University Wireless Networks and Communication Assignment
VerifiedAdded on 2022/10/14
|14
|798
|193
Homework Assignment
AI Summary
This assignment solution covers various aspects of wireless networks and communication, including modulation techniques like Amplitude Shift Keying, Frequency Shift Keying, Phase Shift Keying, and Differential Phase Shift Keying. It also explores Frequency Shift Keying with different bit combinations, analog and frequency modulation waveforms, and 16 QAM constellation diagrams. The solution delves into Cycle Redundancy Check (CRC) error detection, providing a step-by-step computation example. Furthermore, it addresses Direct Sequence Spread Spectrum (DSSS) signal transmission and the rationale behind using hexagonal cell shapes for cellular communication. The assignment provides answers to multiple questions, demonstrating a comprehensive understanding of wireless communication principles.

Running head: WIRELESS NETWORKS AND COMMUNICATION
WIRELESS NETWORKS AND COMMUNICATION
Name of the Student
Name of the University
Author Name
WIRELESS NETWORKS AND COMMUNICATION
Name of the Student
Name of the University
Author Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS NETWORKS AND COMMUNICATION
Table of Contents
1. Answer to question 1..............................................................................................................2
2. Answer to question 2..............................................................................................................6
3. Answer to question 3 :............................................................................................................7
4. Answer to question 4 :............................................................................................................8
5. Answer to question 5 :............................................................................................................9
6. Answer to question 6 :............................................................................................................9
7. Answer to question 7 :..........................................................................................................11
8. Answer to question 8 :..........................................................................................................12
Reference:................................................................................................................................13
Table of Contents
