Web Application Development Report: Functions, Design, Security
VerifiedAdded on 2020/01/28
|21
|6910
|331
Report
AI Summary
This report provides a comprehensive overview of web application development. It begins with an introduction to web applications, their functions, and advantages, followed by an exploration of server-side and client-side scripting languages, including PHP, Python, C++, HTML, CSS, and JavaScript. The report then delves into web security, discussing firewalls, encryption, and various threats like viruses, hacking, phishing, and credit card fraud, along with preventive measures. The core of the report covers designing a web application, synthesizing client-side and server-side functionality, and applying database design principles. It also addresses alternative designs and solutions. The report further discusses the implementation of web applications, including web-enabled database management systems and opportunities for error handling. The final sections focus on the review and testing of web applications, analyzing test results, evaluating feedback, and providing user documentation. The report emphasizes the importance of security, user experience, and efficient design in web application development.

Web Application
Development
Development
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................4
TASK 1............................................................................................................................................4
P1.1 Functions and advantages of web application.....................................................................4
P1.2 Different types of server-side and client-side scripting languages......................................6
P1.3 Web security........................................................................................................................7
TASK 2 ...........................................................................................................................................9
P2.1 Designing a web application ...............................................................................................9
P2.2 Synthesising client-side and server-side functionality......................................................11
P2.3 Applying database design..................................................................................................12
P2.4 Alternative designs and solutions......................................................................................13
TASK 3 .........................................................................................................................................13
P3.1 Implementation of web application...................................................................................13
P3.2 Implementing web-enabled database management system...............................................14
P3.3 Opportunities for error handling and reporting.................................................................15
TASK 4..........................................................................................................................................16
P4.1 Review and testing of web application..............................................................................16
P4.2 Actual test results analysis.................................................................................................17
P4.3 Evaluating independent feedback and providing recommendations.................................18
P4.4 User documentation...........................................................................................................18
CONCLUSION..............................................................................................................................19
REFERENCES..............................................................................................................................21
2
INTRODUCTION...........................................................................................................................4
TASK 1............................................................................................................................................4
P1.1 Functions and advantages of web application.....................................................................4
P1.2 Different types of server-side and client-side scripting languages......................................6
P1.3 Web security........................................................................................................................7
TASK 2 ...........................................................................................................................................9
P2.1 Designing a web application ...............................................................................................9
P2.2 Synthesising client-side and server-side functionality......................................................11
P2.3 Applying database design..................................................................................................12
P2.4 Alternative designs and solutions......................................................................................13
TASK 3 .........................................................................................................................................13
P3.1 Implementation of web application...................................................................................13
P3.2 Implementing web-enabled database management system...............................................14
P3.3 Opportunities for error handling and reporting.................................................................15
TASK 4..........................................................................................................................................16
P4.1 Review and testing of web application..............................................................................16
P4.2 Actual test results analysis.................................................................................................17
P4.3 Evaluating independent feedback and providing recommendations.................................18
P4.4 User documentation...........................................................................................................18
CONCLUSION..............................................................................................................................19
REFERENCES..............................................................................................................................21
2

ILLUSTRATION INDEX
Illustration 1: Standard layout of a web application........................................................................9
3
Illustration 1: Standard layout of a web application........................................................................9
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Internet is perceived as an open library for collecting information from any part of the
world at any time. The medium through which this data is published is a website or a modified
form that is web application. Business organisations have evolved their marketing strategies by
developing platforms that help in easy transfer of information. Apps can be used across various
devices and operating system depending on their compilation procedure. Languages that are
commonly used for web application development are HTML, CSS or JavaScript. Despite of
these many uses and advantages, it is essential that complete system is secure and functions
smoothly without interruptions from external environment. This report is based on basic
knowledge required for web app.
With help of a developed website, one can achieve the aim of this report which is to
provide specific information regarding various aspects of a web application. The different
languages that are involved while developing client side and server side are also described. Basic
need of technology is to make human work much more simpler and managed. Hence, database
management system will be implemented which is continued by proper evaluation of complete
design output.
