as both SSL and TLS make use of asymmetric encryption while transferring shared keys
and hence, there is no key distribution problem.
Data integrity is provided by SSL as well as TLS calculation of message digests. SSL and TLS ensure
data integrity only when CipherSpec in the channel definition makes use of the hash algorithm [8]. Provided
data integrity is being sought, it is important to avoid a CipherSpec where hash algorithm is "None".
made available for organizational members are email, intranet, calendaring and some key company
resources.
Question 5: Network access control and SSL/VPN
NAC or Network Access Control allows administrators in controlling if users can log into SSL VPN
based on an array of parameters like operating system, antivirus software, Java version among others. If
users cannot meet the specific requirements, they get not allowed to sign in.
Options of Network Access Control is accessible from SSL VPN interfaces through Access Control
NAC. Most options in NAC page operate closely with exceptions in NAC for providing actual specifications to
NAC rules.
Confidentiality and Integrity
Question 1: Analysis of Confidentiality and Integrity in SSL
A mix of symmetric and asymmetric encryptions is used by SSL and TLS for ensuring privacy of
messages. During the handshaking in SSL or in TLS, the client as well as the server agrees upon a shared
secret key and specific encryption algorithm for use on a single session only [10]. Every message
transmitted amongst the SSL client and SSL server get encrypted with this algorithm and by the key which
ensures the message is kept confidential even when intercepted. Multiple encryption algorithms are
supported by SSL as both SSL and TLS make use of asymmetric encryption while transferring shared keys
and hence, there is no key distribution problem.
Data integrity is provided by SSL as well as TLS calculation of message digests. SSL and TLS ensure
data integrity only when CipherSpec in the channel definition makes use of the hash algorithm [8]. Provided
data integrity is being sought, it is important to avoid a CipherSpec where hash algorithm is "None".
5VPN TECHNOLOGIES AND SECURITY
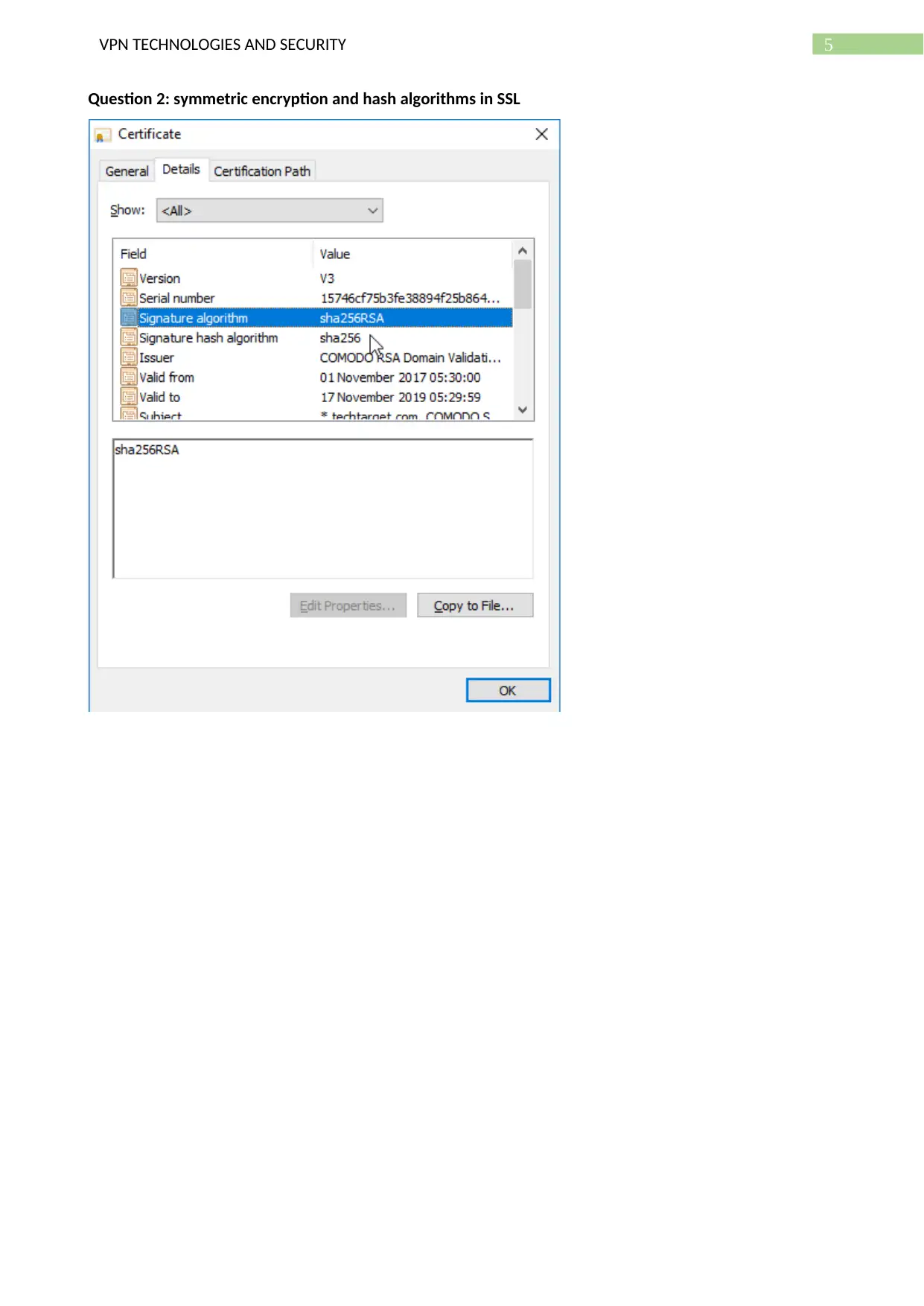
Question 2: symmetric encryption and hash algorithms in SSL
Question 2: symmetric encryption and hash algorithms in SSL
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6VPN TECHNOLOGIES AND SECURITY
