MITS5003 Wireless Networks Assignment: Encoding and Error Control
VerifiedAdded on 2023/06/10
|8
|2390
|475
Homework Assignment
AI Summary
This assignment solution addresses various aspects of wireless networks and communication, starting with the calculation of data rates for a micro robot's remote communication and exploring suitable encoding techniques like NRZ, Manchester, and NRZI. It then delves into representing sensor data using ASK, FSK, and PSK encoding methods and calculating CRC for error detection. The solution also explains other error control and flow control techniques, as well as convolution codes. Furthermore, the assignment covers multiplexing techniques such as TDM, FDM, and CDMA, and discusses the evolution from 3G to 4G and WiMAX, including the features of OFDM. Finally, the solution tackles a Wi-Fi network design scenario for a real estate company, including network architecture, throughput calculation, recommended IEEE standards, and security strategies.

WIRELESS NETWORKS AND COMMUNICATION.
Sam is a computer science student and working on a new micro robot design. The robot continuously
sends every two seconds a status string comprising the accelerometer reading (4 bits), ultrasound
obstacle detection (6 bits), motor functionality (4 bits) and battery power level (2 bits).
Wireless communication according to Elgal,Mesleh and Haas(2011) documents that wireless
communication is the future of the world in the communication arena in the realization of global village
aspect of technology as the driver.
a) Calculate the data rate required for robot to remote controller communication.
Data rate in other words implies the bandwidth or the frequencies that can pass through a
medium .
Accelerometer – 4bits
Ultrasound obstacle detection -6bits
Motor functionality -4bits
Battery power level -2bits
2(battery power level)*4(motor functionality)/accelerometer reading(4)*obstacle
detection(6)
2*4/4*6=0.3Hz.
b) Explain 3 types of suitable encoding techniques could be used to encode the status string.
To encode means to put a sequence of characters into a specialized digital format for efficient
and effective transmission, the suitable encoding techniques would be;
NRZ ENCODING-stands for non-return to zero research by Lu,P,Xu., and Liu ,X(2013) reported
that it is the common and easiest way of transmission of digital signals. NRZ encoding uses two
distinct voltage levels as the signal details of the duo binary digits. It is used for both
synchronous and asynchronous communication. The uniqueness of NRZ is that it only encodes
positive and negative signals and never will encode zeros.
Research by Roufa,Mustafaa , Tylora,Xua,Gruteserb,Trappeb and Serskab(2010) documented
that Manchester Encoding-Is a synchronized encoding category normaly used by physical layer
to take in the synchronized bit stream, the binary data channeled over the cable are not sent as
a series of 1s and 0s.
NRZI ENCODING-stands for non-return to zero inverted encoding. It is majorly used in
telecommunication transmissions in which a bit of data of 1 is a positive voltage while a bit of
data of 0 is a negative voltage. NRZI singles binary signals to eminently physical hints in the
channeling. If a bit of data is 1, NRZI changes at the clock interface. On the other hand if a data
bit is 0, there is no change. NRZI at times have long sequences of 0s or 1s, culminating into clock
recovery hitches.
c) At a certain instance, the sensors provided data as acceleration 5 m/s2 , obstacle at 48 cm, all
motors working (i.e. motor functionality 1111), and battery is 75%.
Write the status string in binary for this instance.
Acceleration -0101
Obstacle – 0100 1000
Battery -0111 0101
Sam is a computer science student and working on a new micro robot design. The robot continuously
sends every two seconds a status string comprising the accelerometer reading (4 bits), ultrasound
obstacle detection (6 bits), motor functionality (4 bits) and battery power level (2 bits).
Wireless communication according to Elgal,Mesleh and Haas(2011) documents that wireless
communication is the future of the world in the communication arena in the realization of global village
aspect of technology as the driver.
a) Calculate the data rate required for robot to remote controller communication.
Data rate in other words implies the bandwidth or the frequencies that can pass through a
medium .
Accelerometer – 4bits
Ultrasound obstacle detection -6bits
Motor functionality -4bits
Battery power level -2bits
2(battery power level)*4(motor functionality)/accelerometer reading(4)*obstacle
detection(6)
2*4/4*6=0.3Hz.
b) Explain 3 types of suitable encoding techniques could be used to encode the status string.
To encode means to put a sequence of characters into a specialized digital format for efficient
and effective transmission, the suitable encoding techniques would be;
NRZ ENCODING-stands for non-return to zero research by Lu,P,Xu., and Liu ,X(2013) reported
that it is the common and easiest way of transmission of digital signals. NRZ encoding uses two
distinct voltage levels as the signal details of the duo binary digits. It is used for both
synchronous and asynchronous communication. The uniqueness of NRZ is that it only encodes
positive and negative signals and never will encode zeros.
