Wide Area Network Technology: Design, Configuration, and Security
VerifiedAdded on 2020/02/14
|25
|5245
|53
Report
AI Summary
This report delves into the intricacies of Wide Area Network (WAN) technology, encompassing various aspects from fundamental concepts to practical implementation. It initiates with an overview of WAN technologies, including point-to-point connections, switching methods (circuit and packet), virtual circuits, and dial-up services, along with relevant devices and protocols like Frame Relay, private lines, NAT/PAT, and ATM. The report then addresses critical WAN concerns, such as network reliability, security threats, and performance degradation, emphasizing the importance of Quality of Service (QoS) and evaluating different trust systems. Furthermore, it outlines the design of a WAN network infrastructure, detailing connectivity options, topology, QoS profiles, and server configurations, followed by an evaluation of the design based on reliability, availability, cost, and scalability. The report also covers the configuration of WAN infrastructure, including device settings and security measures, and concludes with a discussion on network monitoring tools, troubleshooting techniques, and strategies for improving WAN security, reliability, and performance.

Wide Area Networking Technology 1
Wide Area Networking Technology
Student’s Name:
Instructor’s Name:
Date:
Wide Area Networking Technology
Student’s Name:
Instructor’s Name:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wide Area Networking Technology 2
Contents
Task 1..........................................................................................................................................................2
Wide Area Network.................................................................................................................................2
The point to point connection.................................................................................................................3
SWITCHING..............................................................................................................................................4
Circuit Switching......................................................................................................................................4
Packet switching......................................................................................................................................5
WAN virtual circuits.................................................................................................................................6
WAN dialups, devices and switches.........................................................................................................6
WAN protocols........................................................................................................................................6
Frame Relay Technology..........................................................................................................................6
Private Line Technology...........................................................................................................................7
NAT and PAT............................................................................................................................................7
ATM.........................................................................................................................................................7
WAN is open to many security threats and performance degradation; discuss WAN concerns in terms of
network reliability, security and performance. Include a critical evaluation of different trust systems.....7
1.1 QoS....................................................................................................................................................7
1.2 WAN Problems..................................................................................................................................9
Trust Systems in WAN.......................................................................................................................10
2.1 Design with the aid of diagram the WAN network infrastructure to meet the requirement of the
above scenario..........................................................................................................................................10
Connectivity Options – devices..............................................................................................................11
Topology................................................................................................................................................12
QoS profiles.......................................................................................................................................13
Servers...............................................................................................................................................13
DHCP Service Configuration...............................................................................................................14
Inline Power.......................................................................................................................................14
2.2 Evaluation with respect to reliability, availability, cost and scalability [5].......................................14
3.1 The company director asked you to build and configure the WAN infrastructure to meet your
designed WAN infrastructure....................................................................................................................15
Device configuration..............................................................................................................................15
Security..................................................................................................................................................16
Technology............................................................................................................................................17
3.2 Finalize the process of implementation and show the suitability of your network design..................19
Contents
Task 1..........................................................................................................................................................2
Wide Area Network.................................................................................................................................2
The point to point connection.................................................................................................................3
SWITCHING..............................................................................................................................................4
Circuit Switching......................................................................................................................................4
Packet switching......................................................................................................................................5
WAN virtual circuits.................................................................................................................................6
WAN dialups, devices and switches.........................................................................................................6
WAN protocols........................................................................................................................................6
Frame Relay Technology..........................................................................................................................6
Private Line Technology...........................................................................................................................7
NAT and PAT............................................................................................................................................7
ATM.........................................................................................................................................................7
WAN is open to many security threats and performance degradation; discuss WAN concerns in terms of
network reliability, security and performance. Include a critical evaluation of different trust systems.....7
1.1 QoS....................................................................................................................................................7
1.2 WAN Problems..................................................................................................................................9
Trust Systems in WAN.......................................................................................................................10
2.1 Design with the aid of diagram the WAN network infrastructure to meet the requirement of the
above scenario..........................................................................................................................................10
Connectivity Options – devices..............................................................................................................11
Topology................................................................................................................................................12
QoS profiles.......................................................................................................................................13
Servers...............................................................................................................................................13
DHCP Service Configuration...............................................................................................................14
Inline Power.......................................................................................................................................14
2.2 Evaluation with respect to reliability, availability, cost and scalability [5].......................................14
3.1 The company director asked you to build and configure the WAN infrastructure to meet your
designed WAN infrastructure....................................................................................................................15
Device configuration..............................................................................................................................15
Security..................................................................................................................................................16
Technology............................................................................................................................................17
3.2 Finalize the process of implementation and show the suitability of your network design..................19

Wide Area Networking Technology 3
Testing [7]..................................................................................................................................................19
4.1 There are many tools available in the market to monitor the performance and network security.
Explain the use and importance of network monitoring tools. Include some examples of troubleshooting
by using one of the tools you selected......................................................................................................20
4.2 Wide area network known to be open for many external threats, produce a report to improve on
security, reliability and performance.........................................................................................................21
References.................................................................................................................................................23
Task 1
We will cover the protocols and technologies that are involved in the implementation long
distance networks (WAN - Wide Area Network). This will touch on the basis for long-haul
networks, types of services provided, and encapsulation Optional Links. We also discuss the
point to point links, the switch packets and virtual circuits.
