Vulnerability Assessment: Managing Computing Project for Data Security
VerifiedAdded on 2024/07/03
|26
|4689
|338
Report
AI Summary
This report provides a detailed analysis of managing a computing project with a focus on vulnerability assessment within Barclays Bank. It covers project aims, objectives, a project management plan, work breakdown structure, Gantt chart, small-scale research using qualitative and quantitative methods, data analysis, and a reflection on the project's value. The report identifies security issues faced by Barclays due to vulnerabilities in their computing systems, impacting data confidentiality and integrity. It includes recommendations for mitigating these vulnerabilities and improving data security, along with a project logbook and performance review template to ensure effective project management and achievement of stated objectives.

MANAGING A SUCCESSFUL
COMPUTING PROJECT
COMPUTING PROJECT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
P1 Devise project aims and objectives for a chosen scenario......................................................2
P2 Produce a project management plan....................................................................................... 4
P3 Produce a work breakdown structure and a Gantt chart to provide timeframes and stages for
completion...................................................................................................................................6
M1 Produce a comprehensive project management plan............................................................8
Task 2...............................................................................................................................................9
P4 Carry out small-scale research by applying qualitative and quantitative research methods. .9
M2 Evaluate the accuracy and reliability of different research methods applied......................11
Task 3.............................................................................................................................................12
P5 Analyse research and data using appropriate tools and techniques......................................12
P6 Communicate appropriate recommendations as a result of research and data analysis to
draw valid and meaningful conclusions....................................................................................15
M3 Evaluate the selection of appropriate tools and techniques for accuracy and authenticity. 16
Task 4.............................................................................................................................................17
P7 Reflect on the value of undertaking the research to meet stated objectives and own learning
and performance........................................................................................................................17
M4 Evaluate the value of the project management process.......................................................18
Conclusion..................................................................................................................................... 19
References......................................................................................................................................20
Appendix........................................................................................................................................21
Project logbook.......................................................................................................................... 21
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
P1 Devise project aims and objectives for a chosen scenario......................................................2
P2 Produce a project management plan....................................................................................... 4
P3 Produce a work breakdown structure and a Gantt chart to provide timeframes and stages for
completion...................................................................................................................................6
M1 Produce a comprehensive project management plan............................................................8
Task 2...............................................................................................................................................9
P4 Carry out small-scale research by applying qualitative and quantitative research methods. .9
M2 Evaluate the accuracy and reliability of different research methods applied......................11
Task 3.............................................................................................................................................12
P5 Analyse research and data using appropriate tools and techniques......................................12
P6 Communicate appropriate recommendations as a result of research and data analysis to
draw valid and meaningful conclusions....................................................................................15
M3 Evaluate the selection of appropriate tools and techniques for accuracy and authenticity. 16
Task 4.............................................................................................................................................17
P7 Reflect on the value of undertaking the research to meet stated objectives and own learning
and performance........................................................................................................................17
M4 Evaluate the value of the project management process.......................................................18
Conclusion..................................................................................................................................... 19
References......................................................................................................................................20
Appendix........................................................................................................................................21
Project logbook.......................................................................................................................... 21

LIST OF TABLES
Table 1: Gantt chart.........................................................................................................................7
Table 2: Milestone plan...................................................................................................................8
Table 3: Project schedule.................................................................................................................8
Table 4: Performance review template.......................................................................................... 18
Table 5: Project logbook................................................................................................................21
Table 1: Gantt chart.........................................................................................................................7
Table 2: Milestone plan...................................................................................................................8
Table 3: Project schedule.................................................................................................................8
Table 4: Performance review template.......................................................................................... 18
Table 5: Project logbook................................................................................................................21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: Work breakdown structure............................................................................................... 6
Figure 1: Work breakdown structure............................................................................................... 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Security of the customers and employees information and detail is one of the biggest
responsibilities of all the organization but sometimes due to the vulnerability impact they may
face security issues which reduce their data confidentiality and integrity. The below report and
research project will cover the security issues occurring in the Barclays Bank which is based in
the UK and provide banking services to their customers. The report will cover the project plan,
logbook, work breakdown structure, Gantt chart, small-scale research, data analysis, reflection
part and performance review for concluding the project. The report will effectively provide the
findings about impact of vulnerabilities on the computing systems of Barclay’s organization due
to which they face security issues.
