Security Analysis: Web Server Vulnerabilities Report
VerifiedAdded on 2022/08/28
|7
|1313
|27
Report
AI Summary
This report provides a comprehensive analysis of web server vulnerabilities, focusing on various attack types and security best practices. It begins with an introduction to web servers and their importance, followed by a detailed discussion of common attacks such as Denial of Service (DoS), buffer overflow, and cache poisoning. Each attack type is explained with its mechanisms and potential impact on the server. The report then compares and contrasts security best practices to mitigate these attacks, including measures to protect against DoS attacks, cache poisoning, and buffer overflows. Finally, the report recommends a suitable security solution for a medium-sized IT firm undergoing global expansion, emphasizing the installation of only required features, patching applications, and maintaining a least-privileged user group. The report concludes by highlighting the importance of up-to-date security patches and the potential for attackers to exploit vulnerabilities to gain control of the server. The report draws on academic sources to support the analysis and recommendations.

Running head: WEB SERVER VULNERABILITIES
Web Server Vulnerabilities
Name of the Student
Name of the University
Authors note
Web Server Vulnerabilities
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WEB SERVER VULNERABILITIES
Introduction
The internet is the mainly dependent on the webservers that host the resources required
by the webservers. Thus, in order to interrupt the services provided by these servers the attackers
carry out different attacks by targeting the web servers and exploiting the vulnerabilities in the
application in order to gain access to the server (Tripathi et al 2016). The report contributes to
the discussion about the different types of attacks, comparison of best practices for security
measures. Furthermore, recommendation for securing the servers are also provided in the report.
Types of Webserver attacks
DoS (Denial of Service Attacks)
In case Denial of service attack (DOS) attacks, the servers become down and is unable to
serve the response against the requests by users. This kind of attack can be performed through
the use of numerous means. One of the most effective technique is buffer over flow. DOS attacks
mainly intended to overwhelm the server by sending invalid and malicious data packets or
requests (Ben-Asher et al 2015). With the huge amount of the requests the server gets flooded
and leads to the crash of the server as well as application running on the servers. As blocking the
complete network traffic may lead to the loss of access to intended users thus it is required to
take mitigation measure to protect the servers. Denial of service attacks are also categorized in
following three categories Application layer attack, volume attack and finally protocol attack.
Introduction
The internet is the mainly dependent on the webservers that host the resources required
by the webservers. Thus, in order to interrupt the services provided by these servers the attackers
carry out different attacks by targeting the web servers and exploiting the vulnerabilities in the
application in order to gain access to the server (Tripathi et al 2016). The report contributes to
the discussion about the different types of attacks, comparison of best practices for security
measures. Furthermore, recommendation for securing the servers are also provided in the report.
Types of Webserver attacks
DoS (Denial of Service Attacks)
In case Denial of service attack (DOS) attacks, the servers become down and is unable to
serve the response against the requests by users. This kind of attack can be performed through
the use of numerous means. One of the most effective technique is buffer over flow. DOS attacks
mainly intended to overwhelm the server by sending invalid and malicious data packets or
requests (Ben-Asher et al 2015). With the huge amount of the requests the server gets flooded
and leads to the crash of the server as well as application running on the servers. As blocking the
complete network traffic may lead to the loss of access to intended users thus it is required to
take mitigation measure to protect the servers. Denial of service attacks are also categorized in
following three categories Application layer attack, volume attack and finally protocol attack.