Symmetric encryption also called pre shared key based encryption use a single key for encrypting
and decrypting data [5]. Here, both sender and receiver will be needing that same key for communicating.
Generally, sizes of symmetric keys are either 128 or 256 bits where the greater the key size, the tougher it
gets to crack the key. Such as a typical 128-bit key comes with
340,282,366,920,938,463,463,374,607,431,768,211,456 possibilities of encrypting codes [1]. This only
means ‘brute force’ attacks (where attackers try all possible keys till the right key is identified) takes
substantial time for cracking 128-bit keys.
Question 3: VPN client software options
The leading four VPN options for businesses are NCP Secure Entry Client, Open VPN 2.4.3,
TheGreenBow IPSec VPN Client, Microsoft VPN Client for Windows.
Question 4: VPN client OS support
Most VPN clients support windows based operating systems, out of which many support Linux and
Mac OS also. However, the windows 7,8 and 10 operating systems all come included with Microsoft’s own
VPN client included although the solution may not be as user friendly as most of the third-party VPN clients.
Configuring typical third-party VPNs are as straightforward as entering usernames along with sever
addresses. Most of the latest standardized smartphones can set up VPNs with PPTP and L2TP or IPsec
protocols [3]. Every major operating system is capable of configuring a PPTP VPN connection.
Question 5: Support for simultaneous users by VPN
When any VPN connection gets shared through the wireless network, all devices connected with
this network simultaneously comes under VPN protection [9]. As a result, it is not required to go through
the pain of installing VPN applications for every device connected to the network, thus saving time, cost
and memory. Sharing VPN connections over wireless networks also enable employees to benefit from
private as well as secure network experience in company premises.
Anti-Replay
Question 1: SSL mitigation strategies for Anti-Replay attacks
The SSL and TLS channels themselves are protected from replay attacks with MAC or Message
Authentication Code which are calculated using MAC secret as well as a sequence number [4]. The MAC
based security mechanism ensures integrity in all TLS communication channels. SSL encryption also prevent
attackers from getting hold of the token IDs for each session, which are basically the count of GET requests
that are sent for every session.
