Comprehensive Analysis: Security Threats, Countermeasures, and Tools
VerifiedAdded on 2022/11/15
|13
|730
|170
Report
AI Summary
This report provides a detailed analysis of security threats targeting both wired and non-wired devices. It covers a range of vulnerabilities, including rogue access points, spoofing, and configuration-related issues. The report outlines various countermeasures, such as virus scanners, end-to-end encryption, and network authentication protocols like Kerberos. It also examines tools for measuring security risks, including OpenVAS, Vega, and Icinga 2, and discusses practical threat analysis tools and methodologies. Furthermore, the report differentiates between penetration testing and vulnerability assessment, highlighting their benefits and comparing their approaches. Finally, it explores tools for mitigating security vulnerabilities, such as Network Mapper and Nessus, providing a comprehensive overview of security best practices and solutions.

Ways to Mitigate Security
Vulnerabilities
Vulnerabilities
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security threats for wired and non-wired devices.
Countermeasures.
Tools to measure the security risks.
Penetrating test.
Vulnerability assessment.
Comparison between penetrating test & vulnerability
assessment.
Benefits of using penetrating test & vulnerability assessment.
Tools to mitigate the security vulnerability.
References
Topic of Discussion
Countermeasures.
Tools to measure the security risks.
Penetrating test.
Vulnerability assessment.
Comparison between penetrating test & vulnerability
assessment.
Benefits of using penetrating test & vulnerability assessment.
Tools to mitigate the security vulnerability.
References
Topic of Discussion
Security Threats For Wired & Non- Wired Devices
Setting up of rogue access point.
Stolen or lost Wi-Fi device related threats.
Different threats related with configuration.
LAN related security issues (Shu et al., 2016).
Evil twin access points.
Spoofing.
Tampering (Namboodiri et al., 2013).
Setting up of rogue access point.
Stolen or lost Wi-Fi device related threats.
Different threats related with configuration.
LAN related security issues (Shu et al., 2016).
Evil twin access points.
Spoofing.
Tampering (Namboodiri et al., 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Countermeasures
Virus scanners can be used to prevent the risks.
Different levels of security to secure the various emails and
internet mail extension.
End to End encryption in the application (Vacca, 2013).
Implement secure shell in the application layer of the network.
Implement the network authentication protocol known as the
Kerberos.
Virus scanners can be used to prevent the risks.
Different levels of security to secure the various emails and
internet mail extension.
End to End encryption in the application (Vacca, 2013).
Implement secure shell in the application layer of the network.
Implement the network authentication protocol known as the
Kerberos.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Tools to Measure Security Risks
OpenVAS is the tool that which is used to scan the
vulnerabilities.
Vega it helps in scanning the applications.
Cross Site Scripting can be used (Wilhelm,2013).
Icinga 2 it is used to monitor the risks.
Practical Threat Analysis Tools.
OpenVAS is the tool that which is used to scan the
vulnerabilities.
Vega it helps in scanning the applications.
Cross Site Scripting can be used (Wilhelm,2013).
Icinga 2 it is used to monitor the risks.
Practical Threat Analysis Tools.