Research by Roufa,Mustafaa , Tylora,Xua,Gruteserb,Trappeb and Serskab(2010) documented
that Manchester Encoding-Is a synchronized encoding category normaly used by physical layer
to take in the synchronized bit stream, the binary data channeled over the cable are not sent as
a series of 1s and 0s.
NRZI ENCODING-stands for non-return to zero inverted encoding. It is majorly used in
telecommunication transmissions in which a bit of data of 1 is a positive voltage while a bit of
data of 0 is a negative voltage. NRZI singles binary signals to eminently physical hints in the
channeling. If a bit of data is 1, NRZI changes at the clock interface. On the other hand if a data
bit is 0, there is no change. NRZI at times have long sequences of 0s or 1s, culminating into clock
recovery hitches.
c) At a certain instance, the sensors provided data as acceleration 5 m/s2 , obstacle at 48 cm, all
motors working (i.e. motor functionality 1111), and battery is 75%.
Write the status string in binary for this instance.
Acceleration -0101
Obstacle – 0100 1000
Battery -0111 0101
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
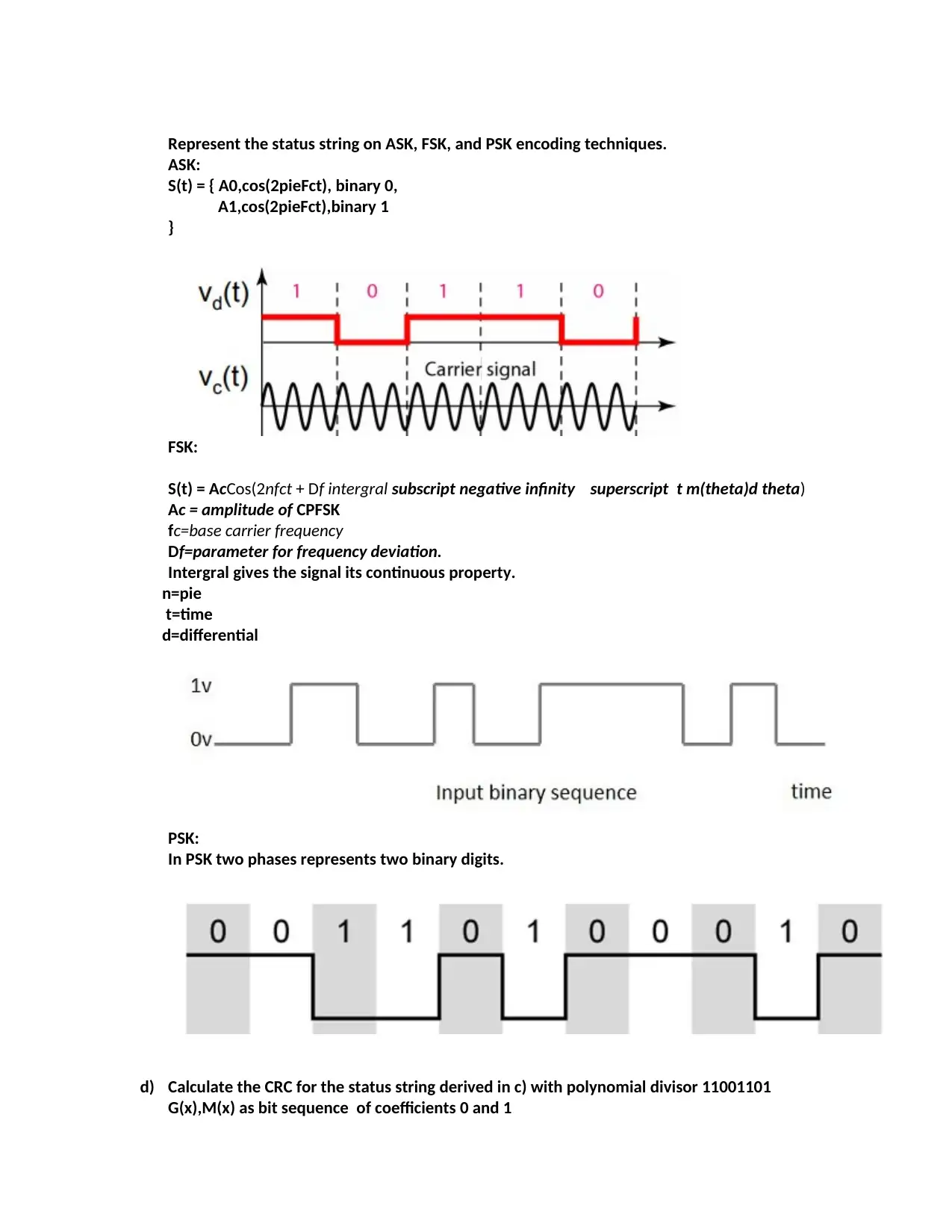
Represent the status string on ASK, FSK, and PSK encoding techniques.
