System Security Analysis: WebGoat, Kali Linux, and Attack Strategies
VerifiedAdded on 2020/03/04
|16
|2081
|46
Report
AI Summary
This report delves into system security, exploring the functionalities of WebGoat and Kali Linux. It begins by detailing the installation process of WebGoat, a software designed for testing system vulnerabilities, and outlines various challenges faced during website hacking attempts. The report then explores potential attack methods, with a focus on SQL injection techniques and their implementation. Furthermore, the report transitions to the application of Kali Linux for hacking, specifically detailing the steps involved in attempting to compromise a Facebook account through social engineering and credential harvesting. The report assesses the attack's effectiveness, evaluates the collected data, and concludes by outlining essential preventive measures to safeguard against such attacks, including strong password practices and awareness of deceptive tactics.

qwertyuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnmqwer
tyuiopasdfghjklzxcvbnmqwertyuiopas
dfghjklzxcvbnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbnmqwertyuio
pasdfghjklzxcvbnmqwertyuiopasdfghj
klzxcvbnmqwertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcvbnmqwerty
uiopasdfghjklzxcvbnmqwertyuiopasdf
ghjklzxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvbnmrty
uiopasdfghjklzxcvbnmqwertyuiopasdf
ghjklzxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvbnmqw
System
Security
opasdfghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnmqwer
tyuiopasdfghjklzxcvbnmqwertyuiopas
dfghjklzxcvbnmqwertyuiopasdfghjklzx
cvbnmqwertyuiopasdfghjklzxcvbnmq
wertyuiopasdfghjklzxcvbnmqwertyuio
pasdfghjklzxcvbnmqwertyuiopasdfghj
klzxcvbnmqwertyuiopasdfghjklzxcvbn
mqwertyuiopasdfghjklzxcvbnmqwerty
uiopasdfghjklzxcvbnmqwertyuiopasdf
ghjklzxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvbnmrty
uiopasdfghjklzxcvbnmqwertyuiopasdf
ghjklzxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvbnmqw
System
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.........................................................................................................................................3
PART A...................................................................................................................................................3
1. Installation procedures for Web goat.........................................................................................3
2. Web Goat Challenge....................................................................................................................4
3. Possible Attack Methods.............................................................................................................6
4. Attack Method Used....................................................................................................................7
PART B................................................................................................................................................7
5. Backtracksteps to Hack Facebook Account (Kali Linux).........................................................7
6. Accomplishment of Attack........................................................................................................13
7. Evaluating the Collected Data..................................................................................................14
8. Preventions.................................................................................................................................14
9. Conclusion..................................................................................................................................14
References..........................................................................................................................................15
Introduction.........................................................................................................................................3
PART A...................................................................................................................................................3
1. Installation procedures for Web goat.........................................................................................3
2. Web Goat Challenge....................................................................................................................4
3. Possible Attack Methods.............................................................................................................6
4. Attack Method Used....................................................................................................................7
PART B................................................................................................................................................7
5. Backtracksteps to Hack Facebook Account (Kali Linux).........................................................7
6. Accomplishment of Attack........................................................................................................13
7. Evaluating the Collected Data..................................................................................................14
8. Preventions.................................................................................................................................14
9. Conclusion..................................................................................................................................14
References..........................................................................................................................................15

Introduction
System security is one of the active concepts now a days .To hack and test the system
security a interesting software called web goat is used. The project deals with the installation
procedures of the web goat software , the challenges faced by the web goat software and the
possible attack methods.
PART A
1. Installation procedures for Web goat
The project deals with the system security. To hope up with the system security the
software tool called the web goat is used. The web goat software requires an operating system
like windows to work with. It also requires the java development kit. The java software is
downloaded from
http://www.oracle.com/technetwork/java/javase/downloads/index.html.webgoat also needs
Apache Tomcat Server. The web goat is downloaded using the link
https://github.com/WebGoat/WebGoat/releases.After the successful installation of web goat,
it is accessed by the url http://localhost:8000/WebGoat.Webgoat is used for hacking the
website. Web goat faces 3 challenges to hack the website.
System security is one of the active concepts now a days .To hack and test the system
security a interesting software called web goat is used. The project deals with the installation
procedures of the web goat software , the challenges faced by the web goat software and the
possible attack methods.