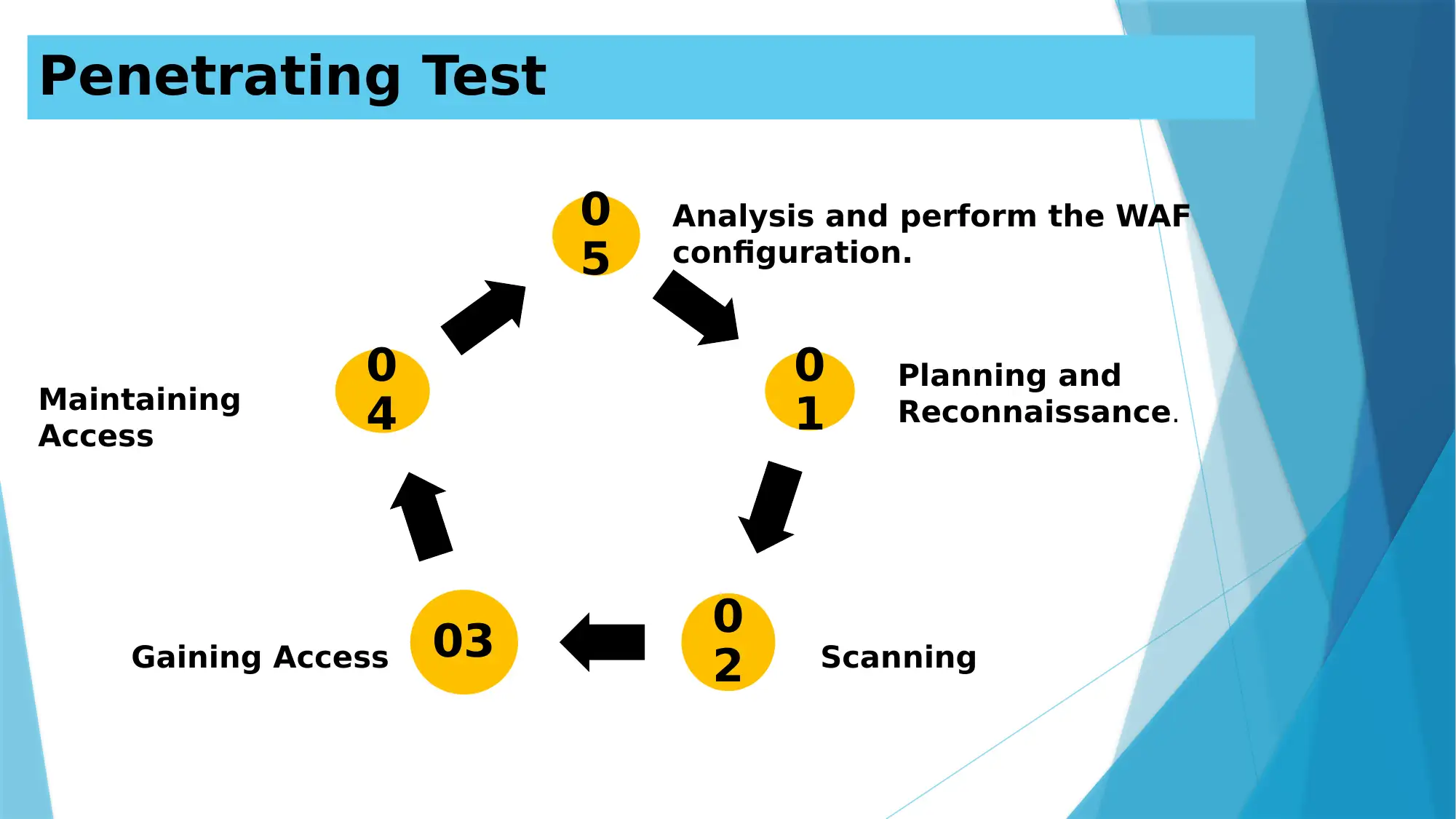
Penetrating Test
0
5
0
1
0
2
03
0
4 Planning and
Reconnaissance.
ScanningGaining Access
Maintaining
Access
Analysis and perform the WAF
configuration.
0
5
0
1
0
2
03
0
4 Planning and
Reconnaissance.
