MSC Digital Forensics and Cybercrime: Kodi Vulnerability Project
VerifiedAdded on 2019/09/20
|9
|2011
|226
Project
AI Summary
This project focuses on identifying and addressing vulnerabilities within Kodi, an open-source media center, when deployed on an embedded Linux system. The project aims to analyze potential security weaknesses, particularly those arising from the use of unsecure HTTP connections for add-on updates and the presence of various repositories. The research encompasses both qualitative and quantitative approaches, including a literature review of embedded Linux and Kodi, along with an analysis of potential vulnerabilities and corresponding exploits. The data collection strategy involves both static and live data collection methods, employing existing tools and potentially developing a custom artifact in Python. The project's deliverables include a project plan, literature review, vulnerability analysis, documentation of exploits, and a proof of concept, along with an ethical statement. It will prioritize high-risk issues and zero-day exploits. The project uses Python to develop a script or program to determine vulnerabilities and apply solutions. The project explores vulnerabilities like buffer overflows, memory mismanagement, and denial-of-service attacks. The goal is to enhance the security of Kodi installations and embedded Linux systems by providing a comprehensive analysis and practical solutions.

Table of Contents
Introduction........................................................................................................................ 3
Aim......................................................................................................................................... 3
Objectives............................................................................................................................ 3
Ethical Statement.............................................................................................................. 3
Intellectual Challenge...................................................................................................... 3
Deliverables........................................................................................................................ 4
Resources............................................................................................................................. 4
Research Approach........................................................................................................... 5
Qualitative Research.................................................................................................................. 5
Quantitative Research...............................................................................................................5
Data Collection Approach............................................................................................... 6
Static Data Collection................................................................................................................. 6
Information Gathering data.................................................................................................................6
Vulnerability Analysis data..................................................................................................................6
Live Data Collection................................................................................................................... 6
Historical data.............................................................................................................................. 7
Limitations and Potential Problems....................................................................................8
Prioritization.............................................................................................................................................. 8
Programming............................................................................................................................................. 8
Kodi Platform.............................................................................................................................................8
Literature Review............................................................................................................. 8
Conclusion........................................................................................................................... 8
Appendix A.......................................................................................................................... 9
Disclaimer Form.............................................................................................................................................9
Introduction........................................................................................................................ 3
Aim......................................................................................................................................... 3
Objectives............................................................................................................................ 3
Ethical Statement.............................................................................................................. 3
Intellectual Challenge...................................................................................................... 3
Deliverables........................................................................................................................ 4
Resources............................................................................................................................. 4
Research Approach........................................................................................................... 5
Qualitative Research.................................................................................................................. 5
Quantitative Research...............................................................................................................5
Data Collection Approach............................................................................................... 6
Static Data Collection................................................................................................................. 6
Information Gathering data.................................................................................................................6
Vulnerability Analysis data..................................................................................................................6
Live Data Collection................................................................................................................... 6
Historical data.............................................................................................................................. 7
Limitations and Potential Problems....................................................................................8
Prioritization.............................................................................................................................................. 8
Programming............................................................................................................................................. 8
Kodi Platform.............................................................................................................................................8
Literature Review............................................................................................................. 8
Conclusion........................................................................................................................... 8
Appendix A.......................................................................................................................... 9
Disclaimer Form.............................................................................................................................................9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
In this project vulnerabilities of an open source media center based on
embedded Linux system will be checked and solution will be installed to prevent
exploiting those vulnerabilities. The open source media center in this case will be
Kodi.
Kodi provide set of add-ons that allow users to download services like YouTube,
drop box, Internet explorer etc. any updates for these services are downloaded
via unsecure http connection, which leaves it open for attacks like man in the
middle. There are also different repositories available to download contents
from.
Although Linux has less reported vulnerabilities than windows however one of
the reason is its low desktop usage as compared to Windows environment. Linux
has reported vulnerabilities in areas like buffer overflow, memory
mismanagement that can result in memory corruption, denial of service.
