MITS5003 Wireless Communication: Analysis of Encoding, Multiplexing
VerifiedAdded on 2023/06/10
|21
|4273
|187
Homework Assignment
AI Summary
This assignment solution delves into various aspects of wireless communication, starting with encoding and error control techniques for a micro-robot design, including calculations for data rate, status string representation using ASK, FSK, and PSK, and CRC calculation. It further explains multiplexing techniques like TDM, FDM, and CDMA, differentiating OFDM and its features in the context of 3G to 4G evolution and WiMAX. The assignment also addresses Wi-Fi network design based on IEEE 802.11ac standards, covering subcarrier bandwidth, bit time, and inter-symbol interference. The document concludes with practical network design considerations, including access point placement, BSS/ESS size calculations, throughput analysis, IEEE standard recommendations, and security measures. Desklib provides access to this and other solved assignments for students.

[Date] WIRELESS
COMMUNICATION
COMMUNICATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CONTENTS
Part I: Encoding and error control............................................................................................................ 2
a) Calculate the data rate required for robot to remote controller communication?..........................2
b) Explain 3 types of suitable encoding techniques could be used to encode the status string.............2
Encoding Techniques: -.............................................................................................................. 2
Bi-polar encoding:...................................................................................................................... 3
c) At a specific occurrence, the sensors gave information as quickening 5 m/s2, snag at
48 cm, all engines working (i.e. engine usefulness 1111), and battery is 75%...............3
I) Write the status string in parallel for this case........................................................................ 3
ii)Represent the status string on ASK, FSK, and PSK encoding strategies...................................3
d) Calculate the CRC for the status string determined in c) with polynomial divisor
11001101....................................................................................................................... 4
e) Briefly clarify some other mistake control and stream control methods that Sam can
use to guarantee the precision of robot control..............................................................5
Error Control:............................................................................................................................. 5
Flow and Error control procedures:............................................................................................ 6
Part II: Multiplexing and multiple access........................................................................................... 7
a) Explain TDM, FDM and CDMA multiplexing techniques with appropriate diagrams. 8
CDMA: -...................................................................................................................................... 9
b) Main air interface within the modification from 3G to 4G and WiMAX. make a case for
however OFDM is completely different from on top of techniques and therefore the
special feature of signals utilized by OFDM..................................................................10
C)IEEE 802.11ac wireless LAN customary uses forty MEGACYCLES per second total
information measure in OFDM theme...........................................................................11
I)For FORTY-EIGHT subscribers what ought to be the subcarrier information measure
(FB)?....................................................................................................................................... 11
ii)Propose an acceptable subcarrier bit time of T to attain orthogonality? ...................11
iii. make a case for however OFDM overcomes the problem of entomb image
interference (ISI)?................................................................................................................. 12
Part III: Wi-Fi................................................................................................................................... 13
a) DESIGN the network specifying the locations of access points and distributions
system showing the backbone network........................................................................13
b) Calculate the BSS and ESS sizes............................................................................14
c) Calculate the turnout for the DS............................................................................16
d) advocate an appropriate IEEE substandard for the network and provides reasons for
wherever selection........................................................................................................ 16
A list of IEEEs substandard that can be used by SAN...............................................................16
e) advocate appropriate security ways for the network................................................17
REFERENCES: -............................................................................................................................... 18
References................................................................................................................... 18
WIRELESS COMMUNICATION
STUDENT ID 1
Part I: Encoding and error control............................................................................................................ 2
a) Calculate the data rate required for robot to remote controller communication?..........................2
b) Explain 3 types of suitable encoding techniques could be used to encode the status string.............2
Encoding Techniques: -.............................................................................................................. 2
Bi-polar encoding:...................................................................................................................... 3
c) At a specific occurrence, the sensors gave information as quickening 5 m/s2, snag at
48 cm, all engines working (i.e. engine usefulness 1111), and battery is 75%...............3
I) Write the status string in parallel for this case........................................................................ 3
ii)Represent the status string on ASK, FSK, and PSK encoding strategies...................................3
d) Calculate the CRC for the status string determined in c) with polynomial divisor
11001101....................................................................................................................... 4
e) Briefly clarify some other mistake control and stream control methods that Sam can
use to guarantee the precision of robot control..............................................................5
Error Control:............................................................................................................................. 5
Flow and Error control procedures:............................................................................................ 6
Part II: Multiplexing and multiple access........................................................................................... 7
a) Explain TDM, FDM and CDMA multiplexing techniques with appropriate diagrams. 8
CDMA: -...................................................................................................................................... 9
b) Main air interface within the modification from 3G to 4G and WiMAX. make a case for
however OFDM is completely different from on top of techniques and therefore the
special feature of signals utilized by OFDM..................................................................10
C)IEEE 802.11ac wireless LAN customary uses forty MEGACYCLES per second total
information measure in OFDM theme...........................................................................11
I)For FORTY-EIGHT subscribers what ought to be the subcarrier information measure
(FB)?....................................................................................................................................... 11
ii)Propose an acceptable subcarrier bit time of T to attain orthogonality? ...................11
iii. make a case for however OFDM overcomes the problem of entomb image
interference (ISI)?................................................................................................................. 12
Part III: Wi-Fi................................................................................................................................... 13
a) DESIGN the network specifying the locations of access points and distributions
system showing the backbone network........................................................................13
b) Calculate the BSS and ESS sizes............................................................................14
c) Calculate the turnout for the DS............................................................................16
d) advocate an appropriate IEEE substandard for the network and provides reasons for
wherever selection........................................................................................................ 16
A list of IEEEs substandard that can be used by SAN...............................................................16
e) advocate appropriate security ways for the network................................................17
REFERENCES: -............................................................................................................................... 18
References................................................................................................................... 18
WIRELESS COMMUNICATION
STUDENT ID 1

PART I: ENCODING AND ERROR CONTROL
Sam is a computer science student and working on a new micro robot design. The robot
continuously sends every two seconds a status string comprising the accelerometer
reading (4 bits), ultrasound obstacle detection (6 bits), motor functionality (4 bits) and
battery power level (2 bits).