ScanningGaining Access
Maintaining
Access
Analysis and perform the WAF
configuration.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
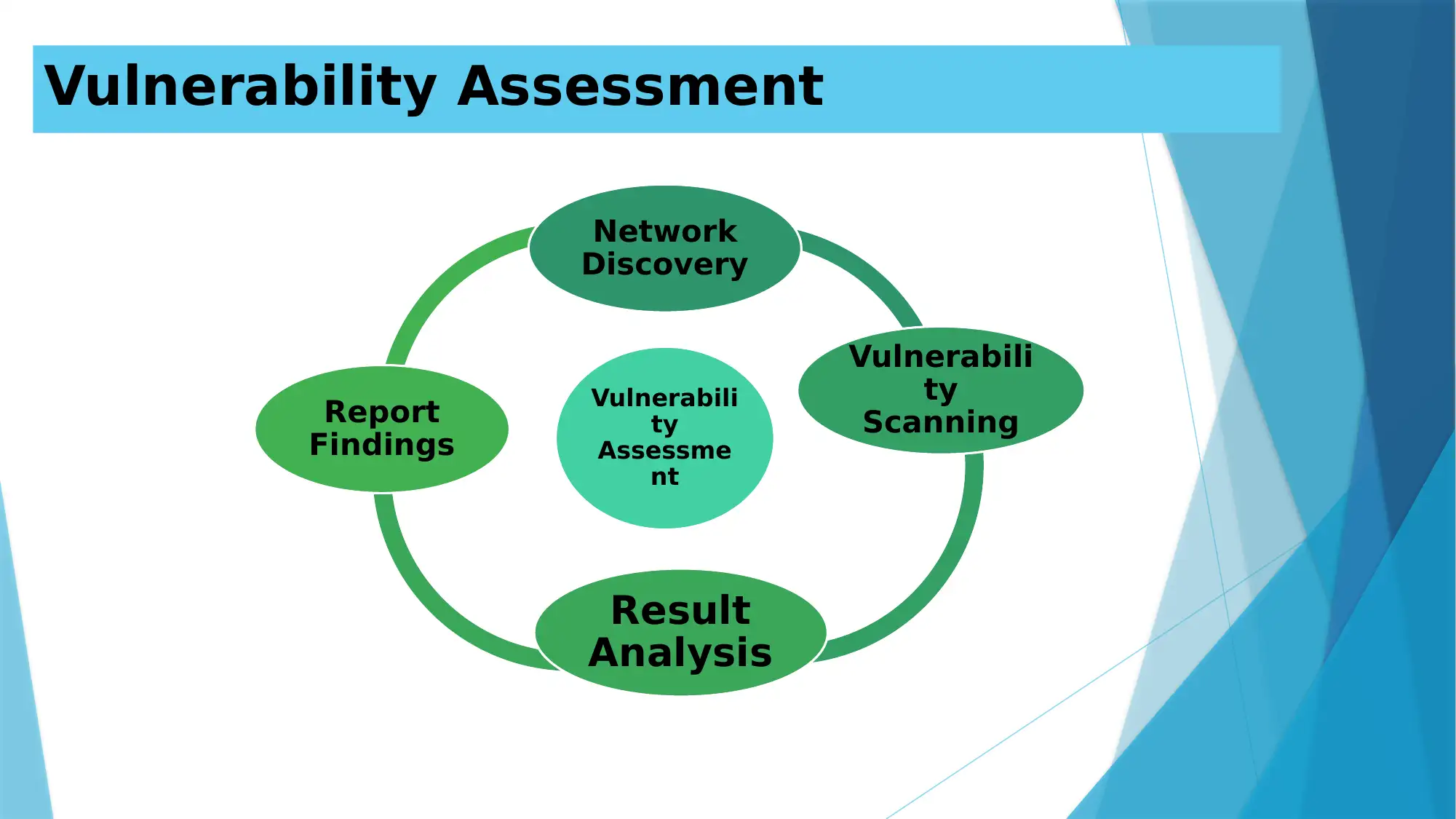
Vulnerability Assessment
Vulnerabili
ty
Assessme
nt
Network
Discovery
Vulnerabili
ty
Scanning
Result
Analysis
Report
Findings
Vulnerabili
ty
Assessme
nt
Network
Discovery
Vulnerabili
ty
Scanning
Result
Analysis
Report
Findings
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Penetrating Test
The organization believes that
there security system is strong
and requires testing to check the
system.
The process is deep and focussed
(Souppaya & Scarfone, 2013).
It helps in prioritizing the list of
vulnerabilities.
Performed by experienced
hackers.
Vulnerability
Assessment
Used by organizations which
have already identified the
issues and need support to
solve the issues.
The process is broad and wide.
It gives out the list of
vulnerabilities.
It is performed by the
automated tools (Rai, Sahoo &
Mehfuz, 2013).
Comparison
The organization believes that
there security system is strong
and requires testing to check the
system.
The process is deep and focussed
(Souppaya & Scarfone, 2013).