Aim
The aim of this project is to identify vulnerabilities in embedded Linux system
and Kodi. Once identified a solution will be installed to make it secure. This
solution will include a script or program to first run penetration testing
programs to identify vulnerabilities and then install solution.
Objectives
Discuss embedded Linux Operating System and Kodi.
Identify possible vulnerabilities in Linux and Kodi.
Examine exploits related to vulnerabilities.
Determine possible solutions for the exploits/vulnerabilities.
Write a script or program to determine vulnerabilities and apply solutions.
Carry out evaluation of the artifact.
Carry out evaluation of the project as a whole.
Ethical Statement
Please see Appendix A for Ethical Statement.
Intellectual Challenge
Embedded Linux is now days used in a variety of devices and to many people it is
near to impossible that these devices can be exploited by taking advantage of
weakness in operating system. There are areas where it can be exploited if not
look after easily. Examples are outdated software, not having up to date patch.
In this project vulnerabilities of an open source media center based on
embedded Linux system will be checked and solution will be installed to prevent
exploiting those vulnerabilities. The open source media center in this case will be
Kodi.
Kodi provide set of add-ons that allow users to download services like YouTube,
drop box, Internet explorer etc. any updates for these services are downloaded
via unsecure http connection, which leaves it open for attacks like man in the
middle. There are also different repositories available to download contents
from.
Although Linux has less reported vulnerabilities than windows however one of
the reason is its low desktop usage as compared to Windows environment. Linux
has reported vulnerabilities in areas like buffer overflow, memory
mismanagement that can result in memory corruption, denial of service.
Aim
The aim of this project is to identify vulnerabilities in embedded Linux system
and Kodi. Once identified a solution will be installed to make it secure. This
solution will include a script or program to first run penetration testing
programs to identify vulnerabilities and then install solution.
Objectives
Discuss embedded Linux Operating System and Kodi.
Identify possible vulnerabilities in Linux and Kodi.
Examine exploits related to vulnerabilities.
Determine possible solutions for the exploits/vulnerabilities.
Write a script or program to determine vulnerabilities and apply solutions.
Carry out evaluation of the artifact.
Carry out evaluation of the project as a whole.
Ethical Statement
Please see Appendix A for Ethical Statement.
Intellectual Challenge
Embedded Linux is now days used in a variety of devices and to many people it is
near to impossible that these devices can be exploited by taking advantage of
weakness in operating system. There are areas where it can be exploited if not
look after easily. Examples are outdated software, not having up to date patch.

Sniffers can be used to access remote Linux operating system, buffer overflow
can be created which results in giving privileged access to attacker.
On top of Embedded Linux there are variety of program runs, ranges robotics to
open source media center like Kodi. Kodi allows third party developers to
created their own add-ons, which can be downloaded by end users, when
downloading these add-ons, or updating them it can give full access to the
system, which will make it open for exploitation. Also it use http to transfer files
or update and it’s not clear how secure it is. Most kodi devices have wireless
cards, which can also be exploited to gain access to local network resources.
This project will help in making sure how these can be made more secure.
Deliverables
Project Plan.
Literature review of Linux and Kodi.
Analysis of Vulnerabilities in Linux and Kodi.
Documentation of Exploits based on step 3.
Proof of concept
Test script for bugs/code errors.
Analysis of test results.
Resources
Hardware
USB Cables
Network cables
Kodi Box
Laptop
ADSL Router
Power cables
Software
Kali Linux Operating System
Kodi Media Center
Microsoft Office
Others
Library Resources
Project Supervisor
can be created which results in giving privileged access to attacker.
On top of Embedded Linux there are variety of program runs, ranges robotics to
open source media center like Kodi. Kodi allows third party developers to
created their own add-ons, which can be downloaded by end users, when
downloading these add-ons, or updating them it can give full access to the
system, which will make it open for exploitation. Also it use http to transfer files
or update and it’s not clear how secure it is. Most kodi devices have wireless
cards, which can also be exploited to gain access to local network resources.
