IT Concepts: Windows Server 2016 Configuration and Network Setup
VerifiedAdded on 2023/06/11
|30
|2776
|138
Report
AI Summary
This report details the configuration of Windows Server 2016 for a local photography studio, focusing on creating a network for storing and accessing photos with data redundancy and web hosting capabilities. The report covers setting up a virtual machine using Windows Server 2016, configuring web hosting and remote shell access using Remote Desktop Protocol (RDP), HTTP and HTTPS services configuration with SSL certificates, network sharing configuration for collaborative file access, and data duplication for ensuring data security. It also justifies the advantages of Windows Server 2016, such as enhanced security and software-defined data centers, and highlights the importance of authentication. The configuration steps are illustrated with screenshots and detailed explanations, providing a comprehensive guide for setting up a server environment tailored to the specific needs of the photography studio. Desklib provides access to this report and other study resources for students.

IT Concepts 1
Student Name
Student ID
Course
Institutional Affiliation
Student Name
Student ID
Course
Institutional Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Concepts 2
Table of Contents
Introduction......................................................................................................................................3
Background Information..................................................................................................................3
Setting up virtual machine using windows server 2016..................................................................4
Web Hosting/Remote Shell Access Configuration..........................................................................8
HTTP and HTTP services Configuration......................................................................................15
Network Sharing Configuration....................................................................................................18
Configuring Data Duplication.......................................................................................................24
Justifications..................................................................................................................................27
Advantages of Windows Sever 2016.........................................................................................27
Importance of Authentication....................................................................................................27
Conclusion.....................................................................................................................................28
Reference List................................................................................................................................29
Table of Contents
Introduction......................................................................................................................................3
Background Information..................................................................................................................3
Setting up virtual machine using windows server 2016..................................................................4
Web Hosting/Remote Shell Access Configuration..........................................................................8
HTTP and HTTP services Configuration......................................................................................15
Network Sharing Configuration....................................................................................................18
Configuring Data Duplication.......................................................................................................24
Justifications..................................................................................................................................27
Advantages of Windows Sever 2016.........................................................................................27
Importance of Authentication....................................................................................................27
Conclusion.....................................................................................................................................28
Reference List................................................................................................................................29

IT Concepts 3
Introduction
A server is a very important part for any organization to facilitate smooth flow of operations and
processes. It processes the requests from the client computers on a local network or over the internet.
There are many types of servers available in the market, for example, print server, file server, web server,
mail server, and many more. It is high-powered computers with large memories, storage, and great
processing speed. Its functions by pulling and pushing data over the network.
A virtual machine is more like a physical computer, but is not, which runs applications and operating
systems. The virtual machine is made up of configuration files and specifications and is supported by
physical resources of the host. The key components that makes up a virtual machine include NVRAM
setting file, configuration file, log file, and virtual disk file.
Background Information
A local photography studio needs a server to be set up that addresses its current IT needs. The studio
needs to create a network that allows photographers to store all the pictures in one place and can be
accessed by all the employees and supports data redundancy to make sure that the work is secured.
Additionally, they would like to host a web server from which customers can be able to access the photos
after been given the rights to access them. The solution is as discussed in the subsequent sections.
Introduction
A server is a very important part for any organization to facilitate smooth flow of operations and
processes. It processes the requests from the client computers on a local network or over the internet.
There are many types of servers available in the market, for example, print server, file server, web server,
mail server, and many more. It is high-powered computers with large memories, storage, and great
processing speed. Its functions by pulling and pushing data over the network.
A virtual machine is more like a physical computer, but is not, which runs applications and operating
systems. The virtual machine is made up of configuration files and specifications and is supported by
physical resources of the host. The key components that makes up a virtual machine include NVRAM
setting file, configuration file, log file, and virtual disk file.
Background Information
A local photography studio needs a server to be set up that addresses its current IT needs. The studio
needs to create a network that allows photographers to store all the pictures in one place and can be
accessed by all the employees and supports data redundancy to make sure that the work is secured.
