IT Networking Design: Wireless Communication Topologies Analysis
VerifiedAdded on 2023/06/15
|12
|1708
|463
Report
AI Summary
This report provides a detailed overview of IT networking design, specifically focusing on wireless communication topologies and WAN technologies. It begins by defining network topologies and delving into three main types: point-to-point, point-to-multipoint, and multipoint-to-point. Each topology is explained with scenarios of usage, advantages, and disadvantages. The report then transitions to WAN technologies, discussing point-to-point protocols, packet-switched protocols, and circuit-switched protocols. For each protocol, the definition and data transmission technologies are outlined, including bandwidth and relevant details. The report concludes with a list of references, providing a comprehensive understanding of the concepts discussed. Desklib provides more solved assignments and past papers for students.

Running head: IT NETWORKING DESIGNING 1
It Networking Designing
It Networking Designing Using Wireless Communication
[Student Name]
[University Name]
It Networking Designing
It Networking Designing Using Wireless Communication
[Student Name]
[University Name]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2IT NETWORKING DESIGNING
Table of Contents
Network Wireless communication..................................................................................................3
Question 1: Configuration topologies..........................................................................................3
Point to point topology.............................................................................................................3
Point to multipoint topology.....................................................................................................5
Multipoint to Point topology....................................................................................................6
Question 2 :WAN Technologies..................................................................................................9
Point-to-Point protocols...........................................................................................................9
Packet switched protocols........................................................................................................9
Circuit switched protocols.....................................................................................................10
Reference.......................................................................................................................................12
Network Wireless communication.
Question 1: Configuration topologies
Table of Contents
Network Wireless communication..................................................................................................3
Question 1: Configuration topologies..........................................................................................3
Point to point topology.............................................................................................................3
Point to multipoint topology.....................................................................................................5
Multipoint to Point topology....................................................................................................6
Question 2 :WAN Technologies..................................................................................................9
Point-to-Point protocols...........................................................................................................9
Packet switched protocols........................................................................................................9
Circuit switched protocols.....................................................................................................10
Reference.......................................................................................................................................12
Network Wireless communication.
Question 1: Configuration topologies

3IT NETWORKING DESIGNING
In computing the network topologies refer to study of how the various elements and
components are arranged or mapped to each other in a given network, these elements includes
connection links , nodes and the workstations.
The topology also describes how the connections are done both physically and logically
between the network nodes.
The network topologies are determined by the graphical maps which are used to
determine the connections between the nodes either physically or logically, below are the various
type of topologies used in the network designs.
Point to point topology.
Definitions.
The point-to-point topology as in the above figure, is referred to as a link that connects
two network nodes or end points permanently .
There is switched point-to-point topology that mainly applies in the telephones
technologies; however the on demand point-to-point connectivity depends mainly on number of
the subscribers of the network (Forouzan, 2014).
.
Scenarios of usage of point to point topology.
The point to point technology can be used in various scenarios which includes the following:
In computing the network topologies refer to study of how the various elements and
components are arranged or mapped to each other in a given network, these elements includes
connection links , nodes and the workstations.
The topology also describes how the connections are done both physically and logically
between the network nodes.
The network topologies are determined by the graphical maps which are used to
determine the connections between the nodes either physically or logically, below are the various
type of topologies used in the network designs.
Point to point topology.
Definitions.
The point-to-point topology as in the above figure, is referred to as a link that connects
two network nodes or end points permanently .
There is switched point-to-point topology that mainly applies in the telephones
technologies; however the on demand point-to-point connectivity depends mainly on number of
the subscribers of the network (Forouzan, 2014).
.
Scenarios of usage of point to point topology.
