Web Application Security Report: Vulnerability Assessment and Testing
VerifiedAdded on 2022/08/17
|13
|1511
|15
Report
AI Summary
This report details a web application security assessment, focusing on vulnerability identification and exploitation techniques. It begins with setting up a vulnerable web application, Mutillidae, on a Kali Linux environment. The report then demonstrates the use of Nmap for port scanning to identify exploitable ports, followed by the use of Wireshark to capture sensitive packet information, and SQLmap to execute SQL injection queries. Screenshots are provided to illustrate the processes and findings. The report analyzes the results obtained from each tool, highlighting the vulnerabilities discovered and the potential impact of successful attacks. The report concludes with a summary of the findings and emphasizes the importance of these tools in understanding and mitigating web application security risks. The report also references several relevant sources to support the analysis.

Running head: WEB APPLICATION SECURITY
Web Application Security
Name of the Student
Name of the University
Author Note
Web Application Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WEB APPLICATION SECURITY
Executive Summary
Scanning, sniffing and SQL injection has become important activities for both
attackers and network administrators. While these activities can be considered unlawful as
they are maliciously used by the attackers, these are also used by network administrators to
identify weak points of the web application. The report is to show how a vulnerable web
application can be set up and how port scans can be performed with nmap to know the
exploitable ports. Then the report is to use Wireshark to gather sensitive packet information.
After that the report is to collect data to execute SQL injection queries through SQL MAP.
Then the report provides critical assessment and ends with conclusions.
Executive Summary
Scanning, sniffing and SQL injection has become important activities for both
attackers and network administrators. While these activities can be considered unlawful as
they are maliciously used by the attackers, these are also used by network administrators to
identify weak points of the web application. The report is to show how a vulnerable web
application can be set up and how port scans can be performed with nmap to know the
exploitable ports. Then the report is to use Wireshark to gather sensitive packet information.
After that the report is to collect data to execute SQL injection queries through SQL MAP.
Then the report provides critical assessment and ends with conclusions.

2WEB APPLICATION SECURITY
Table of Contents
Web Application Setup..............................................................................................................2
Vulnerable Web Application Setup...........................................................................................2
Web Application Security Testing.............................................................................................4
Nmap Scan.............................................................................................................................4
Wireshark Sniffing.................................................................................................................5
SQL MAP...............................................................................................................................7
References................................................................................................................................11
Table of Contents
Web Application Setup..............................................................................................................2
Vulnerable Web Application Setup...........................................................................................2
Web Application Security Testing.............................................................................................4
Nmap Scan.............................................................................................................................4
Wireshark Sniffing.................................................................................................................5
SQL MAP...............................................................................................................................7
References................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WEB APPLICATION SECURITY
Introduction
Scanning, sniffing and SQL injection has become important activities for both
attackers and network administrators. In this report a vulnerable web application called
mutillidae is set up and then nmap scans are performed to know the exploitable ports. The
plat form chosen to set up this vulnerable web application is built upon the Kali Linux
(Debian) operating system. The use of Kali Linux gets rid of the troubles of individually
installing the tools that were required to be used. Then Wireshark is used to gather sensitive
packet information. After that various data is collected by executing a series of SQL injection
queries through SQL MAP. Then this report comes to an end with concluding notes.
Web Application Setup
There exists a lot of website on which penetration testing attempts can be conducted.
However, on most of these websites these attempts will turn futile as they are secured by
having sufficient security mechanisms in place (Savaglia and Wang 2017). Therefore, what
needs to be done is setting up of vulnerable web applications, so that scanning, sniffing and
SQL injection attempts can be made on the particular web pages.
Introduction
Scanning, sniffing and SQL injection has become important activities for both
attackers and network administrators. In this report a vulnerable web application called
mutillidae is set up and then nmap scans are performed to know the exploitable ports. The
plat form chosen to set up this vulnerable web application is built upon the Kali Linux
(Debian) operating system. The use of Kali Linux gets rid of the troubles of individually
installing the tools that were required to be used. Then Wireshark is used to gather sensitive
packet information. After that various data is collected by executing a series of SQL injection
queries through SQL MAP. Then this report comes to an end with concluding notes.
Web Application Setup
There exists a lot of website on which penetration testing attempts can be conducted.
