Wireless Networking: Comparative Analysis, Configuration and Ping Test
VerifiedAdded on 2023/06/04
|10
|1409
|156
Report
AI Summary
This report provides a comparative analysis of Near Field Communication (NFC) and Radio Frequency Identification (RFID) technologies, highlighting their applications in network efficiency and security. It details the configuration of a wireless network using two generic wireless access points, secured with WPA2-PSK encryption and AES, and demonstrates connectivity testing using the ping command. The report further examines the impact of channel changes on access points and the importance of correct passphrase input for network access. It includes screenshots illustrating the configuration processes and test results, offering a practical understanding of wireless network setup and troubleshooting. Desklib offers more solved assignments and resources for students.

Running head: WIRELESS NETWORKING
Wireless Networking
Name of the Student
Name of the University
Author’s Note
Wireless Networking
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORKING
Part A: Comparative Analysis
Q 1 Answer:
The Near filed communication and the radio frequency identification can be used for
different purpose in the network and helps in increasing the efficiency of the workplace of the
organization. RFID technology is mainly applied for maintaining a track package and
inventory and it enables a control on the current business process. The radio waves are used
for communication and NFC has evolved from the RFID and used for enabling secure
communication between the sender and the receiver. The operating range of NFC is 4 inches
and can be used for one or two way communication. NFC smart tags are used in the smart
phone for short distance communication. In case of RFID, it consists of a memory chip for
storing the data and an antenna and for getting the data from the memory chip a RFIS reader
is needed. The RFID tags are used in wide range of application such as in retail products for
tracking the inventory. It also finds its application in the toll for identification of the car and
create bills. It can operate from a larger distance than the NFC. It is a one way
communication and the data in the memory chip flows using the RFID reader.
There are two different types of RFIS tags such as passive and active tag where the
active tag is powered using their own power source and has its ability to broadcast the
information to the reader for a distance of 100m. It is an ideal choice for the industrial
application and management of the assets and improvement of the logistics. The passive
RFID have no source of power and they are powered when an electromagnetic wave is
transmitted from the reader. It can operate at a distance of 25 meter since the radio waves are
strong enough to provide power to the RFID tags.
WIRELESS NETWORKING
Part A: Comparative Analysis
Q 1 Answer:
The Near filed communication and the radio frequency identification can be used for
different purpose in the network and helps in increasing the efficiency of the workplace of the
organization. RFID technology is mainly applied for maintaining a track package and
inventory and it enables a control on the current business process. The radio waves are used
for communication and NFC has evolved from the RFID and used for enabling secure
communication between the sender and the receiver. The operating range of NFC is 4 inches
and can be used for one or two way communication. NFC smart tags are used in the smart
phone for short distance communication. In case of RFID, it consists of a memory chip for
storing the data and an antenna and for getting the data from the memory chip a RFIS reader
is needed. The RFID tags are used in wide range of application such as in retail products for
tracking the inventory. It also finds its application in the toll for identification of the car and
create bills. It can operate from a larger distance than the NFC. It is a one way
communication and the data in the memory chip flows using the RFID reader.
There are two different types of RFIS tags such as passive and active tag where the
active tag is powered using their own power source and has its ability to broadcast the
information to the reader for a distance of 100m. It is an ideal choice for the industrial
application and management of the assets and improvement of the logistics. The passive
RFID have no source of power and they are powered when an electromagnetic wave is
transmitted from the reader. It can operate at a distance of 25 meter since the radio waves are
strong enough to provide power to the RFID tags.
2
WIRELESS NETWORKING
The NFC and the RFID operates at the same frequency and have the similar protocol
and standards. The advantage of the NFC is that it operates in short range and thus become a
secure choice for communicating the data packets. The risk of man in the middle attack is
eliminated for the NFC and it uses peer to peer communication such that the NFC device can
act both as a reader or tag. Due to the security options provided by the NFC it becomes an
ideal choice for using it for contact less payment. It can also be used for sharing of
information and small files between the two NFC enabled devices.
