SIT182 Deakin University: Cybersecurity Vulnerability Analysis Report
VerifiedAdded on 2023/04/22
|21
|2342
|83
Report
AI Summary
This report details the analysis of various web application vulnerabilities, including information leakage, directory traversal, weak encryption, cookie manipulation, and SQL injection. The project aims to demonstrate the process of identifying and exploiting these vulnerabilities in a controlled environment, using tools like Burp Suite and techniques like examining page source code and manipulating URL parameters. The report provides observations, screenshots, and recommendations for each vulnerability, emphasizing the importance of secure coding practices and robust security measures to prevent unauthorized access and data breaches. The assessment was conducted as part of the SIT182 Real World Practices for Cybersecurity course at Deakin University.
IT Write Up
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.................................................................................................................................2
2. information Leakages..................................................................................................................2
2.1 Description..................................................................................................................................2
2.2 Observation.................................................................................................................................2
2.3 Screenshots.................................................................................................................................3
2.4 Recommendation........................................................................................................................4
3. Directory Traversal.....................................................................................................................5
3.1Description...................................................................................................................................5
3.2 Observation.................................................................................................................................5
3.3 Screen shots................................................................................................................................6
3.4 Recommendation:.......................................................................................................................7
4. Weak encryption..........................................................................................................................7
4.1 Description..................................................................................................................................7
4.2 Observation.................................................................................................................................8
4.3 Screenshots.................................................................................................................................8
4.4 Recommendation......................................................................................................................10
5. Cookie manipulation.................................................................................................................10
5.1 Description.................................................................................................................................10
5.2 Screen shots...............................................................................................................................11
5.3 Recommendation......................................................................................................................12
6. SQL injection.............................................................................................................................13
6.1 Description.................................................................................................................................13
6.2 Observation...............................................................................................................................13
6.3 Recommendation......................................................................................................................20
7. Conclusion..................................................................................................................................20
References..........................................................................................................................................21
1. Introduction.................................................................................................................................2
2. information Leakages..................................................................................................................2
2.1 Description..................................................................................................................................2
2.2 Observation.................................................................................................................................2
2.3 Screenshots.................................................................................................................................3
2.4 Recommendation........................................................................................................................4
3. Directory Traversal.....................................................................................................................5
3.1Description...................................................................................................................................5
3.2 Observation.................................................................................................................................5
3.3 Screen shots................................................................................................................................6
3.4 Recommendation:.......................................................................................................................7
4. Weak encryption..........................................................................................................................7
4.1 Description..................................................................................................................................7
4.2 Observation.................................................................................................................................8
4.3 Screenshots.................................................................................................................................8
4.4 Recommendation......................................................................................................................10
5. Cookie manipulation.................................................................................................................10
5.1 Description.................................................................................................................................10
5.2 Screen shots...............................................................................................................................11
5.3 Recommendation......................................................................................................................12
6. SQL injection.............................................................................................................................13
6.1 Description.................................................................................................................................13
6.2 Observation...............................................................................................................................13
6.3 Recommendation......................................................................................................................20
7. Conclusion..................................................................................................................................20
References..........................................................................................................................................21

1. Introduction
The main aim of this project to develop the crack some passwords on different levels of a
website. The implementing the project we can used for the ten levels that are includes are
cryptography, directory traversal, sql injection, malicious redirects, Burp suites, Nmap, session
management, information gathering, reporting.Postings are refreshed day by day and are utilized to
spread and encourage further web hacking. Practically day by day we read about another programmer
assault where website pages from trustworthy locales are contaminated with vindictive code. Site
hacking is an outcome from the selection of online advancements for leading amusements.HTTPS
does not prevent assailants from hacking a site, web server or system. It won't prevent an aggressor
from misusing programming vulnerabilities, animal driving your entrance controls or guarantee your
sites accessibility by moderating Distributed Denial of Services (DDOS) assaults.You can tell if a site
is a "safe" one in the event that it has "https" in its URL and has a little bolt image by it. SSL, or
Secure Sockets Layer, is the innovation behind HTTPS. SSL makes a scrambled connection between
a site and your program which, in principle, guarantees that all information go between them stays
private it will be investigated.