This project will help in making sure how these can be made more secure.
Deliverables
Project Plan.
Literature review of Linux and Kodi.
Analysis of Vulnerabilities in Linux and Kodi.
Documentation of Exploits based on step 3.
Proof of concept
Test script for bugs/code errors.
Analysis of test results.
Resources
Hardware
USB Cables
Network cables
Kodi Box
Laptop
ADSL Router
Power cables
Software
Kali Linux Operating System
Kodi Media Center
Microsoft Office
Others
Library Resources
Project Supervisor
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research Approach
Both qualitative and quantitative approaches will be used in this project.
Qualitative Research
Profound analysis of Linux operating system will be carried out by reading
existing books, papers, journals, and recent research will do this. As Linux is
widely used in variety of devices in embedded form. Linux Kernel is open source
and has been modified by many developers either to update existing software or
tailor it to new requirements. There is a need to work more on bugs or errors in
Linux Kernel as every distribution can carry extra pieces of patches not required
for any other distribution.
Kodi is also an open source media center, which is used to access media sources
on local area network or from Internet. In depth analysis of Kodi will be carried
out on how it work, how the repository are accessed, where they are stored, how
secure is the connection between client and server. As Kodi itself doesn’t provide
any content and user have to download its own media or access any other
provided on the Internet. The access privileged will be explore in this research
and how it can be used to exploit data saved on kodi box and access to local area
network.
Exploration of vulnerabilities will be carried out on both embedded Linux and
Kodi. All these vulnerabilities will be linked to possible exploits and a list will be
generated to demonstrate it. There will be in depth description of vulnerabilities
and exploits.
An artifact will be generated on how to scan Linux operating system and Kodi,
generate results and apply solutions. It can be a program that will have both
scanning and implementation options or separate programs to first display
results and then apply appropriate actions.
Quantitative Research
Selection of existing tools will be made on how we perform vulnerabilities, will
be combined into the artifact created in Python. This new artifact will also look
into issues not covered by existing tools. This artifact will perform both static
and live tests.
Prioritization will be made on how big risk is linked to a specific issue and
solution will be applied as a priority.
The actual artifact itself will be monitor for any bugs or errors, and results will
be monitored to make sure it produces correct results.
Measure
Prioritize
Monitor
Track
Both qualitative and quantitative approaches will be used in this project.
Qualitative Research
Profound analysis of Linux operating system will be carried out by reading
existing books, papers, journals, and recent research will do this. As Linux is
widely used in variety of devices in embedded form. Linux Kernel is open source
and has been modified by many developers either to update existing software or
tailor it to new requirements. There is a need to work more on bugs or errors in
Linux Kernel as every distribution can carry extra pieces of patches not required
for any other distribution.
Kodi is also an open source media center, which is used to access media sources
on local area network or from Internet. In depth analysis of Kodi will be carried
out on how it work, how the repository are accessed, where they are stored, how
secure is the connection between client and server. As Kodi itself doesn’t provide
any content and user have to download its own media or access any other
provided on the Internet. The access privileged will be explore in this research
and how it can be used to exploit data saved on kodi box and access to local area
network.
Exploration of vulnerabilities will be carried out on both embedded Linux and
Kodi. All these vulnerabilities will be linked to possible exploits and a list will be
generated to demonstrate it. There will be in depth description of vulnerabilities
and exploits.
An artifact will be generated on how to scan Linux operating system and Kodi,
generate results and apply solutions. It can be a program that will have both
scanning and implementation options or separate programs to first display
results and then apply appropriate actions.
Quantitative Research
Selection of existing tools will be made on how we perform vulnerabilities, will
be combined into the artifact created in Python. This new artifact will also look
into issues not covered by existing tools. This artifact will perform both static
and live tests.
Prioritization will be made on how big risk is linked to a specific issue and
solution will be applied as a priority.
The actual artifact itself will be monitor for any bugs or errors, and results will
be monitored to make sure it produces correct results.
