Wireless Networking Assignment: WiMAX, WPAN, and Energy Harvesting
VerifiedAdded on 2020/04/07
|9
|1464
|252
Homework Assignment
AI Summary
This assignment delves into various aspects of wireless networking, commencing with a comparative analysis of WiMAX data encryption standards, including 3DES, RSA, and AES, highlighting their block sizes, key sizes, cipher types, and security levels. It then explores WPAN technologies, focusing on Bluetooth and Z-Wave, discussing their applications, and critical security issues such as radio jamming, platform security weaknesses, and device hacking. The assignment further examines energy harvesting in wireless sensor networks (WSNs), emphasizing its significance for sustaining WSNs and the importance of evaluating energy sources for future wireless communication standards. Finally, it discusses digital cellular handsets, outlining the benefits of their use for Telestra, such as improved business productivity, enhanced customer experience, and efficient system updates. The assignment provides references to support its findings.

Running head: WIRELESS NETWORKING 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORKING 2
Question 1
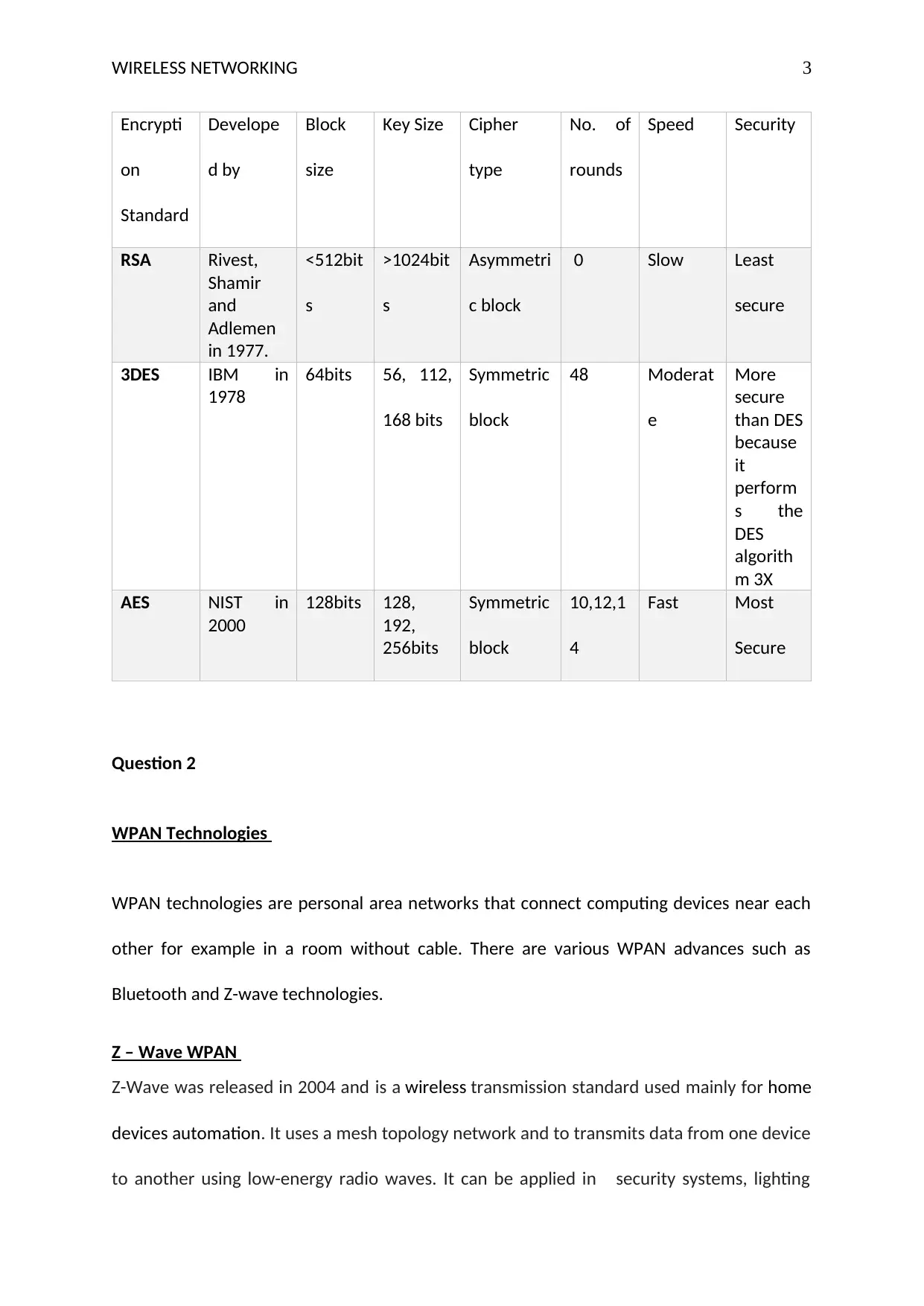
Similarities and differences between WiMax networks data encryption standards
WiMax is an emerging wireless broadband technology established on IEEE 802.16 standard
that serves both fixed and mobile networks as an alternative for cable and DSL (Alzaabi,
Ranjeeth, Alukaidey, & Dr Salman, 2013). WiMAX technology infrastructure is usually set up
with base stations mounted by service providers to install the technology; and receivers,
mounted by clients to receive wireless signals. Like any other wireless standard, WiMAX
encrypts data transmission by deploying several encryption standards including triple 3DES,
an improvement of Data Encryption Standard (DES), Rivest Shamir Adlemen (RSA) and
Advanced Encryption Standard (AES). RSA was developed in 1977, 3DES in 1978 while AES
was developed in 2000. RSA is a public key algorithm because it uses two keys pairs to
encrypt and decrypt the message hence it uses an asymmetric block cipher. Both 3DES and
AES use symmetric block cipher. In terms of power consumption, RSA consumes a lot of