Q 2 Answer:
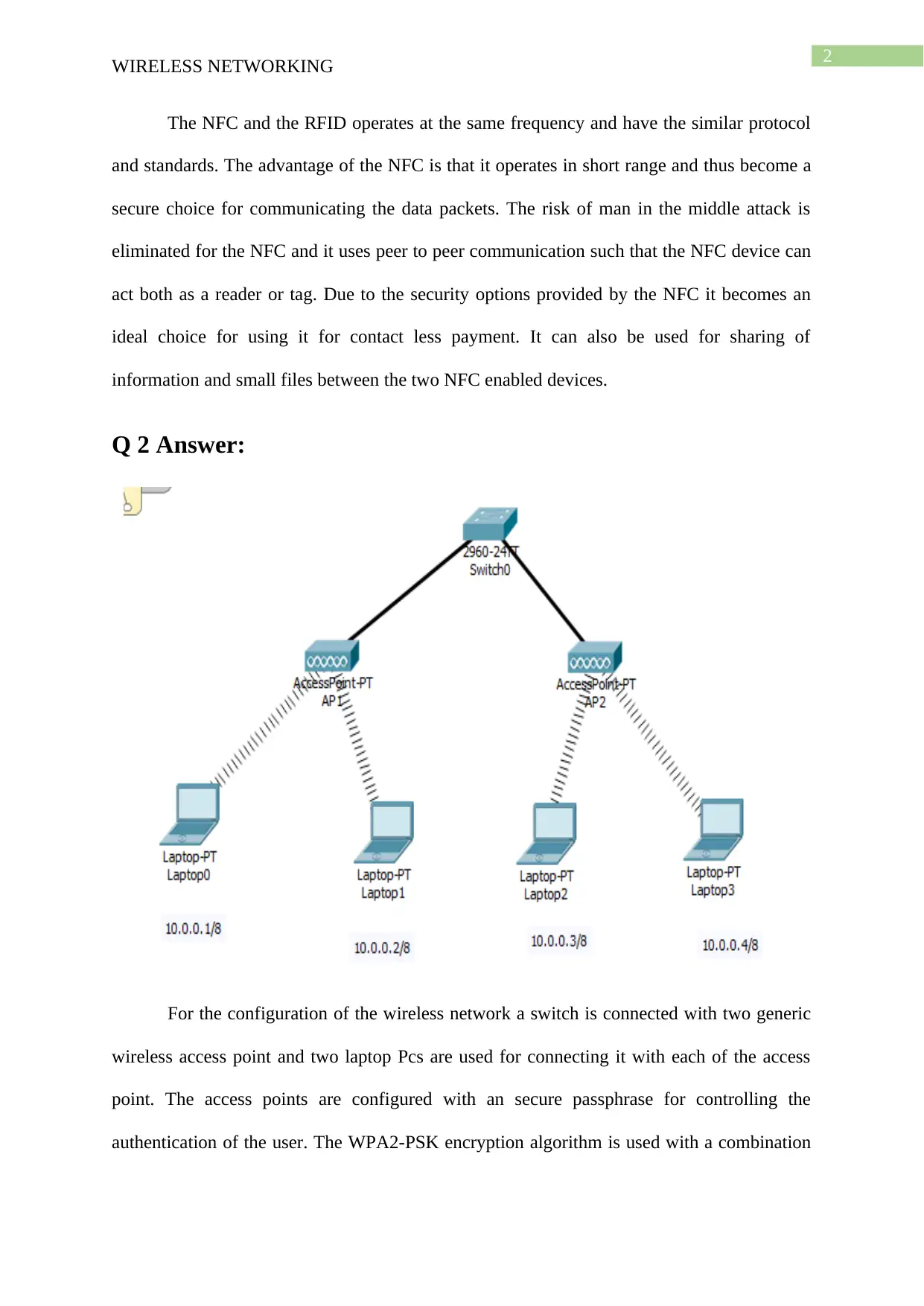
For the configuration of the wireless network a switch is connected with two generic
wireless access point and two laptop Pcs are used for connecting it with each of the access
point. The access points are configured with an secure passphrase for controlling the
authentication of the user. The WPA2-PSK encryption algorithm is used with a combination
WIRELESS NETWORKING
The NFC and the RFID operates at the same frequency and have the similar protocol
and standards. The advantage of the NFC is that it operates in short range and thus become a
secure choice for communicating the data packets. The risk of man in the middle attack is
eliminated for the NFC and it uses peer to peer communication such that the NFC device can
act both as a reader or tag. Due to the security options provided by the NFC it becomes an
ideal choice for using it for contact less payment. It can also be used for sharing of
information and small files between the two NFC enabled devices.