However, on most of these websites these attempts will turn futile as they are secured by
having sufficient security mechanisms in place (Savaglia and Wang 2017). Therefore, what
needs to be done is setting up of vulnerable web applications, so that scanning, sniffing and
SQL injection attempts can be made on the particular web pages.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4WEB APPLICATION SECURITY
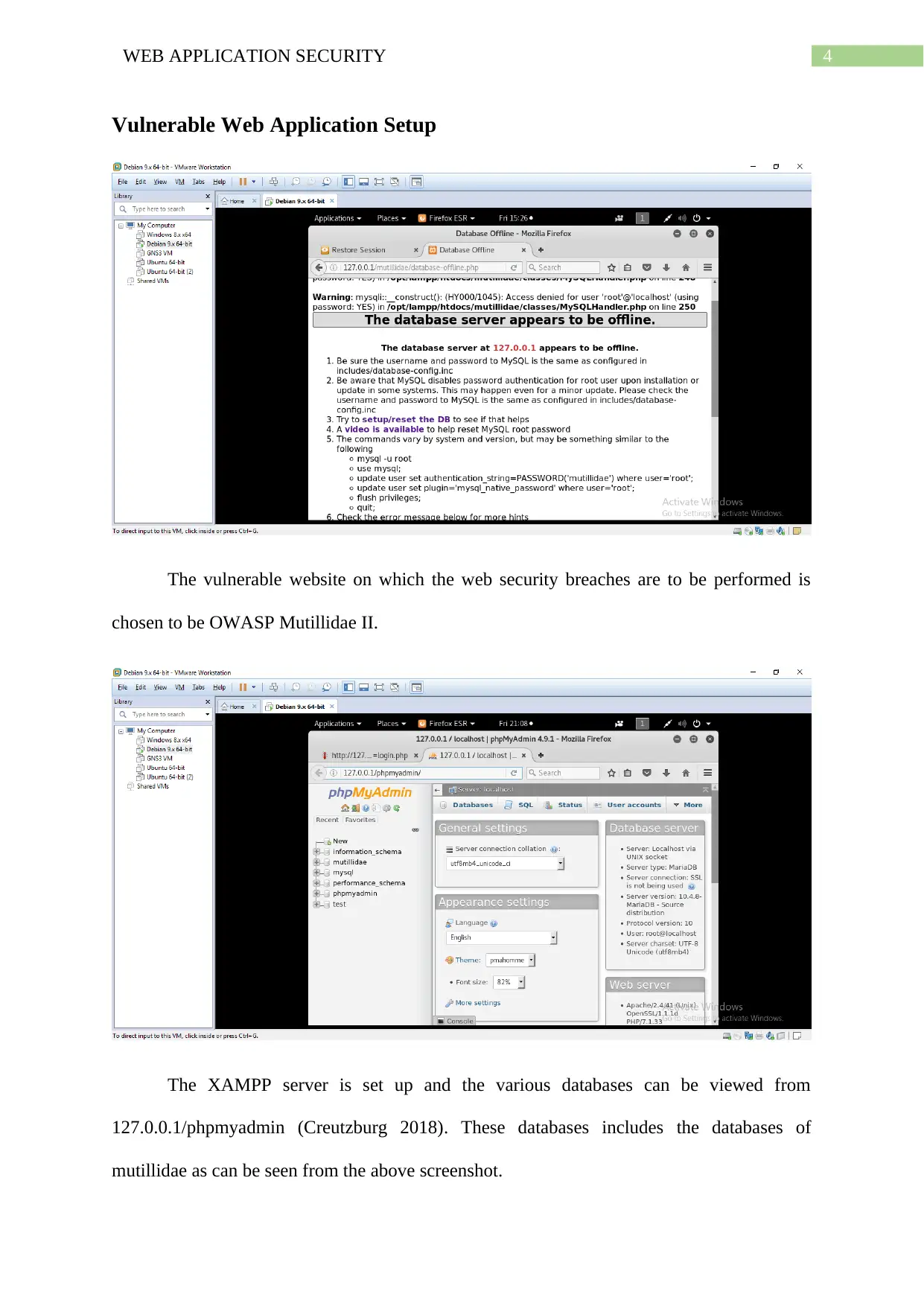
Vulnerable Web Application Setup
The vulnerable website on which the web security breaches are to be performed is
chosen to be OWASP Mutillidae II.
The XAMPP server is set up and the various databases can be viewed from
127.0.0.1/phpmyadmin (Creutzburg 2018). These databases includes the databases of
mutillidae as can be seen from the above screenshot.
Vulnerable Web Application Setup
The vulnerable website on which the web security breaches are to be performed is
chosen to be OWASP Mutillidae II.
The XAMPP server is set up and the various databases can be viewed from
127.0.0.1/phpmyadmin (Creutzburg 2018). These databases includes the databases of
mutillidae as can be seen from the above screenshot.