1
Security of the customers and employees information and detail is one of the biggest
responsibilities of all the organization but sometimes due to the vulnerability impact they may
face security issues which reduce their data confidentiality and integrity. The below report and
research project will cover the security issues occurring in the Barclays Bank which is based in
the UK and provide banking services to their customers. The report will cover the project plan,
logbook, work breakdown structure, Gantt chart, small-scale research, data analysis, reflection
part and performance review for concluding the project. The report will effectively provide the
findings about impact of vulnerabilities on the computing systems of Barclay’s organization due
to which they face security issues.
1

Task 1
P1 Devise project aims and objectives for a chosen scenario
Background of organization
Barclays is one of the largest banking sector organizations which provide banking facilities and
other financial help to their customers. Barclay’s organization is based in the UK and has large
number of customer base in the market which shows their brand image at huge scale. They need
to manage the confidential details and information of their customers and for this they need to
protect their information system from vulnerabilities. It is also essential for them to manage the
reliability, security and confidentiality of their customers details so that they can maintain their
customers trust and achieve data availability (Maina, 2017).
Project description
This project mainly focuses on vulnerability assessment within the Barclays organization that put
impact on the data accuracy, reliability and security with the data availability and confidentiality.
In the organization some computing resources can be vulnerable towards the attacks, damage
and unauthenticated access
Problem statement
Currently organization is facing security issues in their business due to which loss in the
customer information is faced by them. They are facing attacks and unauthenticated access
issues due to which security and confidentiality of the information is getting disturbed. . It is
important for them to analyze the vulnerabilities and its impact so that changes can be
implemented to achieve the data security at high level (Abomhara and Køien, 2015).
Project aim
The project goal or aim is only to analyze the vulnerabilities upon the computing resources that
are currently using by Barclays organization. This project goal helps them to improve their data
accuracy, reliability, confidentiality and security. The goal of this project is just to improve the
organization security by considering the business scope and capabilities.
2
P1 Devise project aims and objectives for a chosen scenario
Background of organization
Barclays is one of the largest banking sector organizations which provide banking facilities and
other financial help to their customers. Barclay’s organization is based in the UK and has large
number of customer base in the market which shows their brand image at huge scale. They need
to manage the confidential details and information of their customers and for this they need to
protect their information system from vulnerabilities. It is also essential for them to manage the
reliability, security and confidentiality of their customers details so that they can maintain their
customers trust and achieve data availability (Maina, 2017).
Project description
This project mainly focuses on vulnerability assessment within the Barclays organization that put
impact on the data accuracy, reliability and security with the data availability and confidentiality.
In the organization some computing resources can be vulnerable towards the attacks, damage
and unauthenticated access
Problem statement
Currently organization is facing security issues in their business due to which loss in the
customer information is faced by them. They are facing attacks and unauthenticated access
issues due to which security and confidentiality of the information is getting disturbed. . It is
important for them to analyze the vulnerabilities and its impact so that changes can be
implemented to achieve the data security at high level (Abomhara and Køien, 2015).
Project aim
The project goal or aim is only to analyze the vulnerabilities upon the computing resources that
are currently using by Barclays organization. This project goal helps them to improve their data
accuracy, reliability, confidentiality and security. The goal of this project is just to improve the
organization security by considering the business scope and capabilities.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project objectives
Is to understand the importance of availability, integrity and confidentiality of data in the
context of the Barclays organization.
Is to evaluate the vulnerabilities impact and sources which put impact on the security and
management of the data.
Is to justify the implementation of some recommendation just to reduce the impact of
vulnerabilities.
3
Is to understand the importance of availability, integrity and confidentiality of data in the
context of the Barclays organization.
Is to evaluate the vulnerabilities impact and sources which put impact on the security and
management of the data.
