Smart Grid and Cloud Computing: WOA-ANN Intrusion Detection Analysis
VerifiedAdded on 2022/09/18
|11
|3856
|28
Report
AI Summary
This report summarizes two research papers focused on network intrusion detection using the Whale Optimization Algorithm (WOA) and Artificial Neural Networks (ANN). The first paper, "A whale optimization algorithm-trained artificial neural network for smart grid cyber intrusion detection," introduces a novel intrusion detection model for smart grids capable of classifying various cyber-attacks using a WOA-trained ANN. The WOA optimizes the ANN's weight vector to minimize mean square error, demonstrating effectiveness using Mississippi State University and Oak Ridge National Laboratory databases. The second paper, "Network Intrusion Detection Framework Based on Whale Swarm Algorithm and Artificial Neural Network in Cloud Computing," proposes a WOA-ANN model to detect DDoS attacks in cloud computing environments, specifically targeting UDP and TCP flooding. The framework utilizes the WOA to enhance the accuracy of the N-IDS by improving the analysis of network traffic. Both papers highlight the potential of WOA-ANN models in enhancing cybersecurity, especially in the context of smart grids and cloud computing, with the first paper concentrating on smart grids and the second on cloud computing. The results show that the WOA can effectively train the ANN to find the optimal weights. The future work includes exploring hybridization with other evolutionary search schemes and the development of a new model for the N-IDS system to reduce the false alarm. The effectiveness of the WOA-ANN model is validated through MATLAB simulations, demonstrating improved accuracy and reduced false alarms compared to existing methods. The papers also discuss the importance of intrusion detection in addressing various challenges related to cyber attacks, failure prediction, and failure detection. The authors suggest further research into hybridizing WOA-ANN with other evolutionary search schemes for enhanced performance.
References:
1. Haghnegahdar, L., & Wang, Y. (2019). A whale optimization algorithm-trained artificial neural network for smart grid cyber intrusion detection.
2. Ahmed Mohammed Fahad, Abdulghani Ali Ahmed, Mohd Nizam Mohmad Kahar. Network Intrusion Detection Framework Based on Whale Swarm Algorithm and Artificial Neural Network in Cloud Computing.
See discussions, stats, and author profiles for this publication at: https://www.researchgate.net/publication/327942748
Network Intrusion Detection Framework Based on Whale Swarm Algorithm
and Artificial Neural Network in Cloud Computing
Chapter · January 2019
DOI: 10.1007/978-3-030-00979-3_6
CITATION
1
READS
26
3 authors:
Some of the authors of this publication are also working on these related projects:
Service Violation Monitoring Model for Detecting and Tracing Bandwidth AbuseView project
examination timetabling problemsView project
Ahmed Fahad
Universiti Malaysia Pahang
7 PUBLICATIONS11CITATIONS
SEE PROFILE
Abdulghani Ali Ahmed
Universiti Malaysia Pahang
37PUBLICATIONS171CITATIONS
SEE PROFILE
Mohd Nizam Mohmad Kahar
Universiti Malaysia Pahang
37PUBLICATIONS244CITATIONS
SEE PROFILE
All content following this page was uploaded by Ahmed Fahad on 22 January 2020.
The user has requested enhancement of the downloaded file.
Network Intrusion Detection Framework Based on Whale Swarm Algorithm
and Artificial Neural Network in Cloud Computing
Chapter · January 2019
DOI: 10.1007/978-3-030-00979-3_6
CITATION
1
READS
26
3 authors:
Some of the authors of this publication are also working on these related projects:
Service Violation Monitoring Model for Detecting and Tracing Bandwidth AbuseView project
examination timetabling problemsView project
Ahmed Fahad
Universiti Malaysia Pahang
7 PUBLICATIONS11CITATIONS
SEE PROFILE
Abdulghani Ali Ahmed
Universiti Malaysia Pahang
37PUBLICATIONS171CITATIONS
SEE PROFILE
Mohd Nizam Mohmad Kahar
Universiti Malaysia Pahang
37PUBLICATIONS244CITATIONS
SEE PROFILE
All content following this page was uploaded by Ahmed Fahad on 22 January 2020.
The user has requested enhancement of the downloaded file.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Intrusion Detection Framework Based on
Whale Swarm Algorithm and Artificial Neural Network
in Cloud Computing
Ahmed Mohammed Fahad, Abdulghani Ali Ahmed, Mohd Nizam Mohmad Kahar
Faculty of Computer Systems & Software Engineering
Universiti Malaysia Pahang, 26300, Kuantan, Malaysia
{ahmedsipher2010@yahoo.com,abdulghani@ump.edu.my,
mnizam@ump.edu.my}
Abstract. Cloud computing is a rapidly developing Internet technology for
facilitating various services to consumers. This technology suggests a
considerable potential to the public or to large companies, such as Amazon,
Google, Microsoft and IBM. This technology is aimed at providing a flexible IT
architecture which is accessible through the Internet for lightweight portability.
However, many issues must be resolved before cloud computing can be
accepted as a viable option to business computing. Cloud computing undergoes
several challenges in security because it is prone to numerous attacks, such as
flooding attacks which are the major problems in cloud computing and one of
the serious threat to cloud computing originates came from denial of service.
This research is aimed at exploring the mechanisms or models that can detect
attacks. Intrusion detection system is a detection model for these attacks and is
divided into two-type H-IDS and N-IDS. We focus on the N-IDS in Eucalyptus
cloud computing to detect DDoS attacks, such as UDP and TCP, to evaluate the
output dataset in MATLAB. Therefore, all technology reviews will be solely
based on network traffic data. Furthermore, the H-IDS is disregarded in this
work.
Keywords: IDS, WOA, ANN, TUIDS, cloud computing.
1 Introduction
A cloud refers to a distinct IT environment that is designed to remotely provide
scalable and measured IT resources [1]. This term originated as a metaphor for the
Internet, which is a network of networks that provide a remote access to a set of
decentralised IT resources [2]. The symbol of a cloud is commonly used to represent
the Internet in various specifications and mainstream documentations of web-based
architectures before cloud computing has become a formalised IT industry sector [3].
Figure 1, illustrates the importance of cloud computing in remote services and virtual
desktop applications [4].