The point to point technology can be used in various scenarios which includes the following:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4IT NETWORKING DESIGNING
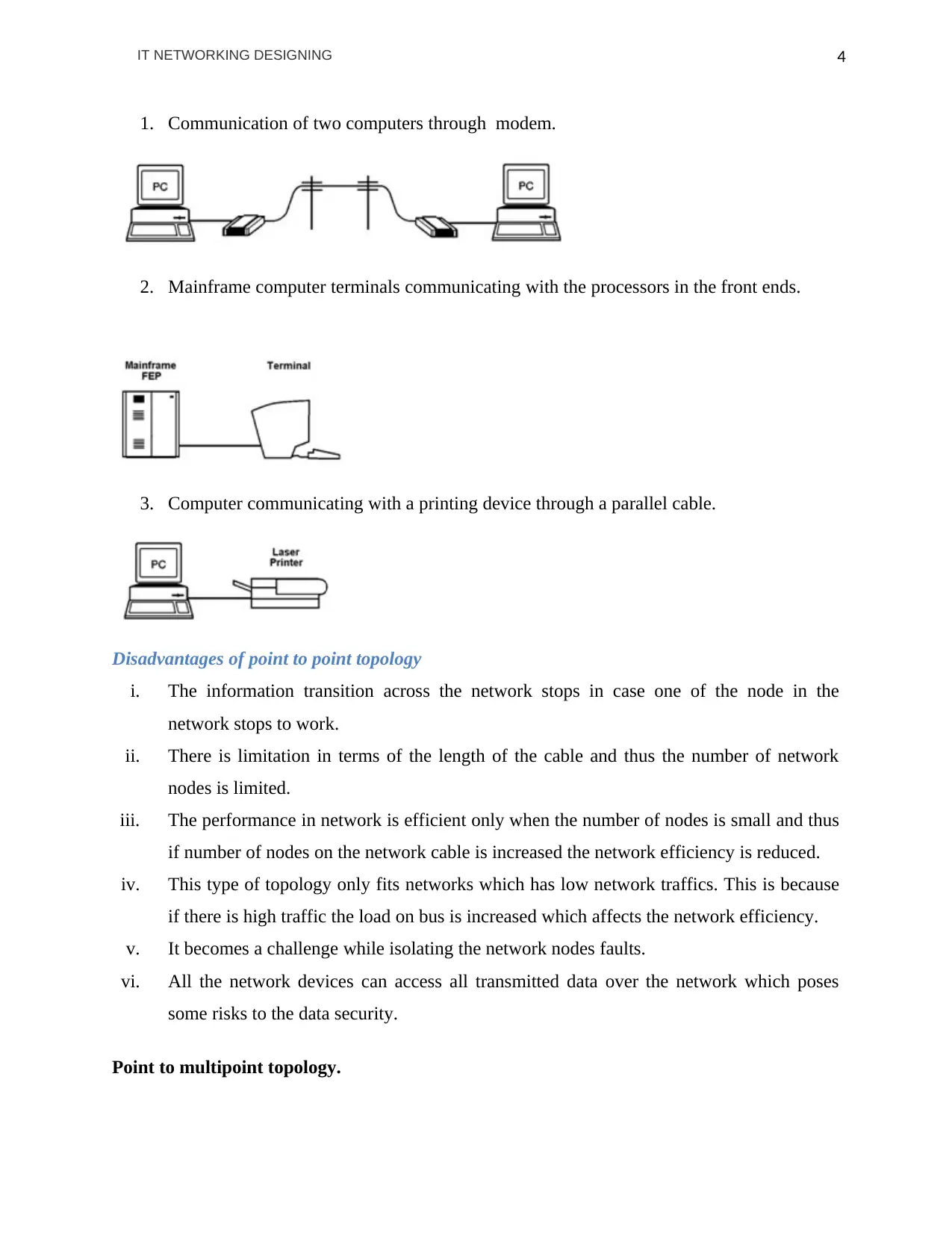
1. Communication of two computers through modem.
2. Mainframe computer terminals communicating with the processors in the front ends.
3. Computer communicating with a printing device through a parallel cable.
Disadvantages of point to point topology
i. The information transition across the network stops in case one of the node in the
network stops to work.
ii. There is limitation in terms of the length of the cable and thus the number of network
nodes is limited.
iii. The performance in network is efficient only when the number of nodes is small and thus
if number of nodes on the network cable is increased the network efficiency is reduced.
iv. This type of topology only fits networks which has low network traffics. This is because
if there is high traffic the load on bus is increased which affects the network efficiency.
v. It becomes a challenge while isolating the network nodes faults.
vi. All the network devices can access all transmitted data over the network which poses
some risks to the data security.
Point to multipoint topology.
1. Communication of two computers through modem.
2. Mainframe computer terminals communicating with the processors in the front ends.
3. Computer communicating with a printing device through a parallel cable.
Disadvantages of point to point topology
i. The information transition across the network stops in case one of the node in the
network stops to work.
ii. There is limitation in terms of the length of the cable and thus the number of network
nodes is limited.
iii. The performance in network is efficient only when the number of nodes is small and thus
if number of nodes on the network cable is increased the network efficiency is reduced.
iv. This type of topology only fits networks which has low network traffics. This is because
if there is high traffic the load on bus is increased which affects the network efficiency.
v. It becomes a challenge while isolating the network nodes faults.
vi. All the network devices can access all transmitted data over the network which poses
some risks to the data security.