PART A
1. Installation procedures for Web goat
The project deals with the system security. To hope up with the system security the
software tool called the web goat is used. The web goat software requires an operating system
like windows to work with. It also requires the java development kit. The java software is
downloaded from
http://www.oracle.com/technetwork/java/javase/downloads/index.html.webgoat also needs
Apache Tomcat Server. The web goat is downloaded using the link
https://github.com/WebGoat/WebGoat/releases.After the successful installation of web goat,
it is accessed by the url http://localhost:8000/WebGoat.Webgoat is used for hacking the
website. Web goat faces 3 challenges to hack the website.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
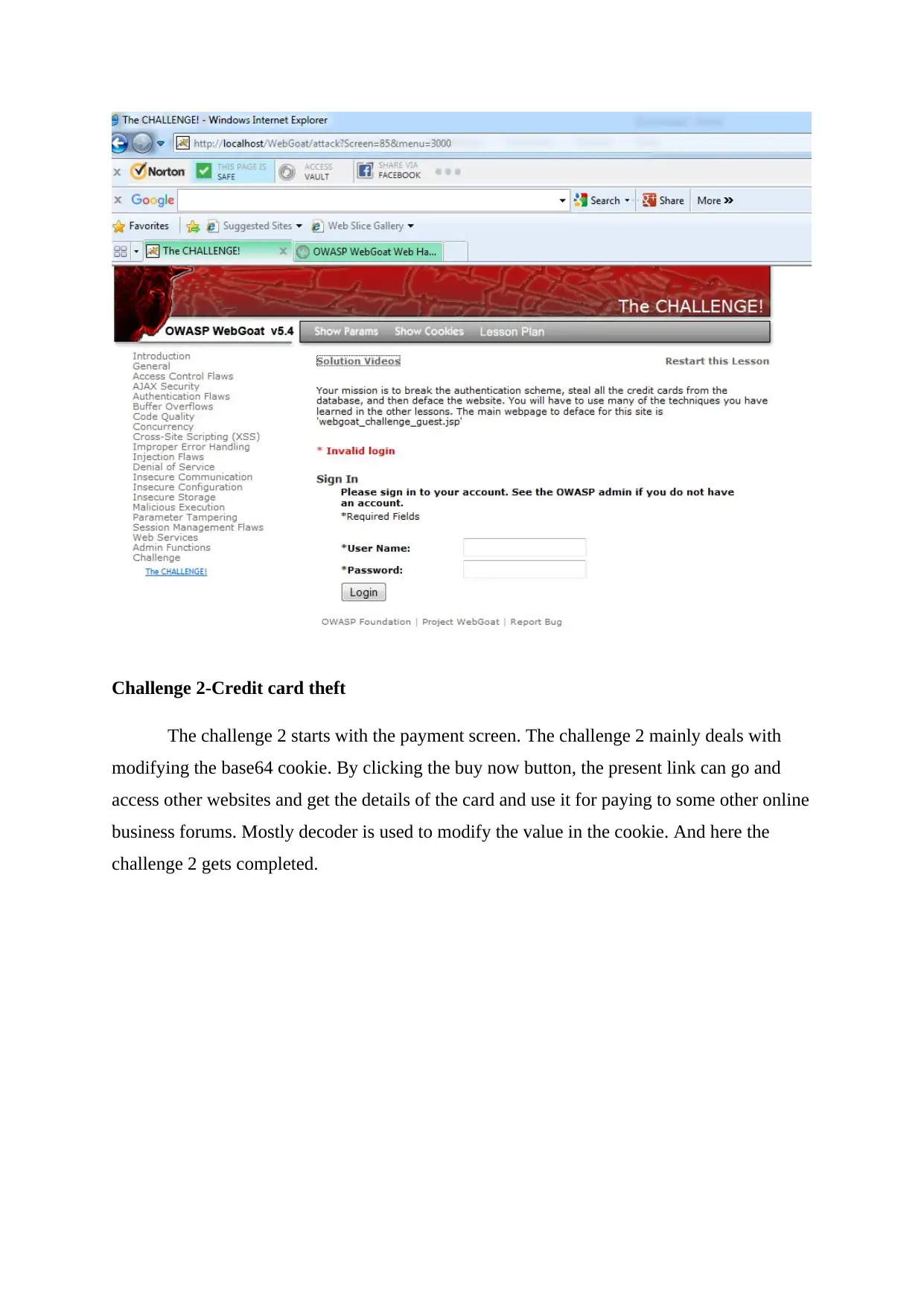
2. Web Goat Challenge
Challenge 1- Breaking the authentication
The first is to break the authentication. The challenge starts with the window which
appears like a login window. Both username and password is tracked by viewing the java
code which is mentioned as private. The username is youaretheweakestlink and the password
is goodbye. Both of these things are tracked by SQL Injection. Setting the cookie with altered
name can also help us retrieving the password.