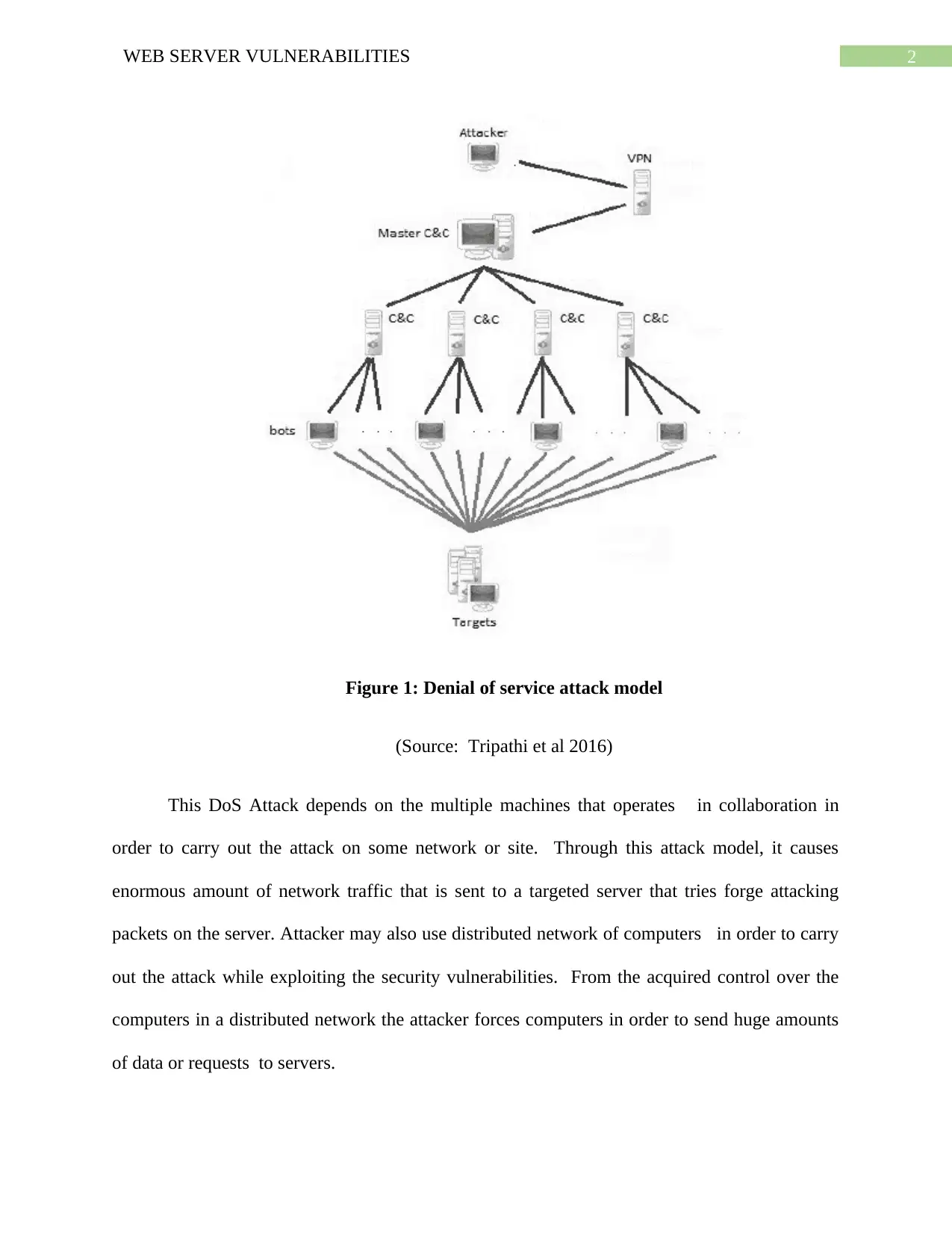
2WEB SERVER VULNERABILITIES
Figure 1: Denial of service attack model
(Source: Tripathi et al 2016)
This DoS Attack depends on the multiple machines that operates in collaboration in
order to carry out the attack on some network or site. Through this attack model, it causes
enormous amount of network traffic that is sent to a targeted server that tries forge attacking
packets on the server. Attacker may also use distributed network of computers in order to carry
out the attack while exploiting the security vulnerabilities. From the acquired control over the
computers in a distributed network the attacker forces computers in order to send huge amounts
of data or requests to servers.
Figure 1: Denial of service attack model
(Source: Tripathi et al 2016)
This DoS Attack depends on the multiple machines that operates in collaboration in
order to carry out the attack on some network or site. Through this attack model, it causes
enormous amount of network traffic that is sent to a targeted server that tries forge attacking
packets on the server. Attacker may also use distributed network of computers in order to carry
out the attack while exploiting the security vulnerabilities. From the acquired control over the
computers in a distributed network the attacker forces computers in order to send huge amounts
of data or requests to servers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WEB SERVER VULNERABILITIES
Buffer Overflow Attacks
For the Buffer Overflow attacks, the attackers try to deliberately overflow the server
buffer memory which is mainly reserved for getting and processing user input. Whenever a web
application running on the web server waits for user’s input, there is an allocated stack space in
the memory is determined (Tripathi et al 2016). This memory segment is required to store the
user provided data. The attackers mainly intend to flood the allocated space by putting arbitrary
data. As the required memory stack becomes full and consequently the users are denied by the
server from providing the service.
