Wireless Network and Security Assessment: Analysis and Recommendations
VerifiedAdded on 2020/02/23
|14
|2305
|61
Report
AI Summary
This report details an analysis of wireless network security, focusing on the use of Acrylic Wi-Fi for network sniffing and vulnerability assessment in a public setting. The study encompasses recording WLAN access points, gathering network information, and utilizing Acrylic Wi-Fi to test the network's security posture. The report explores the MAC addresses, signal strengths, encryption types (WPA, WPA2), and channel usage of available networks. Furthermore, it presents recommendations for enhancing WLAN security, including the implementation of dual-band access points, network penetration testing, and secure configuration practices. The report also includes tables, screenshots, and explanations of techniques applied for network management and security, emphasizing the importance of a robust security approach in wireless network deployments.

Running head: WIRELESS NETWORK AND SECURITY
Wireless Network and Security
Name of the Student
Name of the University
Author’s Note
Wireless Network and Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORK AND SECURITY
Table of Contents
1. Recording the WLAN AP at the Public Place.................................................................2
2. Gathered information from the wireless network............................................................3
3. Use of Acrylic Wi Fi sniffing tool for testing the wireless network...............................4
4. Recommendations for improvement of the WLAN security...........................................6
a. Tables for location.......................................................................................................6
b. Screenshots..................................................................................................................8
c. Explanation of techniques applied for management and securing the network.........10
i. Application of dual bands and its advantage..........................................................10
ii. Security Implication..............................................................................................10
iii. Other Aspects.......................................................................................................10
Bibliography......................................................................................................................12
WIRELESS NETWORK AND SECURITY
Table of Contents
1. Recording the WLAN AP at the Public Place.................................................................2
2. Gathered information from the wireless network............................................................3
3. Use of Acrylic Wi Fi sniffing tool for testing the wireless network...............................4
4. Recommendations for improvement of the WLAN security...........................................6
a. Tables for location.......................................................................................................6
b. Screenshots..................................................................................................................8
c. Explanation of techniques applied for management and securing the network.........10
i. Application of dual bands and its advantage..........................................................10
ii. Security Implication..............................................................................................10
iii. Other Aspects.......................................................................................................10
Bibliography......................................................................................................................12

2
WIRELESS NETWORK AND SECURITY
1. Recording the WLAN AP at the Public Place
For recording the WLAN interface a public place is chosen and the information of the
wireless network are recorded using the Acrylic Wi Fi network sniffing tool. It helps in recording
different wireless network within the range of the wireless adapter of the testing device. The risk
associated with the wireless network can also be analyzed with the help of the network sniffing
tool and thus help in securing the wireless access point [8]. There are distinctive different
instruments accessible additionally that can be connected for the investigation of the remote
system at general location. The MAC address of the wireless adapter, signal strength and quality,
used standards, RSSI, Channel, most extreme speed, WEP, WPA, WPA2, WPS, and Vendor, can
be examined utilizing the apparatus [12]. In addition the signal quality and strength directs
working in 2.4 GHz or 5 Ghz can be known and it creates a measurements of the system. The
entrance point list can be generated using the Acrylic network sniffing tool and it helps to
measure the vulnerability of the remote system. The region of scope of the system can likewise
be found from the sniffing instrument and it can discover the stream of information and discover
the range to pick the best remote association introduced in the system. The area of coverage and
the signal quality generated from the wireless access point can likewise examined by the system
sniffing device [5]. The quantity of channels gave by the remote access point can likewise be
discovered utilizing the Acrylic Wi-Fi device and it can be utilized for breaking down the
execution of the remote system.
WIRELESS NETWORK AND SECURITY
1. Recording the WLAN AP at the Public Place
For recording the WLAN interface a public place is chosen and the information of the
wireless network are recorded using the Acrylic Wi Fi network sniffing tool. It helps in recording
different wireless network within the range of the wireless adapter of the testing device. The risk
associated with the wireless network can also be analyzed with the help of the network sniffing
tool and thus help in securing the wireless access point [8]. There are distinctive different
instruments accessible additionally that can be connected for the investigation of the remote
system at general location. The MAC address of the wireless adapter, signal strength and quality,
used standards, RSSI, Channel, most extreme speed, WEP, WPA, WPA2, WPS, and Vendor, can
be examined utilizing the apparatus [12]. In addition the signal quality and strength directs
working in 2.4 GHz or 5 Ghz can be known and it creates a measurements of the system. The
entrance point list can be generated using the Acrylic network sniffing tool and it helps to
measure the vulnerability of the remote system. The region of scope of the system can likewise
be found from the sniffing instrument and it can discover the stream of information and discover
the range to pick the best remote association introduced in the system. The area of coverage and
the signal quality generated from the wireless access point can likewise examined by the system
sniffing device [5]. The quantity of channels gave by the remote access point can likewise be
discovered utilizing the Acrylic Wi-Fi device and it can be utilized for breaking down the
execution of the remote system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRELESS NETWORK AND SECURITY
Figure 1: Wireless network available near the testing place
The remote system found close to the testing zone are broke down and a testing is done
on the system for finding the defenselessness and the hazard related with the system. The
entrance point are secured with various algorithm, for example, WPA, WPA2 and the rendition
of the WPS utilized can likewise be examined utilizing the Acrylic network sniffer. The area of
coverage of the access point is analyzed and the transmission capacity and the bandwidth can
also be noted using the tool.