Wide Area Network
A WAN is a data communications network that operates beyond the field of LANs action. Wide
area network is spanned over large geographic area and may comprise of several LAN’s.
Testing [7]..................................................................................................................................................19
4.1 There are many tools available in the market to monitor the performance and network security.
Explain the use and importance of network monitoring tools. Include some examples of troubleshooting
by using one of the tools you selected......................................................................................................20
4.2 Wide area network known to be open for many external threats, produce a report to improve on
security, reliability and performance.........................................................................................................21
References.................................................................................................................................................23
Task 1
We will cover the protocols and technologies that are involved in the implementation long
distance networks (WAN - Wide Area Network). This will touch on the basis for long-haul
networks, types of services provided, and encapsulation Optional Links. We also discuss the
point to point links, the switch packets and virtual circuits.
Wide Area Network
A WAN is a data communications network that operates beyond the field of LANs action. Wide
area network is spanned over large geographic area and may comprise of several LAN’s.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Wide Area Networking Technology 4
A WAN uses data links, such as Digital Networks Integrated Services (ISDN), ATM, DSL, X.25
and Frame Relay to access bandwidth across a large area geographical. A WAN connects the
different units of a company, or connects different units to units belonging to other companies,
external services (Databases, etc.), remote users. WAN connect LANs together, or remote
connecting sites. It can be installed in several countries or worldwide. Ultimately, the WANs
operate beyond the geographical area of LAN. By this feature, the WAN transport a range of
information, such as data, voice, images, etc. Different WAN technologies are point to point
links, switching (packet switching and circuit switching), WAN virtual circuit, WAN dialup
services and devices. Some of them are discussed below:
The point to point connection
The point to point connection is fixed and permanent in nature to connect two computers spaced
from each other in a network. It is also known as lease line. Pont to point connection is dedicated
connection between to devices so that better speed and reliability in data transmission can be
achieved. Figure 1 illustrates this type of connection.
Figure: Diagram of a point to point connection
Data can be transmitted through the connection in following two ways:
(1) Datagram transmission: data is transmitted in packet of variable lengths so that
bandwidth can be used more appropriately.
A WAN uses data links, such as Digital Networks Integrated Services (ISDN), ATM, DSL, X.25
and Frame Relay to access bandwidth across a large area geographical. A WAN connects the
different units of a company, or connects different units to units belonging to other companies,
external services (Databases, etc.), remote users. WAN connect LANs together, or remote
connecting sites. It can be installed in several countries or worldwide. Ultimately, the WANs
operate beyond the geographical area of LAN. By this feature, the WAN transport a range of
information, such as data, voice, images, etc. Different WAN technologies are point to point
links, switching (packet switching and circuit switching), WAN virtual circuit, WAN dialup
services and devices. Some of them are discussed below:
The point to point connection
The point to point connection is fixed and permanent in nature to connect two computers spaced
from each other in a network. It is also known as lease line. Pont to point connection is dedicated
connection between to devices so that better speed and reliability in data transmission can be
achieved. Figure 1 illustrates this type of connection.
Figure: Diagram of a point to point connection
Data can be transmitted through the connection in following two ways:
(1) Datagram transmission: data is transmitted in packet of variable lengths so that
bandwidth can be used more appropriately.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wide Area Networking Technology 5
(2) Data stream transmission: data is transmitted as in form of continues byte streams
which are buffered at receiver end to compose as a message.
The advantage of using point to point connection link is that clients in organization gets the
dedicated connection which is fast but it is possible than whole bandwidth may not be used by
client. As a result, it is more expensive per client in comparison of switching technologies.
SWITCHING
Switching involves moving data to through a series of intermediate steps, or segments, rather
than by direct displacement a starting point to a finishing point. The switching instead of
depending on a permanent connection between the source and the destination, it relies on a series
of temporary connections that relay messages from station to station. It serves to same purpose as
the direct connection, but with more efficient use of resources transmission. WANs (and local
networks like Ethernet and Token Ring (token ring) depend first on the packet, but they also
make use of the switching circuit, message switching, and more recently, high speed packet
Switching technology, known as the cell relay naming (Cell relay).
Circuit Switching
Circuit switching corresponds to the creation of a physical connection between the sender and
recipient which is preserved and maintained through the carrier network to provide the
communication for the session. For it to happen, prior installation of connection and allocation of
bandwidth is necessary. Its main drawback is that of any unused bandwidth. Since the connection
is limited to two communicating parties, unused bandwidth can be "borrowed" by any other
transmission. Circuit switching is more like the telephone calls. ISDN is the example of circuit
(2) Data stream transmission: data is transmitted as in form of continues byte streams
which are buffered at receiver end to compose as a message.
