MN603 Trimester 3 2019: Analysis of Wireless Network Routing Protocols
VerifiedAdded on 2022/09/06
|9
|2431
|17
Report
AI Summary
This report provides a comprehensive analysis of geographic routing protocols within wireless networks, evaluating their security vulnerabilities and proposing effective countermeasures. The introduction defines geographic routing and its protocols, like GSPR and GEAR. The analysis section explores the advantages and disadvantages of geographic routing, highlighting its efficiency and scalability, but also its security risks. The report then delves into various security threats, including DDOS attacks, packet mistreating, routing table poisoning, and Hit and Run DDOS attacks, detailing their impact on network performance and data privacy. The countermeasures section suggests best practices for the management plane, emphasizing proper training, encryption-based networks, and the use of firewalls and access control lists (ACLs) to mitigate these threats. The conclusion reiterates the importance of addressing security attacks in geographic routing protocols and recommends implementing comprehensive security measures to protect data and enhance network performance. The report is supported by numerous references to relevant research in the field.

NETWORKING 0
Wireless network and security
Wireless network and security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 1
Table of Contents
Introduction...........................................................................................................................................................2
Analysis of routing protocols..................................................................................................................................2
Geographic routing.............................................................................................................................................2
Advantages and disadvantages of geographic routing.......................................................................................3
Security issues....................................................................................................................................................3
Attacks against the routing protocols.....................................................................................................................3
DDOS attack........................................................................................................................................................3
Packet mistreating attacks..................................................................................................................................4
Routing table poisoning (RTP)............................................................................................................................4
Hit and Run DDOS (HAR) attack..........................................................................................................................4
Countermeasures for addressing attacks...............................................................................................................4
Management plane best practices.....................................................................................................................5
Provide proper training and education...............................................................................................................5
Develop and implement an encryption-based network.....................................................................................5
Other countermeasures.....................................................................................................................................5
Conclusion..............................................................................................................................................................5
References..............................................................................................................................................................7
Table of Contents
Introduction...........................................................................................................................................................2
Analysis of routing protocols..................................................................................................................................2
Geographic routing.............................................................................................................................................2
Advantages and disadvantages of geographic routing.......................................................................................3
Security issues....................................................................................................................................................3
Attacks against the routing protocols.....................................................................................................................3
DDOS attack........................................................................................................................................................3
Packet mistreating attacks..................................................................................................................................4
Routing table poisoning (RTP)............................................................................................................................4
Hit and Run DDOS (HAR) attack..........................................................................................................................4
Countermeasures for addressing attacks...............................................................................................................4
Management plane best practices.....................................................................................................................5
Provide proper training and education...............................................................................................................5
Develop and implement an encryption-based network.....................................................................................5
Other countermeasures.....................................................................................................................................5
Conclusion..............................................................................................................................................................5
References..............................................................................................................................................................7

NETWORKING 2
Introduction
Geographic routing is defined as a routing principle that relies on the geographic position information. Such
kind of routing is used for wireless networks in which a source sends a signal to the geographic location of the
destination instead of utilizing the network address. There are major two kinds of protocols involve in
geographic routing such as GSPR and GEAR [1]. The objective of this research is to examine the security issues
associated with the routing protocols. The key motivation behind this research is to evaluate and analyze the
routing protocols and examine the security attacks against the routing protocols. This paper will include
effective countermeasures that help readers to protect data from hackers and enhance the privacy of data
effectively. There are numerous sections that will cover in this report, for example, routing protocols analysis,
attacks against the routing protocols and countermeasures.
