Detailed Report: WannaCry Ransomware Attack, Impact and Analysis
VerifiedAdded on 2024/06/28
|10
|1079
|253
Report
AI Summary
This report provides a detailed analysis of the WannaCry ransomware attack, a significant cyber security event that emerged in May 2017. It identifies WannaCry as a data kidnapping attack employing asymmetric encryption. The report outlines the attack's technical aspects, including its exploitation of the EternalBlue vulnerability (MS17-010) in Windows systems and its rapid spread through LAN networks. It details the encryption process, the ransom demands, and the kill switch mechanism. Furthermore, the report quantifies the global impact of WannaCry, estimating over 200,000 infected machines and approximately $50,000 in ransom payments. Specific examples of affected organizations, such as Britain’s National Health Service and Honda Motors, are provided to illustrate the real-world consequences. The report concludes by considering the perspectives of both the attacker and the organization under attack, highlighting the importance of robust cyber security measures and timely patching of vulnerabilities. Desklib provides more solved assignments and study resources for students.

Contents
List of Figures..................................................................................................................................2
List of Tables................................................................................................................................... 2
Q1 What sort of cyber security attack was WannaCry Ransomware Attack and when did it first
emerge and occur?........................................................................................................................... 3
Q2 What was the impact of the WannaCry Ransomware Attack in dollar terms for organizations
globally – give two specific examples of organizations that were impacted by the WannaCry
Ransomware Attack?....................................................................................................................... 4
Q3 Explain how the WannaCry Ransomware Attack works as a process and technically –
considering the perspectives of both the attacker and organisation that could be attacked?...........5
References......................................................................................................................................10
List of Figures..................................................................................................................................2
List of Tables................................................................................................................................... 2
Q1 What sort of cyber security attack was WannaCry Ransomware Attack and when did it first
emerge and occur?........................................................................................................................... 3
