MITS5003 Assignment - Wireless Networks: Encoding, Access & Control
VerifiedAdded on 2023/06/10
|9
|992
|374
Homework Assignment
AI Summary
This assignment delves into wireless networks and communication, focusing on encoding, error control, multiplexing, and multiple access techniques. It begins by calculating the data rate for robot-to-controller communication and explores encoding methods like histogram encoding, kernel codebook encoding, and super vector encoding. Error control mechanisms such as Cyclic Redundancy Check (CRC), parity checking, and flow control protocols like Simplex Stop-and-Wait are discussed. The assignment then transitions to multiplexing, covering frequency division multiplexing, wavelength division multiplexing, and time-division multiplexing, along with Orthogonal Frequency Division Multiplexing (OFDM). Finally, it examines Wi-Fi network design, Basic Service Set (BSS), Extended Service Set (ESS), throughput, IEEE 802.11 standards, and security strategies.

WIRELESS NETWORKS AND COMMUNICATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Encoding and Error Control.....................................................................................................3
2. Multiplexing and Multiple Access...........................................................................................4
3. Wi-Fi........................................................................................................................................7
References........................................................................................................................................9
2
1. Encoding and Error Control.....................................................................................................3
2. Multiplexing and Multiple Access...........................................................................................4
3. Wi-Fi........................................................................................................................................7
References........................................................................................................................................9
2

1. Encoding and Error Control
a)
The required data rate for robot to wireless controller communication is up to 500 Hz.
b)
Histogram encoding (VQ)
Kernel codebook encoding (KCB)
Super vector encoding (SV)
c)
Error Control
The error control is end the exchange information from transmission application to an
accepting application likes numerous means and each subject to blunder (Agarwal, 2018).
Cyclic Redundancy Check
The CRC is the effective repetition checking strategy and it is depends on two fold
division of the information unit.
Equality checking
The equality checking is a solitary piece and it is used to display the quantity of 1 bit in
the first information like odd or even. The solitary piece event is changed in transmission, the
message will change the quality and the blunder can be identified now.
Flow Control
In data link layer, the flow control is the one of essential issues that controls the flow of
the information for beneficiary and sender. In communication layer, the flow control is
correspondence medium for beneficiary and sender.
Simplex Stop-and-Wait Protocol
In this Protocol we have taken the accompanying suppositions:
It gives unidirectional Flow of information from sender to recipient.
The Communication channel is thought to be without blunder.
In this Protocol the Sender basically sends information and sits tight for the affirmation from
Receiver. That is the reason it is called Stop-and-Wait Protocol. This write isn't so much
effective; however it is least complex method for Flow Control. In this plan we take
Communication Channel mistake free, however in the event that the Channel has a few blunders
3
a)
The required data rate for robot to wireless controller communication is up to 500 Hz.
b)
Histogram encoding (VQ)
Kernel codebook encoding (KCB)
Super vector encoding (SV)
c)
Error Control
The error control is end the exchange information from transmission application to an
accepting application likes numerous means and each subject to blunder (Agarwal, 2018).
Cyclic Redundancy Check
The CRC is the effective repetition checking strategy and it is depends on two fold
division of the information unit.
Equality checking
The equality checking is a solitary piece and it is used to display the quantity of 1 bit in
the first information like odd or even. The solitary piece event is changed in transmission, the
message will change the quality and the blunder can be identified now.
Flow Control
In data link layer, the flow control is the one of essential issues that controls the flow of
the information for beneficiary and sender. In communication layer, the flow control is
correspondence medium for beneficiary and sender.
Simplex Stop-and-Wait Protocol
In this Protocol we have taken the accompanying suppositions:
It gives unidirectional Flow of information from sender to recipient.
The Communication channel is thought to be without blunder.
