MITS5003 - Wireless Networks and Communication: Robot Communication
VerifiedAdded on 2023/06/10
|12
|1563
|215
Homework Assignment
AI Summary
This assignment focuses on wireless networks and communication, specifically addressing encoding and error control, multiplexing and multiple access techniques, and WIFI technology. It includes calculations for data rates in robot communication, explanations of encoding techniques like NRZ, Polar, and Bi-Polar, and an application of ASK, FSK, and PSK encoding to a robot status string. The assignment also covers CRC calculation for error detection and discusses error and flow control techniques. Furthermore, it explores FDMA, TDMA, CDMA, and OFDM multiplexing techniques, highlighting their applications in different network scenarios. The document concludes with an overview of WIFI, including network backbones, BSS, ESS, throughput considerations, IEEE standards, and security strategies.

Wireless networks and communications
Abbymady
[Course title]
[Date]
Abbymady
[Course title]
[Date]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
PART I-Encoding and error control................................................................................1
Part II: Multiplexing and multiple accesses...................................................................4
Part:III-WIFI....................................................................................................................7
References.................................................................................................................9
Page 1 of 12
PART I-Encoding and error control................................................................................1
Part II: Multiplexing and multiple accesses...................................................................4
Part:III-WIFI....................................................................................................................7
References.................................................................................................................9
Page 1 of 12

PART I-Encoding and error control
a)In digital information, the data rate is the rate in bps (bits-per-
second).Channel capacity is a rate at which the information can be
transmitted over a channel. Hence, in certain conditions, this
phenomenon is known as channel capacity.
Remote control communication for robot as following as
Here
is absolute value of wave length
C iscapacity,
Finally
Here M is the no of discrete signal / bits of communication
That is
Total bits are transmission the robot for remote communications is 16-bit
operation can have performed.
b) Signal Encoding Technique are classified in 4 basic types they are
Ans: Encoding Techniques: -
1.NRZ
2.Polar
3.Bi-Polar
c)
i)As per the given data as following as
Data as acceleration 5 m/s2,
Obstacle at 48 cm
Battery is 75%.
Motor functionality 1111 that means in binary high [F or 15]
