Assignment 1 - VPN Technologies and Security Issues Report - MN610
VerifiedAdded on 2023/02/01
|7
|569
|42
Report
AI Summary
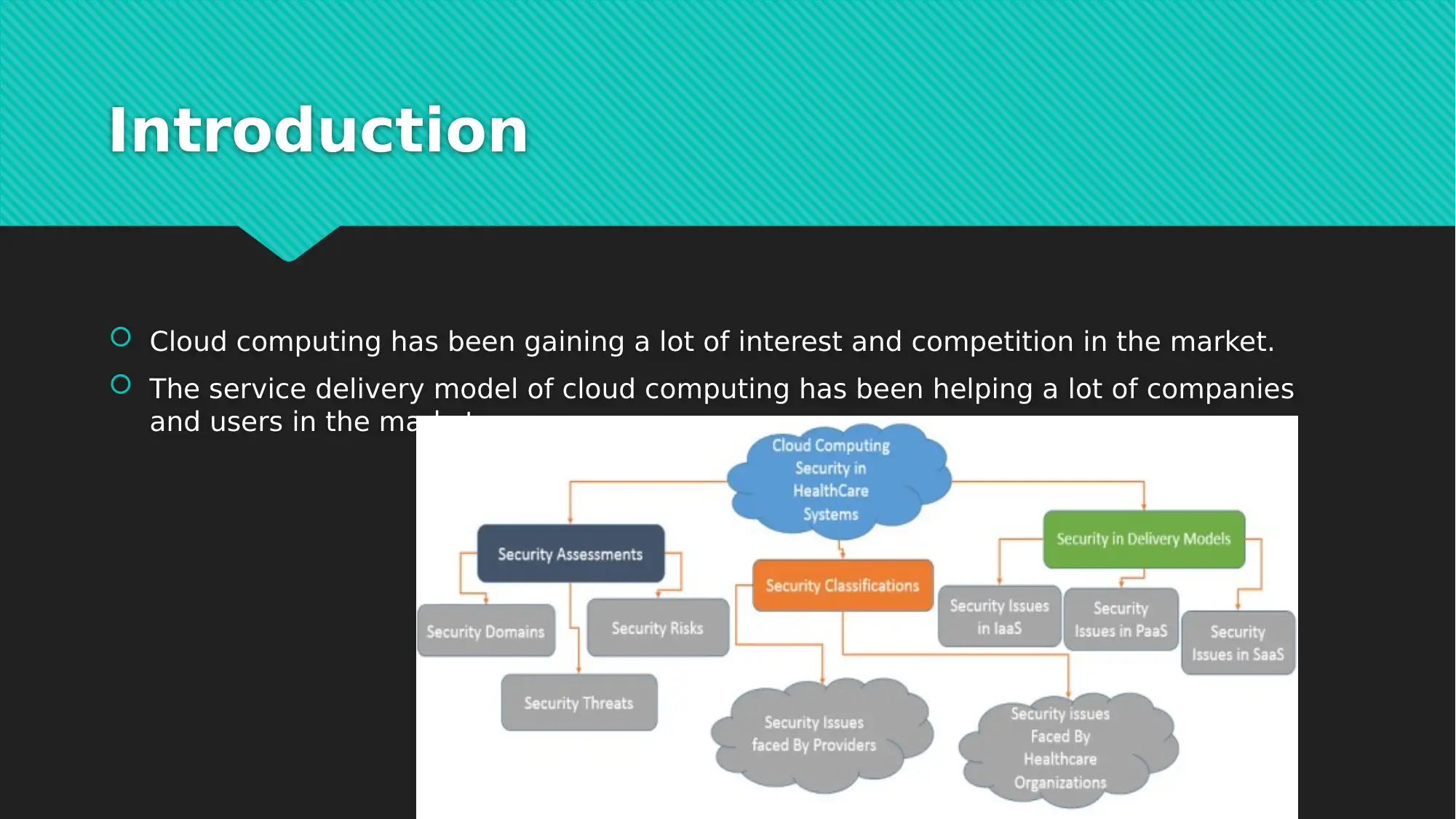
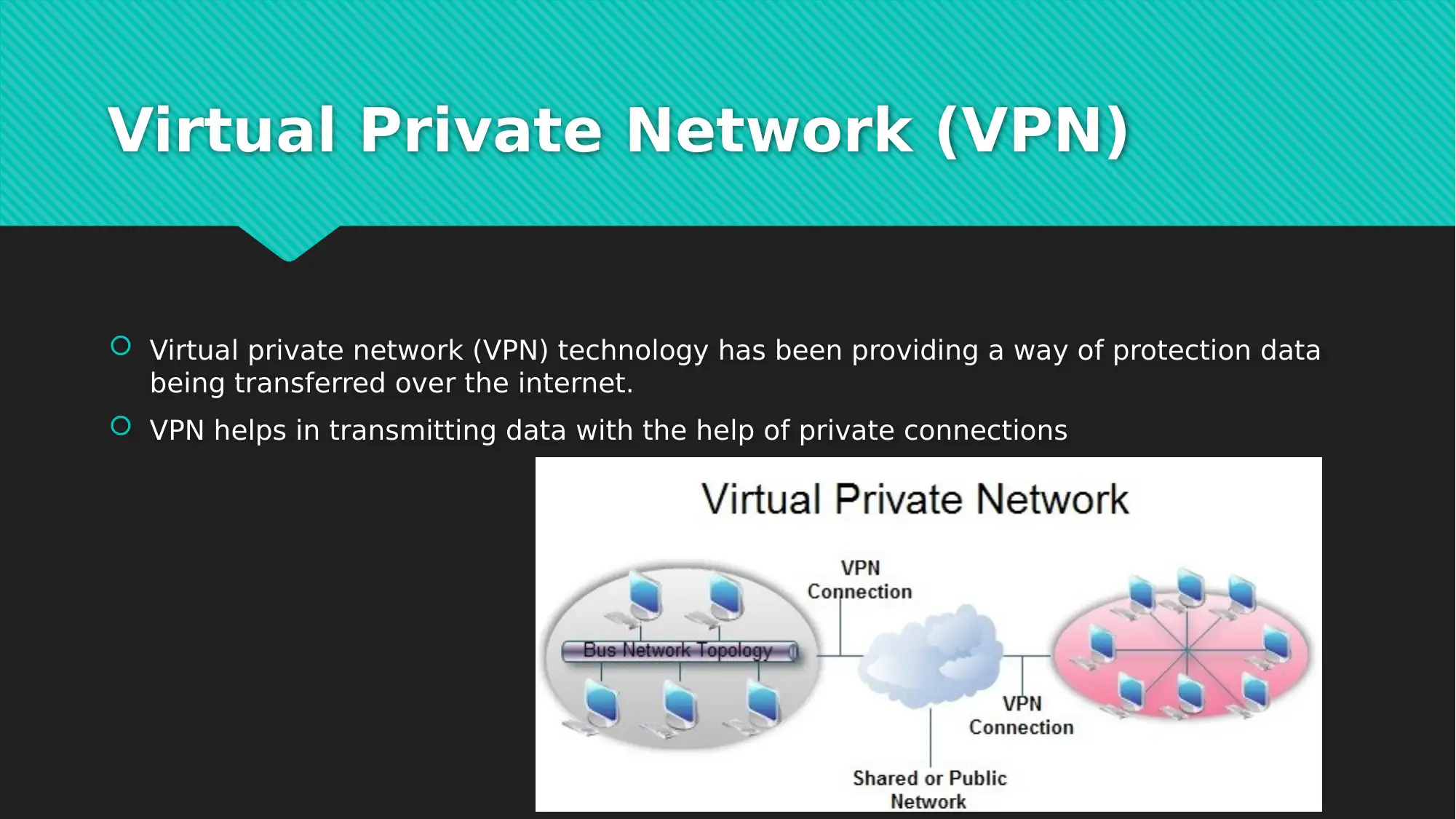
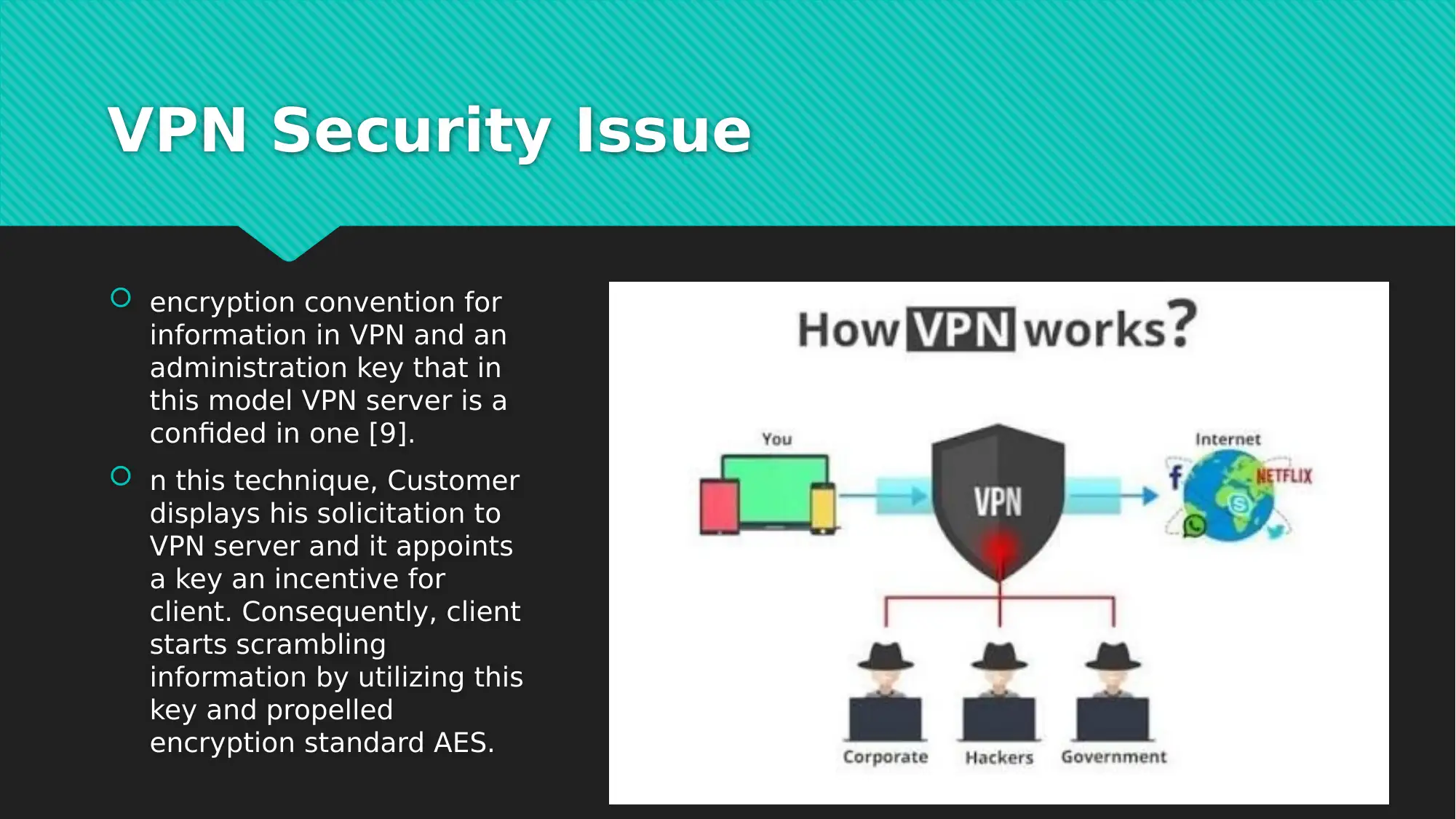
This report examines the crucial role of Virtual Private Networks (VPNs) in securing data within cloud computing environments. It begins by highlighting the growing interest in cloud computing and its service delivery models, emphasizing the associated data security challenges, particularly from malicious actors targeting cloud databases. The report then focuses on VPN technology as a primary solution for protecting data transmitted over the internet. It delves into the specifics of VPN security issues, including encryption conventions and the use of a trusted VPN server that assigns encryption keys. The customer then uses this key to encrypt data using advanced encryption standards such as AES. The conclusion underscores the benefits of cloud computing for businesses and the importance of data security, and the report investigates different VPN encryption strategies. The report includes multiple references to support the analysis.
1 out of 7










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)