Wireless Networking Concept and Security Technologies Report
VerifiedAdded on 2020/04/07
|19
|1159
|117
Report
AI Summary
This report delves into the realm of wireless networking, focusing on security protocols and technologies. It begins by exploring WiMax and its security measures, including AES, Triple DES, and RSA encryption methods. The report then transitions to WPAN technologies, specifically Bluetooth and Zigbee, analyzing their security challenges and vulnerabilities, such as DoS attacks and malware threats. Furthermore, it references research papers that discuss energy harvesting in wireless sensor networks (WSN) and the evolution of energy gathering techniques. The report concludes with a comprehensive overview of the current state and future directions of wireless networking security, providing valuable insights into the ongoing developments in the field.

0
WIRELESS NETWORKING CONCEPT
Wireless networking Concept
Name of the Student
Name of the University
Author’s Note
WIRELESS NETWORKING CONCEPT
Wireless networking Concept
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORKING CONCEPT
1. The use of the advance technology in the market have helped in maintaining the security
of the data and information. Worldwide Interoperability for Microwave Access (WiMax) focuses
on services provided over a long distance by remote broadband access (Bernardos et al., 2014).
The applications of the WiMax have helped in keeping up the security of the information and
data over the system. The WiMax has a safe security convention having three data encryption
system. The three-information encryption strategy has been discussed below:
AES
The Advanced Encryption Standard (AES) is an algorithm that has been endorsed by the
US government. It takes a shot at a degree capable in 128-piece outline. It utilizes 192 and 256
bits keys for encryption process. The reason for the AES is to give a hi-tech level of security to
the information and data in the WiMax (Wu, Wang & Youn, 2014). The use of the AES have
held in keeping up the genuine standard of encoding information and data in the private division.
Triple DES
A triple DES give unique Data Encryption Standard (DES) algorithm that limits the
hackers from breaching the information and data in the system. The triple DES is a critical
standard that aides in using the symmetric calculation in different business association. The
encryption standard uses 56 bits each keys (Cheng, Huang & Du, 2013). The general length of
the key is 168 bits. Nevertheless, different master recommend 112-piece key is more like it.
RSA
RSA is an algorithm that uses asymmetric key encryption over internet. The RSA
calculation helps in encrypting and decrypting messages in the system. The plain content is
changed over into cipher message that is in encoded shape.
WIRELESS NETWORKING CONCEPT
1. The use of the advance technology in the market have helped in maintaining the security
of the data and information. Worldwide Interoperability for Microwave Access (WiMax) focuses
on services provided over a long distance by remote broadband access (Bernardos et al., 2014).
The applications of the WiMax have helped in keeping up the security of the information and
data over the system. The WiMax has a safe security convention having three data encryption
system. The three-information encryption strategy has been discussed below:
AES
The Advanced Encryption Standard (AES) is an algorithm that has been endorsed by the
US government. It takes a shot at a degree capable in 128-piece outline. It utilizes 192 and 256
bits keys for encryption process. The reason for the AES is to give a hi-tech level of security to
the information and data in the WiMax (Wu, Wang & Youn, 2014). The use of the AES have
held in keeping up the genuine standard of encoding information and data in the private division.
Triple DES
A triple DES give unique Data Encryption Standard (DES) algorithm that limits the
hackers from breaching the information and data in the system. The triple DES is a critical
standard that aides in using the symmetric calculation in different business association. The
encryption standard uses 56 bits each keys (Cheng, Huang & Du, 2013). The general length of
the key is 168 bits. Nevertheless, different master recommend 112-piece key is more like it.
RSA
RSA is an algorithm that uses asymmetric key encryption over internet. The RSA
calculation helps in encrypting and decrypting messages in the system. The plain content is
changed over into cipher message that is in encoded shape.

2
WIRELESS NETWORKING CONCEPT
On the other hand, RSA utilizes two keys for the uneven calculation. The key is just
known to the collector and transmitter that aides in giving additional security to the information
and data in the system.