The advantage of using point to point connection link is that clients in organization gets the
dedicated connection which is fast but it is possible than whole bandwidth may not be used by
client. As a result, it is more expensive per client in comparison of switching technologies.
SWITCHING
Switching involves moving data to through a series of intermediate steps, or segments, rather
than by direct displacement a starting point to a finishing point. The switching instead of
depending on a permanent connection between the source and the destination, it relies on a series
of temporary connections that relay messages from station to station. It serves to same purpose as
the direct connection, but with more efficient use of resources transmission. WANs (and local
networks like Ethernet and Token Ring (token ring) depend first on the packet, but they also
make use of the switching circuit, message switching, and more recently, high speed packet
Switching technology, known as the cell relay naming (Cell relay).
Circuit Switching
Circuit switching corresponds to the creation of a physical connection between the sender and
recipient which is preserved and maintained through the carrier network to provide the
communication for the session. For it to happen, prior installation of connection and allocation of
bandwidth is necessary. Its main drawback is that of any unused bandwidth. Since the connection
is limited to two communicating parties, unused bandwidth can be "borrowed" by any other
transmission. Circuit switching is more like the telephone calls. ISDN is the example of circuit
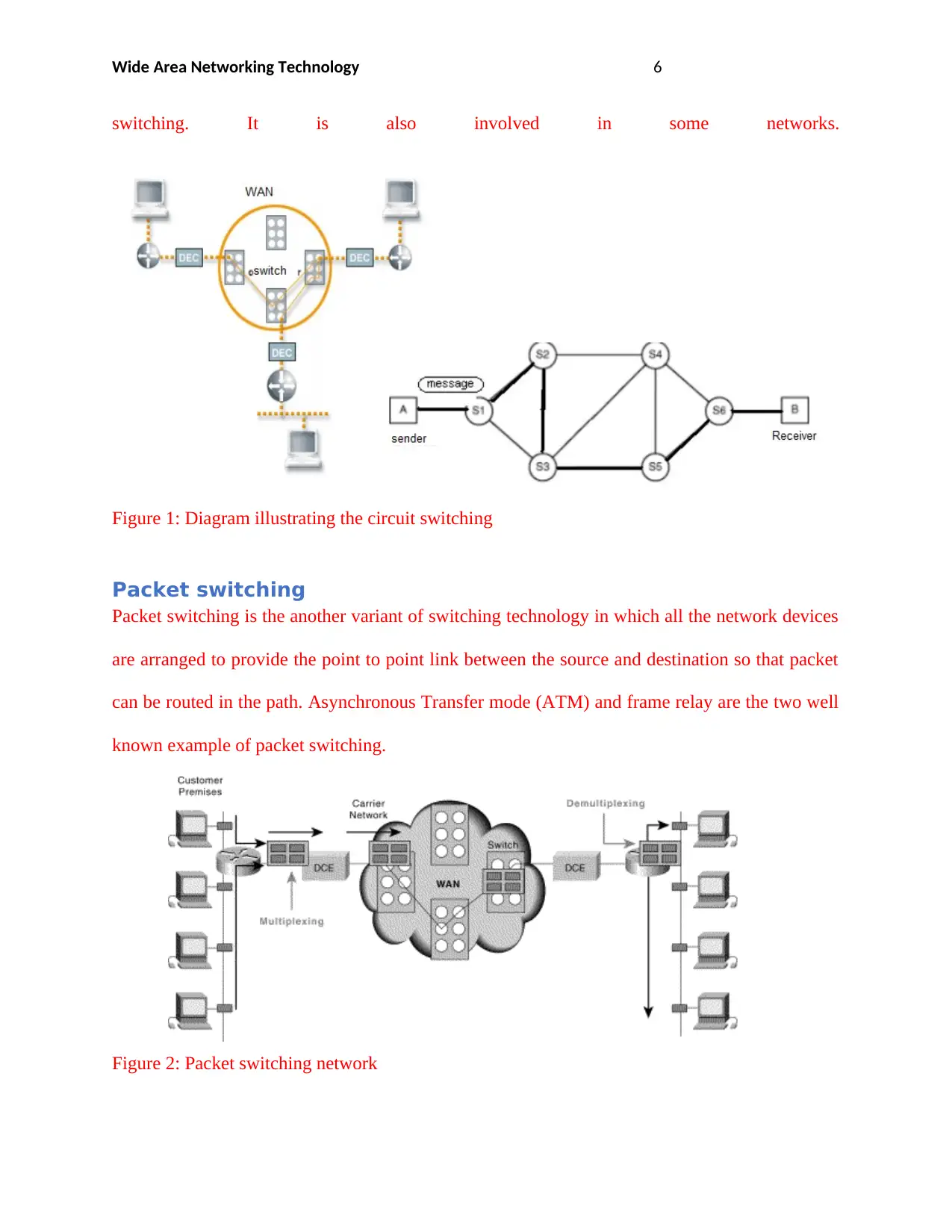
Wide Area Networking Technology 6
switching. It is also involved in some networks.