Point to multipoint topology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5IT NETWORKING DESIGNING
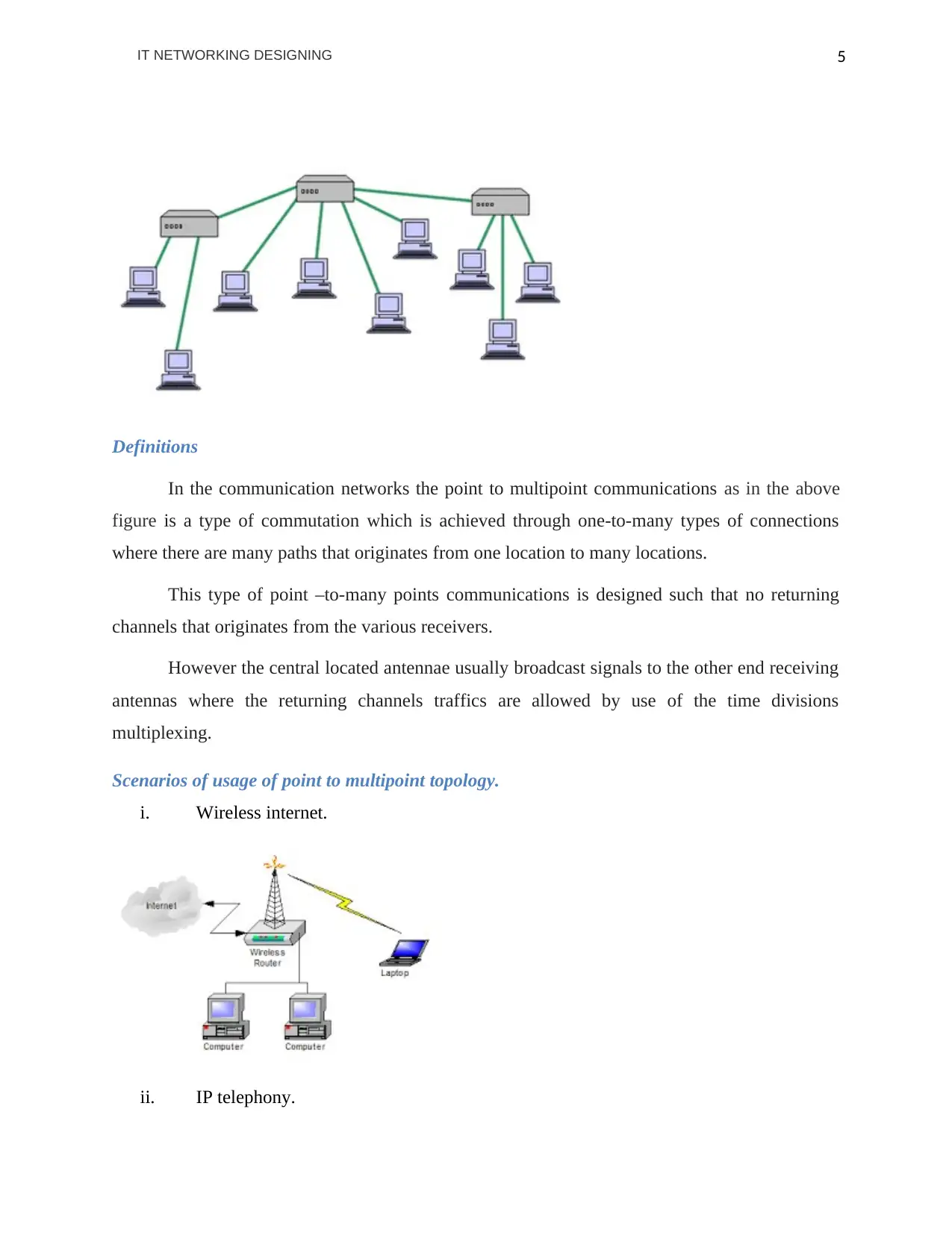
Definitions
In the communication networks the point to multipoint communications as in the above
figure is a type of commutation which is achieved through one-to-many types of connections
where there are many paths that originates from one location to many locations.
This type of point –to-many points communications is designed such that no returning
channels that originates from the various receivers.
However the central located antennae usually broadcast signals to the other end receiving
antennas where the returning channels traffics are allowed by use of the time divisions
multiplexing.
Scenarios of usage of point to multipoint topology.
i. Wireless internet.
ii. IP telephony.