A) CALCULATE THE DATA RATE REQUIRED FOR ROBOT TO REMOTE CONTROLLER
COMMUNICATION?
Ans. Data transfer rate is that the rate that an exact quantity of information is
transferred over a given amount in time. a method this may be done is by a
straightforward equation exploitation what quantity knowledge has been transferred
and the way long it took in total to transfer that knowledge. So, equation is that: "Data
Transfer" divided by "Time Taken". therefore, on condition that measuring system
transmit four bits/sec then the desired rate for automaton to remote controller
communication is zero.5 byte/sec.
B) EXPLAIN 3 TYPES OF SUITABLE ENCODING TECHNIQUES COULD BE USED TO ENCODE
THE STATUS STRING.
Ans:
ENCODING TECHNIQUES : -
The propagated NRZ codes is used to divide the property giving to us that the voltage
levels are always consistent, but a little interim in their nature. ASV = bit 1 and LLV = bit
0.
The two varieties are as per the following:
WIRELESS COMMUNICATION
STUDENT ID 2
Sam is a computer science student and working on a new micro robot design. The robot
continuously sends every two seconds a status string comprising the accelerometer
reading (4 bits), ultrasound obstacle detection (6 bits), motor functionality (4 bits) and
battery power level (2 bits).
A) CALCULATE THE DATA RATE REQUIRED FOR ROBOT TO REMOTE CONTROLLER
COMMUNICATION?
Ans. Data transfer rate is that the rate that an exact quantity of information is
transferred over a given amount in time. a method this may be done is by a
straightforward equation exploitation what quantity knowledge has been transferred
and the way long it took in total to transfer that knowledge. So, equation is that: "Data
Transfer" divided by "Time Taken". therefore, on condition that measuring system
transmit four bits/sec then the desired rate for automaton to remote controller
communication is zero.5 byte/sec.
B) EXPLAIN 3 TYPES OF SUITABLE ENCODING TECHNIQUES COULD BE USED TO ENCODE
THE STATUS STRING.
Ans:
ENCODING TECHNIQUES : -
The propagated NRZ codes is used to divide the property giving to us that the voltage
levels are always consistent, but a little interim in their nature. ASV = bit 1 and LLV = bit
0.
The two varieties are as per the following:
WIRELESS COMMUNICATION
STUDENT ID 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.NRZ-Level: NRZ-L strategy looks simply like the NRZ technique, with the exception
of the primary information one information bit. This is so because NRZ does not usually
contemplate the information but by bit or in extreme modifications, while NRZ-L does
so.
2. NRZ-Inverted: the transition achieved at the start of it is a bit interim in nature
(=bit 1) and bit o is when there is not transition. This is what we call differential coding.
BI-POLAR ENCODING:
Bi-Polar encoding has following attributes:
1. its balance rate is considered to be twice to that of the NRZ and transmission capacity
is also more prominent in nature as compared to NRZ in all senses and ways.
2. Since the changes have been unsurprising in nature and in each piece time, the
collector has the ability to sync itself on the progress i.e., the clock and the flag are
separated.
3. The progress can be towards the start of the program and in the interim too, the time
works at double the exchange rate
C) ALSO, IT WAS NOTED THAT AT CERTAIN OCCURRENCE, THE SENSORS HAVE GIVEN
INFORMATION AS QUCIK AS 5 M/S2, SNAG AT 48 CM, ALL ENGINES WORKING (I.E.
ENGINE USEFULNESS 1111), AND BATTERY IS 75%.
I) WRITE THE STATUS STRING IN PARALLEL FOR THIS CASE
Ans: 010111111
II)REPRESENT THE STATUS STRING ON ASK, FSK, AND PSK ENCODING
STRATEGIES.
WIRELESS COMMUNICATION
STUDENT ID 3
of the primary information one information bit. This is so because NRZ does not usually
contemplate the information but by bit or in extreme modifications, while NRZ-L does
so.
2. NRZ-Inverted: the transition achieved at the start of it is a bit interim in nature
(=bit 1) and bit o is when there is not transition. This is what we call differential coding.
BI-POLAR ENCODING:
Bi-Polar encoding has following attributes:
1. its balance rate is considered to be twice to that of the NRZ and transmission capacity
is also more prominent in nature as compared to NRZ in all senses and ways.