2. Information Leakages
URL link:
https://www.hacksplaining.com/prevention/information-leakage
2.1 Description
The unapproved exchange of ordered data from a PC or server farm to the outside
world. Information spillage can be cultivated by just rationally recalling what was seen, by
physical evacuation of tapes, plates and reports or by inconspicuous methods, for example,
information concealing (see steganography).The are following the stages that are includes
are,
Step 1: Right click on the War Games home page
Step 2: Select: “View Page Source”
Step 3: View HTML code and look for credentials
Step 4: Credentials are highlighted in bold and coloured text
2.2 Observation
The main aim of this project to develop the crack some passwords on different levels of a
website. The implementing the project we can used for the ten levels that are includes are
cryptography, directory traversal, sql injection, malicious redirects, Burp suites, Nmap, session
management, information gathering, reporting.Postings are refreshed day by day and are utilized to
spread and encourage further web hacking. Practically day by day we read about another programmer
assault where website pages from trustworthy locales are contaminated with vindictive code. Site
hacking is an outcome from the selection of online advancements for leading amusements.HTTPS
does not prevent assailants from hacking a site, web server or system. It won't prevent an aggressor
from misusing programming vulnerabilities, animal driving your entrance controls or guarantee your
sites accessibility by moderating Distributed Denial of Services (DDOS) assaults.You can tell if a site
is a "safe" one in the event that it has "https" in its URL and has a little bolt image by it. SSL, or
Secure Sockets Layer, is the innovation behind HTTPS. SSL makes a scrambled connection between
a site and your program which, in principle, guarantees that all information go between them stays
private it will be investigated.
2. Information Leakages
URL link:
https://www.hacksplaining.com/prevention/information-leakage
2.1 Description
The unapproved exchange of ordered data from a PC or server farm to the outside
world. Information spillage can be cultivated by just rationally recalling what was seen, by
physical evacuation of tapes, plates and reports or by inconspicuous methods, for example,
information concealing (see steganography).The are following the stages that are includes
are,
Step 1: Right click on the War Games home page
Step 2: Select: “View Page Source”
Step 3: View HTML code and look for credentials
Step 4: Credentials are highlighted in bold and coloured text
2.2 Observation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The first is the truth that the tag-esteem mix "Content-Type: content/plain; charset="us-
ascii"" appears to for the most part be available in messages sent from an iPhone (default
customer) or customer; in 70% of messages with that tag, this was the situation. Content-
Type was additionally helpful in recognizing different clients. For example, we discovered
that the tag "Content-Type: content/plain; charset="ISO-8859-1"; format=flowed" just
happened with Thunderbird clients on Burp suite (McClure, Scambray & Kurtz, 2012). In
spite of the fact that not as telling, we were additionally ready to recognize circumstances
were frameworks were not being used. Two instances of such are shown with the header tag-
esteem mixes: "Content-Transfer-Encoding: 7bit" and "Content-Transfer-Encoding: cited
printable". In the previous case, we found that this blend just had all the earmarks of being
incorporated in messages not starting from the Windows working framework. In the last case,
none of the messages with this tag were from an Android-based gadget. Obviously, there
should be some alert with depending on these "not being used" results specifically given that
the extent of our example could have influenced our inclusion of these individual gatherings
groups.
2.3 Screenshots
ascii"" appears to for the most part be available in messages sent from an iPhone (default
customer) or customer; in 70% of messages with that tag, this was the situation. Content-
Type was additionally helpful in recognizing different clients. For example, we discovered
that the tag "Content-Type: content/plain; charset="ISO-8859-1"; format=flowed" just
happened with Thunderbird clients on Burp suite (McClure, Scambray & Kurtz, 2012). In
spite of the fact that not as telling, we were additionally ready to recognize circumstances
were frameworks were not being used. Two instances of such are shown with the header tag-
esteem mixes: "Content-Transfer-Encoding: 7bit" and "Content-Transfer-Encoding: cited
printable". In the previous case, we found that this blend just had all the earmarks of being
incorporated in messages not starting from the Windows working framework. In the last case,
none of the messages with this tag were from an Android-based gadget. Obviously, there
should be some alert with depending on these "not being used" results specifically given that
the extent of our example could have influenced our inclusion of these individual gatherings
groups.