Based on the status string in binary in the form parallel is for support 16-
bit operation as like as 0010101010111111
Bit formation is
Page 2 of 12
a)In digital information, the data rate is the rate in bps (bits-per-
second).Channel capacity is a rate at which the information can be
transmitted over a channel. Hence, in certain conditions, this
phenomenon is known as channel capacity.
Remote control communication for robot as following as
Here
is absolute value of wave length
C iscapacity,
Finally
Here M is the no of discrete signal / bits of communication
That is
Total bits are transmission the robot for remote communications is 16-bit
operation can have performed.
b) Signal Encoding Technique are classified in 4 basic types they are
Ans: Encoding Techniques: -
1.NRZ
2.Polar
3.Bi-Polar
c)
i)As per the given data as following as
Data as acceleration 5 m/s2,
Obstacle at 48 cm
Battery is 75%.
Motor functionality 1111 that means in binary high [F or 15]
Based on the status string in binary in the form parallel is for support 16-
bit operation as like as 0010101010111111
Bit formation is
Page 2 of 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
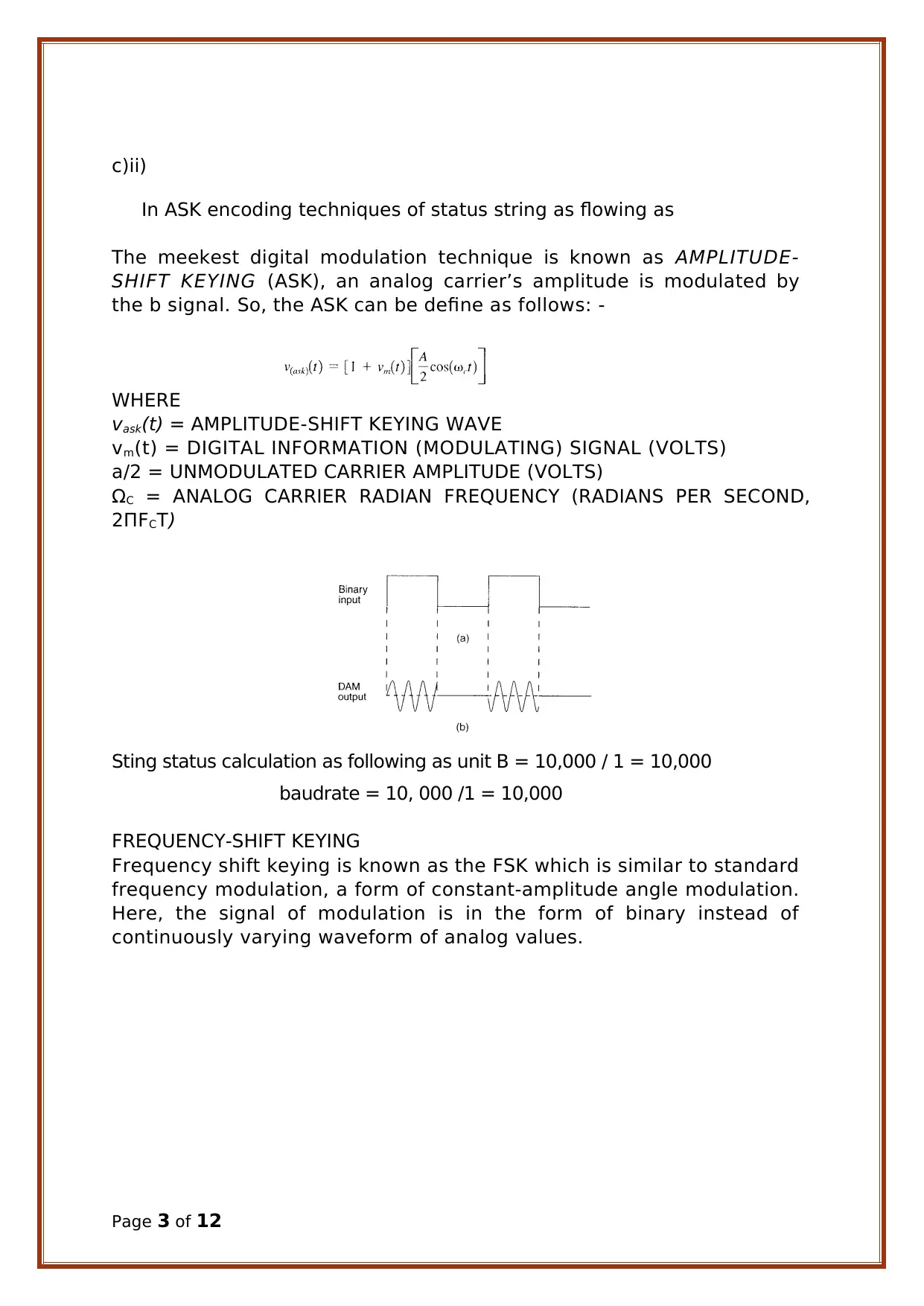
c)ii)
In ASK encoding techniques of status string as flowing as
The meekest digital modulation technique is known as AMPLITUDE-
SHIFT KEYING (ASK), an analog carrier’s amplitude is modulated by
the b signal. So, the ASK can be define as follows: -
WHERE
vask(t) = AMPLITUDE-SHIFT KEYING WAVE
vm(t) = DIGITAL INFORMATION (MODULATING) SIGNAL (VOLTS)
a/2 = UNMODULATED CARRIER AMPLITUDE (VOLTS)
ΩC = ANALOG CARRIER RADIAN FREQUENCY (RADIANS PER SECOND,
2ΠFCT)
Sting status calculation as following as unit B = 10,000 / 1 = 10,000
baudrate = 10, 000 /1 = 10,000
FREQUENCY-SHIFT KEYING
Frequency shift keying is known as the FSK which is similar to standard
frequency modulation, a form of constant-amplitude angle modulation.
Here, the signal of modulation is in the form of binary instead of
continuously varying waveform of analog values.
Page 3 of 12
In ASK encoding techniques of status string as flowing as
The meekest digital modulation technique is known as AMPLITUDE-
SHIFT KEYING (ASK), an analog carrier’s amplitude is modulated by
the b signal. So, the ASK can be define as follows: -
WHERE
vask(t) = AMPLITUDE-SHIFT KEYING WAVE
vm(t) = DIGITAL INFORMATION (MODULATING) SIGNAL (VOLTS)
a/2 = UNMODULATED CARRIER AMPLITUDE (VOLTS)
ΩC = ANALOG CARRIER RADIAN FREQUENCY (RADIANS PER SECOND,
2ΠFCT)
Sting status calculation as following as unit B = 10,000 / 1 = 10,000
baudrate = 10, 000 /1 = 10,000
FREQUENCY-SHIFT KEYING
Frequency shift keying is known as the FSK which is similar to standard
frequency modulation, a form of constant-amplitude angle modulation.
Here, the signal of modulation is in the form of binary instead of
continuously varying waveform of analog values.