2. Since the changes have been unsurprising in nature and in each piece time, the
collector has the ability to sync itself on the progress i.e., the clock and the flag are
separated.
3. The progress can be towards the start of the program and in the interim too, the time
works at double the exchange rate
C) ALSO, IT WAS NOTED THAT AT CERTAIN OCCURRENCE, THE SENSORS HAVE GIVEN
INFORMATION AS QUCIK AS 5 M/S2, SNAG AT 48 CM, ALL ENGINES WORKING (I.E.
ENGINE USEFULNESS 1111), AND BATTERY IS 75%.
I) WRITE THE STATUS STRING IN PARALLEL FOR THIS CASE
Ans: 010111111
II)REPRESENT THE STATUS STRING ON ASK, FSK, AND PSK ENCODING
STRATEGIES.
WIRELESS COMMUNICATION
STUDENT ID 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
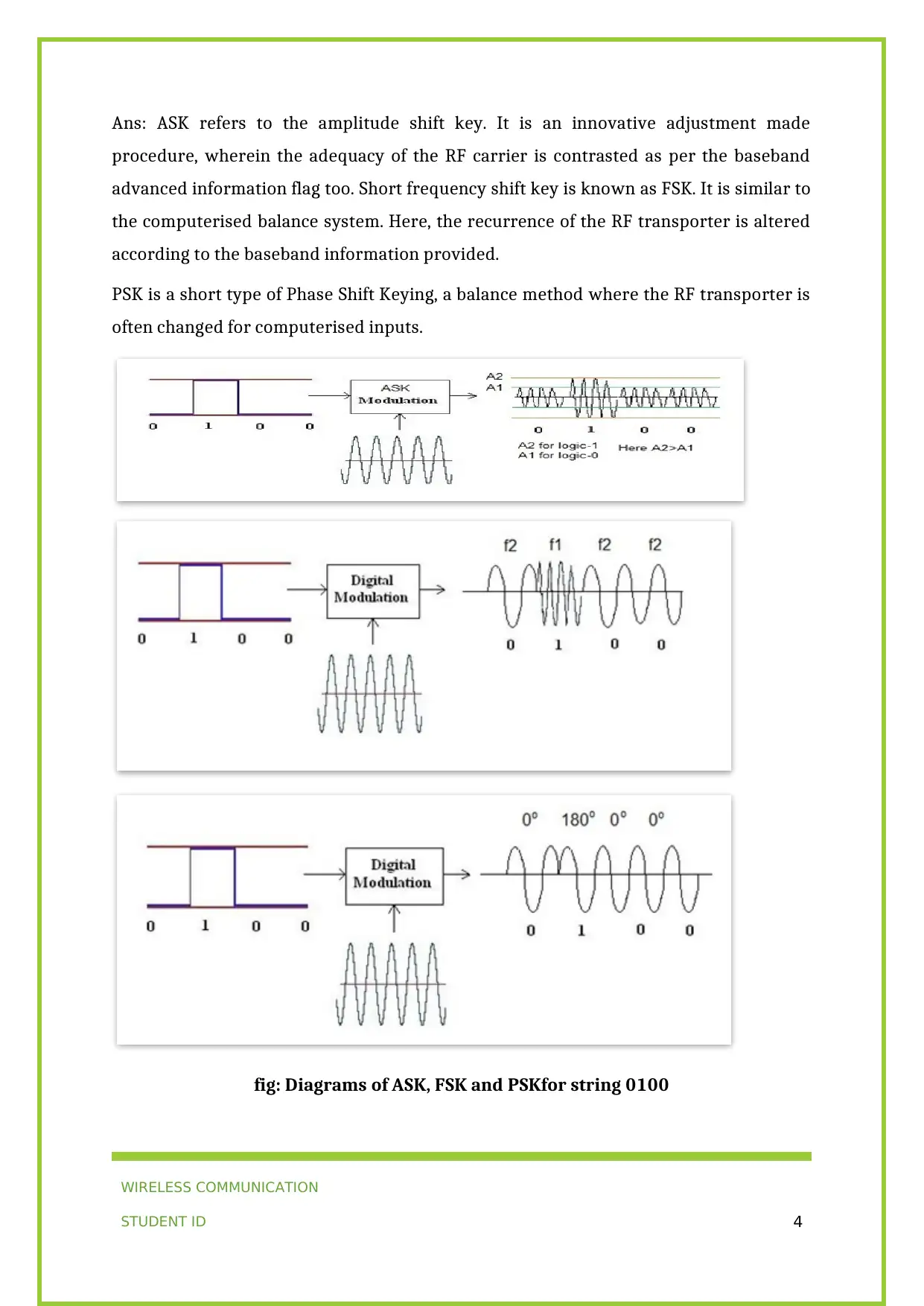
Ans: ASK refers to the amplitude shift key. It is an innovative adjustment made
procedure, wherein the adequacy of the RF carrier is contrasted as per the baseband
advanced information flag too. Short frequency shift key is known as FSK. It is similar to
the computerised balance system. Here, the recurrence of the RF transporter is altered
according to the baseband information provided.