2.3 Screenshots
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For the level 1 user name and password:
Username: Level1
Password: Domain
2.4 Recommendation
The propelled criteria for portraying information spillage occurrences show their
hugeness by giving an assortment of extra learning. Henceforth, these criteria are a
suggestion for specialists which need to build up future information misfortune warning
directions and IS measures.
Username: Level1
Password: Domain
2.4 Recommendation
The propelled criteria for portraying information spillage occurrences show their
hugeness by giving an assortment of extra learning. Henceforth, these criteria are a
suggestion for specialists which need to build up future information misfortune warning
directions and IS measures.

3. Directory Traversal
URL link:
http://ww1.vulnerable.com/
3.1Description
The catalog traversal/way traversal assault (otherwise called dab speck cut assault) is
a HTTP misuse that enables an assailant to get to limited documents, indexes and directions
that live outside the web server's root registry. Index traversal assaults are executed through
internet browsers. An aggressor may control a URL in such way that the site will uncover the
limited documents on the web server(Bae, Lim & Cho, 2016).Hacking circles has built up
this instructional exercise Directory Traversal Attacks (concentrating on a portion of the best
ten vulnerabilities). Commonly, web servers give two security components to limit client get
to:
Access Control Lists (ACLs)
URL link:
http://ww1.vulnerable.com/
3.1Description
The catalog traversal/way traversal assault (otherwise called dab speck cut assault) is
a HTTP misuse that enables an assailant to get to limited documents, indexes and directions
that live outside the web server's root registry. Index traversal assaults are executed through
internet browsers. An aggressor may control a URL in such way that the site will uncover the
limited documents on the web server(Bae, Lim & Cho, 2016).Hacking circles has built up
this instructional exercise Directory Traversal Attacks (concentrating on a portion of the best
ten vulnerabilities). Commonly, web servers give two security components to limit client get
to:
Access Control Lists (ACLs)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Web Document Root Directory
3.2 Observation
The aggressor needs to think about what number of registries to move so as to get to
the ideal catalog, however this should be possible effectively by means of experimentation.
For the live framework to disclose this powerlessness to clients utilizing a site page
server.The entrance control list figures out which clients or gatherings are special to get to,
adjust or execute records on the web server. Clients are confined from getting to the
particular piece of the record framework on the server, which is known as "root", "web
archive root", or "CGI root" catalog. The aggressor utilizes uncommon character
"../"grouping to escape web archive root, or interchange encoding of the "../" succession to
sidestep security channels and access records or registries that live outside the root index.
Some catalog traversal assault varieties include:
These methods utilize uncommon characters, for example, the dab (".") or NULL ("%00")
character muddle catalog traversal misuses. A catalog traversal powerlessness can exist
either in web servers or web applications. Web applications that neglect to approve input
parameters (for example frame parameters, values, and so on.) are powerless against catalog
traversal assaults.
3.3 Screen shots
For the level 2 user name and password:
Username: Level2
Password: Kernel
3.4 Recommendation:
3.2 Observation
The aggressor needs to think about what number of registries to move so as to get to
the ideal catalog, however this should be possible effectively by means of experimentation.
For the live framework to disclose this powerlessness to clients utilizing a site page
server.The entrance control list figures out which clients or gatherings are special to get to,
adjust or execute records on the web server. Clients are confined from getting to the
particular piece of the record framework on the server, which is known as "root", "web
archive root", or "CGI root" catalog. The aggressor utilizes uncommon character
"../"grouping to escape web archive root, or interchange encoding of the "../" succession to
sidestep security channels and access records or registries that live outside the root index.
Some catalog traversal assault varieties include:
These methods utilize uncommon characters, for example, the dab (".") or NULL ("%00")
character muddle catalog traversal misuses. A catalog traversal powerlessness can exist
either in web servers or web applications. Web applications that neglect to approve input
parameters (for example frame parameters, values, and so on.) are powerless against catalog
traversal assaults.
3.3 Screen shots
For the level 2 user name and password:
Username: Level2
Password: Kernel
3.4 Recommendation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For applications being effectively grown, such sifting and approval ought to be a
piece of the SDLC and designers or testing groups ought to be prepared to recognize and
avert such vulnerabilities.
4. Weak encryption
URL link:https://analysiscenter.veracode.com/j_security_check
4.1 Description
With all the web applications out on the web today, and particularly the ones
constructed and arranged by amateurs, it's anything but difficult to discover vulnerabilities.
