Wireless Networking Concepts: Channel Reuse, Security, IoT, Telstra
VerifiedAdded on 2020/05/28
|15
|1083
|28
Homework Assignment
AI Summary
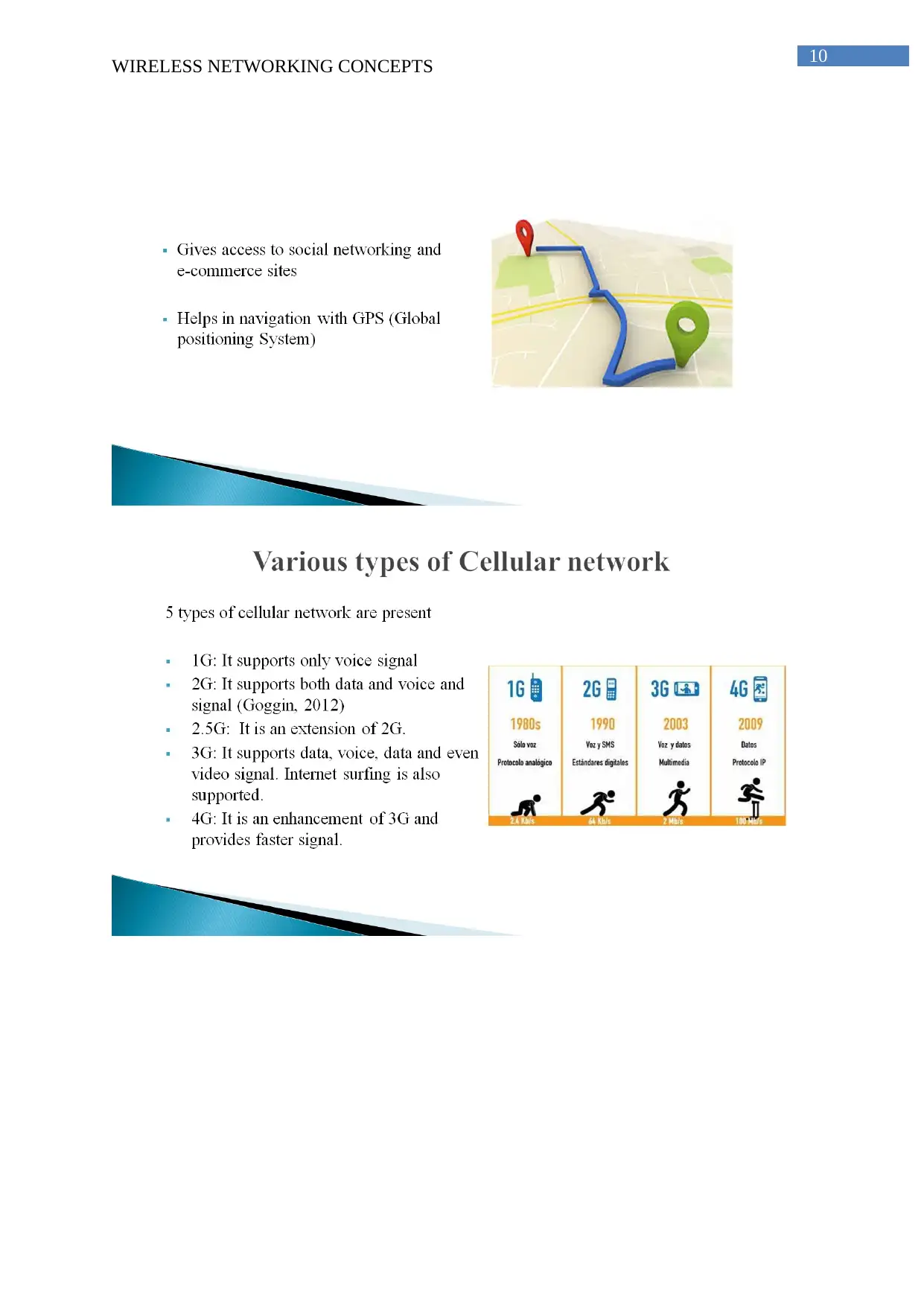
This assignment solution addresses several key concepts in wireless networking. It begins by comparing and contrasting channel reuse in Wireless Local Area Networks (WLANs) with frequency reuse in mobile phone networks, supported by diagrams. The solution then delves into the security challenges of Wireless Metropolitan Area Network (WMAN) technologies, specifically Wi-Fi and WiMAX, identifying vulnerabilities like unauthorized data access, Denial of Service (DoS) attacks, lack of authentication, and lack of encryption. The assignment also includes a critical reflection on the topic of Energy Harvest within the context of the Internet of Things (IoT), based on two provided research papers, one focusing on ZigBee technology and the other on the evolution of the Intranet of Things. Finally, the solution encompasses a presentation on the Telstra case study, though the content of the presentation is not detailed in the provided text. The assignment demonstrates an understanding of various wireless technologies, their security implications, and emerging trends like IoT.
1 out of 15


















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)