It helps in prioritizing the list of
vulnerabilities.
Performed by experienced
hackers.
Vulnerability
Assessment
Used by organizations which
have already identified the
issues and need support to
solve the issues.
The process is broad and wide.
It gives out the list of
vulnerabilities.
It is performed by the
automated tools (Rai, Sahoo &
Mehfuz, 2013).
Comparison
Benefits of Using Penetrating Test &
Vulnerability Assessment
It helps in the identifying the security exposures before the
attackers.
Define the different levels of risks present in the network (Meigh,
2013).
Helps to determine the different hardware and software assets
present.
Helps in protecting the personal data securely.
Helps in satisfying the compliance requirements.
Vulnerability Assessment
It helps in the identifying the security exposures before the
attackers.
Define the different levels of risks present in the network (Meigh,
2013).
Helps to determine the different hardware and software assets
present.
Helps in protecting the personal data securely.
Helps in satisfying the compliance requirements.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Tools to Mitigate Security
Vulnerabilities
Network Mapper tool can be used for security auditing.
Benchmark tool which can be used to scan the network.
The Nessus Security checks the vulnerability (Andrea,
Chrysostomou & Hadjichristofi,2015).
OpenSSH application for checking authentication.
Implementation of MBSA in the system.
Vulnerabilities
Network Mapper tool can be used for security auditing.
Benchmark tool which can be used to scan the network.
The Nessus Security checks the vulnerability (Andrea,
Chrysostomou & Hadjichristofi,2015).
OpenSSH application for checking authentication.
Implementation of MBSA in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Andrea, I., Chrysostomou, C., & Hadjichristofi, G. (2015, July). Internet of Things: Security vulnerabilities
and challenges. In 2015 IEEE Symposium on Computers and Communication (ISCC) (pp. 180-187). IEEE.
Meigh, A. C. (2013). Cone penetration testing: methods and interpretation. Elsevier.
Namboodiri, V., Aravinthan, V., Mohapatra, S. N., Karimi, B., & Jewell, W. (2013). Toward a secure wireless-
based home area network for metering in smart grids. IEEE Systems Journal, 8(2), 509-520.
Rai, R., Sahoo, G., & Mehfuz, S. (2013). Securing software as a service model of cloud computing: Issues and
solutions. arXiv preprint arXiv:1309.2426.
Andrea, I., Chrysostomou, C., & Hadjichristofi, G. (2015, July). Internet of Things: Security vulnerabilities
and challenges. In 2015 IEEE Symposium on Computers and Communication (ISCC) (pp. 180-187). IEEE.
Meigh, A. C. (2013). Cone penetration testing: methods and interpretation. Elsevier.
Namboodiri, V., Aravinthan, V., Mohapatra, S. N., Karimi, B., & Jewell, W. (2013). Toward a secure wireless-
based home area network for metering in smart grids. IEEE Systems Journal, 8(2), 509-520.
Rai, R., Sahoo, G., & Mehfuz, S. (2013). Securing software as a service model of cloud computing: Issues and
solutions. arXiv preprint arXiv:1309.2426.

Shu, Z., Wan, J., Li, D., Lin, J., Vasilakos, A. V., & Imran, M. (2016). Security in software-defined
networking: Threats and countermeasures. Mobile Networks and Applications, 21(5), 764-776.
Souppaya, M., & Scarfone, K. (2013). Guidelines for managing the security of mobile devices in
the enterprise. NIST special publication, 800, 124.
Vacca, J. R. (Ed.). (2013). Managing information security. Elsevier.
Wilhelm, T. (2013). Professional penetration testing: Creating and learning in a hacking lab.
Newnes.
networking: Threats and countermeasures. Mobile Networks and Applications, 21(5), 764-776.
Souppaya, M., & Scarfone, K. (2013). Guidelines for managing the security of mobile devices in
the enterprise. NIST special publication, 800, 124.
Vacca, J. R. (Ed.). (2013). Managing information security. Elsevier.
Wilhelm, T. (2013). Professional penetration testing: Creating and learning in a hacking lab.
Newnes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





