Windows Network Services Proposal for IMI and Media Guru Group
VerifiedAdded on 2019/10/30
|20
|3936
|338
Report
AI Summary
This document presents a comprehensive proposal for establishing secure Windows network services, focusing on the integration of two companies, IMI and Media Guru Group. It details the importance of network security, especially in data-intensive environments, and outlines key components of a robust network infrastructure. The proposal covers server configuration, including planning and setup, managing server settings, and configuring IP addresses. It emphasizes the installation and configuration of Active Directory, including assigning computers to the server, utilizing Active Directory Certificate Services, Federation Services, and Rights Management Services. The report also addresses antivirus installation, focusing on Windows Security Essentials and Microsoft Endpoint Protection. Furthermore, it explains firewall creation and the implementation of DHCP and DNS for network management. The proposal includes diagrams and considerations for disaster recovery, high availability, and security services, concluding with a detailed overview of the proposed network design and its benefits.

WINDOWS NETWORK SERVICES PROPOSAL
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
SL.NO TITLE PG.NO
1 INTRODUCTION 3
2 ABOUT INTERNATIONAL MARKING, IN (IMI) 3
3 OBJECTIVE OF THE DOCUMENT 4
4 BACKGROUND OF THE DOCUMENT 4
5 SERVER-CONFIGURATION 4
6 ACTIVE DIRECTORY INSTALLATION 7
7 ANTIVIRUS INSTALLATION 9
8 FIREWALL CREATION 12
9 DHCP AND DNS 12
10 GENERAL INSTALLATION 13
11 SOFTWARE SUPPORT RESPONSIBILITY 14
12 APPLICATION LICENSES 14
13 APPLICATION TRAFFIC FLOW 14
14 EQUIPMENT INSTALLATION 15
15 OS SUPPORT 15
16 FILE AND STORAGE LOCATION 16
17 DISASTER RECOVERY 17
18 HIGH AVAILABILITY 18
19 SECURITY SERVICE AND SERVICE DETAILS 18
20 CONCLUSION 19
REFERENCES 21
1. INTRODUCTION
SL.NO TITLE PG.NO
1 INTRODUCTION 3
2 ABOUT INTERNATIONAL MARKING, IN (IMI) 3
3 OBJECTIVE OF THE DOCUMENT 4
4 BACKGROUND OF THE DOCUMENT 4
5 SERVER-CONFIGURATION 4
6 ACTIVE DIRECTORY INSTALLATION 7
7 ANTIVIRUS INSTALLATION 9
8 FIREWALL CREATION 12
9 DHCP AND DNS 12
10 GENERAL INSTALLATION 13
11 SOFTWARE SUPPORT RESPONSIBILITY 14
12 APPLICATION LICENSES 14
13 APPLICATION TRAFFIC FLOW 14
14 EQUIPMENT INSTALLATION 15
15 OS SUPPORT 15
16 FILE AND STORAGE LOCATION 16
17 DISASTER RECOVERY 17
18 HIGH AVAILABILITY 18
19 SECURITY SERVICE AND SERVICE DETAILS 18
20 CONCLUSION 19
REFERENCES 21
1. INTRODUCTION

Generally, whenever restructuring or constructing a network for an organization, a different
always takes place. The main areas were these changes experienced in an organization, which
manages is data i.e. information systems. Right from the top hierarchy to the lower department of
the organization covers a data; all had their information that should be maintained. Any error in
the system will always cause an extreme disturbance to the events of the complete organization.
Combining two companies remotely need high security in order to avoid intrusions like a virus,
unwanted access, threat etc. Constructing a secure design module for remote network between
two companies needs a proper secure design, which helps both the companies from data loss,
avoid collision and minimize workload by providing separate access to each department. Each
department in an organization remain independent and private i.e. data from one department
cannot be accessed or viewed by another department. Some access policy has to set to access
data between employees. This paper outlines a proposal that will ensure that there are no errors
in the organization’s network system, particularly in the Active Directory Configuration. It also
provides a faultless structure of how links between IMI head office in Houston, TX which works
on windows server 2012 level, can be securely established with Media Guru Group based out of
Richmond, VA which works on windows server 2003 (Microsoft, 2018).