Figure 1: Diagram illustrating the circuit switching
Packet switching
Packet switching is the another variant of switching technology in which all the network devices
are arranged to provide the point to point link between the source and destination so that packet
can be routed in the path. Asynchronous Transfer mode (ATM) and frame relay are the two well
known example of packet switching.
Figure 2: Packet switching network
switching. It is also involved in some networks.
Figure 1: Diagram illustrating the circuit switching
Packet switching
Packet switching is the another variant of switching technology in which all the network devices
are arranged to provide the point to point link between the source and destination so that packet
can be routed in the path. Asynchronous Transfer mode (ATM) and frame relay are the two well
known example of packet switching.
Figure 2: Packet switching network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Wide Area Networking Technology 7
WAN virtual circuits
Virtual circuits are logical combinations of connections to deliver the packet at the receiver side.
There are two types of virtual circuits: switched virtual circuits (SVCs) and permanent virtual
circuits (PVCs). Difference between both types is that SVCs are more flexible to determine the
routes but complex in nature in comparison of PVCs.
WAN dialups, devices and switches
Dial up services provide the cost effective connection between two nodes in network. Example
of dial up service is dial-on-demand which is used to initiate the connection and to close it on
demand. For it, routers are configured to optimize the path in traffic on channel. Switches,
modems and ISDN terminal adapters are example of WAN devices whereas frame relay and
X.25 are WAN switches.
WAN protocols
Frame Relay Technology
The frame relay (FR) is a switching protocol packet located at the link layer (level 2) of the Open
Systems Interconnection mode (OSI) model, used for intersite exchanges (WAN) it was invented
by Eric Scace, an engineer at Sprint International. PVC (Permanent Virtual Circuit) identify at
the DTE and DCE interfaces through DLCI (Data Link Connection Identifiers) in order to
distinguish the flow from different PVC. DLCIs are generally identification numbers only local
value (an interface) which equates to a sub-interface in some contexts: for example on a router,
each PVC on an interface may well have its own associated IP address.
Private Line Technology
A dedicated line (LS) or leased line is in computer science or telecommunications, a connection
between two points, permanently connected together. It contrasts sharing resources like a VPN
WAN virtual circuits
Virtual circuits are logical combinations of connections to deliver the packet at the receiver side.
There are two types of virtual circuits: switched virtual circuits (SVCs) and permanent virtual
circuits (PVCs). Difference between both types is that SVCs are more flexible to determine the
routes but complex in nature in comparison of PVCs.
WAN dialups, devices and switches
Dial up services provide the cost effective connection between two nodes in network. Example
of dial up service is dial-on-demand which is used to initiate the connection and to close it on
demand. For it, routers are configured to optimize the path in traffic on channel. Switches,
modems and ISDN terminal adapters are example of WAN devices whereas frame relay and
X.25 are WAN switches.
WAN protocols
Frame Relay Technology
The frame relay (FR) is a switching protocol packet located at the link layer (level 2) of the Open
Systems Interconnection mode (OSI) model, used for intersite exchanges (WAN) it was invented
by Eric Scace, an engineer at Sprint International. PVC (Permanent Virtual Circuit) identify at
the DTE and DCE interfaces through DLCI (Data Link Connection Identifiers) in order to
distinguish the flow from different PVC. DLCIs are generally identification numbers only local
value (an interface) which equates to a sub-interface in some contexts: for example on a router,
each PVC on an interface may well have its own associated IP address.
Private Line Technology
A dedicated line (LS) or leased line is in computer science or telecommunications, a connection
between two points, permanently connected together. It contrasts sharing resources like a VPN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Wide Area Networking Technology 8
network type (X25, Frame Relay, ATM, MPLS ...).The dedicated line is often dedicated between
the client and the network access point the operator, after the data is transported either on a TDM
network, ATM or MPLS where Bandwidth is dedicated.
NAT and PAT
NAT and PAT are two protocols that allow machines on a network internal / local access to the
Internet with their IP addresses "non-public", so they include a translate these addresses into
public IP addresses which are limited, hence the need for this translation.
ATM
ATM is Asynchronous Transfer Mode. The data is transferred from a point to other point in
small cells. The use of ATM is done to make a network faster. The standard size of ATM is 53
bytes.. Thus the packets on the layer 3 are subdivided into cells of 53 bytes. ATM is faster than
frame relay as well as Point to Point. Use of ATM allows transfer of video, voice and other data
over the same line.