Challenge 1- Breaking the authentication
The first is to break the authentication. The challenge starts with the window which
appears like a login window. Both username and password is tracked by viewing the java
code which is mentioned as private. The username is youaretheweakestlink and the password
is goodbye. Both of these things are tracked by SQL Injection. Setting the cookie with altered
name can also help us retrieving the password.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Challenge 2-Credit card theft
The challenge 2 starts with the payment screen. The challenge 2 mainly deals with
modifying the base64 cookie. By clicking the buy now button, the present link can go and
access other websites and get the details of the card and use it for paying to some other online
business forums. Mostly decoder is used to modify the value in the cookie. And here the
challenge 2 gets completed.
The challenge 2 starts with the payment screen. The challenge 2 mainly deals with
modifying the base64 cookie. By clicking the buy now button, the present link can go and
access other websites and get the details of the card and use it for paying to some other online
business forums. Mostly decoder is used to modify the value in the cookie. And here the
challenge 2 gets completed.

Challenge 3-Defacing the website
Defacing the website is the final stage of hacking the website and this stage lists out
the currently active websites. This stage displays the two similar frames of a website one is
original and the other is the copy. The copied one is otherwise called the defaced one. To
carry out this we are in need to use the chrome's commands from "tcp" to "&&cd" which
works in accordance with the unix password. This command lists locations and the addresses
of all active websites.
3. Possible Attack Methods
Modifying the fixed parameters
session stealing
by using fake urls
sql injection
The important thing for the attack is to code the authentication and to enable the user to make
the authentication. Sending fake urls can act as the best method to cheat the original user. The
authentication page can be bypassed. The bypassing is done by coding auth=0 or auth=1.
Defacing the website is the final stage of hacking the website and this stage lists out
the currently active websites. This stage displays the two similar frames of a website one is
original and the other is the copy. The copied one is otherwise called the defaced one. To
carry out this we are in need to use the chrome's commands from "tcp" to "&&cd" which
works in accordance with the unix password. This command lists locations and the addresses
of all active websites.
3. Possible Attack Methods
Modifying the fixed parameters
session stealing
by using fake urls
sql injection
The important thing for the attack is to code the authentication and to enable the user to make
the authentication. Sending fake urls can act as the best method to cheat the original user. The
authentication page can be bypassed. The bypassing is done by coding auth=0 or auth=1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4. Attack Method Used
The attack method used here is the SQL injection technique. SQL injection technique
is used to inject codes and attack data. There are many methods used for the SQL injection.
Some of the methods are
Blind SQL injection
Incorrect type handling
Second order SQL injection.
PART B
5. Back tracksteps to Hack Face book Account (Kali Linux)
The Kali Linux plays a major role in hacking the social networks. The following are
the steps involved to hack the Face book account(Kali.org, 2016):
Initially, install the Kali Linux software once the installation completes open up the terminal
screen which is displayed on the screen.
Step 1:Ensure to enter the below mentioned command in the Linus terminal.
root@kali~# setoolkit
The attack method used here is the SQL injection technique. SQL injection technique
is used to inject codes and attack data. There are many methods used for the SQL injection.
Some of the methods are
Blind SQL injection
Incorrect type handling
Second order SQL injection.
PART B
5. Back tracksteps to Hack Face book Account (Kali Linux)
The Kali Linux plays a major role in hacking the social networks. The following are
the steps involved to hack the Face book account(Kali.org, 2016):
Initially, install the Kali Linux software once the installation completes open up the terminal
screen which is displayed on the screen.