TASK 1
P1.1 Functions and advantages of web application
Web application is a computer based software program that is stored in a web server and
accessed by an internet based web browser. It is a modified form of a website. With growing
advancements in internet technology and smartphones, certain interfaces have to be developed in
such a manner that people can access them even without an internet connection. Such platforms
are web applications (Atzori, Iera and Morabito, 2010). Most of these information media are
valid for smartphones that have operating systems like Android, IOS and Windows.
Omnipresence of web applications can be felt very well in 21st century. People are able to
perform their minute tasks with great ease through these applications also known as apps. Web
application development is technique that is used for enhancing web platforms (Bal, 2013).
Functions of Web Application
4
Internet is perceived as an open library for collecting information from any part of the
world at any time. The medium through which this data is published is a website or a modified
form that is web application. Business organisations have evolved their marketing strategies by
developing platforms that help in easy transfer of information. Apps can be used across various
devices and operating system depending on their compilation procedure. Languages that are
commonly used for web application development are HTML, CSS or JavaScript. Despite of
these many uses and advantages, it is essential that complete system is secure and functions
smoothly without interruptions from external environment. This report is based on basic
knowledge required for web app.
With help of a developed website, one can achieve the aim of this report which is to
provide specific information regarding various aspects of a web application. The different
languages that are involved while developing client side and server side are also described. Basic
need of technology is to make human work much more simpler and managed. Hence, database
management system will be implemented which is continued by proper evaluation of complete
design output.
TASK 1
P1.1 Functions and advantages of web application
Web application is a computer based software program that is stored in a web server and
accessed by an internet based web browser. It is a modified form of a website. With growing
advancements in internet technology and smartphones, certain interfaces have to be developed in
such a manner that people can access them even without an internet connection. Such platforms
are web applications (Atzori, Iera and Morabito, 2010). Most of these information media are
valid for smartphones that have operating systems like Android, IOS and Windows.
Omnipresence of web applications can be felt very well in 21st century. People are able to
perform their minute tasks with great ease through these applications also known as apps. Web
application development is technique that is used for enhancing web platforms (Bal, 2013).
Functions of Web Application
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Documentation and reporting of various statistical information can be performed
(Hebeler and et. al., 2011).
Businesses can develop their own web apps so that goods and commodities can be easily
purchased and tracked.
Education purposes are fulfilled. Tutorials and online classrooms are easily approached
through web apps.
Daily news and updates are given.
Remote organisational operations are performed online.
Web application helps in developing user profiles. People can visualise their activities
and functions when they use the user profile option. They have the ability to customise
the themes and set up of a web application according to their needs and requirements. Online shopping is an increasing function of web applications. Customers have direct
access to commodities which are sold by companies in their physical stores.
Advantages1. Cost effective: Environment given to users for using a web application is uniform and
similar. This reduces the manufacturing costs of these apps for different platforms. It is
just a one time development and execution.2. Easy access: The viability and usability of these platforms increases due to high
accessibility over various devices. Once an app is registered for a user, he/she can derive
all their information on any other platform by entering respective credentials (Charland
and Leroux, 2011).3. Customisable: People can customise and change their preferences for layout and look of a
web application. This feature helps in gathering more audience.4. Device restrictions are less: Content that has been formulated for a web app can be
customised and connected to any device. It doesn't demand much complex compatibility
features.5. Effortless installation and maintenance: Complications related to installation and
maintenance are minimum. The web server doesn't require to upgrade the software for
every user. Once installed, it runs smoothly for all future customers.
Disadvantages
5
(Hebeler and et. al., 2011).
Businesses can develop their own web apps so that goods and commodities can be easily
purchased and tracked.
Education purposes are fulfilled. Tutorials and online classrooms are easily approached
through web apps.
Daily news and updates are given.
Remote organisational operations are performed online.
Web application helps in developing user profiles. People can visualise their activities
and functions when they use the user profile option. They have the ability to customise
the themes and set up of a web application according to their needs and requirements. Online shopping is an increasing function of web applications. Customers have direct
access to commodities which are sold by companies in their physical stores.