Whale Swarm Algorithm and Artificial Neural Network
in Cloud Computing
Ahmed Mohammed Fahad, Abdulghani Ali Ahmed, Mohd Nizam Mohmad Kahar
Faculty of Computer Systems & Software Engineering
Universiti Malaysia Pahang, 26300, Kuantan, Malaysia
{ahmedsipher2010@yahoo.com,abdulghani@ump.edu.my,
mnizam@ump.edu.my}
Abstract. Cloud computing is a rapidly developing Internet technology for
facilitating various services to consumers. This technology suggests a
considerable potential to the public or to large companies, such as Amazon,
Google, Microsoft and IBM. This technology is aimed at providing a flexible IT
architecture which is accessible through the Internet for lightweight portability.
However, many issues must be resolved before cloud computing can be
accepted as a viable option to business computing. Cloud computing undergoes
several challenges in security because it is prone to numerous attacks, such as
flooding attacks which are the major problems in cloud computing and one of
the serious threat to cloud computing originates came from denial of service.
This research is aimed at exploring the mechanisms or models that can detect
attacks. Intrusion detection system is a detection model for these attacks and is
divided into two-type H-IDS and N-IDS. We focus on the N-IDS in Eucalyptus
cloud computing to detect DDoS attacks, such as UDP and TCP, to evaluate the
output dataset in MATLAB. Therefore, all technology reviews will be solely
based on network traffic data. Furthermore, the H-IDS is disregarded in this
work.
Keywords: IDS, WOA, ANN, TUIDS, cloud computing.
1 Introduction
A cloud refers to a distinct IT environment that is designed to remotely provide
scalable and measured IT resources [1]. This term originated as a metaphor for the
Internet, which is a network of networks that provide a remote access to a set of
decentralised IT resources [2]. The symbol of a cloud is commonly used to represent
the Internet in various specifications and mainstream documentations of web-based
architectures before cloud computing has become a formalised IT industry sector [3].
Figure 1, illustrates the importance of cloud computing in remote services and virtual
desktop applications [4].

Fig. 1. Cloud computing.
A crucial aspect of cloud security is detecting DDoS attacks [5]. and intrusions that
disrupt the resources of end-users or organisations [6]. An N-IDS can detect these
types of attacks. However, the N-IDS in cloud computing is irrelevant if the attack
classifier is inaccurately written [7]. A DDoS classifier in machine learning is neural
networks. Several important studies have proposed various ANN-based machine
learning classifiers against DDoS in cloud computing [8]. However, considerable
attention for accurate classification and reduction of false alarms remains necessary
[9]. Hence, this work is aimed at proposing a new model, namely, WOA-ANN, to
detect UDP/TCP flooding attacks in the N-IDS in cloud computing. To reduce the
false alarm of the N-IDS system, the WOA-ANN model is used to enhance the
accuracy of the N-IDS by improving the analysis of network traffic which will be
generated by our cloud testbed. We compare the proposed model with existing works
using MATLAB to evaluate and compare their efficiency. At the 2014 Black Hat
conference, a pair of testers from Bishop Fox demonstrated the pooling of a free-tier
public cloud service VM into a mini botnet that could mine bitcoin cryptocurrencies
and potentially perform DDoS or password cracking [10]. Moreover, the qualities that
make the public VM useful, that is, scalability, ease-of-use and stewardship by high-
profile vendors, make this technology an ideal platform for staging DDoS attacks[11].
2. Proposed Framework
Whales are the largest mammals in the world. An adult whale typically measures
30 m in length [12]. Several whale species include killer, Minke, Sei, humpback,
right, finback and blue. Whales, as a predator, never sleep because they breathe on the
ocean surface. These animals are intelligent and show emotions. Hof and Van Der
Gucht highlighted that whales have brain cells, namely, spindle cells, in which are
common in humans. These cells control emotions and social behaviours in humans.
The number of spindle cells in whales is twice as much as that in an adult human;
therefore, whales can think, learn, judge and communicate. For example, killer whales
can create their own dialect.
A crucial aspect of cloud security is detecting DDoS attacks [5]. and intrusions that
disrupt the resources of end-users or organisations [6]. An N-IDS can detect these
types of attacks. However, the N-IDS in cloud computing is irrelevant if the attack
classifier is inaccurately written [7]. A DDoS classifier in machine learning is neural
networks. Several important studies have proposed various ANN-based machine
learning classifiers against DDoS in cloud computing [8]. However, considerable
attention for accurate classification and reduction of false alarms remains necessary
[9]. Hence, this work is aimed at proposing a new model, namely, WOA-ANN, to
detect UDP/TCP flooding attacks in the N-IDS in cloud computing. To reduce the
false alarm of the N-IDS system, the WOA-ANN model is used to enhance the
accuracy of the N-IDS by improving the analysis of network traffic which will be
generated by our cloud testbed. We compare the proposed model with existing works
using MATLAB to evaluate and compare their efficiency. At the 2014 Black Hat
conference, a pair of testers from Bishop Fox demonstrated the pooling of a free-tier
public cloud service VM into a mini botnet that could mine bitcoin cryptocurrencies
and potentially perform DDoS or password cracking [10]. Moreover, the qualities that
make the public VM useful, that is, scalability, ease-of-use and stewardship by high-
profile vendors, make this technology an ideal platform for staging DDoS attacks[11].
2. Proposed Framework
Whales are the largest mammals in the world. An adult whale typically measures
30 m in length [12]. Several whale species include killer, Minke, Sei, humpback,
right, finback and blue. Whales, as a predator, never sleep because they breathe on the
ocean surface. These animals are intelligent and show emotions. Hof and Van Der
Gucht highlighted that whales have brain cells, namely, spindle cells, in which are
common in humans. These cells control emotions and social behaviours in humans.
The number of spindle cells in whales is twice as much as that in an adult human;
therefore, whales can think, learn, judge and communicate. For example, killer whales
can create their own dialect.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Most whales live in groups. A killer whale can live in a group in its lifetime [13].
Figure 2 exhibits the largest baleen whale called humpback. Its size is comparable to
that of a school bus. It typical preys on krill and small fish herds [14]. Its hunting
method is called bubble-net feeding in which it hunts preys that are close to the
surface. This method is accomplished by creating distinctive bubbles along a circle or
a ‘9’-shaped path. Goldbogen et al. studied this interesting behaviour using tag
sensors. A total of 300 tag-derived bubble-net feeding events were captured. These
authors discovered that whales use ‘upward-spiral’ and ‘double-loop’ manoeuvre
patterns.
