Securing VSU's Wireless Network: An 802.1x Implementation Report
VerifiedAdded on 2020/05/16
|10
|2278
|148
Report
AI Summary
This report presents an analysis and design for a secured wireless LAN at Vancouver State University (VSU), focusing on implementing 802.1x authentication to enhance network security. The report addresses the security requirements for VSU's wireless network, including encryption and two-factor authentication, and proposes 802.1x as a solution for access control. It outlines a step-by-step procedure for implementing 802.1x, including configuring the core system, supplicant accounts, and port access control. The report also discusses the ethical implications of the wireless LAN design. The network design includes a three-layer switch, VLANs for voice and data packets, and DHCP protocol for IP allocation. The design utilizes TDM, HDLC, and frame relay for network configuration and RTP and SDP for VOIP devices. The report concludes that the 802.1x implementation enhances security but acknowledges ethical considerations. The report provides a detailed overview of the implementation process and the associated design choices.

Running head: WIRELESS NETWORKS & SECURITY
Analysis and Design of a Secured Wireless LAN
Name of the Student
Name of the University
Author’s Note
Analysis and Design of a Secured Wireless LAN
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORKS & SECURITY
Executive Summary
The purpose of this report is to “implement 802.1 x authentication for VSU’s wireless network” and
facilitate a secured network across the campus. It is a network access control that is applied to the
wireless network in manner to provide the facility of a secured network and support the wired networks
for enabling the network administrator and that is helpful in providing access control to both the wired
and the wireless network. This report presents the aspects related to the security requirements for
VSU’s (Vancouver State University) wireless network and present 802.1x as the solution for accessing
secured network as per the case study. A network design has been presented that will be explaining the
distribution of the network and its access.
WIRELESS NETWORKS & SECURITY
Executive Summary
The purpose of this report is to “implement 802.1 x authentication for VSU’s wireless network” and
facilitate a secured network across the campus. It is a network access control that is applied to the
wireless network in manner to provide the facility of a secured network and support the wired networks
for enabling the network administrator and that is helpful in providing access control to both the wired
and the wireless network. This report presents the aspects related to the security requirements for
VSU’s (Vancouver State University) wireless network and present 802.1x as the solution for accessing
secured network as per the case study. A network design has been presented that will be explaining the
distribution of the network and its access.

2
WIRELESS NETWORKS & SECURITY
Table of Contents
Introduction....................................................................................................................................3
Security Requirements for Wireless Network of VSU-Vancouver...................................................3
802.1x Authentication Mechanism.................................................................................................3
Step-by-Step Procedure of Implementing 802.1x...........................................................................4
Ethical Implication on VSU Secured Wireless LAN design...............................................................5
Design.............................................................................................................................................6
Evaluate / Justification....................................................................................................................7
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................8
WIRELESS NETWORKS & SECURITY
Table of Contents
Introduction....................................................................................................................................3
Security Requirements for Wireless Network of VSU-Vancouver...................................................3
802.1x Authentication Mechanism.................................................................................................3
Step-by-Step Procedure of Implementing 802.1x...........................................................................4
Ethical Implication on VSU Secured Wireless LAN design...............................................................5
Design.............................................................................................................................................6
Evaluate / Justification....................................................................................................................7
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRELESS NETWORKS & SECURITY
Introduction
VSU has 4000 students and 400 faculty those are connected via a wireless network system and it
is necessary to implement a network access control that is capable of restricting and securing the
authorization and authentication to the resources within the network. It is an attempt to implement a
system that is feasible within the existing system of the VSU and a cost effective measure for ensuring
the security of the wireless network. It has three component to perform the authentication and
authorization of the physical devices such as router and switches and other network devices. The goal of
this implementation is to define the authorization and authentication control for the devices and the
users those are connected with the wireless network within the VSU campus.
Security Requirements for Wireless Network of VSU-Vancouver
VSU needs to protect the sensitive data in manner to detect the temper data and add limitations
to the authorization and authentication to the network and data or information being transferred or
stored in the network. The very first requirement is the encryption that is being travelled in the public
network through using certified algorithms. Another requirement for securing this wireless network is
two-authentication that is combination of a security token and something that the user knows. In this
section biometric approaches can be recommended as the best option. WPA, WEP, and WPA2 are the
necessary security requirements for establishment of the secured network within the wireless network
facility of the VSU [6]. Regardless of the fact of encryption and other physical securities, wireless
network cannot be completely secured with the wired connections. These three protocols are capable of
protecting the wireless network and the systems needs to be upgraded after the implementation of this
protocol within the WLAN of the VSU. However, intrusion could not be completely stopped with this
protocol and thus similar protocol with inheritance properties WPA can also be implemented to the
network in manner to provide safe passage and exchange of the information [11]. WPS could be helpful
in enhancing the presented network and will also allow the devices to be linked with the modern access
point.