Advantages1. Cost effective: Environment given to users for using a web application is uniform and
similar. This reduces the manufacturing costs of these apps for different platforms. It is
just a one time development and execution.2. Easy access: The viability and usability of these platforms increases due to high
accessibility over various devices. Once an app is registered for a user, he/she can derive
all their information on any other platform by entering respective credentials (Charland
and Leroux, 2011).3. Customisable: People can customise and change their preferences for layout and look of a
web application. This feature helps in gathering more audience.4. Device restrictions are less: Content that has been formulated for a web app can be
customised and connected to any device. It doesn't demand much complex compatibility
features.5. Effortless installation and maintenance: Complications related to installation and
maintenance are minimum. The web server doesn't require to upgrade the software for
every user. Once installed, it runs smoothly for all future customers.
Disadvantages
5

Reliability towards internet is very high which makes it non-operational during low
connectivity situations.
Every company that establishes its own web application has a separate server. The
browsing speed for an app will be higher on servers than on other client base.
Security is often at risk when transferring data over an app. It has to be rendered for
improved usage.
P1.2 Different types of server-side and client-side scripting languages
Server-side scripting: Every web page has to be present on a platform that is called
server. All applications and pages are being circulated through servers. The complete process of
interpretation of codes and then execution at user end is performed by server side scripting.
Major languages that are used in this part of development are HTML, ASP, JSP, Perl, Ruby, etc.
The web server plays an important role in delivering data to users. Every potential web
application must have a strong server side scripting (Chess and et. al., 2011). Server side
scripting can be static and dynamic depending on the level and usage of that particular web
application . Static websites do not involve massive user interaction. They are merely a page that
is opened on customer's end so that they can read and grab data. HTML is widely used for all
server side protocols and actions because it is easy to use and execute with better understanding.
The company has used three server side scripting languages that is PHP, Python and C+
+. Since, entire processing and creation of the project is processed in server-side, the developers
must be skilled with these languages.
Client-side scripting: Computer programming is the heart of every web application. This
function is based on concept of dynamism which enables web pages to be scripted and changed
according to manufacturer's convenience (O'connell and Walker, 2010.). This scripting is a set of
instructions that has to be given to user computer with help of a web server. It is accomplishment
of user requests in scripting form which is then interpreted with help of server side. Execution of
web application is not possible without help of both scripting sides. Languages that are majorly
used in client side scripting are HTML or XHTML(Extensible Hypertext Markup Language).
These are often referred to as external scripting language. Internal script may be based on CSS or
JavaScript. Web application will be developed with client side scripting based on use of HTML,
CSS and Javascript.
6
connectivity situations.
Every company that establishes its own web application has a separate server. The
browsing speed for an app will be higher on servers than on other client base.
Security is often at risk when transferring data over an app. It has to be rendered for
improved usage.
P1.2 Different types of server-side and client-side scripting languages
Server-side scripting: Every web page has to be present on a platform that is called
server. All applications and pages are being circulated through servers. The complete process of
interpretation of codes and then execution at user end is performed by server side scripting.
Major languages that are used in this part of development are HTML, ASP, JSP, Perl, Ruby, etc.
The web server plays an important role in delivering data to users. Every potential web
application must have a strong server side scripting (Chess and et. al., 2011). Server side
scripting can be static and dynamic depending on the level and usage of that particular web
application . Static websites do not involve massive user interaction. They are merely a page that
is opened on customer's end so that they can read and grab data. HTML is widely used for all
server side protocols and actions because it is easy to use and execute with better understanding.
The company has used three server side scripting languages that is PHP, Python and C+
+. Since, entire processing and creation of the project is processed in server-side, the developers
must be skilled with these languages.
Client-side scripting: Computer programming is the heart of every web application. This
function is based on concept of dynamism which enables web pages to be scripted and changed
according to manufacturer's convenience (O'connell and Walker, 2010.). This scripting is a set of
instructions that has to be given to user computer with help of a web server. It is accomplishment
of user requests in scripting form which is then interpreted with help of server side. Execution of
web application is not possible without help of both scripting sides. Languages that are majorly
used in client side scripting are HTML or XHTML(Extensible Hypertext Markup Language).
These are often referred to as external scripting language. Internal script may be based on CSS or
JavaScript. Web application will be developed with client side scripting based on use of HTML,
CSS and Javascript.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Comparison:
There are three situations that can take place when considering information transfer.
These are client to client, client to server and server to server. The nature and mode of transfer is
totally different in all three cases. In client to client protocol, there is exchange of files. A DCC
connection that is direct client to client connection is established which is used for sharing
individual files. On the contrary, client to server is network where users provide a request to the
server. This request is related to web application like searching or opening a page.