For the ‘upward-spiral’ pattern, humpback whales dive 12 m below the surface
and create bubbles in a spiral shape around the prey. Subsequently, they swim up
towards the ocean surface. The latter pattern consists of three stages: coral loop, lob
tail and capture loop. In the current work, this unique spiral bubble-net feeding
manoeuvre pattern was used for optimisation.
Fig. 2. WOA and bubble movement.
The mathematical models of encircling preys, spiral bubble-net feeding manoeuvre
and searching for preys were outlined. The WOA algorithm was then reported.
Humpback whales are aware of the location of their preys whilst hunting. The current
best candidate solution is assumed as the target prey in the WOA algorithm because
the location of the optimal design in the search space is unknown. The positions of
other search agents are updated by defining the optimal search agent. This behaviour
can be explained by the following equations:
*
( 1) ( ) .X t X t B S (1)
*
. ( ) ( )S K X t X t (2)
where t is the current iteration, and are the coefficient vectors, is the position
vector of the current best solution obtained and is the position vector. Here, is
updated after iterations and are computed as
2 .B b r b (3)
Figure 2 exhibits the largest baleen whale called humpback. Its size is comparable to
that of a school bus. It typical preys on krill and small fish herds [14]. Its hunting
method is called bubble-net feeding in which it hunts preys that are close to the
surface. This method is accomplished by creating distinctive bubbles along a circle or
a ‘9’-shaped path. Goldbogen et al. studied this interesting behaviour using tag
sensors. A total of 300 tag-derived bubble-net feeding events were captured. These
authors discovered that whales use ‘upward-spiral’ and ‘double-loop’ manoeuvre
patterns.
For the ‘upward-spiral’ pattern, humpback whales dive 12 m below the surface
and create bubbles in a spiral shape around the prey. Subsequently, they swim up
towards the ocean surface. The latter pattern consists of three stages: coral loop, lob
tail and capture loop. In the current work, this unique spiral bubble-net feeding
manoeuvre pattern was used for optimisation.
Fig. 2. WOA and bubble movement.
The mathematical models of encircling preys, spiral bubble-net feeding manoeuvre
and searching for preys were outlined. The WOA algorithm was then reported.
Humpback whales are aware of the location of their preys whilst hunting. The current
best candidate solution is assumed as the target prey in the WOA algorithm because
the location of the optimal design in the search space is unknown. The positions of
other search agents are updated by defining the optimal search agent. This behaviour
can be explained by the following equations:
*
( 1) ( ) .X t X t B S (1)
*
. ( ) ( )S K X t X t (2)
where t is the current iteration, and are the coefficient vectors, is the position
vector of the current best solution obtained and is the position vector. Here, is
updated after iterations and are computed as
2 .B b r b (3)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
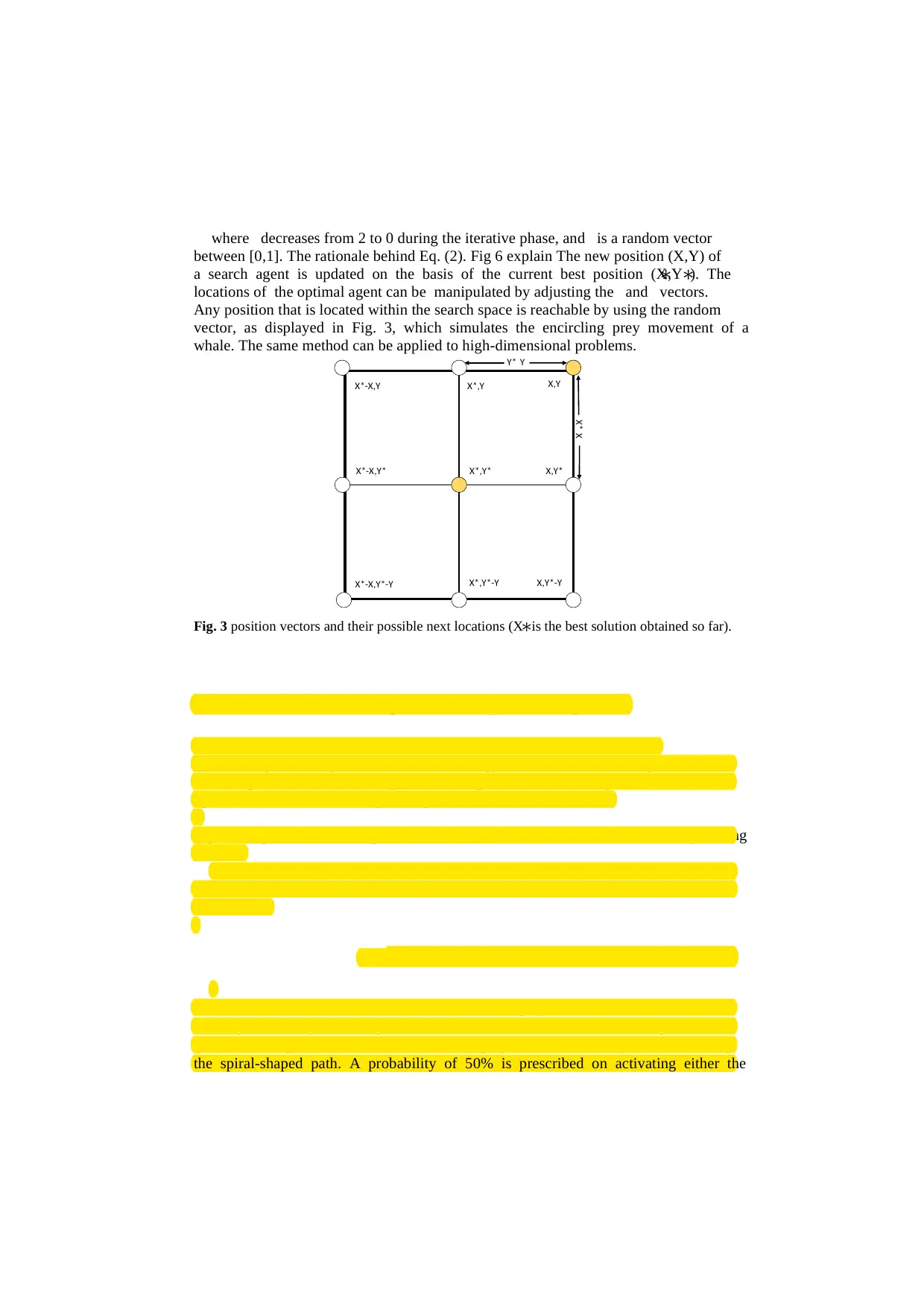
where decreases from 2 to 0 during the iterative phase, and is a random vector
between [0,1]. The rationale behind Eq. (2). Fig 6 explain The new position (X,Y) of
a search agent is updated on the basis of the current best position (X∗,Y∗). The
locations of the optimal agent can be manipulated by adjusting the and vectors.