Q2 What was the impact of the WannaCry Ransomware Attack in dollar terms for organizations
globally – give two specific examples of organizations that were impacted by the WannaCry
Ransomware Attack?....................................................................................................................... 4
Q3 Explain how the WannaCry Ransomware Attack works as a process and technically –
considering the perspectives of both the attacker and organisation that could be attacked?...........5
References......................................................................................................................................10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

List of Figures
Figure 1: Showing encryption process for ransomware..................................................................5
Figure 2: Showing first screen of WannaCry.................................................................................. 6
Figure 3: Showing working of wannacry ransomware....................................................................8
List of Tables
Table 1: Showing basic details about the WannaCry ransomware attack.......................................3
Table 2: Showing Impacts of WannaCry ransomware....................................................................4
Figure 1: Showing encryption process for ransomware..................................................................5
Figure 2: Showing first screen of WannaCry.................................................................................. 6
Figure 3: Showing working of wannacry ransomware....................................................................8
List of Tables
Table 1: Showing basic details about the WannaCry ransomware attack.......................................3
Table 2: Showing Impacts of WannaCry ransomware....................................................................4
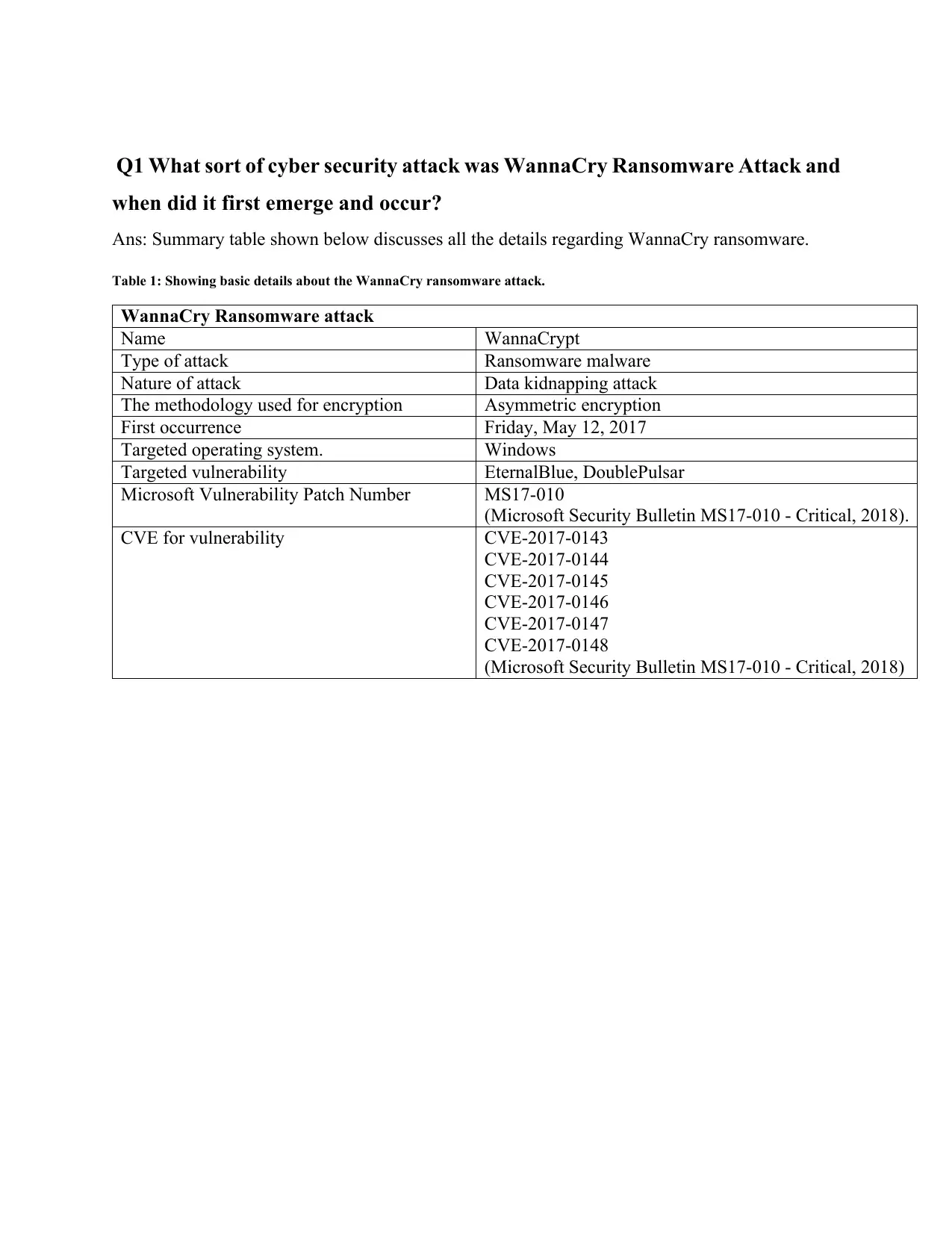
Q1 What sort of cyber security attack was WannaCry Ransomware Attack and
when did it first emerge and occur?
Ans: Summary table shown below discusses all the details regarding WannaCry ransomware.
Table 1: Showing basic details about the WannaCry ransomware attack.
WannaCry Ransomware attack
Name WannaCrypt
Type of attack Ransomware malware
Nature of attack Data kidnapping attack
The methodology used for encryption Asymmetric encryption
First occurrence Friday, May 12, 2017
Targeted operating system. Windows
Targeted vulnerability EternalBlue, DoublePulsar
Microsoft Vulnerability Patch Number MS17-010
(Microsoft Security Bulletin MS17-010 - Critical, 2018).
CVE for vulnerability CVE-2017-0143
CVE-2017-0144
CVE-2017-0145
CVE-2017-0146
CVE-2017-0147
CVE-2017-0148
(Microsoft Security Bulletin MS17-010 - Critical, 2018)
when did it first emerge and occur?
Ans: Summary table shown below discusses all the details regarding WannaCry ransomware.
Table 1: Showing basic details about the WannaCry ransomware attack.