802.1x Authentication Mechanism
The presented network access has three components that includes core in the centre including
routers, network access that includes switches, access point and others and the third component is the
distribution that includes switches and PCs. The latter feature of the 802.1x is helpful in providing
WIRELESS NETWORKS & SECURITY
Introduction
VSU has 4000 students and 400 faculty those are connected via a wireless network system and it
is necessary to implement a network access control that is capable of restricting and securing the
authorization and authentication to the resources within the network. It is an attempt to implement a
system that is feasible within the existing system of the VSU and a cost effective measure for ensuring
the security of the wireless network. It has three component to perform the authentication and
authorization of the physical devices such as router and switches and other network devices. The goal of
this implementation is to define the authorization and authentication control for the devices and the
users those are connected with the wireless network within the VSU campus.
Security Requirements for Wireless Network of VSU-Vancouver
VSU needs to protect the sensitive data in manner to detect the temper data and add limitations
to the authorization and authentication to the network and data or information being transferred or
stored in the network. The very first requirement is the encryption that is being travelled in the public
network through using certified algorithms. Another requirement for securing this wireless network is
two-authentication that is combination of a security token and something that the user knows. In this
section biometric approaches can be recommended as the best option. WPA, WEP, and WPA2 are the
necessary security requirements for establishment of the secured network within the wireless network
facility of the VSU [6]. Regardless of the fact of encryption and other physical securities, wireless
network cannot be completely secured with the wired connections. These three protocols are capable of
protecting the wireless network and the systems needs to be upgraded after the implementation of this
protocol within the WLAN of the VSU. However, intrusion could not be completely stopped with this
protocol and thus similar protocol with inheritance properties WPA can also be implemented to the
network in manner to provide safe passage and exchange of the information [11]. WPS could be helpful
in enhancing the presented network and will also allow the devices to be linked with the modern access
point.
802.1x Authentication Mechanism
The presented network access has three components that includes core in the centre including
routers, network access that includes switches, access point and others and the third component is the
distribution that includes switches and PCs. The latter feature of the 802.1x is helpful in providing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
WIRELESS NETWORKS & SECURITY
authentication manageable in the installation of this network [4]. The architecture presented in the
network provides leverage to the decentralized access device in manner to provide scalable and cost
effective encryption, at this mean time access control centralization can be implemented to some of the
authentication servers.
While running EAP over LAN, the encapsulation of EAP occurs over the message of LAN
(EAPOL). The EAPOL packets’ format has been defined in the specification of the 802.1x. This led to the
occurrence of the EAPOL communication between the authenticator (wireless access point) and the
supplicant (user station) [8]. Thereafter the RADIUS protocol has been applied for the communication
between the RADIUS server and the authenticator. When the end user tries to connect with the WLAN
the authentication process gets started. After receiving the request, the virtual port gets created with
the supplicant and during this situation, for the end user, the authenticator will be acting as the proxy to
pass the authentication server on the behalf of the proxy [5]. The authentication data to the server will
be limited by the authenticator and thereafter the negotiation takes place.
Step-by-Step Procedure of Implementing 802.1x
The core centralized system will be required including the routers that will be a radius server on
the management stations as it is not supported with the TACACS+ authentication protocol.
Thereafter, supplicant accounts will be created on the RADIUS server that will include the
following considerations:
The users of the VSU account will be connected to the authenticator port including the user
name and password of the students and faculties while establishing 802.1x authentication mode [1].
MAC address of the node will be needed for the accounts connected to the authenticator port for both
the username and the password. Every user and the system within the campus will have 802.1x client
software for the connections established for the 802.1x authentication port.
Third step will be Configuration of the Core system including the RADIUS client through
configuring encryption key and IP address of the authentication servers on the VSU network.
Forth step will be to configure the port access control on the switches that include the
configuration of 802.1x port parameters, specifying the port roles, and enabling the “802.1x port-based
network access control.”