2. Gathered information from the wireless network
For the arranging of the Wireless framework particular criteria are required to be seen as,
testing of the banner degree, testing of the execution of the framework, testing of the security
shortcoming, affirmation and affirmation testing and pilot testing of the framework. The Wi Fi
signals are created from the remote access centers and for testing the extent of the banner a
WIRELESS NETWORK AND SECURITY
Figure 1: Wireless network available near the testing place
The remote system found close to the testing zone are broke down and a testing is done
on the system for finding the defenselessness and the hazard related with the system. The
entrance point are secured with various algorithm, for example, WPA, WPA2 and the rendition
of the WPS utilized can likewise be examined utilizing the Acrylic network sniffer. The area of
coverage of the access point is analyzed and the transmission capacity and the bandwidth can
also be noted using the tool.
2. Gathered information from the wireless network
For the arranging of the Wireless framework particular criteria are required to be seen as,
testing of the banner degree, testing of the execution of the framework, testing of the security
shortcoming, affirmation and affirmation testing and pilot testing of the framework. The Wi Fi
signals are created from the remote access centers and for testing the extent of the banner a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
WIRELESS NETWORK AND SECURITY
banner meter is used and it evaluates the banner regards that are required for covering the regions
[10]. The helpful need of the business is analyzed for testing the handiness of the remote plan
and the security approach took after for the headway of the framework is moreover examined.
The procedure includes the plan of the structure and standards and traditions took after for the
headway of the remote framework. The present framework uses the 802.11 standard and
WPA/AES tradition is taken after for securing the passage point [2]. There is a need of security
assessment and checking the security status of the framework and the deficiently masterminded
get to point. The Wi fi get the opportunity to point is required to be poor down with wire shark
and the passage point is organized with the default security settings i.e. the dormancy time out
and confine parameters are not organized.
The passage point is required to be secured and the unused organization traditions are
required to be debilitated for growing the security of the framework. The SSID are appeared as
the name of the framework and the framework is divided for avoiding any risk from the
malignant framework. The present framework is delivered following the client to client
technique for transmission and in this manner the remote stations are related in the framework by
methods for the passageway point. The correspondence of the client are controlled using
particular framework correspondence traditions and there is a need of key security patches.
3. Use of Acrylic Wi Fi sniffing tool for testing the wireless network
Acrylic Wi-Fi sniffing tool is used for sniffing the remote framework close to the testing
zone and a fundamental testing is done on the present framework circumstance and recognize the
torpidity of the framework. A framework score is made and the purposes of enthusiasm of the
transmission limit, torpidity, jitter, ping mishap and security of the framework can be gotten
from the gadget [1]. The obstacle of the remote framework is discussed and peril control
WIRELESS NETWORK AND SECURITY
banner meter is used and it evaluates the banner regards that are required for covering the regions
[10]. The helpful need of the business is analyzed for testing the handiness of the remote plan
and the security approach took after for the headway of the framework is moreover examined.
The procedure includes the plan of the structure and standards and traditions took after for the
headway of the remote framework. The present framework uses the 802.11 standard and
WPA/AES tradition is taken after for securing the passage point [2]. There is a need of security
assessment and checking the security status of the framework and the deficiently masterminded
get to point. The Wi fi get the opportunity to point is required to be poor down with wire shark
and the passage point is organized with the default security settings i.e. the dormancy time out
and confine parameters are not organized.
The passage point is required to be secured and the unused organization traditions are
required to be debilitated for growing the security of the framework. The SSID are appeared as
the name of the framework and the framework is divided for avoiding any risk from the
malignant framework. The present framework is delivered following the client to client
technique for transmission and in this manner the remote stations are related in the framework by
methods for the passageway point. The correspondence of the client are controlled using
particular framework correspondence traditions and there is a need of key security patches.
3. Use of Acrylic Wi Fi sniffing tool for testing the wireless network
Acrylic Wi-Fi sniffing tool is used for sniffing the remote framework close to the testing
zone and a fundamental testing is done on the present framework circumstance and recognize the
torpidity of the framework. A framework score is made and the purposes of enthusiasm of the
transmission limit, torpidity, jitter, ping mishap and security of the framework can be gotten
from the gadget [1]. The obstacle of the remote framework is discussed and peril control
5
WIRELESS NETWORK AND SECURITY
procedure that can be associated for extending the security of the remote framework is analyzed
in the report. Particular encryption frameworks that can be associated is also inspected and the
best practice that the affiliation can apply for the headway of the remote framework is in like
manner discussed in the report.