2. ABOUT INTERNATIONAL MARKING, IN (IMI)
IMI has two sites, one in Houston, TX and another one in Richmond VA. Executives can
manage and run their company. Account section performs market research work and account
maintenance. Media department handle advertising, HR perform HR and financial, etc. This
makes a necessary to safeguard compatibility on configuration structures by producing media,
which will ensure the variance on the configuration that does not cause any failure. There are
totally 110 employees in both Houston and Richmond sites. There is executives department to
always takes place. The main areas were these changes experienced in an organization, which
manages is data i.e. information systems. Right from the top hierarchy to the lower department of
the organization covers a data; all had their information that should be maintained. Any error in
the system will always cause an extreme disturbance to the events of the complete organization.
Combining two companies remotely need high security in order to avoid intrusions like a virus,
unwanted access, threat etc. Constructing a secure design module for remote network between
two companies needs a proper secure design, which helps both the companies from data loss,
avoid collision and minimize workload by providing separate access to each department. Each
department in an organization remain independent and private i.e. data from one department
cannot be accessed or viewed by another department. Some access policy has to set to access
data between employees. This paper outlines a proposal that will ensure that there are no errors
in the organization’s network system, particularly in the Active Directory Configuration. It also
provides a faultless structure of how links between IMI head office in Houston, TX which works
on windows server 2012 level, can be securely established with Media Guru Group based out of
Richmond, VA which works on windows server 2003 (Microsoft, 2018).
2. ABOUT INTERNATIONAL MARKING, IN (IMI)
IMI has two sites, one in Houston, TX and another one in Richmond VA. Executives can
manage and run their company. Account section performs market research work and account
maintenance. Media department handle advertising, HR perform HR and financial, etc. This
makes a necessary to safeguard compatibility on configuration structures by producing media,
which will ensure the variance on the configuration that does not cause any failure. There are
totally 110 employees in both Houston and Richmond sites. There is executives department to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

manage and run the company, account and sales department for performing marketing research
and maintaining accounts, creative, media and production department for advertising, Human
Resources and finances department for performing HR duties, IT department is for managing the
IT for the company. There are separate Active directory domains for network equipment setup
and security mechanisms like firewall, intrusion detection system are used to handle some
vulnerable activities. But all the data cannot be protected by using the firewall and intrusion
detection system. Additional methods are required to protect the data. The aim of this is to build
an interface where communication takes place.
3. OBJECTIVE OF THE DOCUMENT
The objective of the document is to create a network design for the newly started
Company Richmond, VA and to protect the data from all the vulnerable activities. The document
contains the requirements that the design should follow windows server 2012.
4. BACKGROUND OF THE DOCUMENT
The background of the document contains Server installation –windows server 2012, how to
configure server, Active Directory installation, Assign employee system to the server, Antivirus
installation, firewall installation.
5. SERVER-CONFIGURATION
Server configuration ensures how to integrate with a newly joined company with the
existing factor. For increasing business growth and a number of employees that results in
expanding of the server to store data and run the application. Virtualization technology operates
the OS in same similar physical hardware (Microsoft, 2018).
and maintaining accounts, creative, media and production department for advertising, Human
Resources and finances department for performing HR duties, IT department is for managing the
IT for the company. There are separate Active directory domains for network equipment setup
and security mechanisms like firewall, intrusion detection system are used to handle some
vulnerable activities. But all the data cannot be protected by using the firewall and intrusion
detection system. Additional methods are required to protect the data. The aim of this is to build
an interface where communication takes place.
3. OBJECTIVE OF THE DOCUMENT
The objective of the document is to create a network design for the newly started
Company Richmond, VA and to protect the data from all the vulnerable activities. The document
contains the requirements that the design should follow windows server 2012.
4. BACKGROUND OF THE DOCUMENT
The background of the document contains Server installation –windows server 2012, how to
configure server, Active Directory installation, Assign employee system to the server, Antivirus
installation, firewall installation.
5. SERVER-CONFIGURATION
Server configuration ensures how to integrate with a newly joined company with the
existing factor. For increasing business growth and a number of employees that results in
expanding of the server to store data and run the application. Virtualization technology operates
the OS in same similar physical hardware (Microsoft, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5.1 PLANNING INSTALLATION
In order to install a server operating system a proper plan has to ensure where a right
hardware to be placed. The processor has to check because windows server 2012 will run only
on a 64-bit processor. Two versions of the operating system are standard and datacenter. Both
are similar but the difference in maintenance of hardware and guest virtual machines (Techradar,
2013).