ASK:
S(t) = { A0,cos(2pieFct), binary 0,
A1,cos(2pieFct),binary 1
}
FSK:
S(t) = AcCos(2nfct + Df intergral subscript negative infinity superscript t m(theta)d theta)
Ac = amplitude of CPFSK
fc=base carrier frequency
Df=parameter for frequency deviation.
Intergral gives the signal its continuous property.
n=pie
t=time
d=differential
PSK:
In PSK two phases represents two binary digits.
d) Calculate the CRC for the status string derived in c) with polynomial divisor 11001101
G(x),M(x) as bit sequence of coefficients 0 and 1
ASK:
S(t) = { A0,cos(2pieFct), binary 0,
A1,cos(2pieFct),binary 1
}
FSK:
S(t) = AcCos(2nfct + Df intergral subscript negative infinity superscript t m(theta)d theta)
Ac = amplitude of CPFSK
fc=base carrier frequency
Df=parameter for frequency deviation.
Intergral gives the signal its continuous property.
n=pie
t=time
d=differential
PSK:
In PSK two phases represents two binary digits.
d) Calculate the CRC for the status string derived in c) with polynomial divisor 11001101
G(x),M(x) as bit sequence of coefficients 0 and 1

y4 + y3 +y2 +1.
An An+1 An+2 as the message
bits: B(y) = Anyn +An+1y+1 +An+2yn+2
ykB(y) = Q(y)G(y) + R(y)
xkB(y) + R(y)
//addition and subtraction are same at mod 2
Hence YkB(y) – R(y)
11001101 is of degree 3.
Y7 + y6 + y4 + y2 + y +1
Y7 + y2 + 1/y3 +y2 +1) y10+y9 +y7 + y5 + y4 +y3
Minus Y10 + y9 +y7
Y5 + y4 + y3
minusY5 + y4 +y2
y3 + y2
minus y3 + y2 +1
Ans=1
e) Briefly explain some other error control and flow control techniques that Sam can use to
ensure the accuracy of robot control.
f)
Convolution Code
Okamura,Murakami and Orihansh.(2013) found that it is a linear forward error correcting code
which yields parity symbols by convolving a data stream with generating sequences as called .It
can be modelled as a finite state markov state chain that gives a graphic representation known
as the state diagram.
Rate based Flow control
Li and Singh.(2010) records that In rate-based flow control mechanism, each node is given a
maximum rate and an average rate of transmission .The commonly used method of flow control
is biult on windows, in which the rate at which a source sends packets relies on both the size of
a window and on the rate of reply from the network to the origin. On high-speed networks, the
round trip postponement from source to an intermediary node and back is relatively high in
relation with packet transmission times, so that the windowing method does not react quickly
enough to deter congestion and delays. Also, high-speed networks requires to accommodate a
wide scope of source transmission speeds and windows do not perform very well under such
situations.
(iii)Stop and wait technique.
An An+1 An+2 as the message
bits: B(y) = Anyn +An+1y+1 +An+2yn+2
ykB(y) = Q(y)G(y) + R(y)
xkB(y) + R(y)
//addition and subtraction are same at mod 2
Hence YkB(y) – R(y)
11001101 is of degree 3.
Y7 + y6 + y4 + y2 + y +1
Y7 + y2 + 1/y3 +y2 +1) y10+y9 +y7 + y5 + y4 +y3
Minus Y10 + y9 +y7
Y5 + y4 + y3
minusY5 + y4 +y2
y3 + y2
minus y3 + y2 +1
Ans=1
e) Briefly explain some other error control and flow control techniques that Sam can use to
ensure the accuracy of robot control.
f)
Convolution Code
Okamura,Murakami and Orihansh.(2013) found that it is a linear forward error correcting code
which yields parity symbols by convolving a data stream with generating sequences as called .It
can be modelled as a finite state markov state chain that gives a graphic representation known
as the state diagram.
Rate based Flow control
Li and Singh.(2010) records that In rate-based flow control mechanism, each node is given a
maximum rate and an average rate of transmission .The commonly used method of flow control
is biult on windows, in which the rate at which a source sends packets relies on both the size of
a window and on the rate of reply from the network to the origin. On high-speed networks, the
round trip postponement from source to an intermediary node and back is relatively high in
relation with packet transmission times, so that the windowing method does not react quickly
enough to deter congestion and delays. Also, high-speed networks requires to accommodate a
wide scope of source transmission speeds and windows do not perform very well under such
situations.
(iii)Stop and wait technique.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
In this t technique the recipient ilgives an indication of it's readiness to take in data for every
time,the message is packed into frames and the sender must wait for an acknowledgement.
(I)Bandwidth for 48 subscribers.
