Wireless Network Analysis: NFC, RFID Technologies and Ping Testing
VerifiedAdded on 2023/06/04
|6
|1027
|445
Report
AI Summary
This report provides a comparative analysis of Near Field Communication (NFC) and Radio Frequency Identification (RFID) technologies, highlighting their functionalities, differences, and applications. NFC enables secure communication through embedded sensors for data reading and peer-to-peer connections, while RFID uses radio waves for unique item identification, comprising tags, readers, and antennas. The report discusses active and passive RFID tags, detailing their power sources and read ranges. It also covers practical network testing using ping commands to verify connections between laptops and wireless access points, examining the impact of channel changes and passphrase mismatches on network connectivity. The document concludes with a bibliography of relevant research, offering a comprehensive overview of these wireless networking concepts. Desklib provides this and other solved assignments to help students.

Running head: WIRELESS NETWORKING CONCEPTS
Wireless Networking Concepts
Name of the Student
Name of the University
Author’s Note
Wireless Networking Concepts
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORKING CONCEPTS
Part A: Comparative Analysis
Answer to Question 1:
The NFC and RFID are interrelated with each other and it is used for identifying the radio
waves and has high frequency operating at 13.56 Mhz. NFC is used for enabling secure
communication with the use of an embedded sensor that is used for reading data from the
NFC tag and communicate with the different device using peer to peer connection. RFID uses
a radio waves for the identification of the item uniquely and the system is created using a
NFC tag, tag reader and an antenna. An interrogating signal is sent using the antenna and a
unique response is received from the tag. There are two types of NFC tag used for the
establishment of the secure connection i.e. Passive tag and Active tag. A power source is
connected with the system in the active RFID tag and a long read range is used for the
industrial devices for the improvement of the logistics and other operations. The passive
RFID tags are designed without any power source but they are powered using an
electromagnetic energy that are transmitted with the RFID. The radio waves should be strong
for transmitting power to the RFID tag and thus the read range is short.
For establishment of the secure communication the NFC is developed and its operating
frequency is same as the RFID tags. NFC device needs to be in close proximity for its
operation and thus it has become a secure connection choice. It uses the peer to peer
communication and it can work in both tag and reader mode. Since the NFC provides a
unique set of feature it has become an ideal choice for its application in different fields such
as contact less payment and its adoption in the smart phone for creating connection between
the devices. It can help in sharing data and information between the two devices using the
radio waves. There are different NFC devices that can use passive tags that can read the tag
and its compliance with ISO 1593 and there are different data that can eb used passing the
WIRELESS NETWORKING CONCEPTS
Part A: Comparative Analysis
Answer to Question 1:
The NFC and RFID are interrelated with each other and it is used for identifying the radio
waves and has high frequency operating at 13.56 Mhz. NFC is used for enabling secure
communication with the use of an embedded sensor that is used for reading data from the
NFC tag and communicate with the different device using peer to peer connection. RFID uses
a radio waves for the identification of the item uniquely and the system is created using a
NFC tag, tag reader and an antenna. An interrogating signal is sent using the antenna and a
unique response is received from the tag. There are two types of NFC tag used for the
establishment of the secure connection i.e. Passive tag and Active tag. A power source is
connected with the system in the active RFID tag and a long read range is used for the
industrial devices for the improvement of the logistics and other operations. The passive
RFID tags are designed without any power source but they are powered using an
electromagnetic energy that are transmitted with the RFID. The radio waves should be strong
for transmitting power to the RFID tag and thus the read range is short.
For establishment of the secure communication the NFC is developed and its operating
frequency is same as the RFID tags. NFC device needs to be in close proximity for its
operation and thus it has become a secure connection choice. It uses the peer to peer
communication and it can work in both tag and reader mode. Since the NFC provides a
unique set of feature it has become an ideal choice for its application in different fields such
as contact less payment and its adoption in the smart phone for creating connection between
the devices. It can help in sharing data and information between the two devices using the
radio waves. There are different NFC devices that can use passive tags that can read the tag
and its compliance with ISO 1593 and there are different data that can eb used passing the
2
WIRELESS NETWORKING CONCEPTS
information between the users. The frequency range that is used for the operation of the NFC
and the RFID are given below:
LF (Low Frequency) 125 to 134 khz
HF (High Frequency) 13.56 Mhz
UHD Ultra high frequency 856 mhz to 960 mhz.