Analysis of routing protocols
Geographic routing
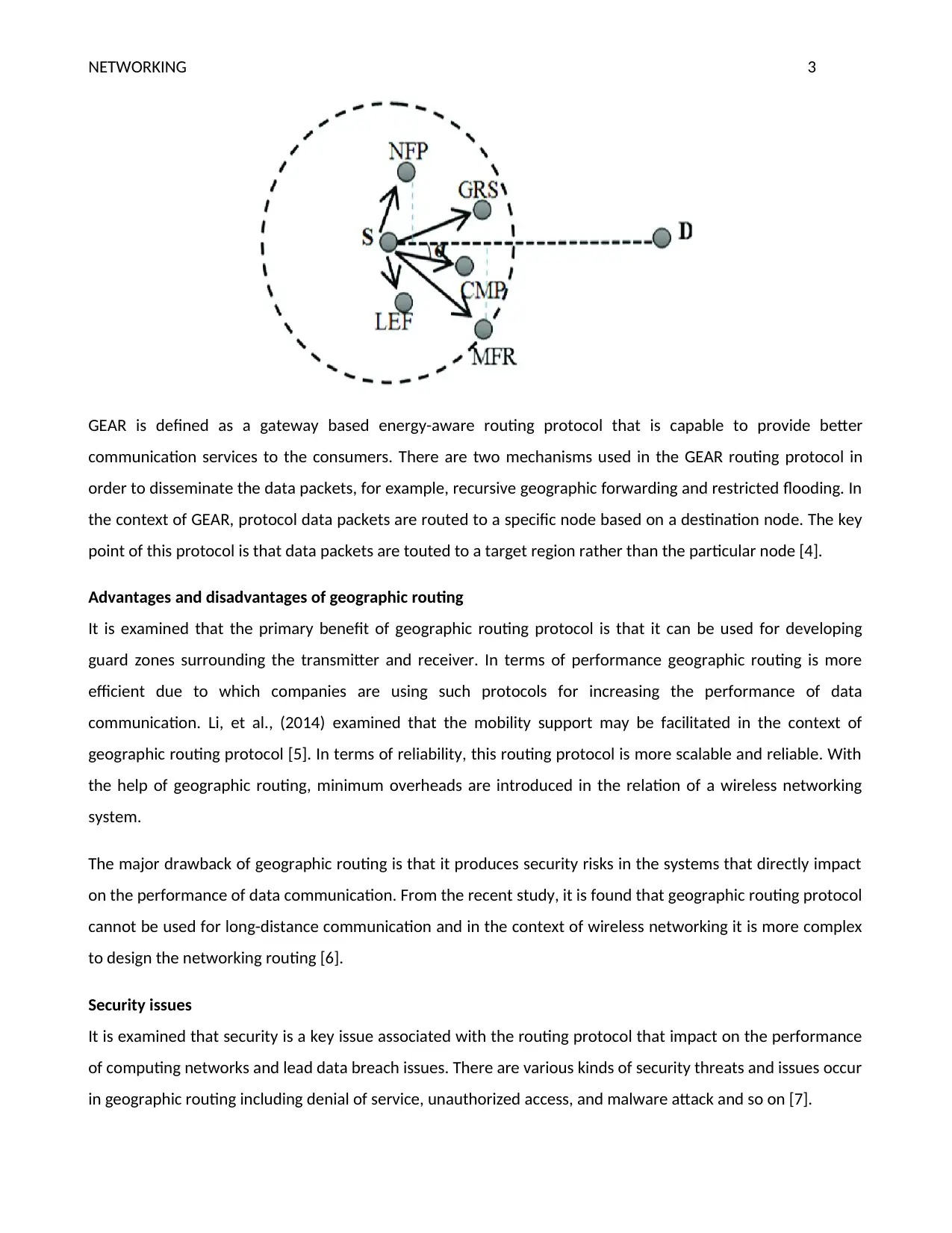
Geographic routing is the best type of protocol where each node known the location of its neighbors. The
source in this routing protocol inserts the destination located inside the data packet [2]. There are two
protocols include in the geographic routing, for example, GPSR and GEAR. In which greedy perimeter stateless
routing (GPSR) is an effective ad responsive protocol that is used for wireless network communication. There
are various classes of GPSR routing protocols such as sensor networks, rooftop networks, Ad-hoc networks, and
vehicular networks. Cai, et al., (2014) Li examined that GPSR routing protocol mainly forwards the perimeter
mode packet with the help of a planer graph traversal [3]. Such kind of routing protocol utilizes greedy
forwarding in order to transfer data packets to nodes which are always progressively closer to the destination.