Distinctly, the server to server connection is completely different from the above two
types. It is internally used by companies to get analytical data about what amount of installs and
visits have been created for a particular web page. All these three functions are interlinked but
their nature of functioning is different.
P1.3 Web security
With comfort and reliance, comes security. It is essential for every web application to be
secure and safe so that no credentials are lost to fraudster advantages. Web application security is
ensured by information technology software that take care of security and protection of web
services. Hackers are always in search of an opportunity where they can detect a flaw in a
particular website (Kothari, Le and Nydegger, 2010.). Threats like misuse of user data, money
laundering, compromise in network services are faced by web apps. Network security is ensured
by firewall software and encryptions.
Preventive measures for making a web experience more secure and authentic is through
network security. Client side scripting is crucial and most valuable data. The infrastructure is
build on this end. Firewalls control the incoming and outgoing data over the server (Akhawe and
et. al., 2010). Certain security rules have been established by firewall settings which control the
flow of information. Belonging to internal structure of a web application, Firewall is only
accessible by some encryptions.
Encryptions help in making the route of data transfer secure and approachable by only
user and client. It cannot be accessed by third parities or external users. Internet is used by all
types of users. It is most unsafe and insecure platform for data sharing. But firewall encryption
enables good flow of information both internally and externally (Katkar and Kulkarni 2012).
The security standards body that has been functioning currently is OWASP(Open Web
7
There are three situations that can take place when considering information transfer.
These are client to client, client to server and server to server. The nature and mode of transfer is
totally different in all three cases. In client to client protocol, there is exchange of files. A DCC
connection that is direct client to client connection is established which is used for sharing
individual files. On the contrary, client to server is network where users provide a request to the
server. This request is related to web application like searching or opening a page.
Distinctly, the server to server connection is completely different from the above two
types. It is internally used by companies to get analytical data about what amount of installs and
visits have been created for a particular web page. All these three functions are interlinked but
their nature of functioning is different.
P1.3 Web security
With comfort and reliance, comes security. It is essential for every web application to be
secure and safe so that no credentials are lost to fraudster advantages. Web application security is
ensured by information technology software that take care of security and protection of web
services. Hackers are always in search of an opportunity where they can detect a flaw in a
particular website (Kothari, Le and Nydegger, 2010.). Threats like misuse of user data, money
laundering, compromise in network services are faced by web apps. Network security is ensured
by firewall software and encryptions.
Preventive measures for making a web experience more secure and authentic is through
network security. Client side scripting is crucial and most valuable data. The infrastructure is
build on this end. Firewalls control the incoming and outgoing data over the server (Akhawe and
et. al., 2010). Certain security rules have been established by firewall settings which control the
flow of information. Belonging to internal structure of a web application, Firewall is only
accessible by some encryptions.
Encryptions help in making the route of data transfer secure and approachable by only
user and client. It cannot be accessed by third parities or external users. Internet is used by all
types of users. It is most unsafe and insecure platform for data sharing. But firewall encryption
enables good flow of information both internally and externally (Katkar and Kulkarni 2012).
The security standards body that has been functioning currently is OWASP(Open Web
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Application Security Project). It works as a community that provides guidelines and instructions
for creating a safe environment over the internet. After emergence of this body, certain secure
websites have devised a generic agreement which appears every time a person accesses those
websites or apps.
Encryption allows the transfer of data in coded format. It can be decoded only at the other
end of communication. For example, a person requests a company website to show the products
and services it has been giving to customers. This request will be processed under encrypted
code which can be decoded at company server's end. If third party interventions are observed
then, firewall gets activated and no loss of data is observed (Matbouli and Gao, 2012).
Information regarding details of customer and company is to be secured from hackers and
intruders. There are various tools and techniques that can be utilised for improving web security.
Frauds can be in any form. Credit fraud, phishing, hacking, virus attack, etc. Virus attack: Malicious software often gets addressed in some servers and computer
networks that are not encrypted and protected. This software is called as computer virus.