5WEB APPLICATION SECURITY
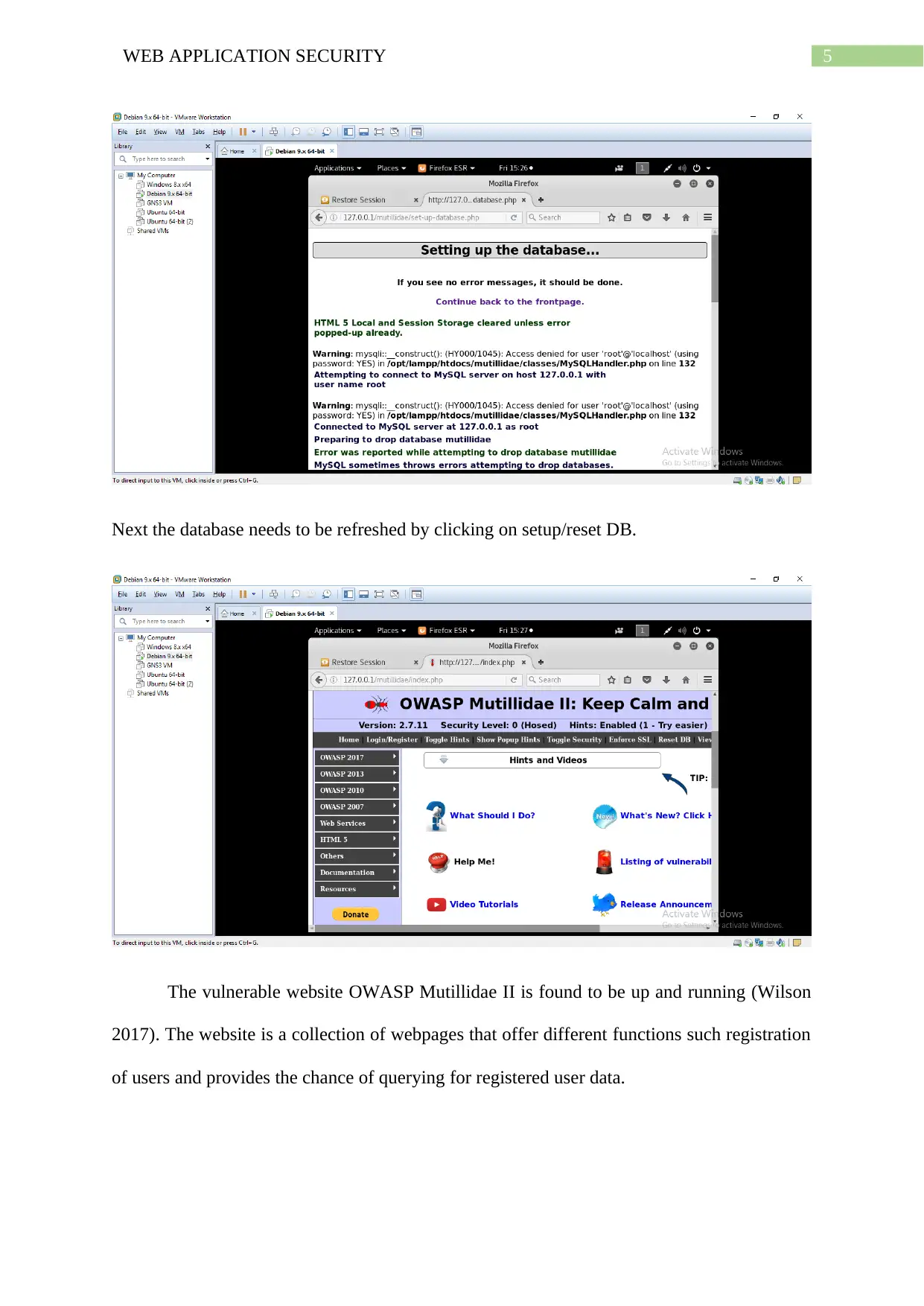
Next the database needs to be refreshed by clicking on setup/reset DB.
The vulnerable website OWASP Mutillidae II is found to be up and running (Wilson
2017). The website is a collection of webpages that offer different functions such registration
of users and provides the chance of querying for registered user data.
Next the database needs to be refreshed by clicking on setup/reset DB.
The vulnerable website OWASP Mutillidae II is found to be up and running (Wilson
2017). The website is a collection of webpages that offer different functions such registration
of users and provides the chance of querying for registered user data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6WEB APPLICATION SECURITY
Web Application Security Testing
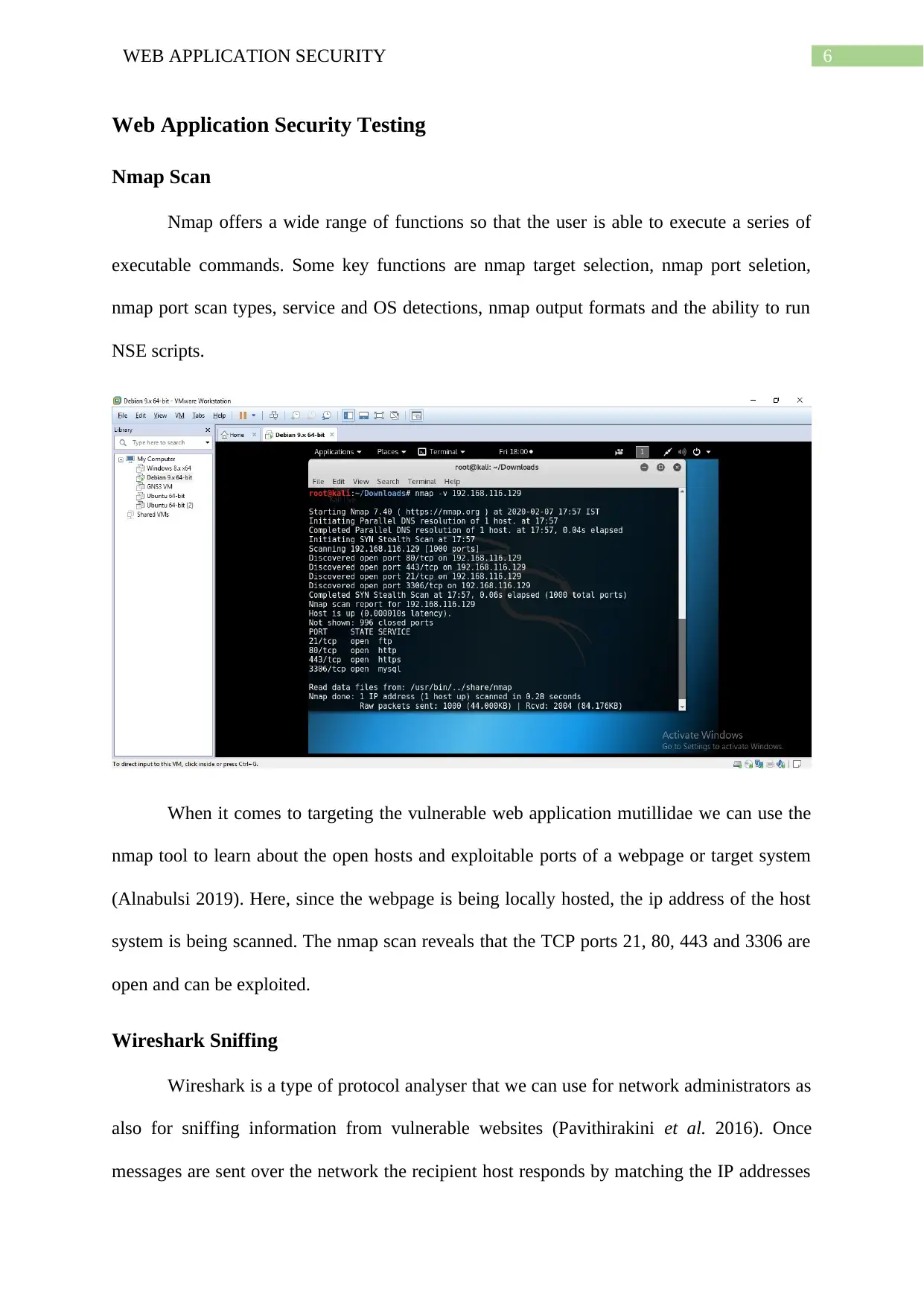
Nmap Scan
Nmap offers a wide range of functions so that the user is able to execute a series of
executable commands. Some key functions are nmap target selection, nmap port seletion,
nmap port scan types, service and OS detections, nmap output formats and the ability to run
NSE scripts.
When it comes to targeting the vulnerable web application mutillidae we can use the
nmap tool to learn about the open hosts and exploitable ports of a webpage or target system
(Alnabulsi 2019). Here, since the webpage is being locally hosted, the ip address of the host
system is being scanned. The nmap scan reveals that the TCP ports 21, 80, 443 and 3306 are
open and can be exploited.
Wireshark Sniffing
Wireshark is a type of protocol analyser that we can use for network administrators as
also for sniffing information from vulnerable websites (Pavithirakini et al. 2016). Once
messages are sent over the network the recipient host responds by matching the IP addresses
Web Application Security Testing
Nmap Scan
Nmap offers a wide range of functions so that the user is able to execute a series of
executable commands. Some key functions are nmap target selection, nmap port seletion,
nmap port scan types, service and OS detections, nmap output formats and the ability to run
NSE scripts.
When it comes to targeting the vulnerable web application mutillidae we can use the
nmap tool to learn about the open hosts and exploitable ports of a webpage or target system
(Alnabulsi 2019). Here, since the webpage is being locally hosted, the ip address of the host
system is being scanned. The nmap scan reveals that the TCP ports 21, 80, 443 and 3306 are
open and can be exploited.