Additionally, they would like to host a web server from which customers can be able to access the photos
after been given the rights to access them. The solution is as discussed in the subsequent sections.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Concepts 4
Setting up virtual machine using windows server 2016
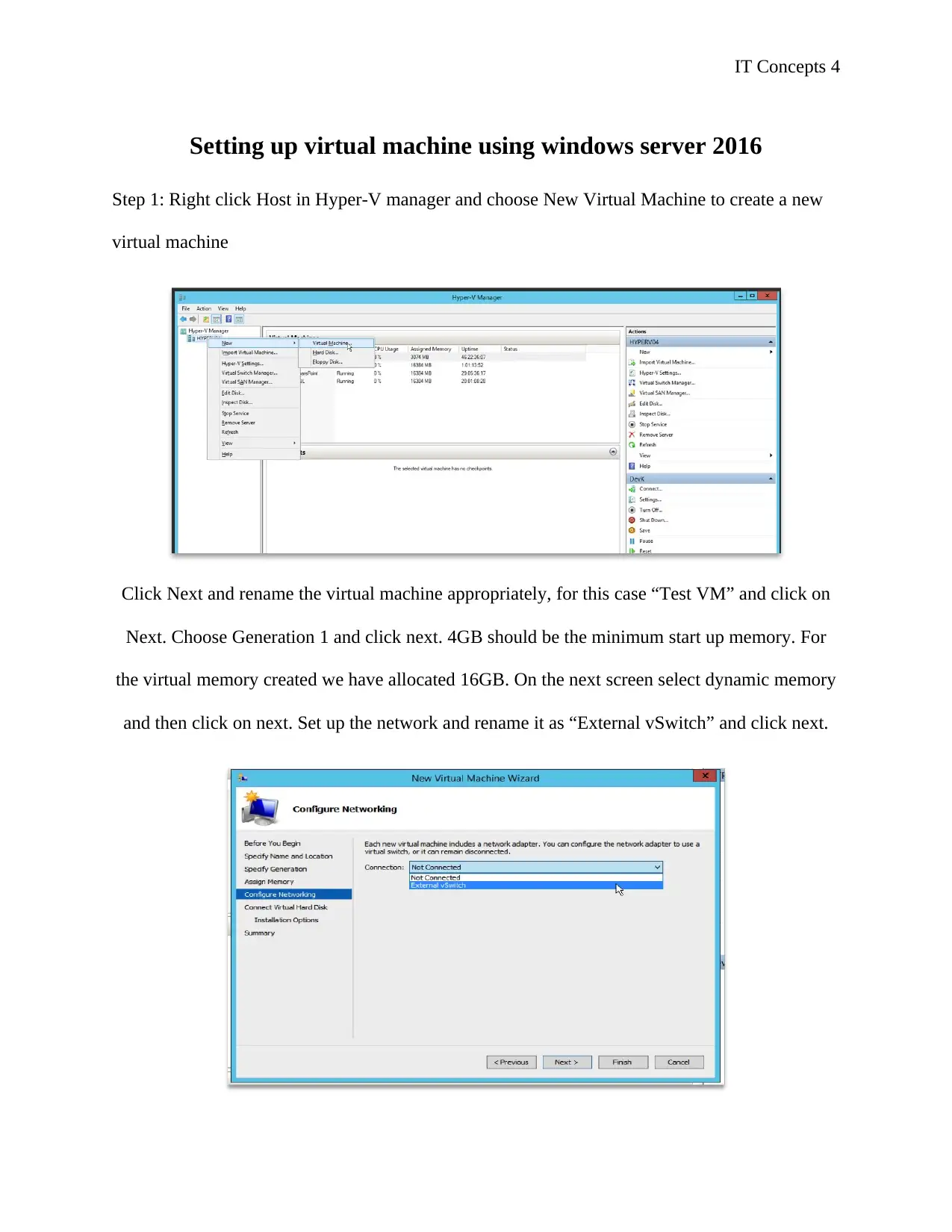
Step 1: Right click Host in Hyper-V manager and choose New Virtual Machine to create a new
virtual machine
Click Next and rename the virtual machine appropriately, for this case “Test VM” and click on
Next. Choose Generation 1 and click next. 4GB should be the minimum start up memory. For
the virtual memory created we have allocated 16GB. On the next screen select dynamic memory
and then click on next. Set up the network and rename it as “External vSwitch” and click next.
Setting up virtual machine using windows server 2016
Step 1: Right click Host in Hyper-V manager and choose New Virtual Machine to create a new
virtual machine
Click Next and rename the virtual machine appropriately, for this case “Test VM” and click on
Next. Choose Generation 1 and click next. 4GB should be the minimum start up memory. For