Fb=N/2*delta_f where delta_f is the subcarrier frequency spacing.
d_f=1/Ts where Ts is the duration.
48/2*1/Ts is the fb.
(ii) suitable subcarrier bit time.
Using appropriate algorithm:
SA=(X,X_2,X....X-1,X,1,X-2...)
Bit value confined between 0-N thus appropriate rate=0<=c<=N
(iii) Explain how OFDM overcomes inter symbol interface, it is a propagation error which arises
from multipath signals formally known as noise.The common mitigation technique is the use of
adaptive equalizer.
Uqualization method,this is an equalizer that auto adapts to time variant traits and usually used
with coherent modulation techniques like the PSK.
Part III: Multiplexing and multiple access
Multiplexing plays an important role in communication as it allows the combination of
multiple streams together. Different multiplexing techniques are used for various applications.
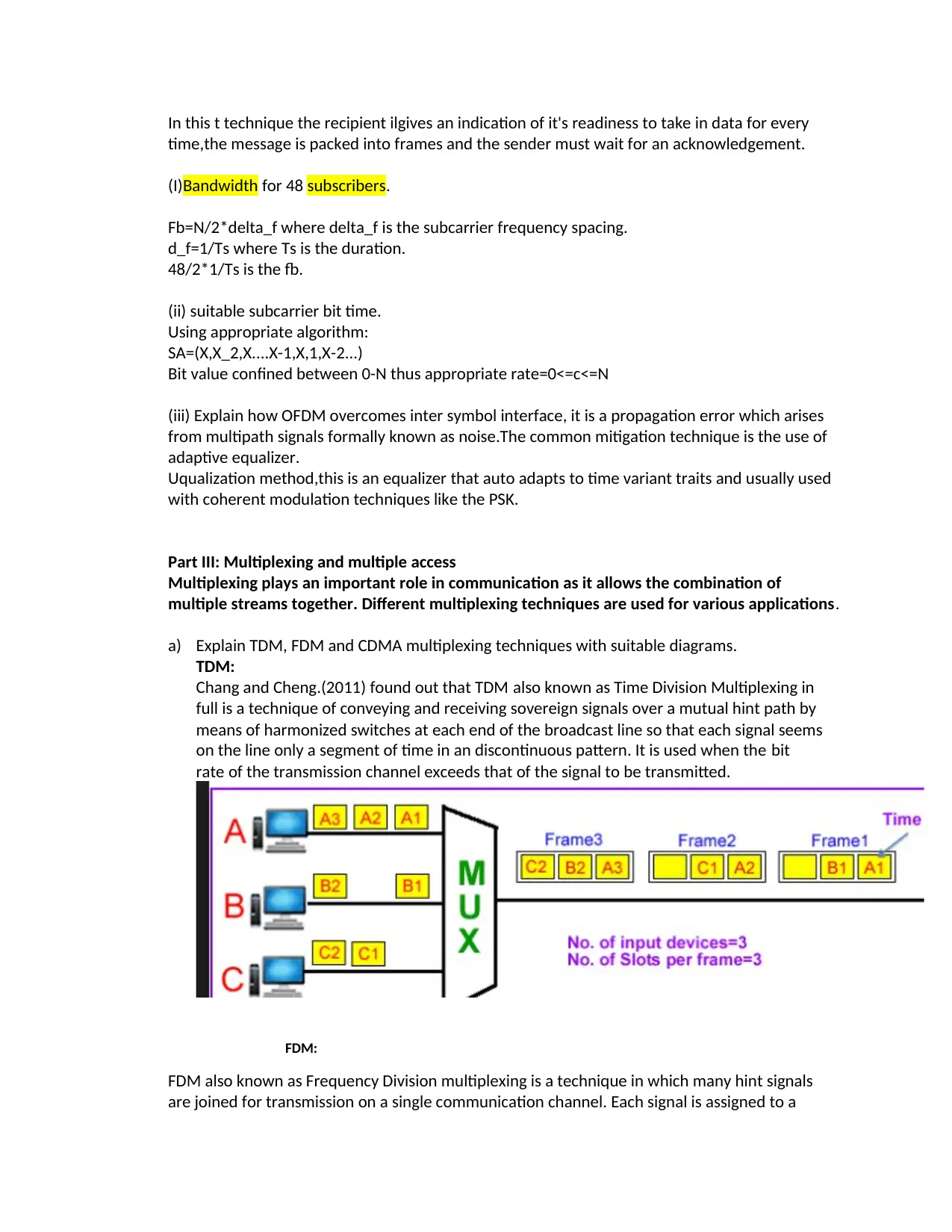
a) Explain TDM, FDM and CDMA multiplexing techniques with suitable diagrams.
