CKIT511: Security Engineering - Vulnerability Scanning with Nessus
VerifiedAdded on 2023/01/19
|12
|769
|44
Practical Assignment
AI Summary
This report details a vulnerability assessment performed on an AWS Ubuntu server, as part of a Security Engineering and Compliance course (CKIT511). The student utilizes Amazon EC2 instances and logs in using provided credentials. The assignment involves network reconnaissance using nmap to identify active hosts and scan for open ports. Different nmap commands are used for various types of scans, including TCP connect, SYN, and OS detection. The student then installs and configures Nessus on a server to perform vulnerability scans, providing screenshots of the results. The report covers the steps involved in setting up the environment, performing the scans, and interpreting the findings, demonstrating practical application of security tools and techniques. The report also includes a bibliography of relevant research papers.

Running head: SOFTWARE ENGINEERING
Software Engineering
Name of the Student
Name of the University
Author’s Note
Software Engineering
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
SOFTWARE ENGINEERING
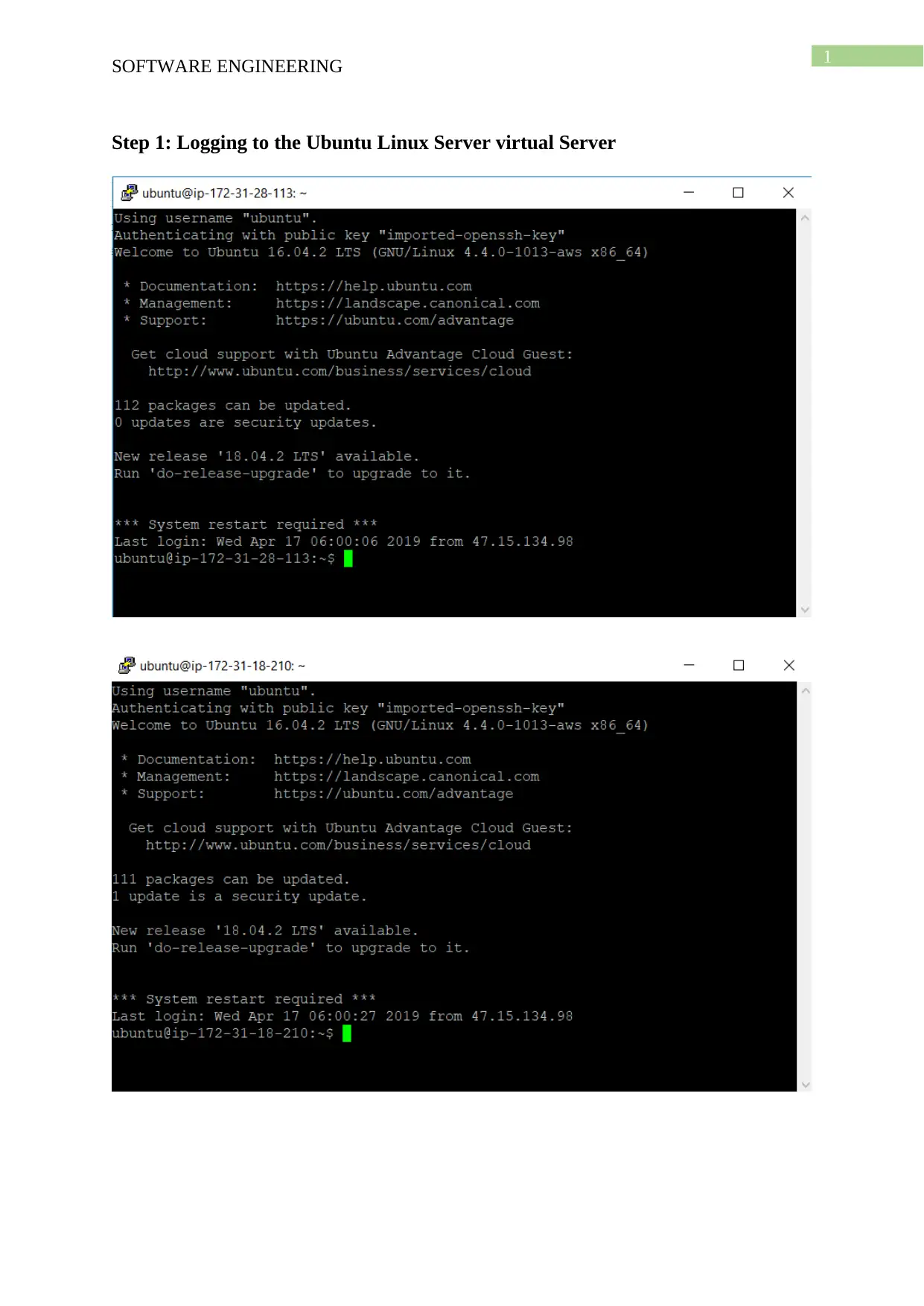
Step 1: Logging to the Ubuntu Linux Server virtual Server
SOFTWARE ENGINEERING
Step 1: Logging to the Ubuntu Linux Server virtual Server
2
SOFTWARE ENGINEERING
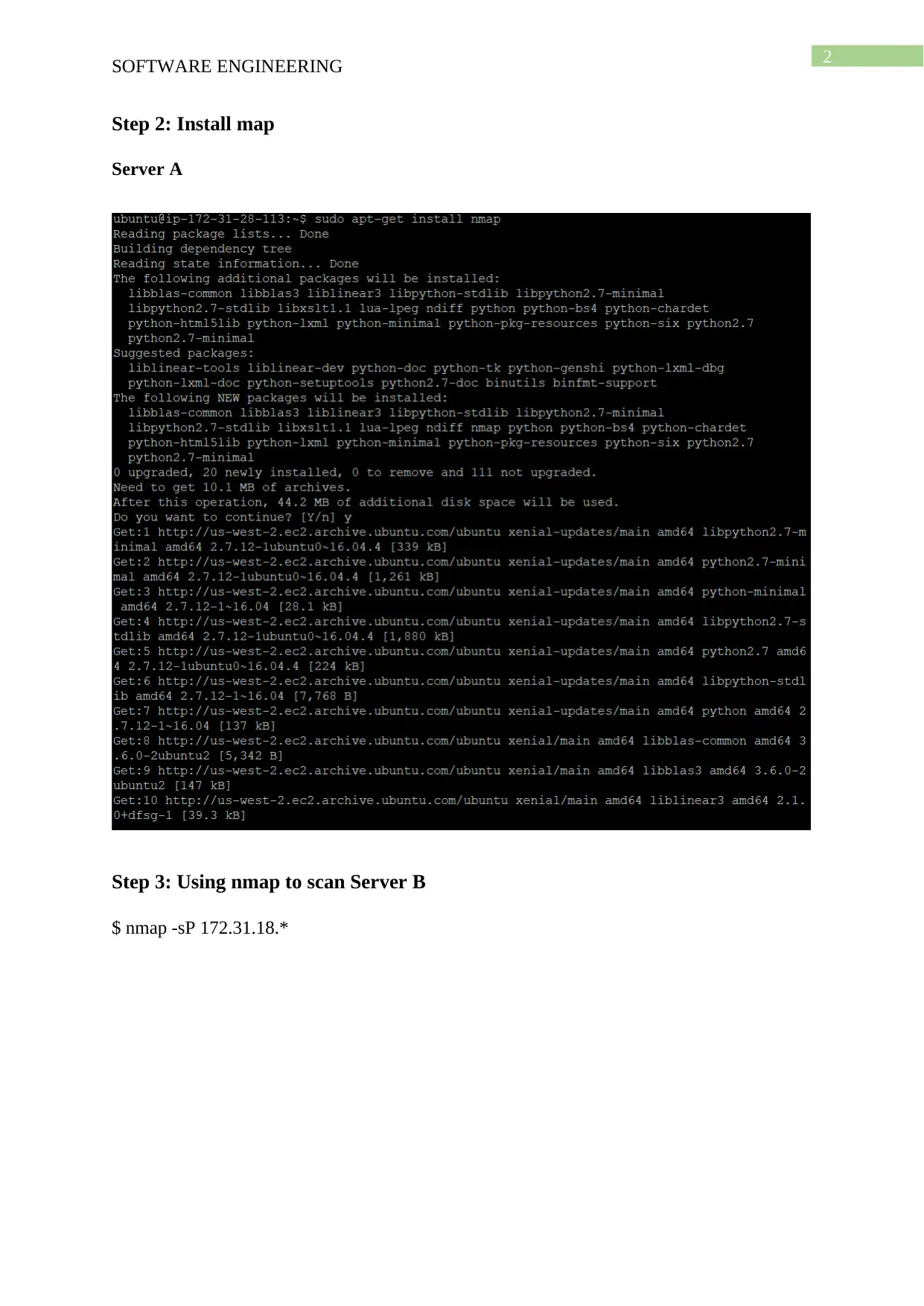
Step 2: Install map
Server A
Step 3: Using nmap to scan Server B
$ nmap -sP 172.31.18.*
SOFTWARE ENGINEERING
Step 2: Install map
Server A
Step 3: Using nmap to scan Server B
$ nmap -sP 172.31.18.*
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
SOFTWARE ENGINEERING
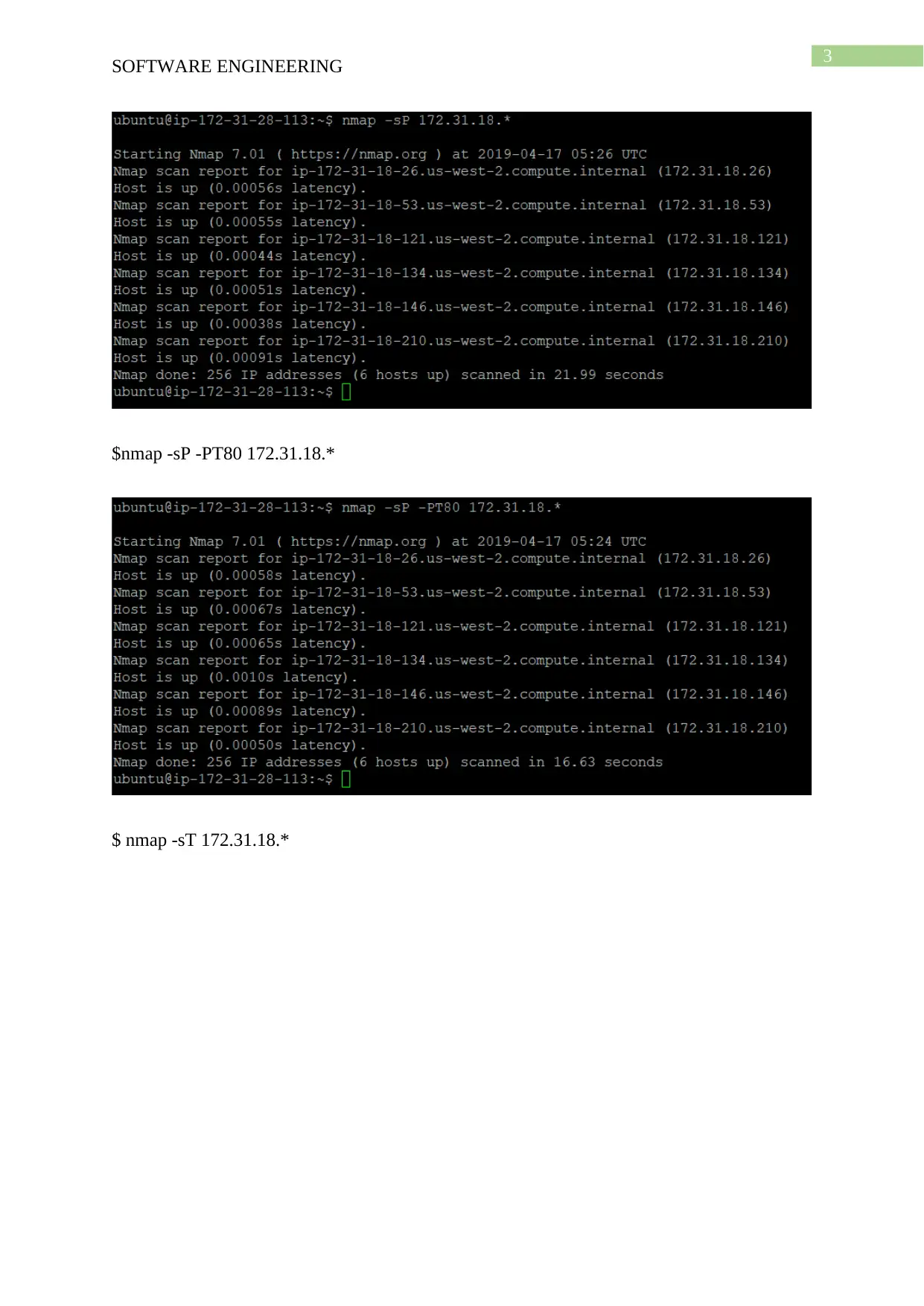
$nmap -sP -PT80 172.31.18.*
$ nmap -sT 172.31.18.*
SOFTWARE ENGINEERING
$nmap -sP -PT80 172.31.18.*
$ nmap -sT 172.31.18.*
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SOFTWARE ENGINEERING
$ sudo nmap -sS -O 172.31.18.210
SOFTWARE ENGINEERING
$ sudo nmap -sS -O 172.31.18.210

5
SOFTWARE ENGINEERING
Step 4: Installing Nessus on Server B
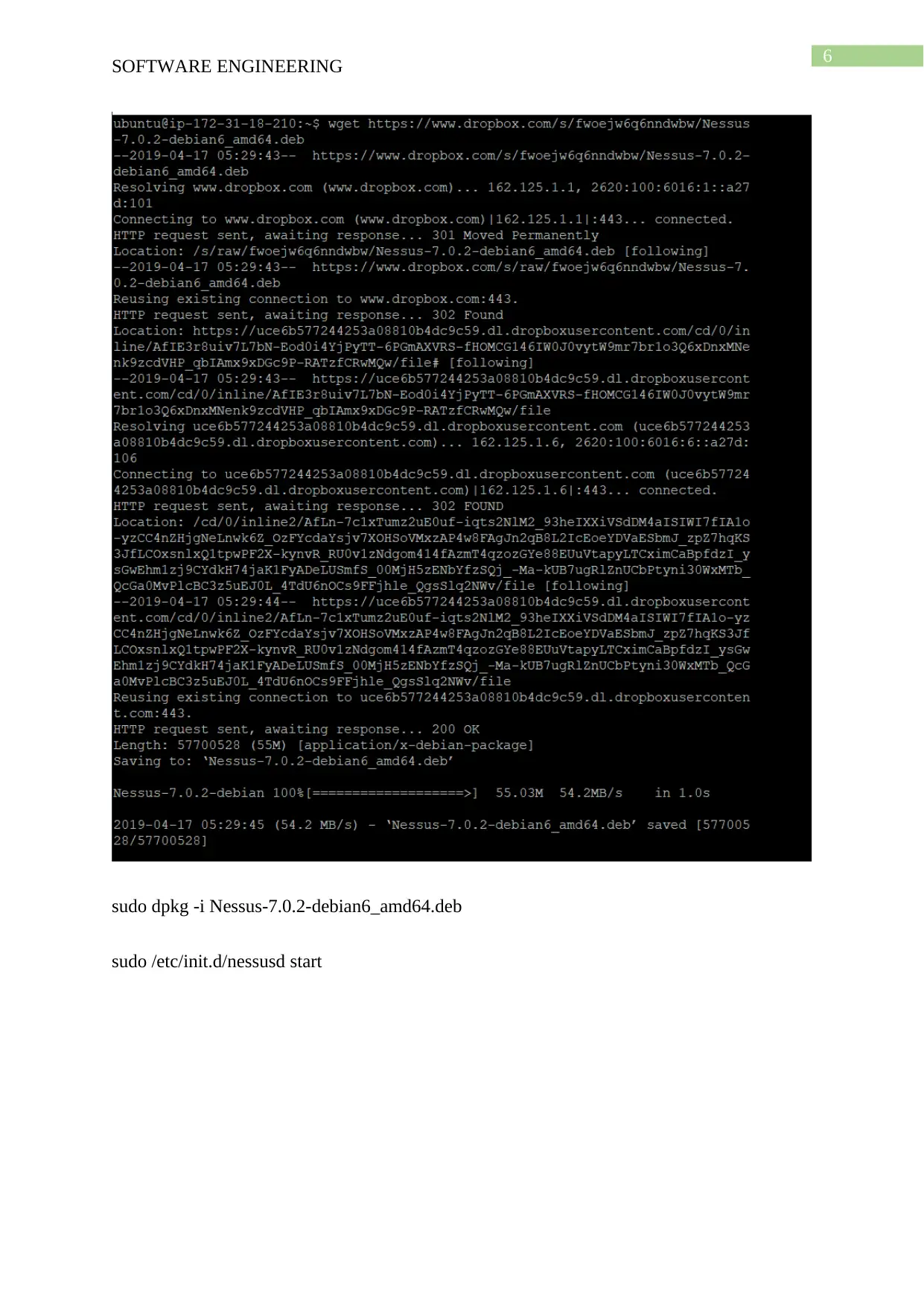