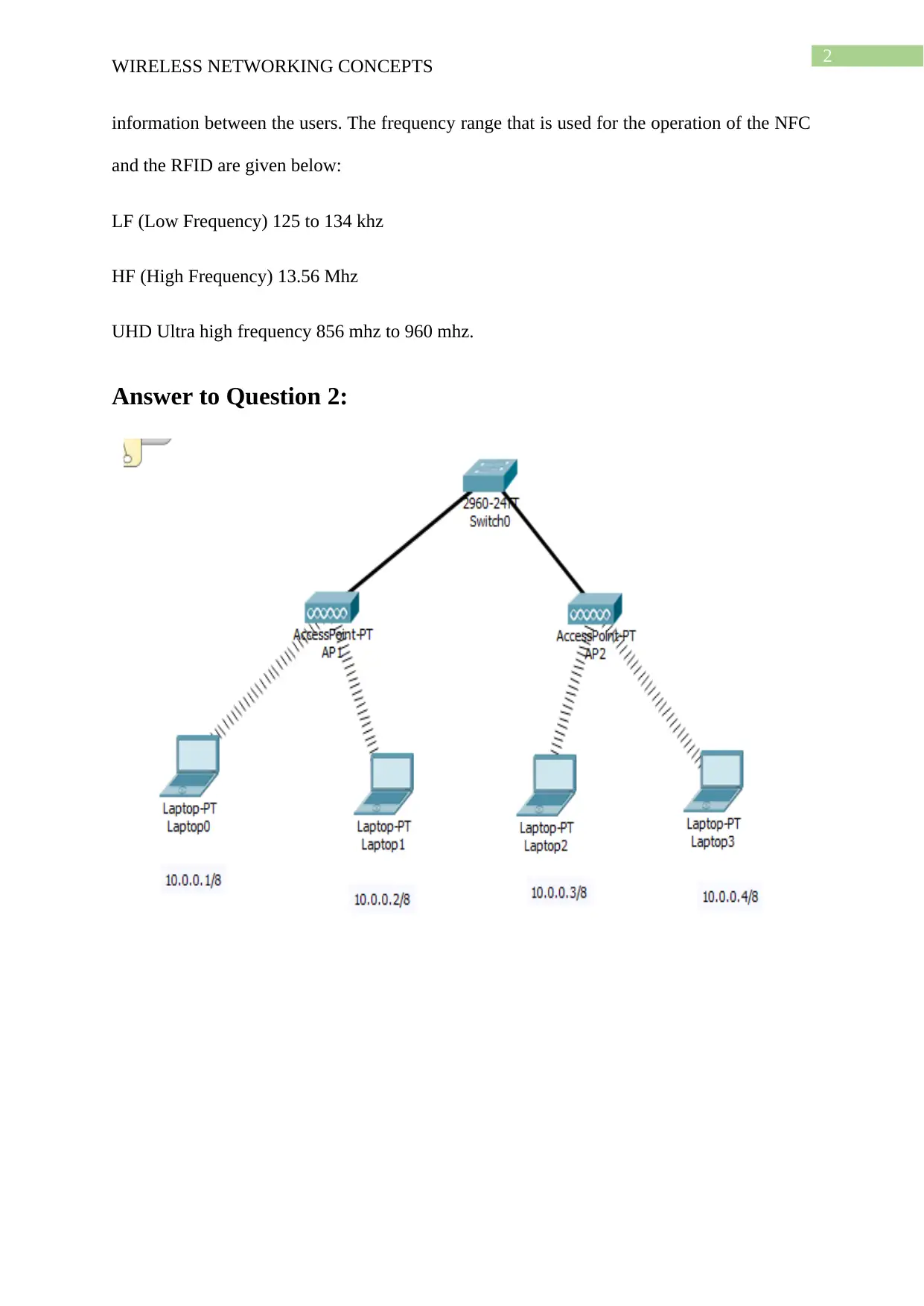
Answer to Question 2:
WIRELESS NETWORKING CONCEPTS
information between the users. The frequency range that is used for the operation of the NFC
and the RFID are given below:
LF (Low Frequency) 125 to 134 khz
HF (High Frequency) 13.56 Mhz
UHD Ultra high frequency 856 mhz to 960 mhz.