Is to justify the implementation of some recommendation just to reduce the impact of
vulnerabilities.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P2 Produce a project management plan
Barclays bank can attain the security desire with the help of the project management plan. The
project planning is one of the process for initiating the concept, resources planning, framework
design and approach implementation. They need to focus on quality management and
monitoring. Following is the project management plan for Barclays bank:
Cost: Every organization need to make their budget before starting project or completing
project. It is identified that this project requires $20,000 of budget to start and finish the project.
In the budget major areas are covered like- technical hardware or software, resources, designing
of security framework and quality assurance with the various approaches. They need to reserve
some additional amount also for risk management such as- $2,000.
Project scope: This project manages the reliable and accurate information in effective manner.
With this project, the Barclays bank also achieves data confidentiality and security that improve
decision making process and operational activities (Puthal et al, 2015).
Duration or time: to start and finish this project at least 2 months are required as the project
time. It is essential for organization to manage their resources availability and delays in last two
weeks so that project must be completed on time and with effectiveness. The management of
time is quite constraint with the policies and business operation role management.
Project quality: TQM (Total Quality Management) is the approach which can be used by
organization to manage the project quality. This will help to consider the time, efforts and cost
and organization need to ensure out the outcomes to prevent the vulnerable activities. The
organization need to monitor and measure the project quality for achieving project baseline.
Communication: Personal interaction and mails are some channels which can be used by
organization to communicate the project details with other members and stakeholders. The can
use services of mail to report about the routine progress with the team members. This will help
them avoid the conflicts and they can resolve issues and also monitor the project progress
together (Hussain et al, 2017).
4
Barclays bank can attain the security desire with the help of the project management plan. The
project planning is one of the process for initiating the concept, resources planning, framework
design and approach implementation. They need to focus on quality management and
monitoring. Following is the project management plan for Barclays bank:
Cost: Every organization need to make their budget before starting project or completing
project. It is identified that this project requires $20,000 of budget to start and finish the project.
In the budget major areas are covered like- technical hardware or software, resources, designing
of security framework and quality assurance with the various approaches. They need to reserve
some additional amount also for risk management such as- $2,000.
Project scope: This project manages the reliable and accurate information in effective manner.
With this project, the Barclays bank also achieves data confidentiality and security that improve
decision making process and operational activities (Puthal et al, 2015).
Duration or time: to start and finish this project at least 2 months are required as the project
time. It is essential for organization to manage their resources availability and delays in last two
weeks so that project must be completed on time and with effectiveness. The management of
time is quite constraint with the policies and business operation role management.
Project quality: TQM (Total Quality Management) is the approach which can be used by
organization to manage the project quality. This will help to consider the time, efforts and cost
and organization need to ensure out the outcomes to prevent the vulnerable activities. The
organization need to monitor and measure the project quality for achieving project baseline.
Communication: Personal interaction and mails are some channels which can be used by
organization to communicate the project details with other members and stakeholders. The can
use services of mail to report about the routine progress with the team members. This will help
them avoid the conflicts and they can resolve issues and also monitor the project progress
together (Hussain et al, 2017).
4

Project risk: Time and cost management is one of the risks which are associated with this
project which is required to be overcome and avoid by the Barclays Bank and their team. The
resources unavailability and delay at the work to avoid risk and to achieve quality outcomes.
This is required to secure data, resources use and risk which is effective for this project.
Project resources: Barclays Bank has the technical department that can conduct system audit
and security management. The organization needs resources to plan the resources and quality
assurance. They need at least five employees who can implement this project and between them
work need to be equally distributed for achieving goal (Islam et al, 2016).
5
project which is required to be overcome and avoid by the Barclays Bank and their team. The
resources unavailability and delay at the work to avoid risk and to achieve quality outcomes.
This is required to secure data, resources use and risk which is effective for this project.
Project resources: Barclays Bank has the technical department that can conduct system audit
and security management. The organization needs resources to plan the resources and quality
assurance. They need at least five employees who can implement this project and between them
work need to be equally distributed for achieving goal (Islam et al, 2016).
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P3 Produce a work breakdown structure and a Gantt chart to provide timeframes and stages for
completion
Work breakdown structure is required to plan manageable modules of project goals which they
need to be communicated with team members with the high quality of performance. Following is
the WBS for Barclays Bank project:
Figure 1: Work breakdown structure
Gantt chart is required to set the project activities and then implement as per the time required.