Definitions
In the communication networks the point to multipoint communications as in the above
figure is a type of commutation which is achieved through one-to-many types of connections
where there are many paths that originates from one location to many locations.
This type of point –to-many points communications is designed such that no returning
channels that originates from the various receivers.
However the central located antennae usually broadcast signals to the other end receiving
antennas where the returning channels traffics are allowed by use of the time divisions
multiplexing.
Scenarios of usage of point to multipoint topology.
i. Wireless internet.
ii. IP telephony.
6IT NETWORKING DESIGNING
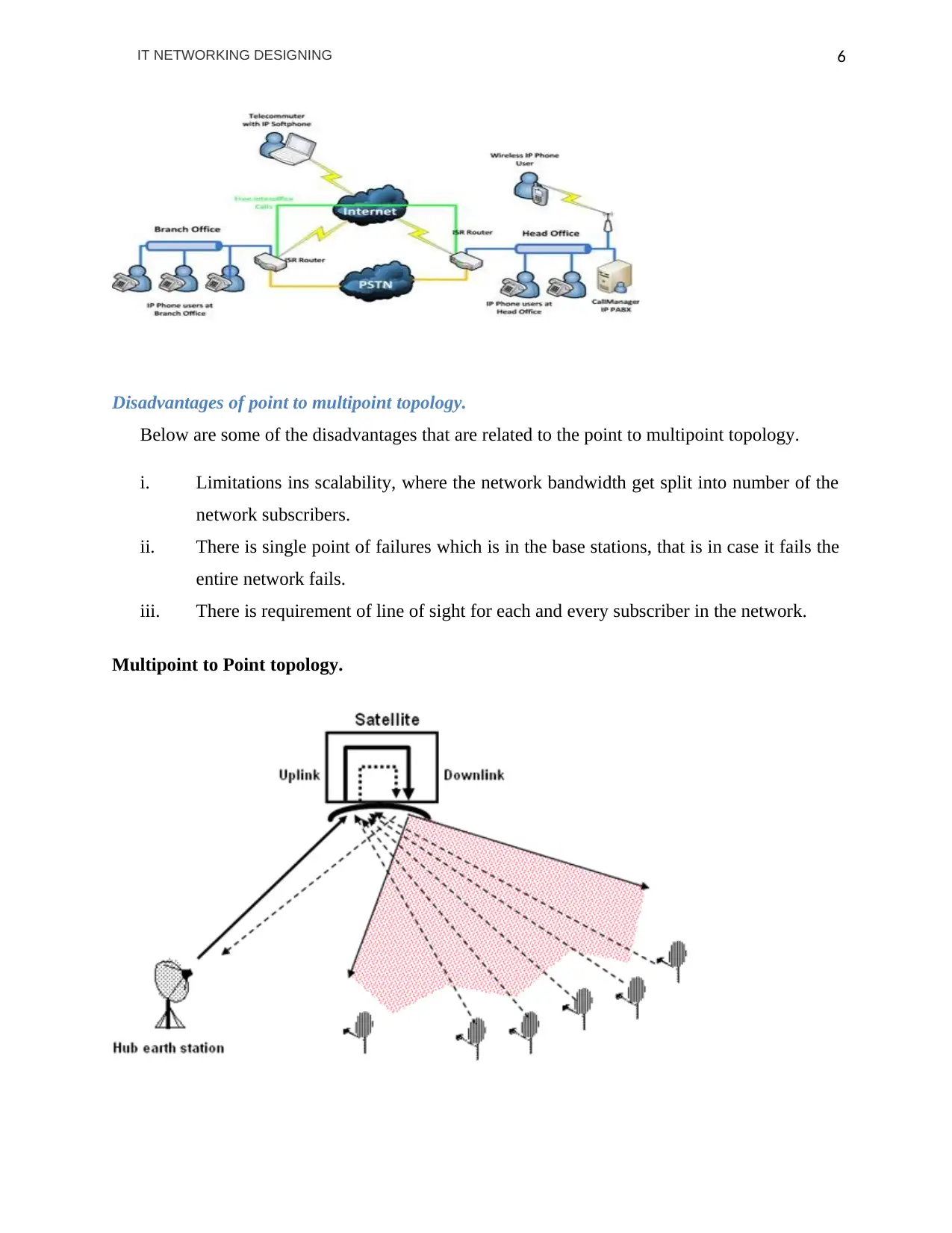
Disadvantages of point to multipoint topology.
Below are some of the disadvantages that are related to the point to multipoint topology.
i. Limitations ins scalability, where the network bandwidth get split into number of the
network subscribers.
ii. There is single point of failures which is in the base stations, that is in case it fails the
entire network fails.
iii. There is requirement of line of sight for each and every subscriber in the network.