Some of the most common viruses are trojan horses, keyloggers, worms, ransomware,
etc. These are used as a tool to deplete computer functions and disrupt company's
functioning. It also helps in getting private information from receiving side through virus
attacks. Hacking: The process in which a person breaches security features of a network and
takes away all important data for his/her personal use is hacking. Hacking is a cyber
crime and is mainly intended to steal profits and money. Phishing: Email marketing is rapidly increasing. Fraudsters and intruders take this as an
opportunity to obtain private information of targeted person. Phishing is known as this
practise of fraud emails in the name of reputed companies. It is also known as email
spoofing.
Credit Fraud: Credit cards have emerged as an increasing medium for transactions.
Intruders explore this opportunity and transact money from consumers by getting detailed
information about their credit cards.
Apart from encryption and firewall settings, there are some other tools that can be used
for minimising these problems and dangers. Some of them are discusses below:
8
for creating a safe environment over the internet. After emergence of this body, certain secure
websites have devised a generic agreement which appears every time a person accesses those
websites or apps.
Encryption allows the transfer of data in coded format. It can be decoded only at the other
end of communication. For example, a person requests a company website to show the products
and services it has been giving to customers. This request will be processed under encrypted
code which can be decoded at company server's end. If third party interventions are observed
then, firewall gets activated and no loss of data is observed (Matbouli and Gao, 2012).
Information regarding details of customer and company is to be secured from hackers and
intruders. There are various tools and techniques that can be utilised for improving web security.
Frauds can be in any form. Credit fraud, phishing, hacking, virus attack, etc. Virus attack: Malicious software often gets addressed in some servers and computer
networks that are not encrypted and protected. This software is called as computer virus.
Some of the most common viruses are trojan horses, keyloggers, worms, ransomware,
etc. These are used as a tool to deplete computer functions and disrupt company's
functioning. It also helps in getting private information from receiving side through virus
attacks. Hacking: The process in which a person breaches security features of a network and
takes away all important data for his/her personal use is hacking. Hacking is a cyber
crime and is mainly intended to steal profits and money. Phishing: Email marketing is rapidly increasing. Fraudsters and intruders take this as an
opportunity to obtain private information of targeted person. Phishing is known as this
practise of fraud emails in the name of reputed companies. It is also known as email
spoofing.
Credit Fraud: Credit cards have emerged as an increasing medium for transactions.
Intruders explore this opportunity and transact money from consumers by getting detailed
information about their credit cards.
Apart from encryption and firewall settings, there are some other tools that can be used
for minimising these problems and dangers. Some of them are discusses below:
8

VPN: Virtual Private network is a security management tool which enables users to
create a private network over a public or maximum users network. VPN can be used with
help of internet for secure transfer of information and disabling virus attack. Public key: Cryptographic techniques are used for enabling public key. A key generation
program is initiated which provides a public key and a private key. The rights for
accessing these keys is limited to owners only.
Symmetric key and asymmetric key : Symmetric keys are a type of algorithm which is
initiated to secure information of a defined and confined network. Stream ciphers and
block ciphers are certain types of symmetric keys. On the other hand, asymmetric keys
are a pair of public and private keys. It means that when transfer of information takes
place between a public user and private user then asymmetric key algorithms are
initiated.
TASK 2
P2.1 Designing a web application
Web application is an easier approach of companies to gain maximum customers. Certain
specific rules have to be followed for achieving a good user interactive portal.
Reinvention of new patterns must be prohibited or avoided. Users get adapted to
functions and platforms that are quick and easy (Pan, Xiao and Lu, 2010). If same
operating system gets upgraded by engaging into new working techniques then threats of
substitution by other platforms will increase. Hence, design must be based on common
principles and similar working patterns.
Grouping or menu drops must be customised in such a manner that information or
guidelines regarding usage are clearly depicted without any complications.
Communication must be effective. It is important that proposed design is able to
communicate the purpose and objective of company (Erdogan, Meland and Mathieson,
2010). This includes deployment of good scenarios.
Catching and output buffering are a must so that once the web application is installed on
a device then no round trips are made towards web browser and downlink servers. Catch
remains to internal part of software and is a form of temporary data storage.
9
create a private network over a public or maximum users network. VPN can be used with
help of internet for secure transfer of information and disabling virus attack. Public key: Cryptographic techniques are used for enabling public key. A key generation
program is initiated which provides a public key and a private key. The rights for
accessing these keys is limited to owners only.