Any position that is located within the search space is reachable by using the random
vector, as displayed in Fig. 3, which simulates the encircling prey movement of a
whale. The same method can be applied to high-dimensional problems.
X* X
Y* Y
X*-X,Y
X*-X,Y*
X*-X,Y*-Y
X*,Y*
X*,Y*-Y X,Y*-Y
X,Y*
X*,Y X,Y
Fig. 3 position vectors and their possible next locations (X∗is the best solution obtained so far).
2.1 Bubble-net attacking method (exploitation phase)
The bubble-net strategy can be performed using the following approaches:
1. Shrinking encircling mechanism: This strategy is achieved via reducing the value
of in Eq. (1) from 2 to 0 during the iterative procedure. The new position of a search
agent can then be identified by setting the random values in [−1,1].
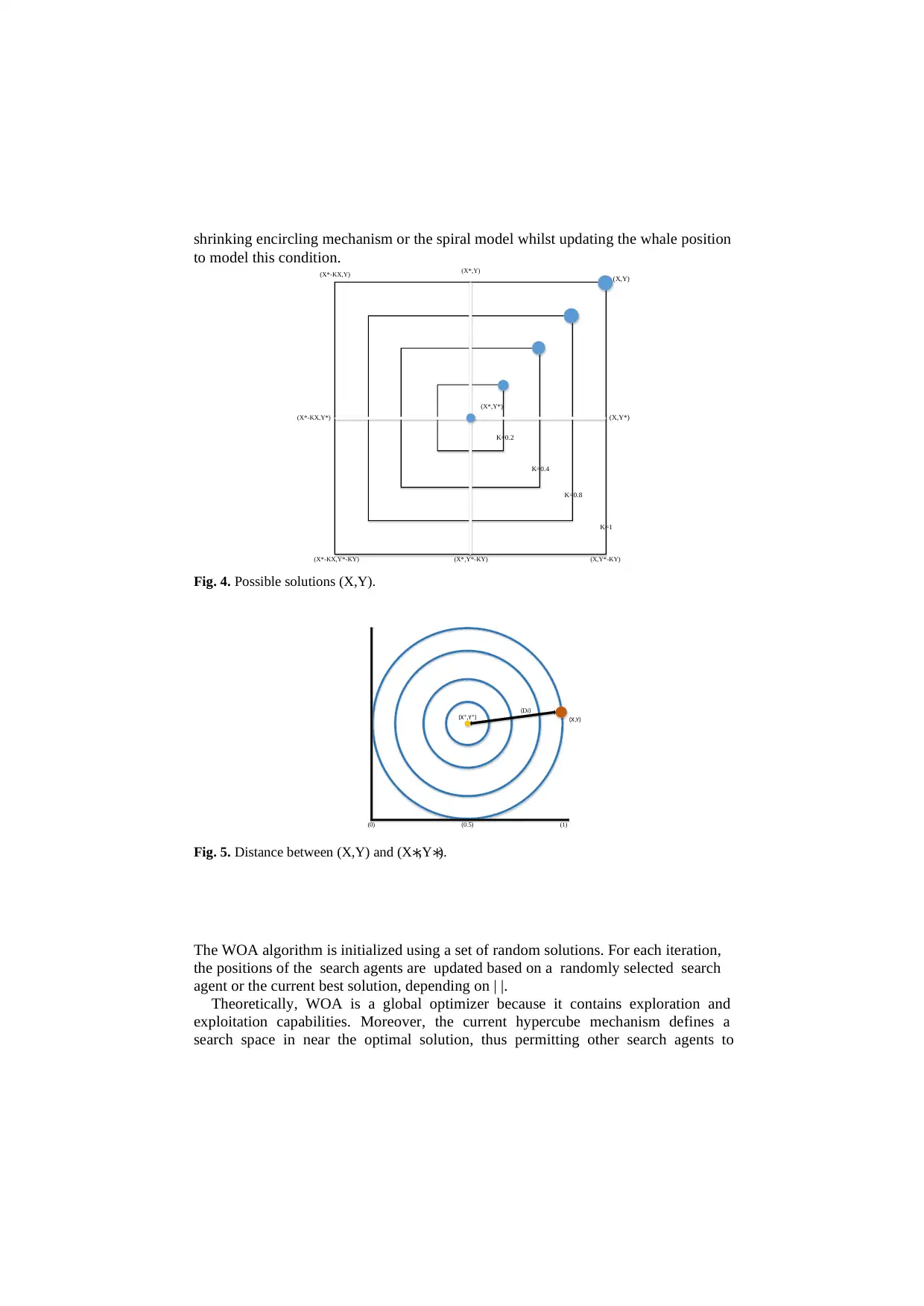
Figure 4, presents several possible solutions (X,Y) that can be obtained by setting
0≤K≤1.
2. Spiral updating position: In Figure 8, the distance between (X,Y) and (X ∗,Y∗) is
calculated first. A spiral equation is then established to represent the helix-shaped
movement.:
*
( 1) . .cos(2 ) ( )ml
X t S e l X t . (4)
where indicates the distance of the ith whale to the prey, m is a constant that defines
the shape of the logarithmic spiral and l is a random number within the range [−1,1]. In
general, a humpback whale swims around the prey within a shrinking circle, following
the spiral-shaped path. A probability of 50% is prescribed on activating either the
between [0,1]. The rationale behind Eq. (2). Fig 6 explain The new position (X,Y) of
a search agent is updated on the basis of the current best position (X∗,Y∗). The
locations of the optimal agent can be manipulated by adjusting the and vectors.