power while AES and 3DES are low on power consumption. AES is more secure, followed by
3DES and RSA has low security. Table1 below summarizes the differences and some
similarities between the three encryption algorithms (Verma, Guha, & Mishra, 2016).
Question 1
Similarities and differences between WiMax networks data encryption standards
WiMax is an emerging wireless broadband technology established on IEEE 802.16 standard
that serves both fixed and mobile networks as an alternative for cable and DSL (Alzaabi,
Ranjeeth, Alukaidey, & Dr Salman, 2013). WiMAX technology infrastructure is usually set up
with base stations mounted by service providers to install the technology; and receivers,
mounted by clients to receive wireless signals. Like any other wireless standard, WiMAX
encrypts data transmission by deploying several encryption standards including triple 3DES,
an improvement of Data Encryption Standard (DES), Rivest Shamir Adlemen (RSA) and
Advanced Encryption Standard (AES). RSA was developed in 1977, 3DES in 1978 while AES
was developed in 2000. RSA is a public key algorithm because it uses two keys pairs to
encrypt and decrypt the message hence it uses an asymmetric block cipher. Both 3DES and
AES use symmetric block cipher. In terms of power consumption, RSA consumes a lot of
power while AES and 3DES are low on power consumption. AES is more secure, followed by
3DES and RSA has low security. Table1 below summarizes the differences and some
similarities between the three encryption algorithms (Verma, Guha, & Mishra, 2016).
WIRELESS NETWORKING 3
Encrypti
on
Standard
Develope
d by
Block
size
Key Size Cipher
type
No. of
rounds
Speed Security
RSA Rivest,
Shamir
and
Adlemen
in 1977.
<512bit
s
>1024bit
s
Asymmetri
c block
0 Slow Least
secure
3DES IBM in
1978
64bits 56, 112,
168 bits
Symmetric
block
48 Moderat
e
More
secure
than DES
because
it
perform
s the
DES
algorith
m 3X
AES NIST in
2000
128bits 128,
192,
256bits
Symmetric
block
10,12,1
4
Fast Most
Secure
Question 2
WPAN Technologies
WPAN technologies are personal area networks that connect computing devices near each
other for example in a room without cable. There are various WPAN advances such as
Bluetooth and Z-wave technologies.