WAN is open to many security threats and performance
degradation; discuss WAN concerns in terms of network
reliability, security and performance. Include a critical
evaluation of different trust systems
1.1 QoS [6]
Over the past few years, data networks have become increasingly viable for different types of
telephony devices. The benefits of converged networks have become very apparent in recent
times. This makes it very convincing for companies to adapt VOIP over WAN. WAN is known
for its plentiful raw bandwidth. However, for VOIP it is necessary to make sure that packet
throughput is remarkably high. Throughput is important for the VoIP to function well. Without
network type (X25, Frame Relay, ATM, MPLS ...).The dedicated line is often dedicated between
the client and the network access point the operator, after the data is transported either on a TDM
network, ATM or MPLS where Bandwidth is dedicated.
NAT and PAT
NAT and PAT are two protocols that allow machines on a network internal / local access to the
Internet with their IP addresses "non-public", so they include a translate these addresses into
public IP addresses which are limited, hence the need for this translation.
ATM
ATM is Asynchronous Transfer Mode. The data is transferred from a point to other point in
small cells. The use of ATM is done to make a network faster. The standard size of ATM is 53
bytes.. Thus the packets on the layer 3 are subdivided into cells of 53 bytes. ATM is faster than
frame relay as well as Point to Point. Use of ATM allows transfer of video, voice and other data
over the same line.
WAN is open to many security threats and performance
degradation; discuss WAN concerns in terms of network
reliability, security and performance. Include a critical
evaluation of different trust systems
1.1 QoS [6]
Over the past few years, data networks have become increasingly viable for different types of
telephony devices. The benefits of converged networks have become very apparent in recent
times. This makes it very convincing for companies to adapt VOIP over WAN. WAN is known
for its plentiful raw bandwidth. However, for VOIP it is necessary to make sure that packet
throughput is remarkably high. Throughput is important for the VoIP to function well. Without

Wide Area Networking Technology 9
the right QoS settings, bandwidth hogging would happen in the WAN. Bandwidth hogging can
cause an increase in the amount of jitter and latency of voice, especially when certain video and
data applications run in the background.
In the WAN connection, packets that take more than 200 milliseconds to travel between
locations can reduce voice quality. This is when the transaction becomes absolutely
unacceptable. If employees in the company are using their mobile devices for VoIP, they will see
a considerable amount of interjection. This will make it difficult for users to differentiate pauses
and high latency.
Companies that connect different branches with VoIP should have extreme network policy based
QoS. Several components are required to satisfy these requirements. Several components are
needed to manage bandwidth characteristics. In simpler terms, policy based QoS is a
combination of treatment and classification. These policies make sure network administrators
can control the bandwidth of several applications. Conversely, jitter and latency can be
controlled over applications that require them. This classification can be done using implicit
information – voice VLAN, TCP/UDP ports or explicit information – 802.1p code points
DiffServ. The treatment revolves around bandwidth and priotitzation management, which is also
taken care in extreme network switches through max and min bandwidth control – in conjunction
with 8 queues on every switch port. For a company that has branches in four different locations
and the main HQ, i series chipset switches are sufficient. These queues can be carefully rate
shaped, thus controlling latency of the network. This would be a simple policy based QoS for
this company. Appropriate QoS tools should be used to make sure real time voice traffic is
managed accurately.
1.2 WAN Problems [5][4]
the right QoS settings, bandwidth hogging would happen in the WAN. Bandwidth hogging can
cause an increase in the amount of jitter and latency of voice, especially when certain video and
data applications run in the background.
In the WAN connection, packets that take more than 200 milliseconds to travel between
locations can reduce voice quality. This is when the transaction becomes absolutely
unacceptable. If employees in the company are using their mobile devices for VoIP, they will see
a considerable amount of interjection. This will make it difficult for users to differentiate pauses
and high latency.
Companies that connect different branches with VoIP should have extreme network policy based
QoS. Several components are required to satisfy these requirements. Several components are
needed to manage bandwidth characteristics. In simpler terms, policy based QoS is a
combination of treatment and classification. These policies make sure network administrators
can control the bandwidth of several applications. Conversely, jitter and latency can be
controlled over applications that require them. This classification can be done using implicit
information – voice VLAN, TCP/UDP ports or explicit information – 802.1p code points
DiffServ. The treatment revolves around bandwidth and priotitzation management, which is also
taken care in extreme network switches through max and min bandwidth control – in conjunction
with 8 queues on every switch port. For a company that has branches in four different locations
and the main HQ, i series chipset switches are sufficient. These queues can be carefully rate
shaped, thus controlling latency of the network. This would be a simple policy based QoS for
this company. Appropriate QoS tools should be used to make sure real time voice traffic is
managed accurately.
