Wireless Networking Concepts Report: Encryption, Security, and Reviews
VerifiedAdded on 2020/04/07
|12
|1000
|32
Report
AI Summary
This report delves into the intricacies of wireless networking, providing a comprehensive overview of key concepts and technologies. It begins by examining the encryption methods employed in Wi-Max, including AES, EAP, and PKMv2, elucidating their functionalities and advantages. The report then addresses the security challenges associated with Wireless Personal Area Networks (WPANs), specifically focusing on DDoS and malware attacks, and their implications. Furthermore, it includes reviews of two research papers that explore energy harvesting in Wireless Sensor Networks (WSNs) and wireless communications. Finally, the report analyzes a presentation file detailing the benefits Telestra can derive from wireless cellular networks. The report concludes by synthesizing the discussed concepts, offering insights into the current state and future of wireless networking.

Running head: WIRELESS NETWORKING CONCEPTS
Wireless Networking Concepts
Name of the Student
Name of the University
Author’s note
Wireless Networking Concepts
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS NETWORKING CONCEPTS
Table of Contents
Introduction....................................................................................................................1
1. Encryption methods of Wi-Max.................................................................................1
2. Wireless Personal Area Network and its security challenges....................................2
3. Review of two research papers..................................................................................2
4. Telestra presentation file............................................................................................3
Conclusion......................................................................................................................9
References....................................................................................................................10
Table of Contents
Introduction....................................................................................................................1
1. Encryption methods of Wi-Max.................................................................................1
2. Wireless Personal Area Network and its security challenges....................................2
3. Review of two research papers..................................................................................2
4. Telestra presentation file............................................................................................3
Conclusion......................................................................................................................9
References....................................................................................................................10

2WIRELESS NETWORKING CONCEPTS
Introduction
The report will highlight Wi-Max encryption methods, WPAN security challenges,
two journal articles’ reviews and Telestra getting benefits from the wireless cellular network.
1. Encryption methods of Wi-Max
Wi-Max has three encryption methods and they are AES, EAP and PKMv2.
PKMv2: This protocol has the varied properties and it contains the mutual
authentication. This mutual authentication is carried out by integrating the message integrity
algorithms, EAP-based protocols and RSA-based protocols, and key management protocols
(Sharma & Singh, 2017). The protocol is utilized for the authentic exchange of the
cryptographic keys for broadcast traffic and multicast traffic.
AES: Advanced Encryption Standard is based on Rijndael algorithm. This encryption
method is agile and can be configured with ease. It also requires less memory compared to all
other encryption standards like PKMv2 or 3DES. Thus all of them prefer this key because of
all these advantageous features. The algorithm works on the 128-bit block size of data and
this block size of data are arranged in a 4x4 array of bytes and this arrangement is called
state. This standard is used to encipher over the air traffic.
EAP: EAP protocol is used to connect a computer to the Internet, the authentication
procedure that is used and supported by EAP are public key encryption authentication, token
cards, smart cards and one-time passwords. The user requests for connection to the wireless
network via an access point (Sharma & Singh, 2017). The access point asks for ID from the
user and transfers data to the authorized users’ server.
Introduction
The report will highlight Wi-Max encryption methods, WPAN security challenges,
two journal articles’ reviews and Telestra getting benefits from the wireless cellular network.
1. Encryption methods of Wi-Max
Wi-Max has three encryption methods and they are AES, EAP and PKMv2.
PKMv2: This protocol has the varied properties and it contains the mutual
authentication. This mutual authentication is carried out by integrating the message integrity
algorithms, EAP-based protocols and RSA-based protocols, and key management protocols
(Sharma & Singh, 2017). The protocol is utilized for the authentic exchange of the
cryptographic keys for broadcast traffic and multicast traffic.
AES: Advanced Encryption Standard is based on Rijndael algorithm. This encryption
method is agile and can be configured with ease. It also requires less memory compared to all
other encryption standards like PKMv2 or 3DES. Thus all of them prefer this key because of
all these advantageous features. The algorithm works on the 128-bit block size of data and
this block size of data are arranged in a 4x4 array of bytes and this arrangement is called
state. This standard is used to encipher over the air traffic.
EAP: EAP protocol is used to connect a computer to the Internet, the authentication
procedure that is used and supported by EAP are public key encryption authentication, token
cards, smart cards and one-time passwords. The user requests for connection to the wireless
network via an access point (Sharma & Singh, 2017). The access point asks for ID from the
user and transfers data to the authorized users’ server.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WIRELESS NETWORKING CONCEPTS
2. Wireless Personal Area Network and its security challenges
The security challenges faced are-
DDoS attacks: DDoS attacks sabotage one's computer and take the ownership of the
computer system thus steal the sensitive information of the computer this kind of attack is
very common and this attack generally occurs in insecure wireless personal area network
(Achary & Lalseta, 2017). The customers may be unaware that their system has been hacked,
when they try to enter their system they will find out that their database and the system have
been hacked. This can also lead to the shutdown of one's server computer as well.