the virtual memory created we have allocated 16GB. On the next screen select dynamic memory
and then click on next. Set up the network and rename it as “External vSwitch” and click next.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 5
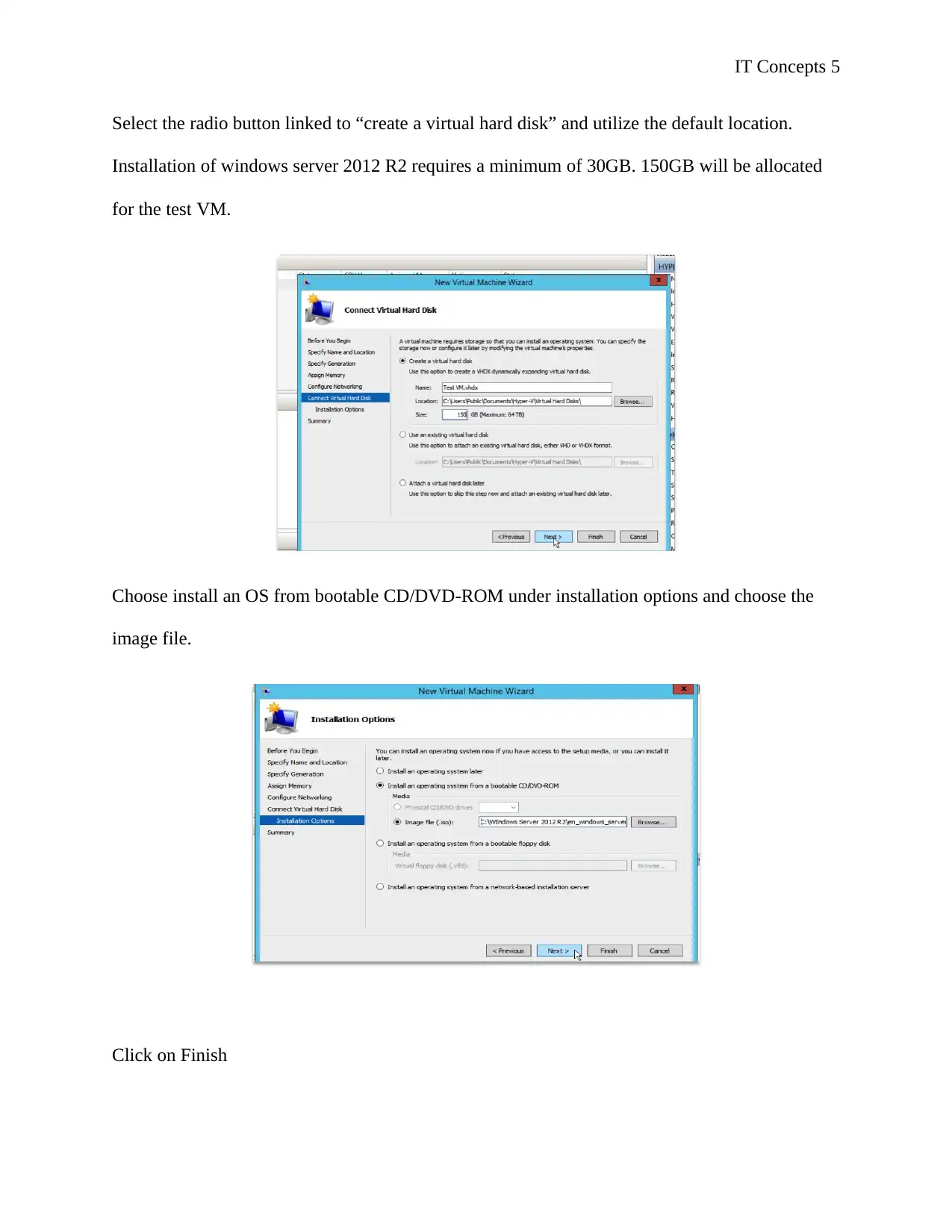
Select the radio button linked to “create a virtual hard disk” and utilize the default location.
Installation of windows server 2012 R2 requires a minimum of 30GB. 150GB will be allocated
for the test VM.
Choose install an OS from bootable CD/DVD-ROM under installation options and choose the
image file.
Click on Finish
Select the radio button linked to “create a virtual hard disk” and utilize the default location.
Installation of windows server 2012 R2 requires a minimum of 30GB. 150GB will be allocated
for the test VM.
Choose install an OS from bootable CD/DVD-ROM under installation options and choose the
image file.
Click on Finish
IT Concepts 6
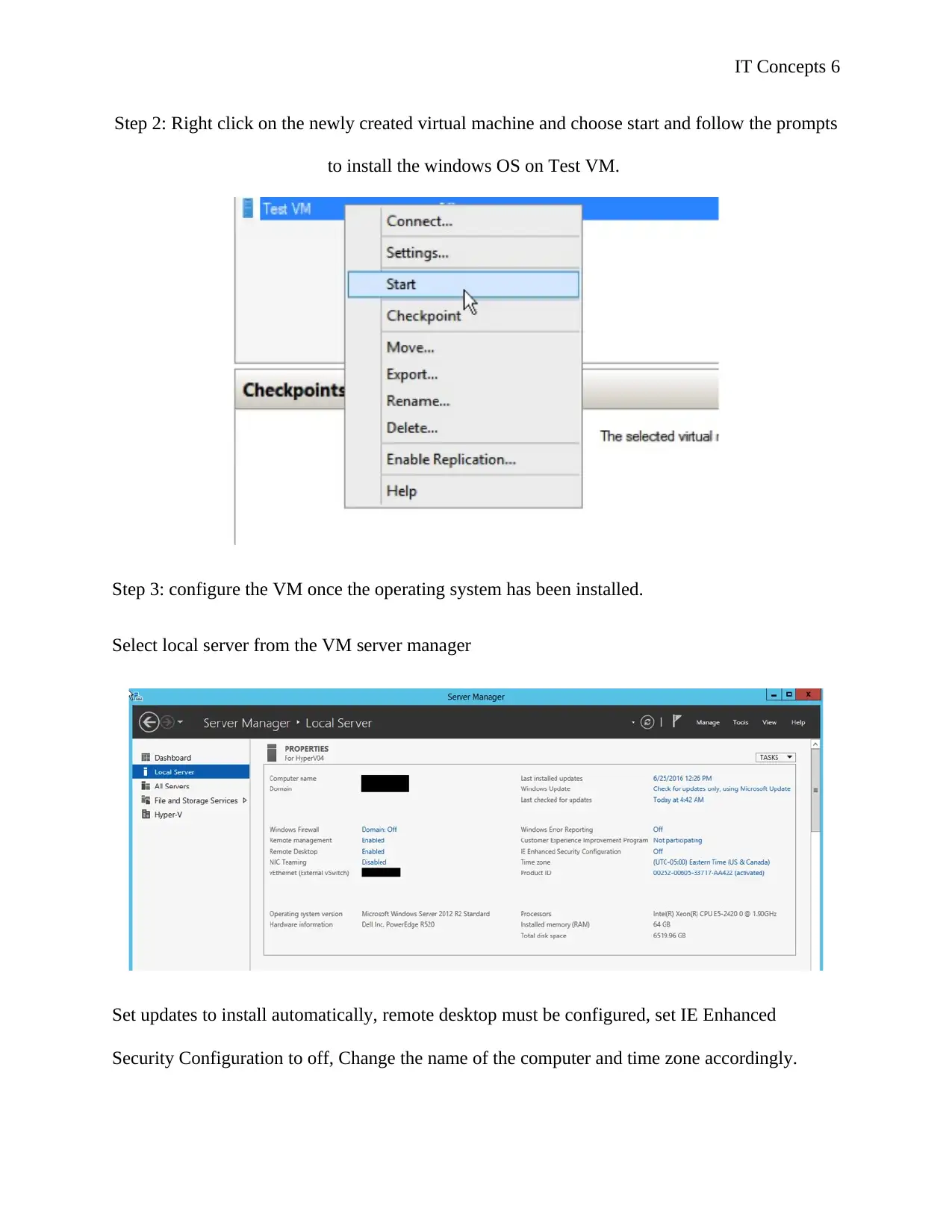
Step 2: Right click on the newly created virtual machine and choose start and follow the prompts
to install the windows OS on Test VM.