PSK is a short type of Phase Shift Keying, a balance method where the RF transporter is
often changed for computerised inputs.
fig: Diagrams of ASK, FSK and PSKfor string 0100
WIRELESS COMMUNICATION
STUDENT ID 4
procedure, wherein the adequacy of the RF carrier is contrasted as per the baseband
advanced information flag too. Short frequency shift key is known as FSK. It is similar to
the computerised balance system. Here, the recurrence of the RF transporter is altered
according to the baseband information provided.
PSK is a short type of Phase Shift Keying, a balance method where the RF transporter is
often changed for computerised inputs.
fig: Diagrams of ASK, FSK and PSKfor string 0100
WIRELESS COMMUNICATION
STUDENT ID 4
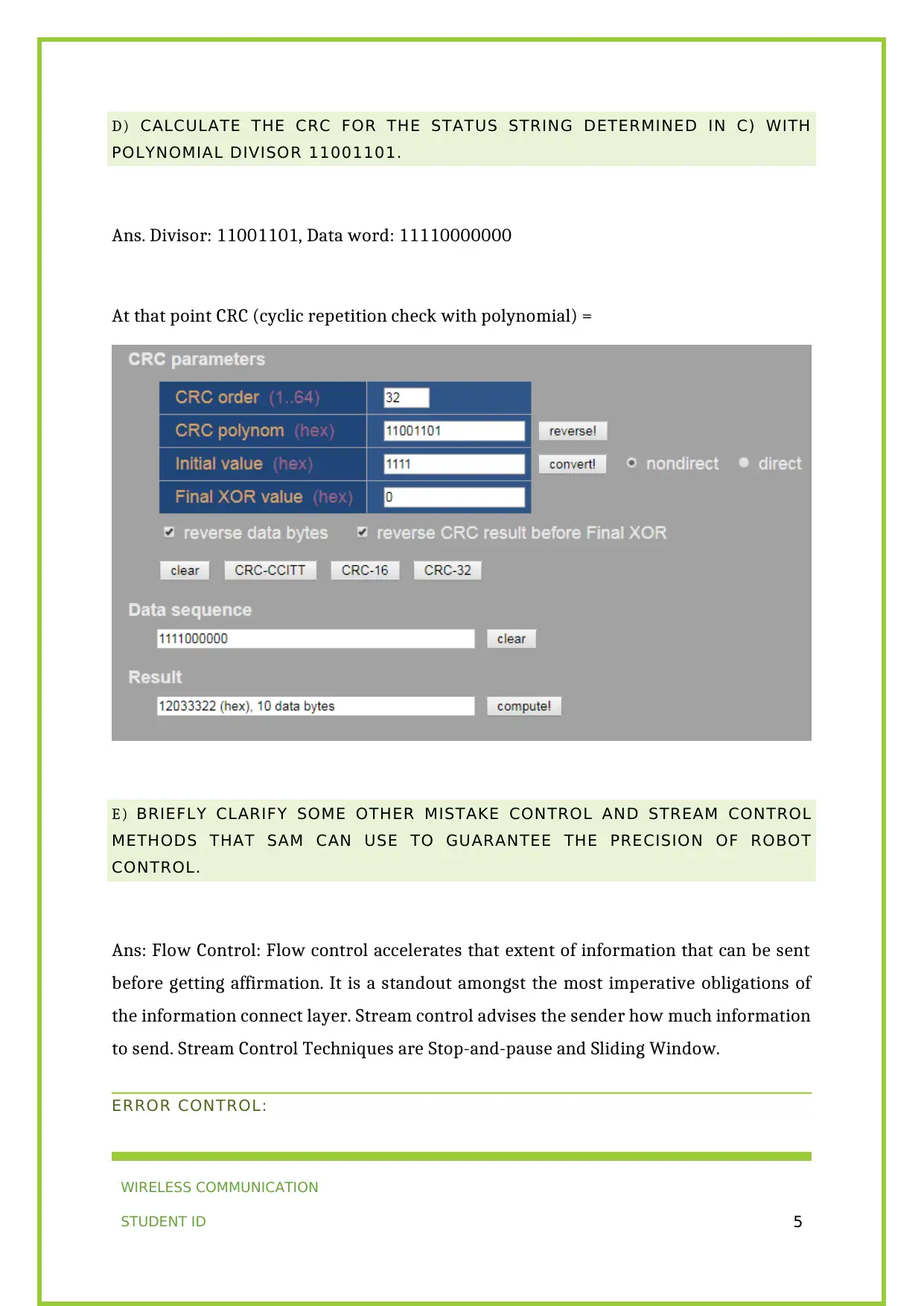
D) CALCULATE THE CRC FOR THE STATUS STRING DETERMINED IN C) WITH
POLYNOMIAL DIVISOR 11001101.
Ans. Divisor: 11001101, Data word: 11110000000
At that point CRC (cyclic repetition check with polynomial) =
E) BRIEFLY CLARIFY SOME OTHER MISTAKE CONTROL AND STREAM CONTROL
METHODS THAT SAM CAN USE TO GUARANTEE THE PRECISION OF ROBOT
CONTROL.