Step 1:Ensure to enter the below mentioned command in the Linus terminal.
root@kali~# setoolkit
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
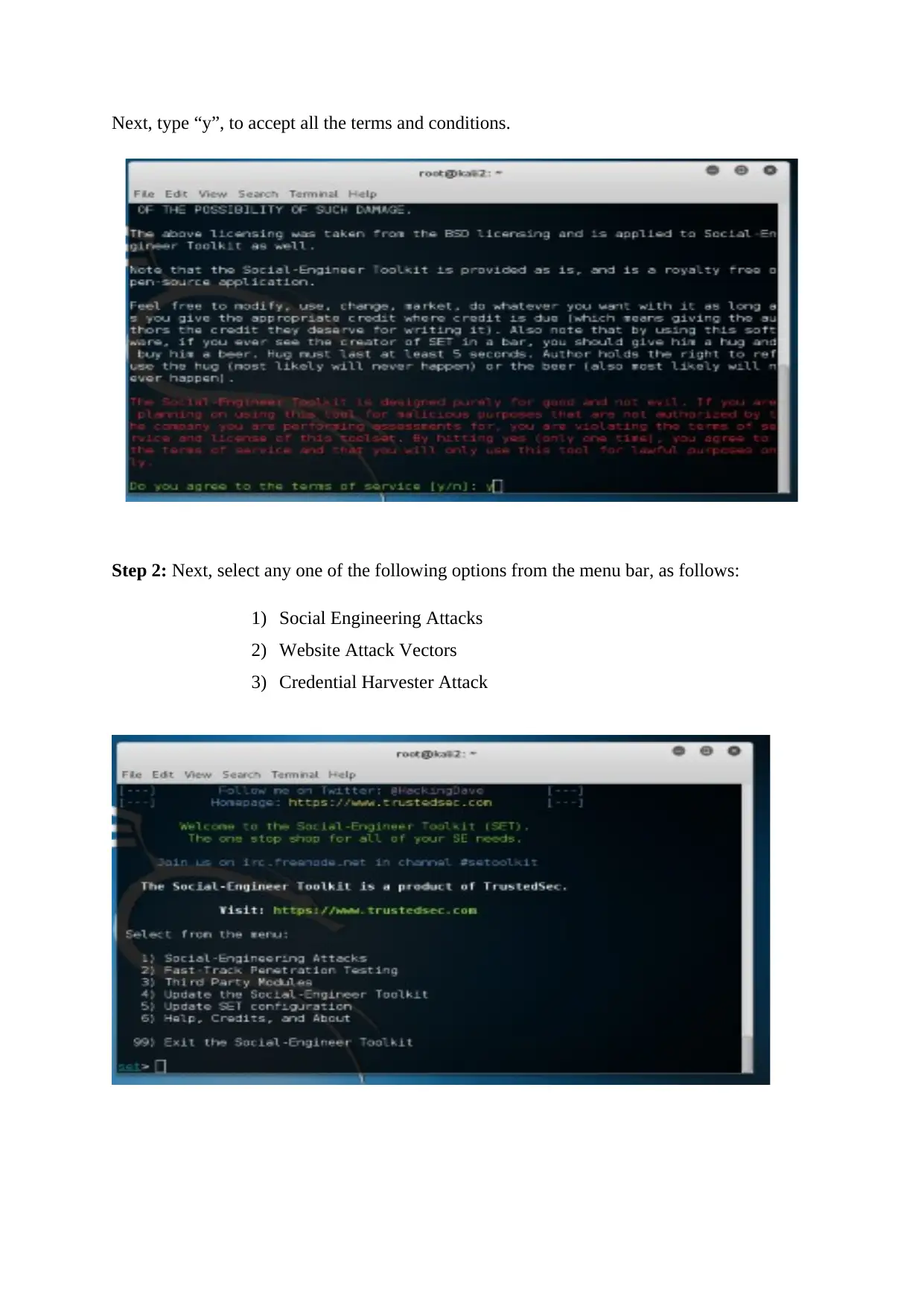
Next, type “y”, to accept all the terms and conditions.