Step 3: configure the VM once the operating system has been installed.
Select local server from the VM server manager
Set updates to install automatically, remote desktop must be configured, set IE Enhanced
Security Configuration to off, Change the name of the computer and time zone accordingly.
Step 2: Right click on the newly created virtual machine and choose start and follow the prompts
to install the windows OS on Test VM.
Step 3: configure the VM once the operating system has been installed.
Select local server from the VM server manager
Set updates to install automatically, remote desktop must be configured, set IE Enhanced
Security Configuration to off, Change the name of the computer and time zone accordingly.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Concepts 7
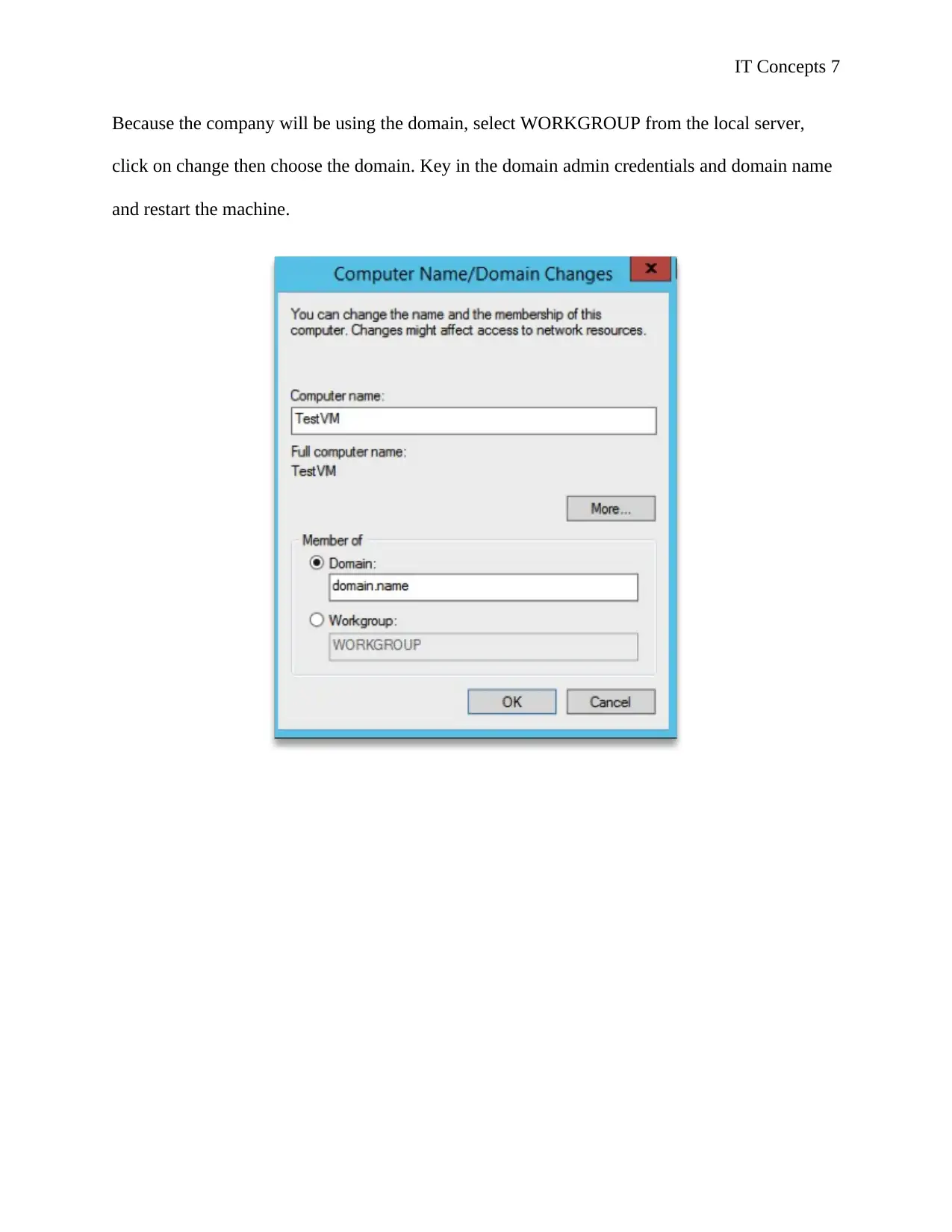
Because the company will be using the domain, select WORKGROUP from the local server,
click on change then choose the domain. Key in the domain admin credentials and domain name
and restart the machine.