WannaCry Ransomware attack
Name WannaCrypt
Type of attack Ransomware malware
Nature of attack Data kidnapping attack
The methodology used for encryption Asymmetric encryption
First occurrence Friday, May 12, 2017
Targeted operating system. Windows
Targeted vulnerability EternalBlue, DoublePulsar
Microsoft Vulnerability Patch Number MS17-010
(Microsoft Security Bulletin MS17-010 - Critical, 2018).
CVE for vulnerability CVE-2017-0143
CVE-2017-0144
CVE-2017-0145
CVE-2017-0146
CVE-2017-0147
CVE-2017-0148
(Microsoft Security Bulletin MS17-010 - Critical, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q2 What was the impact of the WannaCry Ransomware Attack in dollar terms
for organizations globally – give two specific examples of organizations that
were impacted by the WannaCry Ransomware Attack?
Ans: Summary table shown below discusses the major impact of WannaCry ransomware.
Table 2: Showing Impacts of WannaCry ransomware.
Impact of WannaCry Ransomware attack
Total machine infected Estimate. >200,000
Total ransom paid Estimate. ~ $50,000 bitcoin payment.
Top affected sectors. Services
Manufacturing
Public administration departments
Wholesale trade online platforms
Finance insurance and real estate platforms
A number of countries affected. ~150
Organization mostly affected. Britain’s National Health Service: This
organization experienced service
breakdown in nearly 40 hospitals across
the country.
Honda Motors: Production was stopped in
Honda motors japan car plant when
WannaCry virus hits their computer
networks.
for organizations globally – give two specific examples of organizations that
were impacted by the WannaCry Ransomware Attack?
Ans: Summary table shown below discusses the major impact of WannaCry ransomware.
Table 2: Showing Impacts of WannaCry ransomware.
Impact of WannaCry Ransomware attack
Total machine infected Estimate. >200,000
Total ransom paid Estimate. ~ $50,000 bitcoin payment.
Top affected sectors. Services
Manufacturing
Public administration departments
Wholesale trade online platforms
Finance insurance and real estate platforms
A number of countries affected. ~150
Organization mostly affected. Britain’s National Health Service: This
organization experienced service
breakdown in nearly 40 hospitals across
the country.
Honda Motors: Production was stopped in
Honda motors japan car plant when
WannaCry virus hits their computer
networks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Q3 Explain how the WannaCry Ransomware Attack works as a process and
technically – considering the perspectives of both the attacker and organization
that could be attacked?
WannaCry which is also known as WannaCrypt is the biggest ransomware breakout recorded to
date. It infected approx. 150 countries infecting Britain healthcare agency. Having such big feat
this is less of a crafted ransomware more of a sophisticated one (Richter, 2018).
This ransomware first gets access to victim’s machine in form of an email attachment. It contains
an application which perform the role of encrypting and decrypting data, files containing
encryption keys for encrypting victims data, a copy of the Tor browser (What is WannaCrypt
ransomware, how does it work & how to stay safe, 2018). This can spread rapidly through LAN
exploiting SMB vulnerability to others machines present in the same network.
Figure 1: Showing the encryption process for ransomware.
Source: (Fruhlinger, 2018).
technically – considering the perspectives of both the attacker and organization
that could be attacked?
WannaCry which is also known as WannaCrypt is the biggest ransomware breakout recorded to
date. It infected approx. 150 countries infecting Britain healthcare agency. Having such big feat
this is less of a crafted ransomware more of a sophisticated one (Richter, 2018).
This ransomware first gets access to victim’s machine in form of an email attachment. It contains
an application which perform the role of encrypting and decrypting data, files containing
encryption keys for encrypting victims data, a copy of the Tor browser (What is WannaCrypt
ransomware, how does it work & how to stay safe, 2018). This can spread rapidly through LAN
exploiting SMB vulnerability to others machines present in the same network.
Figure 1: Showing the encryption process for ransomware.
Source: (Fruhlinger, 2018).

This ransomware uses Asymmetric public key encryption in order to encrypt some files. The
encryption process does not get started as soon as it downloaded. First, it tries to make a connection
to a URL which is “http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/”.
WannaCrypt searches for popular extensions
like .psd , .xltx , .iso , .pst , .xlw , .jar , .rar , .zip , .java , .raw and many more.