This is effective to analyze the progress of the project as per the defined duration. Following is
the Gantt chart with activities and time:
6
Computing project
Planning
Hand on
machines
User and
system
analysis
Document
the strategy
Identify
skills
Requirement
specification
Meeting
s
Focus on
issues
Ouline
solutions
Risk
identification
Pre-design
Communicati
on for project
requirement
Finalization
of solutions
Contract and
agreement
Revise cost
and time
Designing
Logical
design
Physical
resources
Protyping
and risk
managment
Implement
ation
Configuratio
n of device
and software
additional
installation
Docume
ntation
Testing
Configurat
ion testing
Physical
installation
Quality
analysis
Post-
implementation
Maintenan
ce guide
Recomme
ndations
Training and
development
Resource
handover
Project
closure
completion
Work breakdown structure is required to plan manageable modules of project goals which they
need to be communicated with team members with the high quality of performance. Following is
the WBS for Barclays Bank project:
Figure 1: Work breakdown structure
Gantt chart is required to set the project activities and then implement as per the time required.
This is effective to analyze the progress of the project as per the defined duration. Following is
the Gantt chart with activities and time:
6
Computing project
Planning
Hand on
machines
User and
system
analysis
Document
the strategy
Identify
skills
Requirement
specification
Meeting
s
Focus on
issues
Ouline
solutions
Risk
identification
Pre-design
Communicati
on for project
requirement
Finalization
of solutions
Contract and
agreement
Revise cost
and time
Designing
Logical
design
Physical
resources
Protyping
and risk
managment
Implement