Q 2 Answer:
For the configuration of the wireless network a switch is connected with two generic
wireless access point and two laptop Pcs are used for connecting it with each of the access
point. The access points are configured with an secure passphrase for controlling the
authentication of the user. The WPA2-PSK encryption algorithm is used with a combination
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
WIRELESS NETWORKING
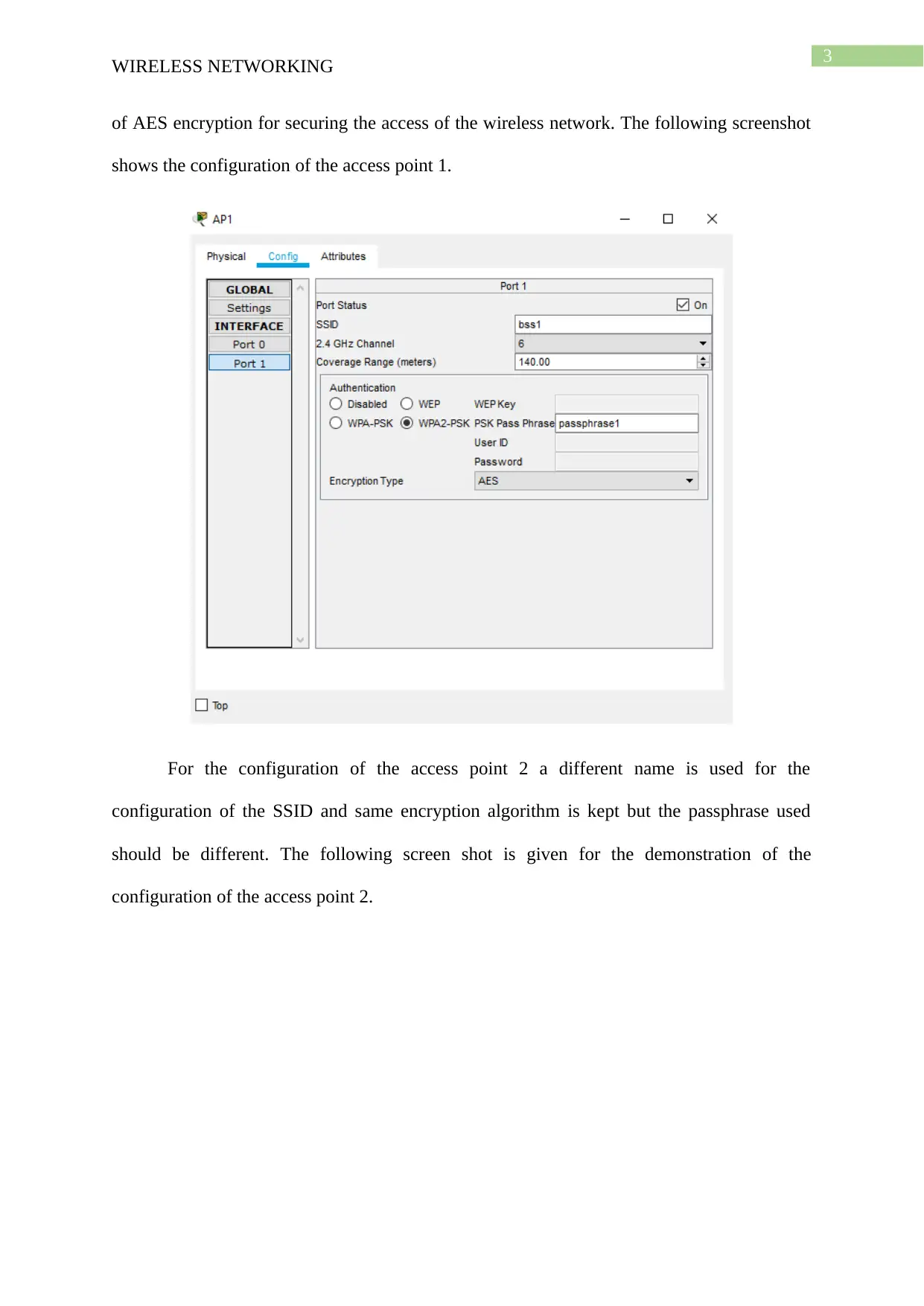
of AES encryption for securing the access of the wireless network. The following screenshot
shows the configuration of the access point 1.