Wireshark Sniffing
Wireshark is a type of protocol analyser that we can use for network administrators as
also for sniffing information from vulnerable websites (Pavithirakini et al. 2016). Once
messages are sent over the network the recipient host responds by matching the IP addresses
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7WEB APPLICATION SECURITY
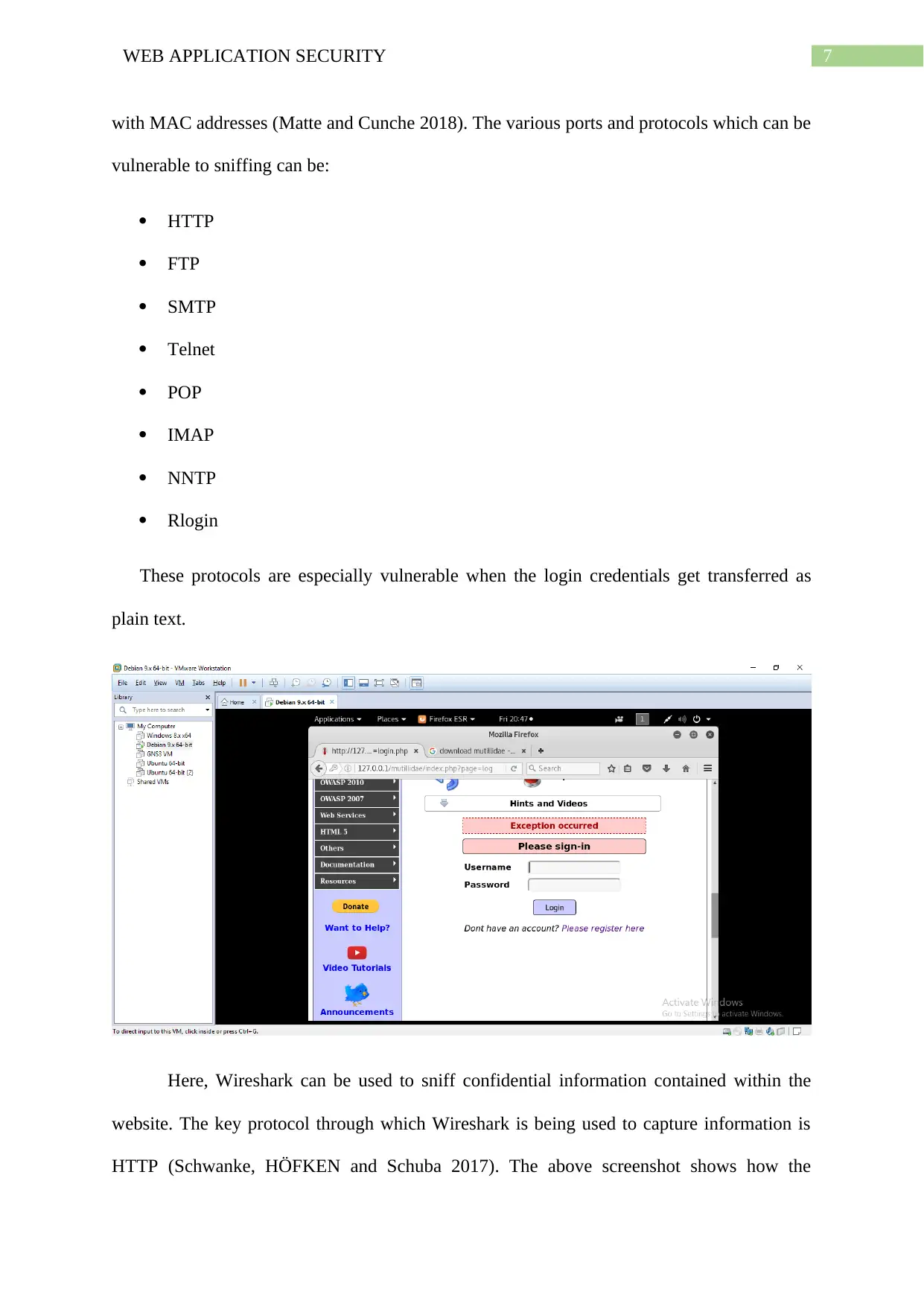
with MAC addresses (Matte and Cunche 2018). The various ports and protocols which can be
vulnerable to sniffing can be:
HTTP
FTP
SMTP
Telnet
POP
IMAP
NNTP
Rlogin
These protocols are especially vulnerable when the login credentials get transferred as
plain text.
Here, Wireshark can be used to sniff confidential information contained within the
website. The key protocol through which Wireshark is being used to capture information is
HTTP (Schwanke, HÖFKEN and Schuba 2017). The above screenshot shows how the
with MAC addresses (Matte and Cunche 2018). The various ports and protocols which can be
vulnerable to sniffing can be:
HTTP
FTP
SMTP
Telnet
POP
IMAP
NNTP
Rlogin
These protocols are especially vulnerable when the login credentials get transferred as
plain text.