Ans: Flow Control: Flow control accelerates that extent of information that can be sent
before getting affirmation. It is a standout amongst the most imperative obligations of
the information connect layer. Stream control advises the sender how much information
to send. Stream Control Techniques are Stop-and-pause and Sliding Window.
ERROR CONTROL:
WIRELESS COMMUNICATION
STUDENT ID 5
POLYNOMIAL DIVISOR 11001101.
Ans. Divisor: 11001101, Data word: 11110000000
At that point CRC (cyclic repetition check with polynomial) =
E) BRIEFLY CLARIFY SOME OTHER MISTAKE CONTROL AND STREAM CONTROL
METHODS THAT SAM CAN USE TO GUARANTEE THE PRECISION OF ROBOT
CONTROL.
Ans: Flow Control: Flow control accelerates that extent of information that can be sent
before getting affirmation. It is a standout amongst the most imperative obligations of
the information connect layer. Stream control advises the sender how much information
to send. Stream Control Techniques are Stop-and-pause and Sliding Window.
ERROR CONTROL:
WIRELESS COMMUNICATION
STUDENT ID 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Error control in the information connect layer depends on ARQ (programmed rehash
asks for), which is the retransmission of information. The term mistake control alludes
to techniques for fault identification and retransmission. Whenever a blunder is
identified in a trade, indicated outlines are retransmitted. This procedure is called ARQ.
To guarantee dependable correspondence, there necessities to exist stream control
(dealing with the measure of information the sender sends), and mistake control (that
information touches base at the goal blunder free).
Flow and Error control should be done at a few layers. For hub to-hub connections,
stream and mistake control is done in the information interface layer. For end-point to
end-point, stream and blunder control is completed in the vehicle layer. Numerous
elements including line clamour can change or wipe out at least one bits of a given
information unit. Dependable frameworks must have component for identifying and
revising such mistakes. Mistake identification and amendment are executed either at
the information connect layer or the vehicle layer of the OSI demonstrate.
FOLLOWING ARE THE FLOW AND ERROR CONTROL PROCEDURES:
Stop-and-Wait ARQ,
Go-back N ARQ,
Selective Repeat ARQ
(i)Stop & Wait Flow control:
WIRELESS COMMUNICATION
STUDENT ID 6
asks for), which is the retransmission of information. The term mistake control alludes
to techniques for fault identification and retransmission. Whenever a blunder is
identified in a trade, indicated outlines are retransmitted. This procedure is called ARQ.
To guarantee dependable correspondence, there necessities to exist stream control
(dealing with the measure of information the sender sends), and mistake control (that
information touches base at the goal blunder free).
Flow and Error control should be done at a few layers. For hub to-hub connections,
stream and mistake control is done in the information interface layer. For end-point to
end-point, stream and blunder control is completed in the vehicle layer. Numerous
elements including line clamour can change or wipe out at least one bits of a given
information unit. Dependable frameworks must have component for identifying and
revising such mistakes. Mistake identification and amendment are executed either at
the information connect layer or the vehicle layer of the OSI demonstrate.
FOLLOWING ARE THE FLOW AND ERROR CONTROL PROCEDURES:
Stop-and-Wait ARQ,
Go-back N ARQ,
Selective Repeat ARQ
(i)Stop & Wait Flow control:
WIRELESS COMMUNICATION
STUDENT ID 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The sender needs to sit tight for an affirmation of each edge that it sends. Just when an
affirmation has been gotten is the following edge sent. In Stop&Wait stream control,
beneficiary shows the availability getting information for casing. For each casing that is
sent, there should be an affirmation, which takes a comparable measure of engendering
time to return to the sender. Just a single edge can be in transmission at once. This
prompts wastefulness if spread deferral is any longer than the transmission delay
(ii) Go-back-n ARQ: -
Collector window measure is 1. In this strategy, on the off chance that one casing is lost
or harmed all edges sent, since the last edge renowned are retransmitted.
(ii) Selective Repeat ARQ: new highlights:
In this process only, damage packet is retransmit.
So that Sam can use one of them to ensure the accuracy of robot control.
WIRELESS COMMUNICATION
STUDENT ID 7
affirmation has been gotten is the following edge sent. In Stop&Wait stream control,
beneficiary shows the availability getting information for casing. For each casing that is
sent, there should be an affirmation, which takes a comparable measure of engendering
time to return to the sender. Just a single edge can be in transmission at once. This
prompts wastefulness if spread deferral is any longer than the transmission delay
(ii) Go-back-n ARQ: -
Collector window measure is 1. In this strategy, on the off chance that one casing is lost
or harmed all edges sent, since the last edge renowned are retransmitted.
(ii) Selective Repeat ARQ: new highlights:
In this process only, damage packet is retransmit.
So that Sam can use one of them to ensure the accuracy of robot control.