Multipoint to Point topology.
Disadvantages of point to multipoint topology.
Below are some of the disadvantages that are related to the point to multipoint topology.
i. Limitations ins scalability, where the network bandwidth get split into number of the
network subscribers.
ii. There is single point of failures which is in the base stations, that is in case it fails the
entire network fails.
iii. There is requirement of line of sight for each and every subscriber in the network.
Multipoint to Point topology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7IT NETWORKING DESIGNING
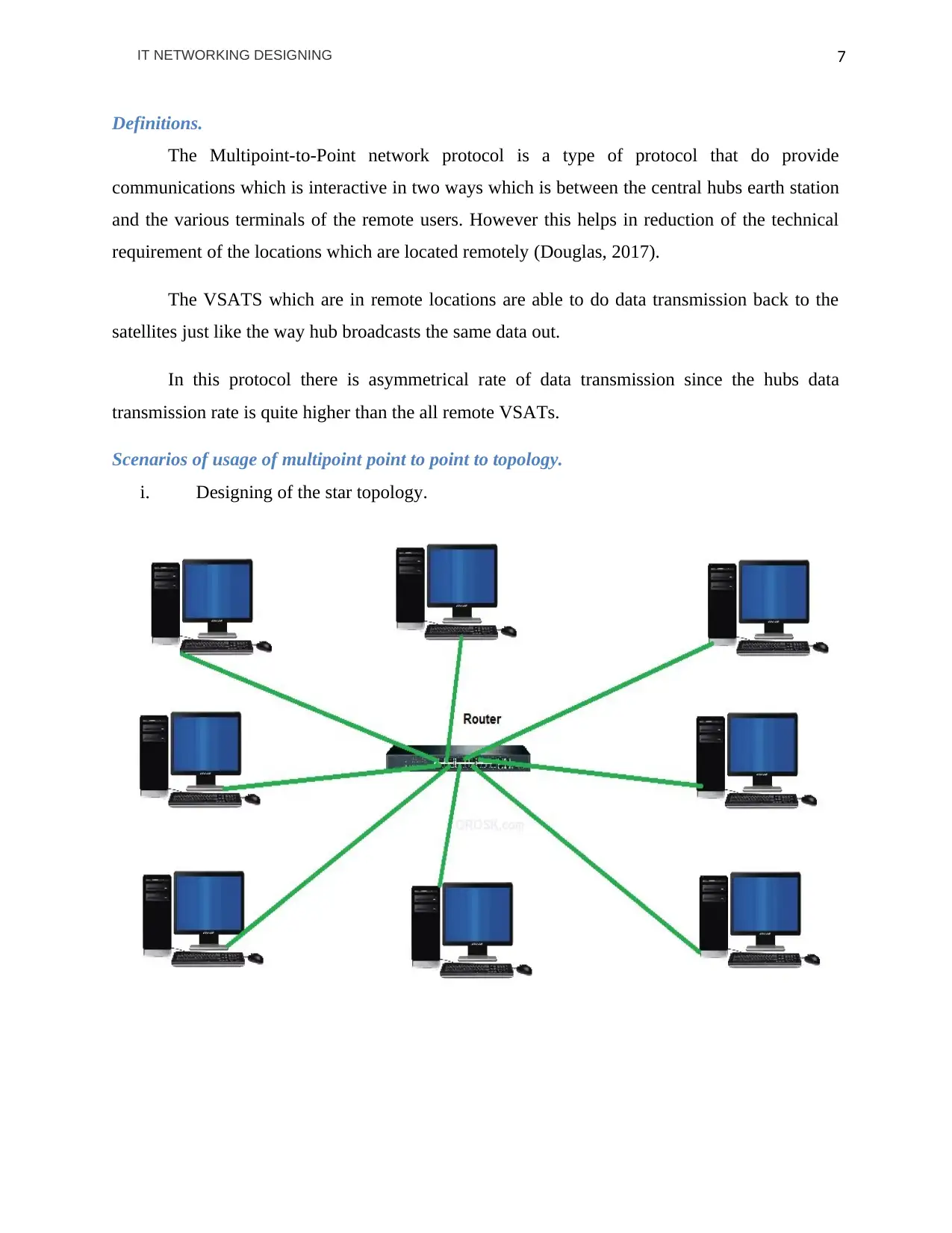
Definitions.