2. The WPAN technologies are innovative technologies that aides in giving smooth
transmission of information and data with legitimate security. The two cases of WPAN advances
are Bluetooth and Zigbee. There are diverse sorts of difficulties identified with security of the
information and data amid the transmission. The assaults are against the secrecy and honesty of
the information and data (Makris, Skoutas & Skianis, 2013). Bluetooth is not able to give local
customer check. The Bluetooth connection is not ready to keep up the express conduct of the
associated gadgets. There is a tremendous danger of the DoS assaults in the system. The
transmission of information can be hindered because of DoS assault in the system (Amadeo et
al., 2014). The malignant section of the malwares and infections in the system causes
information break in the system. The sensitive information is in a danger of being defiled by the
malicious viruses.
Zigbee is a remote communication device that devours low power for giving low rate
cryptographic keys to security. The association between two gadgets in the system starts the
information transmission channel. There are different assaults in the Zigbee that causes
tremendous information rupture in the system.
3. Shaikh, Faisal Karim, and Sherali Zeadally. "Energy harvesting in wireless sensor
networks: A comprehensive review." Renewable and Sustainable Energy Reviews 55 (2016):
1041-1054.
WIRELESS NETWORKING CONCEPT
On the other hand, RSA utilizes two keys for the uneven calculation. The key is just
known to the collector and transmitter that aides in giving additional security to the information
and data in the system.
2. The WPAN technologies are innovative technologies that aides in giving smooth
transmission of information and data with legitimate security. The two cases of WPAN advances
are Bluetooth and Zigbee. There are diverse sorts of difficulties identified with security of the
information and data amid the transmission. The assaults are against the secrecy and honesty of
the information and data (Makris, Skoutas & Skianis, 2013). Bluetooth is not able to give local
customer check. The Bluetooth connection is not ready to keep up the express conduct of the
associated gadgets. There is a tremendous danger of the DoS assaults in the system. The
transmission of information can be hindered because of DoS assault in the system (Amadeo et
al., 2014). The malignant section of the malwares and infections in the system causes
information break in the system. The sensitive information is in a danger of being defiled by the
malicious viruses.
Zigbee is a remote communication device that devours low power for giving low rate
cryptographic keys to security. The association between two gadgets in the system starts the
information transmission channel. There are different assaults in the Zigbee that causes
tremendous information rupture in the system.
3. Shaikh, Faisal Karim, and Sherali Zeadally. "Energy harvesting in wireless sensor
networks: A comprehensive review." Renewable and Sustainable Energy Reviews 55 (2016):
1041-1054.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRELESS NETWORKING CONCEPT
This paper manages the social consequences of advances in the Wireless Sensor Network
(WSN). WSN incorporate monstrous number of static sensor focus focuses those aides in low
preparing. There are different wellsprings of centrality for the WSNs including Radio
Frequency-based significance gathering, Solar-based noteworthiness gathering, Thermal-based
Energy Harvesting and Flow-based vitality securing. There are different methodologies talked
about in the paper for the data gathering in progresses. As argued by Haas, (2013), this
framework may makes harm the environmental nature.
Ulukus, Sennur, et al. "Energy harvesting wireless communications: A review of recent
advances." IEEE Journal on Selected Areas in Communications 33.3 (2015): 360-381.
This paper talks about the new advances executed in the vitality gathering division. As
remarked by Wang, Zhang & Gulliver, (2014), the new advances in the criticalness gathering
have changed the standard situation of vitality acquiring. Haas, (2013) argued that the utilization
of the pushed methods in the vitality gathering have develops the shrouded cost of different
criticalness sources what's more exhausting the steady assets. Different conditions and
speculations talked about in the paper that uses the consistent idea of vitality amassing and
changing over it into current improvement.
WIRELESS NETWORKING CONCEPT
This paper manages the social consequences of advances in the Wireless Sensor Network
(WSN). WSN incorporate monstrous number of static sensor focus focuses those aides in low
preparing. There are different wellsprings of centrality for the WSNs including Radio
Frequency-based significance gathering, Solar-based noteworthiness gathering, Thermal-based
Energy Harvesting and Flow-based vitality securing. There are different methodologies talked
about in the paper for the data gathering in progresses. As argued by Haas, (2013), this
framework may makes harm the environmental nature.
Ulukus, Sennur, et al. "Energy harvesting wireless communications: A review of recent
advances." IEEE Journal on Selected Areas in Communications 33.3 (2015): 360-381.