1. Answer to question 1..............................................................................................................2
2. Answer to question 2..............................................................................................................6
3. Answer to question 3 :............................................................................................................7
4. Answer to question 4 :............................................................................................................8
5. Answer to question 5 :............................................................................................................9
6. Answer to question 6 :............................................................................................................9
7. Answer to question 7 :..........................................................................................................11
8. Answer to question 8 :..........................................................................................................12
Reference:................................................................................................................................13

2WIRELESS NETWORKS AND COMMUNICATION
1. Answer to question 1 :
Modulation Techniques for converting binary data “110101” into analog waveforms.
A. Using Two level Amplitude Shift Keying :
1. Answer to question 1 :
Modulation Techniques for converting binary data “110101” into analog waveforms.
A. Using Two level Amplitude Shift Keying :
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3WIRELESS NETWORKS AND COMMUNICATION
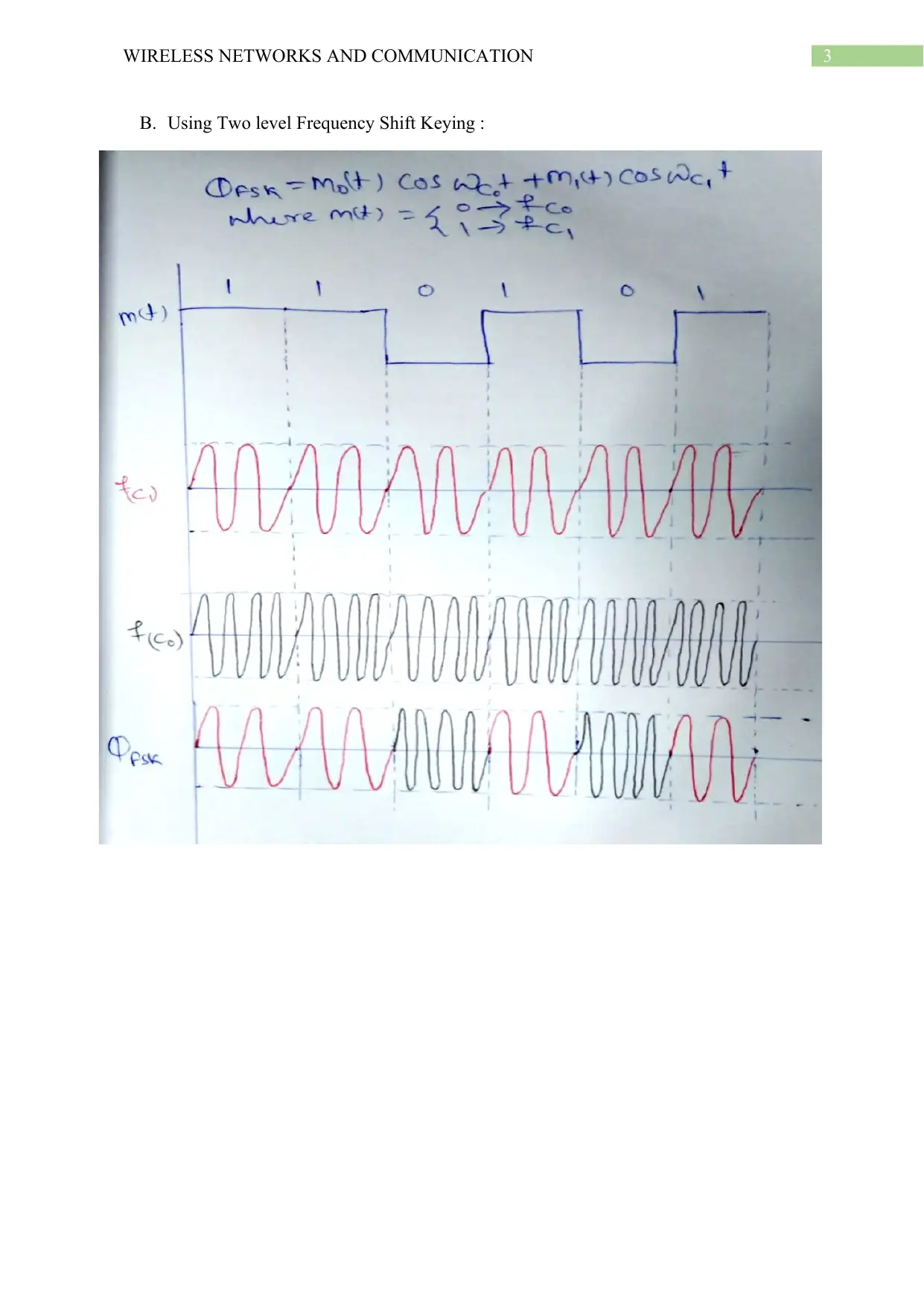
B. Using Two level Frequency Shift Keying :
B. Using Two level Frequency Shift Keying :
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4WIRELESS NETWORKS AND COMMUNICATION
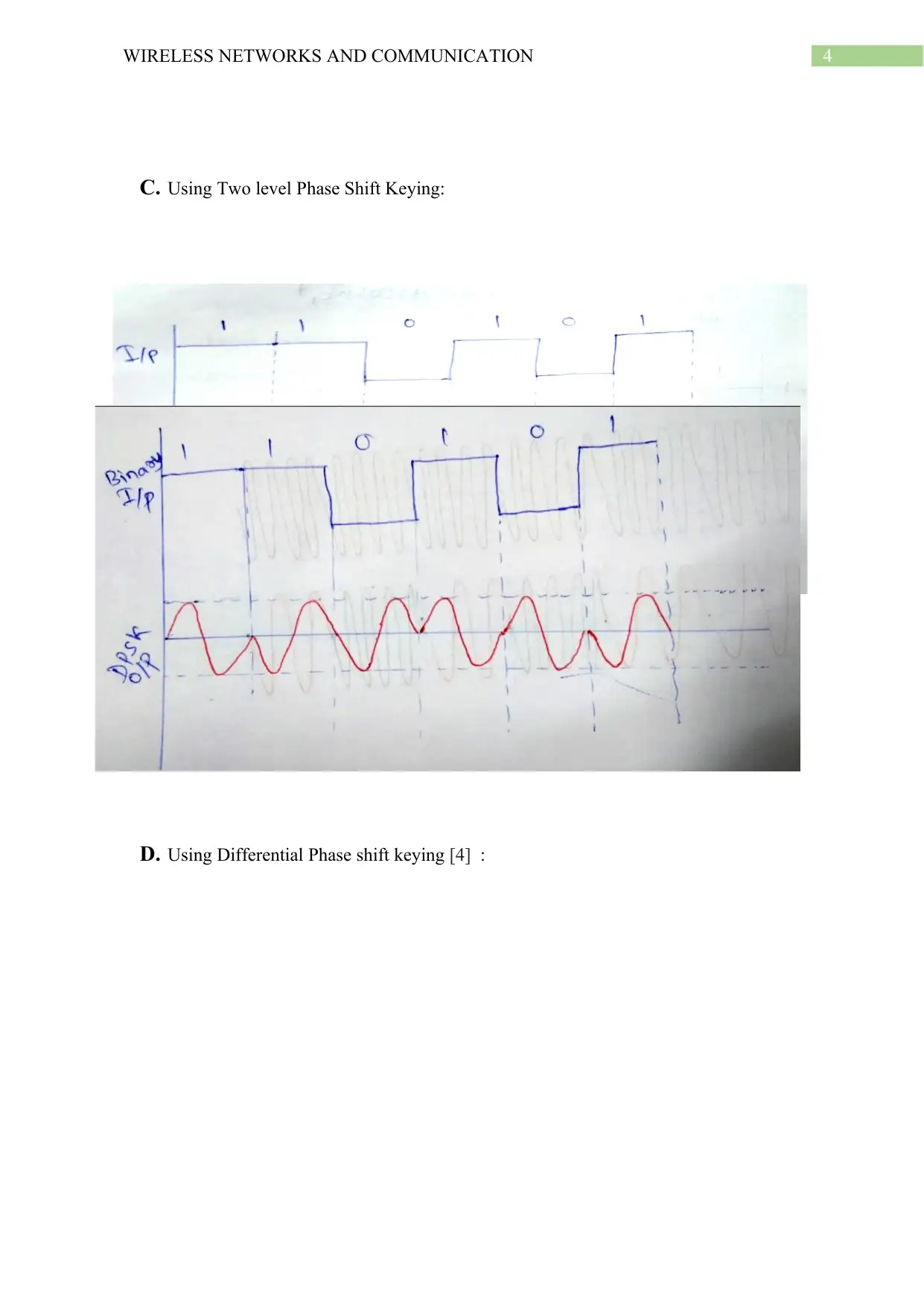
C. Using Two level Phase Shift Keying:
D. Using Differential Phase shift keying [4] :
C. Using Two level Phase Shift Keying:
D. Using Differential Phase shift keying [4] :
5WIRELESS NETWORKS AND COMMUNICATION
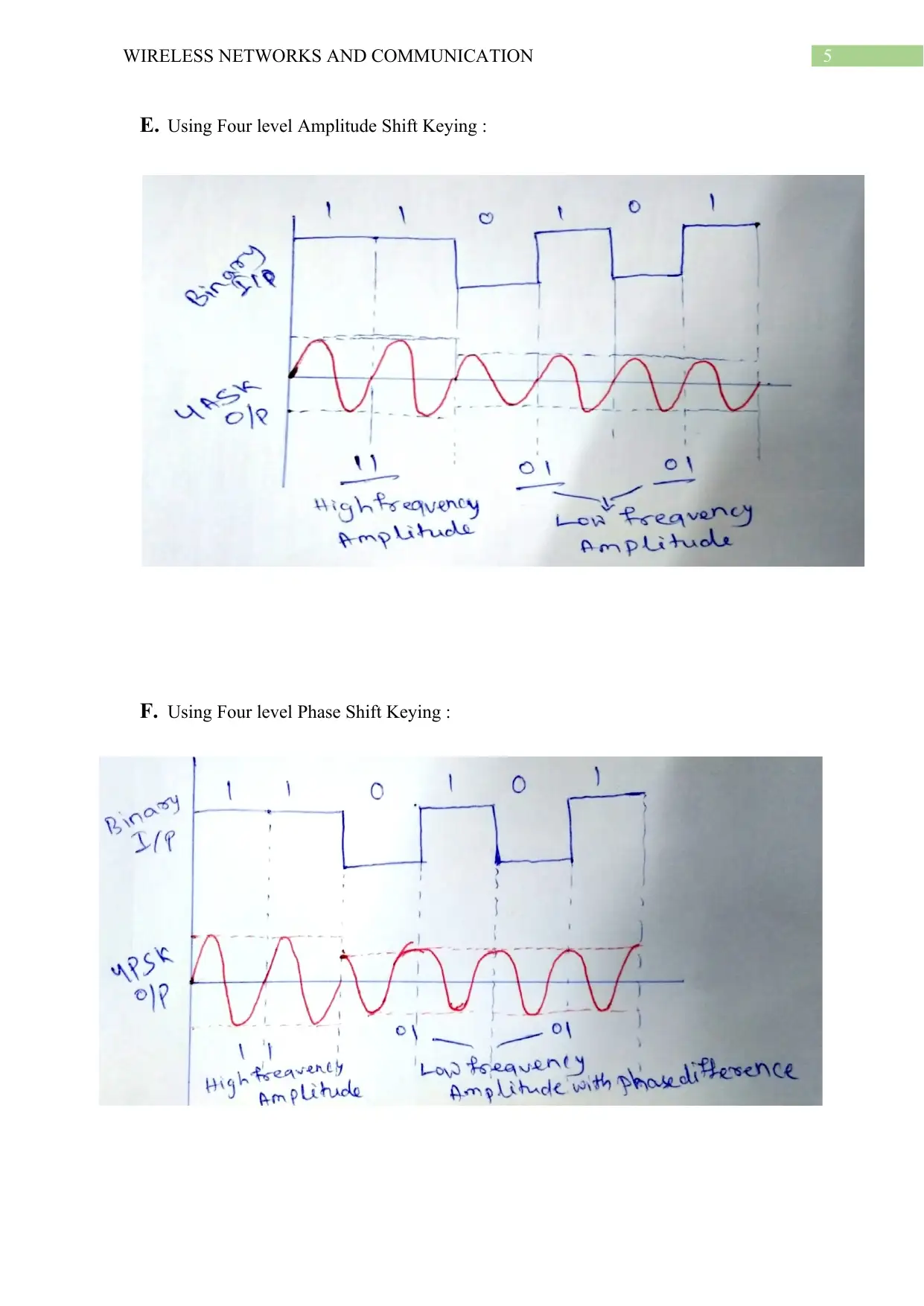
E. Using Four level Amplitude Shift Keying :
F. Using Four level Phase Shift Keying :
E. Using Four level Amplitude Shift Keying :
F. Using Four level Phase Shift Keying :
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6WIRELESS NETWORKS AND COMMUNICATION
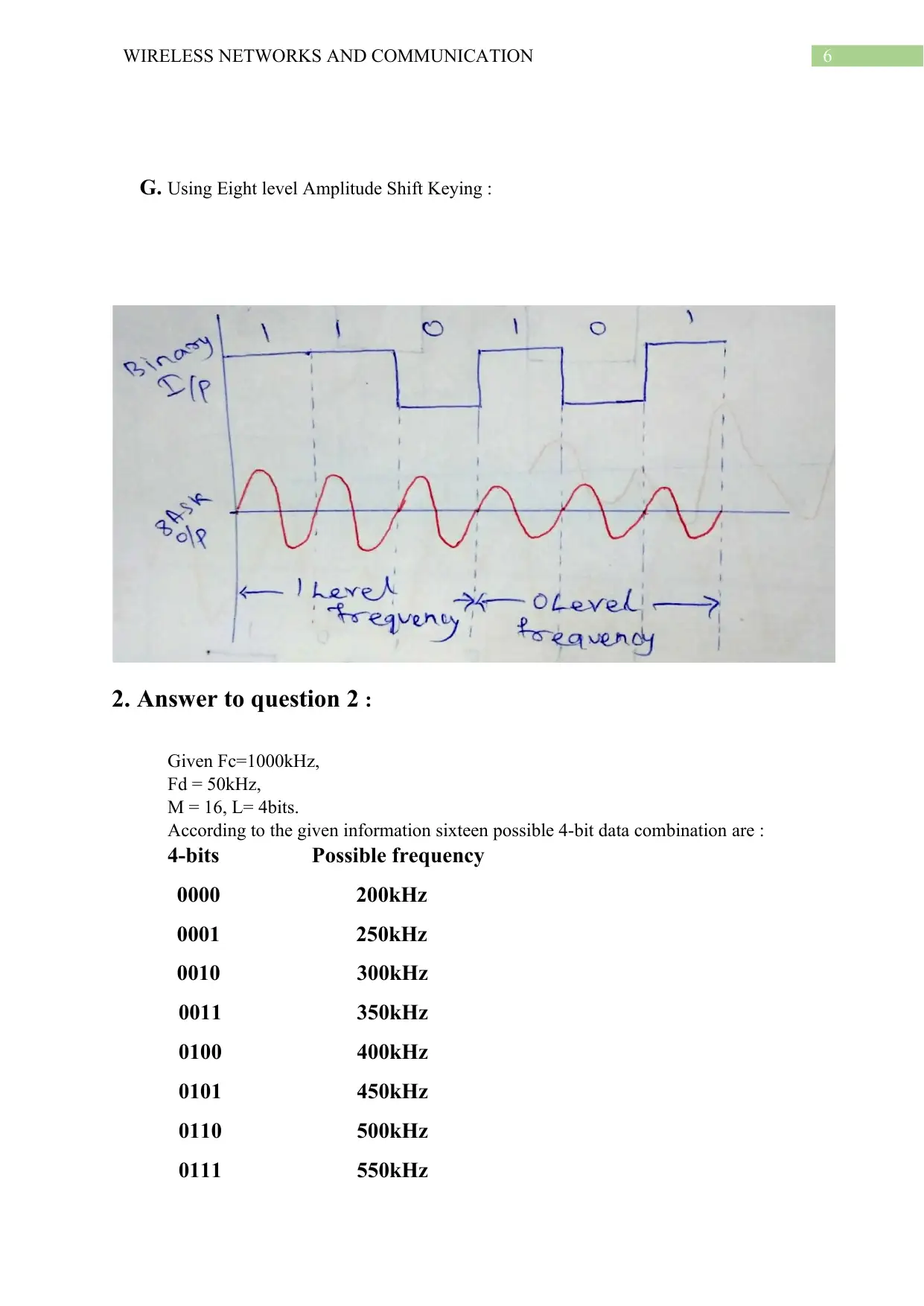
G. Using Eight level Amplitude Shift Keying :
2. Answer to question 2 :