5.2 SET-UP
Initial set-up provides implanting disc into the computer and switch on the server.
Booting system will start to load the software by getting common details like language currency,
time and installation starts (Techradar, 2013).
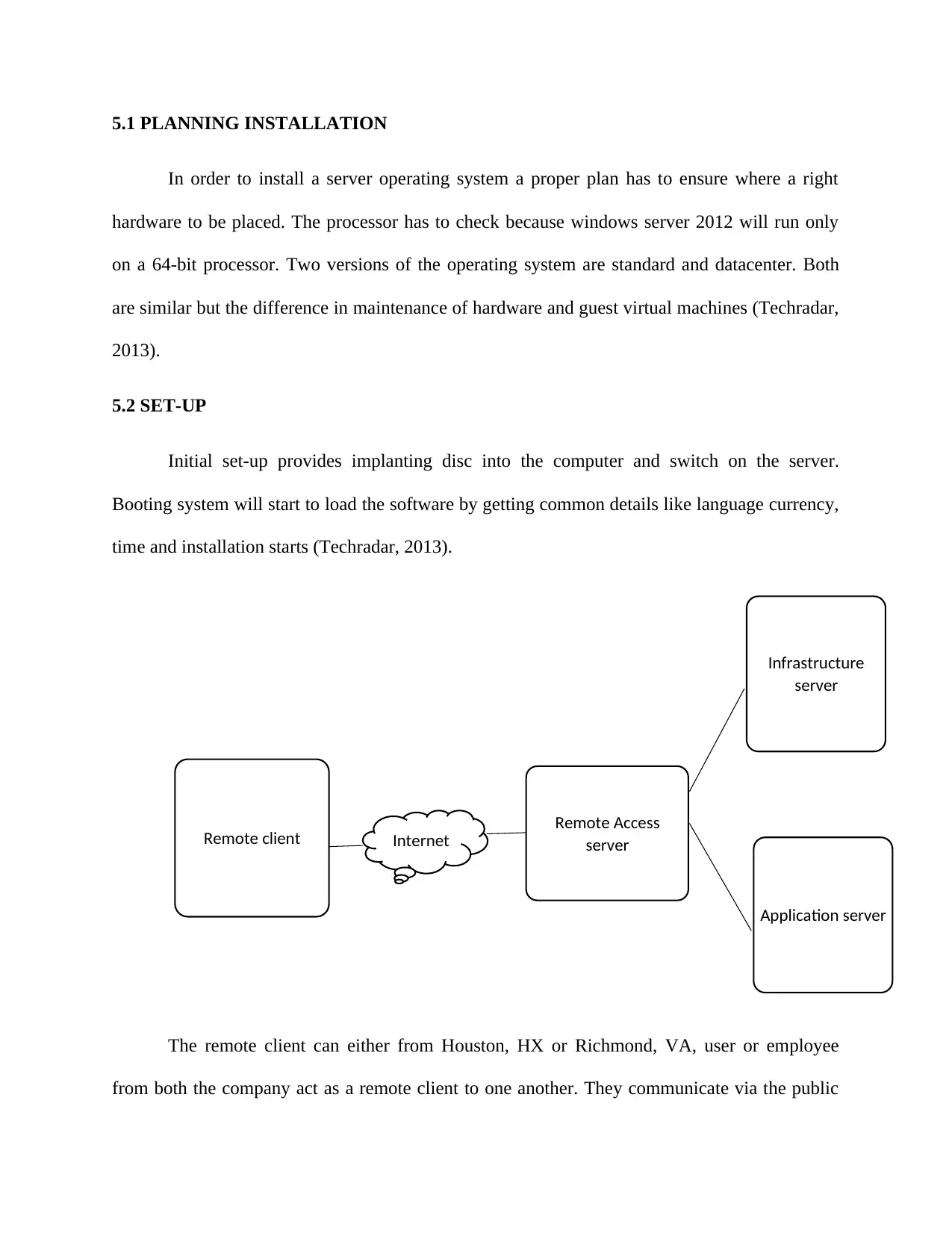
The remote client can either from Houston, HX or Richmond, VA, user or employee
from both the company act as a remote client to one another. They communicate via the public
Remote client Internet
Remote Access
server
Infrastructure
server
Application server
In order to install a server operating system a proper plan has to ensure where a right
hardware to be placed. The processor has to check because windows server 2012 will run only
on a 64-bit processor. Two versions of the operating system are standard and datacenter. Both
are similar but the difference in maintenance of hardware and guest virtual machines (Techradar,
2013).