Z – Wave WPAN
Z-Wave was released in 2004 and is a wireless transmission standard used mainly for home
devices automation. It uses a mesh topology network and to transmits data from one device
to another using low-energy radio waves. It can be applied in security systems, lighting
Encrypti
on
Standard
Develope
d by
Block
size
Key Size Cipher
type
No. of
rounds
Speed Security
RSA Rivest,
Shamir
and
Adlemen
in 1977.
<512bit
s
>1024bit
s
Asymmetri
c block
0 Slow Least
secure
3DES IBM in
1978
64bits 56, 112,
168 bits
Symmetric
block
48 Moderat
e
More
secure
than DES
because
it
perform
s the
DES
algorith
m 3X
AES NIST in
2000
128bits 128,
192,
256bits
Symmetric
block
10,12,1
4
Fast Most
Secure
Question 2
WPAN Technologies
WPAN technologies are personal area networks that connect computing devices near each
other for example in a room without cable. There are various WPAN advances such as
Bluetooth and Z-wave technologies.
Z – Wave WPAN
Z-Wave was released in 2004 and is a wireless transmission standard used mainly for home
devices automation. It uses a mesh topology network and to transmits data from one device
to another using low-energy radio waves. It can be applied in security systems, lighting
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS NETWORKING 4
control systems, thermostats, locks, windows, and garage door openers. Z- Wave is simpler
and cheaper to install compared to ZigBee (SmartHome, 2017).
Security Issues
The most pressing challenge for computing networks is maintain data and information
security. According to (ABR, 2017) Z-Wave can security problems including the following
i) Radio waves jamming. Since it is a wireless standard, signals can suffer a jamming
attack such as interference and blocking. When radio jamming happens, data
transmission cannot occur for the devices in the network making it inefficient.
ii) Platform security weakness. Z-Wave is still an emerging technology, its security are
therefore in development.
iii) Device hacking. Since Z-Wave supports the Internet of Things technology that aims
to interconnect objects together, it is prone to hacker device attacks. Internet of
Things is also a developing technology.
Bluetooth WPAN
Bluetooth is a wireless standard used to create both mobile and fixed personal area
networks between devices in short range distances using radio waves.
Security issues
Like other wireless communications, Bluetooth is vulnerable to network attacks including
the following (SansInsitute, 2003)
i) Eavesdropping. It is very easy for attackers to personify and eavesdrop on
communication in a Bluetooth setup. The technology uses devices that have little
control systems, thermostats, locks, windows, and garage door openers. Z- Wave is simpler
and cheaper to install compared to ZigBee (SmartHome, 2017).
Security Issues
The most pressing challenge for computing networks is maintain data and information
security. According to (ABR, 2017) Z-Wave can security problems including the following
i) Radio waves jamming. Since it is a wireless standard, signals can suffer a jamming
attack such as interference and blocking. When radio jamming happens, data
transmission cannot occur for the devices in the network making it inefficient.
ii) Platform security weakness. Z-Wave is still an emerging technology, its security are
therefore in development.
iii) Device hacking. Since Z-Wave supports the Internet of Things technology that aims
to interconnect objects together, it is prone to hacker device attacks. Internet of
Things is also a developing technology.
Bluetooth WPAN
Bluetooth is a wireless standard used to create both mobile and fixed personal area
networks between devices in short range distances using radio waves.
Security issues
Like other wireless communications, Bluetooth is vulnerable to network attacks including
the following (SansInsitute, 2003)
i) Eavesdropping. It is very easy for attackers to personify and eavesdrop on
communication in a Bluetooth setup. The technology uses devices that have little
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORKING 5
security features and do not have enhanced authentication security features and can
therefore provide easy intrusion to the network.
ii) Person in the middle attack. Since it uses a hopping mechanism, it is easy to
intercept data communication in a Bluetooth network setup.
iii) Denial of service attack. Bluetooth networks signals are prone to radio signals denial
of service attack making them inefficient.