The Multipoint-to-Point network protocol is a type of protocol that do provide
communications which is interactive in two ways which is between the central hubs earth station
and the various terminals of the remote users. However this helps in reduction of the technical
requirement of the locations which are located remotely (Douglas, 2017).
The VSATS which are in remote locations are able to do data transmission back to the
satellites just like the way hub broadcasts the same data out.
In this protocol there is asymmetrical rate of data transmission since the hubs data
transmission rate is quite higher than the all remote VSATs.
Scenarios of usage of multipoint point to point to topology.
i. Designing of the star topology.
Definitions.
The Multipoint-to-Point network protocol is a type of protocol that do provide
communications which is interactive in two ways which is between the central hubs earth station
and the various terminals of the remote users. However this helps in reduction of the technical
requirement of the locations which are located remotely (Douglas, 2017).
The VSATS which are in remote locations are able to do data transmission back to the
satellites just like the way hub broadcasts the same data out.
In this protocol there is asymmetrical rate of data transmission since the hubs data
transmission rate is quite higher than the all remote VSATs.
Scenarios of usage of multipoint point to point to topology.
i. Designing of the star topology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8IT NETWORKING DESIGNING
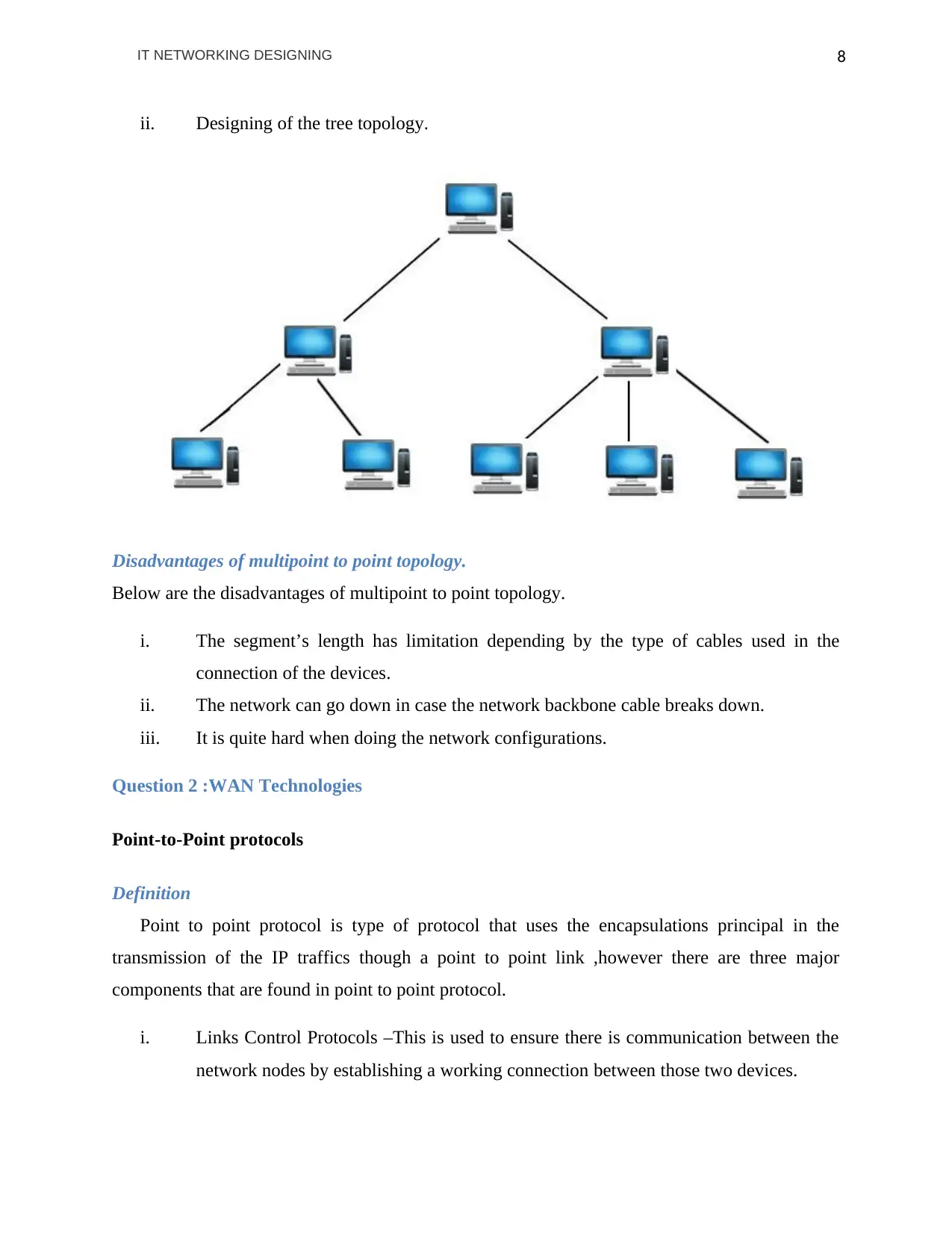
ii. Designing of the tree topology.