Some are more dangerous than others, yet the results of even the scarcest rupture can be
colossal in the hands of a gifted programmer. Catalog traversal is a generally straightforward
assault yet can be utilized to uncover touchy data on a server.
4.2 Observation
Catalog traversal vulnerabilities can be found by testing HTTP solicitations,
structures, and treats, yet the most effortless approach to check whether an application is
powerless against this sort of assault is by essentially deciding whether a URL utilizes a GET
inquiry. A GET ask for contains the parameters straightforwardly in the URL link.
4.3 Screenshots
piece of the SDLC and designers or testing groups ought to be prepared to recognize and
avert such vulnerabilities.
4. Weak encryption
URL link:https://analysiscenter.veracode.com/j_security_check
4.1 Description
With all the web applications out on the web today, and particularly the ones
constructed and arranged by amateurs, it's anything but difficult to discover vulnerabilities.
Some are more dangerous than others, yet the results of even the scarcest rupture can be
colossal in the hands of a gifted programmer. Catalog traversal is a generally straightforward
assault yet can be utilized to uncover touchy data on a server.
4.2 Observation
Catalog traversal vulnerabilities can be found by testing HTTP solicitations,
structures, and treats, yet the most effortless approach to check whether an application is
powerless against this sort of assault is by essentially deciding whether a URL utilizes a GET
inquiry. A GET ask for contains the parameters straightforwardly in the URL link.