In this Protocol the Sender basically sends information and sits tight for the affirmation from
Receiver. That is the reason it is called Stop-and-Wait Protocol. This write isn't so much
effective; however it is least complex method for Flow Control. In this plan we take
Communication Channel mistake free, however in the event that the Channel has a few blunders
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
then beneficiary can't get the right information from sender so it won't feasible for sender to send
the following information (since it won't get recognize from collector). So it will end the
correspondence, to take care of this issue there are two new ideas were presented ("Flow and
Error Control Techniques", 2018)
2. Multiplexing and Multiple Access
a)
Multiplexing is used to joins advanced and simple signs headed for transmission via PC
channel and solitary correspondence line. Sorts of Multiplexing Distinctive sort of multiplexing
is utilized as a part of correspondence. In this article, the accompanying three noteworthy
multiplexing methods are examined:
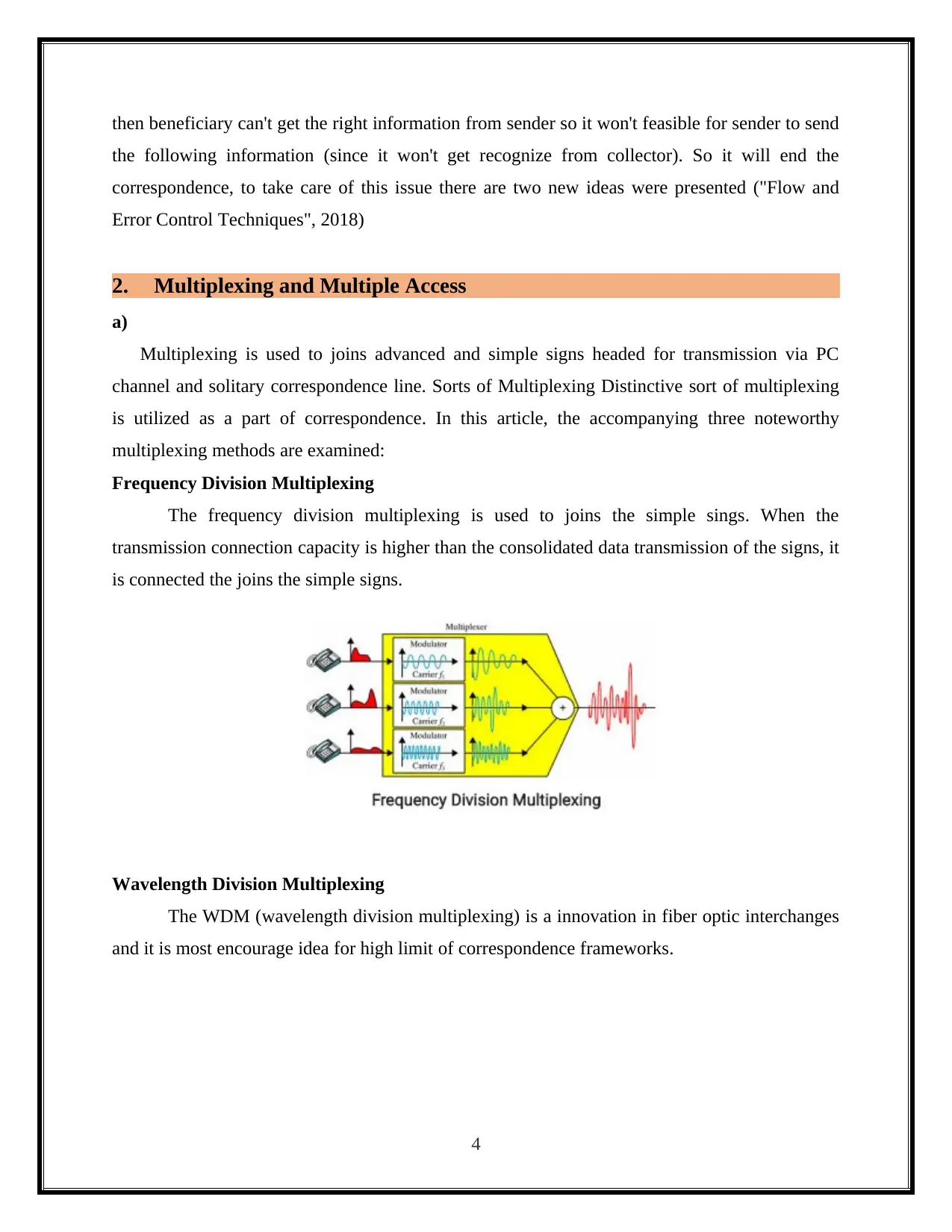
Frequency Division Multiplexing
The frequency division multiplexing is used to joins the simple sings. When the
transmission connection capacity is higher than the consolidated data transmission of the signs, it
is connected the joins the simple signs.
Wavelength Division Multiplexing
The WDM (wavelength division multiplexing) is a innovation in fiber optic interchanges
and it is most encourage idea for high limit of correspondence frameworks.