Figure: Geographic routing protocol [2]
Introduction
Geographic routing is defined as a routing principle that relies on the geographic position information. Such
kind of routing is used for wireless networks in which a source sends a signal to the geographic location of the
destination instead of utilizing the network address. There are major two kinds of protocols involve in
geographic routing such as GSPR and GEAR [1]. The objective of this research is to examine the security issues
associated with the routing protocols. The key motivation behind this research is to evaluate and analyze the
routing protocols and examine the security attacks against the routing protocols. This paper will include
effective countermeasures that help readers to protect data from hackers and enhance the privacy of data
effectively. There are numerous sections that will cover in this report, for example, routing protocols analysis,
attacks against the routing protocols and countermeasures.
Analysis of routing protocols
Geographic routing
Geographic routing is the best type of protocol where each node known the location of its neighbors. The
source in this routing protocol inserts the destination located inside the data packet [2]. There are two
protocols include in the geographic routing, for example, GPSR and GEAR. In which greedy perimeter stateless
routing (GPSR) is an effective ad responsive protocol that is used for wireless network communication. There
are various classes of GPSR routing protocols such as sensor networks, rooftop networks, Ad-hoc networks, and
vehicular networks. Cai, et al., (2014) Li examined that GPSR routing protocol mainly forwards the perimeter
mode packet with the help of a planer graph traversal [3]. Such kind of routing protocol utilizes greedy
forwarding in order to transfer data packets to nodes which are always progressively closer to the destination.
Figure: Geographic routing protocol [2]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
NETWORKING 3
GEAR is defined as a gateway based energy-aware routing protocol that is capable to provide better
communication services to the consumers. There are two mechanisms used in the GEAR routing protocol in
order to disseminate the data packets, for example, recursive geographic forwarding and restricted flooding. In
the context of GEAR, protocol data packets are routed to a specific node based on a destination node. The key
point of this protocol is that data packets are touted to a target region rather than the particular node [4].
Advantages and disadvantages of geographic routing
It is examined that the primary benefit of geographic routing protocol is that it can be used for developing
guard zones surrounding the transmitter and receiver. In terms of performance geographic routing is more
efficient due to which companies are using such protocols for increasing the performance of data
communication. Li, et al., (2014) examined that the mobility support may be facilitated in the context of
geographic routing protocol [5]. In terms of reliability, this routing protocol is more scalable and reliable. With
the help of geographic routing, minimum overheads are introduced in the relation of a wireless networking
system.
The major drawback of geographic routing is that it produces security risks in the systems that directly impact
on the performance of data communication. From the recent study, it is found that geographic routing protocol
cannot be used for long-distance communication and in the context of wireless networking it is more complex
to design the networking routing [6].
Security issues
It is examined that security is a key issue associated with the routing protocol that impact on the performance
of computing networks and lead data breach issues. There are various kinds of security threats and issues occur
in geographic routing including denial of service, unauthorized access, and malware attack and so on [7].
GEAR is defined as a gateway based energy-aware routing protocol that is capable to provide better
communication services to the consumers. There are two mechanisms used in the GEAR routing protocol in
order to disseminate the data packets, for example, recursive geographic forwarding and restricted flooding. In
the context of GEAR, protocol data packets are routed to a specific node based on a destination node. The key
point of this protocol is that data packets are touted to a target region rather than the particular node [4].
Advantages and disadvantages of geographic routing
It is examined that the primary benefit of geographic routing protocol is that it can be used for developing
guard zones surrounding the transmitter and receiver. In terms of performance geographic routing is more
efficient due to which companies are using such protocols for increasing the performance of data
communication. Li, et al., (2014) examined that the mobility support may be facilitated in the context of
geographic routing protocol [5]. In terms of reliability, this routing protocol is more scalable and reliable. With
the help of geographic routing, minimum overheads are introduced in the relation of a wireless networking
system.