Question 2: Protecting organizations from attacks to SSL
There has been a dramatic rise in attacks to SSL having encrypted internet traffic in organizations
account for about one-third of total inbound as well as outbound network accesses. Industry wide trends
like cloud-based applications are making it mandatory for organizations to adopt encrypted connections for
Symmetric encryption also called pre shared key based encryption use a single key for encrypting
and decrypting data [5]. Here, both sender and receiver will be needing that same key for communicating.
Generally, sizes of symmetric keys are either 128 or 256 bits where the greater the key size, the tougher it
gets to crack the key. Such as a typical 128-bit key comes with
340,282,366,920,938,463,463,374,607,431,768,211,456 possibilities of encrypting codes [1]. This only
means ‘brute force’ attacks (where attackers try all possible keys till the right key is identified) takes
substantial time for cracking 128-bit keys.
Question 3: VPN client software options
The leading four VPN options for businesses are NCP Secure Entry Client, Open VPN 2.4.3,
TheGreenBow IPSec VPN Client, Microsoft VPN Client for Windows.
Question 4: VPN client OS support
Most VPN clients support windows based operating systems, out of which many support Linux and
Mac OS also. However, the windows 7,8 and 10 operating systems all come included with Microsoft’s own
VPN client included although the solution may not be as user friendly as most of the third-party VPN clients.
Configuring typical third-party VPNs are as straightforward as entering usernames along with sever
addresses. Most of the latest standardized smartphones can set up VPNs with PPTP and L2TP or IPsec
protocols [3]. Every major operating system is capable of configuring a PPTP VPN connection.
Question 5: Support for simultaneous users by VPN
When any VPN connection gets shared through the wireless network, all devices connected with
this network simultaneously comes under VPN protection [9]. As a result, it is not required to go through
the pain of installing VPN applications for every device connected to the network, thus saving time, cost
and memory. Sharing VPN connections over wireless networks also enable employees to benefit from
private as well as secure network experience in company premises.
Anti-Replay
Question 1: SSL mitigation strategies for Anti-Replay attacks
The SSL and TLS channels themselves are protected from replay attacks with MAC or Message
Authentication Code which are calculated using MAC secret as well as a sequence number [4]. The MAC
based security mechanism ensures integrity in all TLS communication channels. SSL encryption also prevent
attackers from getting hold of the token IDs for each session, which are basically the count of GET requests
that are sent for every session.
Question 2: Protecting organizations from attacks to SSL
There has been a dramatic rise in attacks to SSL having encrypted internet traffic in organizations
account for about one-third of total inbound as well as outbound network accesses. Industry wide trends
like cloud-based applications are making it mandatory for organizations to adopt encrypted connections for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7VPN TECHNOLOGIES AND SECURITY
ensuring privacy. The recently internet protocol HTTP/2 also mandates some form of encryption to be used
in all kinds of communications among the browsers and servers [2]. This importance of SSL protected
solutions continues to gain in value with the number of encrypted connections being on the rise and thus
the count of attacks to SSL.
ensuring privacy. The recently internet protocol HTTP/2 also mandates some form of encryption to be used
in all kinds of communications among the browsers and servers [2]. This importance of SSL protected
solutions continues to gain in value with the number of encrypted connections being on the rise and thus
the count of attacks to SSL.

8VPN TECHNOLOGIES AND SECURITY
References
[1] B.F. Cruz, K.N. Domingo, F.E. De Guzman, J.B. Cotiangco, and C.B. Hilario, Expanded 128-bit Data
Encryption Standard. Int. J. Comput. Sci. Mob. Comput, 68(8), pp.133-142., 2017.
[2] D.B.C. Marques, Learning from HTTP/2 encrypted traffic: a machine learning-based analysis tool., 2018.
[3] F.A. Salman, Implementation of IPsec-VPN tunneling using GNS3. Indonesian Journal of Electrical
Engineering and Computer Science, 7(3), pp.855-860., 2017.
[4] L. Perrin, and A. Brisson, August. Enhancing transport layer security with Dynamic Identity Verification
and Authentication (DIVA): Maintaining and enhancing SSL/TLS reliability. In 2017 IEEE SmartWorld,
Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing &
Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI) (pp. 1-5). IEEE., 2017.