Any position that is located within the search space is reachable by using the random
vector, as displayed in Fig. 3, which simulates the encircling prey movement of a
whale. The same method can be applied to high-dimensional problems.
X* X
Y* Y
X*-X,Y
X*-X,Y*
X*-X,Y*-Y
X*,Y*
X*,Y*-Y X,Y*-Y
X,Y*
X*,Y X,Y
Fig. 3 position vectors and their possible next locations (X∗is the best solution obtained so far).
2.1 Bubble-net attacking method (exploitation phase)
The bubble-net strategy can be performed using the following approaches:
1. Shrinking encircling mechanism: This strategy is achieved via reducing the value
of in Eq. (1) from 2 to 0 during the iterative procedure. The new position of a search
agent can then be identified by setting the random values in [−1,1].
Figure 4, presents several possible solutions (X,Y) that can be obtained by setting
0≤K≤1.
2. Spiral updating position: In Figure 8, the distance between (X,Y) and (X ∗,Y∗) is
calculated first. A spiral equation is then established to represent the helix-shaped
movement.:
*
( 1) . .cos(2 ) ( )ml
X t S e l X t . (4)
where indicates the distance of the ith whale to the prey, m is a constant that defines
the shape of the logarithmic spiral and l is a random number within the range [−1,1]. In
general, a humpback whale swims around the prey within a shrinking circle, following
the spiral-shaped path. A probability of 50% is prescribed on activating either the
shrinking encircling mechanism or the spiral model whilst updating the whale position
to model this condition.
(X*,Y*)
K=0.2
K=0.4
K=0.8
K=1
(X,Y)
(X*,Y)
(X*-KX,Y)
(X*-KX,Y*)
(X*-KX,Y*-KY) (X*,Y*-KY) (X,Y*-KY)
(X,Y*)
Fig. 4. Possible solutions (X,Y).
(X*,Y*) (X,Y)
(Di)
(0) (0.5) (1)
Fig. 5. Distance between (X,Y) and (X∗,Y∗).
The WOA algorithm is initialized using a set of random solutions. For each iteration,
the positions of the search agents are updated based on a randomly selected search
agent or the current best solution, depending on | |.
Theoretically, WOA is a global optimizer because it contains exploration and
exploitation capabilities. Moreover, the current hypercube mechanism defines a
search space in near the optimal solution, thus permitting other search agents to
to model this condition.
(X*,Y*)
K=0.2
K=0.4
K=0.8
K=1
(X,Y)
(X*,Y)
(X*-KX,Y)
(X*-KX,Y*)
(X*-KX,Y*-KY) (X*,Y*-KY) (X,Y*-KY)
(X,Y*)
Fig. 4. Possible solutions (X,Y).
(X*,Y*) (X,Y)
(Di)
(0) (0.5) (1)
Fig. 5. Distance between (X,Y) and (X∗,Y∗).
The WOA algorithm is initialized using a set of random solutions. For each iteration,
the positions of the search agents are updated based on a randomly selected search
agent or the current best solution, depending on | |.
Theoretically, WOA is a global optimizer because it contains exploration and
exploitation capabilities. Moreover, the current hypercube mechanism defines a
search space in near the optimal solution, thus permitting other search agents to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

search for the current best record within the domain. The mathematical model of the
adaptive version of the WOA algorithm is
( 1)X t
*
*
( ) . 0.5
. cos(2 ) ( ) 0.5
{ ml
X t B S if
S e l X t if
(5)
where is a random number between [0,1]. In certain cases, a humpback whale
searches for a prey randomly.
2.2 Searching for prey (exploration phase)
The method can be adopted by using a similar approach of varying the vector to
search for a prey (i.e. exploration). In the random method, with random values greater
than or less than 1 is used to ensure that each search agent is far from the reference.
Whale. Here, the position is updated randomly in accordance with the randomly
selected search agent. The global search operation in WOA can be performed by
applying this mechanism and setting | | > 1. The corresponding mathematical
model is:
. ( ) ( )randS K X t X t (6)
( 1) ( ) .randX t X t B S (8)
3. Classifier Design
In practice, a smooth transition between exploration and exploitation is feasible. Here,
several iterations are allocated exploration (| | ≥ 1), whereas the remaining iterations
are dedicated for exploitation (| | < 1). In WOA, only two main adjustable internal
parameters are available. The current work considers a simple version of WOA by
neglecting the other evolutionary operations that mimic the real behavior of
humpback whales. Therefore, hybridization with evolutionary search schemes can be
further explored.
The average values obtained from the fitness function are considered those of the
candidate solutions. The value of this fitness function is verified during the iteration
until a new best value is found. The attribute that provides a minimum error value is
selected to complete the selection and evaluation processes. The flow of the proposed
method is as follows:
adaptive version of the WOA algorithm is
( 1)X t
*
*
( ) . 0.5
. cos(2 ) ( ) 0.5
{ ml
X t B S if
S e l X t if
(5)
where is a random number between [0,1]. In certain cases, a humpback whale
searches for a prey randomly.
2.2 Searching for prey (exploration phase)
The method can be adopted by using a similar approach of varying the vector to
search for a prey (i.e. exploration). In the random method, with random values greater
than or less than 1 is used to ensure that each search agent is far from the reference.
Whale. Here, the position is updated randomly in accordance with the randomly
selected search agent. The global search operation in WOA can be performed by
applying this mechanism and setting | | > 1. The corresponding mathematical
model is:
. ( ) ( )randS K X t X t (6)
( 1) ( ) .randX t X t B S (8)
3. Classifier Design
In practice, a smooth transition between exploration and exploitation is feasible. Here,
several iterations are allocated exploration (| | ≥ 1), whereas the remaining iterations
are dedicated for exploitation (| | < 1). In WOA, only two main adjustable internal
parameters are available. The current work considers a simple version of WOA by
neglecting the other evolutionary operations that mimic the real behavior of
humpback whales. Therefore, hybridization with evolutionary search schemes can be
further explored.