WIRELESS COMMUNICATION
STUDENT ID 7

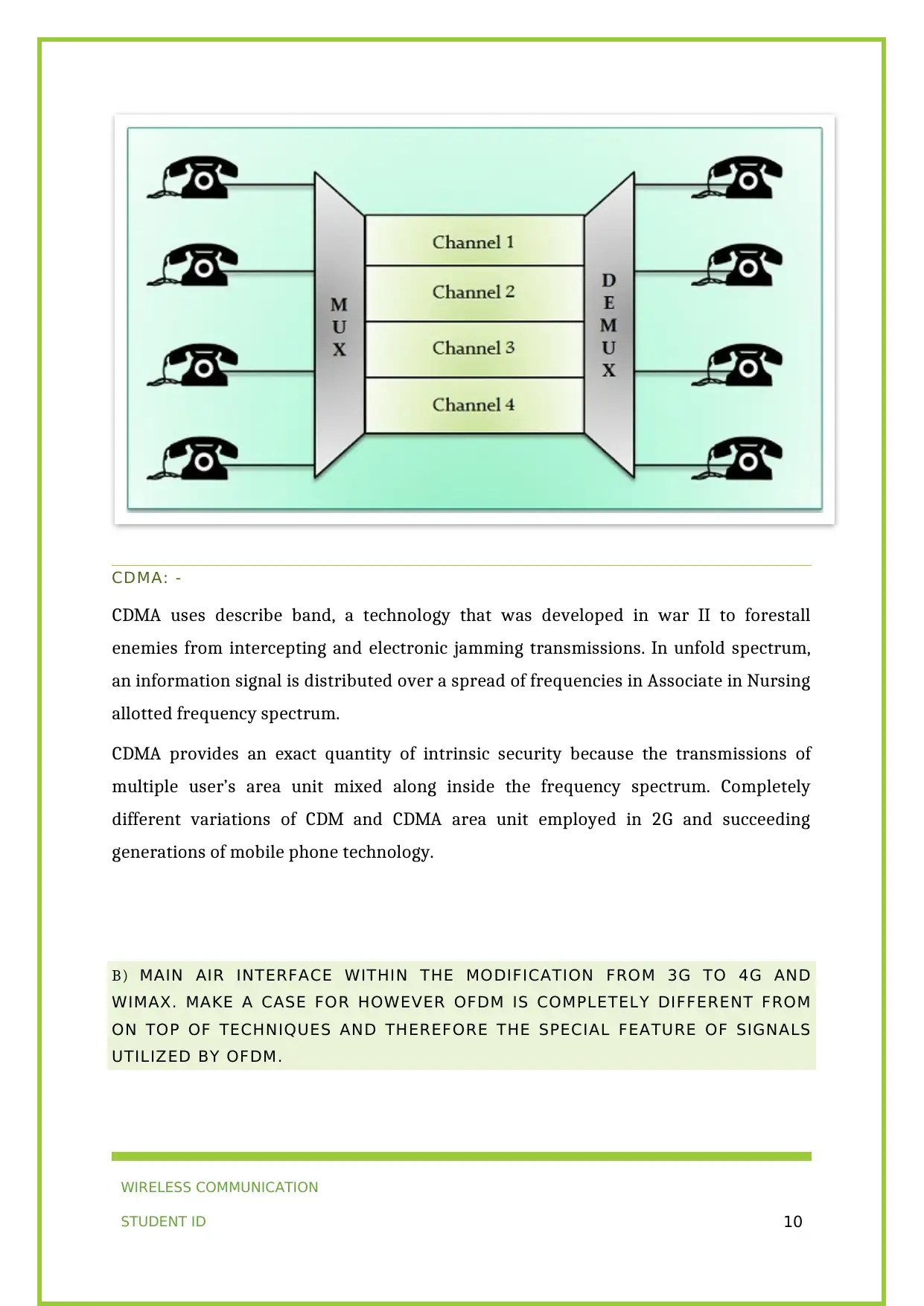
PART II: MULTIPLEXING AND MULTIPLE ACCESS
Multiplexing plays a crucial role in communication because it permits the mix of
multiple streams along. completely different multiplexing techniques area unit used for
numerous applications.
A) EXPLAIN TDM, FDM AND CDMA MULTIPLEXING TECHNIQUES WITH
APPROPRIATE DIAGRAMS.
Ans. Multiplexing could be a technique through that many signals area unit at the same
time transmitted over one link. Multiplexed system involves n range of devices that
share the capability of 1 link that’s however a link (path) will have multiple channels. At
the receiver, the only stream is directed to the Demultiplexer (DEMUX), that is once
more translated into its part transmission and sent to their supposed receivers.
TDM is taken into account to be a digital procedure which might be used once the
transmission medium rate amount is over the information rate requisite of the
transmission and receiving devices. every frame consists of a group of your time slots,
and parts of every supply is allotted a time interval per frame.
WIRELESS COMMUNICATION
STUDENT ID 8
Multiplexing plays a crucial role in communication because it permits the mix of
multiple streams along. completely different multiplexing techniques area unit used for
numerous applications.
A) EXPLAIN TDM, FDM AND CDMA MULTIPLEXING TECHNIQUES WITH
APPROPRIATE DIAGRAMS.
Ans. Multiplexing could be a technique through that many signals area unit at the same
time transmitted over one link. Multiplexed system involves n range of devices that
share the capability of 1 link that’s however a link (path) will have multiple channels. At
the receiver, the only stream is directed to the Demultiplexer (DEMUX), that is once
more translated into its part transmission and sent to their supposed receivers.