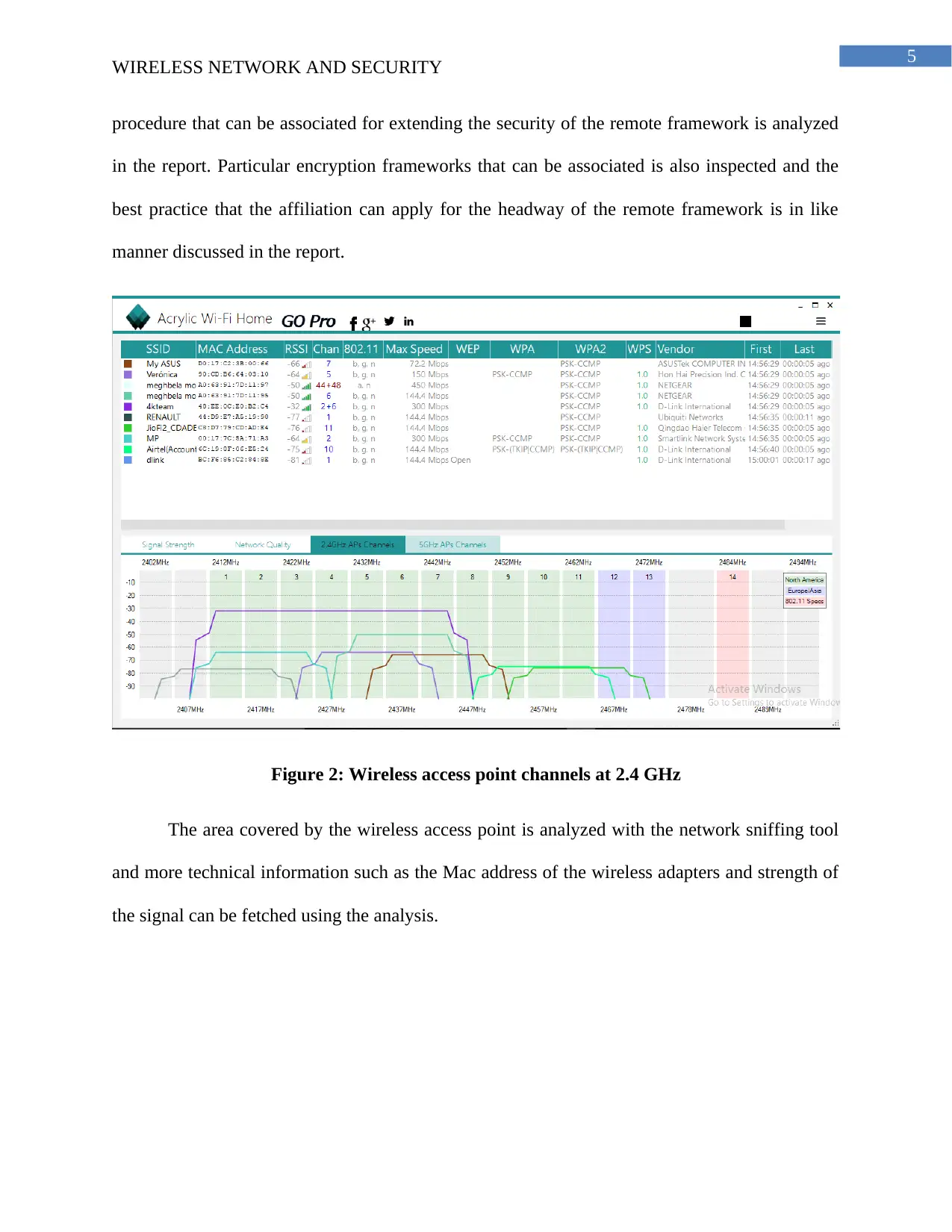
Figure 2: Wireless access point channels at 2.4 GHz
The area covered by the wireless access point is analyzed with the network sniffing tool
and more technical information such as the Mac address of the wireless adapters and strength of
the signal can be fetched using the analysis.
WIRELESS NETWORK AND SECURITY
procedure that can be associated for extending the security of the remote framework is analyzed
in the report. Particular encryption frameworks that can be associated is also inspected and the
best practice that the affiliation can apply for the headway of the remote framework is in like
manner discussed in the report.