4.3 Screenshots
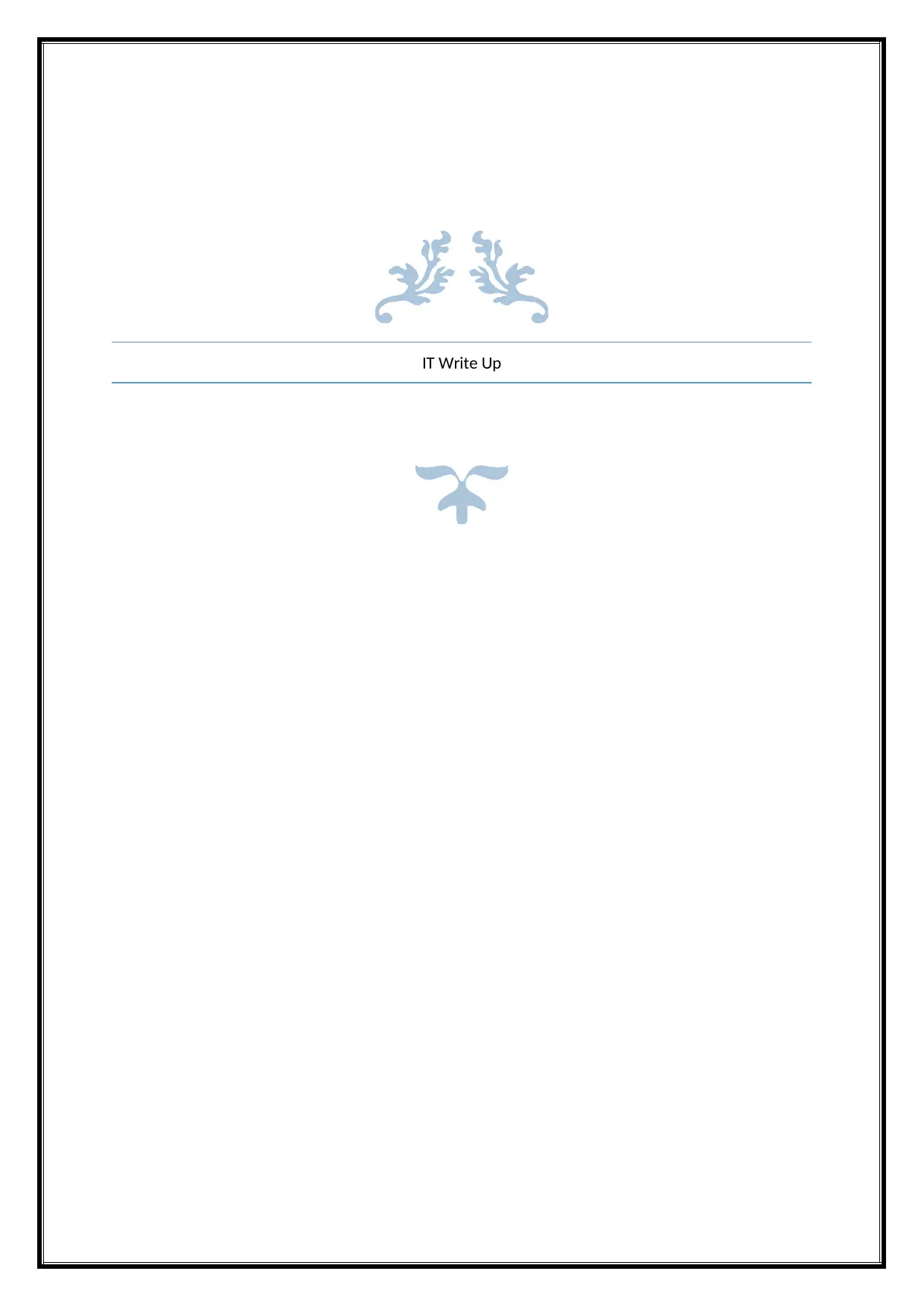
Level 3: username and password is,
Username: Level3
Password: Admin
4.4 Recommendation
Catalog traversal on other working frameworks works along these lines, yet there are
slight contrasts included.
5. Cookie manipulation
URL link :
https://portswigger.net/sc/owasp_accesscontrols_1.png
https://portswigger.net/sc/owasp_authcookies_3.png
5.1 Description
An essential comprehension of these dialects is required so as to totally comprehend
the ideas that are passed on thus. Notwithstanding an essential comprehension of the scripting
dialects that are used in this paper, the peruse ought to be respectably acquainted with the
structure and operations of web servers and web server sub-parts; that being stated, an
absence of information in these zones ought not hinder you from perusing on. The data
contained inside this report can, at any rate, furnish you with an essential comprehension of
effects of Directory Traversal assaults.
Username: Level3
Password: Admin
4.4 Recommendation
Catalog traversal on other working frameworks works along these lines, yet there are
slight contrasts included.
5. Cookie manipulation
URL link :
https://portswigger.net/sc/owasp_accesscontrols_1.png
https://portswigger.net/sc/owasp_authcookies_3.png
5.1 Description
An essential comprehension of these dialects is required so as to totally comprehend
the ideas that are passed on thus. Notwithstanding an essential comprehension of the scripting
dialects that are used in this paper, the peruse ought to be respectably acquainted with the