TDM is taken into account to be a digital procedure which might be used once the
transmission medium rate amount is over the information rate requisite of the
transmission and receiving devices. every frame consists of a group of your time slots,
and parts of every supply is allotted a time interval per frame.
WIRELESS COMMUNICATION
STUDENT ID 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
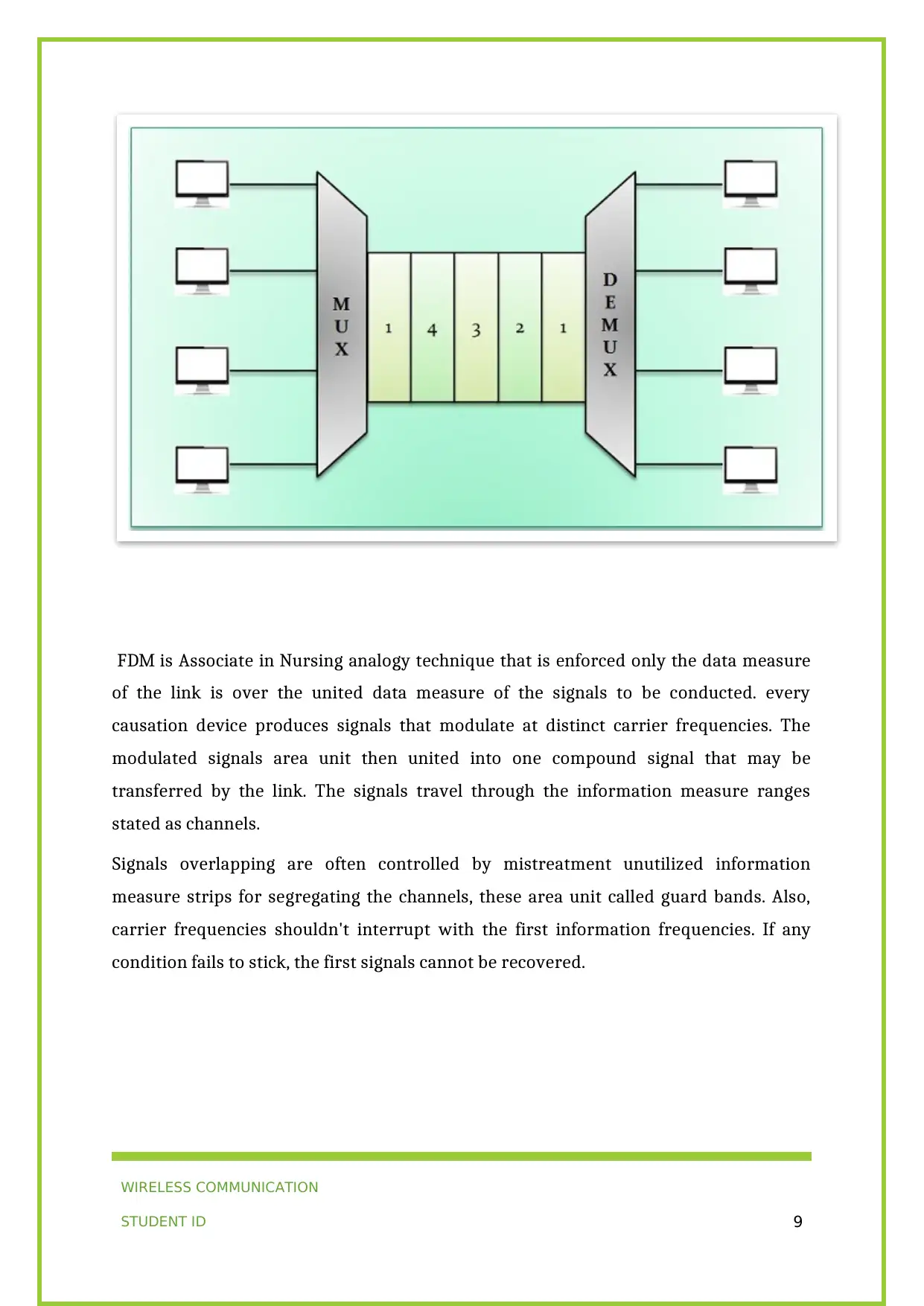
FDM is Associate in Nursing analogy technique that is enforced only the data measure
of the link is over the united data measure of the signals to be conducted. every
causation device produces signals that modulate at distinct carrier frequencies. The
modulated signals area unit then united into one compound signal that may be
transferred by the link. The signals travel through the information measure ranges
stated as channels.
Signals overlapping are often controlled by mistreatment unutilized information
measure strips for segregating the channels, these area unit called guard bands. Also,
carrier frequencies shouldn't interrupt with the first information frequencies. If any
condition fails to stick, the first signals cannot be recovered.
WIRELESS COMMUNICATION
STUDENT ID 9
of the link is over the united data measure of the signals to be conducted. every
causation device produces signals that modulate at distinct carrier frequencies. The
modulated signals area unit then united into one compound signal that may be
transferred by the link. The signals travel through the information measure ranges
stated as channels.
