Wireless Networking Concepts Report - Networking Security Fundamentals
VerifiedAdded on 2020/03/23
|30
|2291
|108
Report
AI Summary
This report delves into the core concepts of wireless networking, focusing on encryption standards like 3DES, AES, and RSA used in WiMAX networks to secure data transmission. It examines WPAN technologies, particularly Bluetooth and ZigBee, highlighting their security vulnerabilities such as bluebugging, bluesnarfing, and potential threats to data integrity. The report also analyzes energy harvesting techniques in wireless sensor networks (WSNs), discussing various methods like solar, thermal, and radio frequency-based energy harvesting to overcome power limitations. Two research articles are summarized, discussing the importance of energy harvesting for WSNs and recent advancements in the field. The report provides a comprehensive overview of the challenges and solutions related to wireless network security and energy efficiency, offering valuable insights into the current trends and future directions in wireless communication.

Running head: WIRELESS NETWORKING CONCEPTS
Wireless Networking Concepts
Name of the Student
Name of the University
Author Note
Student ID:____________ Family name: ____________________________________
Given names: __________________________________________________________
Subject name: ________________________________ Subject code: _____________
Lecturer: _____________________________________ Assignment No: ___________
Wireless Networking Concepts
Name of the Student
Name of the University
Author Note
Student ID:____________ Family name: ____________________________________
Given names: __________________________________________________________
Subject name: ________________________________ Subject code: _____________
Lecturer: _____________________________________ Assignment No: ___________
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS NETWORKING CONCEPTS
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................4
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................8
References..........................................................................................................................28
Table of Contents
Answer 1..............................................................................................................................2
Answer 2..............................................................................................................................4
Answer 3..............................................................................................................................5
Answer 4..............................................................................................................................8
References..........................................................................................................................28
2WIRELESS NETWORKING CONCEPTS
Answer 1
Encryption is a process of converting a particular information or data into a code in order
to prevent unauthorized access to the data. Encryption helps in limiting the access to a particular
data only to the registered users (Pathan, 2016). There is different encryption standards used in
order to protect privacy as well as confidentiality of the data. General Interoperability for