Page 3 of 12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
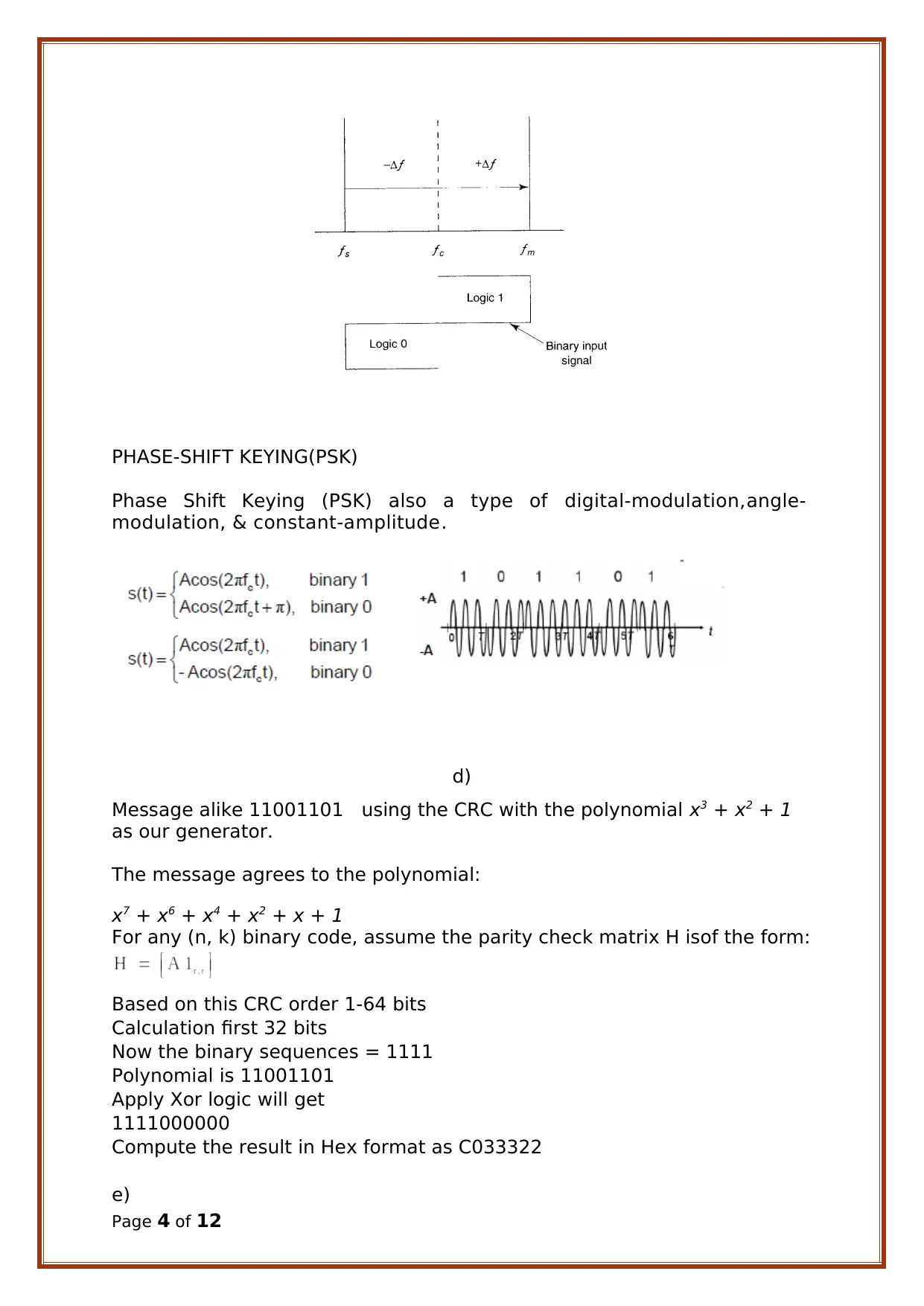
PHASE-SHIFT KEYING(PSK)
Phase Shift Keying (PSK) also a type of digital-modulation,angle-
modulation, & constant-amplitude.
d)
Message alike 11001101 using the CRC with the polynomial x3 + x2 + 1
as our generator.
The message agrees to the polynomial:
x7 + x6 + x4 + x2 + x + 1
For any (n, k) binary code, assume the parity check matrix H isof the form:
Based on this CRC order 1-64 bits
Calculation first 32 bits
Now the binary sequences = 1111
Polynomial is 11001101
Apply Xor logic will get
1111000000
Compute the result in Hex format as C033322
e)
Page 4 of 12
Phase Shift Keying (PSK) also a type of digital-modulation,angle-
modulation, & constant-amplitude.
d)
Message alike 11001101 using the CRC with the polynomial x3 + x2 + 1
as our generator.