Symmetric key and asymmetric key : Symmetric keys are a type of algorithm which is
initiated to secure information of a defined and confined network. Stream ciphers and
block ciphers are certain types of symmetric keys. On the other hand, asymmetric keys
are a pair of public and private keys. It means that when transfer of information takes
place between a public user and private user then asymmetric key algorithms are
initiated.
TASK 2
P2.1 Designing a web application
Web application is an easier approach of companies to gain maximum customers. Certain
specific rules have to be followed for achieving a good user interactive portal.
Reinvention of new patterns must be prohibited or avoided. Users get adapted to
functions and platforms that are quick and easy (Pan, Xiao and Lu, 2010). If same
operating system gets upgraded by engaging into new working techniques then threats of
substitution by other platforms will increase. Hence, design must be based on common
principles and similar working patterns.
Grouping or menu drops must be customised in such a manner that information or
guidelines regarding usage are clearly depicted without any complications.
Communication must be effective. It is important that proposed design is able to
communicate the purpose and objective of company (Erdogan, Meland and Mathieson,
2010). This includes deployment of good scenarios.
Catching and output buffering are a must so that once the web application is installed on
a device then no round trips are made towards web browser and downlink servers. Catch
remains to internal part of software and is a form of temporary data storage.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
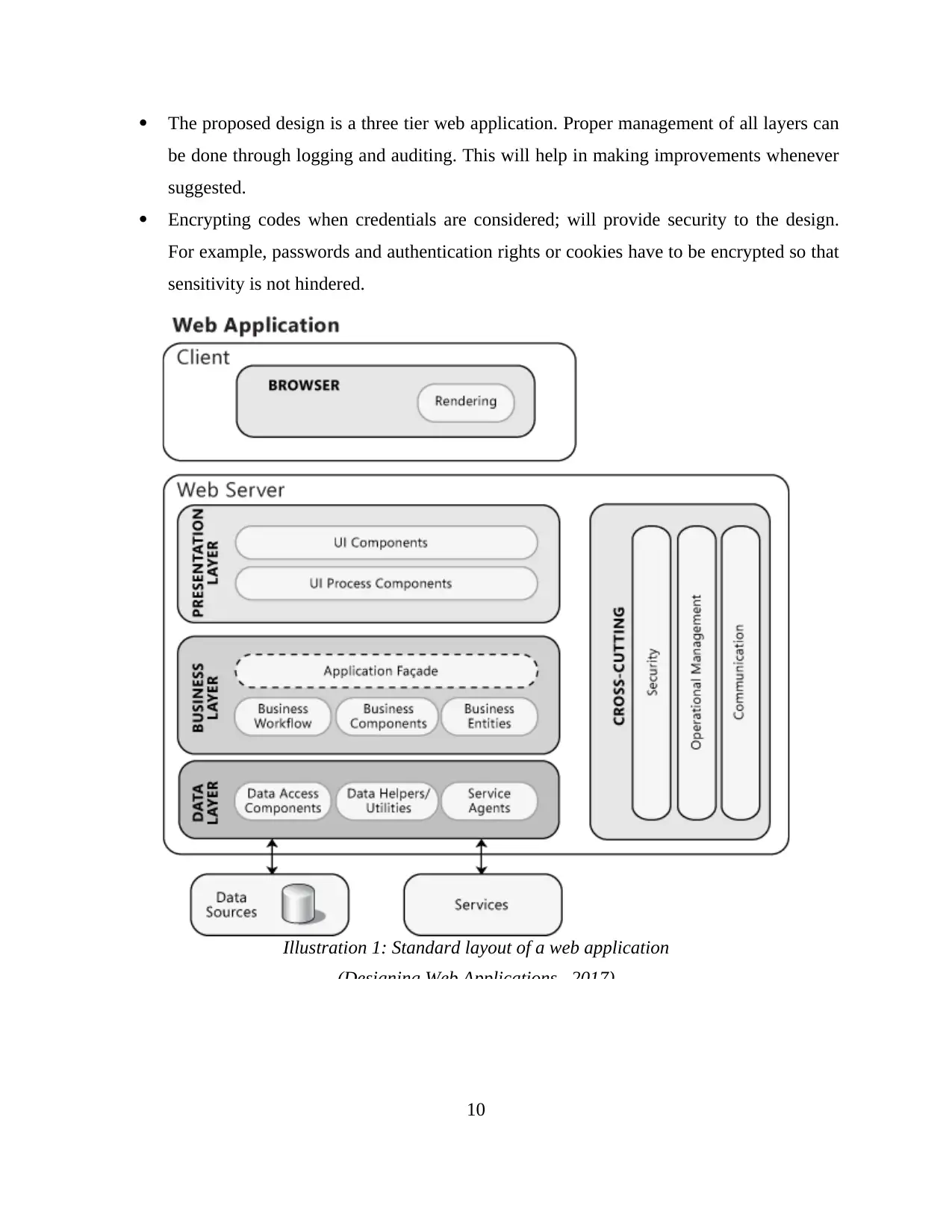
The proposed design is a three tier web application. Proper management of all layers can
be done through logging and auditing. This will help in making improvements whenever
suggested.