Question 3
Energy harvesting: A reflection
To lay ground on energy harvesting critical reflection according to the two papers, I would
like to first introduce the concept of wireless sensor networks (WSNs). WSNs are wireless
networks comprising of spatially dispersed independent devices using sensors to monitor
physical or environmental conditions. They are applied in health monitoring, area
monitoring, natural disaster prevention, forest fire detections, resource monitoring, home
devices automation and more. The most important thing in a WSN is energy for the nodes in
the network. They need constant energy to be able to perform their functions. To achieve
this, energy harvesting is important. It is the concept of obtaining thermal, kinetic, wind,
solar energy for WSN devices. Looking at some of the recent advances in technology such as
the Internet of Things, energy harvesting will increasingly develop in future. It is therefore
important to perform energy harvesting in order to sustain WSNs.
Both authors agree on the fact that WSNs network need to be constantly supplied with
energy for efficiency and continued operation. For instance, a WSN that has been set up in
the middle of a forest to detect a forest fire would be of no help if the nodes are depleted
on battery power.
security features and do not have enhanced authentication security features and can
therefore provide easy intrusion to the network.
ii) Person in the middle attack. Since it uses a hopping mechanism, it is easy to
intercept data communication in a Bluetooth network setup.
iii) Denial of service attack. Bluetooth networks signals are prone to radio signals denial
of service attack making them inefficient.
Question 3
Energy harvesting: A reflection
To lay ground on energy harvesting critical reflection according to the two papers, I would
like to first introduce the concept of wireless sensor networks (WSNs). WSNs are wireless
networks comprising of spatially dispersed independent devices using sensors to monitor
physical or environmental conditions. They are applied in health monitoring, area
monitoring, natural disaster prevention, forest fire detections, resource monitoring, home
devices automation and more. The most important thing in a WSN is energy for the nodes in
the network. They need constant energy to be able to perform their functions. To achieve
this, energy harvesting is important. It is the concept of obtaining thermal, kinetic, wind,
solar energy for WSN devices. Looking at some of the recent advances in technology such as
the Internet of Things, energy harvesting will increasingly develop in future. It is therefore
important to perform energy harvesting in order to sustain WSNs.
Both authors agree on the fact that WSNs network need to be constantly supplied with
energy for efficiency and continued operation. For instance, a WSN that has been set up in
the middle of a forest to detect a forest fire would be of no help if the nodes are depleted
on battery power.

WIRELESS NETWORKING 6
It is important to measure the required energy levels of a WSN before seeking to harvest the
energy for its use. Ambient energy resources may not be enough to provide the needed
energy and external sources may be called for.
Energy harvesting will be very crucial for the development and sustainability of wireless
communication standards in future. It is thus important to evaluate energy sources and
implement procedure to facilitate the developments.
Technology is increasingly changing and enhancing our lives. Energy harvesting is an
emerging technology that will improve wireless communication standards especially WSNs.
It will enable their efficiency and sustainability, as well as help conserve other energy
resources.
Question 4
Digital Cellular Handsets
A digital cellular handset is a mobile device that can receive both audio and digital data,
process it and transmit it in form of radio waves (TechTarget, 2017).
Benefits of using cellular handsets for Telestra
Cellular handsets have become very popular in use for organizations because of great
features such as portability and Internet access. Cellular handsets are more convenient to
use than notebook computers because they provide hands-free options such as headsets,
Bluetooth enabled, can use extra batteries, and portable charging devices. Small cellular
handsets also features including text messaging capabilities unlike notebooks, have a call
It is important to measure the required energy levels of a WSN before seeking to harvest the
energy for its use. Ambient energy resources may not be enough to provide the needed
energy and external sources may be called for.
Energy harvesting will be very crucial for the development and sustainability of wireless
communication standards in future. It is thus important to evaluate energy sources and
implement procedure to facilitate the developments.
Technology is increasingly changing and enhancing our lives. Energy harvesting is an
emerging technology that will improve wireless communication standards especially WSNs.
It will enable their efficiency and sustainability, as well as help conserve other energy
resources.
Question 4
Digital Cellular Handsets
A digital cellular handset is a mobile device that can receive both audio and digital data,
process it and transmit it in form of radio waves (TechTarget, 2017).