The message agrees to the polynomial:
x7 + x6 + x4 + x2 + x + 1
For any (n, k) binary code, assume the parity check matrix H isof the form:
Based on this CRC order 1-64 bits
Calculation first 32 bits
Now the binary sequences = 1111
Polynomial is 11001101
Apply Xor logic will get
1111000000
Compute the result in Hex format as C033322
e)
Page 4 of 12
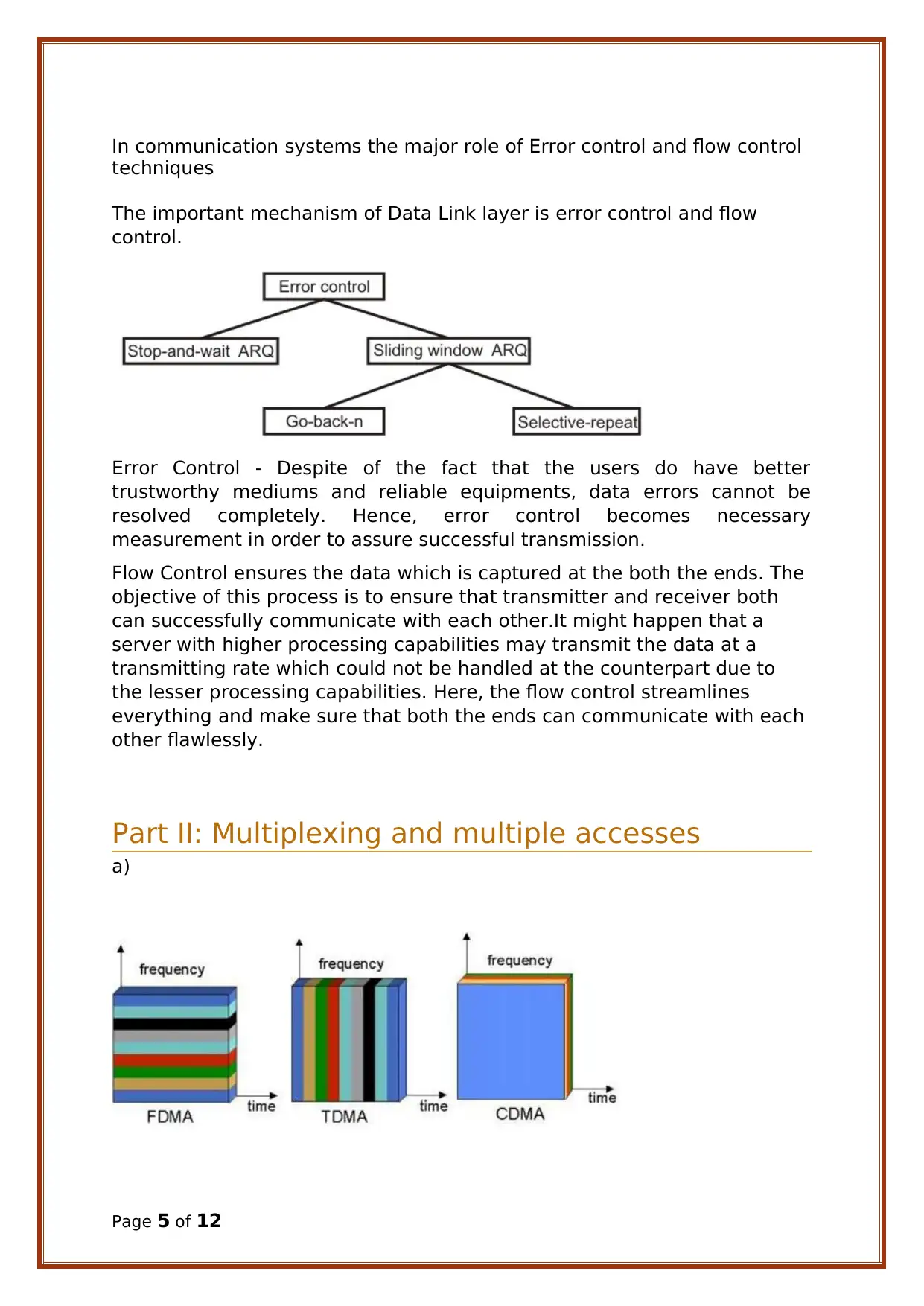
In communication systems the major role of Error control and flow control
techniques
The important mechanism of Data Link layer is error control and flow
control.