Microwave Access (WiMax) is implied as the transport of the organizations to the long remote
broadband access. It offers point-to-point and furthermore multipoint application. Of course, it is
enabled for updating security of the framework at the period of transmission to the last mile.
Additionally, WiMax utilizes three sorts of data encryption standards remembering the true
objective to guarantee data and furthermore information (Tan & Wu, 2013). The three data
encryption standards for WiMAX networks are 3DES or triple data encryption standard, AES
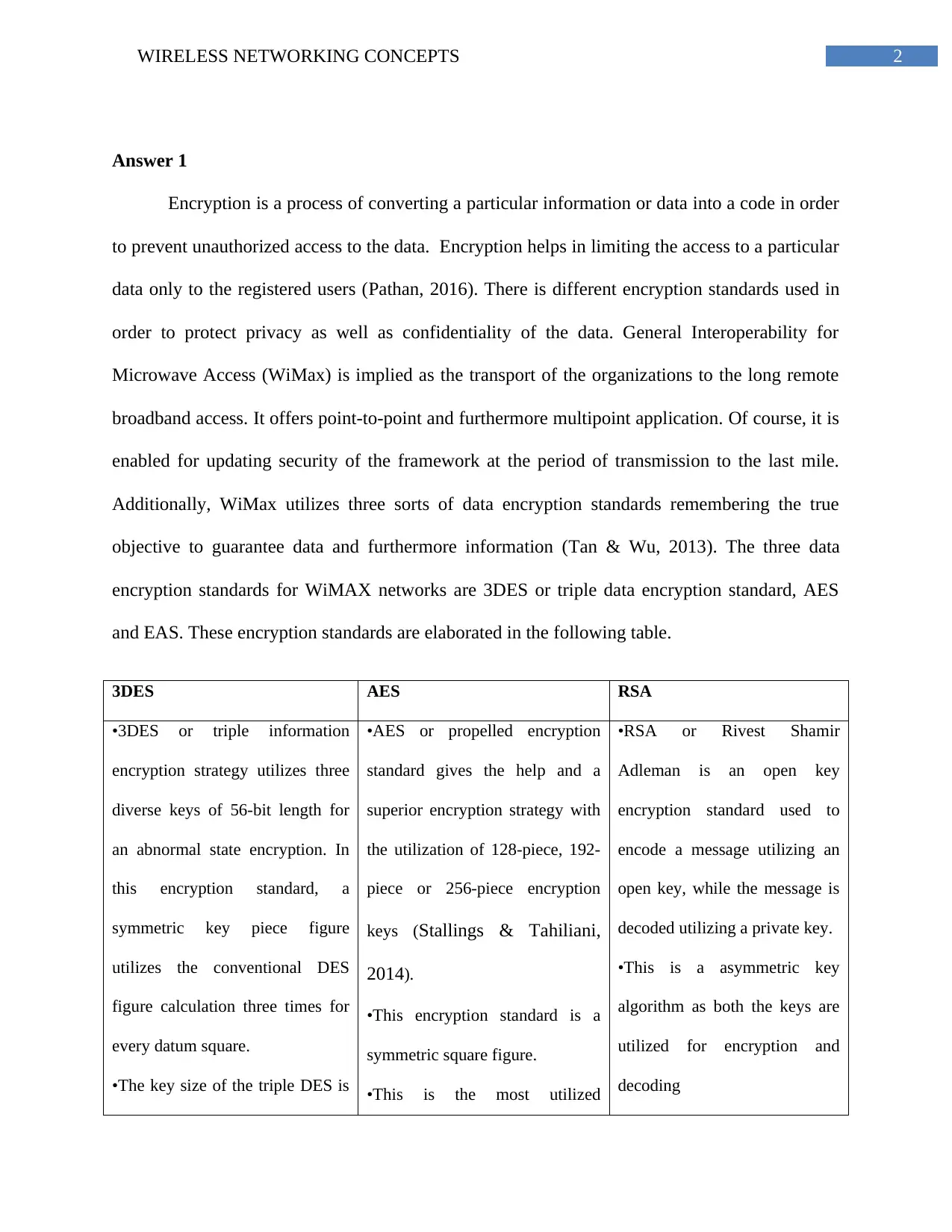
and EAS. These encryption standards are elaborated in the following table.
3DES AES RSA
•3DES or triple information
encryption strategy utilizes three
diverse keys of 56-bit length for
an abnormal state encryption. In
this encryption standard, a
symmetric key piece figure
utilizes the conventional DES
figure calculation three times for
every datum square.
•The key size of the triple DES is
•AES or propelled encryption
standard gives the help and a
superior encryption strategy with
the utilization of 128-piece, 192-
piece or 256-piece encryption
keys (Stallings & Tahiliani,
2014).
•This encryption standard is a
symmetric square figure.
•This is the most utilized
•RSA or Rivest Shamir
Adleman is an open key
encryption standard used to
encode a message utilizing an
open key, while the message is
decoded utilizing a private key.
•This is a asymmetric key
algorithm as both the keys are
utilized for encryption and
decoding
Answer 1
Encryption is a process of converting a particular information or data into a code in order
to prevent unauthorized access to the data. Encryption helps in limiting the access to a particular
data only to the registered users (Pathan, 2016). There is different encryption standards used in
order to protect privacy as well as confidentiality of the data. General Interoperability for
Microwave Access (WiMax) is implied as the transport of the organizations to the long remote
broadband access. It offers point-to-point and furthermore multipoint application. Of course, it is
enabled for updating security of the framework at the period of transmission to the last mile.
Additionally, WiMax utilizes three sorts of data encryption standards remembering the true
objective to guarantee data and furthermore information (Tan & Wu, 2013). The three data
encryption standards for WiMAX networks are 3DES or triple data encryption standard, AES
and EAS. These encryption standards are elaborated in the following table.
3DES AES RSA
•3DES or triple information
encryption strategy utilizes three
diverse keys of 56-bit length for
an abnormal state encryption. In
this encryption standard, a
symmetric key piece figure
utilizes the conventional DES
figure calculation three times for
every datum square.
•The key size of the triple DES is
•AES or propelled encryption
standard gives the help and a
superior encryption strategy with
the utilization of 128-piece, 192-
piece or 256-piece encryption
keys (Stallings & Tahiliani,
2014).
•This encryption standard is a
symmetric square figure.
•This is the most utilized
•RSA or Rivest Shamir
Adleman is an open key
encryption standard used to
encode a message utilizing an
open key, while the message is
decoded utilizing a private key.