Malware attack: The intruders attack one’s computer system via insecure network via
virus attacks. The virus installed into one’s system can steal one’s data, can alter one’s data
and can even destroy one’s files resides in the customer data as well.
3. Review of two research papers
First paper review: Wireless Sensor Networks is gaining prominence due to the
enhancement of Internet of Things as well as Cyber-Physical Systems. In this paper, the
effective harvesting system to use the power of WSN technology for WSN environment has
been showcased. Various energy predictions models have been prescribed in this paper that
has the capability to embellish the energy harvested in Wireless Sensor Network (Shaikh &
Zeadally, 2016). This paper has also highlighted the issues that need to be detected to
embellish the harvesting system for the WSN environment so that the system can be utilized
in profitable and effective manner.
Second paper review: This paper has highlighted the energy that is harvesting the
wireless communications. All the aspects of the wireless networks like network issues,
energy harvesting nodes, transmission scheduling policies, resource allocation and harvesting
2. Wireless Personal Area Network and its security challenges
The security challenges faced are-
DDoS attacks: DDoS attacks sabotage one's computer and take the ownership of the
computer system thus steal the sensitive information of the computer this kind of attack is
very common and this attack generally occurs in insecure wireless personal area network
(Achary & Lalseta, 2017). The customers may be unaware that their system has been hacked,
when they try to enter their system they will find out that their database and the system have
been hacked. This can also lead to the shutdown of one's server computer as well.
Malware attack: The intruders attack one’s computer system via insecure network via
virus attacks. The virus installed into one’s system can steal one’s data, can alter one’s data
and can even destroy one’s files resides in the customer data as well.
3. Review of two research papers
First paper review: Wireless Sensor Networks is gaining prominence due to the
enhancement of Internet of Things as well as Cyber-Physical Systems. In this paper, the
effective harvesting system to use the power of WSN technology for WSN environment has
been showcased. Various energy predictions models have been prescribed in this paper that
has the capability to embellish the energy harvested in Wireless Sensor Network (Shaikh &
Zeadally, 2016). This paper has also highlighted the issues that need to be detected to
embellish the harvesting system for the WSN environment so that the system can be utilized
in profitable and effective manner.
Second paper review: This paper has highlighted the energy that is harvesting the
wireless communications. All the aspects of the wireless networks like network issues,
energy harvesting nodes, transmission scheduling policies, resource allocation and harvesting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS NETWORKING CONCEPTS
nodes elaborately (Ulukus et al., 2015). Various models associated with harvesting nodes