WIRELESS NETWORKS & SECURITY
authentication manageable in the installation of this network [4]. The architecture presented in the
network provides leverage to the decentralized access device in manner to provide scalable and cost
effective encryption, at this mean time access control centralization can be implemented to some of the
authentication servers.
While running EAP over LAN, the encapsulation of EAP occurs over the message of LAN
(EAPOL). The EAPOL packets’ format has been defined in the specification of the 802.1x. This led to the
occurrence of the EAPOL communication between the authenticator (wireless access point) and the
supplicant (user station) [8]. Thereafter the RADIUS protocol has been applied for the communication
between the RADIUS server and the authenticator. When the end user tries to connect with the WLAN
the authentication process gets started. After receiving the request, the virtual port gets created with
the supplicant and during this situation, for the end user, the authenticator will be acting as the proxy to
pass the authentication server on the behalf of the proxy [5]. The authentication data to the server will
be limited by the authenticator and thereafter the negotiation takes place.
Step-by-Step Procedure of Implementing 802.1x
The core centralized system will be required including the routers that will be a radius server on
the management stations as it is not supported with the TACACS+ authentication protocol.
Thereafter, supplicant accounts will be created on the RADIUS server that will include the
following considerations:
The users of the VSU account will be connected to the authenticator port including the user
name and password of the students and faculties while establishing 802.1x authentication mode [1].
MAC address of the node will be needed for the accounts connected to the authenticator port for both
the username and the password. Every user and the system within the campus will have 802.1x client
software for the connections established for the 802.1x authentication port.
Third step will be Configuration of the Core system including the RADIUS client through
configuring encryption key and IP address of the authentication servers on the VSU network.
Forth step will be to configure the port access control on the switches that include the
configuration of 802.1x port parameters, specifying the port roles, and enabling the “802.1x port-based
network access control.”

5
WIRELESS NETWORKS & SECURITY
Ethical Implication on VSU Secured Wireless LAN design
There are many ethical issues in the implication of wireless LAN design for the VSU as if
proper authorization and authentication is not implemented to the network it could be misused by any
unauthorized individual [3]. The network need to be password protected as keeping the network open
could be the easiest path for the intruders to enter the network and thus, access to the data or
information saved in the network and could allow the intruder to access, manipulate or delete the data.
This could also lead to privacy and security issues of the individuals connected to the network. There are
the possibilities that any internal unauthorized user could get access to the data or information of other
individual connected via the same network.
WIRELESS NETWORKS & SECURITY
Ethical Implication on VSU Secured Wireless LAN design
There are many ethical issues in the implication of wireless LAN design for the VSU as if
proper authorization and authentication is not implemented to the network it could be misused by any