•This is a asymmetric key
algorithm as both the keys are
utilized for encryption and
decoding
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3WIRELESS NETWORKING CONCEPTS
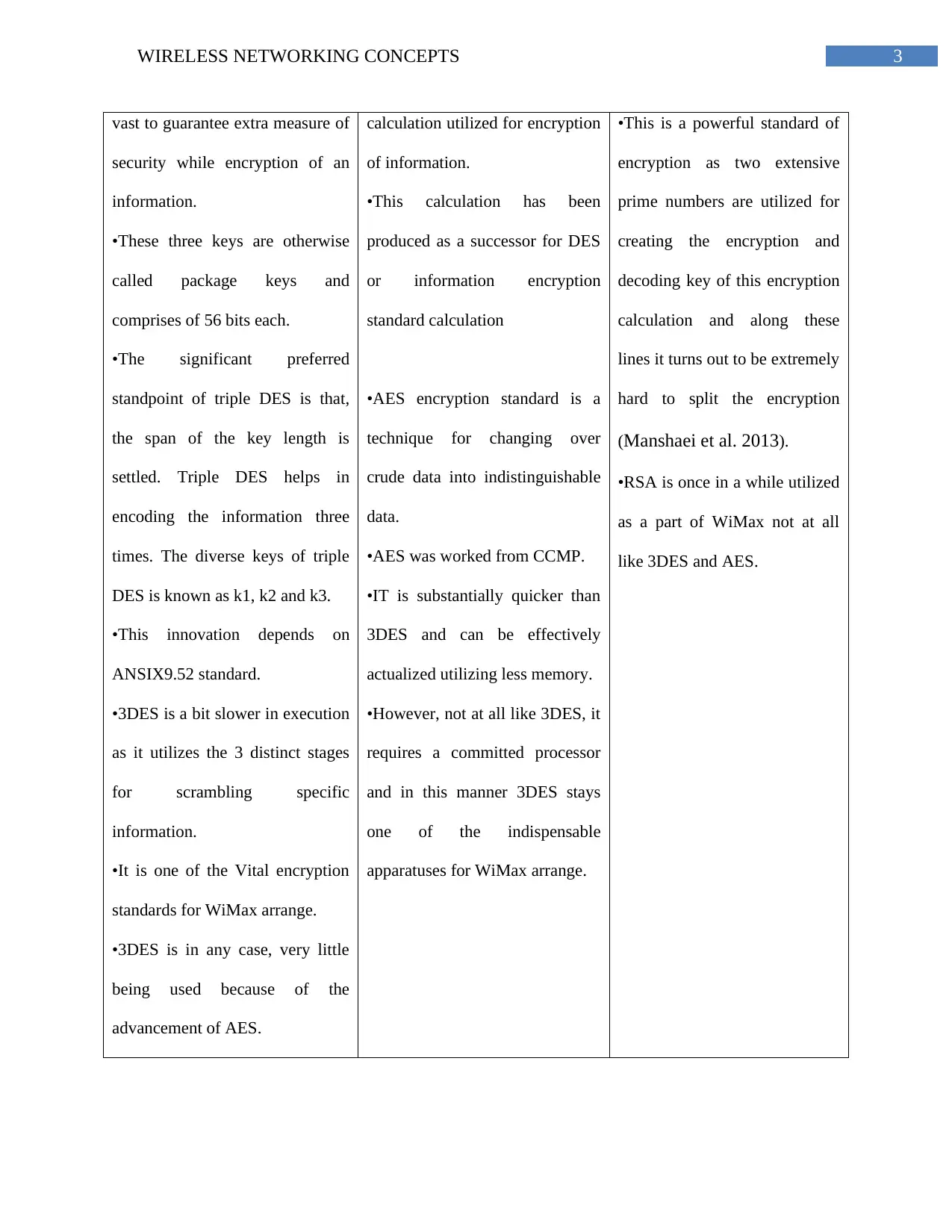
vast to guarantee extra measure of
security while encryption of an
information.
•These three keys are otherwise
called package keys and
comprises of 56 bits each.
•The significant preferred
standpoint of triple DES is that,
the span of the key length is
settled. Triple DES helps in
encoding the information three
times. The diverse keys of triple
DES is known as k1, k2 and k3.
•This innovation depends on
ANSIX9.52 standard.
•3DES is a bit slower in execution
as it utilizes the 3 distinct stages
for scrambling specific
information.
•It is one of the Vital encryption
standards for WiMax arrange.
•3DES is in any case, very little
being used because of the
advancement of AES.
calculation utilized for encryption
of information.
•This calculation has been
produced as a successor for DES
or information encryption
standard calculation
•AES encryption standard is a
technique for changing over
crude data into indistinguishable
data.
•AES was worked from CCMP.
•IT is substantially quicker than
3DES and can be effectively
actualized utilizing less memory.