ation
Configuratio
n of device
and software
additional
installation
Docume
ntation
Testing
Configurat
ion testing
Physical
installation
Quality
analysis
Post-
implementation
Maintenan
ce guide
Recomme
ndations
Training and
development
Resource
handover
Project
closure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
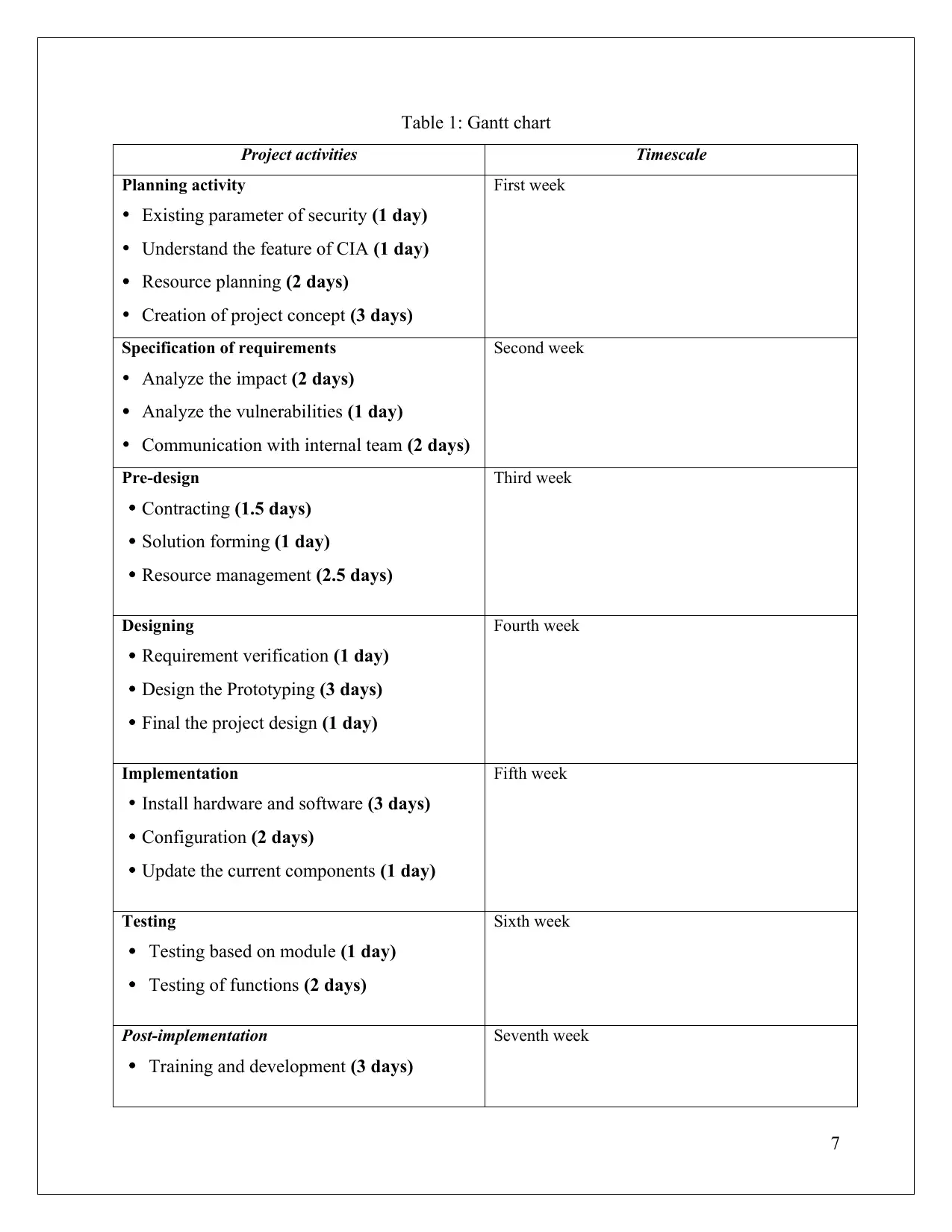
Table 1: Gantt chart
Project activities Timescale
Planning activity
Existing parameter of security (1 day)
Understand the feature of CIA (1 day)
Resource planning (2 days)
Creation of project concept (3 days)
First week
Specification of requirements
Analyze the impact (2 days)
Analyze the vulnerabilities (1 day)
Communication with internal team (2 days)
Second week
Pre-design
Contracting (1.5 days)
Solution forming (1 day)
Resource management (2.5 days)
Third week
Designing
Requirement verification (1 day)
Design the Prototyping (3 days)
Final the project design (1 day)
Fourth week
Implementation
Install hardware and software (3 days)
Configuration (2 days)
Update the current components (1 day)
Fifth week
Testing
Testing based on module (1 day)
Testing of functions (2 days)
Sixth week
Post-implementation
Training and development (3 days)
Seventh week
7
Project activities Timescale
Planning activity
Existing parameter of security (1 day)
Understand the feature of CIA (1 day)
Resource planning (2 days)
Creation of project concept (3 days)
First week
Specification of requirements
Analyze the impact (2 days)
Analyze the vulnerabilities (1 day)
Communication with internal team (2 days)
Second week
Pre-design
Contracting (1.5 days)
Solution forming (1 day)
Resource management (2.5 days)
Third week
Designing
Requirement verification (1 day)