Error Control - Despite of the fact that the users do have better
trustworthy mediums and reliable equipments, data errors cannot be
resolved completely. Hence, error control becomes necessary
measurement in order to assure successful transmission.
Flow Control ensures the data which is captured at the both the ends. The
objective of this process is to ensure that transmitter and receiver both
can successfully communicate with each other.It might happen that a
server with higher processing capabilities may transmit the data at a
transmitting rate which could not be handled at the counterpart due to
the lesser processing capabilities. Here, the flow control streamlines
everything and make sure that both the ends can communicate with each
other flawlessly.
Part II: Multiplexing and multiple accesses
a)
Page 5 of 12
techniques
The important mechanism of Data Link layer is error control and flow
control.
Error Control - Despite of the fact that the users do have better
trustworthy mediums and reliable equipments, data errors cannot be
resolved completely. Hence, error control becomes necessary
measurement in order to assure successful transmission.
Flow Control ensures the data which is captured at the both the ends. The
objective of this process is to ensure that transmitter and receiver both
can successfully communicate with each other.It might happen that a
server with higher processing capabilities may transmit the data at a
transmitting rate which could not be handled at the counterpart due to
the lesser processing capabilities. Here, the flow control streamlines
everything and make sure that both the ends can communicate with each
other flawlessly.
Part II: Multiplexing and multiple accesses
a)
Page 5 of 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

FDMA (Frequency Division Multiple Access) unique frequency band or
channel is assigned to individually user, the same frequency cannot be
accessed by other user.
TDMA (Time-Division-Multiple-Access) ,the radio spectrum is
separated into time-span-slots.Now, each slot, is given to only one
user to receive or transmit data.
CDMA (Code Division Multiple Access) Here, special code sequence has
been assigned to each user who can independently and asynchronously
transmit and receive signals
b)
ORTHOGONAL FREQUENCY DIVISION MULTIPLEXING (OFDM) as a
resources of delivering power efficient signaling for vast users at the
similar channel. Individually frequency in equation (5.127) is modulated
with binary data (ON/OFF) to run a number of parallel carriers respectively
is comprising a percentage of user data. The 3g network can support only
cellular & PC ‘s
Page 6 of 12
channel is assigned to individually user, the same frequency cannot be
accessed by other user.
TDMA (Time-Division-Multiple-Access) ,the radio spectrum is
separated into time-span-slots.Now, each slot, is given to only one
user to receive or transmit data.
CDMA (Code Division Multiple Access) Here, special code sequence has
been assigned to each user who can independently and asynchronously
transmit and receive signals
b)
ORTHOGONAL FREQUENCY DIVISION MULTIPLEXING (OFDM) as a
resources of delivering power efficient signaling for vast users at the
similar channel. Individually frequency in equation (5.127) is modulated
with binary data (ON/OFF) to run a number of parallel carriers respectively
is comprising a percentage of user data. The 3g network can support only
cellular & PC ‘s
Page 6 of 12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Mobile WiMAX provides a simple IP network, with all IETF protocols LTE
network is a more complex multi-layer network burdened with proprietary
3G cellular protocols
c)
WLANs and PANs provide broadband telecommunications accessin the
local exchange, driven by demand for broadband Internet access from
business and homes due exponential development the internet.
1)
1 TU = 1024 microseconds
Beacon interval =100 TU (100x 1024 microseconds or 102.4 milliseconds)
Timestamp (8 byte)
Beacon Interval (2 byte)
.Capability info (2 byte)
.SSID (variable size)
. Supported Rates (variable size)
For48 subscribers using6 fbps
2)
Bit time of T to achieve orthogonality
3)
The fundamental design of OFDM transmissions imposts a huge number of
narrowband, orthogonal subcarriers to independently grip data
Page 7 of 12
network is a more complex multi-layer network burdened with proprietary
3G cellular protocols
c)
WLANs and PANs provide broadband telecommunications accessin the
local exchange, driven by demand for broadband Internet access from
business and homes due exponential development the internet.