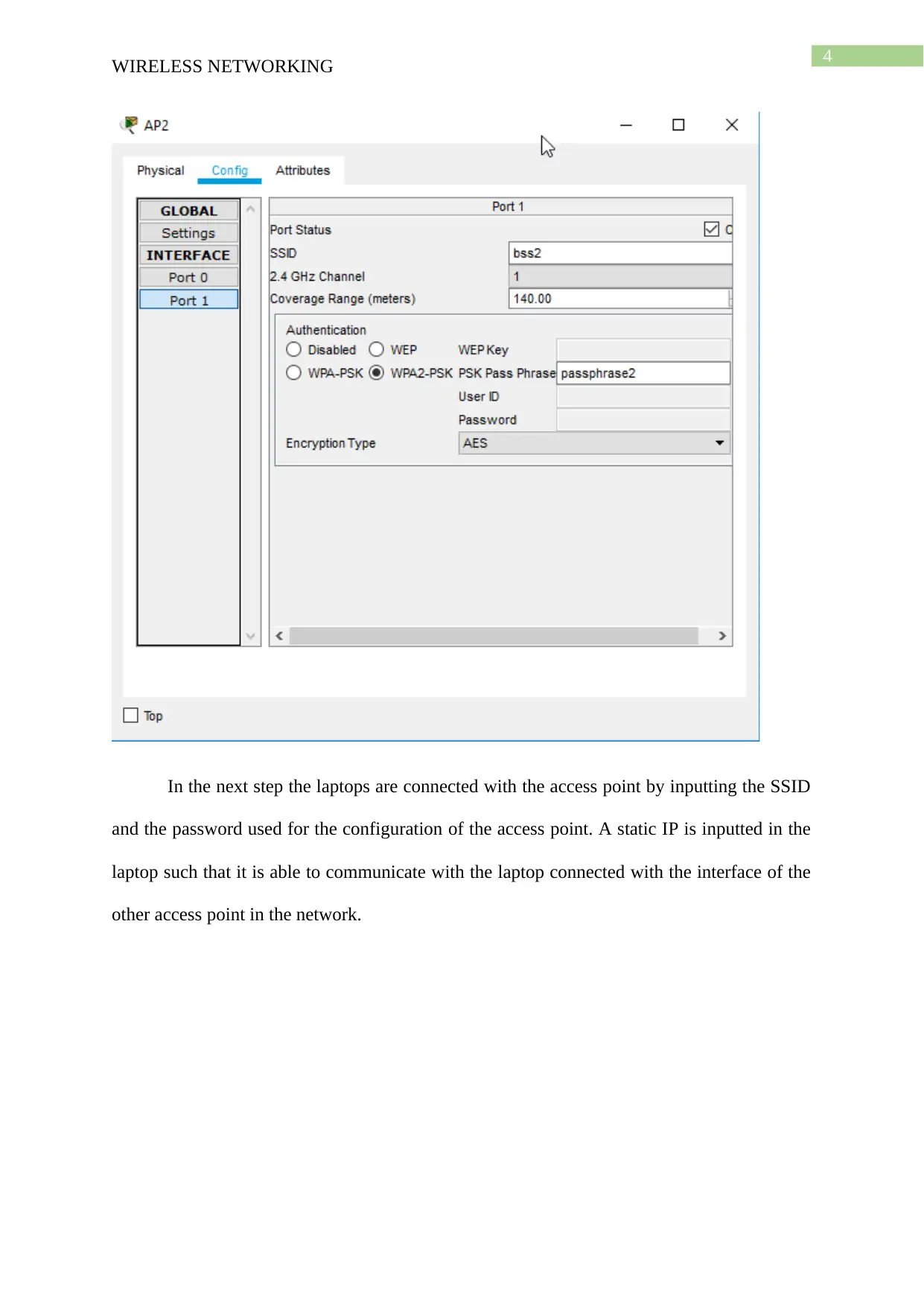
For the configuration of the access point 2 a different name is used for the
configuration of the SSID and same encryption algorithm is kept but the passphrase used
should be different. The following screen shot is given for the demonstration of the
configuration of the access point 2.
WIRELESS NETWORKING
of AES encryption for securing the access of the wireless network. The following screenshot
shows the configuration of the access point 1.