1.2 WAN Problems [5][4]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Wide Area Networking Technology 10
WAN has several problems that should be dealt with carefully. The company has to have a well-
stocked toolkit to handle these problems. The network design should take care of insufficient
bandwidth. Network techniques should be used to optimize bandwidth using data reduction and
compression. If redundancies are removed from the network and caching is introduced, issues of
insufficient bandwidth can be overcome. There are special WAN optimization controllers to
support reduction and compression. Standard web security gateways have this technique too.
In organizational level, applications that perform poorly should be removed. This can be
achieved by deploying a ADC near the application servers. Other effective options include the
use of WOCs with optimization features and web application firewalls. Network reliability is a
major concern in WAN systems. In order to improve network reliability, organizations can
reduce link downtime. The company has to reduce the number of links for a particular operation.
For example, the number of links for faxing can be reduced. Then, link balancing and dynamic
routing has to be encouraged. It would be wise to use combination VPN or router devices or edge
based firewalls to ensure network reliability.
Likewise, application reliability has to be taken care. Local load balancing done in Layer 3 and
Layer 2 ADC devices can forward load based on a standard set of algorithms. Global load
balancing (like how the current company has systems in different locations), should be designed
to take care of load from different data centers. This might be less effective but it is required.
Trust Systems in WAN
Network security is a critical component of WAN. This is where trust systems come into the
picture. A well known trust system would be edge switching. This offers cooperative firewalls
for company networks. These firewalls are capable of managing all types of communication. It
dissolves boundaries in closed and open networks. All communication is managed by a policy.
WAN has several problems that should be dealt with carefully. The company has to have a well-
stocked toolkit to handle these problems. The network design should take care of insufficient
bandwidth. Network techniques should be used to optimize bandwidth using data reduction and
compression. If redundancies are removed from the network and caching is introduced, issues of
insufficient bandwidth can be overcome. There are special WAN optimization controllers to
support reduction and compression. Standard web security gateways have this technique too.
In organizational level, applications that perform poorly should be removed. This can be
achieved by deploying a ADC near the application servers. Other effective options include the
use of WOCs with optimization features and web application firewalls. Network reliability is a
major concern in WAN systems. In order to improve network reliability, organizations can
reduce link downtime. The company has to reduce the number of links for a particular operation.
For example, the number of links for faxing can be reduced. Then, link balancing and dynamic
routing has to be encouraged. It would be wise to use combination VPN or router devices or edge
based firewalls to ensure network reliability.
Likewise, application reliability has to be taken care. Local load balancing done in Layer 3 and