The average values obtained from the fitness function are considered those of the
candidate solutions. The value of this fitness function is verified during the iteration
until a new best value is found. The attribute that provides a minimum error value is
selected to complete the selection and evaluation processes. The flow of the proposed
method is as follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
E (i) = wTrain. TrainData.E+ wTest.TestData.E (9)
where wTrain and wTest are the heights to be used for training and test data. The
error values obtained from the training and test data will be used to calculate the
fitness function. In the proposed method, wTrain: 0.7 and wTest: 0.3 are considered.
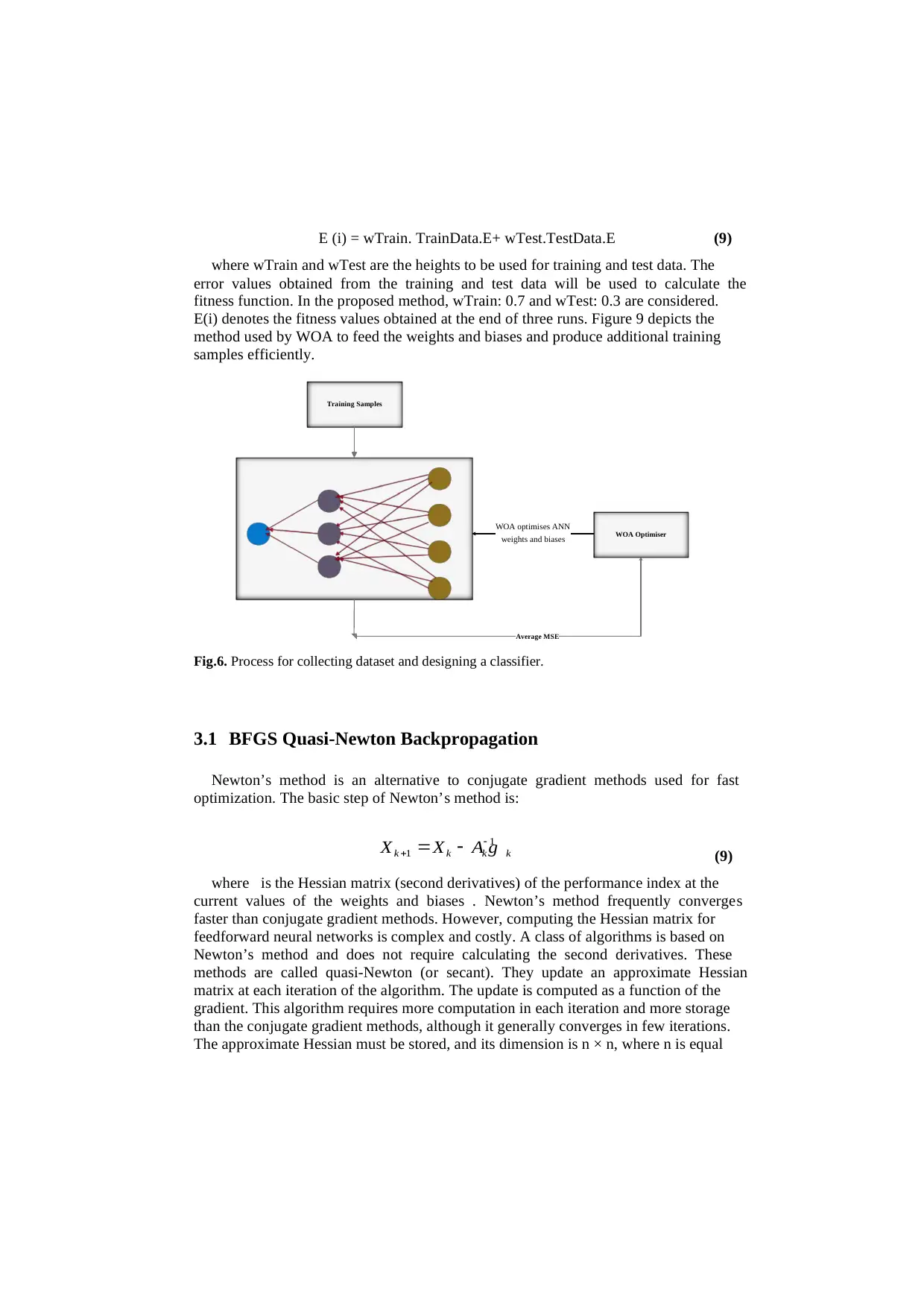
E(i) denotes the fitness values obtained at the end of three runs. Figure 9 depicts the
method used by WOA to feed the weights and biases and produce additional training
samples efficiently.
Training Samples
WOA Optimiser
WOA optimises ANN
weights and biases
Average MSE
Fig.6. Process for collecting dataset and designing a classifier.
3.1 BFGS Quasi-Newton Backpropagation
Newton’s method is an alternative to conjugate gradient methods used for fast
optimization. The basic step of Newton’s method is:
1
1k k k kX X A g
(9)
where is the Hessian matrix (second derivatives) of the performance index at the
current values of the weights and biases . Newton’s method frequently converges
faster than conjugate gradient methods. However, computing the Hessian matrix for
feedforward neural networks is complex and costly. A class of algorithms is based on
Newton’s method and does not require calculating the second derivatives. These
methods are called quasi-Newton (or secant). They update an approximate Hessian
matrix at each iteration of the algorithm. The update is computed as a function of the
gradient. This algorithm requires more computation in each iteration and more storage
than the conjugate gradient methods, although it generally converges in few iterations.
The approximate Hessian must be stored, and its dimension is n × n, where n is equal
where wTrain and wTest are the heights to be used for training and test data. The
error values obtained from the training and test data will be used to calculate the
fitness function. In the proposed method, wTrain: 0.7 and wTest: 0.3 are considered.
E(i) denotes the fitness values obtained at the end of three runs. Figure 9 depicts the
method used by WOA to feed the weights and biases and produce additional training
samples efficiently.
Training Samples
WOA Optimiser
WOA optimises ANN
weights and biases
Average MSE
Fig.6. Process for collecting dataset and designing a classifier.