4
the following information (since it won't get recognize from collector). So it will end the
correspondence, to take care of this issue there are two new ideas were presented ("Flow and
Error Control Techniques", 2018)
2. Multiplexing and Multiple Access
a)
Multiplexing is used to joins advanced and simple signs headed for transmission via PC
channel and solitary correspondence line. Sorts of Multiplexing Distinctive sort of multiplexing
is utilized as a part of correspondence. In this article, the accompanying three noteworthy
multiplexing methods are examined:
Frequency Division Multiplexing
The frequency division multiplexing is used to joins the simple sings. When the
transmission connection capacity is higher than the consolidated data transmission of the signs, it
is connected the joins the simple signs.
Wavelength Division Multiplexing
The WDM (wavelength division multiplexing) is a innovation in fiber optic interchanges
and it is most encourage idea for high limit of correspondence frameworks.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
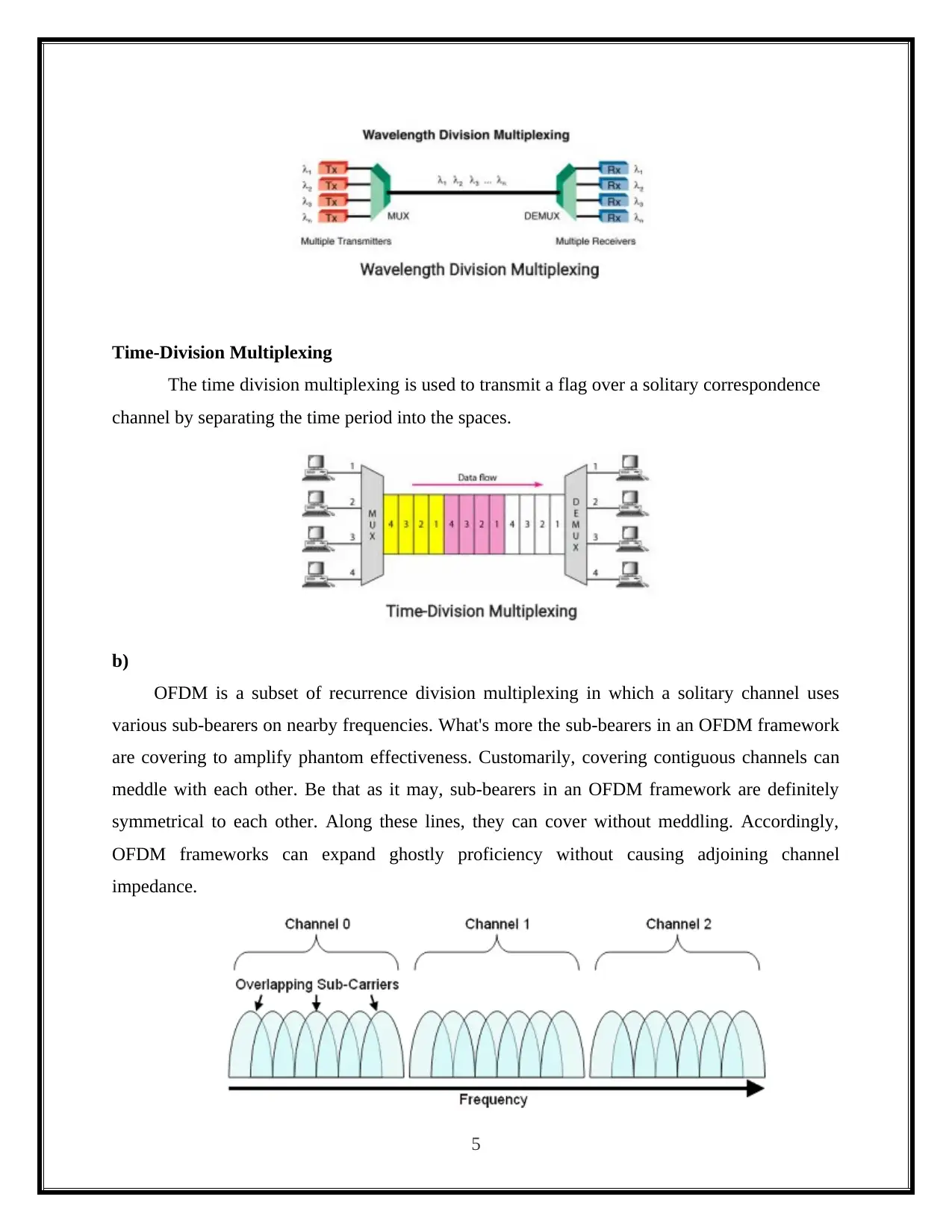
Time-Division Multiplexing
The time division multiplexing is used to transmit a flag over a solitary correspondence
channel by separating the time period into the spaces.