TDM:
Chang and Cheng.(2011) found out that TDM also known as Time Division Multiplexing in
full is a technique of conveying and receiving sovereign signals over a mutual hint path by
means of harmonized switches at each end of the broadcast line so that each signal seems
on the line only a segment of time in an discontinuous pattern. It is used when the bit
rate of the transmission channel exceeds that of the signal to be transmitted.
FDM:
FDM also known as Frequency Division multiplexing is a technique in which many hint signals
are joined for transmission on a single communication channel. Each signal is assigned to a
time,the message is packed into frames and the sender must wait for an acknowledgement.
(I)Bandwidth for 48 subscribers.
Fb=N/2*delta_f where delta_f is the subcarrier frequency spacing.
d_f=1/Ts where Ts is the duration.
48/2*1/Ts is the fb.
(ii) suitable subcarrier bit time.
Using appropriate algorithm:
SA=(X,X_2,X....X-1,X,1,X-2...)
Bit value confined between 0-N thus appropriate rate=0<=c<=N
(iii) Explain how OFDM overcomes inter symbol interface, it is a propagation error which arises
from multipath signals formally known as noise.The common mitigation technique is the use of
adaptive equalizer.
Uqualization method,this is an equalizer that auto adapts to time variant traits and usually used
with coherent modulation techniques like the PSK.
Part III: Multiplexing and multiple access
Multiplexing plays an important role in communication as it allows the combination of
multiple streams together. Different multiplexing techniques are used for various applications.
a) Explain TDM, FDM and CDMA multiplexing techniques with suitable diagrams.
TDM:
Chang and Cheng.(2011) found out that TDM also known as Time Division Multiplexing in
full is a technique of conveying and receiving sovereign signals over a mutual hint path by
means of harmonized switches at each end of the broadcast line so that each signal seems
on the line only a segment of time in an discontinuous pattern. It is used when the bit
rate of the transmission channel exceeds that of the signal to be transmitted.
FDM:
FDM also known as Frequency Division multiplexing is a technique in which many hint signals
are joined for transmission on a single communication channel. Each signal is assigned to a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
unique frequency within the major channel and requires to be harmonized. The channel should
have a good bandwidth to be able to take in a range of frequencies.
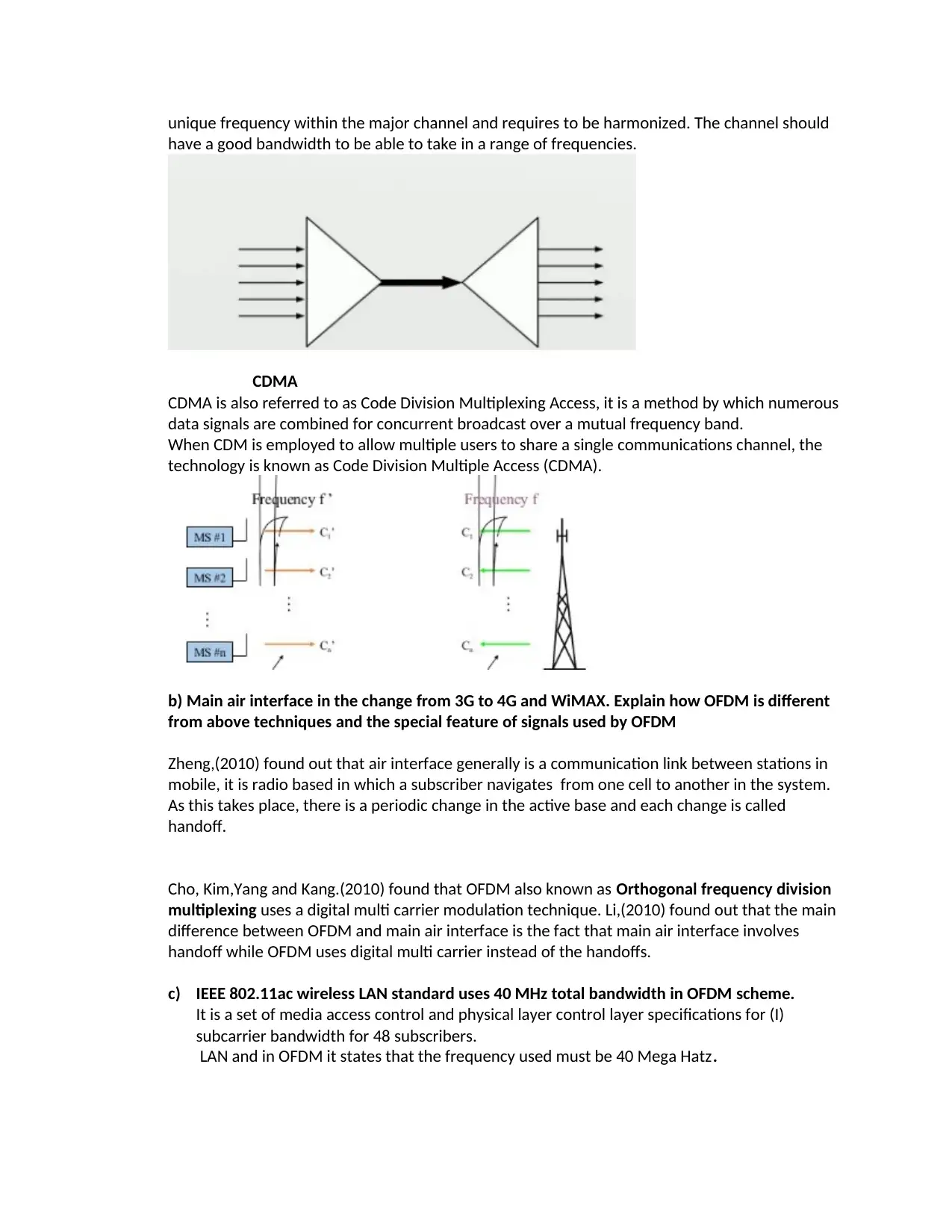
CDMA
CDMA is also referred to as Code Division Multiplexing Access, it is a method by which numerous
data signals are combined for concurrent broadcast over a mutual frequency band.