Given Fc=1000kHz,
Fd = 50kHz,
M = 16, L= 4bits.
According to the given information sixteen possible 4-bit data combination are :
4-bits Possible frequency
0000 200kHz
0001 250kHz
0010 300kHz
0011 350kHz
0100 400kHz
0101 450kHz
0110 500kHz
0111 550kHz
G. Using Eight level Amplitude Shift Keying :
2. Answer to question 2 :
Given Fc=1000kHz,
Fd = 50kHz,
M = 16, L= 4bits.
According to the given information sixteen possible 4-bit data combination are :
4-bits Possible frequency
0000 200kHz
0001 250kHz
0010 300kHz
0011 350kHz
0100 400kHz
0101 450kHz
0110 500kHz
0111 550kHz
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7WIRELESS NETWORKS AND COMMUNICATION
1000 600kHz
1001 650kHz
1010 700kHz
1011 750kHz
1100 800kHz
1101 850kHz
1110 900kHz
1111 950kHz
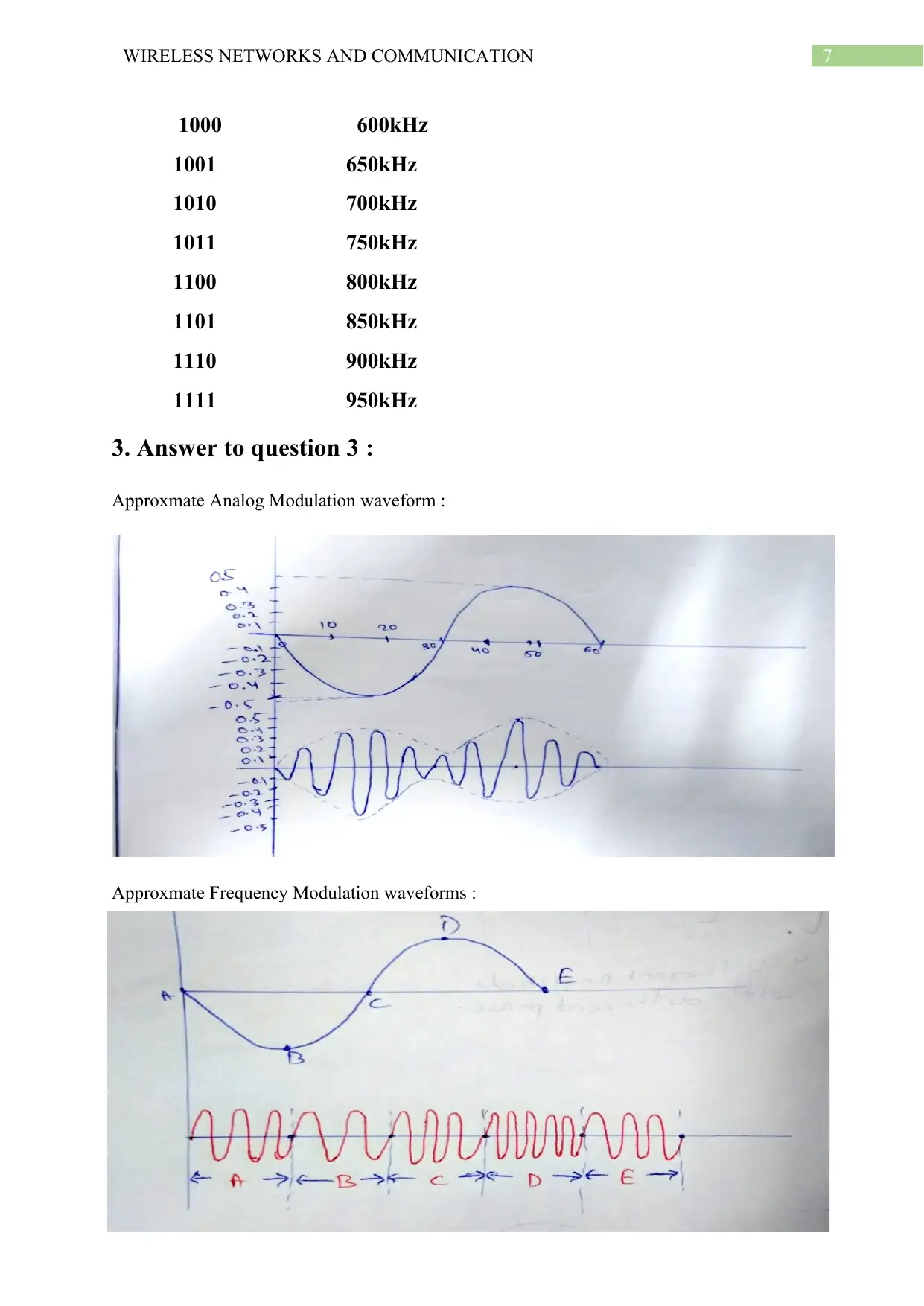
3. Answer to question 3 :
Approxmate Analog Modulation waveform :
Approxmate Frequency Modulation waveforms :
1000 600kHz
1001 650kHz
1010 700kHz
1011 750kHz
1100 800kHz
1101 850kHz
1110 900kHz
1111 950kHz
3. Answer to question 3 :
Approxmate Analog Modulation waveform :
Approxmate Frequency Modulation waveforms :
8WIRELESS NETWORKS AND COMMUNICATION
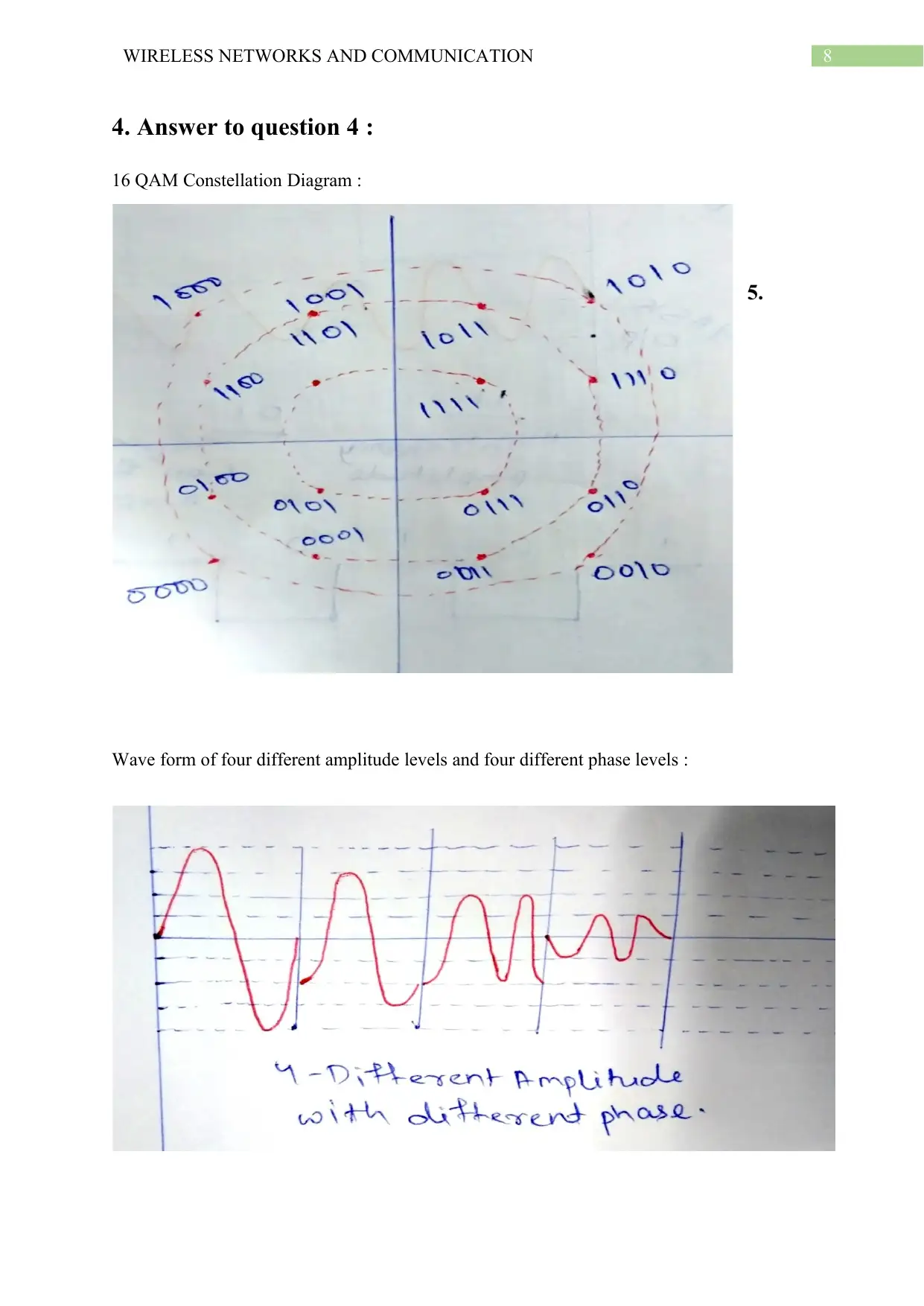
4. Answer to question 4 :
16 QAM Constellation Diagram :
5.