Measure
Prioritize
Monitor
Track
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Data Collection Approach
Data will be collected from Linux Kernel and Kodi Application. Number of
existing tools will be used to extract data, due to the nature of this subject data
extraction will be carried out in two states.
Static Data Collection
For the purpose of static data collection, tests will be carried out on data, which
doesn’t change when Linux and Kodi are running. These tests will be made using
existing free tools. Static data collection will be further divided into two stages as
below
Information Gathering data
At this stage information will be gathered which could potential be exploited,
some of the information gathered is below.
Applications running on different port than normal
Search for website hosted on particular website
Identify applications which uses insecure http get for information leakage.
Gather information on subdomains, email addresses, tcp port scan, whois lookup.
Firewall testing will be carried out.
Vulnerability Analysis data
This phase of data collection will be focused on getting data for any existing
vulnerabilities or ones, which haven’t been discovered or exploited yet. Some of
the vulnerabilities checked are below.
Checking potential of Buffer overflow
Insufficient memory
Memory leakage
Unused functions and variables
Zero day attack.
Denial of Service.
Live Data Collection
In live data collection tools will be used to show all the processes, which are
currently running. Although tests carried out at this stage might be similar to the
ones used for static data collection, however it will be more focused on currently
running processes.
Data will be collected from Linux Kernel and Kodi Application. Number of
existing tools will be used to extract data, due to the nature of this subject data
extraction will be carried out in two states.
Static Data Collection
For the purpose of static data collection, tests will be carried out on data, which
doesn’t change when Linux and Kodi are running. These tests will be made using
existing free tools. Static data collection will be further divided into two stages as
below
Information Gathering data
At this stage information will be gathered which could potential be exploited,
some of the information gathered is below.
Applications running on different port than normal
Search for website hosted on particular website
Identify applications which uses insecure http get for information leakage.
Gather information on subdomains, email addresses, tcp port scan, whois lookup.
Firewall testing will be carried out.
Vulnerability Analysis data
This phase of data collection will be focused on getting data for any existing
vulnerabilities or ones, which haven’t been discovered or exploited yet. Some of