Answer to Question 2:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRELESS NETWORKING CONCEPTS
a. Ping Test
Ping is used for testing the connection between the laptops connected with the
wireless access point and testing the transmission of data packet between the device
connected with the different wireless access point in the network. For answering the question
the command prompt is opened in laptop 1 and the command ping 10.0.0.3 is used for testing
the connection with the laptop connected with the access point 2. The laptop is connected
with the access point using the SSID and the passphrase used in the access point.
b. If the channel is changed in any of the access point from the two access point connected
with each other via a layer 2 switch no major difference is found in the network. If a
WIRELESS NETWORKING CONCEPTS
a. Ping Test
Ping is used for testing the connection between the laptops connected with the
wireless access point and testing the transmission of data packet between the device
connected with the different wireless access point in the network. For answering the question
the command prompt is opened in laptop 1 and the command ping 10.0.0.3 is used for testing
the connection with the laptop connected with the access point 2. The laptop is connected
with the access point using the SSID and the passphrase used in the access point.
b. If the channel is changed in any of the access point from the two access point connected
with each other via a layer 2 switch no major difference is found in the network. If a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
WIRELESS NETWORKING CONCEPTS
continuous ping is done with the laptop connected in the network the ping fails for some time
and it is reconnected with the network after a certain duration of time. The use of the same
channel can also cause interference and distortion the signal and thus can cause packet loss.
c. If the passphrase that is used for configuration of the access point not matches with the
passphrase that is given in the laptop while establishment of the connection between the
laptop and the access point the laptop cannot send and receive data packet in the network.
WIRELESS NETWORKING CONCEPTS
continuous ping is done with the laptop connected in the network the ping fails for some time
and it is reconnected with the network after a certain duration of time. The use of the same
channel can also cause interference and distortion the signal and thus can cause packet loss.
c. If the passphrase that is used for configuration of the access point not matches with the
passphrase that is given in the laptop while establishment of the connection between the
laptop and the access point the laptop cannot send and receive data packet in the network.

5
WIRELESS NETWORKING CONCEPTS
Bibliography
Chew, C. B., Mahinderjit-Singh, M., Wei, K. C., Sheng, T. W., Husin, M. H., & Malim, N.
H. A. H. (2015). Sensors-enabled smart attendance systems using NFC and RFID
technologies. Int. J. New Comput. Archit. Appl, 5, 19-29.
Orozco, J., Chavira, G., Castro, I., Bolaños, J. F., Sánchez, R. A., & Cantú, J. F. (2014).
Towards NFC and RFID Combination to Automatic Services. International Journal
of Engineering, 4(8), 8269.
Park, C. W., Ahn, J. H., & Lee, T. J. (2017). Fast object identification with mode switching
for coexistence of NFC and RFID. Transactions on Emerging Telecommunications
Technologies, 28(2), e2939.
Prodanoff, Z. G., Jones, E. L., Chi, H., Elfayoumy, S., & Cummings, C. (2016). Survey of
Security Challenges in NFC and RFID for E-Health Applications. International
Journal of E-Health and Medical Communications (IJEHMC), 7(2), 1-13.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, August). Study on effective
pattern of magnetic sheet attached on NFC antenna. In Radio-Frequency Integration
Technology (RFIT), 2015 IEEE International Symposium on (pp. 208-210). IEEE.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, November). A study on the
effective pattern of magnetic sheet considering their characteristics attached on NFC
antenna. In Antennas and Propagation (ISAP), 2015 International Symposium (pp. 1-
4). IEEE.
WIRELESS NETWORKING CONCEPTS
Bibliography
Chew, C. B., Mahinderjit-Singh, M., Wei, K. C., Sheng, T. W., Husin, M. H., & Malim, N.
H. A. H. (2015). Sensors-enabled smart attendance systems using NFC and RFID
technologies. Int. J. New Comput. Archit. Appl, 5, 19-29.
Orozco, J., Chavira, G., Castro, I., Bolaños, J. F., Sánchez, R. A., & Cantú, J. F. (2014).
Towards NFC and RFID Combination to Automatic Services. International Journal
of Engineering, 4(8), 8269.
Park, C. W., Ahn, J. H., & Lee, T. J. (2017). Fast object identification with mode switching
for coexistence of NFC and RFID. Transactions on Emerging Telecommunications
Technologies, 28(2), e2939.
Prodanoff, Z. G., Jones, E. L., Chi, H., Elfayoumy, S., & Cummings, C. (2016). Survey of
Security Challenges in NFC and RFID for E-Health Applications. International
Journal of E-Health and Medical Communications (IJEHMC), 7(2), 1-13.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, August). Study on effective
pattern of magnetic sheet attached on NFC antenna. In Radio-Frequency Integration
Technology (RFIT), 2015 IEEE International Symposium on (pp. 208-210). IEEE.
Sekiguchi, T., Okano, Y., Ohmura, N., & Ogino, S. (2015, November). A study on the
effective pattern of magnetic sheet considering their characteristics attached on NFC
antenna. In Antennas and Propagation (ISAP), 2015 International Symposium (pp. 1-
4). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