5.2 SET-UP
Initial set-up provides implanting disc into the computer and switch on the server.
Booting system will start to load the software by getting common details like language currency,
time and installation starts (Techradar, 2013).
The remote client can either from Houston, HX or Richmond, VA, user or employee
from both the company act as a remote client to one another. They communicate via the public
Remote client Internet
Remote Access
server
Infrastructure
server
Application server

internet using a server; both can access the server remotely using its userID and password. Server
consist of infrastructure server and application server where infrastructure server secure the
traffic on the network by monitoring virus and firewall whereas application server will used to
access application related events like database access, network access to communicate etc
(Techradar, 2013).
5.3 SERVER MANAGE AND CHANGING COMPUTER NAME
On installing server and windows operating system on a system, managing server a login
access has to be done which requires Admin password to access. Server manage tab has a server
event which changes from a UI to desktop mode and click Configure this local server on server
managing window. In addition, each server has its own name and renaming is possible, this can
be done at change server name. This allows restarting system (Techradar, 2013).
5.4 CONFIGURATION OF SERVER WITH IP ADDRESS
In order to connect with the network, this server has to set with IP address, default
gateway and DNS. Ethernet will allow configuring on the network and there on double clicking
on adaptor will -help to change address. Internet protocol version4 will allow adding all IP
address (Techradar, 2013)
5.5 MANAGE REMOTELY WITH REMOTE DESKTOP
By setting remote desktop one, can access manage the entire server from another system
i.e. inside or outside of the organization. Set remote desktop entry and select “remote connection
to this computer” to remotely manage the server. If users are expended then by adding a new
user can add to the existing server (Techradar, 2013).
consist of infrastructure server and application server where infrastructure server secure the
traffic on the network by monitoring virus and firewall whereas application server will used to
access application related events like database access, network access to communicate etc
(Techradar, 2013).
5.3 SERVER MANAGE AND CHANGING COMPUTER NAME
On installing server and windows operating system on a system, managing server a login
access has to be done which requires Admin password to access. Server manage tab has a server
event which changes from a UI to desktop mode and click Configure this local server on server
managing window. In addition, each server has its own name and renaming is possible, this can
be done at change server name. This allows restarting system (Techradar, 2013).
5.4 CONFIGURATION OF SERVER WITH IP ADDRESS
In order to connect with the network, this server has to set with IP address, default
gateway and DNS. Ethernet will allow configuring on the network and there on double clicking
on adaptor will -help to change address. Internet protocol version4 will allow adding all IP
address (Techradar, 2013)
5.5 MANAGE REMOTELY WITH REMOTE DESKTOP
By setting remote desktop one, can access manage the entire server from another system
i.e. inside or outside of the organization. Set remote desktop entry and select “remote connection
to this computer” to remotely manage the server. If users are expended then by adding a new
user can add to the existing server (Techradar, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.6 SERVER UPDATE
Server Updating is simple and fast in windows and by keeps on updating will allow the
system to stay fast and managing easily. It gives an automatic update and manual update option
to which and where to install (Techradar, 2013).
5.7 STIMULATE SERVER
Last part of this work is to activate the server, server activation requires a product key and this
allows configuring the server and ready to use.
6. ACTIVE DIRECTORY INSTALLATION
This Active Directory Installation helps the server to assign the agent-managed computer to the
management group. To create Active Directory Domain Service (AD DS) some commands are
used and it contains operations on manager management group. MOMADAdmin.exe is
necessary to install manager management group (Microsoft, 2018).
ManagementGroupName
This has a name of the management group that create an active directory container.
MOMAdminSecurityGroup
This is a security group that has a domain format plays as an admin security role.
<path>\MOMADAdmin.exe
<ManagementGroupName><MOMAdminSecurityGroup><RunAsAccount><Domain>
Server Updating is simple and fast in windows and by keeps on updating will allow the
system to stay fast and managing easily. It gives an automatic update and manual update option
to which and where to install (Techradar, 2013).
5.7 STIMULATE SERVER
Last part of this work is to activate the server, server activation requires a product key and this
allows configuring the server and ready to use.