have been detailed with respect to various network scales.
4. Telestra presentation file
Slide 1
nodes elaborately (Ulukus et al., 2015). Various models associated with harvesting nodes
have been detailed with respect to various network scales.
4. Telestra presentation file
Slide 1

5WIRELESS NETWORKING CONCEPTS
Slide 2
Slide 3
Slide 2
Slide 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6WIRELESS NETWORKING CONCEPTS
Slide 4
Slide 5
Slide 4
Slide 5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS NETWORKING CONCEPTS
Slide 6
Slide 7
Slide 6
Slide 7
8WIRELESS NETWORKING CONCEPTS
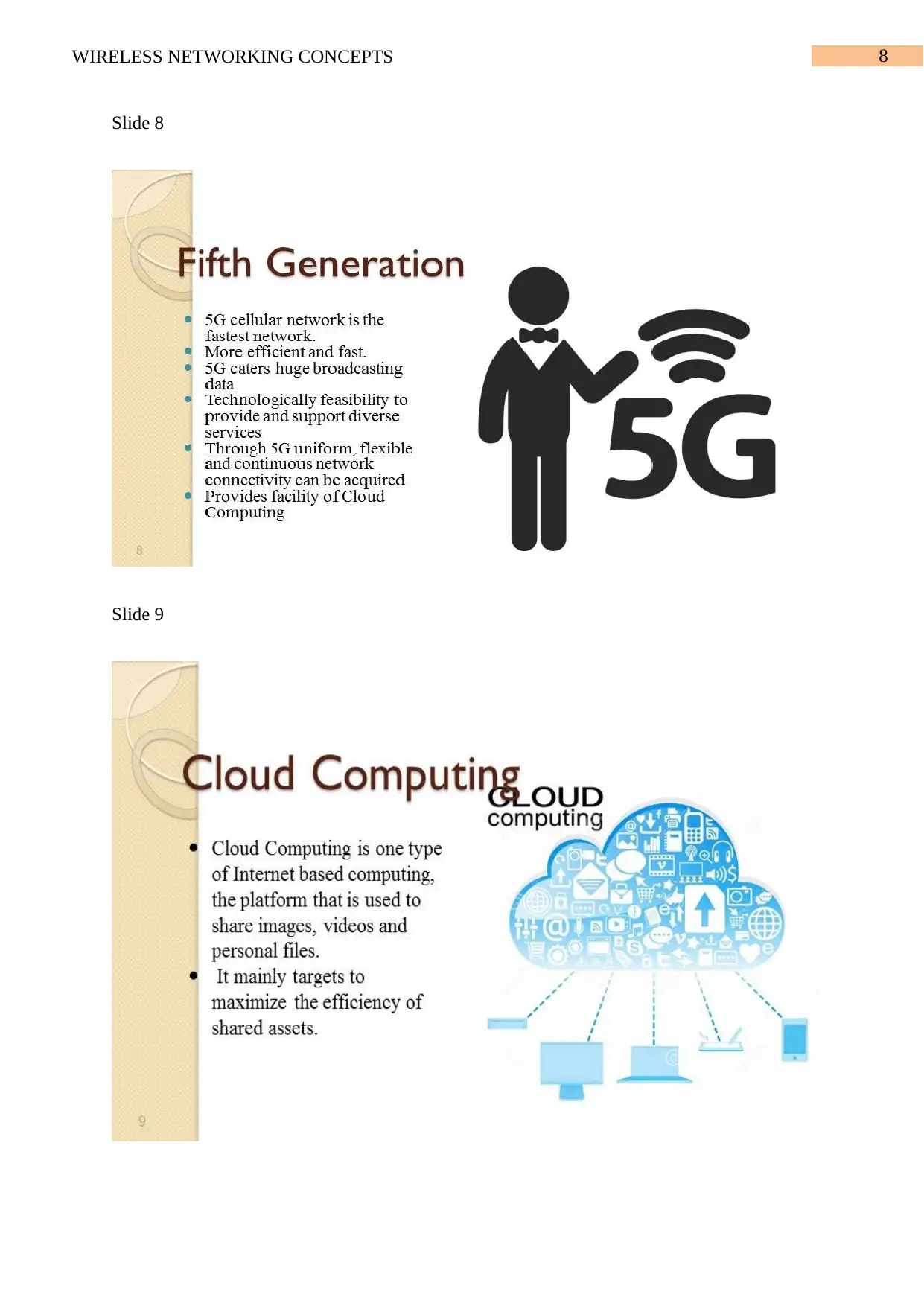
Slide 8
Slide 9
Slide 8
Slide 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9WIRELESS NETWORKING CONCEPTS
Slide 10
Slide 11
Slide 10
Slide 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10WIRELESS NETWORKING CONCEPTS
Slide 12
Conclusion
Wi-Max encryption procedures have been well illustrated in this report. The security
challenges associated with WPAN technologies have been showcased too. The two articles
have been reviewed as well. A presentation has been well demonstrated stated the benefits
that Telestra can acquire from the wireless cellular network.
Slide 12
Conclusion
Wi-Max encryption procedures have been well illustrated in this report. The security
challenges associated with WPAN technologies have been showcased too. The two articles
have been reviewed as well. A presentation has been well demonstrated stated the benefits
that Telestra can acquire from the wireless cellular network.

11WIRELESS NETWORKING CONCEPTS
References
Achary, R., & Lalseta, J. S. (2017). Internet of Things: Essential Technology, Application
Domain, Privacy and Security Challenges. International Journal of Computer
Applications, 157(6).
Shaikh, F. K., & Zeadally, S. (2016). Energy harvesting in wireless sensor networks: A
comprehensive review. Renewable and Sustainable Energy Reviews, 55, 1041-1054.
Sharma, S., & Singh, H. (2017). An Effectual Approach for Security and Integrity against
Wicked Node Attacks in Wi-Max Network Environment. Indian Journal of Science
and Technology, 10(27).
Ulukus, S., Yener, A., Erkip, E., Simeone, O., Zorzi, M., Grover, P., & Huang, K. (2015).
Energy harvesting wireless communications: A review of recent advances. IEEE
Journal on Selected Areas in Communications, 33(3), 360-381.
References
Achary, R., & Lalseta, J. S. (2017). Internet of Things: Essential Technology, Application
Domain, Privacy and Security Challenges. International Journal of Computer
Applications, 157(6).
Shaikh, F. K., & Zeadally, S. (2016). Energy harvesting in wireless sensor networks: A
comprehensive review. Renewable and Sustainable Energy Reviews, 55, 1041-1054.
Sharma, S., & Singh, H. (2017). An Effectual Approach for Security and Integrity against
Wicked Node Attacks in Wi-Max Network Environment. Indian Journal of Science
and Technology, 10(27).
Ulukus, S., Yener, A., Erkip, E., Simeone, O., Zorzi, M., Grover, P., & Huang, K. (2015).
Energy harvesting wireless communications: A review of recent advances. IEEE
Journal on Selected Areas in Communications, 33(3), 360-381.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