b)
OFDM is a subset of recurrence division multiplexing in which a solitary channel uses
various sub-bearers on nearby frequencies. What's more the sub-bearers in an OFDM framework
are covering to amplify phantom effectiveness. Customarily, covering contiguous channels can
meddle with each other. Be that as it may, sub-bearers in an OFDM framework are definitely
symmetrical to each other. Along these lines, they can cover without meddling. Accordingly,
OFDM frameworks can expand ghostly proficiency without causing adjoining channel
impedance.
5
The time division multiplexing is used to transmit a flag over a solitary correspondence
channel by separating the time period into the spaces.
b)
OFDM is a subset of recurrence division multiplexing in which a solitary channel uses
various sub-bearers on nearby frequencies. What's more the sub-bearers in an OFDM framework
are covering to amplify phantom effectiveness. Customarily, covering contiguous channels can
meddle with each other. Be that as it may, sub-bearers in an OFDM framework are definitely
symmetrical to each other. Along these lines, they can cover without meddling. Accordingly,
OFDM frameworks can expand ghostly proficiency without causing adjoining channel
impedance.
5

c)
i)
Bandwidth - 20MHz
ii)
The subset of recurrence division multiplexing is called as OFDM and it is a solitary
channel uses the various sub bearers on nearby frequencies. These subcarriers can be halfway
cover without meddling with contiguous sub-bearers in light of the fact that the most extreme
intensity of each subcarrier relates specifically with the base intensity of each neighboring
channel. Beneath, we outline the recurrence space of an OFDM framework graphically. As
should be obvious from the figure, each sub-carrier is spoken to by an alternate pinnacle.
Likewise, the pinnacle of each sub-carrier relates specifically with the zero intersection all things
considered.
iii)
ISI is normally produced when transmitting in a multipath blurring channel. In this sort of
channel, numerous duplicates of the transmitted flag are gotten at various time interims, which
cause interference. For effortlessness, how about we expect that we have an OFDM transmission
of two OFDM images with two stacked subcarriers.
3. Wi-Fi
a)
Network Design
6
i)
Bandwidth - 20MHz
ii)
The subset of recurrence division multiplexing is called as OFDM and it is a solitary
channel uses the various sub bearers on nearby frequencies. These subcarriers can be halfway
cover without meddling with contiguous sub-bearers in light of the fact that the most extreme
intensity of each subcarrier relates specifically with the base intensity of each neighboring
channel. Beneath, we outline the recurrence space of an OFDM framework graphically. As
should be obvious from the figure, each sub-carrier is spoken to by an alternate pinnacle.
Likewise, the pinnacle of each sub-carrier relates specifically with the zero intersection all things
considered.
iii)
ISI is normally produced when transmitting in a multipath blurring channel. In this sort of
channel, numerous duplicates of the transmitted flag are gotten at various time interims, which
cause interference. For effortlessness, how about we expect that we have an OFDM transmission
of two OFDM images with two stacked subcarriers.