For the configuration of the access point 2 a different name is used for the
configuration of the SSID and same encryption algorithm is kept but the passphrase used
should be different. The following screen shot is given for the demonstration of the
configuration of the access point 2.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
WIRELESS NETWORKING
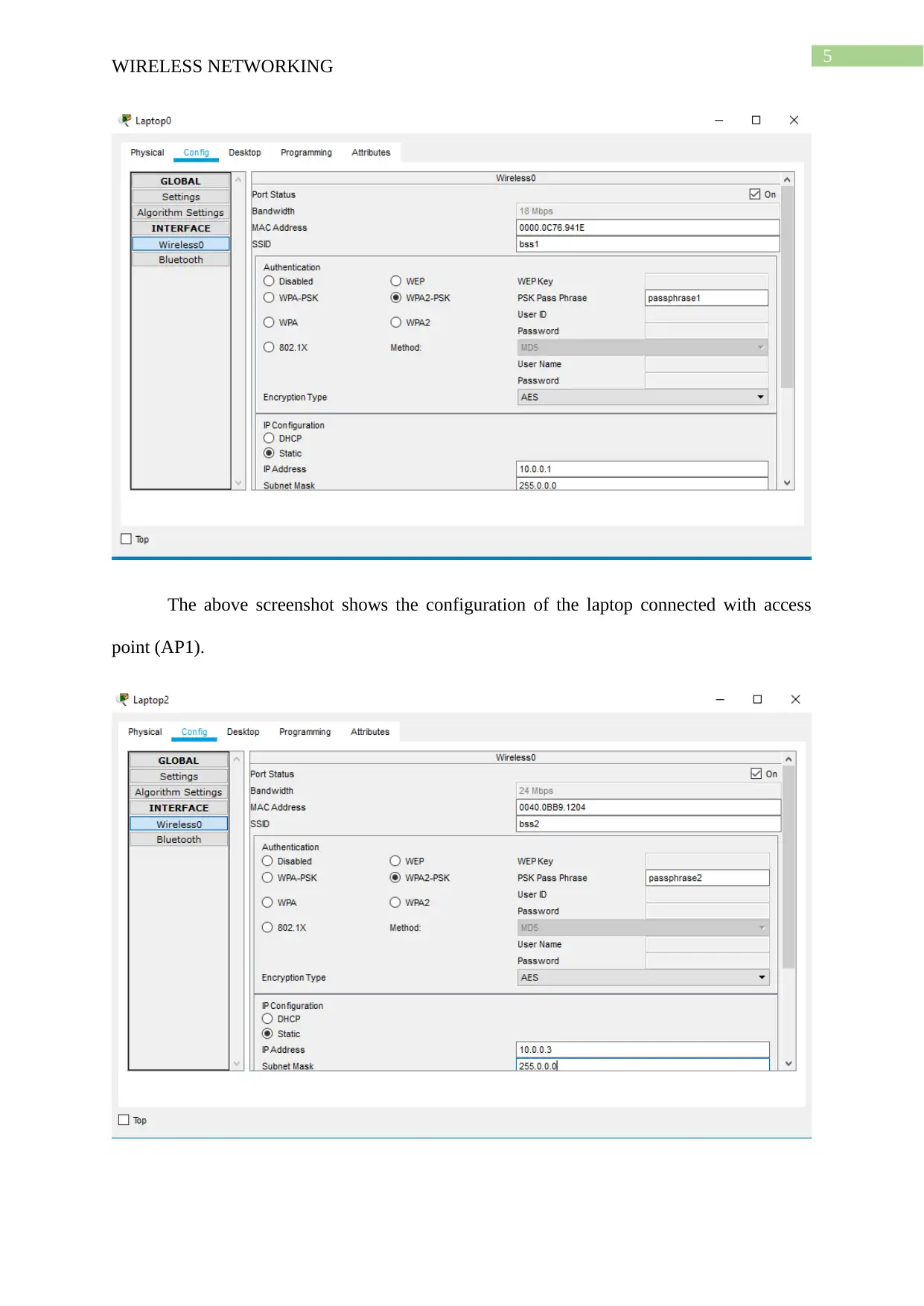
In the next step the laptops are connected with the access point by inputting the SSID
and the password used for the configuration of the access point. A static IP is inputted in the
laptop such that it is able to communicate with the laptop connected with the interface of the
other access point in the network.
WIRELESS NETWORKING
In the next step the laptops are connected with the access point by inputting the SSID
and the password used for the configuration of the access point. A static IP is inputted in the
laptop such that it is able to communicate with the laptop connected with the interface of the
other access point in the network.
5
WIRELESS NETWORKING
The above screenshot shows the configuration of the laptop connected with access
point (AP1).
WIRELESS NETWORKING
The above screenshot shows the configuration of the laptop connected with access
point (AP1).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRELESS NETWORKING
The above screen shot shows the configuration of the laptop connected with the
second access point (AP2).