Because the company will be using the domain, select WORKGROUP from the local server,
click on change then choose the domain. Key in the domain admin credentials and domain name
and restart the machine.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 8
Web Hosting/Remote Shell Access Configuration
Windows systems administrators use a Microsoft-proprietary remote access protocol to remotely
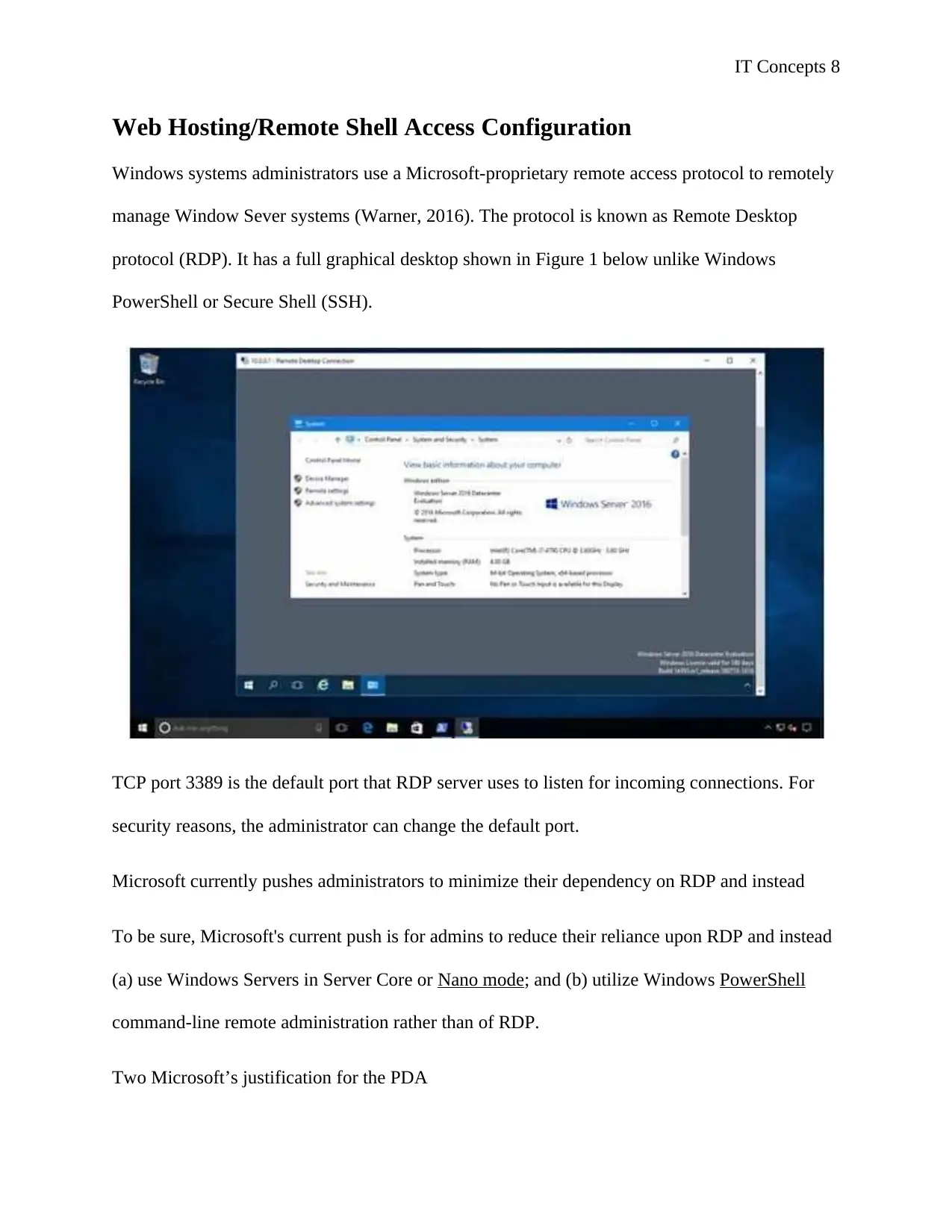
manage Window Sever systems (Warner, 2016). The protocol is known as Remote Desktop
protocol (RDP). It has a full graphical desktop shown in Figure 1 below unlike Windows
PowerShell or Secure Shell (SSH).
TCP port 3389 is the default port that RDP server uses to listen for incoming connections. For
security reasons, the administrator can change the default port.
Microsoft currently pushes administrators to minimize their dependency on RDP and instead
To be sure, Microsoft's current push is for admins to reduce their reliance upon RDP and instead
(a) use Windows Servers in Server Core or Nano mode; and (b) utilize Windows PowerShell
command-line remote administration rather than of RDP.
Two Microsoft’s justification for the PDA
Web Hosting/Remote Shell Access Configuration
Windows systems administrators use a Microsoft-proprietary remote access protocol to remotely
manage Window Sever systems (Warner, 2016). The protocol is known as Remote Desktop
protocol (RDP). It has a full graphical desktop shown in Figure 1 below unlike Windows
PowerShell or Secure Shell (SSH).
TCP port 3389 is the default port that RDP server uses to listen for incoming connections. For
security reasons, the administrator can change the default port.
Microsoft currently pushes administrators to minimize their dependency on RDP and instead
To be sure, Microsoft's current push is for admins to reduce their reliance upon RDP and instead
(a) use Windows Servers in Server Core or Nano mode; and (b) utilize Windows PowerShell
command-line remote administration rather than of RDP.
Two Microsoft’s justification for the PDA
IT Concepts 9
A GUI interface uses unnecessary system resources
A GUI interface broadens the attack surface of your servers
Irrespective, many administrators are used to RDB- based remote administration and likely to do
the same in the recently released Windows Server 2016 Operating System (Cisco, 2016). The
procedure of enabling RDP in Server 2016 is as follows (the procedure is the same to that of
windows server 2012 R2).