Step 2: Next, select any one of the following options from the menu bar, as follows:
1) Social Engineering Attacks
2) Website Attack Vectors
3) Credential Harvester Attack
Step 2: Next, select any one of the following options from the menu bar, as follows:
1) Social Engineering Attacks
2) Website Attack Vectors
3) Credential Harvester Attack
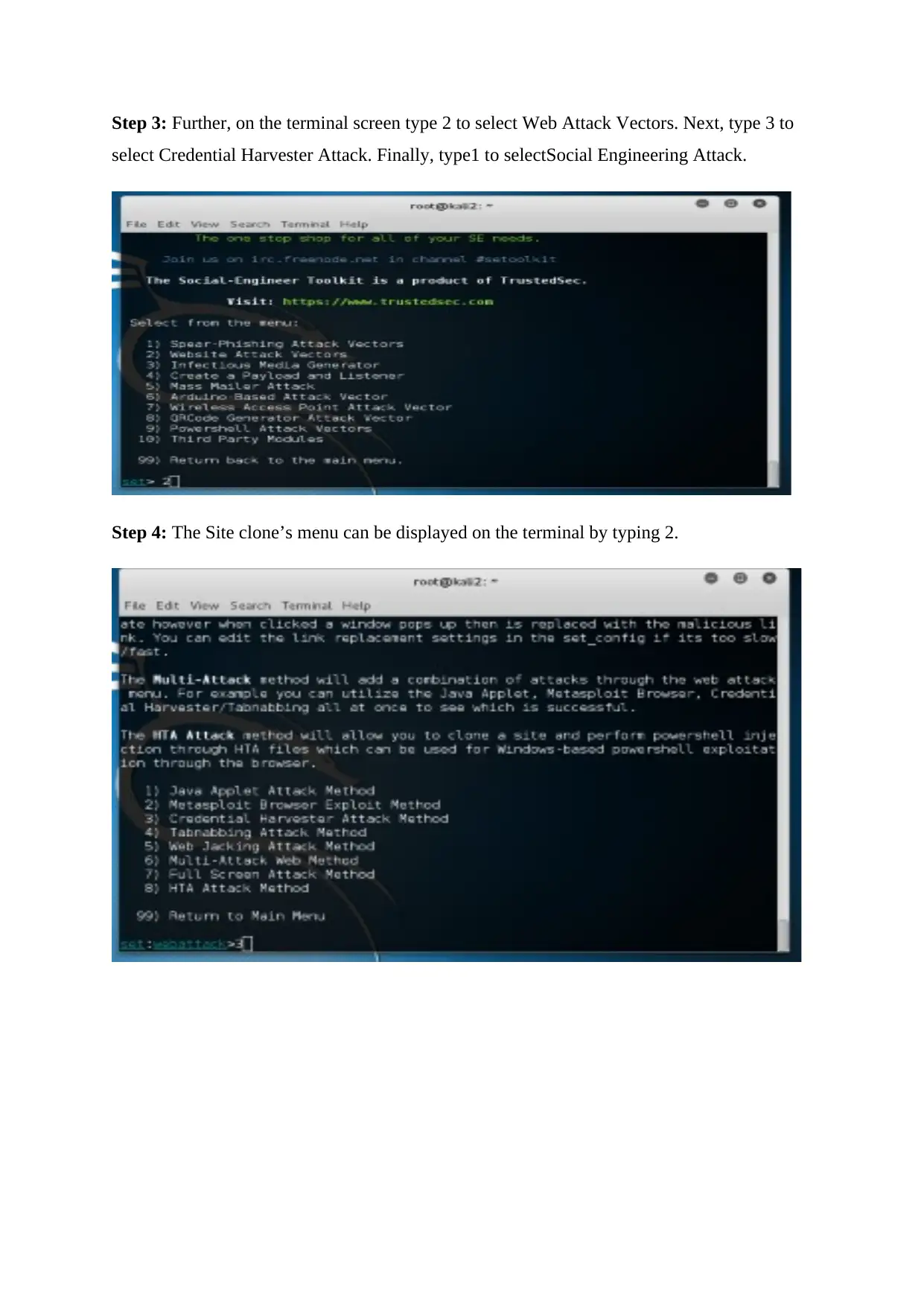
Step 3: Further, on the terminal screen type 2 to select Web Attack Vectors. Next, type 3 to
select Credential Harvester Attack. Finally, type1 to selectSocial Engineering Attack.
