WEP Network Design: Security, Implementation, and Analysis Report
VerifiedAdded on 2022/10/11
|12
|509
|16
Report
AI Summary
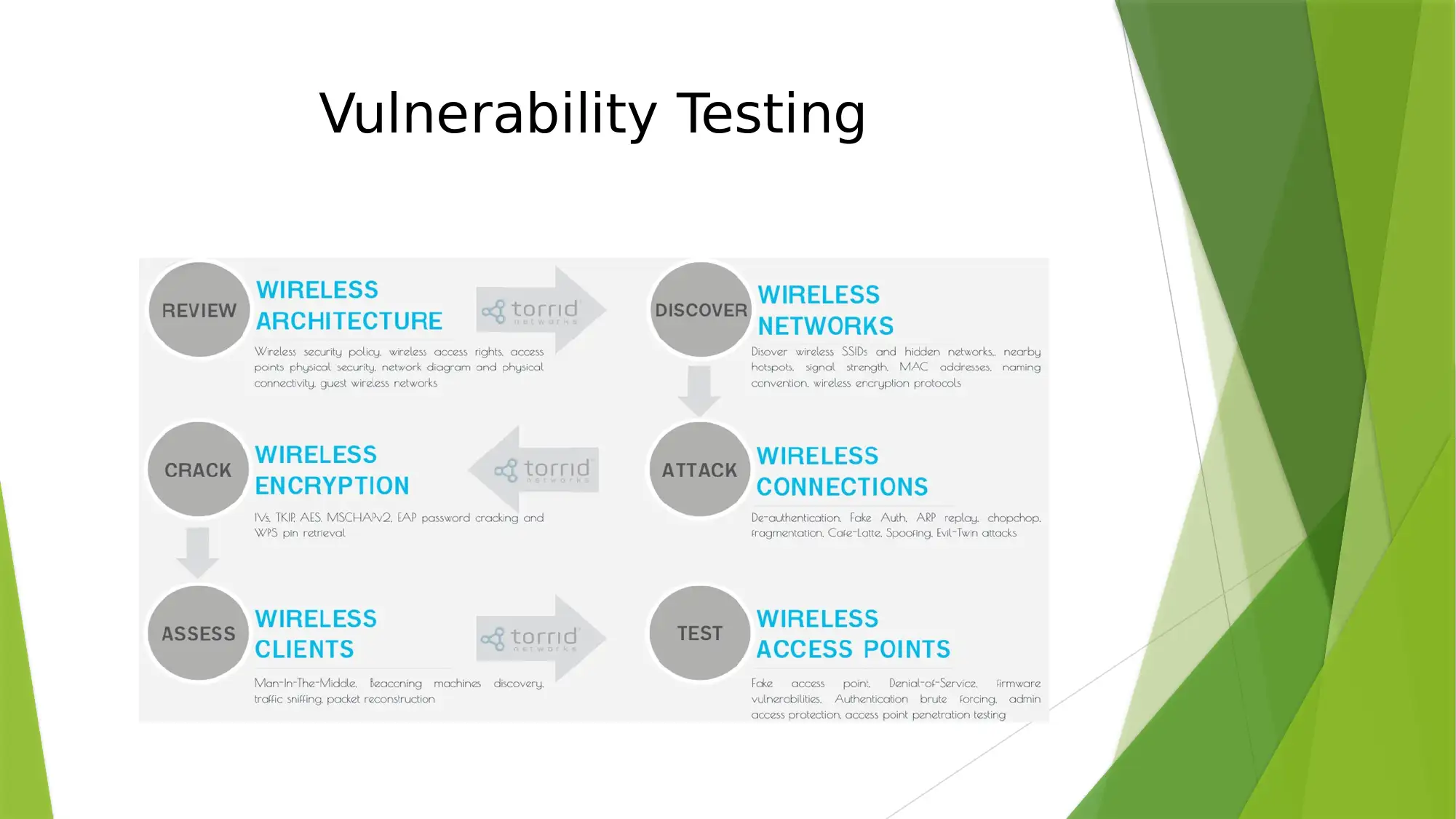
This report delves into the intricacies of WEP network design, emphasizing security and implementation strategies. It begins by highlighting the increasing popularity of wireless networks, and the need for secure designs. The report addresses the requirements for wireless networks, specifically focusing on the needs of Camp David and the US president. It then explores various security vulnerabilities, including eavesdropping, message manipulation, and denial-of-service attacks. To combat these threats, the report proposes a robust security architecture, including the use of EAP-MD5, CHAP protocol, and transport layer security. Furthermore, it recommends the implementation of stateful firewalls and software solutions such as remote hub server programming bundles and multiport serial boards to enhance network security and performance. Finally, the report includes a list of references.
1 out of 12












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)