The major drawback of geographic routing is that it produces security risks in the systems that directly impact
on the performance of data communication. From the recent study, it is found that geographic routing protocol
cannot be used for long-distance communication and in the context of wireless networking it is more complex
to design the networking routing [6].
Security issues
It is examined that security is a key issue associated with the routing protocol that impact on the performance
of computing networks and lead data breach issues. There are various kinds of security threats and issues occur
in geographic routing including denial of service, unauthorized access, and malware attack and so on [7].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORKING 4
Attacks against the routing protocols
There are various security threats and attacks occur in the relation of routing protocols which are described
below:
DDOS attack
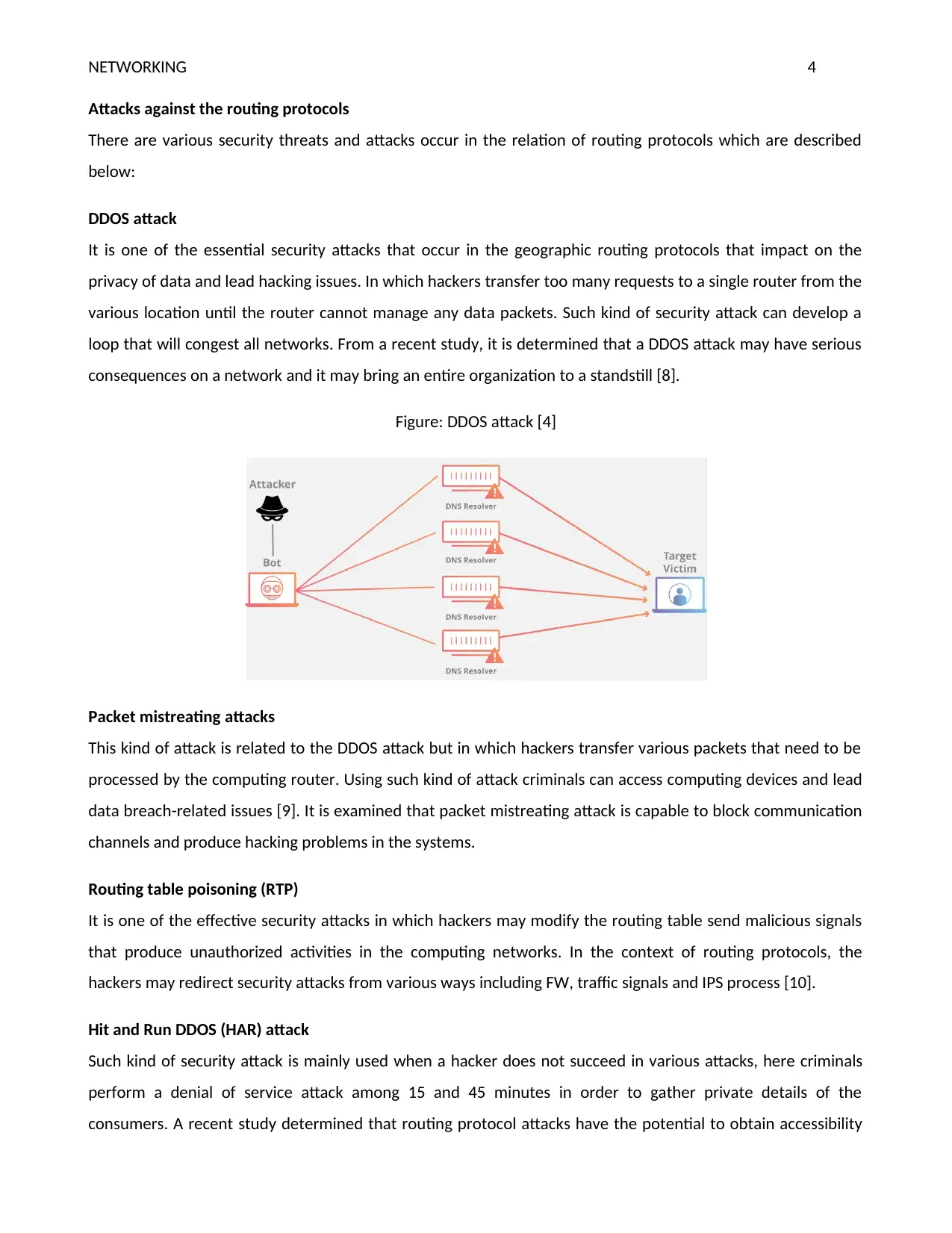
It is one of the essential security attacks that occur in the geographic routing protocols that impact on the
privacy of data and lead hacking issues. In which hackers transfer too many requests to a single router from the
various location until the router cannot manage any data packets. Such kind of security attack can develop a
loop that will congest all networks. From a recent study, it is determined that a DDOS attack may have serious
consequences on a network and it may bring an entire organization to a standstill [8].