Signals overlapping are often controlled by mistreatment unutilized information
measure strips for segregating the channels, these area unit called guard bands. Also,
carrier frequencies shouldn't interrupt with the first information frequencies. If any
condition fails to stick, the first signals cannot be recovered.
WIRELESS COMMUNICATION
STUDENT ID 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CDMA: -
CDMA uses describe band, a technology that was developed in war II to forestall
enemies from intercepting and electronic jamming transmissions. In unfold spectrum,
an information signal is distributed over a spread of frequencies in Associate in Nursing
allotted frequency spectrum.
CDMA provides an exact quantity of intrinsic security because the transmissions of
multiple user’s area unit mixed along inside the frequency spectrum. Completely
different variations of CDM and CDMA area unit employed in 2G and succeeding
generations of mobile phone technology.
B) MAIN AIR INTERFACE WITHIN THE MODIFICATION FROM 3G TO 4G AND
WIMAX. MAKE A CASE FOR HOWEVER OFDM IS COMPLETELY DIFFERENT FROM
ON TOP OF TECHNIQUES AND THEREFORE THE SPECIAL FEATURE OF SIGNALS
UTILIZED BY OFDM.
WIRELESS COMMUNICATION
STUDENT ID 10
CDMA uses describe band, a technology that was developed in war II to forestall
enemies from intercepting and electronic jamming transmissions. In unfold spectrum,
an information signal is distributed over a spread of frequencies in Associate in Nursing
allotted frequency spectrum.
CDMA provides an exact quantity of intrinsic security because the transmissions of
multiple user’s area unit mixed along inside the frequency spectrum. Completely
different variations of CDM and CDMA area unit employed in 2G and succeeding
generations of mobile phone technology.
B) MAIN AIR INTERFACE WITHIN THE MODIFICATION FROM 3G TO 4G AND
WIMAX. MAKE A CASE FOR HOWEVER OFDM IS COMPLETELY DIFFERENT FROM
ON TOP OF TECHNIQUES AND THEREFORE THE SPECIAL FEATURE OF SIGNALS
UTILIZED BY OFDM.
WIRELESS COMMUNICATION
STUDENT ID 10

Ans: WiMAX technology was introduced by the Institute of Electrical and Electronic
Engineers (IEEE). It had a customary selection of 802.16d-2004 (used in mounted
wireless applications) and 802.16e-2005 (mobile wireless) in order to ensure supply of
worldwide microwave access. Since telecommunication industry is extremely involved
with wireless communication, the numerous transmission modes were established for
this purpose to be solved.
Technologies 3G 4G
Design Began 1990 2000
Developed 2002 2010
Cellular Services
Higher Capacity, Broadband Data up to
2Mbps
Higher Capacity, completely IP Based,
Multimedia Data
Versions WCDMA, CDMA-2000 OFDM, UWB
Bandwidth 2 Mbps 10 Mbps - 20 Mbps
Multiplexing CDMA FDMA, TDMA, CDMA
Core Network Packet Network All-IP Networks
C)IEEE 802.11AC WIRELESS LAN CUSTOMARY USES FORTY MEGACYCLES PER
SECOND TOTAL INFORMATION MEASURE IN OFDM THEME.
I)FOR FORTY-EIGHT SUBSCRIBERS WHAT OUGHT TO BE THE SUBCARRIER
INFORMATION MEASURE (FB)?
Ans: In OFDM system, the carrier’s area unit curving to amounted curving signals area
unit known as orthogonal once the product is adequate to 0 over one stage.
II)PROPOSE AN ACCEPTABLE SUBCARRIER BIT TIME OF T TO ATTAIN
ORTHOGONALITY?
WIRELESS COMMUNICATION
STUDENT ID 11
Engineers (IEEE). It had a customary selection of 802.16d-2004 (used in mounted
wireless applications) and 802.16e-2005 (mobile wireless) in order to ensure supply of
worldwide microwave access. Since telecommunication industry is extremely involved
with wireless communication, the numerous transmission modes were established for
this purpose to be solved.
Technologies 3G 4G
Design Began 1990 2000
Developed 2002 2010
Cellular Services
Higher Capacity, Broadband Data up to
2Mbps
Higher Capacity, completely IP Based,
Multimedia Data
Versions WCDMA, CDMA-2000 OFDM, UWB
Bandwidth 2 Mbps 10 Mbps - 20 Mbps
Multiplexing CDMA FDMA, TDMA, CDMA
Core Network Packet Network All-IP Networks
C)IEEE 802.11AC WIRELESS LAN CUSTOMARY USES FORTY MEGACYCLES PER
SECOND TOTAL INFORMATION MEASURE IN OFDM THEME.
I)FOR FORTY-EIGHT SUBSCRIBERS WHAT OUGHT TO BE THE SUBCARRIER
INFORMATION MEASURE (FB)?
Ans: In OFDM system, the carrier’s area unit curving to amounted curving signals area
unit known as orthogonal once the product is adequate to 0 over one stage.
II)PROPOSE AN ACCEPTABLE SUBCARRIER BIT TIME OF T TO ATTAIN
ORTHOGONALITY?
WIRELESS COMMUNICATION
STUDENT ID 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