unauthorized individual [3]. The network need to be password protected as keeping the network open
could be the easiest path for the intruders to enter the network and thus, access to the data or
information saved in the network and could allow the intruder to access, manipulate or delete the data.
This could also lead to privacy and security issues of the individuals connected to the network. There are
the possibilities that any internal unauthorized user could get access to the data or information of other
individual connected via the same network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRELESS NETWORKS & SECURITY
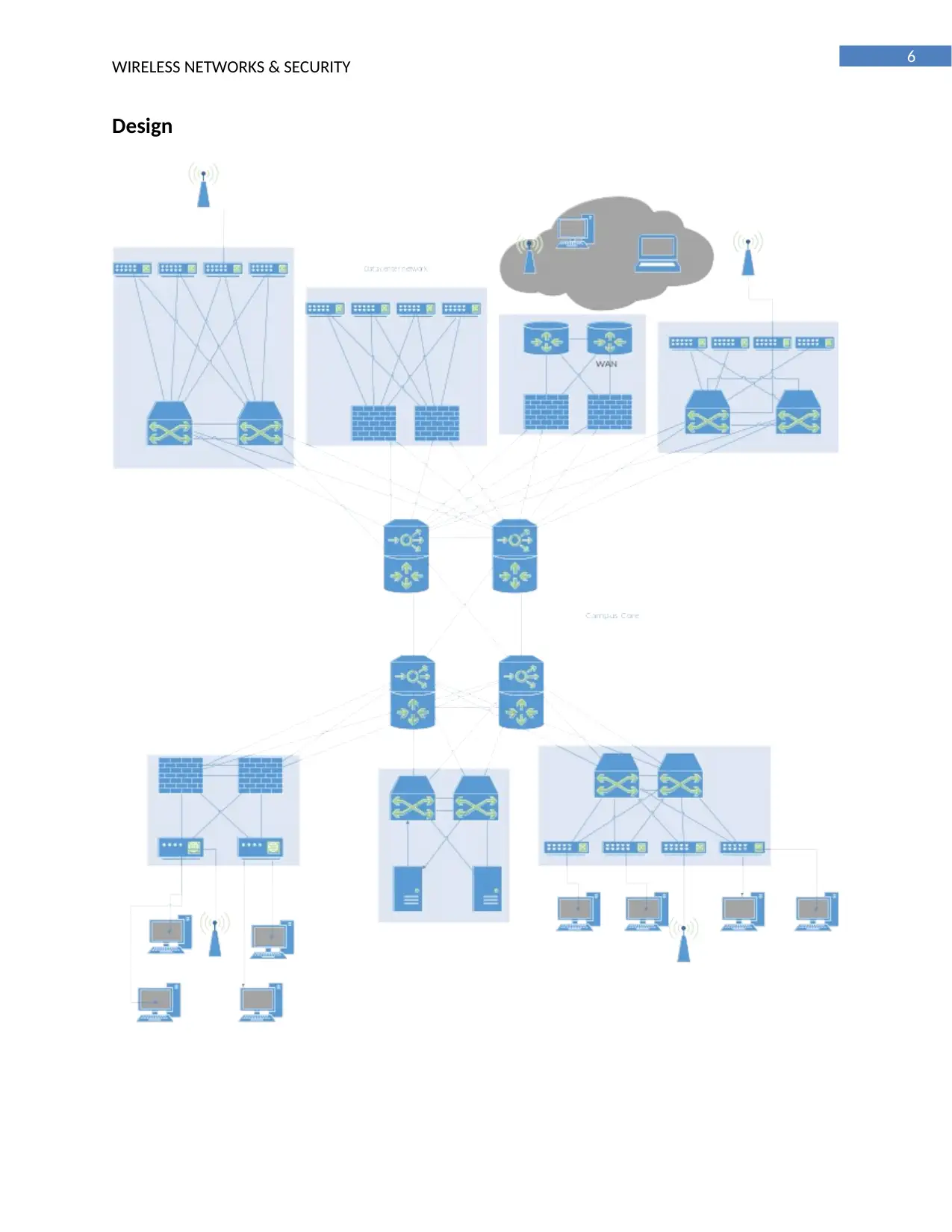
Design
WIRELESS NETWORKS & SECURITY
Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
WIRELESS NETWORKS & SECURITY
Evaluate / Justification
The presented network design has been created the required data points that need to be
established at each points of the connectivity. In manner to enhance the efficiency and providing
continuous flow of the network, access points have been installed at the layers of the network [7]. A
three layer switch has been also implemented within the ground floor router in manner to manage the
network and eliminate the risk of the network downtime while using the network. The voice packets and
the data packets have been sent to the network through using different VLAN in manner to reduce the
risk related to the communication delay and congestions in the risk. The routers those have been
installed in the network are configured with the DHCP protocol in manner to allocate the IP to the
connected network at its nodes [12]. For the configuration of the network, TDM, HDLC, and frame Relay
has been used in which the frame relay has been implemented for the packet switching and high level
data linkage control in manner to establish the transmission of the data packets in the network. In
manner to avoid the deadlock situation in the network, time division multiplexing has been established
in the network in manner to enhance the security standard and efficiency of the developed system [2].
For the configuration of the VOIP devices within the network, RTP (Real Time Transfer Protocol) and SDP
(Session Description Protocol) has been established.
Conclusion
Based on the above report it can be concluded that and established system has been presented
for the implementation of the 802.1x based “wireless network for the authorization and authentication
at the Vancouver State University” and related aspects of this implementation. This report explains the
requirements needed for the security of the wireless network within the campus of the VSU and
presented 802.1x as the solution for enhancing the security of the wireless network. This report
emphasize on the enhancement of the security of the wireless network established within the existing
system of the VSU. A diagram has been presented in this report that is a complete description of the
network in manner to establish then secured network and establish the authorization and
authentication of the users connected via the network. 802.1x authorization mechanism has been also
proposed in this report that is being applied to the network and this mechanism is helpful in
understanding the procedures involved in the protection of the network. This ;implementation can be a
helpful measure for the enhancement of the security of the wireless network established within the VSU
however,, there are several ethical implications within the network that are the crucial factors while
configuring the network with 802.1x authorization and authentication.