When CDM is employed to allow multiple users to share a single communications channel, the
technology is known as Code Division Multiple Access (CDMA).
b) Main air interface in the change from 3G to 4G and WiMAX. Explain how OFDM is different
from above techniques and the special feature of signals used by OFDM
Zheng,(2010) found out that air interface generally is a communication link between stations in
mobile, it is radio based in which a subscriber navigates from one cell to another in the system.
As this takes place, there is a periodic change in the active base and each change is called
handoff.
Cho, Kim,Yang and Kang.(2010) found that OFDM also known as Orthogonal frequency division
multiplexing uses a digital multi carrier modulation technique. Li,(2010) found out that the main
difference between OFDM and main air interface is the fact that main air interface involves
handoff while OFDM uses digital multi carrier instead of the handoffs.
c) IEEE 802.11ac wireless LAN standard uses 40 MHz total bandwidth in OFDM scheme.
It is a set of media access control and physical layer control layer specifications for (I)
subcarrier bandwidth for 48 subscribers.
LAN and in OFDM it states that the frequency used must be 40 Mega Hatz.
have a good bandwidth to be able to take in a range of frequencies.
CDMA
CDMA is also referred to as Code Division Multiplexing Access, it is a method by which numerous
data signals are combined for concurrent broadcast over a mutual frequency band.
When CDM is employed to allow multiple users to share a single communications channel, the
technology is known as Code Division Multiple Access (CDMA).
b) Main air interface in the change from 3G to 4G and WiMAX. Explain how OFDM is different
from above techniques and the special feature of signals used by OFDM
Zheng,(2010) found out that air interface generally is a communication link between stations in
mobile, it is radio based in which a subscriber navigates from one cell to another in the system.
As this takes place, there is a periodic change in the active base and each change is called
handoff.
Cho, Kim,Yang and Kang.(2010) found that OFDM also known as Orthogonal frequency division
multiplexing uses a digital multi carrier modulation technique. Li,(2010) found out that the main
difference between OFDM and main air interface is the fact that main air interface involves
handoff while OFDM uses digital multi carrier instead of the handoffs.
c) IEEE 802.11ac wireless LAN standard uses 40 MHz total bandwidth in OFDM scheme.
It is a set of media access control and physical layer control layer specifications for (I)
subcarrier bandwidth for 48 subscribers.
LAN and in OFDM it states that the frequency used must be 40 Mega Hatz.
