Wireless Communication Report: Channel Reuse, WMAN, IoT Technologies
VerifiedAdded on 2020/05/28
|15
|1529
|40
Report
AI Summary
This report provides a comprehensive analysis of wireless communication technologies. It begins by exploring channel reuse in WLAN networks, discussing its dynamic control on receive sensitivity and the different modes of configuration. The report then delves into WMAN technologies, examining backhaul and last-mile security challenges, including the security issues arising from microcells and small cells, as well as API management vulnerabilities. Furthermore, the report investigates the Internet of Things (IoT), analyzing two research papers focusing on ZigBee technology and the transition from the Intranet of Things to a future Internet of Things, highlighting technical challenges and potential solutions related to wireless and mobility networking. The report concludes by referencing the sources used. This report is a valuable resource for students studying wireless communication, offering detailed insights into key concepts and technologies.

Running head: WIRELESS COMMUNICATION
Wireless Communication
Name of Student-
Name of University-
Author’s Note-
Wireless Communication
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS COMMUNICATION
Table of Contents
Answer to question 1:..........................................................................................................2
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................4
Answer to Question 4:.........................................................................................................6
References..........................................................................................................................13
Table of Contents
Answer to question 1:..........................................................................................................2
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................4
Answer to Question 4:.........................................................................................................6
References..........................................................................................................................13

2WIRELESS COMMUNICATION
Answer to question 1:
The main work of channel reuse in the network of WLAN is that it can have dynamic
control on Rx (receive sensitivity). The dynamic control helps to improve spatial reuse in the
network (Zhai et al. 2013). The feature of channel reuse is mainly applied to the channels of non-
DFS. Channels of reuse are made disabled for the DFS Channels and also do not reflect the
detection of DFS Radar Signature. There are mainly three features of channel reuse that are
configured. They are static modes, disable modes, and dynamic modes. Whereas, the frequencies
that are allowed for services are then reused in area of regular pattern in mobile phones. The
mobile networking areas are mostly known as cells. All the areas of the mobile phones are
covered by only one base station. All the works that are done in this era of digitization are gone
wireless (Wu, Ahn & Kim, 2013). The interchange of a device can also be done without using
the wire. The technology has already changed the way that people uses digital technology and
digital gadgets. Technology has given a rise in the in subject accreditation in the master’s degree
and in bachelor’s degree.
The wireless technology has some basic fundamentals. The mobile phones that are used
get network from the radio waves. The waves of the mobile phones are mainly composed of
lengthy and diverse bandwidth and also have lengthy frequency (Saquib, Hossain & Kim, 2013).
The frequencies that are allocated to service are mainly used in a regular pattern called the cells
that are covered by a base station. The nets of these cells in the mobile are mostly of hexagonal
pattern. The cells are used in an adjacent way so that there is a mutual interference between the
users and the users have to remain below the harmful level. The cell which gets separated away
reuses their frequencies. The cellphone is defined as wireless phones (Bernardos et al., 2014).
Answer to question 1:
The main work of channel reuse in the network of WLAN is that it can have dynamic
control on Rx (receive sensitivity). The dynamic control helps to improve spatial reuse in the
network (Zhai et al. 2013). The feature of channel reuse is mainly applied to the channels of non-
DFS. Channels of reuse are made disabled for the DFS Channels and also do not reflect the
detection of DFS Radar Signature. There are mainly three features of channel reuse that are
configured. They are static modes, disable modes, and dynamic modes. Whereas, the frequencies
that are allowed for services are then reused in area of regular pattern in mobile phones. The
mobile networking areas are mostly known as cells. All the areas of the mobile phones are
covered by only one base station. All the works that are done in this era of digitization are gone
wireless (Wu, Ahn & Kim, 2013). The interchange of a device can also be done without using
the wire. The technology has already changed the way that people uses digital technology and
digital gadgets. Technology has given a rise in the in subject accreditation in the master’s degree
and in bachelor’s degree.
The wireless technology has some basic fundamentals. The mobile phones that are used
get network from the radio waves. The waves of the mobile phones are mainly composed of
lengthy and diverse bandwidth and also have lengthy frequency (Saquib, Hossain & Kim, 2013).