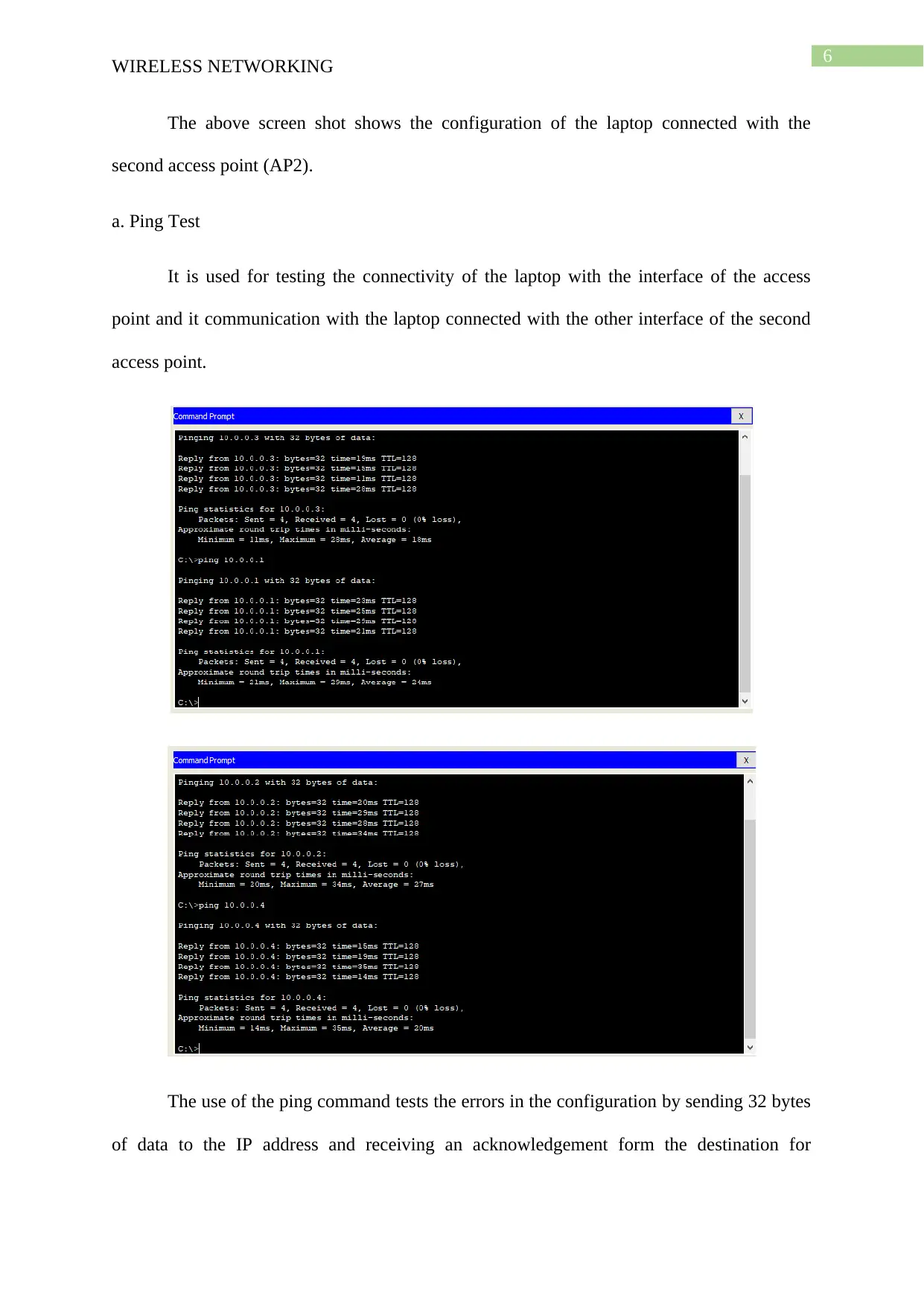
a. Ping Test
It is used for testing the connectivity of the laptop with the interface of the access
point and it communication with the laptop connected with the other interface of the second
access point.
The use of the ping command tests the errors in the configuration by sending 32 bytes
of data to the IP address and receiving an acknowledgement form the destination for
WIRELESS NETWORKING
The above screen shot shows the configuration of the laptop connected with the
second access point (AP2).
a. Ping Test
It is used for testing the connectivity of the laptop with the interface of the access
point and it communication with the laptop connected with the other interface of the second
access point.