the vulnerabilities checked are below.
Checking potential of Buffer overflow
Insufficient memory
Memory leakage
Unused functions and variables
Zero day attack.
Denial of Service.
Live Data Collection
In live data collection tools will be used to show all the processes, which are
currently running. Although tests carried out at this stage might be similar to the
ones used for static data collection, however it will be more focused on currently
running processes.
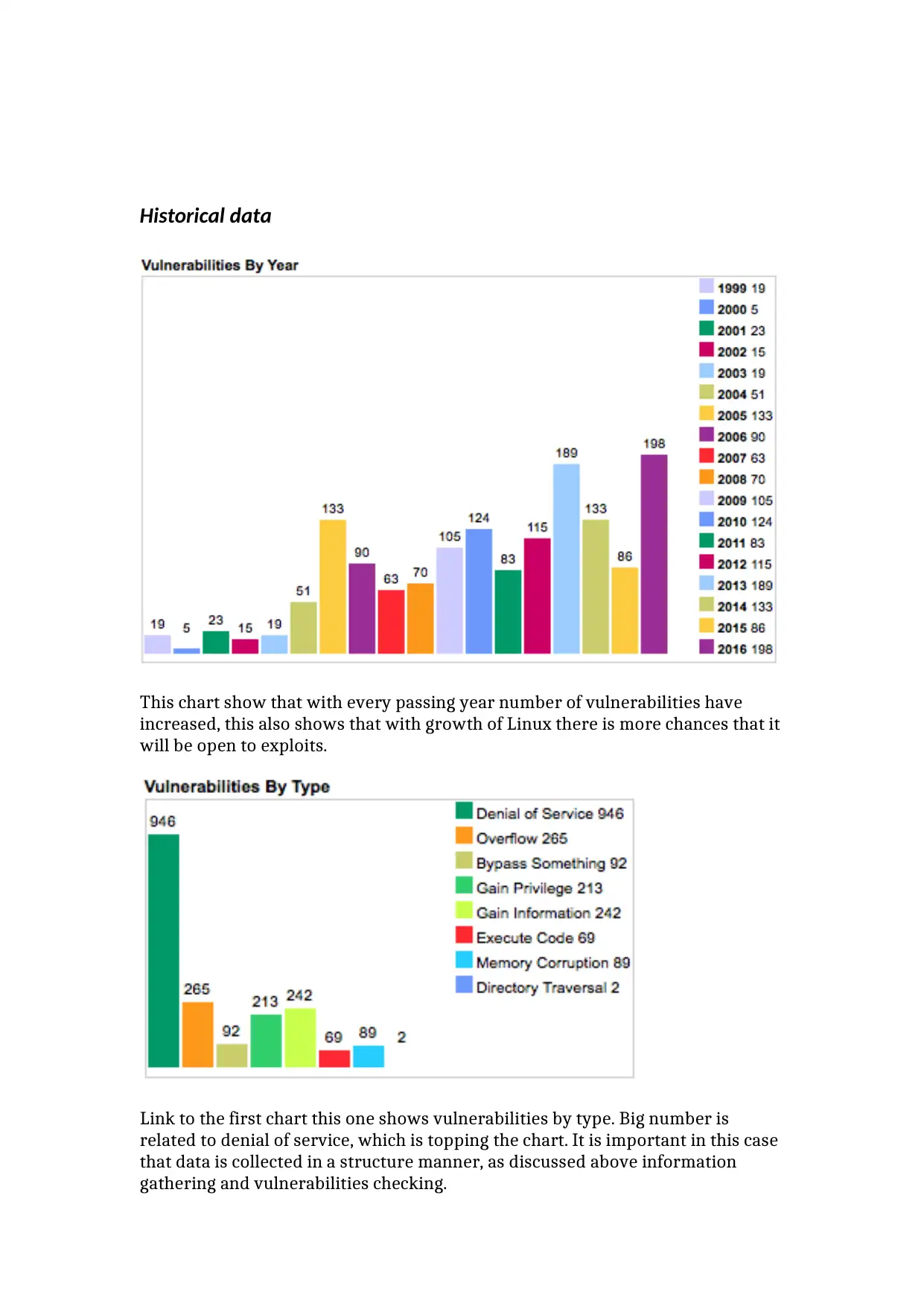
Historical data
This chart show that with every passing year number of vulnerabilities have
increased, this also shows that with growth of Linux there is more chances that it
will be open to exploits.
Link to the first chart this one shows vulnerabilities by type. Big number is
related to denial of service, which is topping the chart. It is important in this case
that data is collected in a structure manner, as discussed above information
gathering and vulnerabilities checking.
This chart show that with every passing year number of vulnerabilities have
increased, this also shows that with growth of Linux there is more chances that it
will be open to exploits.
Link to the first chart this one shows vulnerabilities by type. Big number is
related to denial of service, which is topping the chart. It is important in this case
that data is collected in a structure manner, as discussed above information
gathering and vulnerabilities checking.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Limitations and Potential Problems.
Prioritization
There are many vulnerabilities in Linux Kernel some are high security risks as
compare to others. Covering each vulnerability including zero day can be a huge
task. There is a possibility to narrow this list to high-risk issues and zero day
exploits.
Programming
Programming language chosen for this project is Python, which is rich in library
and easy to learn. Despite having experience in writing programs, lot of time is
required to put into learning this language to write a quality script or program.
Kodi Platform
Kodi is open source platform however the way it works, it is going to be difficult
to stop every possible exploit. One example is that it has so many repositories
and scanning each of them is going to be a difficult task. Add-ons can also be
added in this platform and with restricting their access to root may stop it from
being updated or even install.
Literature Review
Conclusion
Prioritization
There are many vulnerabilities in Linux Kernel some are high security risks as
compare to others. Covering each vulnerability including zero day can be a huge
task. There is a possibility to narrow this list to high-risk issues and zero day
exploits.