Layer 2 ADC devices can forward load based on a standard set of algorithms. Global load
balancing (like how the current company has systems in different locations), should be designed
to take care of load from different data centers. This might be less effective but it is required.
Trust Systems in WAN
Network security is a critical component of WAN. This is where trust systems come into the
picture. A well known trust system would be edge switching. This offers cooperative firewalls
for company networks. These firewalls are capable of managing all types of communication. It
dissolves boundaries in closed and open networks. All communication is managed by a policy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Wide Area Networking Technology 11
These firewalls are designed to collect and give evidence for different types of network attacks.
Thus, the WAN connections become trust worthy. Trust systems in WAN encourage the use of
new firewalls and Edge switching over Network Address Translations.
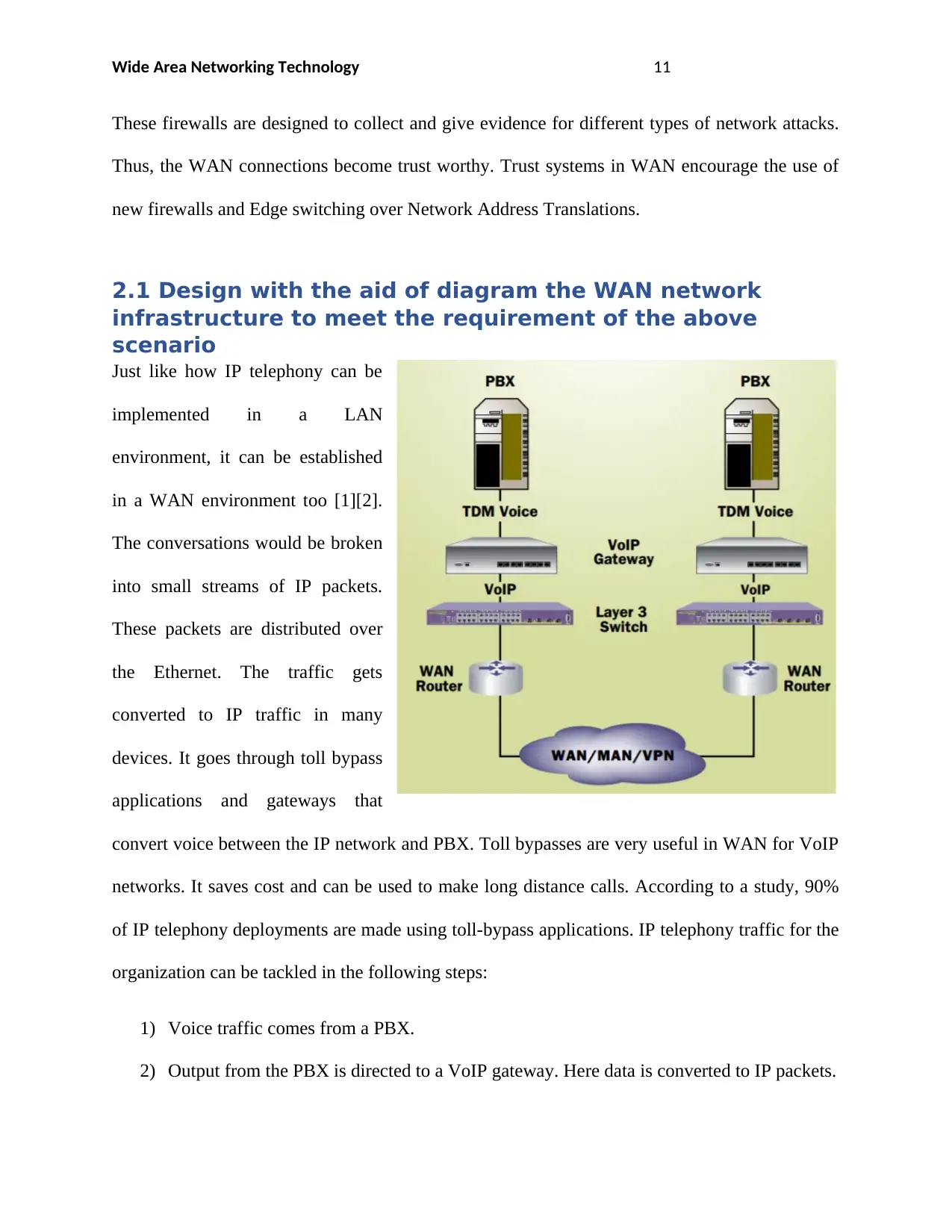
2.1 Design with the aid of diagram the WAN network
infrastructure to meet the requirement of the above
scenario
Just like how IP telephony can be
implemented in a LAN
environment, it can be established
in a WAN environment too [1][2].
The conversations would be broken
into small streams of IP packets.
These packets are distributed over
the Ethernet. The traffic gets
converted to IP traffic in many
devices. It goes through toll bypass
applications and gateways that
convert voice between the IP network and PBX. Toll bypasses are very useful in WAN for VoIP
networks. It saves cost and can be used to make long distance calls. According to a study, 90%
of IP telephony deployments are made using toll-bypass applications. IP telephony traffic for the
organization can be tackled in the following steps:
1) Voice traffic comes from a PBX.
2) Output from the PBX is directed to a VoIP gateway. Here data is converted to IP packets.
These firewalls are designed to collect and give evidence for different types of network attacks.
Thus, the WAN connections become trust worthy. Trust systems in WAN encourage the use of
new firewalls and Edge switching over Network Address Translations.
2.1 Design with the aid of diagram the WAN network
infrastructure to meet the requirement of the above
scenario
Just like how IP telephony can be
implemented in a LAN
environment, it can be established
in a WAN environment too [1][2].
The conversations would be broken
into small streams of IP packets.
These packets are distributed over
the Ethernet. The traffic gets
converted to IP traffic in many
devices. It goes through toll bypass
applications and gateways that
convert voice between the IP network and PBX. Toll bypasses are very useful in WAN for VoIP
networks. It saves cost and can be used to make long distance calls. According to a study, 90%
of IP telephony deployments are made using toll-bypass applications. IP telephony traffic for the
organization can be tackled in the following steps:
1) Voice traffic comes from a PBX.
2) Output from the PBX is directed to a VoIP gateway. Here data is converted to IP packets.
Wide Area Networking Technology 12
3) IP packets are prepared and sent over an IP-based WAN network.
4) At the other end, IP Packets are converted to data that can be fed into the PBX.
Here, the IP-based WAN network is a private entity with frame relay service or ATM service or
leased lines. For this company, a public internet service provider or IP carrier will be required at
each branch.