Figure: DDOS attack [4]
Packet mistreating attacks
This kind of attack is related to the DDOS attack but in which hackers transfer various packets that need to be
processed by the computing router. Using such kind of attack criminals can access computing devices and lead
data breach-related issues [9]. It is examined that packet mistreating attack is capable to block communication
channels and produce hacking problems in the systems.
Routing table poisoning (RTP)
It is one of the effective security attacks in which hackers may modify the routing table send malicious signals
that produce unauthorized activities in the computing networks. In the context of routing protocols, the
hackers may redirect security attacks from various ways including FW, traffic signals and IPS process [10].
Hit and Run DDOS (HAR) attack
Such kind of security attack is mainly used when a hacker does not succeed in various attacks, here criminals
perform a denial of service attack among 15 and 45 minutes in order to gather private details of the
consumers. A recent study determined that routing protocol attacks have the potential to obtain accessibility
Attacks against the routing protocols
There are various security threats and attacks occur in the relation of routing protocols which are described
below:
DDOS attack
It is one of the essential security attacks that occur in the geographic routing protocols that impact on the
privacy of data and lead hacking issues. In which hackers transfer too many requests to a single router from the
various location until the router cannot manage any data packets. Such kind of security attack can develop a
loop that will congest all networks. From a recent study, it is determined that a DDOS attack may have serious
consequences on a network and it may bring an entire organization to a standstill [8].
Figure: DDOS attack [4]
Packet mistreating attacks
This kind of attack is related to the DDOS attack but in which hackers transfer various packets that need to be
processed by the computing router. Using such kind of attack criminals can access computing devices and lead
data breach-related issues [9]. It is examined that packet mistreating attack is capable to block communication
channels and produce hacking problems in the systems.
Routing table poisoning (RTP)
It is one of the effective security attacks in which hackers may modify the routing table send malicious signals
that produce unauthorized activities in the computing networks. In the context of routing protocols, the
hackers may redirect security attacks from various ways including FW, traffic signals and IPS process [10].
Hit and Run DDOS (HAR) attack
Such kind of security attack is mainly used when a hacker does not succeed in various attacks, here criminals
perform a denial of service attack among 15 and 45 minutes in order to gather private details of the
consumers. A recent study determined that routing protocol attacks have the potential to obtain accessibility

NETWORKING 5
of the networks and reduce the privacy of data effectively. Therefore, it is stated that companies should focus
on unauthorized access and lead security of data effectively [11]. All these are major attacks that occur in the
geographic routing protocols that need to be managed on a priority basis.
Countermeasures for addressing attacks
There are numerous techniques and approaches that can be used for addressing attacks related to routing
protocols which are described below:
Management plane best practices
It is argued that lack of security and unauthorized access both are major factors that lead to privacy-related
issues in the routing protocols. For handling security issues in routing protocols companies should enforce
password policy and implement role-based access control that has the potential to manage the authenticity of
data [12]. Moreover, companies can implement NTP in order to keep time on the computing network and fix IP
address which can handle access related issues. All these are major countermeasures that can be included in
the management plan and handle security threats in routing protocols.
Provide proper training and education
It is observed that many employees are not aware of the security attacks and threats due to which they use
third-party networks and perform data communication. Therefore, it is suggested that companies should
provide proper training to the employees and aware to use only secure networks and protocols while
developing a wireless communication system [13].