6. ACTIVE DIRECTORY INSTALLATION
This Active Directory Installation helps the server to assign the agent-managed computer to the
management group. To create Active Directory Domain Service (AD DS) some commands are
used and it contains operations on manager management group. MOMADAdmin.exe is
necessary to install manager management group (Microsoft, 2018).
ManagementGroupName
This has a name of the management group that create an active directory container.
MOMAdminSecurityGroup
This is a security group that has a domain format plays as an admin security role.
<path>\MOMADAdmin.exe
<ManagementGroupName><MOMAdminSecurityGroup><RunAsAccount><Domain>
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RunAsAccount
This allows reading, writing and deleting objects in Active Directory that use domain
format/username.
Domain
It will create a name of the domain when a management group container is generated.
6.1. ASSIGN COMPUTER TO SERVER
Active Directory Domain service used to assign managing server i.e. primary management and
secondary management. This can be created before Agent Assignment and failover wizard. Any
agent cannot deploy both of this so computer agent called MOMAgent.msi can manually deploy
this (Techtarget, 2018).
6.2 ACTIVE DIRECTORY CERTIFICATE SERVICE
Usually, for secure access to network server used to provide public key infrastructure but on a
windows server, it provides Active Directory Certificates Service, which will generate PKI and
provide encryption, Digital signature and digital certificate. This AD CS will handle all the
security-related events in-house. AD CS on this network will use existing information on the
register to generate a certificate and it allows group policy among different departments to
choose which type of certificate to select. Once the system connects to online for the first time a
request sent to active directory to find certificate on which type it should be given to end user
from policy report. Thus, it will automatically renew, add and delete the request upon some
condition (Techtarget, 2018).
This allows reading, writing and deleting objects in Active Directory that use domain
format/username.
Domain
It will create a name of the domain when a management group container is generated.
6.1. ASSIGN COMPUTER TO SERVER
Active Directory Domain service used to assign managing server i.e. primary management and
secondary management. This can be created before Agent Assignment and failover wizard. Any
agent cannot deploy both of this so computer agent called MOMAgent.msi can manually deploy
this (Techtarget, 2018).
6.2 ACTIVE DIRECTORY CERTIFICATE SERVICE
Usually, for secure access to network server used to provide public key infrastructure but on a
windows server, it provides Active Directory Certificates Service, which will generate PKI and
provide encryption, Digital signature and digital certificate. This AD CS will handle all the
security-related events in-house. AD CS on this network will use existing information on the
register to generate a certificate and it allows group policy among different departments to
choose which type of certificate to select. Once the system connects to online for the first time a
request sent to active directory to find certificate on which type it should be given to end user
from policy report. Thus, it will automatically renew, add and delete the request upon some
condition (Techtarget, 2018).

6.3 ACTIVE DIRECTORY FEDERATION SERVICE
Active Directory Federation Service (ADFS) provides the users on windows server a
single sign-on access. It allows the user to the first login, once it is sign-in user ID and password
is saved in the server, which will allow the user to access the computer on its boundaries.
Whenever a third party access occurs on a windows server, it will control the authentication by
checking its record in the federation register (Techtarget, 2018).
6.3 ACTIVE DIRECTORY RIGHT MANAGEMENT SERVICE
Active Directory Right Management Service (AD RMS) will allow the user to manage
the data by protecting using data access policy. Once the user accesses the data remotely using
windows server, RMS will act as a security tool to protect data from unwanted satiation
(Techtarget, 2018).
7. ANTIVIRUS INSTALLATION
Providing security for windows server is an essential part to maintain information on
server and data is being corrupt. Windows security essentials and windows endpoint protection
are used for security.
7.1 WINDOWS SECURITY ESSENTIAL
Configure windows essential on windows server 2012. Download a right .exe file from
the respected website. The right .exe file for security essential is mseinstall.exe. Install this and
once it gets install click compatibility mode in properties where the admin has to check the “Run
this program in compatibility mode for” which will open a command prompt as an admin.
Finally run reinstall from downloads.
Active Directory Federation Service (ADFS) provides the users on windows server a
single sign-on access. It allows the user to the first login, once it is sign-in user ID and password
is saved in the server, which will allow the user to access the computer on its boundaries.
Whenever a third party access occurs on a windows server, it will control the authentication by
checking its record in the federation register (Techtarget, 2018).
