Report on Security for Wireless Network Users: [Company Name] Analysis
VerifiedAdded on 2020/04/01
|6
|757
|115
Report
AI Summary
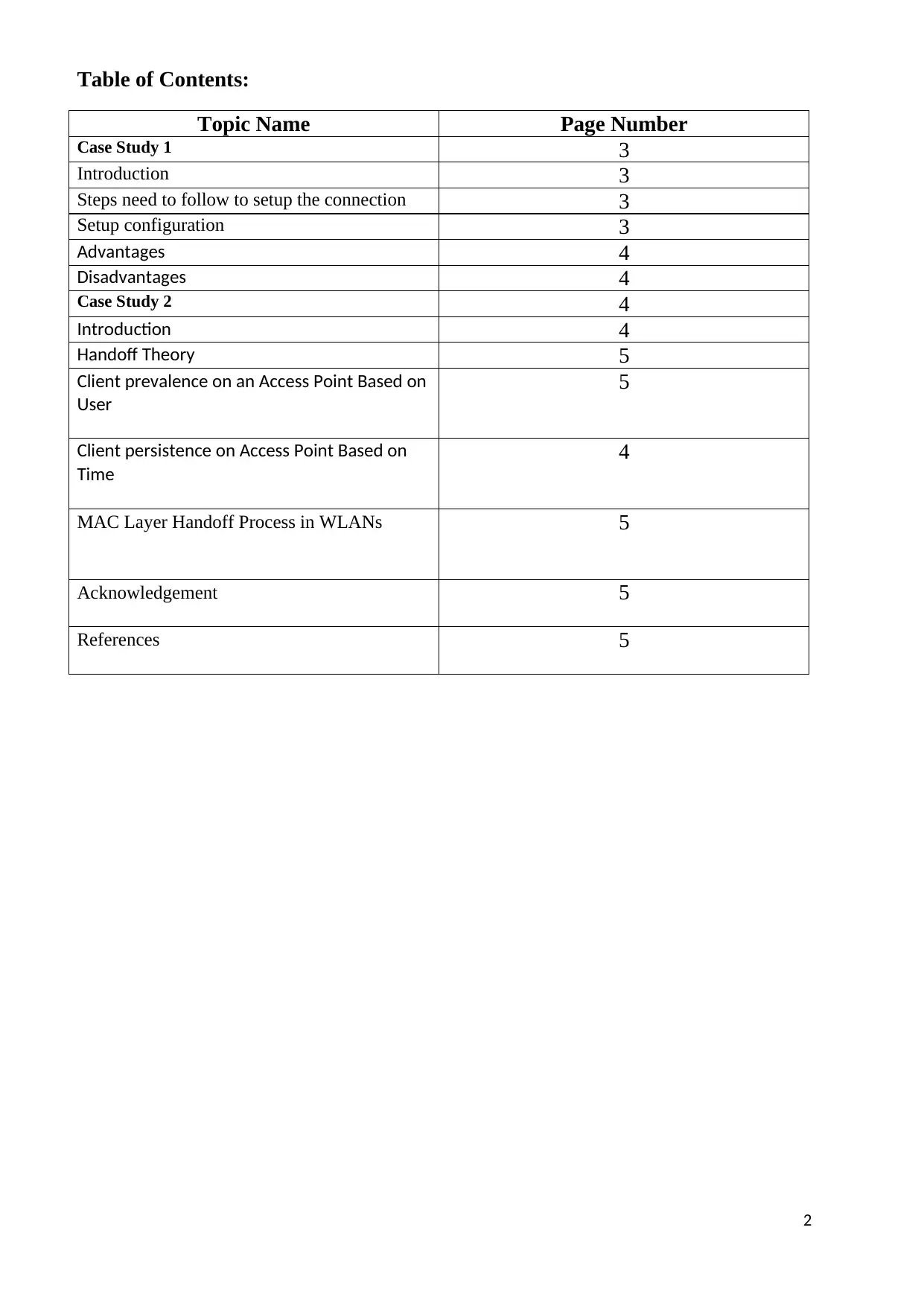
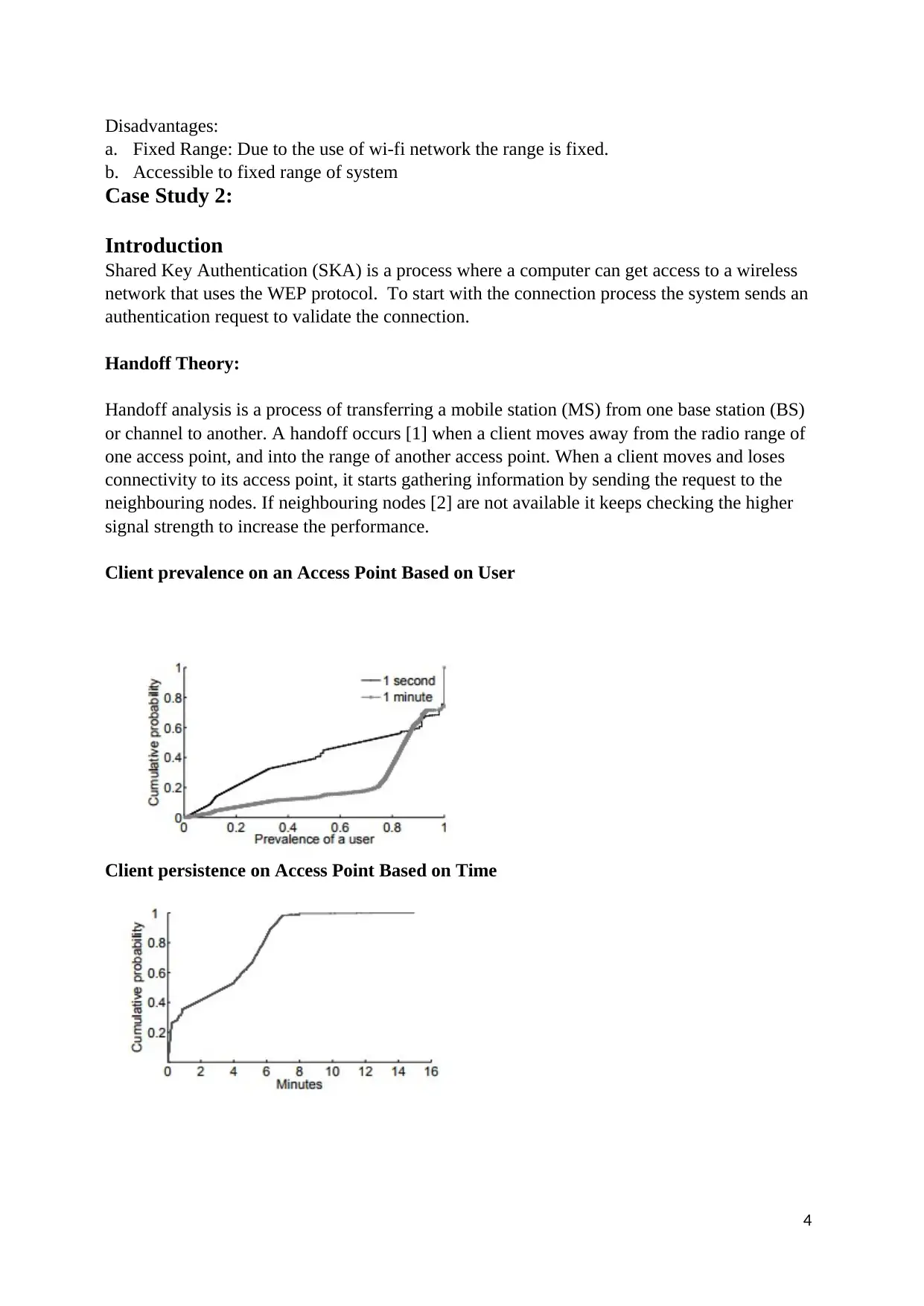
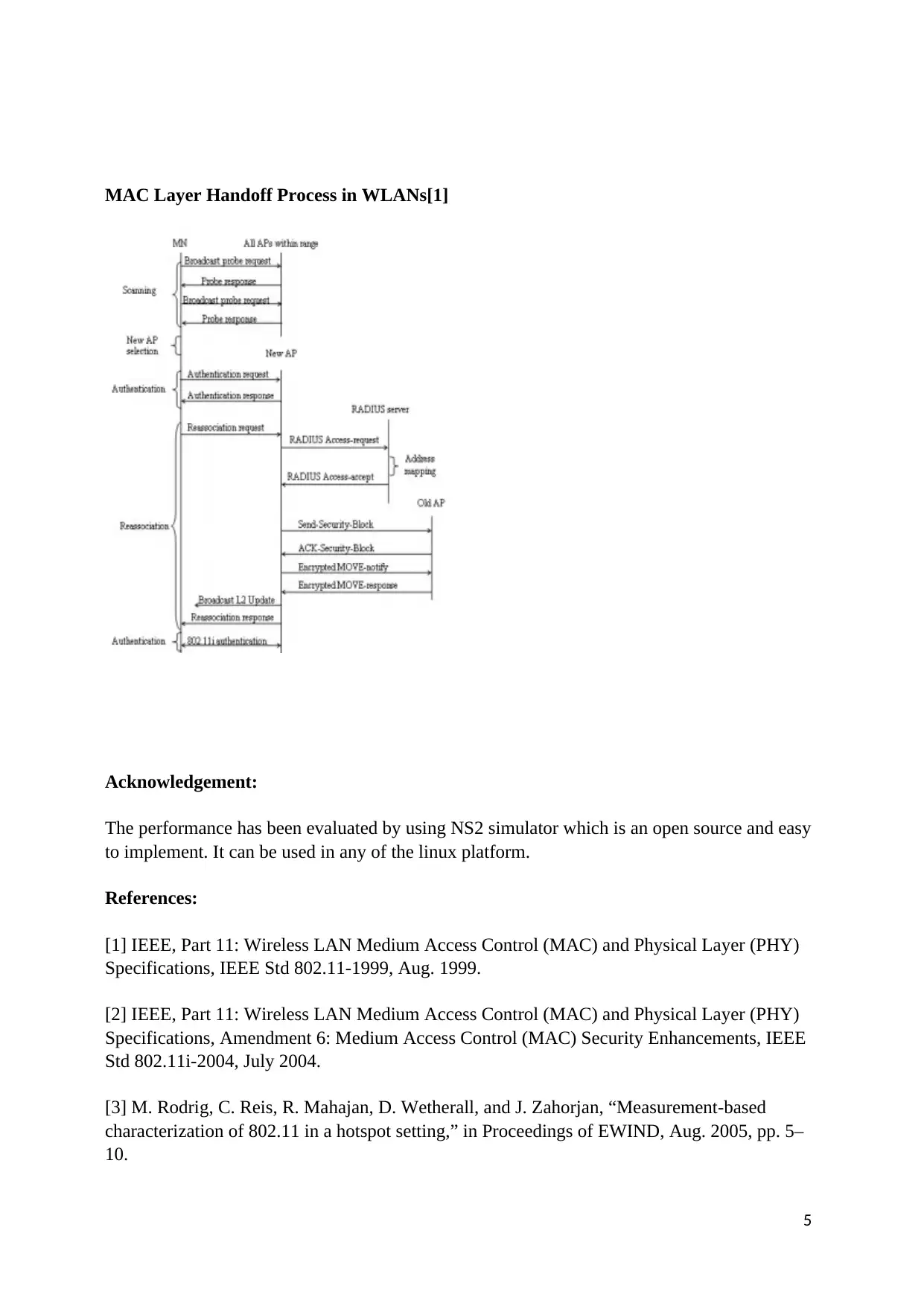
This report, focusing on wireless network security, begins with an introduction and a table of contents outlining the key areas covered. The report presents two case studies. Case Study 1 addresses securing a wireless camera setup, detailing the necessary steps, security protocols (like WPA-2), advantages (cost-effectiveness, scalability, and security), and disadvantages (fixed range). Case Study 2 delves into Shared Key Authentication (SKA) and the handoff theory, explaining the process of transferring a mobile station between base stations. It examines client prevalence and persistence on access points, followed by a discussion of the MAC layer handoff process in WLANs. The report acknowledges the use of the NS2 simulator for performance evaluation and concludes with references to relevant IEEE standards and research papers.
1 out of 6










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)