Develop and implement an encryption-based network
It is stated that the involvement of encryption is the best practice for handling data breach issues in the routing
protocols. Encryption provides a way where companies can perform data communication effectively and
convert the signals into a code that cannot be detected by the criminals [14]. Therefore, using encryption and
firewall tools companies can enhance the privacy of data and routing protocols. A firewall helps to detect
unwanted signals and lead the performance of wireless networks that helps in the enhancement of the
protocol's security.
Other countermeasures
It is reported that companies should use backup plans and reduce traffic signals that occurred in the systems by
which the level of security can be enhanced in routing protocols. ACL is the best practice that can be used to
filter traffic signals from the routing interfaces and the TCP intercept can be adopted to protect from SYN flood
attacks that occur in the wireless networks [14]. Moreover, companies should add ACL for blocking unwanted
of the networks and reduce the privacy of data effectively. Therefore, it is stated that companies should focus
on unauthorized access and lead security of data effectively [11]. All these are major attacks that occur in the
geographic routing protocols that need to be managed on a priority basis.
Countermeasures for addressing attacks
There are numerous techniques and approaches that can be used for addressing attacks related to routing
protocols which are described below:
Management plane best practices
It is argued that lack of security and unauthorized access both are major factors that lead to privacy-related
issues in the routing protocols. For handling security issues in routing protocols companies should enforce
password policy and implement role-based access control that has the potential to manage the authenticity of
data [12]. Moreover, companies can implement NTP in order to keep time on the computing network and fix IP
address which can handle access related issues. All these are major countermeasures that can be included in
the management plan and handle security threats in routing protocols.
Provide proper training and education
It is observed that many employees are not aware of the security attacks and threats due to which they use
third-party networks and perform data communication. Therefore, it is suggested that companies should
provide proper training to the employees and aware to use only secure networks and protocols while
developing a wireless communication system [13].
Develop and implement an encryption-based network
It is stated that the involvement of encryption is the best practice for handling data breach issues in the routing
protocols. Encryption provides a way where companies can perform data communication effectively and
convert the signals into a code that cannot be detected by the criminals [14]. Therefore, using encryption and
firewall tools companies can enhance the privacy of data and routing protocols. A firewall helps to detect
unwanted signals and lead the performance of wireless networks that helps in the enhancement of the
protocol's security.
Other countermeasures
It is reported that companies should use backup plans and reduce traffic signals that occurred in the systems by
which the level of security can be enhanced in routing protocols. ACL is the best practice that can be used to
filter traffic signals from the routing interfaces and the TCP intercept can be adopted to protect from SYN flood
attacks that occur in the wireless networks [14]. Moreover, companies should add ACL for blocking unwanted
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORKING 6
signals so routing protocols do not take the time to forward data packets. Malicious is a key attack that occurs
in the routing protocols that impact on the private data and increase data breach problems. Therefore,
companies should design and implement an IPS system in order to block malicious attacks.
Conclusion
From this research, it can be concluded that geographic routing protocol can be used in the development of
wireless communication network but it is significant to address security attacks. This report provided depth
examination and analysis of routing protocols and reviewed the security issues related to geographic routing. It
is found that the geographic routing protocol has larger scalability and reliability by which companies can
develop an effective wireless network. It is true that security issues affect the performance of routing protocols
and lead data breach issues. DDOS is a common security attack that impacts on the privacy of data and reduces
the security of routing protocols by transferring traffic signals. Therefore, it is recommended that companies
should include firewalls, encryption and ACL systems in order to block unwanted and malicious signals
effectively.
signals so routing protocols do not take the time to forward data packets. Malicious is a key attack that occurs
in the routing protocols that impact on the private data and increase data breach problems. Therefore,
companies should design and implement an IPS system in order to block malicious attacks.