•However, not at all like 3DES, it
requires a committed processor
and in this manner 3DES stays
one of the indispensable
apparatuses for WiMax arrange.
•This is a powerful standard of
encryption as two extensive
prime numbers are utilized for
creating the encryption and
decoding key of this encryption
calculation and along these
lines it turns out to be extremely
hard to split the encryption
(Manshaei et al. 2013).
•RSA is once in a while utilized
as a part of WiMax not at all
like 3DES and AES.
vast to guarantee extra measure of
security while encryption of an
information.
•These three keys are otherwise
called package keys and
comprises of 56 bits each.
•The significant preferred
standpoint of triple DES is that,
the span of the key length is
settled. Triple DES helps in
encoding the information three
times. The diverse keys of triple
DES is known as k1, k2 and k3.
•This innovation depends on
ANSIX9.52 standard.
•3DES is a bit slower in execution
as it utilizes the 3 distinct stages
for scrambling specific
information.
•It is one of the Vital encryption
standards for WiMax arrange.
•3DES is in any case, very little
being used because of the
advancement of AES.
calculation utilized for encryption
of information.
•This calculation has been
produced as a successor for DES
or information encryption
standard calculation
•AES encryption standard is a
technique for changing over
crude data into indistinguishable
data.
•AES was worked from CCMP.
•IT is substantially quicker than
3DES and can be effectively
actualized utilizing less memory.
•However, not at all like 3DES, it
requires a committed processor
and in this manner 3DES stays
one of the indispensable
apparatuses for WiMax arrange.
•This is a powerful standard of
encryption as two extensive
prime numbers are utilized for
creating the encryption and
decoding key of this encryption
calculation and along these
lines it turns out to be extremely
hard to split the encryption
(Manshaei et al. 2013).
•RSA is once in a while utilized
as a part of WiMax not at all
like 3DES and AES.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS NETWORKING CONCEPTS
Answer 2
WPAN or remote individual area network is a system of interconnecting gadgets giving a
wireless connection with the gadgets. WPAN advances are fundamentally utilized for short range
correspondences, low power utilization, minimal effort and are extremely useful for setting up
little individual systems.
The two cases of WPAN innovation incorporate Bluetooth and ZigBee. Bluetooth is a
broadly utilized WPAN innovation. Bluetooth is a standard for short-go remote interconnection
of versatile and electronic gadgets (Fragouli, 2015). Zigbee on other hand is more
straightforward and more affordable than Bluetooth. The essential preferred standpoint of Zigbee
is its simplicity of establishment, information exchange and minimal effort. In any case, there are
sure security worries that are related with these WPAN advancements.
The security difficulties of WPAN and Bluetooth are expounded in the accompanying
passages
Bluetooth
Endorsement of the Bluetooth devices can't be proficient, which can cause unequivocal
direct of the related contraptions. In this perspective, it is fundamental to state that there is a
tremendous hazard for DoS ambushes on the Bluetooth devices at the period of transmission of
data and also information (Loo, Mauri & Ortiz, 2016). It can be harmful area of the outside
social occasions at the period of transmission system of data. Regardless, sensitive data might be
hurt and moreover contaminated at the period of remote transmission.
The security dangers related with Bluetooth innovation in WPAN are recorded
underneath
Answer 2
WPAN or remote individual area network is a system of interconnecting gadgets giving a
wireless connection with the gadgets. WPAN advances are fundamentally utilized for short range
correspondences, low power utilization, minimal effort and are extremely useful for setting up
little individual systems.
The two cases of WPAN innovation incorporate Bluetooth and ZigBee. Bluetooth is a
broadly utilized WPAN innovation. Bluetooth is a standard for short-go remote interconnection
of versatile and electronic gadgets (Fragouli, 2015). Zigbee on other hand is more
straightforward and more affordable than Bluetooth. The essential preferred standpoint of Zigbee
is its simplicity of establishment, information exchange and minimal effort. In any case, there are
sure security worries that are related with these WPAN advancements.
The security difficulties of WPAN and Bluetooth are expounded in the accompanying
passages
Bluetooth
Endorsement of the Bluetooth devices can't be proficient, which can cause unequivocal
direct of the related contraptions. In this perspective, it is fundamental to state that there is a
tremendous hazard for DoS ambushes on the Bluetooth devices at the period of transmission of
data and also information (Loo, Mauri & Ortiz, 2016). It can be harmful area of the outside
social occasions at the period of transmission system of data. Regardless, sensitive data might be
hurt and moreover contaminated at the period of remote transmission.