Here, Wireshark can be used to sniff confidential information contained within the
website. The key protocol through which Wireshark is being used to capture information is
HTTP (Schwanke, HÖFKEN and Schuba 2017). The above screenshot shows how the
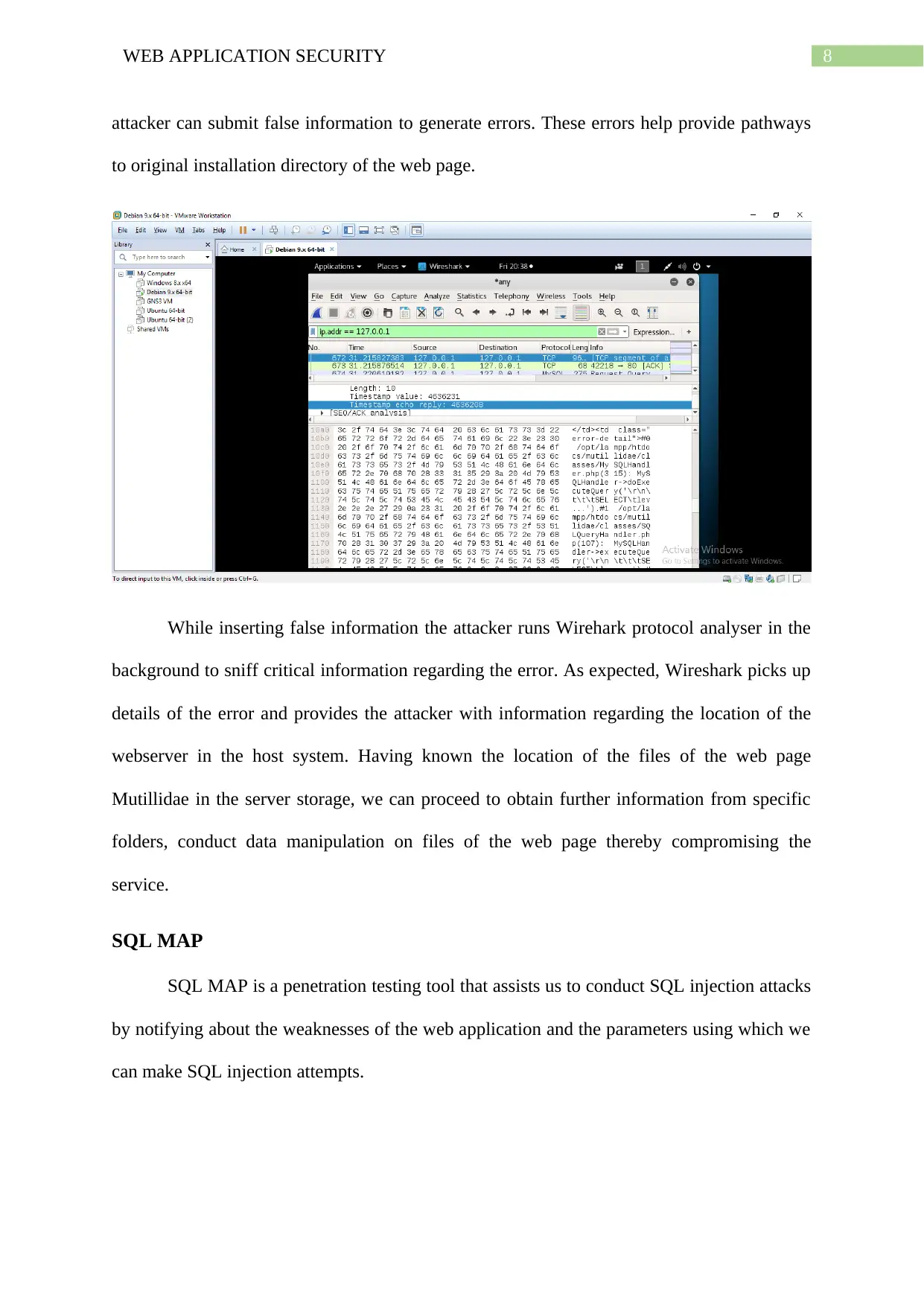
8WEB APPLICATION SECURITY
attacker can submit false information to generate errors. These errors help provide pathways
to original installation directory of the web page.
While inserting false information the attacker runs Wirehark protocol analyser in the
background to sniff critical information regarding the error. As expected, Wireshark picks up
details of the error and provides the attacker with information regarding the location of the
webserver in the host system. Having known the location of the files of the web page
Mutillidae in the server storage, we can proceed to obtain further information from specific
folders, conduct data manipulation on files of the web page thereby compromising the
service.
SQL MAP
SQL MAP is a penetration testing tool that assists us to conduct SQL injection attacks
by notifying about the weaknesses of the web application and the parameters using which we
can make SQL injection attempts.
attacker can submit false information to generate errors. These errors help provide pathways
to original installation directory of the web page.
While inserting false information the attacker runs Wirehark protocol analyser in the
background to sniff critical information regarding the error. As expected, Wireshark picks up
details of the error and provides the attacker with information regarding the location of the
webserver in the host system. Having known the location of the files of the web page
Mutillidae in the server storage, we can proceed to obtain further information from specific
folders, conduct data manipulation on files of the web page thereby compromising the
service.