Even if the stack recovers from crash, it gets back goes to return address, in case the
return address is changed by the attackers and redirected to the desired range, and finally the
replaced code is executed. After the execution of the command it grants the attacker to
vulnerable sections of web servers.
Cache poisoning attacks
For the web servers, the Cache poisoning is relying upon the insertion of the corrupt
data in the cache database of the server and the domain name system. Domain Name System is
responsible for associating the domain names with the respective IP addresses (Al-Khurafi
2015). The computing devices that are connecting with internet and rely on the DNS in order to
resolve URLs or email addresses with the corresponding IP addresses. With the cache poisoning
attacks the attackers sends forged responses from some imposter DNS that reroutes a specific
domain name to another IP address which is usually controlled by attacker.
Comparison of security best practices for protecting the server
Securing the servers from DoS attacks
Buffer Overflow Attacks
For the Buffer Overflow attacks, the attackers try to deliberately overflow the server
buffer memory which is mainly reserved for getting and processing user input. Whenever a web
application running on the web server waits for user’s input, there is an allocated stack space in
the memory is determined (Tripathi et al 2016). This memory segment is required to store the
user provided data. The attackers mainly intend to flood the allocated space by putting arbitrary
data. As the required memory stack becomes full and consequently the users are denied by the
server from providing the service.
Even if the stack recovers from crash, it gets back goes to return address, in case the
return address is changed by the attackers and redirected to the desired range, and finally the
replaced code is executed. After the execution of the command it grants the attacker to
vulnerable sections of web servers.
Cache poisoning attacks
For the web servers, the Cache poisoning is relying upon the insertion of the corrupt
data in the cache database of the server and the domain name system. Domain Name System is
responsible for associating the domain names with the respective IP addresses (Al-Khurafi
2015). The computing devices that are connecting with internet and rely on the DNS in order to
resolve URLs or email addresses with the corresponding IP addresses. With the cache poisoning
attacks the attackers sends forged responses from some imposter DNS that reroutes a specific
domain name to another IP address which is usually controlled by attacker.
Comparison of security best practices for protecting the server
Securing the servers from DoS attacks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WEB SERVER VULNERABILITIES
In order to protect the servers from the denial of service of attacks it is important to stop
the malicious data packets or service requests from reaching the web servers. In this way it
becomes easy to control null routing traffic to the targeted server (Tripathi et al 2016). By
stopping, dropping and redirecting the request flooding it is possible to save the server from
crash. Furthermore the DoS optimized software firewalls can help in identification and flushing
of the data packets before reaching the server before a certain threshold.
Securing from cache poisoning
In cache poisoning attacks the most difficult stage is the way to determine if an DNS
response from the services to the servers are legitimate or not. An measure that can be
considered as preventive measure is the server should be configures in such a way that only the
necessary services are only allowed to be executed on the server (Al-Khurafi 2015). With the
additional services which are not necessary running on the server increases attack surface that
lead to exploitation of the vulnerabilities by the attackers.
Prevention of Buffer overflow attack
In order to save the servers from buffer overflow attacks, bounds checking is an
important technique. It is a compiler-based technique which checks run-time bounds information
for the allocated block of memory buffer. In addition to that patching the applications is also
important to make the application secured so that they cannot be exploited by the attackers.
In order to protect the servers from the denial of service of attacks it is important to stop
the malicious data packets or service requests from reaching the web servers. In this way it
becomes easy to control null routing traffic to the targeted server (Tripathi et al 2016). By
stopping, dropping and redirecting the request flooding it is possible to save the server from
crash. Furthermore the DoS optimized software firewalls can help in identification and flushing
of the data packets before reaching the server before a certain threshold.