1)
1 TU = 1024 microseconds
Beacon interval =100 TU (100x 1024 microseconds or 102.4 milliseconds)
Timestamp (8 byte)
Beacon Interval (2 byte)
.Capability info (2 byte)
.SSID (variable size)
. Supported Rates (variable size)
For48 subscribers using6 fbps
2)
Bit time of T to achieve orthogonality
3)
The fundamental design of OFDM transmissions imposts a huge number of
narrowband, orthogonal subcarriers to independently grip data
Page 7 of 12
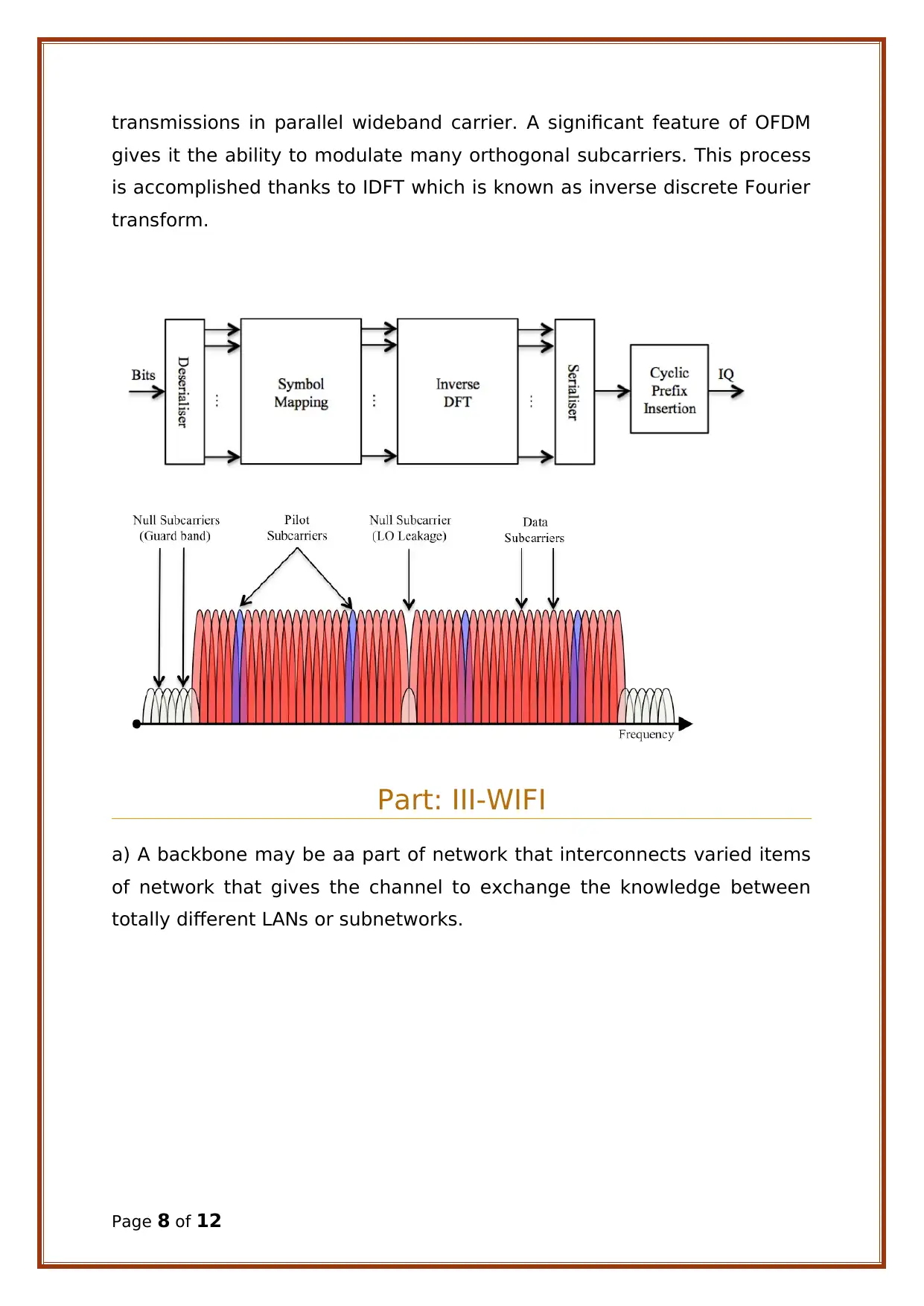
transmissions in parallel wideband carrier. A significant feature of OFDM
gives it the ability to modulate many orthogonal subcarriers. This process
is accomplished thanks to IDFT which is known as inverse discrete Fourier
transform.
Part: III-WIFI
a) A backbone may be aa part of network that interconnects varied items
of network that gives the channel to exchange the knowledge between
totally different LANs or subnetworks.
Page 8 of 12
gives it the ability to modulate many orthogonal subcarriers. This process
is accomplished thanks to IDFT which is known as inverse discrete Fourier
transform.
Part: III-WIFI
a) A backbone may be aa part of network that interconnects varied items
of network that gives the channel to exchange the knowledge between
totally different LANs or subnetworks.