Disadvantages of multipoint to point topology.
Below are the disadvantages of multipoint to point topology.
i. The segment’s length has limitation depending by the type of cables used in the
connection of the devices.
ii. The network can go down in case the network backbone cable breaks down.
iii. It is quite hard when doing the network configurations.
Question 2 :WAN Technologies
Point-to-Point protocols
Definition
Point to point protocol is type of protocol that uses the encapsulations principal in the
transmission of the IP traffics though a point to point link ,however there are three major
components that are found in point to point protocol.
i. Links Control Protocols –This is used to ensure there is communication between the
network nodes by establishing a working connection between those two devices.
ii. Designing of the tree topology.
Disadvantages of multipoint to point topology.
Below are the disadvantages of multipoint to point topology.
i. The segment’s length has limitation depending by the type of cables used in the
connection of the devices.
ii. The network can go down in case the network backbone cable breaks down.
iii. It is quite hard when doing the network configurations.
Question 2 :WAN Technologies
Point-to-Point protocols
Definition
Point to point protocol is type of protocol that uses the encapsulations principal in the
transmission of the IP traffics though a point to point link ,however there are three major
components that are found in point to point protocol.
i. Links Control Protocols –This is used to ensure there is communication between the
network nodes by establishing a working connection between those two devices.
9IT NETWORKING DESIGNING
ii. Authentication protocol-This is used to facilitate security this is by ensuring that the
connections between the nodes is always secure .
iii. Network control protocol-This is another component that usually initialize the
protocol in order to enable handling of protocols in the multiple networks layers.
Data transmission technologies.
In this type of protocol there are various types of technologies that are used to allow the
transmission of the data from one point to the other in the network, however the data being
transmitted is many forms like electromagnetic signals radio waves, microwaves and infra-red
signals. Below are the technologies used.
Technology Bandwidth protocol
copper wire 100 Mb/s to 1 Gb/s Point-to-point
optical fiber 10 Gb/s and above Point-to-point
wireless communications channel 25 Mb/s to 211Mb/s Point-to-point
Computer’s bus 8 Mb/s to 1.07Gb/s Point-to-point
Packet switched protocols
ii. Authentication protocol-This is used to facilitate security this is by ensuring that the
connections between the nodes is always secure .
iii. Network control protocol-This is another component that usually initialize the
protocol in order to enable handling of protocols in the multiple networks layers.
Data transmission technologies.
In this type of protocol there are various types of technologies that are used to allow the
transmission of the data from one point to the other in the network, however the data being
transmitted is many forms like electromagnetic signals radio waves, microwaves and infra-red
signals. Below are the technologies used.
Technology Bandwidth protocol
copper wire 100 Mb/s to 1 Gb/s Point-to-point
optical fiber 10 Gb/s and above Point-to-point
wireless communications channel 25 Mb/s to 211Mb/s Point-to-point
Computer’s bus 8 Mb/s to 1.07Gb/s Point-to-point
Packet switched protocols
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10IT NETWORKING DESIGNING
Definition
This is a protocol as in the above figure where the data message that is being transmitted
is split into small units called packets where every packet is give the respective source’s and
destination’s address since each packet follows a different route towards their destinations and
the packets are able to use various routes in case the some of the routes are not available
(Andrew , 2015).
Therefore in packet switching there is division of messages into data packets where each
is transmitted individually and thus the internet make use of the packet-switching protocol in
connectivity and data transmission.
Data transmission technologies.
In this protocol there are various technologies that are used to transmit the data and they
use different bandwidth ,some of the technologies used are as follows:
Technology Bandwidth protocol
Routers (wireless/and wired routers) 20 Mb/s to 5 Gb/s Packet switched
copper wire(cat5 or cat6) 100 Mb/s to 1 Gb/s Packet switched
optical fiber cable 10 Gb/s and above Packet switched
Computer’s bus(serial or parallel bus) 8 Mb/s to 1.07Gb/s Packet switched
Circuit switched protocols
Definition
The circuit switched protocol as in the above figure is the telecommunication networks
implementation methods where there are two involved nodes in network that establishes a
dedicated type of communication channel or circuit via the network before the communication of
the two nodes (Behrouz , 2016).