3.1 BFGS Quasi-Newton Backpropagation
Newton’s method is an alternative to conjugate gradient methods used for fast
optimization. The basic step of Newton’s method is:
1
1k k k kX X A g
(9)
where is the Hessian matrix (second derivatives) of the performance index at the
current values of the weights and biases . Newton’s method frequently converges
faster than conjugate gradient methods. However, computing the Hessian matrix for
feedforward neural networks is complex and costly. A class of algorithms is based on
Newton’s method and does not require calculating the second derivatives. These
methods are called quasi-Newton (or secant). They update an approximate Hessian
matrix at each iteration of the algorithm. The update is computed as a function of the
gradient. This algorithm requires more computation in each iteration and more storage
than the conjugate gradient methods, although it generally converges in few iterations.
The approximate Hessian must be stored, and its dimension is n × n, where n is equal

to the number of weights and biases in the network. For large networks, using the
conjugate gradient algorithms is favorable.
4. Model For N-IDS In-Eucalyptus Cloud Computing
The proposed model is aimed at synthesizing the Eucalyptus cloud as the N-IDS
that analyses the generated traffic and blocks the TCP/UDP flooding and Smurf
DDoS attack. A TUIDS DDoS dataset is prepared using the TUIDS testbed
architecture with a demilitarized zone (DMZ); hosts are divided into several
VLANs, where each VLAN belongs to an L3 or L2 switch inside the network. The
attackers are placed in wired and wireless networks with reflectors, but the target is
placed inside the internal network. The target generates low- and high-rate DDoS
traffics. We consider real-time low- and high-rate DDoS attack scenarios for both
datasets during our experiments. However, a low-rate attack does not consume all
computing resources on the server or bandwidth of the network that connects the
server to the Internet. Hence, a real low-rate DDoS attack scenario contains attack and
attack-free traffics. We mix low-rate attack and legitimate traffics during our
experiment to prepare the real low-rate DDoS attack scenarios in the TUIDS DDoS
dataset.
Fig. 7. New pre-processor rule structure in Eucalyptus cloud computing.
Many experiments have been conducted in this work to empirically demonstrate
the impact of methodological factors, as discussed in Section 4.3.2. The experiments
can be summarized as follows: General observations: exploring classifier performance
and validation methods. Performance on original datasets: providing a benchmark that
is used to compare the results obtained from subsequent experiments. Removing new
attacks from the test set: this experiment is conducted to determine.
conjugate gradient algorithms is favorable.
4. Model For N-IDS In-Eucalyptus Cloud Computing
The proposed model is aimed at synthesizing the Eucalyptus cloud as the N-IDS
that analyses the generated traffic and blocks the TCP/UDP flooding and Smurf
DDoS attack. A TUIDS DDoS dataset is prepared using the TUIDS testbed
architecture with a demilitarized zone (DMZ); hosts are divided into several
VLANs, where each VLAN belongs to an L3 or L2 switch inside the network. The
attackers are placed in wired and wireless networks with reflectors, but the target is
placed inside the internal network. The target generates low- and high-rate DDoS
traffics. We consider real-time low- and high-rate DDoS attack scenarios for both
datasets during our experiments. However, a low-rate attack does not consume all
computing resources on the server or bandwidth of the network that connects the
server to the Internet. Hence, a real low-rate DDoS attack scenario contains attack and
attack-free traffics. We mix low-rate attack and legitimate traffics during our
experiment to prepare the real low-rate DDoS attack scenarios in the TUIDS DDoS
dataset.
Fig. 7. New pre-processor rule structure in Eucalyptus cloud computing.
Many experiments have been conducted in this work to empirically demonstrate
the impact of methodological factors, as discussed in Section 4.3.2. The experiments
can be summarized as follows: General observations: exploring classifier performance
and validation methods. Performance on original datasets: providing a benchmark that
is used to compare the results obtained from subsequent experiments. Removing new
attacks from the test set: this experiment is conducted to determine.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5. Classifier Process In MATLAB
We offer three specific benefits of classifier combinations. Statistical: if the amount of
training data insufficiently models the hypothesis space with one classifier, then the
combined knowledge of an ensemble of classifiers may reach accurate predictions. 2.
Computational: algorithms can be trapped in local optima and finding the global
optimum may be computationally expensive. However, executing several local search
algorithms from different starting points and combining them may be favorable.
A hybrid classifier is developed in MATLAB using our dataset. First, we must
perform the normalization process for the dataset. Then, the dataset will have been
delivered to the training and testing sets in the following proportions: 70% training
and 30% testing. The target will be TCP, UDP and Smurf attacks. The results are
validated through evaluation which was derived from the machine learning metrics.
Prepare a training dataset
and perform the
normalisation process
MATLAB software
Open Training Dataset
Select custom classifier in
WOA-ANN
Selected Test Options
Results
Cross-validation folds=observation
Prediction error rates, confusion matrices
and model estimators.
Prediction in formation
Fig. 11. WOA classifier test using MATLAB.
6 Conclusions
This work proposes a new classifier design based on a hybrid artificial neural network
and whale swarm algorithm to feed the ANN weights and biases. However, the model
cannot function without a derivative dataset. This dataset is derived from our testbed
design based on a developed TUIDS network topology over the Eucalyptus cloud
computing. In the N-IDS, sensing is used in real time for the normal and upnormal
traffic DDoS attacks through Snort. The log-output from the dataset has been
analyzed in MATLAB.
We offer three specific benefits of classifier combinations. Statistical: if the amount of
training data insufficiently models the hypothesis space with one classifier, then the
combined knowledge of an ensemble of classifiers may reach accurate predictions. 2.
Computational: algorithms can be trapped in local optima and finding the global
optimum may be computationally expensive. However, executing several local search
algorithms from different starting points and combining them may be favorable.
A hybrid classifier is developed in MATLAB using our dataset. First, we must
perform the normalization process for the dataset. Then, the dataset will have been
delivered to the training and testing sets in the following proportions: 70% training
and 30% testing. The target will be TCP, UDP and Smurf attacks. The results are
validated through evaluation which was derived from the machine learning metrics.
Prepare a training dataset
and perform the
normalisation process
MATLAB software
Open Training Dataset
Select custom classifier in
WOA-ANN
Selected Test Options
Results
Cross-validation folds=observation
Prediction error rates, confusion matrices
and model estimators.
Prediction in formation
Fig. 11. WOA classifier test using MATLAB.