Design the Prototyping (3 days)
Final the project design (1 day)
Fourth week
Implementation
Install hardware and software (3 days)
Configuration (2 days)
Update the current components (1 day)
Fifth week
Testing
Testing based on module (1 day)
Testing of functions (2 days)
Sixth week
Post-implementation
Training and development (3 days)
Seventh week
7
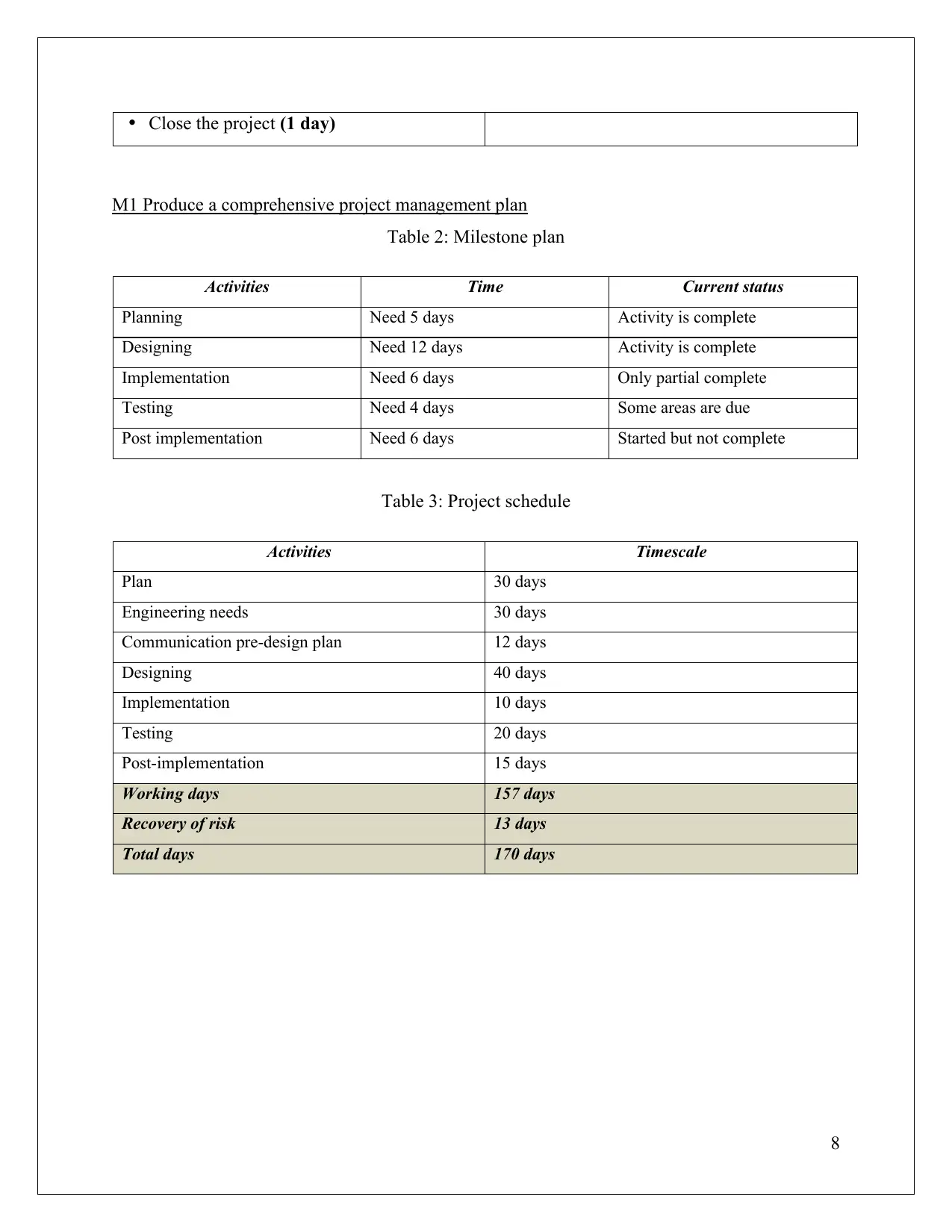
Close the project (1 day)
M1 Produce a comprehensive project management plan
Table 2: Milestone plan
Activities Time Current status
Planning Need 5 days Activity is complete
Designing Need 12 days Activity is complete
Implementation Need 6 days Only partial complete
Testing Need 4 days Some areas are due
Post implementation Need 6 days Started but not complete
Table 3: Project schedule
Activities Timescale
Plan 30 days
Engineering needs 30 days
Communication pre-design plan 12 days
Designing 40 days
Implementation 10 days
Testing 20 days
Post-implementation 15 days
Working days 157 days
Recovery of risk 13 days
Total days 170 days
8
M1 Produce a comprehensive project management plan
Table 2: Milestone plan
Activities Time Current status
Planning Need 5 days Activity is complete
Designing Need 12 days Activity is complete
Implementation Need 6 days Only partial complete
Testing Need 4 days Some areas are due
Post implementation Need 6 days Started but not complete
Table 3: Project schedule
Activities Timescale
Plan 30 days
Engineering needs 30 days
Communication pre-design plan 12 days
Designing 40 days
Implementation 10 days
Testing 20 days
Post-implementation 15 days
Working days 157 days
Recovery of risk 13 days
Total days 170 days
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