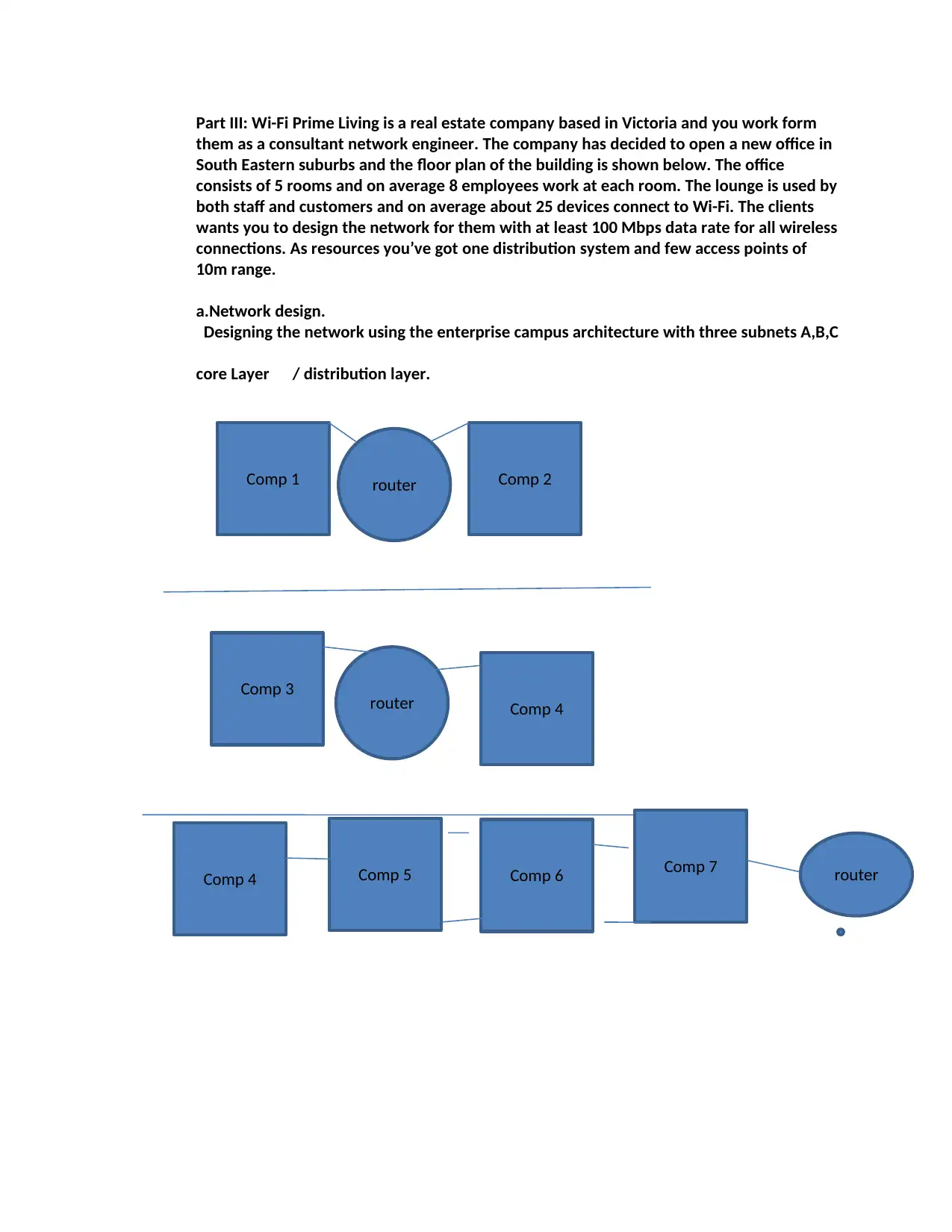
Part III: Wi-Fi Prime Living is a real estate company based in Victoria and you work form
them as a consultant network engineer. The company has decided to open a new office in
South Eastern suburbs and the floor plan of the building is shown below. The office
consists of 5 rooms and on average 8 employees work at each room. The lounge is used by
both staff and customers and on average about 25 devices connect to Wi-Fi. The clients
wants you to design the network for them with at least 100 Mbps data rate for all wireless
connections. As resources you’ve got one distribution system and few access points of
10m range.
a.Network design.
Designing the network using the enterprise campus architecture with three subnets A,B,C
core Layer / distribution layer.
Comp 1 Comp 2
Comp 3
Comp 4
Comp 4 Comp 5 Comp 6 Comp 7
router
router
router
them as a consultant network engineer. The company has decided to open a new office in
South Eastern suburbs and the floor plan of the building is shown below. The office
consists of 5 rooms and on average 8 employees work at each room. The lounge is used by
both staff and customers and on average about 25 devices connect to Wi-Fi. The clients
wants you to design the network for them with at least 100 Mbps data rate for all wireless
connections. As resources you’ve got one distribution system and few access points of
10m range.
a.Network design.
Designing the network using the enterprise campus architecture with three subnets A,B,C
core Layer / distribution layer.
Comp 1 Comp 2
Comp 3
Comp 4
Comp 4 Comp 5 Comp 6 Comp 7
router
router
router
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

b. Calculating the BSS, bss is the common access point of the two networks,ess on the
other side is the effective sample size.
Ess=1/n intergral of i=1 to n*y
c. calculating throughput for DS.
Differentiated Services DS is a protocol for showing and controlling network traffic by class.
DS= bandwidth/nodes.
d. Recommend a suitable IEEE substandard for the network and give reasons.
I would recommend IEEE 802.2 as the substandard for this network , it is
responsible for data link that are sovereign of the underlying medium thus makes it
suitable for this network.
e. Recommend security strategies.
Coming up with safety put ups would necessitate one to have in mind the safety
loopholes that the network might encounter. In this scenario the internet safety is
the key issue to take into consideration.