Server Manager
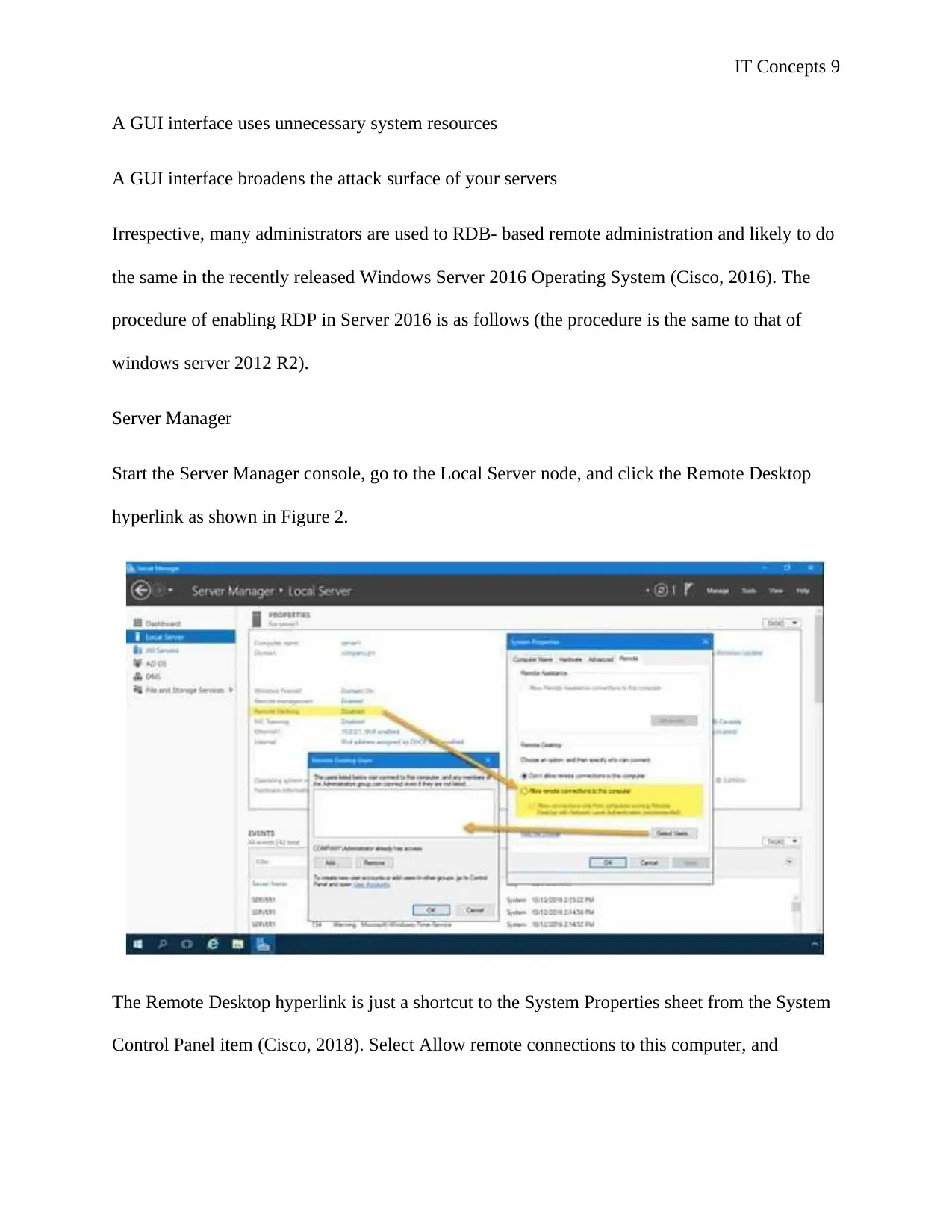
Start the Server Manager console, go to the Local Server node, and click the Remote Desktop
hyperlink as shown in Figure 2.
The Remote Desktop hyperlink is just a shortcut to the System Properties sheet from the System
Control Panel item (Cisco, 2018). Select Allow remote connections to this computer, and
A GUI interface uses unnecessary system resources
A GUI interface broadens the attack surface of your servers
Irrespective, many administrators are used to RDB- based remote administration and likely to do
the same in the recently released Windows Server 2016 Operating System (Cisco, 2016). The
procedure of enabling RDP in Server 2016 is as follows (the procedure is the same to that of
windows server 2012 R2).
Server Manager
Start the Server Manager console, go to the Local Server node, and click the Remote Desktop
hyperlink as shown in Figure 2.
The Remote Desktop hyperlink is just a shortcut to the System Properties sheet from the System
Control Panel item (Cisco, 2018). Select Allow remote connections to this computer, and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Concepts 10
optionally enable Allow connections only from computers running Remote Desktop with
Network Level Authentication (recommended).
Windows Server is protected against Denial of Service Attacks by the Network Authentication
(NLA).
Before any the server establishes any graphical session, it requires authentication to take place
(Markle, 2017). The NLA also allows the Server to conserve system resource.
Windows PowerShell
From a lower-point of view, incoming RDP connections can be enabled on using two Registry
values and a Windows Firewall rule on the server. Run the following commands after opening an
elevated Windows PowerShell session.