If found then it change the existing extension to “.WNCRY” to the file name
This so-called kill switch has been pushed. A security researcher registered this domain and slow
down the wildfire of WannaCry.
After encrypting the files on the victim machine, it shows a message like this when we try to access
any of files.
Figure 2: Showing the first screen of WannaCry.
Source: (What is WannaCrypt ransomware, how does it work & how to stay safe, 2018).
encryption process does not get started as soon as it downloaded. First, it tries to make a connection
to a URL which is “http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/”.
WannaCrypt searches for popular extensions
like .psd , .xltx , .iso , .pst , .xlw , .jar , .rar , .zip , .java , .raw and many more.
If found then it change the existing extension to “.WNCRY” to the file name
This so-called kill switch has been pushed. A security researcher registered this domain and slow
down the wildfire of WannaCry.
After encrypting the files on the victim machine, it shows a message like this when we try to access
any of files.
Figure 2: Showing the first screen of WannaCry.
Source: (What is WannaCrypt ransomware, how does it work & how to stay safe, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Next step is to ask for ransom from the victim which initially was $300 and later raised to $600.
And if the ransom is paid it is not guaranteed that victim will get his files back.
And if the ransom is paid it is not guaranteed that victim will get his files back.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
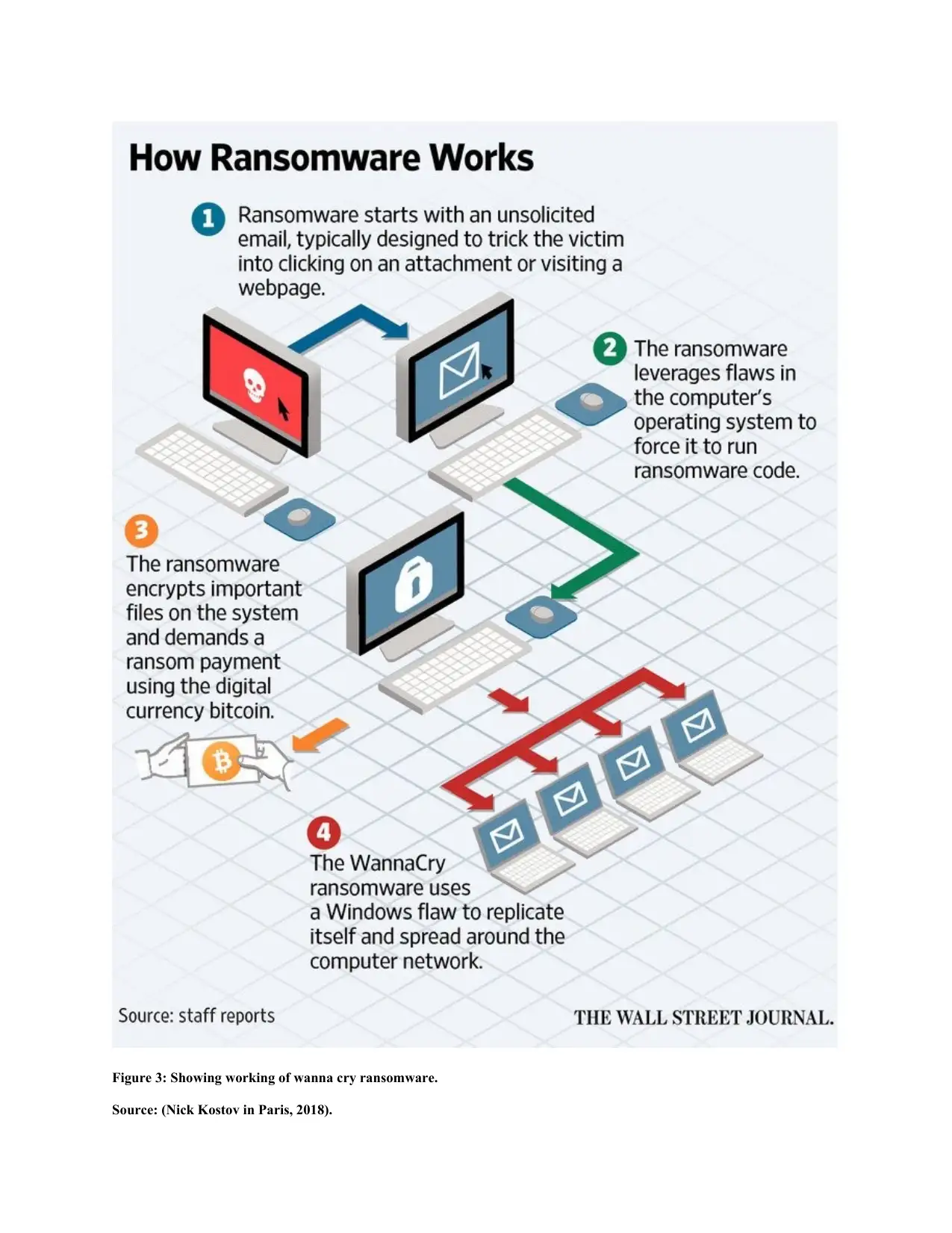
Figure 3: Showing working of wanna cry ransomware.