Conclusion
From this research, it can be concluded that geographic routing protocol can be used in the development of
wireless communication network but it is significant to address security attacks. This report provided depth
examination and analysis of routing protocols and reviewed the security issues related to geographic routing. It
is found that the geographic routing protocol has larger scalability and reliability by which companies can
develop an effective wireless network. It is true that security issues affect the performance of routing protocols
and lead data breach issues. DDOS is a common security attack that impacts on the privacy of data and reduces
the security of routing protocols by transferring traffic signals. Therefore, it is recommended that companies
should include firewalls, encryption and ACL systems in order to block unwanted and malicious signals
effectively.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING 7
References
[1]. V.N., Soares, J.J. Rodrigues and, F., Farahmand, “GeoSpray: A geographic routing protocol for vehicular
delay-tolerant networks,” Information Fusion, vol. 15, no. 5, pp.102-113, 2014.
[2]. R.W., Coutinho, A., Boukerche, L.F. Vieira and, A.A., Loureiro, “GEDAR: geographic and opportunistic
routing protocol with depth adjustment for mobile underwater sensor networks,” In 2014 IEEE
International Conference on Communications (ICC), vol. 12, no. 6, pp. 251-256, 2014.
[3]. X., Cai, Y., He, C., Zhao, L. Zhu and, C., Li, “LSGO: link state aware geographic opportunistic routing
protocol for VANETs,” EURASIP Journal on wireless communications and networking, vol. 2014, no. 1,
p.96, 2014.
[4]. X., Jin, R., Zhang, J. Sun and, Y., Zhang, “TIGHT: A geographic routing protocol for cognitive radio
mobile ad hoc networks,” IEEE Transactions on Wireless Communications, vol. 13, no. 8, pp.4670-4681,
2014.
[5]. C., Li, C., Zhao, L., Zhu, H. Lin and, J., Li, “Geographic routing protocol for vehicular ad hoc networks in
city scenarios: a proposal and analysis,” International Journal of Communication Systems, vol. 27, no.
12, pp.4126-4143, 2014.
[6]. J.M., Chang, C.F., Lai, H.C. Chao and, R., Zhu, “An energy-efficient geographic routing protocol design in
a vehicular ad-hoc network," Computing, vol. 96, no. 2, pp.119-131, 2014.
[7]. A.K. Jain and, V., Tokekar, “Mitigating the effects of Black hole attacks on AODV routing protocol in
mobile ad hoc networks,” In 2015 International Conference on Pervasive Computing (ICPC), vol. 12, no.
6, pp. 1-6, 2015.
[8]. H., Moudni, M., Er-rouidi, H. Mouncif and, B., El Hadadi, “Performance analysis of AODV routing
protocol in MANET under the influence of routing attacks,” In 2016 International Conference on
Electrical and Information Technologies (ICEIT), vol. 12, no. 6, pp. 536-542.
[9]. K.V. Arya and, S.S., Rajput, “Securing AODV routing protocol in MANET using NMAC with HBKS
Technique,” In 2014 International Conference on Signal Processing and Integrated Networks (SPIN) , vol.
12, no. 6, pp. 281-285, 2014.
[10]. S.M., Zin, N.B., Anuar, M.L.M. Kiah and, A.S.K., Pathan, “Routing protocol design for secure
WSN: Review and open research issues,” Journal of Network and Computer Applications, vol. 41, no.
12, pp.517-530, 2014.
[11]. P. Tyagi and, D., Dembla, “Performance analysis and implementation of proposed mechanism
for detection and prevention of security attacks in routing protocols of vehicular ad-hoc network
(VANET),” Egyptian informatics journal, vol. 18, no. 2, pp.133-139, 2017.
References
[1]. V.N., Soares, J.J. Rodrigues and, F., Farahmand, “GeoSpray: A geographic routing protocol for vehicular
delay-tolerant networks,” Information Fusion, vol. 15, no. 5, pp.102-113, 2014.
[2]. R.W., Coutinho, A., Boukerche, L.F. Vieira and, A.A., Loureiro, “GEDAR: geographic and opportunistic
routing protocol with depth adjustment for mobile underwater sensor networks,” In 2014 IEEE
International Conference on Communications (ICC), vol. 12, no. 6, pp. 251-256, 2014.