Encrypting codes when credentials are considered; will provide security to the design.
For example, passwords and authentication rights or cookies have to be encrypted so that
sensitivity is not hindered.
10
Illustration 1: Standard layout of a web application
(Designing Web Applications, 2017)
be done through logging and auditing. This will help in making improvements whenever
suggested.
Encrypting codes when credentials are considered; will provide security to the design.
For example, passwords and authentication rights or cookies have to be encrypted so that
sensitivity is not hindered.
10
Illustration 1: Standard layout of a web application
(Designing Web Applications, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P2.2 Synthesising client-side and server-side functionality
Architectural design or layout once made has to be synthesised with help of proper codes
and scripts so that end result is similar to the one that is proposed on rough design. Client-side
and server-side scripting is performed as second stage of development process. The client-side
servers are like source generators (Taivalsaari and Mikkonen, 2011). Instructions are formulated
from this end and given to server-side. An interpreter is already installed on servers so that
instructions can be compiled and user demands can be successfully met. Functionality is checked
once a code is executed. Errors are likely to appear after execution. This has to be resolved at
client-end itself. To avoid future consequences, every company provides a development time
period so that users don't find it difficult while interacting.
Server-side functionality is complete responsibility of host server which is assigned by
company for particular regions. Asynchronous messages that are sent by client side are received
at this end. The presence of server-side code helps in creating a dynamic environment between
client and server. Users do not directly interact with clients (Garrett, 2010). This is an
advantageous situation to change and improve internal architecture of web application.
Integration is performed once codes are generated. This step provides a client augmentation
which provides servers information regarding errors.
P2.3 Applying database design
MySQL database can be applied for developing simpler methodologies of web app. Once
the application goes live on internet, then users will fill in their data and credentials. This
information needs to be managed and classified so that chaos is not created when bulk collection
is achieved. Database Management Systems or DBMS is applied to web apps for scaling robust
data efficiently (Satzinger, Jackson and Burd, 2011). The DBMS software that easily integrates
with the coding structure of an app is MySQL community server. This tool has interactive
graphic user interface and is compatible with most operating systems, especially Linux.
Microsoft Access is also a famous tool that can be used for application in DBMS but the
drawback it carries with itself is high purchasing costs. Moreover, flexibility is less with this
software.
Interfaces that are build in an application must be efficient to easily handle bulk data at
every instant (Paterno, 2012). For example, a company launches its app of an online clothing
11
Architectural design or layout once made has to be synthesised with help of proper codes
and scripts so that end result is similar to the one that is proposed on rough design. Client-side
and server-side scripting is performed as second stage of development process. The client-side
servers are like source generators (Taivalsaari and Mikkonen, 2011). Instructions are formulated
from this end and given to server-side. An interpreter is already installed on servers so that
instructions can be compiled and user demands can be successfully met. Functionality is checked
once a code is executed. Errors are likely to appear after execution. This has to be resolved at
client-end itself. To avoid future consequences, every company provides a development time
period so that users don't find it difficult while interacting.
Server-side functionality is complete responsibility of host server which is assigned by
company for particular regions. Asynchronous messages that are sent by client side are received
at this end. The presence of server-side code helps in creating a dynamic environment between
client and server. Users do not directly interact with clients (Garrett, 2010). This is an
advantageous situation to change and improve internal architecture of web application.