This paper talks about the new advances executed in the vitality gathering division. As
remarked by Wang, Zhang & Gulliver, (2014), the new advances in the criticalness gathering
have changed the standard situation of vitality acquiring. Haas, (2013) argued that the utilization
of the pushed methods in the vitality gathering have develops the shrouded cost of different
criticalness sources what's more exhausting the steady assets. Different conditions and
speculations talked about in the paper that uses the consistent idea of vitality amassing and
changing over it into current improvement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
WIRELESS NETWORKING CONCEPT
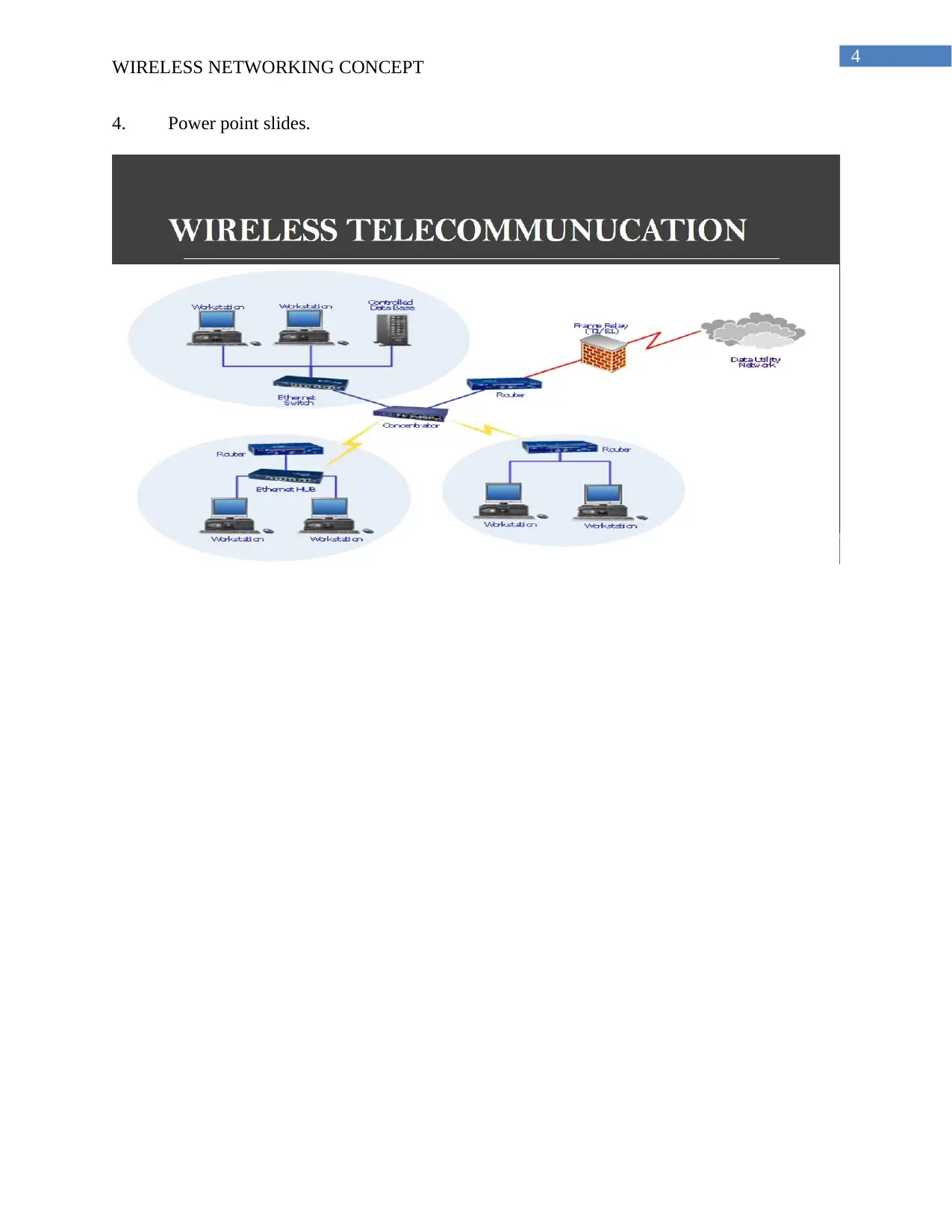
4. Power point slides.
WIRELESS NETWORKING CONCEPT
4. Power point slides.
5
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
8
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
11
WIRELESS NETWORKING CONCEPT
WIRELESS NETWORKING CONCEPT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