Page 8 of 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
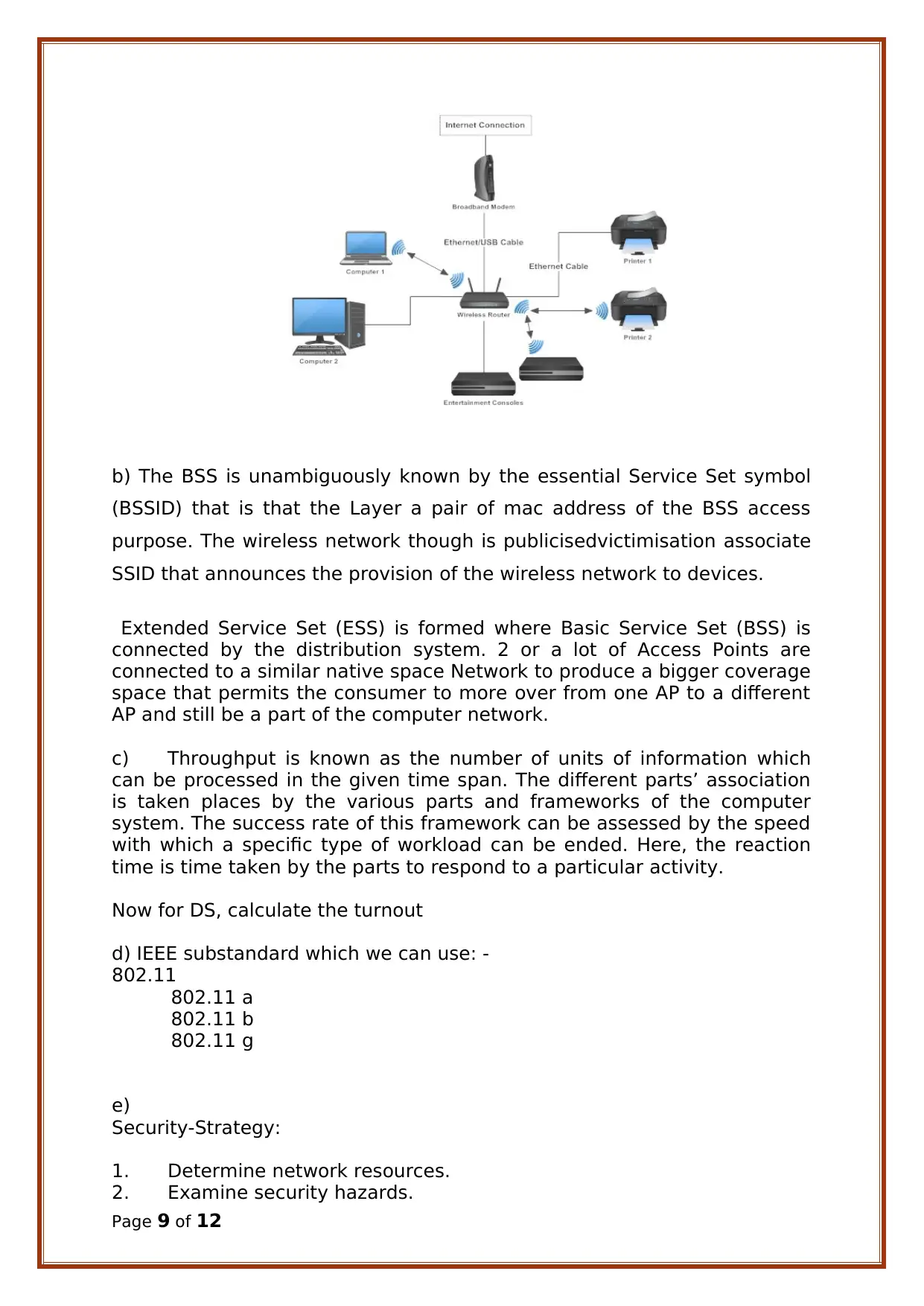
b) The BSS is unambiguously known by the essential Service Set symbol
(BSSID) that is that the Layer a pair of mac address of the BSS access
purpose. The wireless network though is publicisedvictimisation associate
SSID that announces the provision of the wireless network to devices.
Extended Service Set (ESS) is formed where Basic Service Set (BSS) is
connected by the distribution system. 2 or a lot of Access Points are
connected to a similar native space Network to produce a bigger coverage
space that permits the consumer to more over from one AP to a different
AP and still be a part of the computer network.
c) Throughput is known as the number of units of information which
can be processed in the given time span. The different parts’ association
is taken places by the various parts and frameworks of the computer
system. The success rate of this framework can be assessed by the speed
with which a specific type of workload can be ended. Here, the reaction
time is time taken by the parts to respond to a particular activity.