SQL MAP
SQL MAP is a penetration testing tool that assists us to conduct SQL injection attacks
by notifying about the weaknesses of the web application and the parameters using which we
can make SQL injection attempts.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
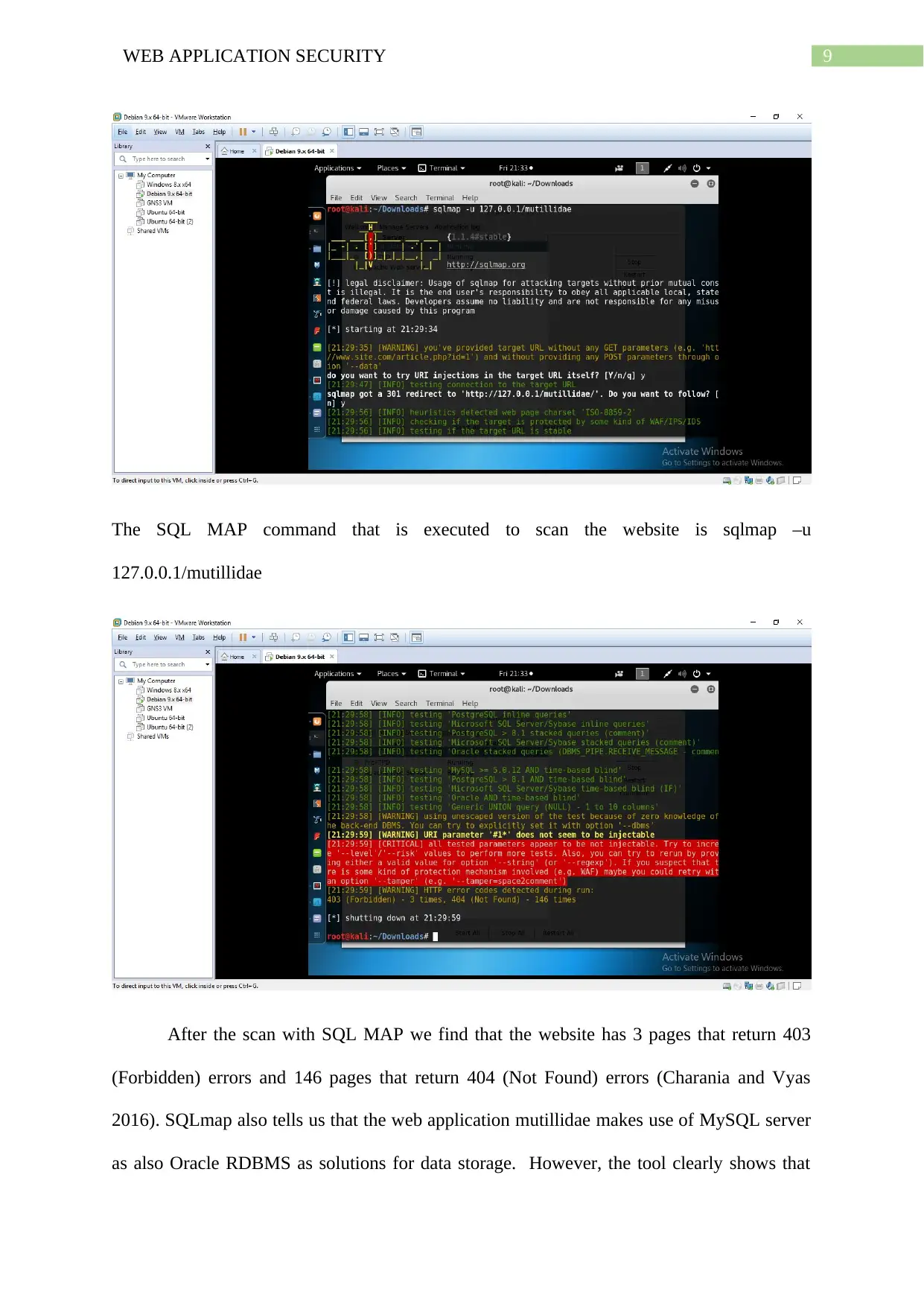
9WEB APPLICATION SECURITY
The SQL MAP command that is executed to scan the website is sqlmap –u
127.0.0.1/mutillidae
After the scan with SQL MAP we find that the website has 3 pages that return 403
(Forbidden) errors and 146 pages that return 404 (Not Found) errors (Charania and Vyas
2016). SQLmap also tells us that the web application mutillidae makes use of MySQL server
as also Oracle RDBMS as solutions for data storage. However, the tool clearly shows that
The SQL MAP command that is executed to scan the website is sqlmap –u
127.0.0.1/mutillidae
After the scan with SQL MAP we find that the website has 3 pages that return 403
(Forbidden) errors and 146 pages that return 404 (Not Found) errors (Charania and Vyas
2016). SQLmap also tells us that the web application mutillidae makes use of MySQL server
as also Oracle RDBMS as solutions for data storage. However, the tool clearly shows that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
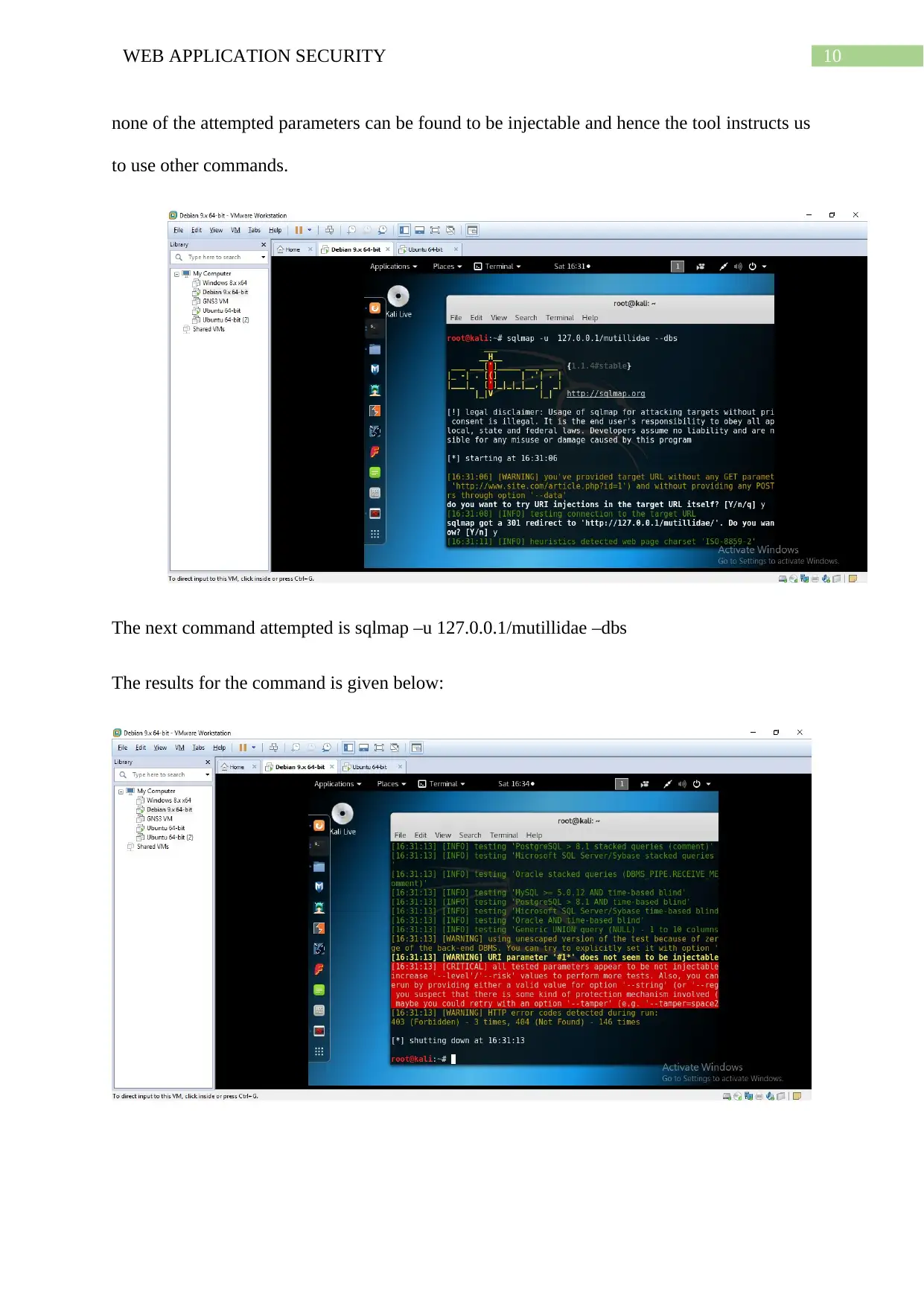
10WEB APPLICATION SECURITY
none of the attempted parameters can be found to be injectable and hence the tool instructs us
to use other commands.
The next command attempted is sqlmap –u 127.0.0.1/mutillidae –dbs
The results for the command is given below:
none of the attempted parameters can be found to be injectable and hence the tool instructs us
to use other commands.
The next command attempted is sqlmap –u 127.0.0.1/mutillidae –dbs
The results for the command is given below:

11WEB APPLICATION SECURITY
As can be observed from the above screenshot, the web application is still not
injectable due to lack of adequate knowledge regarding the back end databases. This means
the web application mutillidae is not safe for SQL injection attempts (Kar, Panigrahi and
Sundararajan 2016). However, since we know that a database schema PIPE exists, we can