This create the fDenyTSConnections value and set it to 0 (off). This is important as we don't
want to reject Terminal Services (TS) connections.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal Server' -Name
'fDenyTSConnections' -Value 0 -PropertyType dword -Force
UserAuthentication valu (NLA) is created and enabled by the second command. Network Layer
Authentication is important and should be enabled by default in the server.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal
ServerWinStationsRDP-Tcp' -Name 'UserAuthentication' -Value 1 -PropertyType dword -Force
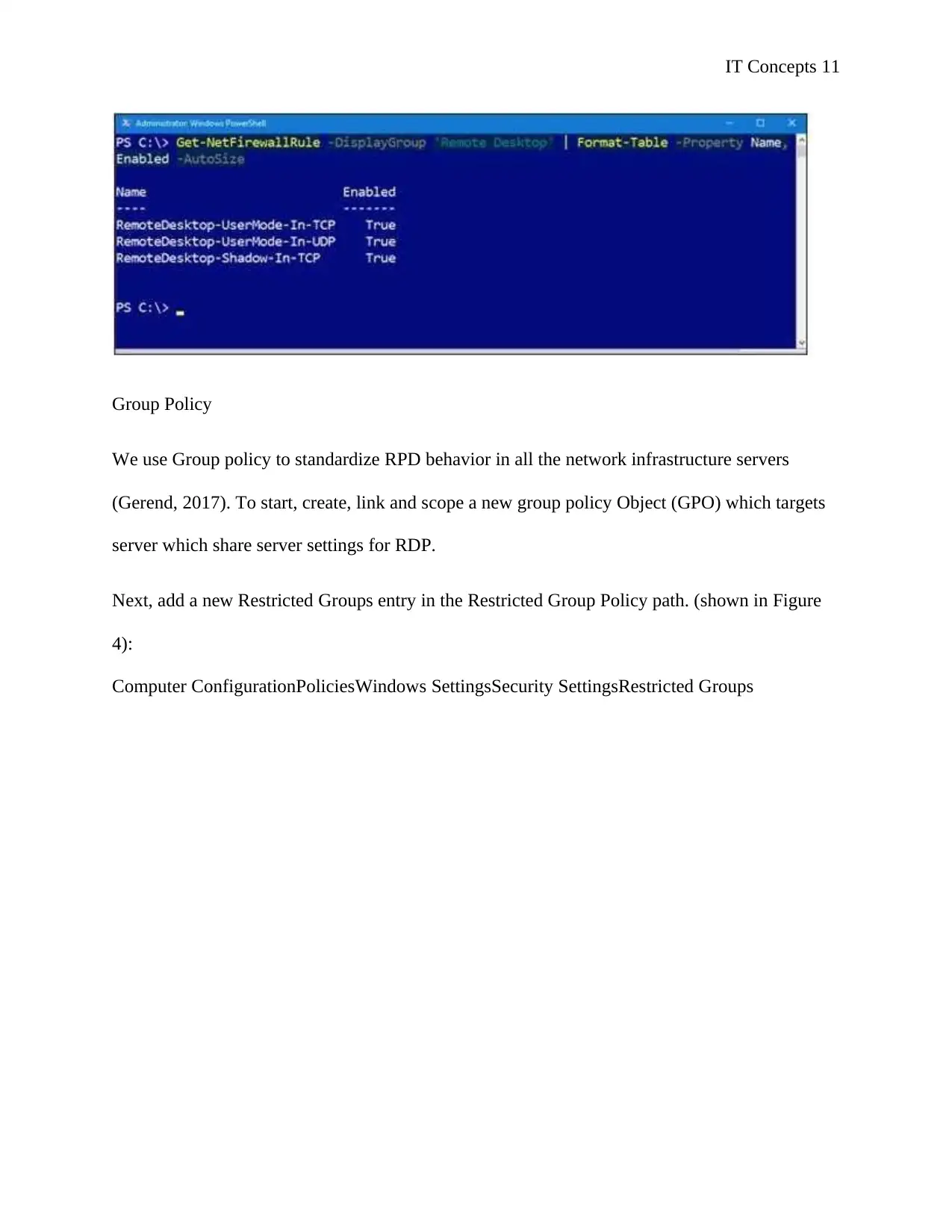
Use the next command to enable Predefined “Remote Desktop” windows firewall rule. This can
be then invoked by the Get-NetFirewallRule PowerShell cmdlet to verify as shown in Figure 3.
Enable-NetFirewallRule -DisplayGroup 'Remote Desktop'
optionally enable Allow connections only from computers running Remote Desktop with
Network Level Authentication (recommended).
Windows Server is protected against Denial of Service Attacks by the Network Authentication
(NLA).
Before any the server establishes any graphical session, it requires authentication to take place
(Markle, 2017). The NLA also allows the Server to conserve system resource.
Windows PowerShell
From a lower-point of view, incoming RDP connections can be enabled on using two Registry
values and a Windows Firewall rule on the server. Run the following commands after opening an
elevated Windows PowerShell session.
This create the fDenyTSConnections value and set it to 0 (off). This is important as we don't
want to reject Terminal Services (TS) connections.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal Server' -Name
'fDenyTSConnections' -Value 0 -PropertyType dword -Force
UserAuthentication valu (NLA) is created and enabled by the second command. Network Layer
Authentication is important and should be enabled by default in the server.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal
ServerWinStationsRDP-Tcp' -Name 'UserAuthentication' -Value 1 -PropertyType dword -Force
Use the next command to enable Predefined “Remote Desktop” windows firewall rule. This can
be then invoked by the Get-NetFirewallRule PowerShell cmdlet to verify as shown in Figure 3.