wget https://www.dropbox.com/s/fwoejw6q6nndwbw/Nessus-7.0.2-debian6_amd64.deb
SOFTWARE ENGINEERING
Step 4: Installing Nessus on Server B
wget https://www.dropbox.com/s/fwoejw6q6nndwbw/Nessus-7.0.2-debian6_amd64.deb
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
SOFTWARE ENGINEERING
sudo dpkg -i Nessus-7.0.2-debian6_amd64.deb
sudo /etc/init.d/nessusd start
SOFTWARE ENGINEERING
sudo dpkg -i Nessus-7.0.2-debian6_amd64.deb
sudo /etc/init.d/nessusd start
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
SOFTWARE ENGINEERING
$ sudo ufw allow 8834/tcp
SOFTWARE ENGINEERING
$ sudo ufw allow 8834/tcp
8
SOFTWARE ENGINEERING
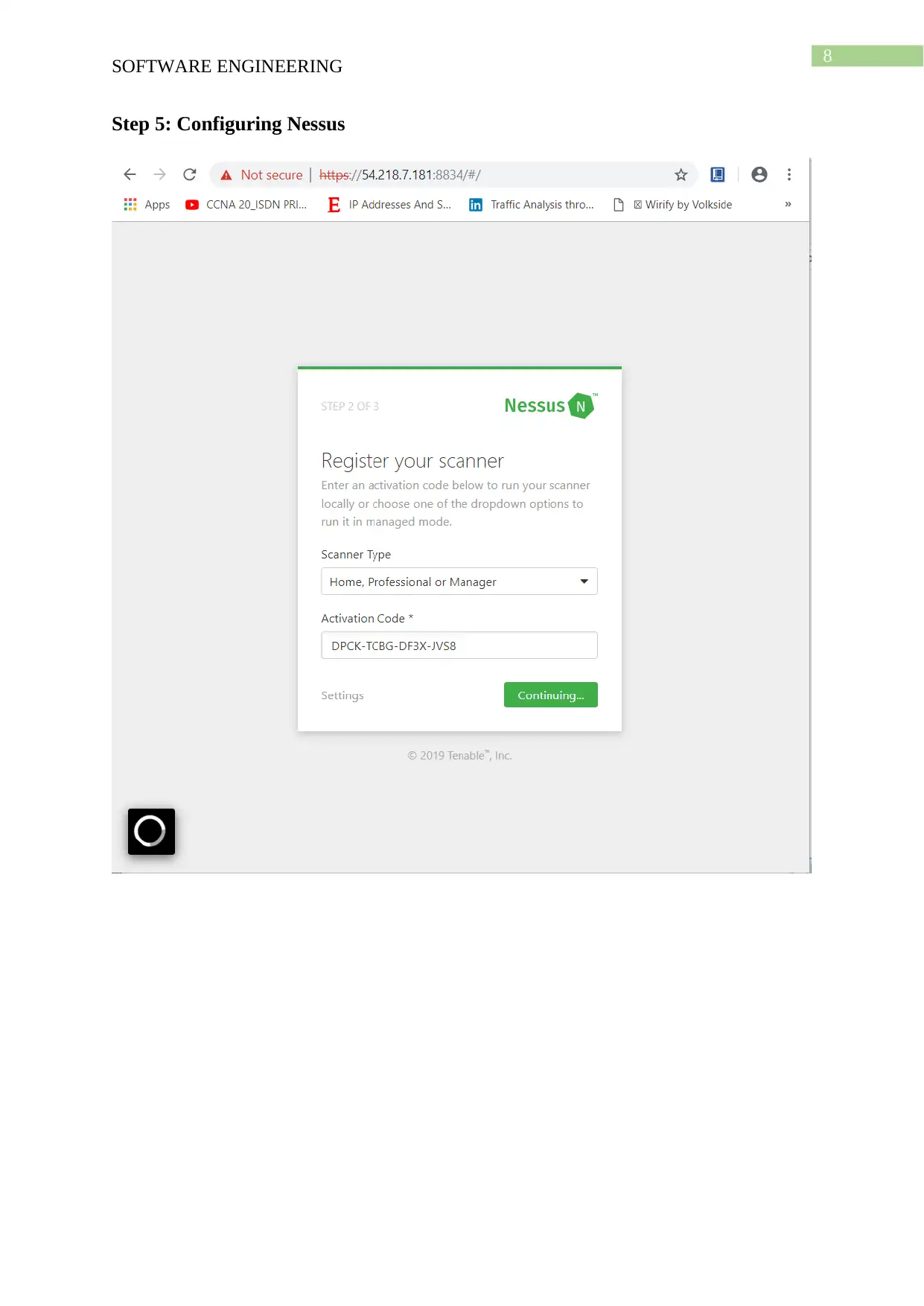
Step 5: Configuring Nessus
SOFTWARE ENGINEERING
Step 5: Configuring Nessus
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
SOFTWARE ENGINEERING
The main requirement of the assignment is to perform a vulnerability scan on the
network and identification of the steps essential for performing the scan. For performing the
vulnerability test each of the steps are needed to be followed that are given in the report. In