Definition
This is a protocol as in the above figure where the data message that is being transmitted
is split into small units called packets where every packet is give the respective source’s and
destination’s address since each packet follows a different route towards their destinations and
the packets are able to use various routes in case the some of the routes are not available
(Andrew , 2015).
Therefore in packet switching there is division of messages into data packets where each
is transmitted individually and thus the internet make use of the packet-switching protocol in
connectivity and data transmission.
Data transmission technologies.
In this protocol there are various technologies that are used to transmit the data and they
use different bandwidth ,some of the technologies used are as follows:
Technology Bandwidth protocol
Routers (wireless/and wired routers) 20 Mb/s to 5 Gb/s Packet switched
copper wire(cat5 or cat6) 100 Mb/s to 1 Gb/s Packet switched
optical fiber cable 10 Gb/s and above Packet switched
Computer’s bus(serial or parallel bus) 8 Mb/s to 1.07Gb/s Packet switched
Circuit switched protocols
Definition
The circuit switched protocol as in the above figure is the telecommunication networks
implementation methods where there are two involved nodes in network that establishes a
dedicated type of communication channel or circuit via the network before the communication of
the two nodes (Behrouz , 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11IT NETWORKING DESIGNING
.
The circuits established thus provides full bandwidths channels which ensure the
connection is maintained for the entire period of communication, however this circuits acts like
the communicating nodes were linked through an electrical circuit.
In this protocol the system do establish the physical connections where the data is transmitted
among the two nodes and the channels closes immediately when the data transmissions are
completed (William, 2014).
In this system there are three major phases as follows:
i. Establishing the Circuit-This is the process where the a link which is dedicated is set up
between the source device and destination device.
ii. Transferring data- This is the process where the data is transmitted from the sources to
destinations devices.
iii. Disconnecting the circuits-This is the stage where after the communication is completed
the dedicated link is removed to close the communication.
Therefore the protocol is able o transmit the data through the dedicated connection at a
bandwidth of 37-39 KB/s with for messages limitations.
Data transmission technologies.
Technology Bandwidth protocol
Dedicated
links
37-39 KB/s Packet switched
(Tom , 2015).
.
The circuits established thus provides full bandwidths channels which ensure the
connection is maintained for the entire period of communication, however this circuits acts like
the communicating nodes were linked through an electrical circuit.
In this protocol the system do establish the physical connections where the data is transmitted
among the two nodes and the channels closes immediately when the data transmissions are
completed (William, 2014).
In this system there are three major phases as follows:
i. Establishing the Circuit-This is the process where the a link which is dedicated is set up
between the source device and destination device.
ii. Transferring data- This is the process where the data is transmitted from the sources to
destinations devices.
iii. Disconnecting the circuits-This is the stage where after the communication is completed
the dedicated link is removed to close the communication.
Therefore the protocol is able o transmit the data through the dedicated connection at a
bandwidth of 37-39 KB/s with for messages limitations.
Data transmission technologies.
Technology Bandwidth protocol
Dedicated
links
37-39 KB/s Packet switched
(Tom , 2015).

12IT NETWORKING DESIGNING
Reference
Andrew ,S(2015).Computer Networks. New York:
Prentice Hall.
Behrouz ,A.(2016).Data Communication and Networking.New York:
McGraw-Hill Education.
Douglas,C(2017).Internetworking with TCP/IP, Volume 1. California:
Addison-Wesley Professional.
Forouzan,I.(2014). Computer Networks: A Top – Down Approach.
New York: McGraw-Hill .
Tom ,C.(2015).IPv6 Address Planning: Designing an Address Plan for the Future.
San Francisco: O'Reilly Media
William,S.(2014). Data and Computer Communication. New Delhi:
Tata McGraw Hill.
Reference
Andrew ,S(2015).Computer Networks. New York:
Prentice Hall.
Behrouz ,A.(2016).Data Communication and Networking.New York:
McGraw-Hill Education.
Douglas,C(2017).Internetworking with TCP/IP, Volume 1. California:
Addison-Wesley Professional.
Forouzan,I.(2014). Computer Networks: A Top – Down Approach.
New York: McGraw-Hill .
Tom ,C.(2015).IPv6 Address Planning: Designing an Address Plan for the Future.
San Francisco: O'Reilly Media
William,S.(2014). Data and Computer Communication. New Delhi:
Tata McGraw Hill.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