The frequencies that are allocated to service are mainly used in a regular pattern called the cells
that are covered by a base station. The nets of these cells in the mobile are mostly of hexagonal
pattern. The cells are used in an adjacent way so that there is a mutual interference between the
users and the users have to remain below the harmful level. The cell which gets separated away
reuses their frequencies. The cellphone is defined as wireless phones (Bernardos et al., 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3WIRELESS COMMUNICATION
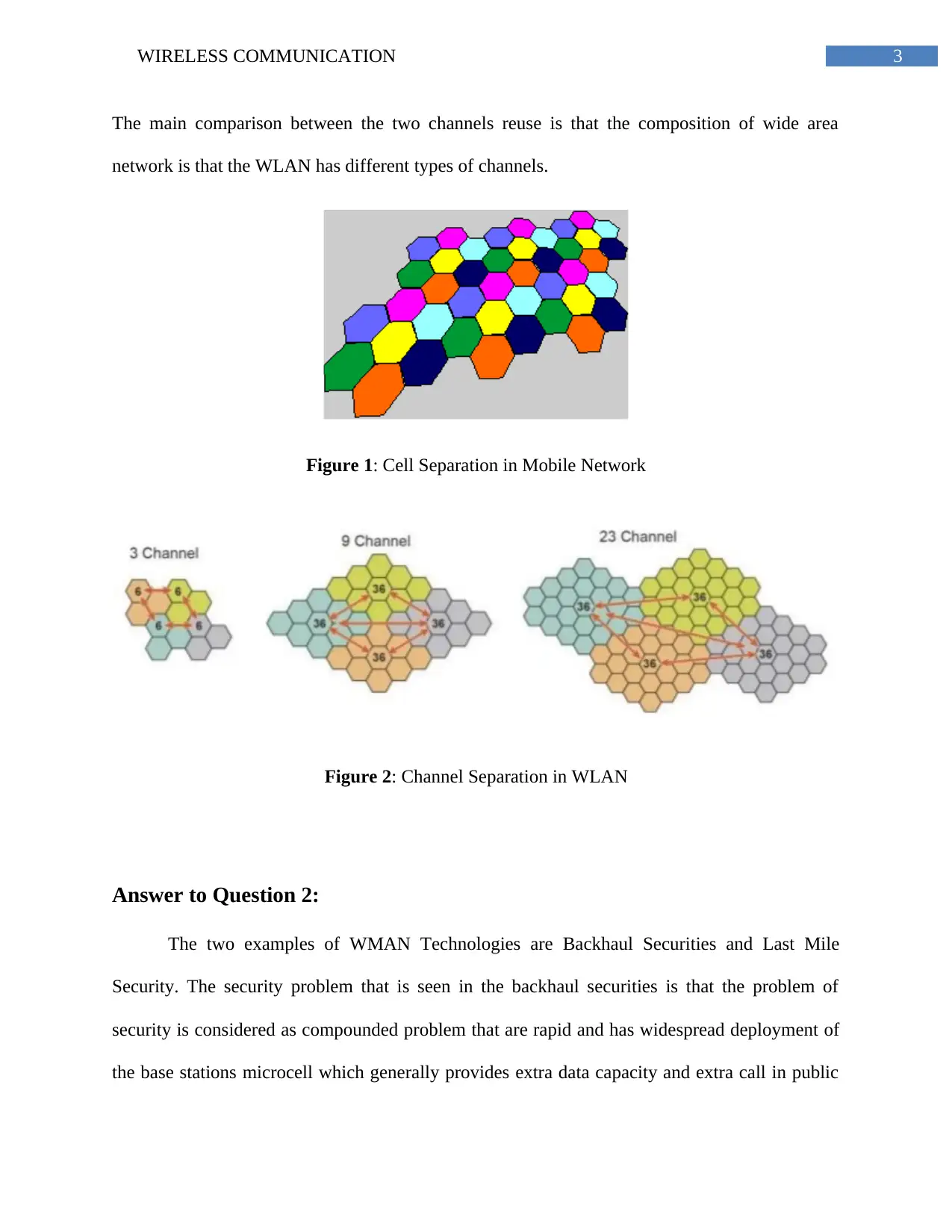
The main comparison between the two channels reuse is that the composition of wide area
network is that the WLAN has different types of channels.
Figure 1: Cell Separation in Mobile Network
Figure 2: Channel Separation in WLAN
Answer to Question 2:
The two examples of WMAN Technologies are Backhaul Securities and Last Mile
Security. The security problem that is seen in the backhaul securities is that the problem of
security is considered as compounded problem that are rapid and has widespread deployment of
the base stations microcell which generally provides extra data capacity and extra call in public
The main comparison between the two channels reuse is that the composition of wide area
network is that the WLAN has different types of channels.
Figure 1: Cell Separation in Mobile Network
Figure 2: Channel Separation in WLAN
Answer to Question 2:
The two examples of WMAN Technologies are Backhaul Securities and Last Mile
Security. The security problem that is seen in the backhaul securities is that the problem of
security is considered as compounded problem that are rapid and has widespread deployment of
the base stations microcell which generally provides extra data capacity and extra call in public
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS COMMUNICATION
areas that includes office complexes or shopping malls (Bouhafs, Mackay & Merabti, 2014). The
analyst of Heavy Reading generally expects that the number of cellular sites mainly grow in
about 50 % by the end of 2015 which is estimated to about eight million cellular sites
approximately. The new sites that will be created will be generally have micro cells and small
cells that are demanded to deliver an extra bandwidth to a lower cost of subscription.
The security issue in Last Mile Security is the API management platforms that mainly
allow the provider of API to apply some security policies on proxies. This mainly works for the
calls of API from outside of the enterprise and also disciplined consumers from the enterprise
that generally goes through the API platform. But, a disgruntle employee or rogue API consumer
may be able to bypass all the securities that are present on the gateway of the network and invoke
to the backend directly (Cheng, Huang & Du, 2013). The security can also be bypassed by a
consumer who has external API by the process of leveraging the vulnerabilities of the firewall or
by phishing method. The attacks or security issues that are faced by this kind of WMAN
networks are generally known as end run attacks. There should always a good practice at the
backend of API so that they can be secured in the public network.