WIRELESS NETWORKS & SECURITY
Evaluate / Justification
The presented network design has been created the required data points that need to be
established at each points of the connectivity. In manner to enhance the efficiency and providing
continuous flow of the network, access points have been installed at the layers of the network [7]. A
three layer switch has been also implemented within the ground floor router in manner to manage the
network and eliminate the risk of the network downtime while using the network. The voice packets and
the data packets have been sent to the network through using different VLAN in manner to reduce the
risk related to the communication delay and congestions in the risk. The routers those have been
installed in the network are configured with the DHCP protocol in manner to allocate the IP to the
connected network at its nodes [12]. For the configuration of the network, TDM, HDLC, and frame Relay
has been used in which the frame relay has been implemented for the packet switching and high level
data linkage control in manner to establish the transmission of the data packets in the network. In
manner to avoid the deadlock situation in the network, time division multiplexing has been established
in the network in manner to enhance the security standard and efficiency of the developed system [2].
For the configuration of the VOIP devices within the network, RTP (Real Time Transfer Protocol) and SDP
(Session Description Protocol) has been established.
Conclusion
Based on the above report it can be concluded that and established system has been presented
for the implementation of the 802.1x based “wireless network for the authorization and authentication
at the Vancouver State University” and related aspects of this implementation. This report explains the
requirements needed for the security of the wireless network within the campus of the VSU and
presented 802.1x as the solution for enhancing the security of the wireless network. This report
emphasize on the enhancement of the security of the wireless network established within the existing
system of the VSU. A diagram has been presented in this report that is a complete description of the
network in manner to establish then secured network and establish the authorization and
authentication of the users connected via the network. 802.1x authorization mechanism has been also
proposed in this report that is being applied to the network and this mechanism is helpful in
understanding the procedures involved in the protection of the network. This ;implementation can be a
helpful measure for the enhancement of the security of the wireless network established within the VSU
however,, there are several ethical implications within the network that are the crucial factors while
configuring the network with 802.1x authorization and authentication.

8
WIRELESS NETWORKS & SECURITY
Bibliography
[1] J. Xu, Z. Zhang, and J. Rong, “The Campus Road Planning and Design Research,” Procedia - Soc.
Behav. Sci., vol. 43, pp. 579–586, 2012.
[2] J. Wang, X. Bai, and J. She, “Wireless Campus Network Design and Optimization Based on
OPNET,” Proc. - 2015 Int. Conf. Cyber-Enabled Distrib. Comput. Knowl. Discov. CyberC 2015, pp. 525–528,
2015.
[3] M. Guo and J. Guo, “Constructing smart campus network based on ubiquitous sensor
technology,” in 2015 5th International Conference on Information Science and Technology, ICIST 2015 ,
2015, pp. 265–268.
[4] M. C. Chan, C. Chen, J. X. Huang, T. Kuo, L. H. Yen, and C. C. Tseng, “OpenNet: A simulator for
software-defined wireless local area network,” in IEEE Wireless Communications and Networking
Conference, WCNC, 2014, pp. 3332–3336.
[5] Z. Du, Y. Liu, and Y. Wang, “Relation based access control in campus social network system,” in
Procedia Computer Science, 2013, vol. 17, pp. 14–20.
[6] A. Masiero and A. Cenedese, “On triangulation algorithms in large scale camera network
systems,” in Proceedings of the American Control Conference, 2012.
[7] R. Balakrishna, H. Koutsopoulos, M. Ben-Akiva, B. Fernandez Ruiz, M. Mehta, J. Barcelo, S.
Zhang, H. Yang, and L. Singh, “Simulation-Based Evaluation of Advanced Traveler Information Systems,”
Transp. Res. Rec., vol. 1225, no. February, pp. 90–98, 2014.
[8] G. N. Bifulco, G. E. Cantarella, and F. Simonelli, “Design of signal setting and advanced traveler
information systems,” in Journal of Intelligent Transportation Systems: Technology, Planning, and
Operations, 2014, vol. 18, no. 1, pp. 30–40.
[9] J. Zhang, T. Arentze, and H. Timmermans, “A multimodal transport network model for advanced
traveler information systems,” J. Ubiquitous Syst. Pervasive Networks, vol. 4, no. 1, pp. 21–27, 2012.