Integration is performed once codes are generated. This step provides a client augmentation
which provides servers information regarding errors.
P2.3 Applying database design
MySQL database can be applied for developing simpler methodologies of web app. Once
the application goes live on internet, then users will fill in their data and credentials. This
information needs to be managed and classified so that chaos is not created when bulk collection
is achieved. Database Management Systems or DBMS is applied to web apps for scaling robust
data efficiently (Satzinger, Jackson and Burd, 2011). The DBMS software that easily integrates
with the coding structure of an app is MySQL community server. This tool has interactive
graphic user interface and is compatible with most operating systems, especially Linux.
Microsoft Access is also a famous tool that can be used for application in DBMS but the
drawback it carries with itself is high purchasing costs. Moreover, flexibility is less with this
software.
Interfaces that are build in an application must be efficient to easily handle bulk data at
every instant (Paterno, 2012). For example, a company launches its app of an online clothing
11

store and publishes it to all citizens of UK. With growing publicity and awareness of the
company, audience will increase. This implies more number of users will be able to shop and
track their orders. Being a transactional website, real time interaction will be prominent for
clients. Application of DBMS will help in dealing with these situations. It is mandatory to
involve database so that electronic records can be maintained (Tidwell, 2010). It not only helps
in gathering information about users but also tracks company's movements. If app is subjected to
hacking conditions then, detection of offender becomes easy. Several options like cloud
computing and Big data; which are technological tools for data handling and storage can also be
linked with host servers.
P2.4 Alternative designs and solutions
Designs that are adopted for development of websites into applications must be simple
and easy to operate. Sophistication is an important feature of successful applications. Consumers
are very specific in their choices for professional and sophisticated designs. Colour layout and
minimum layer architecture is the heart of every website. Simple approach to elements makes it
easy for coders to generate codes (Paterno, 2012). Choices must be present but not in vast
number. This creates a lot of confusion and chaos in minds of users.
Technology like hide and conceal can e adopted as a better solution for design. It works
as an elaborative menu bar when mouse is placed on that particular header. It creates
more space and lessens stress over eyes.
Specialised controls can be introduced so that situational handling is best executed. For
example, sliders for navigation and click and drag buttons in search options. This gives
users better hold over little situations.
Disabling pressed buttons is a must to be included in design. Often applications encounter
a problem that is based on submission of forms. Slow loading speeds enable users to
submit particular data twice or thrice. This can be solved by disabling buttons that are
pressed one until result is not depicted (Hubbard and et. al., 2011). This will increase
working efficiency of the project.
Search data must be sensitive to content so that users get desired results for their filled
context.
12
company, audience will increase. This implies more number of users will be able to shop and
track their orders. Being a transactional website, real time interaction will be prominent for
clients. Application of DBMS will help in dealing with these situations. It is mandatory to
involve database so that electronic records can be maintained (Tidwell, 2010). It not only helps
in gathering information about users but also tracks company's movements. If app is subjected to
hacking conditions then, detection of offender becomes easy. Several options like cloud
computing and Big data; which are technological tools for data handling and storage can also be
linked with host servers.
P2.4 Alternative designs and solutions
Designs that are adopted for development of websites into applications must be simple
and easy to operate. Sophistication is an important feature of successful applications. Consumers
are very specific in their choices for professional and sophisticated designs. Colour layout and
minimum layer architecture is the heart of every website. Simple approach to elements makes it
easy for coders to generate codes (Paterno, 2012). Choices must be present but not in vast
number. This creates a lot of confusion and chaos in minds of users.
Technology like hide and conceal can e adopted as a better solution for design. It works
as an elaborative menu bar when mouse is placed on that particular header. It creates
more space and lessens stress over eyes.
Specialised controls can be introduced so that situational handling is best executed. For
example, sliders for navigation and click and drag buttons in search options. This gives
users better hold over little situations.
Disabling pressed buttons is a must to be included in design. Often applications encounter
a problem that is based on submission of forms. Slow loading speeds enable users to
submit particular data twice or thrice. This can be solved by disabling buttons that are
pressed one until result is not depicted (Hubbard and et. al., 2011). This will increase
working efficiency of the project.
Search data must be sensitive to content so that users get desired results for their filled
context.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