6.3 ACTIVE DIRECTORY RIGHT MANAGEMENT SERVICE
Active Directory Right Management Service (AD RMS) will allow the user to manage
the data by protecting using data access policy. Once the user accesses the data remotely using
windows server, RMS will act as a security tool to protect data from unwanted satiation
(Techtarget, 2018).
7. ANTIVIRUS INSTALLATION
Providing security for windows server is an essential part to maintain information on
server and data is being corrupt. Windows security essentials and windows endpoint protection
are used for security.
7.1 WINDOWS SECURITY ESSENTIAL
Configure windows essential on windows server 2012. Download a right .exe file from
the respected website. The right .exe file for security essential is mseinstall.exe. Install this and
once it gets install click compatibility mode in properties where the admin has to check the “Run
this program in compatibility mode for” which will open a command prompt as an admin.
Finally run reinstall from downloads.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
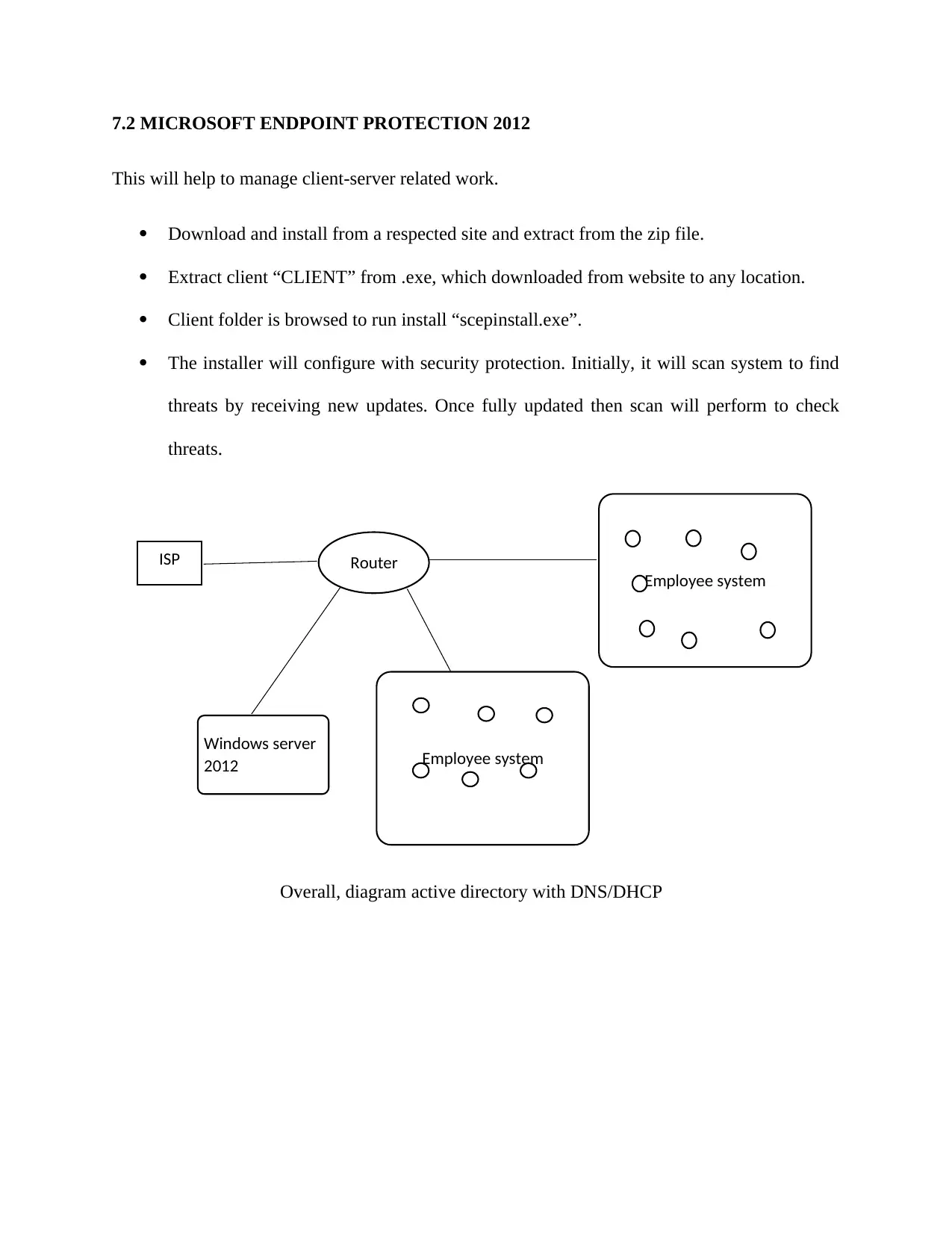
7.2 MICROSOFT ENDPOINT PROTECTION 2012
This will help to manage client-server related work.