Strategies:
An entry guideline that defines entry permissions and preferences. The entry
guideline must give guidelines for connecting external networks, connecting devices to a
network, and adding new programs to program. An entry guideline may also guide on
how data is grouped for instance, private, internal, and top privacy for that matter.
A responsibility entry that shows the obligation of users and management. The
obligation guideline should single out an audit capability and provide incident-handling
guidelines that stipulates what to do and whom to contact if a possible intrusion is
detected.
Access guideline that sets up trust by an effective password policy and sets up steps for
not onsite location authentication.
A privacy guideline that dictates reasonable expectations of privacy concerning the
overseeing of email, logging of keystrokes, and entry to files.
Developing Security Procedures
Safety procedures done on safety policies. Guidelines define set up, entry, audit, and
maintenance procedure. Safety procedures are written for end users, network
admins. Safety procedures should single out how to tackle incidents
other side is the effective sample size.
Ess=1/n intergral of i=1 to n*y
c. calculating throughput for DS.
Differentiated Services DS is a protocol for showing and controlling network traffic by class.
DS= bandwidth/nodes.
d. Recommend a suitable IEEE substandard for the network and give reasons.
I would recommend IEEE 802.2 as the substandard for this network , it is
responsible for data link that are sovereign of the underlying medium thus makes it
suitable for this network.
e. Recommend security strategies.
Coming up with safety put ups would necessitate one to have in mind the safety
loopholes that the network might encounter. In this scenario the internet safety is
the key issue to take into consideration.
Strategies:
An entry guideline that defines entry permissions and preferences. The entry
guideline must give guidelines for connecting external networks, connecting devices to a
network, and adding new programs to program. An entry guideline may also guide on
how data is grouped for instance, private, internal, and top privacy for that matter.
A responsibility entry that shows the obligation of users and management. The
obligation guideline should single out an audit capability and provide incident-handling
guidelines that stipulates what to do and whom to contact if a possible intrusion is
detected.
Access guideline that sets up trust by an effective password policy and sets up steps for
not onsite location authentication.
A privacy guideline that dictates reasonable expectations of privacy concerning the
overseeing of email, logging of keystrokes, and entry to files.
Developing Security Procedures
Safety procedures done on safety policies. Guidelines define set up, entry, audit, and
maintenance procedure. Safety procedures are written for end users, network
admins. Safety procedures should single out how to tackle incidents
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References.
Lu, P., Xu, Z., Lu, X., & Liu, X. (2013). Digital image information encryption based on
compressive sensing and double random-phase encoding technique. Optik-
International Journal for Light and Electron Optics, 124(16), 2514-2518.
Ishtiaq Roufa, R. M., Mustafaa, H., Travis Taylora, S. O., Xua, W., Gruteserb, M.,
Trappeb, W., & Seskarb, I. (2010, August). Security and privacy vulnerabilities of in-
car wireless networks: A tire pressure monitoring system case study. In 19th
USENIX Security Symposium, Washington DC (pp. 11-13).
Li, P., & Singh, H. (2010). U.S. Patent No. 7,817,558. Washington, DC: U.S. Patent
and Trademark Office.
Chang, D. C., & Chen, S. (2011). U.S. Patent Application No. 12/848,953.
Cho, Y. S., Kim, J., Yang, W. Y., & Kang, C. G. (2010). MIMO-OFDM wireless
communications with MATLAB. John Wiley & Sons.
Elgala, H., Mesleh, R., & Haas, H. (2011). Indoor optical wireless communication:
potential and state-of-the-art. IEEE Communications Magazine, 49(9).
Lu, P., Xu, Z., Lu, X., & Liu, X. (2013). Digital image information encryption based on
compressive sensing and double random-phase encoding technique. Optik-
International Journal for Light and Electron Optics, 124(16), 2514-2518.
Ishtiaq Roufa, R. M., Mustafaa, H., Travis Taylora, S. O., Xua, W., Gruteserb, M.,
Trappeb, W., & Seskarb, I. (2010, August). Security and privacy vulnerabilities of in-
car wireless networks: A tire pressure monitoring system case study. In 19th
USENIX Security Symposium, Washington DC (pp. 11-13).
Li, P., & Singh, H. (2010). U.S. Patent No. 7,817,558. Washington, DC: U.S. Patent
and Trademark Office.
Chang, D. C., & Chen, S. (2011). U.S. Patent Application No. 12/848,953.
Cho, Y. S., Kim, J., Yang, W. Y., & Kang, C. G. (2010). MIMO-OFDM wireless
communications with MATLAB. John Wiley & Sons.
Elgala, H., Mesleh, R., & Haas, H. (2011). Indoor optical wireless communication:
potential and state-of-the-art. IEEE Communications Magazine, 49(9).
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