structure and operations of web servers and web server sub-parts; that being stated, an
absence of information in these zones ought not hinder you from perusing on. The data
contained inside this report can, at any rate, furnish you with an essential comprehension of
effects of Directory Traversal assaults.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
5.2 Screen shots
The level 4 user name and password
User name: Level 4
Password: Cookies
The level 5 user name and password
User name: Level 5
Password: auth cookies
The level 4 user name and password
User name: Level 4
Password: Cookies
The level 5 user name and password
User name: Level 5
Password: auth cookies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
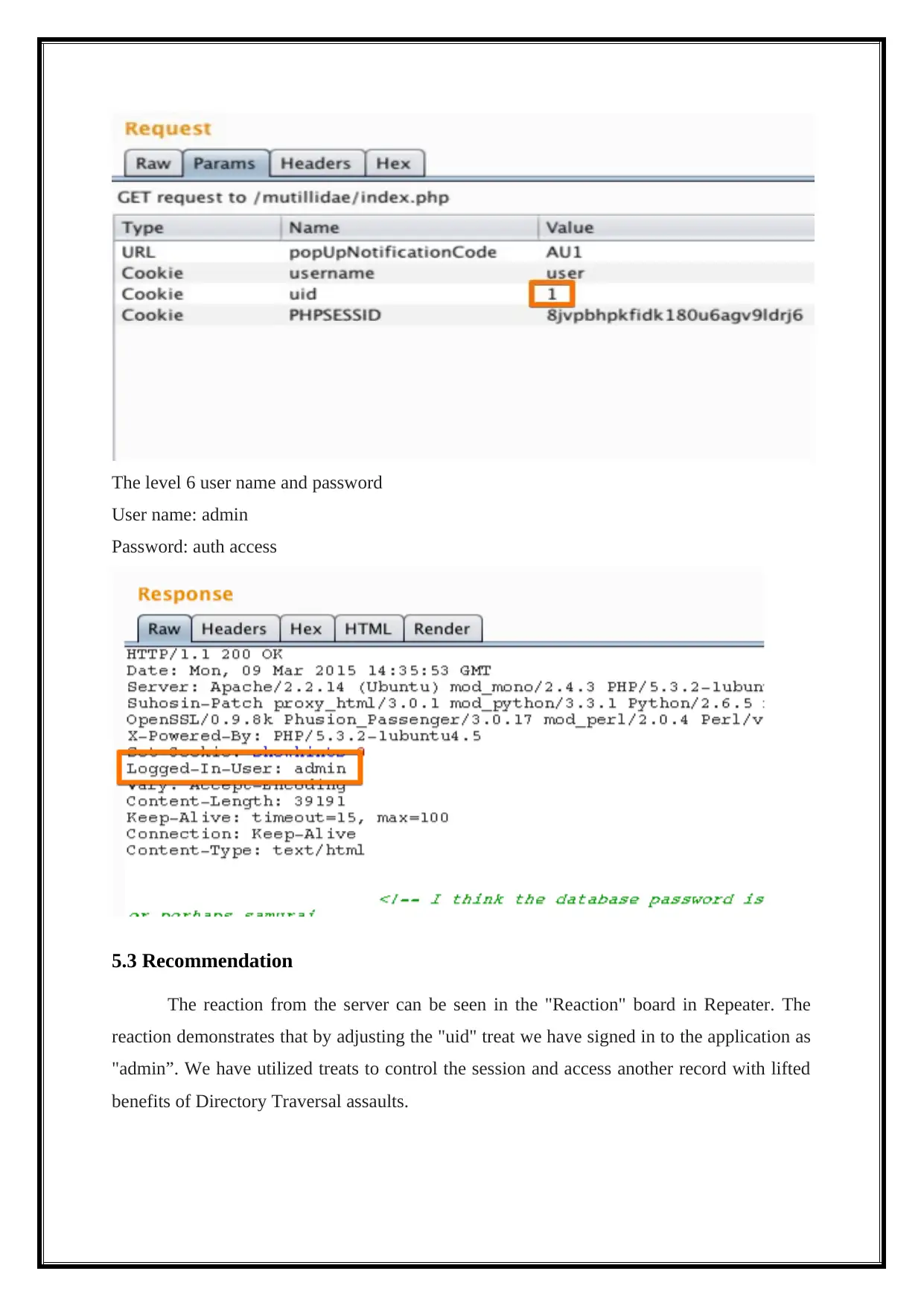
The level 6 user name and password
User name: admin
Password: auth access
5.3 Recommendation
The reaction from the server can be seen in the "Reaction" board in Repeater. The
reaction demonstrates that by adjusting the "uid" treat we have signed in to the application as
"admin”. We have utilized treats to control the session and access another record with lifted
benefits of Directory Traversal assaults.
User name: admin
Password: auth access
5.3 Recommendation
The reaction from the server can be seen in the "Reaction" board in Repeater. The
reaction demonstrates that by adjusting the "uid" treat we have signed in to the application as
"admin”. We have utilized treats to control the session and access another record with lifted
benefits of Directory Traversal assaults.