Enable-NetFirewallRule -DisplayGroup 'Remote Desktop'
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Concepts 11
Group Policy
We use Group policy to standardize RPD behavior in all the network infrastructure servers
(Gerend, 2017). To start, create, link and scope a new group policy Object (GPO) which targets
server which share server settings for RDP.
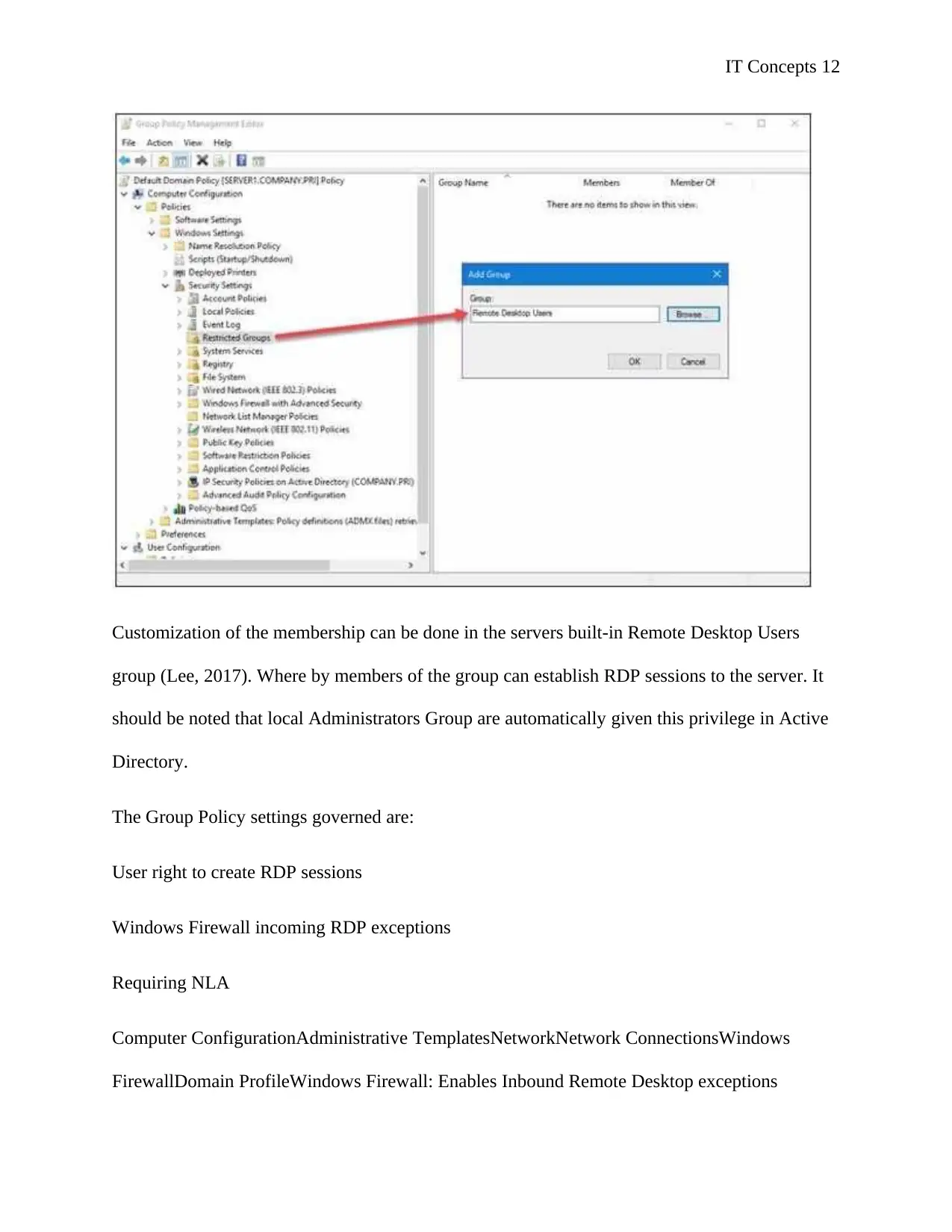
Next, add a new Restricted Groups entry in the Restricted Group Policy path. (shown in Figure
4):
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsRestricted Groups
Group Policy
We use Group policy to standardize RPD behavior in all the network infrastructure servers
(Gerend, 2017). To start, create, link and scope a new group policy Object (GPO) which targets
server which share server settings for RDP.
Next, add a new Restricted Groups entry in the Restricted Group Policy path. (shown in Figure
4):
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsRestricted Groups
IT Concepts 12
Customization of the membership can be done in the servers built-in Remote Desktop Users
group (Lee, 2017). Where by members of the group can establish RDP sessions to the server. It
should be noted that local Administrators Group are automatically given this privilege in Active
Directory.
The Group Policy settings governed are:
User right to create RDP sessions
Windows Firewall incoming RDP exceptions
Requiring NLA
Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows
FirewallDomain ProfileWindows Firewall: Enables Inbound Remote Desktop exceptions
Customization of the membership can be done in the servers built-in Remote Desktop Users
group (Lee, 2017). Where by members of the group can establish RDP sessions to the server. It
should be noted that local Administrators Group are automatically given this privilege in Active
Directory.
The Group Policy settings governed are:
User right to create RDP sessions
Windows Firewall incoming RDP exceptions
Requiring NLA
Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows
FirewallDomain ProfileWindows Firewall: Enables Inbound Remote Desktop exceptions
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