The security dangers related with Bluetooth innovation in WPAN are recorded
underneath

5WIRELESS NETWORKING CONCEPTS
1) Bluebugging: In this security danger where a programmer breaks into a Bluetooth
network and can exploit the system without the learning of the proprietor.
2) Blue jacking: In this security threat, the aggressor sends hurtful messages to the sender
that could be opened up consequently and introduce the vindictive substance.
3) Bkuesnarfing: the aggressor gets access into the network and gets unapproved access
to the information introduce. Bluesnarfing is one of the threats drew in with the development that
can empower the aggressors remembering the ultimate objective to fabricate the utilization of the
contraptions that are Bluetooth included (Liang & Yu, 2015). Besides, it searches for IMEI
number of the Bluetooth contraptions and furthermore getting related through the system.
ZigBee
The security concerns related with ZigBee are recorded underneath
1) A programmer may break into a ZigBee system and increase physical access to the
information and the encryption key of the gadget along these lines uncovering the classified data.
2) Another significant hazard related with this assault is impersonating a hub of a system
keeping in mind the end goal to access the information.
Answer 3
First article: Shaikh, Faisal Karim, and Sherali Zeadally. "Energy harvesting in wireless
sensor networks: A comprehensive review." Renewable and Sustainable Energy Reviews 55
(2016): 1041-1054.
1) Bluebugging: In this security danger where a programmer breaks into a Bluetooth
network and can exploit the system without the learning of the proprietor.
2) Blue jacking: In this security threat, the aggressor sends hurtful messages to the sender
that could be opened up consequently and introduce the vindictive substance.
3) Bkuesnarfing: the aggressor gets access into the network and gets unapproved access
to the information introduce. Bluesnarfing is one of the threats drew in with the development that
can empower the aggressors remembering the ultimate objective to fabricate the utilization of the
contraptions that are Bluetooth included (Liang & Yu, 2015). Besides, it searches for IMEI
number of the Bluetooth contraptions and furthermore getting related through the system.
ZigBee
The security concerns related with ZigBee are recorded underneath
1) A programmer may break into a ZigBee system and increase physical access to the
information and the encryption key of the gadget along these lines uncovering the classified data.
2) Another significant hazard related with this assault is impersonating a hub of a system
keeping in mind the end goal to access the information.
Answer 3
First article: Shaikh, Faisal Karim, and Sherali Zeadally. "Energy harvesting in wireless
sensor networks: A comprehensive review." Renewable and Sustainable Energy Reviews 55
(2016): 1041-1054.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIRELESS NETWORKING CONCEPTS
The paper discusses with the path toward using of essentialness in Wireless Sensor
Network. The framework joins a broad number of static sensor center points, which helps the
low taking care of. Moreover, there are a couple of wellsprings of imperativeness consolidating
into Wireless Sensor Network and radio repeat based essentialness drew in with the framework.
Close by these, sun fueled based essentialness and furthermore warm based imperativeness and
stream based essentialness harvesting is consolidated into the methodology (Yang et al., 2015).
There are moreover a couple of philosophies depicted in the present paper with the ultimate
objective of using imperativeness satisfactorily.
The way toward yielding or collecting the vitality from outer sources is known as vitality
gathering. The distinctive outer wellsprings of energy collecting incorporate sunlight based
energy, wind energy, hydropower energy et cetera (Hu & Qian, 2014). Productive energy
gathering approaches are investigated with a specific end goal to take out the impediment of
energy concerning the advancement of Wireless sensor systems or WSNs. Energy collecting is
vital with a specific end goal to beat the issue confronted sue to the exhaustion of sensor hub in
WSN, because of which the system neglects to play out its duty legitimately.
Second article: Ulukus, Sennur, et al. "Energy harvesting wireless communications: A
review of recent advances." IEEE Journal on Selected Areas in Communications 33.3 (2015):
360-381.
In the particular article, there are discoursed about new advances completed amid the
time spent imperativeness gathering zone (Pierson & DeHaan, 2015). There are new movements
in essentialness procuring, which can be changed for regular circumstance of imperativeness
gathering. Regardless, the convincing use of the bleeding edge system in the treatment of
The paper discusses with the path toward using of essentialness in Wireless Sensor
Network. The framework joins a broad number of static sensor center points, which helps the
low taking care of. Moreover, there are a couple of wellsprings of imperativeness consolidating
into Wireless Sensor Network and radio repeat based essentialness drew in with the framework.