Programming
Programming language chosen for this project is Python, which is rich in library
and easy to learn. Despite having experience in writing programs, lot of time is
required to put into learning this language to write a quality script or program.
Kodi Platform
Kodi is open source platform however the way it works, it is going to be difficult
to stop every possible exploit. One example is that it has so many repositories
and scanning each of them is going to be a difficult task. Add-ons can also be
added in this platform and with restricting their access to root may stop it from
being updated or even install.
Literature Review
Conclusion
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Appendix A
Disclaimer Form
The following declaration should be made in cases where the researcher and the supervisor
(where applicable) conclude that it is not necessary to apply for ethical approval for a
specific research project.
PART A: TO BE COMPLETED BY RESEARCHER
Name of Researcher: Mian Saud Rehman
Student/Course Details (If Applicable)
Student ID Number: R028142E
Name of Supervisor(s)/Module Tutor: Rachel Cornes
PhD/MPhil project:
Taught Postgraduate
Project/Assignment: Award Title:
Module
Title:
MSC Digital Forensics and Cybercrime Analysis
Research Methods for NetworkingUndergraduate
Project/Assignment:
Project Title: Evaluate vulnerabilities in Kodi on Embedded Linux Operating system
Project Outline:
Give a brief description
of research procedure
(methods, tests etc.)
Expected Start Date: 1/1/2017 Expected End
Date:
01/04/2017
Declaration
I/We confirm that the University’s Ethical Review Policy has been consulted and that all
ethical issues and implications in relation to the above project have been considered. I/We
confirm that ethical approval need not be sought. I/We confirm that:
The research does not involve human or animal participants
The research does not present an indirect risk to non-participants (human or animal).
The research does not raise ethical issues due to the potential social or environmental
implications of the study.
The research does not re-use previously collected personal data which is sensitive in
nature, or enables the identification of individuals.
Signature of Researcher: Mian Saud Rehman Date: 04/12/2016
Disclaimer Form
The following declaration should be made in cases where the researcher and the supervisor
(where applicable) conclude that it is not necessary to apply for ethical approval for a
specific research project.
PART A: TO BE COMPLETED BY RESEARCHER
Name of Researcher: Mian Saud Rehman
Student/Course Details (If Applicable)
Student ID Number: R028142E
Name of Supervisor(s)/Module Tutor: Rachel Cornes
PhD/MPhil project:
Taught Postgraduate
Project/Assignment: Award Title:
Module
Title:
MSC Digital Forensics and Cybercrime Analysis
Research Methods for NetworkingUndergraduate
Project/Assignment:
Project Title: Evaluate vulnerabilities in Kodi on Embedded Linux Operating system
Project Outline:
Give a brief description
of research procedure
(methods, tests etc.)
Expected Start Date: 1/1/2017 Expected End
Date:
01/04/2017
Declaration
I/We confirm that the University’s Ethical Review Policy has been consulted and that all
ethical issues and implications in relation to the above project have been considered. I/We
confirm that ethical approval need not be sought. I/We confirm that:
The research does not involve human or animal participants
The research does not present an indirect risk to non-participants (human or animal).
The research does not raise ethical issues due to the potential social or environmental
implications of the study.
The research does not re-use previously collected personal data which is sensitive in
nature, or enables the identification of individuals.
Signature of Researcher: Mian Saud Rehman Date: 04/12/2016

Signature(s) of Project
Supervisor(s)
(If applicable)
Date:
NB: If the research departs from the protocol which provides the basis for this disclaimer then ethical
review may be required and the applicant and supervisor (where applicable) should consider whether
or not the disclaimer declaration remains appropriate. If it is no longer appropriate an application for
ethical review MUST be submitted.
Supervisor(s)
(If applicable)
Date:
NB: If the research departs from the protocol which provides the basis for this disclaimer then ethical
review may be required and the applicant and supervisor (where applicable) should consider whether
or not the disclaimer declaration remains appropriate. If it is no longer appropriate an application for
ethical review MUST be submitted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