3. Wi-Fi
a)
Network Design
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
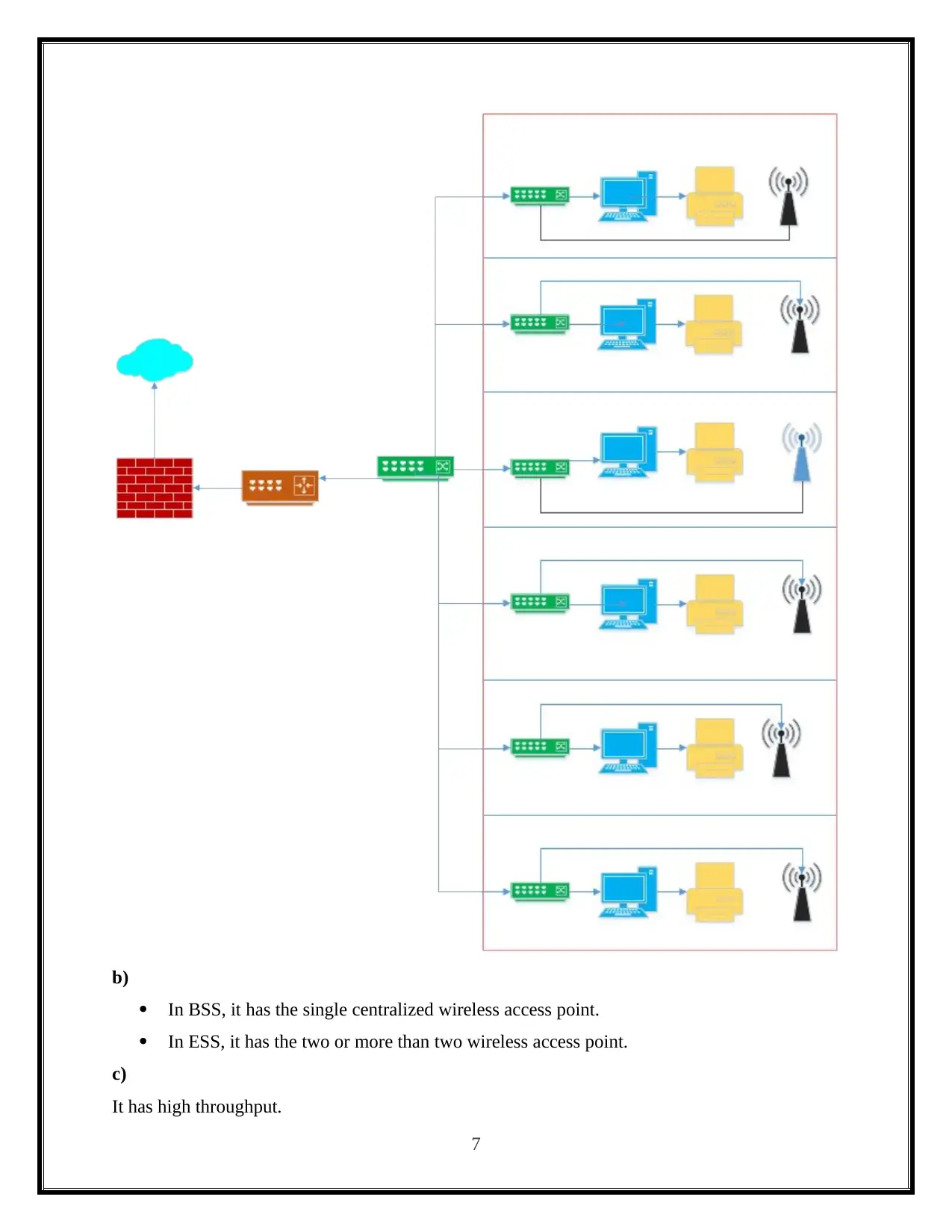
b)
In BSS, it has the single centralized wireless access point.
In ESS, it has the two or more than two wireless access point.
c)
It has high throughput.
7
In BSS, it has the single centralized wireless access point.
In ESS, it has the two or more than two wireless access point.
c)
It has high throughput.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

d)
IEEE 802.11
The IEEE 802.11 wireless LAN is used to provide the free system access between the
processing gadgets by utilizing the radio waves instead of a link foundation. It is generally
intended to information of transmission framework. Across the board acknowledgment of
WLANs relies based on industry institutionalization to guarantee item similarity and
dependability among the various makers.
e)
Security Strategy
The security strategy is used to minimize the possible threats and attacks by implement
the security policies and controls.
References
8
IEEE 802.11
The IEEE 802.11 wireless LAN is used to provide the free system access between the
processing gadgets by utilizing the radio waves instead of a link foundation. It is generally
intended to information of transmission framework. Across the board acknowledgment of
WLANs relies based on industry institutionalization to guarantee item similarity and
dependability among the various makers.
e)
Security Strategy
The security strategy is used to minimize the possible threats and attacks by implement
the security policies and controls.
References
8

Agarwal, T. (2018). What are the different Types of Multiplexing in communication system?.
Retrieved from https://www.edgefx.in/what-are-the-different-types-of-multiplexing-in-
communication-system/
Flow and Error Control Techniques. (2018). Retrieved from https://gradeup.co/flow-and-error-
control-techniques-i-28750a29-ba8d-11e5-b537-dcac2f2dd7d1
9
Retrieved from https://www.edgefx.in/what-are-the-different-types-of-multiplexing-in-
communication-system/
Flow and Error Control Techniques. (2018). Retrieved from https://gradeup.co/flow-and-error-
control-techniques-i-28750a29-ba8d-11e5-b537-dcac2f2dd7d1
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