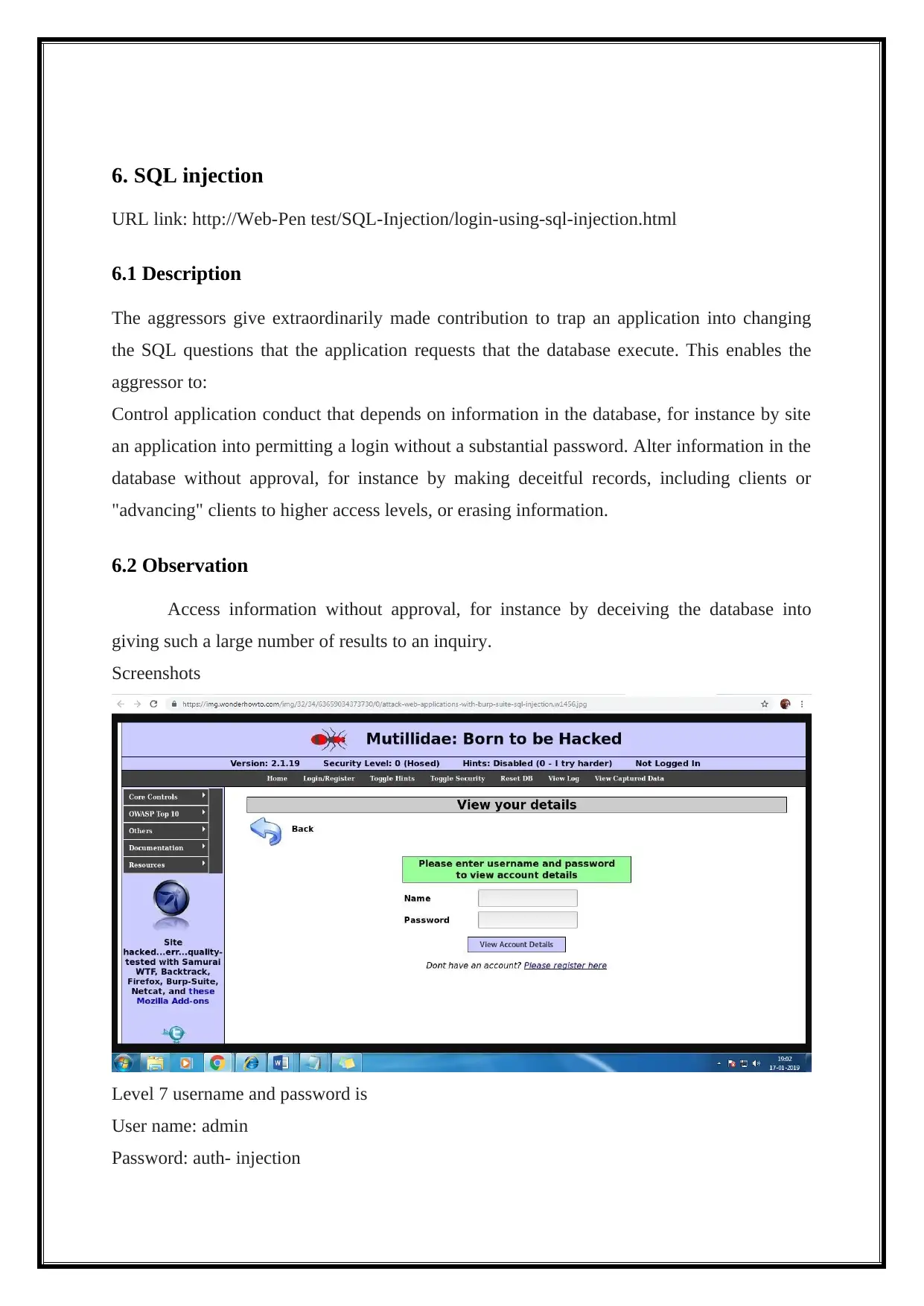
6. SQL injection
URL link: http://Web-Pen test/SQL-Injection/login-using-sql-injection.html
6.1 Description
The aggressors give extraordinarily made contribution to trap an application into changing
the SQL questions that the application requests that the database execute. This enables the
aggressor to:
Control application conduct that depends on information in the database, for instance by site
an application into permitting a login without a substantial password. Alter information in the
database without approval, for instance by making deceitful records, including clients or
"advancing" clients to higher access levels, or erasing information.
6.2 Observation
Access information without approval, for instance by deceiving the database into
giving such a large number of results to an inquiry.
Screenshots
Level 7 username and password is
User name: admin
Password: auth- injection
URL link: http://Web-Pen test/SQL-Injection/login-using-sql-injection.html
6.1 Description
The aggressors give extraordinarily made contribution to trap an application into changing
the SQL questions that the application requests that the database execute. This enables the
aggressor to:
Control application conduct that depends on information in the database, for instance by site
an application into permitting a login without a substantial password. Alter information in the
database without approval, for instance by making deceitful records, including clients or
"advancing" clients to higher access levels, or erasing information.
6.2 Observation
Access information without approval, for instance by deceiving the database into
giving such a large number of results to an inquiry.
Screenshots
Level 7 username and password is
User name: admin
Password: auth- injection
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