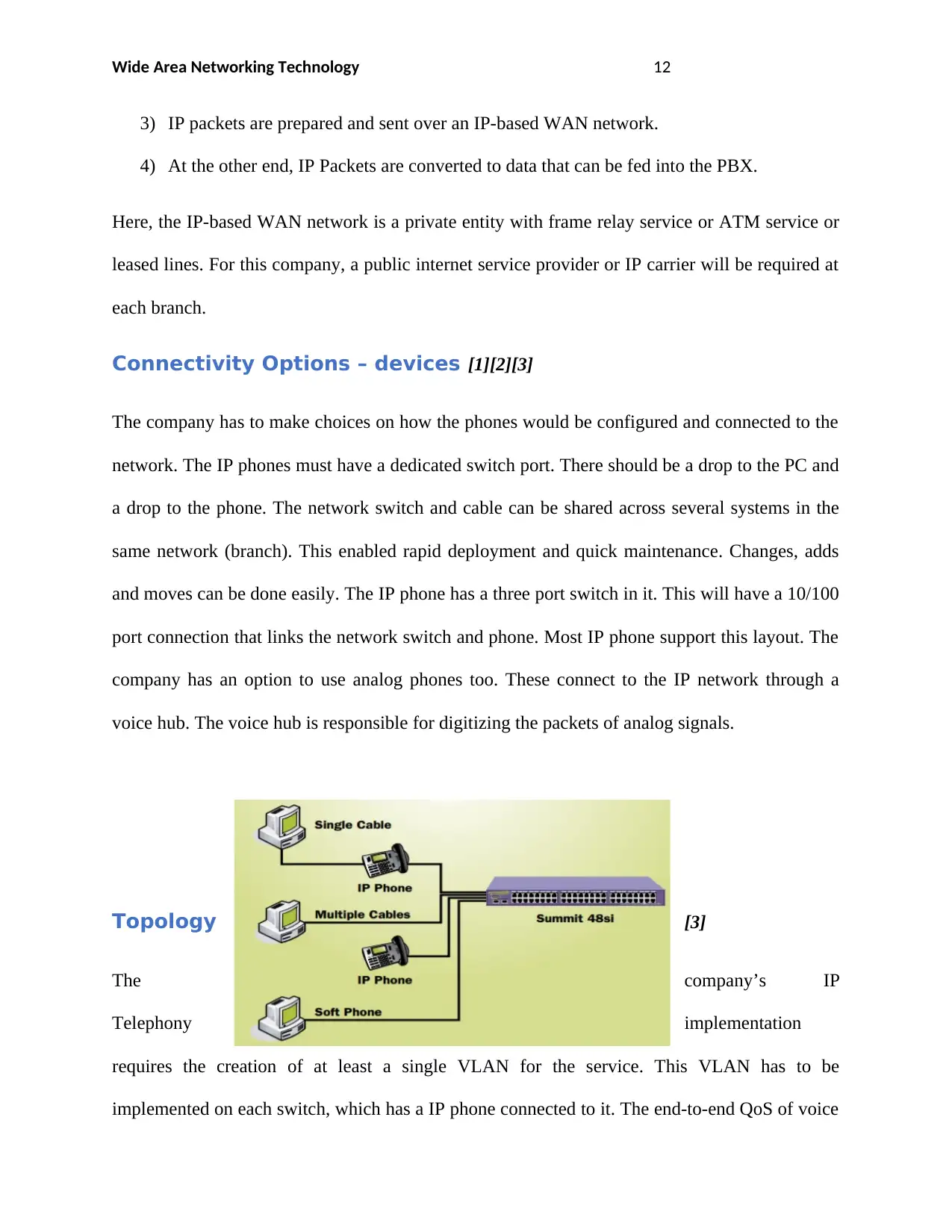
Connectivity Options – devices [1][2][3]
The company has to make choices on how the phones would be configured and connected to the
network. The IP phones must have a dedicated switch port. There should be a drop to the PC and
a drop to the phone. The network switch and cable can be shared across several systems in the
same network (branch). This enabled rapid deployment and quick maintenance. Changes, adds
and moves can be done easily. The IP phone has a three port switch in it. This will have a 10/100
port connection that links the network switch and phone. Most IP phone support this layout. The
company has an option to use analog phones too. These connect to the IP network through a
voice hub. The voice hub is responsible for digitizing the packets of analog signals.
Topology [3]
The company’s IP
Telephony implementation
requires the creation of at least a single VLAN for the service. This VLAN has to be
implemented on each switch, which has a IP phone connected to it. The end-to-end QoS of voice
3) IP packets are prepared and sent over an IP-based WAN network.
4) At the other end, IP Packets are converted to data that can be fed into the PBX.
Here, the IP-based WAN network is a private entity with frame relay service or ATM service or
leased lines. For this company, a public internet service provider or IP carrier will be required at
each branch.
Connectivity Options – devices [1][2][3]
The company has to make choices on how the phones would be configured and connected to the
network. The IP phones must have a dedicated switch port. There should be a drop to the PC and
a drop to the phone. The network switch and cable can be shared across several systems in the
same network (branch). This enabled rapid deployment and quick maintenance. Changes, adds
and moves can be done easily. The IP phone has a three port switch in it. This will have a 10/100
port connection that links the network switch and phone. Most IP phone support this layout. The
company has an option to use analog phones too. These connect to the IP network through a
voice hub. The voice hub is responsible for digitizing the packets of analog signals.
Topology [3]
The company’s IP
Telephony implementation
requires the creation of at least a single VLAN for the service. This VLAN has to be
implemented on each switch, which has a IP phone connected to it. The end-to-end QoS of voice
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