Now for DS, calculate the turnout
d) IEEE substandard which we can use: -
802.11
802.11 a
802.11 b
802.11 g
e)
Security-Strategy:
1. Determine network resources.
2. Examine security hazards.
Page 9 of 12
(BSSID) that is that the Layer a pair of mac address of the BSS access
purpose. The wireless network though is publicisedvictimisation associate
SSID that announces the provision of the wireless network to devices.
Extended Service Set (ESS) is formed where Basic Service Set (BSS) is
connected by the distribution system. 2 or a lot of Access Points are
connected to a similar native space Network to produce a bigger coverage
space that permits the consumer to more over from one AP to a different
AP and still be a part of the computer network.
c) Throughput is known as the number of units of information which
can be processed in the given time span. The different parts’ association
is taken places by the various parts and frameworks of the computer
system. The success rate of this framework can be assessed by the speed
with which a specific type of workload can be ended. Here, the reaction
time is time taken by the parts to respond to a particular activity.
Now for DS, calculate the turnout
d) IEEE substandard which we can use: -
802.11
802.11 a
802.11 b
802.11 g
e)
Security-Strategy:
1. Determine network resources.
2. Examine security hazards.
Page 9 of 12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. Examine security requirements and tradeoffs.
4. Grow a security set up.
5. Sketch a security strategy.
Bibliography
4G or Fourth Generation Networks | TelecomSpace. (2018). Retrieved from
http://www.telecomspace.com/nextgen-4g.html
(2018). [Ebook].
Ganapati, P., Ganapati, P., Goode, L., Calore, M., Staff, W., & Pardes, A. et al.
(2018). Wired Explains: Everything You Need to Know About 4G Wireless.
Retrieved from https://www.wired.com/2010/06/wired-explains-4g/
Infrared Communication - Introduction of IR and It's Functionality. (2018).
Retrieved from https://www.bing.com/cr?
IG=0D0EDBD88BB847DA81582D7180771405&CID=1E6DF36147CE6E42
2D5FFF4946336F7E&rd=1&h=RdBPHEIb9i4tLmmBdoOwCBvAxw7y9wC
RT66-HK9v3eU&v=1&r=https%3a%2f%2fwww.elprocus.com
%2fcommunication-using-infrared-technology%2f&p=DevEx.LB.1,5541.1
Page 10 of 12
4. Grow a security set up.
5. Sketch a security strategy.
Bibliography
4G or Fourth Generation Networks | TelecomSpace. (2018). Retrieved from
http://www.telecomspace.com/nextgen-4g.html
(2018). [Ebook].
Ganapati, P., Ganapati, P., Goode, L., Calore, M., Staff, W., & Pardes, A. et al.
(2018). Wired Explains: Everything You Need to Know About 4G Wireless.
Retrieved from https://www.wired.com/2010/06/wired-explains-4g/
Infrared Communication - Introduction of IR and It's Functionality. (2018).
Retrieved from https://www.bing.com/cr?
IG=0D0EDBD88BB847DA81582D7180771405&CID=1E6DF36147CE6E42
2D5FFF4946336F7E&rd=1&h=RdBPHEIb9i4tLmmBdoOwCBvAxw7y9wC
RT66-HK9v3eU&v=1&r=https%3a%2f%2fwww.elprocus.com
%2fcommunication-using-infrared-technology%2f&p=DevEx.LB.1,5541.1
Page 10 of 12

Invest in Canada Bureau. (2012). Invest in Canada. [Ottawa].
Prasad, R., & Mihovska, A. (2009). New horizons in mobile and wireless
communications. Boston: Artech House.
Rappaport, T. (2009). Wireless communications. Upper Saddle River, NJ: Prentice
Hall PTR.
Rumney, M., & Technologies, A. (2013). LTE and the Evolution to 4G Wireless.
New York: Wiley.
Stallings, W. (2014). Data and computer communications. Boston, Mass: Pearson.
Page 11 of 12
Prasad, R., & Mihovska, A. (2009). New horizons in mobile and wireless
communications. Boston: Artech House.
Rappaport, T. (2009). Wireless communications. Upper Saddle River, NJ: Prentice
Hall PTR.
Rumney, M., & Technologies, A. (2013). LTE and the Evolution to 4G Wireless.
New York: Wiley.
Stallings, W. (2014). Data and computer communications. Boston, Mass: Pearson.
Page 11 of 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