Wave form of four different amplitude levels and four different phase levels :
4. Answer to question 4 :
16 QAM Constellation Diagram :
5.
Wave form of four different amplitude levels and four different phase levels :
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9WIRELESS NETWORKS AND COMMUNICATION
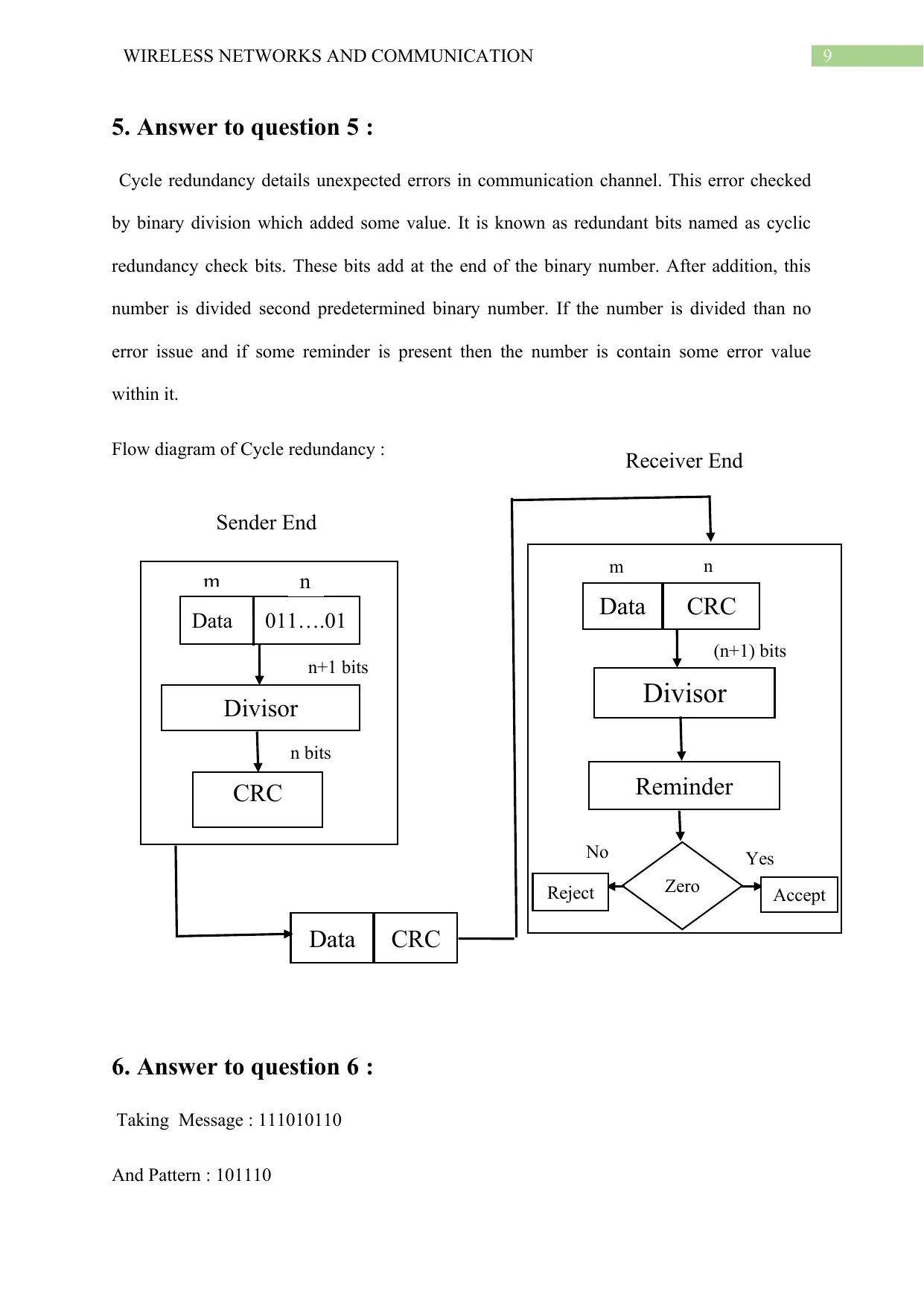
5. Answer to question 5 :
Cycle redundancy details unexpected errors in communication channel. This error checked
by binary division which added some value. It is known as redundant bits named as cyclic
redundancy check bits. These bits add at the end of the binary number. After addition, this
number is divided second predetermined binary number. If the number is divided than no
error issue and if some reminder is present then the number is contain some error value
within it.