[5] M. Bellare, D. Kane, and P. Rogaway, August. Big-key symmetric encryption: Resisting key exfiltration. In
Annual International Cryptology Conference (pp. 373-402). Springer, Berlin, Heidelberg., 2016.
[6] M. Liyanage, P. Kumar, M. Ylianttila, and A. Gurtov, Novel secure VPN architectures for LTE backhaul
networks. Security and Communication Networks, 9(10), pp.1198-1215., 2016.
[7] M. Zhang, Study on Remote Access for Library Based on SSL VPN. International Journal of Control and
Automation, 9(1), pp.111-122., 2016.
[8] R. Oppliger, SSL and TLS: Theory and Practice. Artech House., 2016.
[9] S. Xiao, March. Technical Analysis and Application of VPN. In 2017 7th International Conference on
Education, Management, Computer and Society (EMCS 2017). Atlantis Press., 2017.
[10] S.M. Kim, Y.H. Goo, M.S. Kim, S.G. Choi, and M.J. Choi, August. A method for service identification of
SSL/TLS encrypted traffic with the relation of session ID and Server IP. In 2015 17th Asia-Pacific Network
Operations and Management Symposium (APNOMS) (pp. 487-490). IEEE., 2015.
[11] Z. Zhipeng, S. Chandel, S. Jingyao, Y. Shilin, Y. Yunnan, and Z. Jingji, February. VPN: a Boon or Trap?: A
Comparative Study of MPLS, IPSec, and SSL Virtual Private Networks. In 2018 Second International
Conference on Computing Methodologies and Communication (ICCMC) (pp. 510-515). IEEE., 2018.
References
[1] B.F. Cruz, K.N. Domingo, F.E. De Guzman, J.B. Cotiangco, and C.B. Hilario, Expanded 128-bit Data
Encryption Standard. Int. J. Comput. Sci. Mob. Comput, 68(8), pp.133-142., 2017.
[2] D.B.C. Marques, Learning from HTTP/2 encrypted traffic: a machine learning-based analysis tool., 2018.
[3] F.A. Salman, Implementation of IPsec-VPN tunneling using GNS3. Indonesian Journal of Electrical
Engineering and Computer Science, 7(3), pp.855-860., 2017.
[4] L. Perrin, and A. Brisson, August. Enhancing transport layer security with Dynamic Identity Verification
and Authentication (DIVA): Maintaining and enhancing SSL/TLS reliability. In 2017 IEEE SmartWorld,
Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing &
Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI) (pp. 1-5). IEEE., 2017.
[5] M. Bellare, D. Kane, and P. Rogaway, August. Big-key symmetric encryption: Resisting key exfiltration. In
Annual International Cryptology Conference (pp. 373-402). Springer, Berlin, Heidelberg., 2016.
[6] M. Liyanage, P. Kumar, M. Ylianttila, and A. Gurtov, Novel secure VPN architectures for LTE backhaul
networks. Security and Communication Networks, 9(10), pp.1198-1215., 2016.
[7] M. Zhang, Study on Remote Access for Library Based on SSL VPN. International Journal of Control and
Automation, 9(1), pp.111-122., 2016.
[8] R. Oppliger, SSL and TLS: Theory and Practice. Artech House., 2016.
[9] S. Xiao, March. Technical Analysis and Application of VPN. In 2017 7th International Conference on
Education, Management, Computer and Society (EMCS 2017). Atlantis Press., 2017.
[10] S.M. Kim, Y.H. Goo, M.S. Kim, S.G. Choi, and M.J. Choi, August. A method for service identification of
SSL/TLS encrypted traffic with the relation of session ID and Server IP. In 2015 17th Asia-Pacific Network
Operations and Management Symposium (APNOMS) (pp. 487-490). IEEE., 2015.
[11] Z. Zhipeng, S. Chandel, S. Jingyao, Y. Shilin, Y. Yunnan, and Z. Jingji, February. VPN: a Boon or Trap?: A
Comparative Study of MPLS, IPSec, and SSL Virtual Private Networks. In 2018 Second International
Conference on Computing Methodologies and Communication (ICCMC) (pp. 510-515). IEEE., 2018.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