6 Conclusions
This work proposes a new classifier design based on a hybrid artificial neural network
and whale swarm algorithm to feed the ANN weights and biases. However, the model
cannot function without a derivative dataset. This dataset is derived from our testbed
design based on a developed TUIDS network topology over the Eucalyptus cloud
computing. In the N-IDS, sensing is used in real time for the normal and upnormal
traffic DDoS attacks through Snort. The log-output from the dataset has been
analyzed in MATLAB.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Acknowledgments
This work was supported by the Faculty of Computer System and Software
Engineering, Universiti Malaysia Pahang under FRGS Grant No. RDU160106 and
RDU Grant No. RDU160365.
References
[1] J. W. Rittinghouse and J. F. Ransome, Cloud computing: implementation,
management, and security. CRC press, 2016.
[2] A. A. Ahmed, A. Jantan, and G. A. Ali, "A potent model for unwanted traffic
detection in QoS network domain," JDCTA, vol. 4, pp. 122-130, 2010.
[3] S. Kaul, K. Sood, and A. Jain, "Cloud Computing and its Emerging Need:
Advantages and Issues," International Journal of Advanced Research in
Computer Science, vol. 8, no. 3, 2017.
[4] N. Sultan, "Cloud computing for education: A new dawn?," International
Journal of Information Management, vol. 30, no. 2, pp. 109-116, 2010.
[5] J. Mirkovic and P. Reiher, "A taxonomy of DDoS attack and DDoS defense
mechanisms," ACM SIGCOMM Computer Communication Review, vol. 34,
no. 2, pp. 39-53, 2004.
[6] O. E. Elejla, A. B. JANTAN, and A. A. AHMED, "THREE LAYERS
APPROACH FOR NETWORK SCANNING DETECTION," Journal of
Theoretical & Applied Information Technology, vol. 70, no. 2, 2014.
[7] A. A. Ahmed, "Investigation model for DDoS attack detection in real-time,"
International Journal of Software Engineering & Computer Sciences
(IJSECS), vol. 1, pp. 93-105, 2015.
[8] A. A. Ahmed, A. Jantan, and T.-C. Wan, "Filtration model for the detection
of malicious traffic in large-scale networks," Computer Communications,
vol. 82, pp. 59-70, 2016.
[9] C. H. Rowland and A. L. Rhodes, "Method and system for reducing the false
alarm rate of network intrusion detection systems," ed: Google Patents, 2011.
[10] M. Nanavati, P. Colp, B. Aiello, and A. Warfield, "Cloud security: a
gathering storm," Commun. ACM, vol. 57, no. 5, pp. 70-79, 2014.
[11] A. A. Ahmed, A. S. Sadiq, and M. F. Zolkipli, "Traceback model for
identifying sources of distributed attacks in real time," Security and
Communication Networks, vol. 9, no. 13, pp. 2173-2185, 2016.
[12] S. Mirjalili and A. Lewis, "The Whale Optimization Algorithm," Advances
in Engineering Software, vol. 95, no. Supplement C, pp. 51-67, 2016/05/01/
2016.
[13] S. Mirjalili and A. Lewis, "The whale optimization algorithm," Advances in
Engineering Software, vol. 95, pp. 51-67, 2016.
[14] I. Aljarah, H. Faris, and S. Mirjalili, "Optimizing connection weights in
neural networks using the whale optimization algorithm," Soft Computing,
vol. 22, no. 1, pp. 1-15, 2018.
View publication statsView publication stats
This work was supported by the Faculty of Computer System and Software
Engineering, Universiti Malaysia Pahang under FRGS Grant No. RDU160106 and
RDU Grant No. RDU160365.
References
[1] J. W. Rittinghouse and J. F. Ransome, Cloud computing: implementation,
management, and security. CRC press, 2016.
[2] A. A. Ahmed, A. Jantan, and G. A. Ali, "A potent model for unwanted traffic
detection in QoS network domain," JDCTA, vol. 4, pp. 122-130, 2010.
[3] S. Kaul, K. Sood, and A. Jain, "Cloud Computing and its Emerging Need:
Advantages and Issues," International Journal of Advanced Research in
Computer Science, vol. 8, no. 3, 2017.
[4] N. Sultan, "Cloud computing for education: A new dawn?," International
Journal of Information Management, vol. 30, no. 2, pp. 109-116, 2010.
[5] J. Mirkovic and P. Reiher, "A taxonomy of DDoS attack and DDoS defense
mechanisms," ACM SIGCOMM Computer Communication Review, vol. 34,
no. 2, pp. 39-53, 2004.
[6] O. E. Elejla, A. B. JANTAN, and A. A. AHMED, "THREE LAYERS
APPROACH FOR NETWORK SCANNING DETECTION," Journal of
Theoretical & Applied Information Technology, vol. 70, no. 2, 2014.
[7] A. A. Ahmed, "Investigation model for DDoS attack detection in real-time,"
International Journal of Software Engineering & Computer Sciences
(IJSECS), vol. 1, pp. 93-105, 2015.
[8] A. A. Ahmed, A. Jantan, and T.-C. Wan, "Filtration model for the detection
of malicious traffic in large-scale networks," Computer Communications,
vol. 82, pp. 59-70, 2016.
[9] C. H. Rowland and A. L. Rhodes, "Method and system for reducing the false
alarm rate of network intrusion detection systems," ed: Google Patents, 2011.
[10] M. Nanavati, P. Colp, B. Aiello, and A. Warfield, "Cloud security: a
gathering storm," Commun. ACM, vol. 57, no. 5, pp. 70-79, 2014.
[11] A. A. Ahmed, A. S. Sadiq, and M. F. Zolkipli, "Traceback model for
identifying sources of distributed attacks in real time," Security and
Communication Networks, vol. 9, no. 13, pp. 2173-2185, 2016.
[12] S. Mirjalili and A. Lewis, "The Whale Optimization Algorithm," Advances
in Engineering Software, vol. 95, no. Supplement C, pp. 51-67, 2016/05/01/
2016.
[13] S. Mirjalili and A. Lewis, "The whale optimization algorithm," Advances in
Engineering Software, vol. 95, pp. 51-67, 2016.
[14] I. Aljarah, H. Faris, and S. Mirjalili, "Optimizing connection weights in
neural networks using the whale optimization algorithm," Soft Computing,
vol. 22, no. 1, pp. 1-15, 2018.
View publication statsView publication stats
1 out of 11
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