Download and install from a respected site and extract from the zip file.
Extract client “CLIENT” from .exe, which downloaded from website to any location.
Client folder is browsed to run install “scepinstall.exe”.
The installer will configure with security protection. Initially, it will scan system to find
threats by receiving new updates. Once fully updated then scan will perform to check
threats.
Overall, diagram active directory with DNS/DHCP
ISP Router
Windows server
2012 Employee system
Employee system
This will help to manage client-server related work.
Download and install from a respected site and extract from the zip file.
Extract client “CLIENT” from .exe, which downloaded from website to any location.
Client folder is browsed to run install “scepinstall.exe”.
The installer will configure with security protection. Initially, it will scan system to find
threats by receiving new updates. Once fully updated then scan will perform to check
threats.
Overall, diagram active directory with DNS/DHCP
ISP Router
Windows server
2012 Employee system
Employee system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
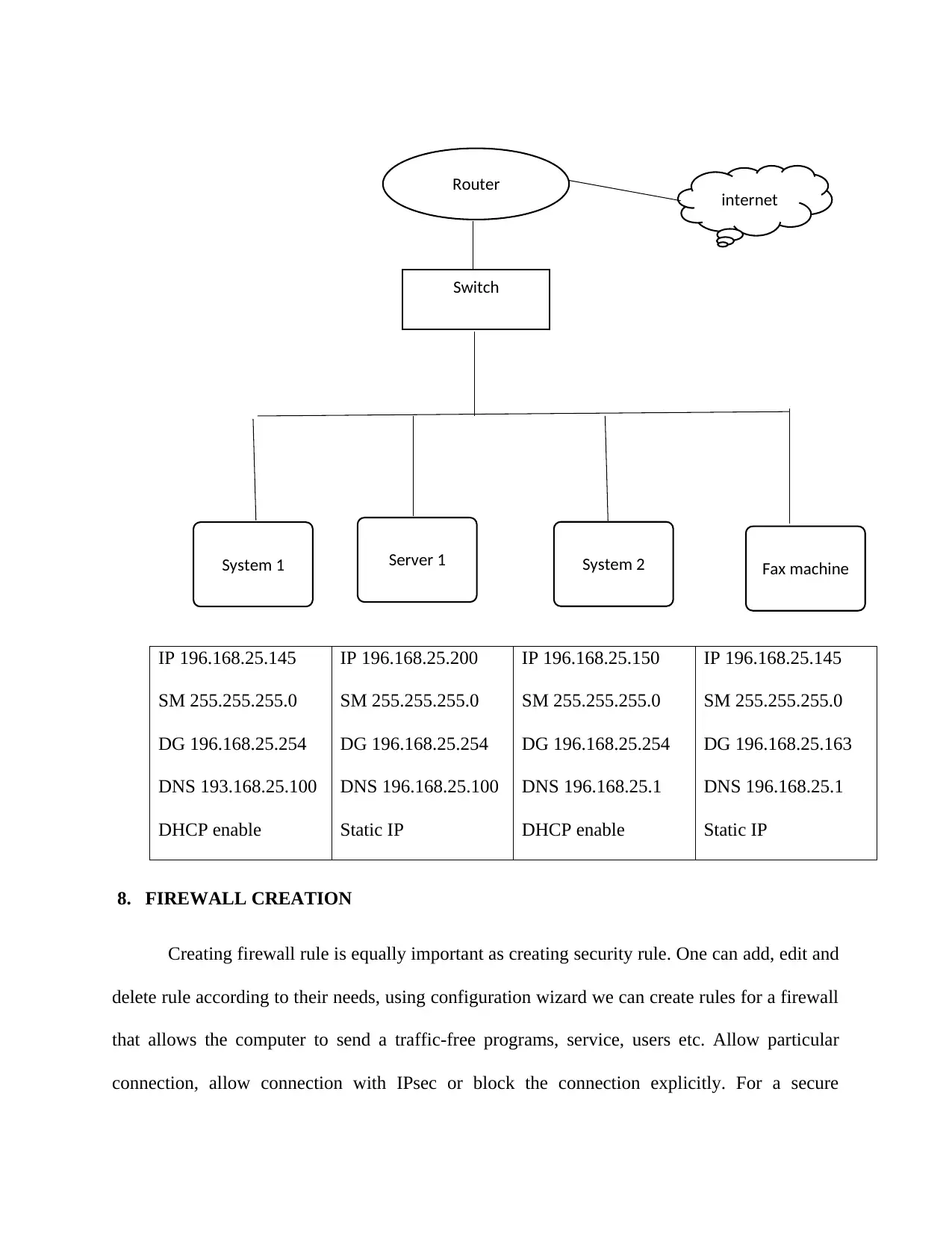
8. FIREWALL CREATION
Creating firewall rule is equally important as creating security rule. One can add, edit and
delete rule according to their needs, using configuration wizard we can create rules for a firewall
that allows the computer to send a traffic-free programs, service, users etc. Allow particular
connection, allow connection with IPsec or block the connection explicitly. For a secure
Router internet
Switch
System 1 Server 1 System 2 Fax machine
IP 196.168.25.145
SM 255.255.255.0
DG 196.168.25.254
DNS 193.168.25.100
DHCP enable
IP 196.168.25.200
SM 255.255.255.0
DG 196.168.25.254
DNS 196.168.25.100
Static IP
IP 196.168.25.150
SM 255.255.255.0
DG 196.168.25.254
DNS 196.168.25.1
DHCP enable
IP 196.168.25.145
SM 255.255.255.0
DG 196.168.25.163
DNS 196.168.25.1
Static IP
Creating firewall rule is equally important as creating security rule. One can add, edit and
delete rule according to their needs, using configuration wizard we can create rules for a firewall
that allows the computer to send a traffic-free programs, service, users etc. Allow particular
connection, allow connection with IPsec or block the connection explicitly. For a secure
Router internet
Switch
System 1 Server 1 System 2 Fax machine
IP 196.168.25.145
SM 255.255.255.0
DG 196.168.25.254
DNS 193.168.25.100