The use of the ping command tests the errors in the configuration by sending 32 bytes
of data to the IP address and receiving an acknowledgement form the destination for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
WIRELESS NETWORKING
confirming that the connection is successfully established. For performing the test the laptop
1 is opened and from the desktop the command prompt is opened for running the test. The
command ping <IP ADDRESS>, where the IP address of the destination is given to check the
connection between the source and the destination address. For performing the ping test the
laptop needs to be connected with the access point using the proper SSID and password and it
should also be configured with an IP address of the same class and subnet. The failure of
configuration of the laptop with the proper credentials can cause error and ping failure.
b. If there is a change in the channel for the access point no difference is noted and the
following screenshot shows the running of a continuous ping and changing the channel of the
access point 2 there is no loss of packets during the change occurs. The response time have
increased from 17 to 51 ms during the change but it has become stable from the next ping.
The use of the same channel for both the access point can cause interference and
degrade the quality of the signal emitted from the wireless access point.
c. When the passphrase does not matches with the wireless access point the laptop is not
allowed to connect with the access point for sending and receiving data packets In order to
WIRELESS NETWORKING
confirming that the connection is successfully established. For performing the test the laptop
1 is opened and from the desktop the command prompt is opened for running the test. The
command ping <IP ADDRESS>, where the IP address of the destination is given to check the
connection between the source and the destination address. For performing the ping test the
laptop needs to be connected with the access point using the proper SSID and password and it
should also be configured with an IP address of the same class and subnet. The failure of
configuration of the laptop with the proper credentials can cause error and ping failure.
b. If there is a change in the channel for the access point no difference is noted and the
following screenshot shows the running of a continuous ping and changing the channel of the
access point 2 there is no loss of packets during the change occurs. The response time have
increased from 17 to 51 ms during the change but it has become stable from the next ping.
The use of the same channel for both the access point can cause interference and
degrade the quality of the signal emitted from the wireless access point.
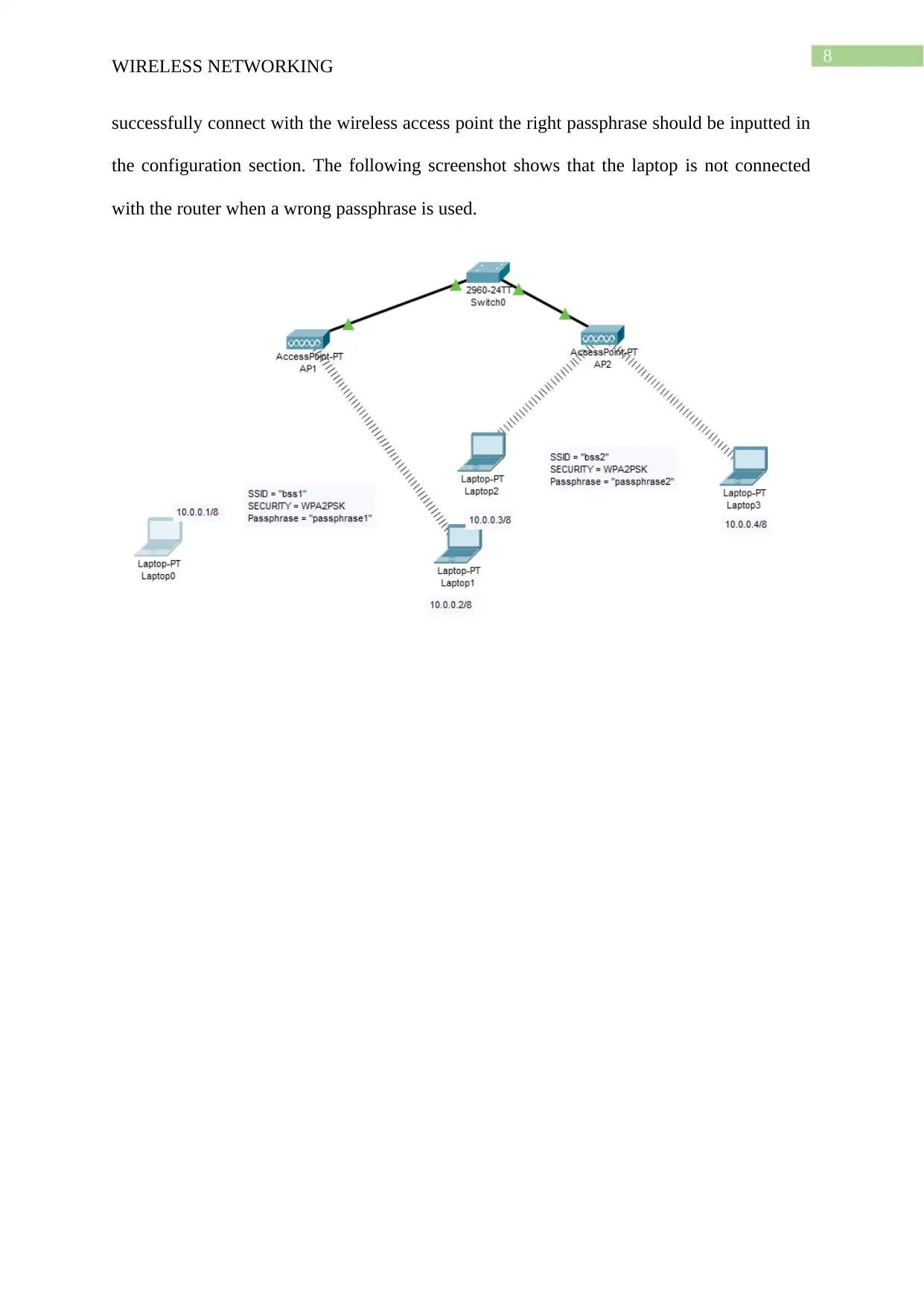
c. When the passphrase does not matches with the wireless access point the laptop is not
allowed to connect with the access point for sending and receiving data packets In order to
8
WIRELESS NETWORKING
successfully connect with the wireless access point the right passphrase should be inputted in
the configuration section. The following screenshot shows that the laptop is not connected
with the router when a wrong passphrase is used.