obtain further information like tables from this database schema and subsequently fetch the
different columns of the different tables contained by the database.
Conclusion
In conclusion, the report successfully highlights the importance of port scans, sniffing
and SQL injection with the help of tools like nmap, Wireshark and SQL map. The report is
observed to begin with setting up a vulnerable web application called mutillidae. The
platform that is observed to be used for setting up the vulnerable web application is built
upon the Kali Linux which happens to be a Debian based Linux operating system. Then the
report shows how to perform port scans with nmap, sniffing of packet information with
Wireshark and SQL injections through SQL map. Here each of the tools used successfully
exploits the vulnerabilities of the web application. After the demonstration with suitable
screenshots, the report comes to an end.
As can be observed from the above screenshot, the web application is still not
injectable due to lack of adequate knowledge regarding the back end databases. This means
the web application mutillidae is not safe for SQL injection attempts (Kar, Panigrahi and
Sundararajan 2016). However, since we know that a database schema PIPE exists, we can
obtain further information like tables from this database schema and subsequently fetch the
different columns of the different tables contained by the database.
Conclusion
In conclusion, the report successfully highlights the importance of port scans, sniffing
and SQL injection with the help of tools like nmap, Wireshark and SQL map. The report is
observed to begin with setting up a vulnerable web application called mutillidae. The
platform that is observed to be used for setting up the vulnerable web application is built
upon the Kali Linux which happens to be a Debian based Linux operating system. Then the
report shows how to perform port scans with nmap, sniffing of packet information with
Wireshark and SQL injections through SQL map. Here each of the tools used successfully
exploits the vulnerabilities of the web application. After the demonstration with suitable
screenshots, the report comes to an end.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