Flow diagram of Cycle redundancy :
6. Answer to question 6 :
Taking Message : 111010110
And Pattern : 101110
Data 011….01
m n
Divisor
CRC
Data CRC
Data CRC
Divisor
Reminder
Zero AcceptReject
n+1 bits
n bits
m n
(n+1) bits
No Yes
Sender End
Receiver End
5. Answer to question 5 :
Cycle redundancy details unexpected errors in communication channel. This error checked
by binary division which added some value. It is known as redundant bits named as cyclic
redundancy check bits. These bits add at the end of the binary number. After addition, this
number is divided second predetermined binary number. If the number is divided than no
error issue and if some reminder is present then the number is contain some error value
within it.
Flow diagram of Cycle redundancy :
6. Answer to question 6 :
Taking Message : 111010110
And Pattern : 101110
Data 011….01
m n
Divisor
CRC
Data CRC
Data CRC
Divisor
Reminder
Zero AcceptReject
n+1 bits
n bits
m n
(n+1) bits
No Yes
Sender End
Receiver End
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10WIRELESS NETWORKS AND COMMUNICATION
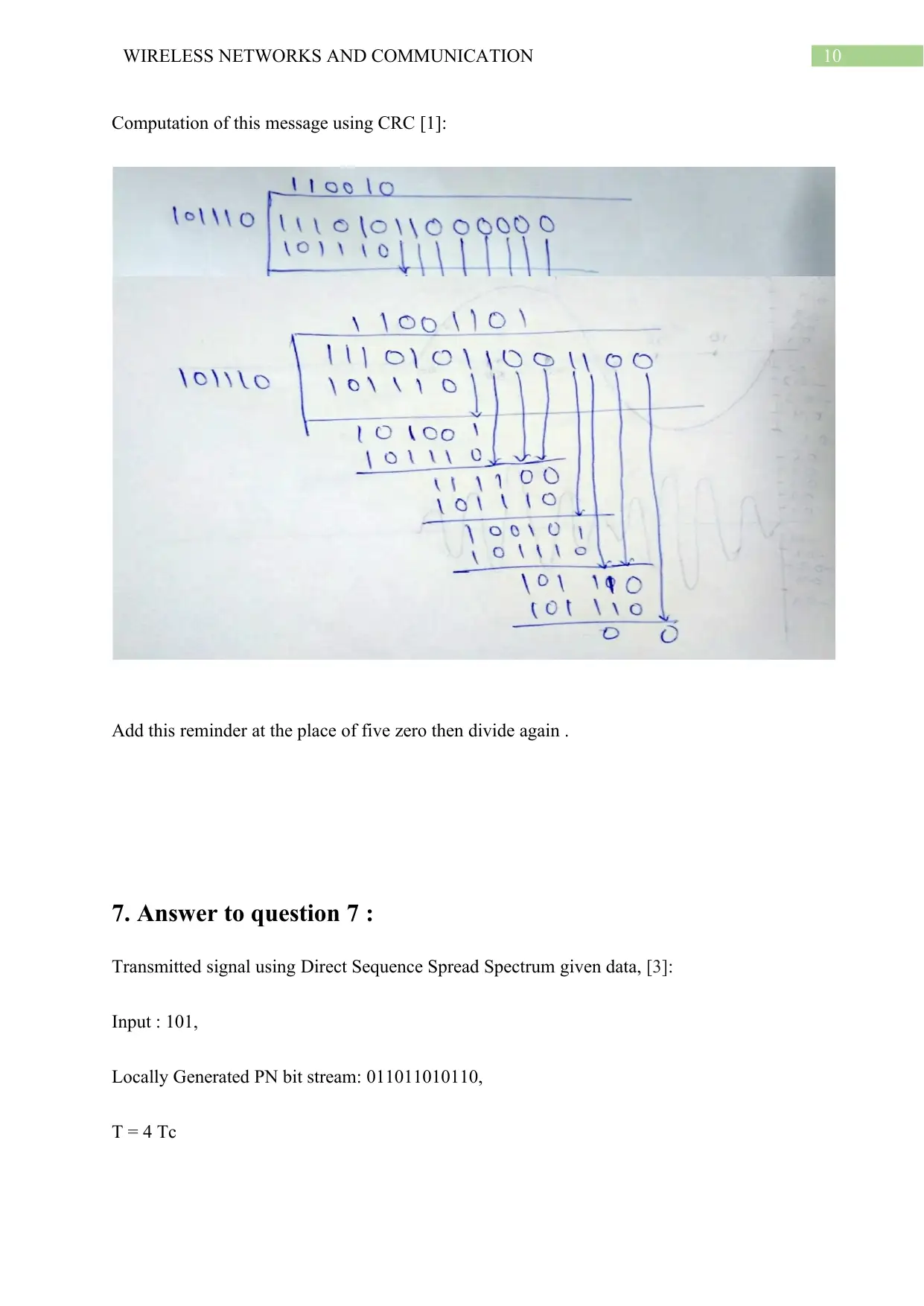
Computation of this message using CRC [1]:
Add this reminder at the place of five zero then divide again .