Step 4: The Site clone’s menu can be displayed on the terminal by typing 2.
select Credential Harvester Attack. Finally, type1 to selectSocial Engineering Attack.
Step 4: The Site clone’s menu can be displayed on the terminal by typing 2.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
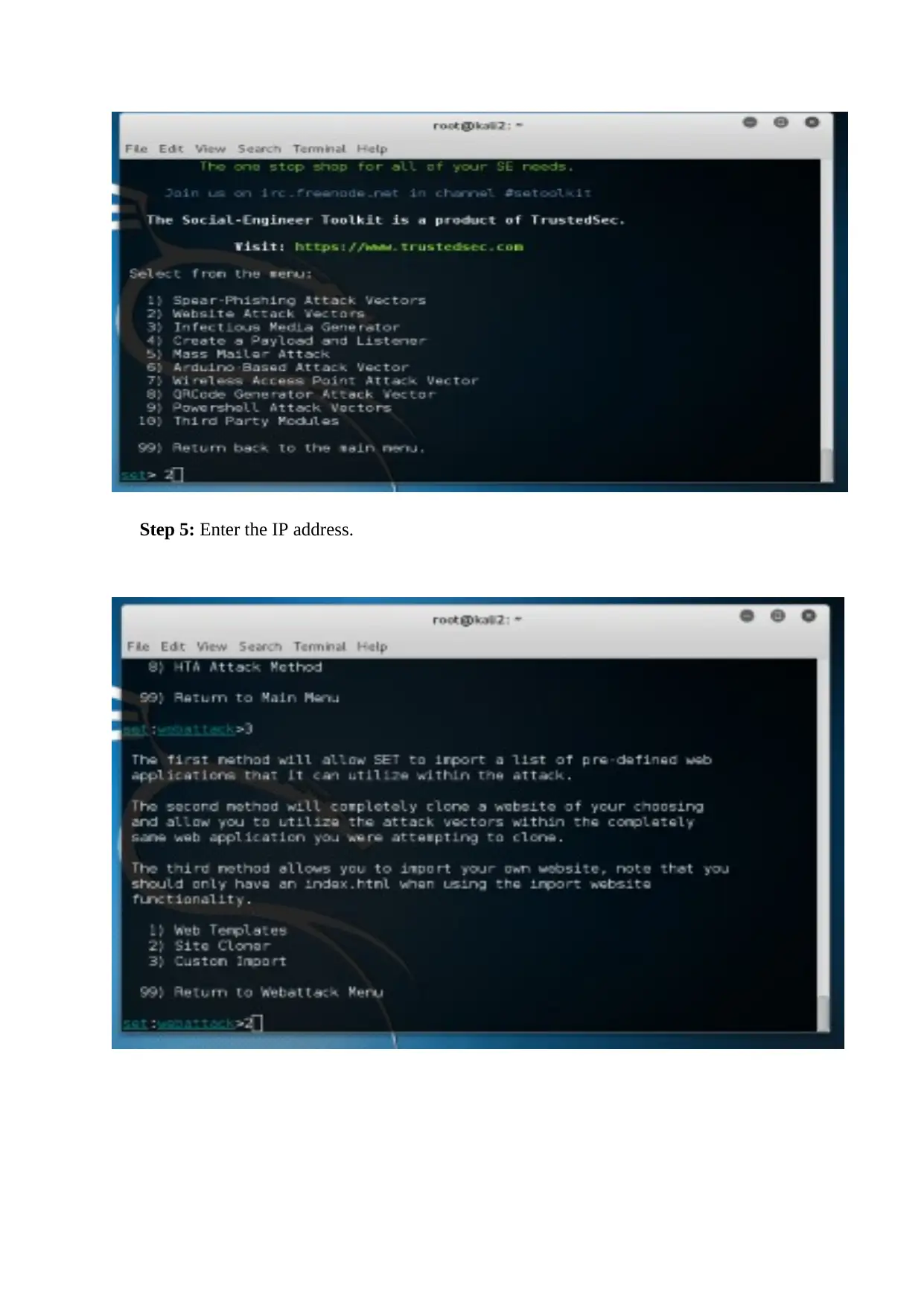
Step 5: Enter the IP address.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Step 6: Provide“www.fb.com” in the clone.