[10] A. Ben Ahmed, M. Meyer, Y. Okuyama, and A. Ben Abdallah, “Adaptive error- and traffic-aware
router architecture for 3D network-on-chip systems,” in Proceedings - 2014 IEEE 8th International
Symposium on Embedded Multicore/Manycore SoCs, MCSoC 2014, 2014, pp. 197–204.
WIRELESS NETWORKS & SECURITY
Bibliography
[1] J. Xu, Z. Zhang, and J. Rong, “The Campus Road Planning and Design Research,” Procedia - Soc.
Behav. Sci., vol. 43, pp. 579–586, 2012.
[2] J. Wang, X. Bai, and J. She, “Wireless Campus Network Design and Optimization Based on
OPNET,” Proc. - 2015 Int. Conf. Cyber-Enabled Distrib. Comput. Knowl. Discov. CyberC 2015, pp. 525–528,
2015.
[3] M. Guo and J. Guo, “Constructing smart campus network based on ubiquitous sensor
technology,” in 2015 5th International Conference on Information Science and Technology, ICIST 2015 ,
2015, pp. 265–268.
[4] M. C. Chan, C. Chen, J. X. Huang, T. Kuo, L. H. Yen, and C. C. Tseng, “OpenNet: A simulator for
software-defined wireless local area network,” in IEEE Wireless Communications and Networking
Conference, WCNC, 2014, pp. 3332–3336.
[5] Z. Du, Y. Liu, and Y. Wang, “Relation based access control in campus social network system,” in
Procedia Computer Science, 2013, vol. 17, pp. 14–20.
[6] A. Masiero and A. Cenedese, “On triangulation algorithms in large scale camera network
systems,” in Proceedings of the American Control Conference, 2012.
[7] R. Balakrishna, H. Koutsopoulos, M. Ben-Akiva, B. Fernandez Ruiz, M. Mehta, J. Barcelo, S.
Zhang, H. Yang, and L. Singh, “Simulation-Based Evaluation of Advanced Traveler Information Systems,”
Transp. Res. Rec., vol. 1225, no. February, pp. 90–98, 2014.
[8] G. N. Bifulco, G. E. Cantarella, and F. Simonelli, “Design of signal setting and advanced traveler
information systems,” in Journal of Intelligent Transportation Systems: Technology, Planning, and
Operations, 2014, vol. 18, no. 1, pp. 30–40.
[9] J. Zhang, T. Arentze, and H. Timmermans, “A multimodal transport network model for advanced
traveler information systems,” J. Ubiquitous Syst. Pervasive Networks, vol. 4, no. 1, pp. 21–27, 2012.
[10] A. Ben Ahmed, M. Meyer, Y. Okuyama, and A. Ben Abdallah, “Adaptive error- and traffic-aware
router architecture for 3D network-on-chip systems,” in Proceedings - 2014 IEEE 8th International
Symposium on Embedded Multicore/Manycore SoCs, MCSoC 2014, 2014, pp. 197–204.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
WIRELESS NETWORKS & SECURITY
[11] A. Higgins, C. Begley, J. Lalor, I. Coyne, K. Murphy, and N. Elliott, “Factors influencing advanced
practitioners’ ability to enact leadership: A case study within Irish healthcare,” J. Nurs. Manag., vol. 22,
no. 7, pp. 894–905, 2014.
[12] R. O. Topaloglu, “ICCAD-2014 CAD contest in design for manufacturability flow for advanced
semiconductor nodes and benchmark suite,” in IEEE/ACM International Conference on Computer-Aided
Design, Digest of Technical Papers, ICCAD, 2015, vol. 2015–January, no. January, pp. 367–368.
WIRELESS NETWORKS & SECURITY
[11] A. Higgins, C. Begley, J. Lalor, I. Coyne, K. Murphy, and N. Elliott, “Factors influencing advanced
practitioners’ ability to enact leadership: A case study within Irish healthcare,” J. Nurs. Manag., vol. 22,
no. 7, pp. 894–905, 2014.
[12] R. O. Topaloglu, “ICCAD-2014 CAD contest in design for manufacturability flow for advanced
semiconductor nodes and benchmark suite,” in IEEE/ACM International Conference on Computer-Aided
Design, Digest of Technical Papers, ICCAD, 2015, vol. 2015–January, no. January, pp. 367–368.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