the first step the virtual instance of Amazon EC2 is needed to be logged in from putty with
the private key. For the server A ubuntu@34.209.250.155 is used as the IP address and for
the server B ubuntu@54.218.7.181 is used. Nmap is installed on server A for performing the
vulnerability testing on server B and a scan is performed with the Ip address assigned to the
server and finding the range of active hosts running on the network. The command nmap -sP
172.31.18.* is used for sending icmp echo and TCP ACK for the hosts found active in the
network. On getting response from the host it is marked as active and the wildcard character
is used for listing all the servers that are connected in the host network. The availability of the
system can also be checked without sending the ICMP request by sending TCP ping sweep
and sending ack to the servers connected in the targeted network. A response is send from the
servers that are UP with TCP RST. The process works using -PT flag for targeting a specific
port on the network and for this the following command is used:
Nmap -sP -PT80 172.31.18.*
SOFTWARE ENGINEERING
The main requirement of the assignment is to perform a vulnerability scan on the
network and identification of the steps essential for performing the scan. For performing the
vulnerability test each of the steps are needed to be followed that are given in the report. In
the first step the virtual instance of Amazon EC2 is needed to be logged in from putty with
the private key. For the server A ubuntu@34.209.250.155 is used as the IP address and for
the server B ubuntu@54.218.7.181 is used. Nmap is installed on server A for performing the
vulnerability testing on server B and a scan is performed with the Ip address assigned to the
server and finding the range of active hosts running on the network. The command nmap -sP
172.31.18.* is used for sending icmp echo and TCP ACK for the hosts found active in the
network. On getting response from the host it is marked as active and the wildcard character
is used for listing all the servers that are connected in the host network. The availability of the
system can also be checked without sending the ICMP request by sending TCP ping sweep
and sending ack to the servers connected in the targeted network. A response is send from the
servers that are UP with TCP RST. The process works using -PT flag for targeting a specific
port on the network and for this the following command is used:
Nmap -sP -PT80 172.31.18.*
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
SOFTWARE ENGINEERING
There are different types of scans that can be performed on the host network using the
nmap such as TCP connect, Stealth FIN, TCP SYN, NULL and Xmas Tree. The flags -sT, -
sF, -sS, -sN and -sX and -sU are used for performing the scans and this commands are run in
server A for analysing the vulnerability of server B. The OS running on the targeted server
can also be identified by performing the scan but it can take long time for completion of the
scan for the host and thus a specific target is selected for performing the scan. Thus the
command sudo nmap -sS -O 172.31.18.210 is used for performing the scan on server B.