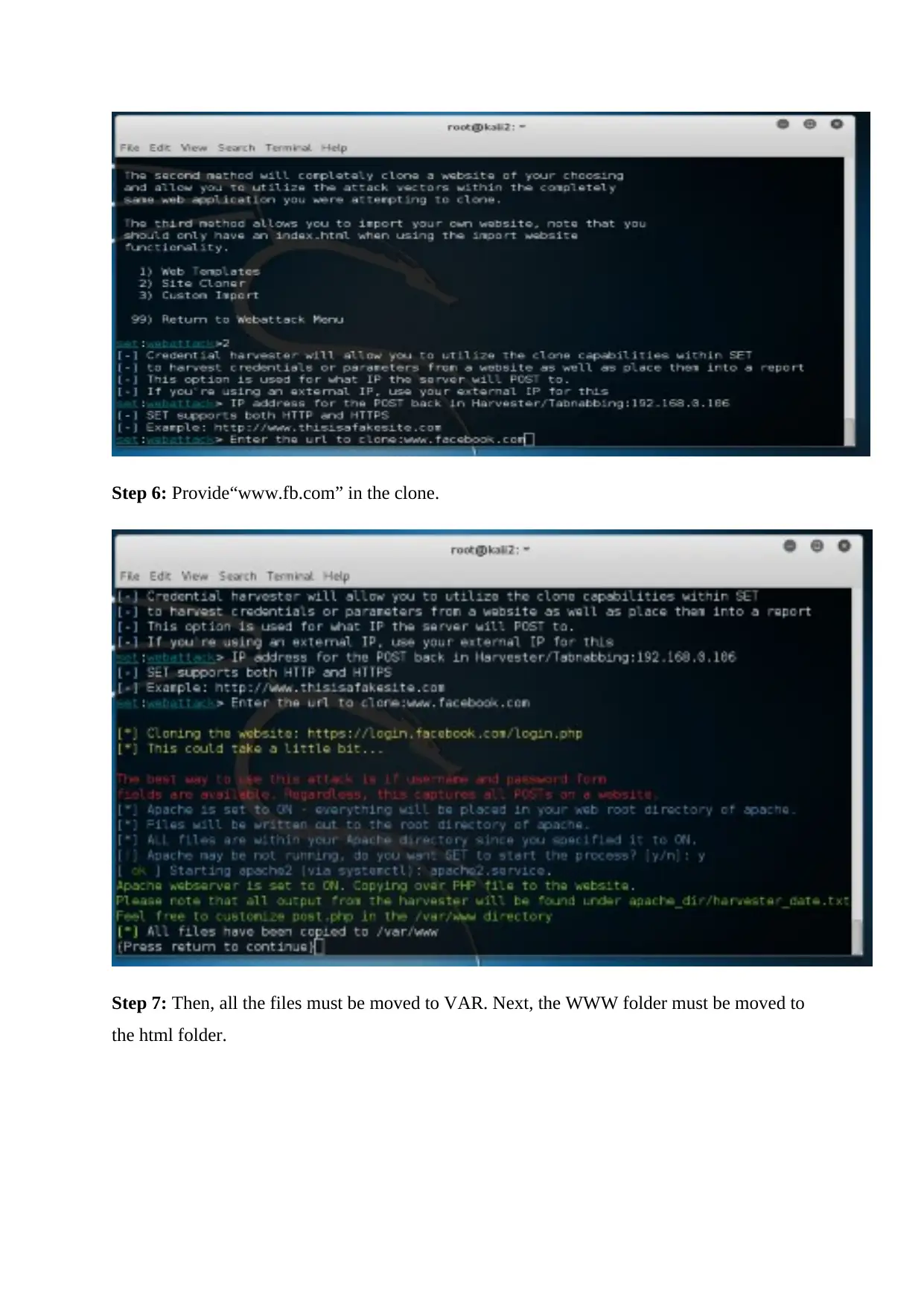
Step 7: Then, all the files must be moved to VAR. Next, the WWW folder must be moved to
the html folder.
Step 7: Then, all the files must be moved to VAR. Next, the WWW folder must be moved to
the html folder.