DHCP enable
IP 196.168.25.200
SM 255.255.255.0
DG 196.168.25.254
DNS 196.168.25.100
Static IP
IP 196.168.25.150
SM 255.255.255.0
DG 196.168.25.254
DNS 196.168.25.1
DHCP enable
IP 196.168.25.145
SM 255.255.255.0
DG 196.168.25.163
DNS 196.168.25.1
Static IP

connection on firewall security rule along with firewall, rule with IPsec. However, security rule
alone will not allow the connection to travel through the firewall so firewall rule has to create.
By default windows, the firewall will turn on and manages to run on windows server 2012.
Firewall rules and setting can be managed on windows server manager window, where on tools
select windows firewall with advanced security.
9. DHCP AND DNS
Every user or connection has a domain name, implementing DNS and DHCP on the
server use a static IP address which we created on server configuration i.e. assign on IP to DNS
and DHCP. DHCP allows as assigning IP address to physical address, which can be used for
same time. DNS on network helps to rename the local server to run on the network.
A group of policy has been created so that when an admin is not present a particular
permission has given to company users to use the server. Thus, help the system and server to
achieve flexibility where a group of policy helps the users in the absence of administrator.
Syslog Configuration
General setting
Syslog facility
Enable
Local6
alone will not allow the connection to travel through the firewall so firewall rule has to create.
By default windows, the firewall will turn on and manages to run on windows server 2012.
Firewall rules and setting can be managed on windows server manager window, where on tools
select windows firewall with advanced security.
9. DHCP AND DNS
Every user or connection has a domain name, implementing DNS and DHCP on the
server use a static IP address which we created on server configuration i.e. assign on IP to DNS
and DHCP. DHCP allows as assigning IP address to physical address, which can be used for
same time. DNS on network helps to rename the local server to run on the network.
A group of policy has been created so that when an admin is not present a particular
permission has given to company users to use the server. Thus, help the system and server to
achieve flexibility where a group of policy helps the users in the absence of administrator.
Syslog Configuration
General setting
Syslog facility
Enable
Local6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