In the next step Nessus is installed in server B for scanning the vulnerabilities in the
server. Since in the previous assignment snort and wireshark was installed in server A we
does not have the need to uninstall them for proceeding with scanning vulnerability with
Nessus. The package of Nessus is needed to be downloaded from Dropbox and using the
command wget https://www.dropbox.com/fwoejw6q6nndwbw/nessus-1.0.2-
debian6_amd64.deb. The package is downloaded and installed and the service is started and
allowed on 8834 tcp port. The Nessus is configured by registering on the Nessus website and
the trial version is started and for connecting with the server B the Ip address of the server is
inputted followed by the port number 8834 for connecting with the server. The screenshot the
screen is attached with the report for the demonstration of the vulnerability of the Linux
server.
SOFTWARE ENGINEERING
There are different types of scans that can be performed on the host network using the
nmap such as TCP connect, Stealth FIN, TCP SYN, NULL and Xmas Tree. The flags -sT, -
sF, -sS, -sN and -sX and -sU are used for performing the scans and this commands are run in
server A for analysing the vulnerability of server B. The OS running on the targeted server
can also be identified by performing the scan but it can take long time for completion of the
scan for the host and thus a specific target is selected for performing the scan. Thus the
command sudo nmap -sS -O 172.31.18.210 is used for performing the scan on server B.
In the next step Nessus is installed in server B for scanning the vulnerabilities in the
server. Since in the previous assignment snort and wireshark was installed in server A we
does not have the need to uninstall them for proceeding with scanning vulnerability with
Nessus. The package of Nessus is needed to be downloaded from Dropbox and using the
command wget https://www.dropbox.com/fwoejw6q6nndwbw/nessus-1.0.2-
debian6_amd64.deb. The package is downloaded and installed and the service is started and
allowed on 8834 tcp port. The Nessus is configured by registering on the Nessus website and
the trial version is started and for connecting with the server B the Ip address of the server is
inputted followed by the port number 8834 for connecting with the server. The screenshot the
screen is attached with the report for the demonstration of the vulnerability of the Linux
server.

11
SOFTWARE ENGINEERING
Bibliography
Rohrmann, R., Patton, M.W. and Chen, H., 2016, September. Anonymous port scanning:
Performing network reconnaissance through Tor. In 2016 IEEE Conference on Intelligence
and Security Informatics (ISI) (pp. 217-217). IEEE.
Wang, Y. and Yang, J., 2017, March. Ethical hacking and network defense: Choose your best
network vulnerability scanning tool. In 2017 31st International Conference on Advanced
Information Networking and Applications Workshops (WAINA) (pp. 110-113). IEEE.
SOFTWARE ENGINEERING
Bibliography
Rohrmann, R., Patton, M.W. and Chen, H., 2016, September. Anonymous port scanning:
Performing network reconnaissance through Tor. In 2016 IEEE Conference on Intelligence
and Security Informatics (ISI) (pp. 217-217). IEEE.
Wang, Y. and Yang, J., 2017, March. Ethical hacking and network defense: Choose your best
network vulnerability scanning tool. In 2017 31st International Conference on Advanced
Information Networking and Applications Workshops (WAINA) (pp. 110-113). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