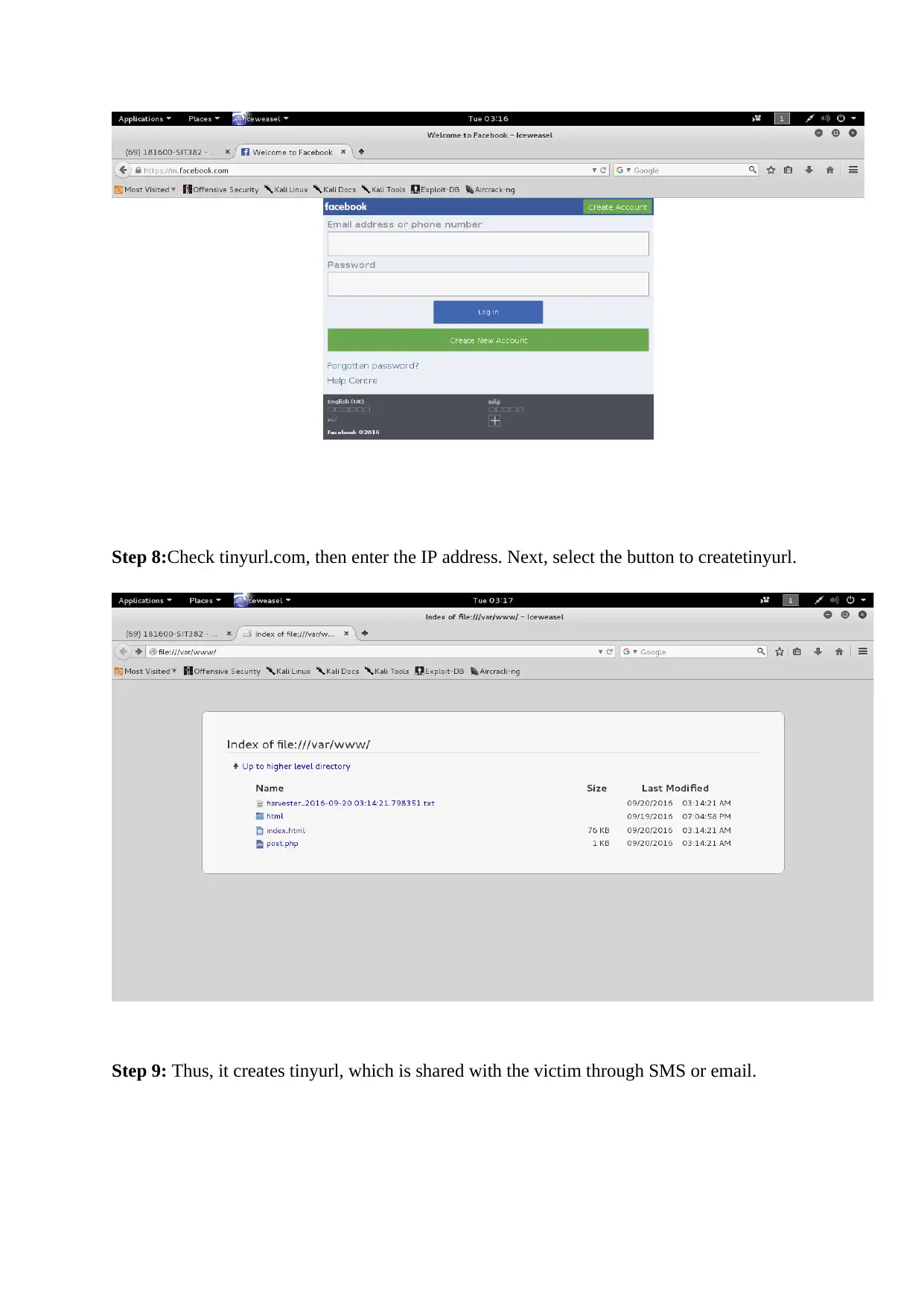
Step 8:Check tinyurl.com, then enter the IP address. Next, select the button to createtinyurl.
Step 9: Thus, it creates tinyurl, which is shared with the victim through SMS or email.
Step 9: Thus, it creates tinyurl, which is shared with the victim through SMS or email.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