[3]. X., Cai, Y., He, C., Zhao, L. Zhu and, C., Li, “LSGO: link state aware geographic opportunistic routing
protocol for VANETs,” EURASIP Journal on wireless communications and networking, vol. 2014, no. 1,
p.96, 2014.
[4]. X., Jin, R., Zhang, J. Sun and, Y., Zhang, “TIGHT: A geographic routing protocol for cognitive radio
mobile ad hoc networks,” IEEE Transactions on Wireless Communications, vol. 13, no. 8, pp.4670-4681,
2014.
[5]. C., Li, C., Zhao, L., Zhu, H. Lin and, J., Li, “Geographic routing protocol for vehicular ad hoc networks in
city scenarios: a proposal and analysis,” International Journal of Communication Systems, vol. 27, no.
12, pp.4126-4143, 2014.
[6]. J.M., Chang, C.F., Lai, H.C. Chao and, R., Zhu, “An energy-efficient geographic routing protocol design in
a vehicular ad-hoc network," Computing, vol. 96, no. 2, pp.119-131, 2014.
[7]. A.K. Jain and, V., Tokekar, “Mitigating the effects of Black hole attacks on AODV routing protocol in
mobile ad hoc networks,” In 2015 International Conference on Pervasive Computing (ICPC), vol. 12, no.
6, pp. 1-6, 2015.
[8]. H., Moudni, M., Er-rouidi, H. Mouncif and, B., El Hadadi, “Performance analysis of AODV routing
protocol in MANET under the influence of routing attacks,” In 2016 International Conference on
Electrical and Information Technologies (ICEIT), vol. 12, no. 6, pp. 536-542.
[9]. K.V. Arya and, S.S., Rajput, “Securing AODV routing protocol in MANET using NMAC with HBKS
Technique,” In 2014 International Conference on Signal Processing and Integrated Networks (SPIN) , vol.
12, no. 6, pp. 281-285, 2014.
[10]. S.M., Zin, N.B., Anuar, M.L.M. Kiah and, A.S.K., Pathan, “Routing protocol design for secure
WSN: Review and open research issues,” Journal of Network and Computer Applications, vol. 41, no.
12, pp.517-530, 2014.
[11]. P. Tyagi and, D., Dembla, “Performance analysis and implementation of proposed mechanism
for detection and prevention of security attacks in routing protocols of vehicular ad-hoc network
(VANET),” Egyptian informatics journal, vol. 18, no. 2, pp.133-139, 2017.

NETWORKING 8
[12]. E.E. Khin and, T., Phyu, “Impact of black hole attack on AODV routing protocol,” International
Journal of Information Technology, Modeling and Computing (IJITMC), vol. 2, no. 2, pp.9-17, 2014.
[13]. P., Nayak, V. Bhavani and, B., Lavanya, “Impact of black hole and sink hole attacks on routing
protocols for WSN,” International Journal of Computer Applications, vol. 116, no. 4, pp. 12-18, 2015.
[14]. A.A., Chavan, D.S. Kurule and, P.U., Dere, “Performance analysis of AODV and DSDV routing
protocol in MANET and modifications in AODV against black hole attack,” Procedia Computer
Science, vol. 79, no. 6, pp.835-844, 2016.
[12]. E.E. Khin and, T., Phyu, “Impact of black hole attack on AODV routing protocol,” International
Journal of Information Technology, Modeling and Computing (IJITMC), vol. 2, no. 2, pp.9-17, 2014.
[13]. P., Nayak, V. Bhavani and, B., Lavanya, “Impact of black hole and sink hole attacks on routing
protocols for WSN,” International Journal of Computer Applications, vol. 116, no. 4, pp. 12-18, 2015.
[14]. A.A., Chavan, D.S. Kurule and, P.U., Dere, “Performance analysis of AODV and DSDV routing
protocol in MANET and modifications in AODV against black hole attack,” Procedia Computer
Science, vol. 79, no. 6, pp.835-844, 2016.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