Securing from cache poisoning
In cache poisoning attacks the most difficult stage is the way to determine if an DNS
response from the services to the servers are legitimate or not. An measure that can be
considered as preventive measure is the server should be configures in such a way that only the
necessary services are only allowed to be executed on the server (Al-Khurafi 2015). With the
additional services which are not necessary running on the server increases attack surface that
lead to exploitation of the vulnerabilities by the attackers.
Prevention of Buffer overflow attack
In order to save the servers from buffer overflow attacks, bounds checking is an
important technique. It is a compiler-based technique which checks run-time bounds information
for the allocated block of memory buffer. In addition to that patching the applications is also
important to make the application secured so that they cannot be exploited by the attackers.

5WEB SERVER VULNERABILITIES
Recommend solution for the server
As the organization is trying to expand thus it can lead to increased attack surface.
Therefore, it is suggested to install and execute only required features of applications on the web
servers and not the vulnerable, unnecessary services.
• Installing and patching latest version of application running on the servers.
• maintaining a custom and least-privileged user group. So that execution and
modification cannot be achieved randomly.
• web server needs to be configured in such a way that web content files can be
only read only and cannot be written by the running Web service processes.
Conclusion
In order to avoid the web servers from being exposed to different severe attacks like the
buffer overflow it is very important to patch the server application with up-to-date security
patches from the vendors .Another important aspect of this kind of attacks is, hackers/attackers
can replace some executable command in acquired stack to gain control over it. Even though the
execution of replaced code/command is dependent on return address specified by attacker.
Recommend solution for the server
As the organization is trying to expand thus it can lead to increased attack surface.
Therefore, it is suggested to install and execute only required features of applications on the web
servers and not the vulnerable, unnecessary services.
• Installing and patching latest version of application running on the servers.
• maintaining a custom and least-privileged user group. So that execution and
modification cannot be achieved randomly.
• web server needs to be configured in such a way that web content files can be
only read only and cannot be written by the running Web service processes.
Conclusion
In order to avoid the web servers from being exposed to different severe attacks like the
buffer overflow it is very important to patch the server application with up-to-date security
patches from the vendors .Another important aspect of this kind of attacks is, hackers/attackers
can replace some executable command in acquired stack to gain control over it. Even though the
execution of replaced code/command is dependent on return address specified by attacker.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WEB SERVER VULNERABILITIES
References
Al-Khurafi, Ossama B., and Mohammad A. Al-Ahmad. "Survey of web application vulnerability
attacks." 2015 4th International Conference on Advanced Computer Science Applications and
Technologies (ACSAT). IEEE, 2015.
Ben-Asher, Noam, and Cleotilde Gonzalez. "Effects of cyber security knowledge on attack
detection." Computers in Human Behavior 48 (2015): 51-61.
Tripathi, Nikhil, Neminath Hubballi, and Yogendra Singh. "How secure are web servers? An
empirical study of slow HTTP DoS attacks and detection." 2016 11th International Conference
on Availability, Reliability and Security (ARES). IEEE, 2016.
Van Goethem, Tom, Wouter Joosen, and Nick Nikiforakis. "The clock is still ticking: Timing
attacks in the modern web." Proceedings of the 22nd ACM SIGSAC Conference on Computer
and Communications Security. 2015.
References
Al-Khurafi, Ossama B., and Mohammad A. Al-Ahmad. "Survey of web application vulnerability
attacks." 2015 4th International Conference on Advanced Computer Science Applications and
Technologies (ACSAT). IEEE, 2015.
Ben-Asher, Noam, and Cleotilde Gonzalez. "Effects of cyber security knowledge on attack
detection." Computers in Human Behavior 48 (2015): 51-61.
Tripathi, Nikhil, Neminath Hubballi, and Yogendra Singh. "How secure are web servers? An
empirical study of slow HTTP DoS attacks and detection." 2016 11th International Conference
on Availability, Reliability and Security (ARES). IEEE, 2016.
Van Goethem, Tom, Wouter Joosen, and Nick Nikiforakis. "The clock is still ticking: Timing
attacks in the modern web." Proceedings of the 22nd ACM SIGSAC Conference on Computer
and Communications Security. 2015.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