Benefits of using cellular handsets for Telestra
Cellular handsets have become very popular in use for organizations because of great
features such as portability and Internet access. Cellular handsets are more convenient to
use than notebook computers because they provide hands-free options such as headsets,
Bluetooth enabled, can use extra batteries, and portable charging devices. Small cellular
handsets also features including text messaging capabilities unlike notebooks, have a call
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS NETWORKING 7
sim cards, GPS positioning, digital camera and more. For Telestra, suing digital cellular
handsets will provide the following benefits
i) Business productivity. Using cellular phones to work will improve business processes
and therefore overall business productivity.
ii) Improved customer experience. Since technicians will be able to access company
system in the field, they will be able to provide customers with better updated
responses hence enhancing customer experience
iii) Quick system updates. Technicians will be able to update company data in the field
as they work which will ensure the company is working with updated information
iv) Less errors. Instant work updates will lessen the errors brought about by using pen
and paper technology and improve business policies
sim cards, GPS positioning, digital camera and more. For Telestra, suing digital cellular
handsets will provide the following benefits
i) Business productivity. Using cellular phones to work will improve business processes
and therefore overall business productivity.
ii) Improved customer experience. Since technicians will be able to access company
system in the field, they will be able to provide customers with better updated
responses hence enhancing customer experience
iii) Quick system updates. Technicians will be able to update company data in the field
as they work which will ensure the company is working with updated information
iv) Less errors. Instant work updates will lessen the errors brought about by using pen
and paper technology and improve business policies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORKING 8
References
ABR. (2017, September 20). Introduction to the Z-Wave Security Ecosystem. Retrieved from
sigma designs: http://z-wave.sigmadesigns.com/wp-content/uploads/2016/08/Z-
Wave-Security-White-Paper.pdf
Alzaabi, M., Ranjeeth, K., Alukaidey, T., & Dr Salman, K. (2013). SECURITY ALGORITHMS FOR
WIMAX. International Journal of Network Security & Its Applications (IJNSA), 31-32.
SansInsitute. (2003, September 20). Bluetooth And Its Inherent Security Issues. Retrieved
from Sans.org:
https://www.sans.org/reading-room/whitepapers/wireless/bluetooth-inherent-
security-issues-945
SmartHome. (2017, August 20). What is Z-Wave? Retrieved from smart home:
https://www.smarthome.com/sc-what-is-zwave-home-automation
TechTarget. (2017, September 21). cellular telephone (mobile telephone). Retrieved from
Tech Target : http://searchmobilecomputing.techtarget.com/definition/cellular-
telephone
Verma, A., Guha, P., & Mishra, S. (2016). Comparative Study of Different Cryptographic.
International Journal of Emerging Trends & Technology in Computer Science
(IJETTCS), 58-60.
References
ABR. (2017, September 20). Introduction to the Z-Wave Security Ecosystem. Retrieved from
sigma designs: http://z-wave.sigmadesigns.com/wp-content/uploads/2016/08/Z-
Wave-Security-White-Paper.pdf
Alzaabi, M., Ranjeeth, K., Alukaidey, T., & Dr Salman, K. (2013). SECURITY ALGORITHMS FOR
WIMAX. International Journal of Network Security & Its Applications (IJNSA), 31-32.
SansInsitute. (2003, September 20). Bluetooth And Its Inherent Security Issues. Retrieved
from Sans.org:
https://www.sans.org/reading-room/whitepapers/wireless/bluetooth-inherent-
security-issues-945
SmartHome. (2017, August 20). What is Z-Wave? Retrieved from smart home:
https://www.smarthome.com/sc-what-is-zwave-home-automation
TechTarget. (2017, September 21). cellular telephone (mobile telephone). Retrieved from
Tech Target : http://searchmobilecomputing.techtarget.com/definition/cellular-
telephone
Verma, A., Guha, P., & Mishra, S. (2016). Comparative Study of Different Cryptographic.
International Journal of Emerging Trends & Technology in Computer Science
(IJETTCS), 58-60.

WIRELESS NETWORKING 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