WIRELESS NETWORKING
successfully connect with the wireless access point the right passphrase should be inputted in
the configuration section. The following screenshot shows that the laptop is not connected
with the router when a wrong passphrase is used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
WIRELESS NETWORKING
Bibliography
Chew, C. B., Mahinderjit-Singh, M., Wei, K. C., Sheng, T. W., Husin, M. H., & Malim, N.
H. A. H. (2015). Sensors-enabled smart attendance systems using NFC and RFID
technologies. Int. J. New Comput. Archit. Appl, 5, 19-29.
Orozco, J., Chavira, G., Castro, I., Bolaños, J. F., Sánchez, R. A., & Cantú, J. F. (2014).
Towards NFC and RFID Combination to Automatic Services. International Journal
of Engineering, 4(8), 8269.
Park, C. W., Ahn, J. H., & Lee, T. J. (2017). Fast object identification with mode switching
for coexistence of NFC and RFID. Transactions on Emerging Telecommunications
Technologies, 28(2), e2939.
Prodanoff, Z. G., Jones, E. L., Chi, H., Elfayoumy, S., & Cummings, C. (2016). Survey of
Security Challenges in NFC and RFID for E-Health Applications. International
Journal of E-Health and Medical Communications (IJEHMC), 7(2), 1-13.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, August). Study on effective
pattern of magnetic sheet attached on NFC antenna. In Radio-Frequency Integration
Technology (RFIT), 2015 IEEE International Symposium on (pp. 208-210). IEEE.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, November). A study on the
effective pattern of magnetic sheet considering their characteristics attached on NFC
antenna. In Antennas and Propagation (ISAP), 2015 International Symposium (pp. 1-
4). IEEE.
WIRELESS NETWORKING
Bibliography
Chew, C. B., Mahinderjit-Singh, M., Wei, K. C., Sheng, T. W., Husin, M. H., & Malim, N.
H. A. H. (2015). Sensors-enabled smart attendance systems using NFC and RFID
technologies. Int. J. New Comput. Archit. Appl, 5, 19-29.
Orozco, J., Chavira, G., Castro, I., Bolaños, J. F., Sánchez, R. A., & Cantú, J. F. (2014).
Towards NFC and RFID Combination to Automatic Services. International Journal
of Engineering, 4(8), 8269.
Park, C. W., Ahn, J. H., & Lee, T. J. (2017). Fast object identification with mode switching
for coexistence of NFC and RFID. Transactions on Emerging Telecommunications
Technologies, 28(2), e2939.
Prodanoff, Z. G., Jones, E. L., Chi, H., Elfayoumy, S., & Cummings, C. (2016). Survey of
Security Challenges in NFC and RFID for E-Health Applications. International
Journal of E-Health and Medical Communications (IJEHMC), 7(2), 1-13.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, August). Study on effective
pattern of magnetic sheet attached on NFC antenna. In Radio-Frequency Integration
Technology (RFIT), 2015 IEEE International Symposium on (pp. 208-210). IEEE.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, November). A study on the
effective pattern of magnetic sheet considering their characteristics attached on NFC
antenna. In Antennas and Propagation (ISAP), 2015 International Symposium (pp. 1-
4). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