Answer to Question 3:
The two research papers on Internet of Things have described about the ZigBee
technology and Intranet of Things (Elarabi, Deep & Rai, 2015). The first research paper, namely,
“Design and Simulation of State-of-Art ZigBee Transmitter for IoT Wireless Devices” discusses
regarding the fast development of wireless networking that has occurred in the past few years.
The main aim of this wireless networking was the higher speed and longer range of applications.
The incrementing requirement for less power consumption and less data has shown the path for
developing ZigBee technology. The development of ZigBee technology was eventually done for
areas that includes office complexes or shopping malls (Bouhafs, Mackay & Merabti, 2014). The
analyst of Heavy Reading generally expects that the number of cellular sites mainly grow in
about 50 % by the end of 2015 which is estimated to about eight million cellular sites
approximately. The new sites that will be created will be generally have micro cells and small
cells that are demanded to deliver an extra bandwidth to a lower cost of subscription.
The security issue in Last Mile Security is the API management platforms that mainly
allow the provider of API to apply some security policies on proxies. This mainly works for the
calls of API from outside of the enterprise and also disciplined consumers from the enterprise
that generally goes through the API platform. But, a disgruntle employee or rogue API consumer
may be able to bypass all the securities that are present on the gateway of the network and invoke
to the backend directly (Cheng, Huang & Du, 2013). The security can also be bypassed by a
consumer who has external API by the process of leveraging the vulnerabilities of the firewall or
by phishing method. The attacks or security issues that are faced by this kind of WMAN
networks are generally known as end run attacks. There should always a good practice at the
backend of API so that they can be secured in the public network.
Answer to Question 3:
The two research papers on Internet of Things have described about the ZigBee
technology and Intranet of Things (Elarabi, Deep & Rai, 2015). The first research paper, namely,
“Design and Simulation of State-of-Art ZigBee Transmitter for IoT Wireless Devices” discusses
regarding the fast development of wireless networking that has occurred in the past few years.
The main aim of this wireless networking was the higher speed and longer range of applications.
The incrementing requirement for less power consumption and less data has shown the path for
developing ZigBee technology. The development of ZigBee technology was eventually done for

5WIRELESS COMMUNICATION
the WPAN or Wireless Personal Area Networks, focussed at the management and all the
applications related to military (Elarabi, Deep & Rai, 2015). The major requirements for these
applications were lower cost, lower rate of data and more battery life. The devices that are based
on ZigBee mainly operate in the frequency bands of 868MHz, 915MHz and even 2.4GHz. The
maximum rate of data for ZigBee technology is 250K bits per second. The research paper has
also described about the different blocks of architecture of a ZigBee transmitter. ZigBee
technology has probable applications in IoT, for the reason that it is a specific device of lower
power and less rate of data (Elarabi, Deep & Rai, 2015). The focus of the research paper is given
to the designing of any ZigBee transmitter by utilizing Verilog for applications of IoT.
The second research paper namely, “From Today’s Intranet of Things to a Future Internet
of Things: A Wireless- and Mobility- Related View”, mainly describes about the recent state of
IoT, and the procedure of how the present situation of the Intranets of Things can change into a
more integrated system (Zorzi et al., 2010). The research paper has also summarized about the
major technical challenges regarding wireless networking and mobility networking. It has also
outlined about some of the preliminary ideas on the procedure of addressing the challenges in
IoT.
the WPAN or Wireless Personal Area Networks, focussed at the management and all the
applications related to military (Elarabi, Deep & Rai, 2015). The major requirements for these
applications were lower cost, lower rate of data and more battery life. The devices that are based
on ZigBee mainly operate in the frequency bands of 868MHz, 915MHz and even 2.4GHz. The
maximum rate of data for ZigBee technology is 250K bits per second. The research paper has
also described about the different blocks of architecture of a ZigBee transmitter. ZigBee
technology has probable applications in IoT, for the reason that it is a specific device of lower
power and less rate of data (Elarabi, Deep & Rai, 2015). The focus of the research paper is given
to the designing of any ZigBee transmitter by utilizing Verilog for applications of IoT.
The second research paper namely, “From Today’s Intranet of Things to a Future Internet
of Things: A Wireless- and Mobility- Related View”, mainly describes about the recent state of
IoT, and the procedure of how the present situation of the Intranets of Things can change into a
more integrated system (Zorzi et al., 2010). The research paper has also summarized about the
major technical challenges regarding wireless networking and mobility networking. It has also
outlined about some of the preliminary ideas on the procedure of addressing the challenges in
IoT.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIRELESS COMMUNICATION
Answer to Question 4:
Answer to Question 4:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7WIRELESS COMMUNICATION
8WIRELESS COMMUNICATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9WIRELESS COMMUNICATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10WIRELESS COMMUNICATION
11WIRELESS COMMUNICATION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