Close by these, sun fueled based essentialness and furthermore warm based imperativeness and
stream based essentialness harvesting is consolidated into the methodology (Yang et al., 2015).
There are moreover a couple of philosophies depicted in the present paper with the ultimate
objective of using imperativeness satisfactorily.
The way toward yielding or collecting the vitality from outer sources is known as vitality
gathering. The distinctive outer wellsprings of energy collecting incorporate sunlight based
energy, wind energy, hydropower energy et cetera (Hu & Qian, 2014). Productive energy
gathering approaches are investigated with a specific end goal to take out the impediment of
energy concerning the advancement of Wireless sensor systems or WSNs. Energy collecting is
vital with a specific end goal to beat the issue confronted sue to the exhaustion of sensor hub in
WSN, because of which the system neglects to play out its duty legitimately.
Second article: Ulukus, Sennur, et al. "Energy harvesting wireless communications: A
review of recent advances." IEEE Journal on Selected Areas in Communications 33.3 (2015):
360-381.
In the particular article, there are discoursed about new advances completed amid the
time spent imperativeness gathering zone (Pierson & DeHaan, 2015). There are new movements
in essentialness procuring, which can be changed for regular circumstance of imperativeness
gathering. Regardless, the convincing use of the bleeding edge system in the treatment of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS NETWORKING CONCEPTS
imperativeness procuring. It has extended starting costs of a couple of imperativeness sources
nearby weariness of standard sources. There are a couple of conditions and what's more
speculations related to the technique have been discussed in the present paper, which uses the
standard thought of the imperativeness gathering and furthermore changing over it into the front
line development.
In like manner, offering essentialness to the path toward get-together capacity to the
remote sensor contraptions to the center points that can be always acquiring imperativeness from
the nature and man-made circumstance (Biswas et al. 2015). It swings to give promising future
to the remote frameworks and furthermore self-reasonability of close by the virtual operation
with the framework. Energy harvesting system enables the remote sensor hubs to gain ceaseless
energy from the nature and distraught made marvel. Along these lines, the procedure of energy
collecting can help in finding out a promising future in the field of remote system by decreasing
the utilization of ordinary energy to a significant sum.
The distinctive energy harvesting methods are explained underneath.
1) Radio Frequency based Energy harvesting: This energy harvesting strategies manages
the change of radio waves into DC control energy
2) Solar energy harvesting: there is plenitude of sun oriented energy and in this way
appropriate collecting systems can be utilized for looming the issues related with remote sensor
systems.
3) Thermal Energy: This strategy for energy harvesting changes over the warmth energy
into electrical energy. The strategy utilized is Seebeck impact (Zou et al., 2015).
imperativeness procuring. It has extended starting costs of a couple of imperativeness sources
nearby weariness of standard sources. There are a couple of conditions and what's more
speculations related to the technique have been discussed in the present paper, which uses the
standard thought of the imperativeness gathering and furthermore changing over it into the front
line development.
In like manner, offering essentialness to the path toward get-together capacity to the
remote sensor contraptions to the center points that can be always acquiring imperativeness from
the nature and man-made circumstance (Biswas et al. 2015). It swings to give promising future
to the remote frameworks and furthermore self-reasonability of close by the virtual operation
with the framework. Energy harvesting system enables the remote sensor hubs to gain ceaseless
energy from the nature and distraught made marvel. Along these lines, the procedure of energy
collecting can help in finding out a promising future in the field of remote system by decreasing
the utilization of ordinary energy to a significant sum.
The distinctive energy harvesting methods are explained underneath.
1) Radio Frequency based Energy harvesting: This energy harvesting strategies manages
the change of radio waves into DC control energy
2) Solar energy harvesting: there is plenitude of sun oriented energy and in this way
appropriate collecting systems can be utilized for looming the issues related with remote sensor
systems.
3) Thermal Energy: This strategy for energy harvesting changes over the warmth energy
into electrical energy. The strategy utilized is Seebeck impact (Zou et al., 2015).

8WIRELESS NETWORKING CONCEPTS
4) Wind Energy harvesting: This energy can be collected for era of power
5) Hydro energy harvesting: The energy or quality of falling water can be collected for
saddling the energy.
Answer 4
4) Wind Energy harvesting: This energy can be collected for era of power
5) Hydro energy harvesting: The energy or quality of falling water can be collected for
saddling the energy.
Answer 4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9WIRELESS NETWORKING CONCEPTS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10WIRELESS NETWORKING CONCEPTS

11WIRELESS NETWORKING CONCEPTS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