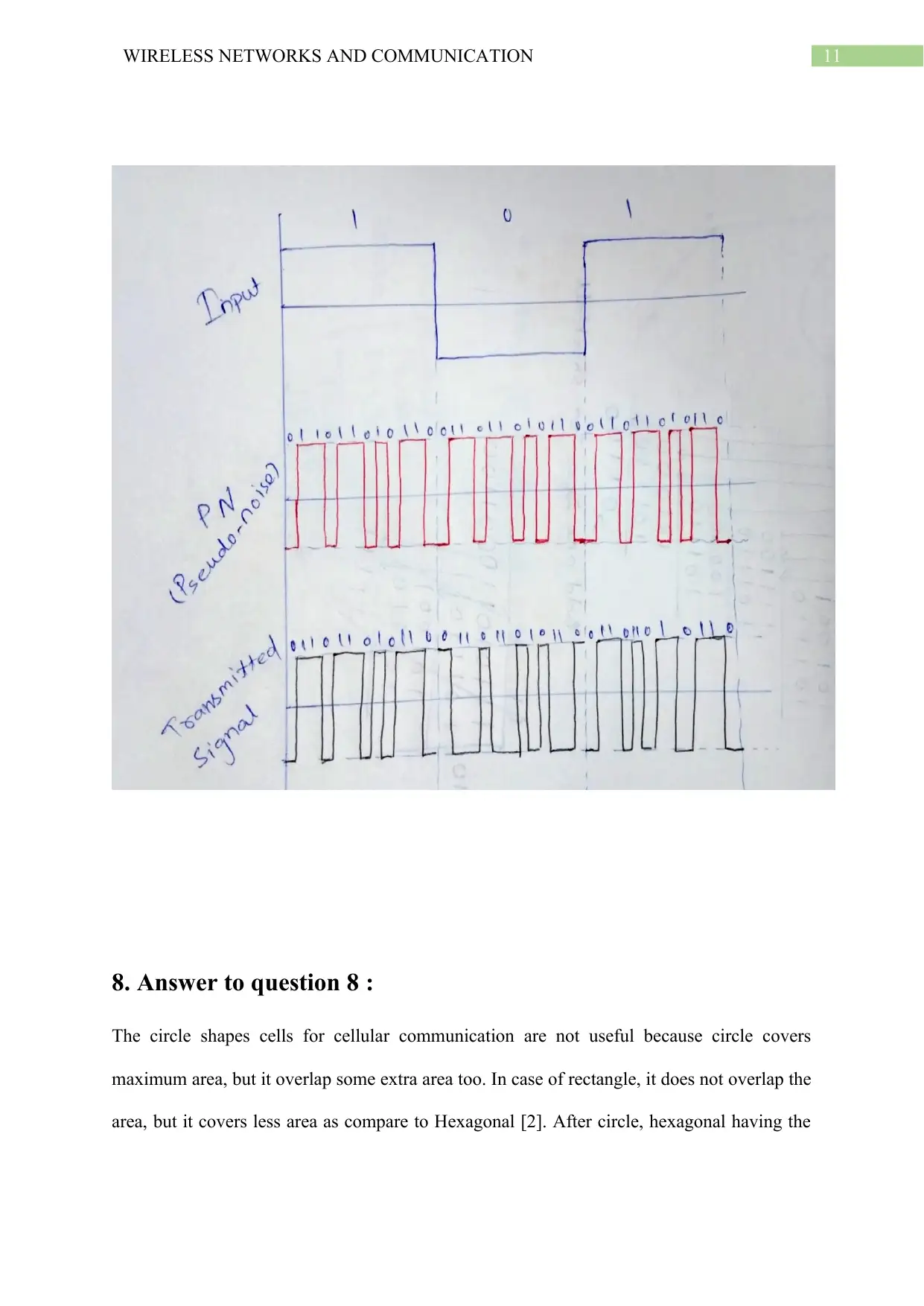
7. Answer to question 7 :
Transmitted signal using Direct Sequence Spread Spectrum given data, [3]:
Input : 101,
Locally Generated PN bit stream: 011011010110,
T = 4 Tc
Computation of this message using CRC [1]:
Add this reminder at the place of five zero then divide again .
7. Answer to question 7 :
Transmitted signal using Direct Sequence Spread Spectrum given data, [3]:
Input : 101,
Locally Generated PN bit stream: 011011010110,
T = 4 Tc
11WIRELESS NETWORKS AND COMMUNICATION
8. Answer to question 8 :
The circle shapes cells for cellular communication are not useful because circle covers
maximum area, but it overlap some extra area too. In case of rectangle, it does not overlap the
area, but it covers less area as compare to Hexagonal [2]. After circle, hexagonal having the
8. Answer to question 8 :
The circle shapes cells for cellular communication are not useful because circle covers
maximum area, but it overlap some extra area too. In case of rectangle, it does not overlap the
area, but it covers less area as compare to Hexagonal [2]. After circle, hexagonal having the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