Source: (Nick Kostov in Paris, 2018).
Source: (Nick Kostov in Paris, 2018).

As organizations tend to have an internal network this ransomware is made to exploit the same
vulnerability of smb protocol thus can spread to other machines on the same network once
downloaded to a single machine of an organization.
vulnerability of smb protocol thus can spread to other machines on the same network once
downloaded to a single machine of an organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Anon, 2018. Microsoft Security Bulletin MS17-010 - Critical. [online] Docs.microsoft.com.
Available at: <https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2017/ms17-
010> [Accessed 25 Jul. 2018].
Anon, 2018. What is WannaCrypt ransomware, how does it work & how to stay safe. [online] The
Windows Club. Available at: <https://www.thewindowsclub.com/what-is-wannacrypt-
ransomware> [Accessed 25 Jul. 2018].
Fruhlinger, J., 2018. What is ransomware? How it works and how to remove it. [online] CSO
Online. Available at: <https://www.csoonline.com/article/3236183/ransomware/what-is-
ransomware-how-it-works-and-how-to-remove-it.html> [Accessed 25 Jul. 2018].
Nick Kostov in Paris, J., 2018. Cyberattack Victims Begin to Assess Financial Damage. [online]
WSJ. Available at: <https://www.wsj.com/articles/cyberattack-spreads-though-at-slower-pace-
1494835536?mod=e2tweu> [Accessed 25 Jul. 2018].
Richter, F., 2018. Infographic: 200,000+ Systems Affected by WannaCry Ransom Attack. [online]
Statista Infographics. Available at: <https://www.statista.com/chart/9399/wannacry-cyber-attack-
in-numbers/> [Accessed 25 Jul. 2018].
Anon, 2018. Microsoft Security Bulletin MS17-010 - Critical. [online] Docs.microsoft.com.
Available at: <https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2017/ms17-
010> [Accessed 25 Jul. 2018].
Anon, 2018. What is WannaCrypt ransomware, how does it work & how to stay safe. [online] The
Windows Club. Available at: <https://www.thewindowsclub.com/what-is-wannacrypt-
ransomware> [Accessed 25 Jul. 2018].
Fruhlinger, J., 2018. What is ransomware? How it works and how to remove it. [online] CSO
Online. Available at: <https://www.csoonline.com/article/3236183/ransomware/what-is-
ransomware-how-it-works-and-how-to-remove-it.html> [Accessed 25 Jul. 2018].
Nick Kostov in Paris, J., 2018. Cyberattack Victims Begin to Assess Financial Damage. [online]
WSJ. Available at: <https://www.wsj.com/articles/cyberattack-spreads-though-at-slower-pace-
1494835536?mod=e2tweu> [Accessed 25 Jul. 2018].
Richter, F., 2018. Infographic: 200,000+ Systems Affected by WannaCry Ransom Attack. [online]
Statista Infographics. Available at: <https://www.statista.com/chart/9399/wannacry-cyber-attack-
in-numbers/> [Accessed 25 Jul. 2018].
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