Figure 2: Wireless access point channels at 2.4 GHz
The area covered by the wireless access point is analyzed with the network sniffing tool
and more technical information such as the Mac address of the wireless adapters and strength of
the signal can be fetched using the analysis.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRELESS NETWORK AND SECURITY
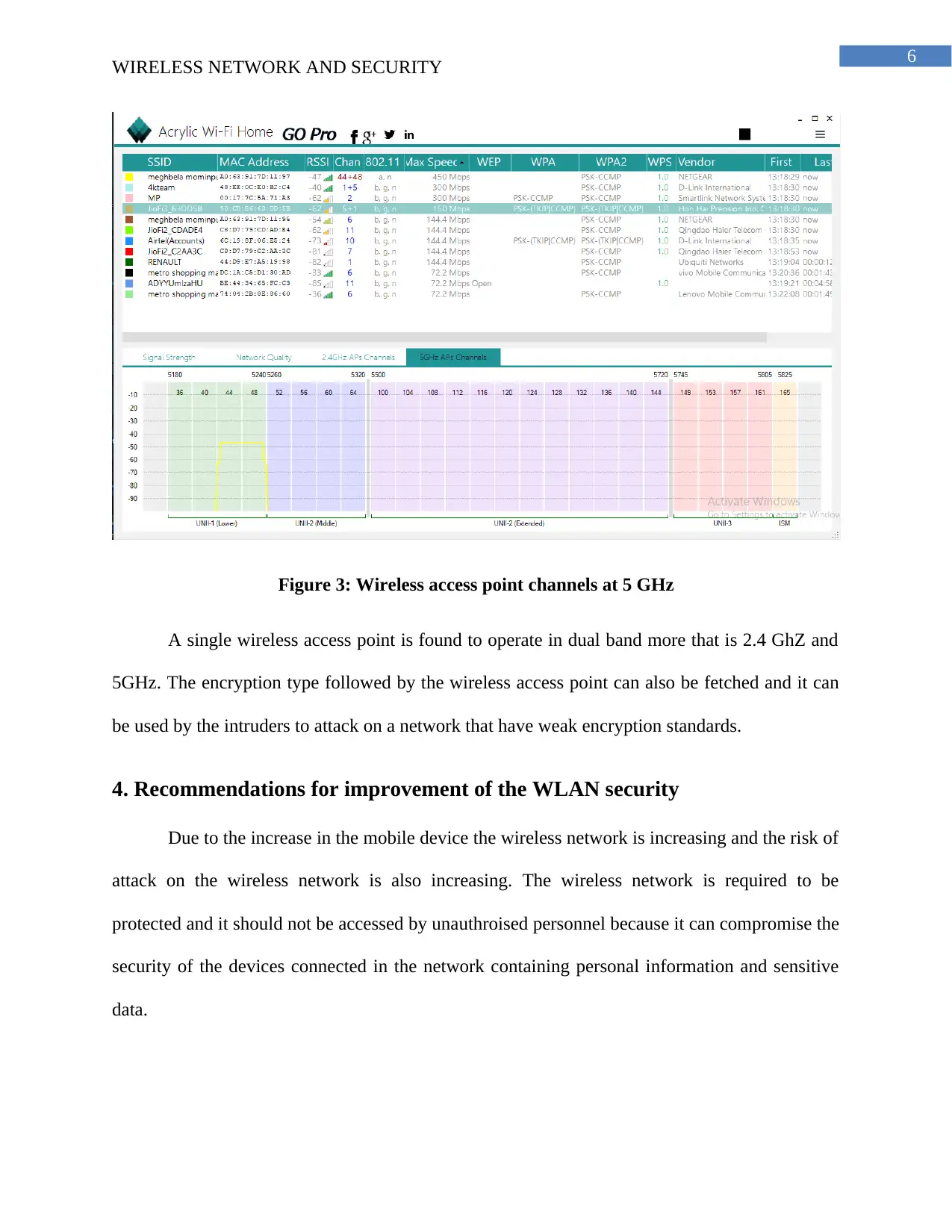
Figure 3: Wireless access point channels at 5 GHz
A single wireless access point is found to operate in dual band more that is 2.4 GhZ and
5GHz. The encryption type followed by the wireless access point can also be fetched and it can
be used by the intruders to attack on a network that have weak encryption standards.
4. Recommendations for improvement of the WLAN security
Due to the increase in the mobile device the wireless network is increasing and the risk of
attack on the wireless network is also increasing. The wireless network is required to be
protected and it should not be accessed by unauthroised personnel because it can compromise the
security of the devices connected in the network containing personal information and sensitive
data.
WIRELESS NETWORK AND SECURITY
Figure 3: Wireless access point channels at 5 GHz
A single wireless access point is found to operate in dual band more that is 2.4 GhZ and
5GHz. The encryption type followed by the wireless access point can also be fetched and it can
be used by the intruders to attack on a network that have weak encryption standards.
4. Recommendations for improvement of the WLAN security
Due to the increase in the mobile device the wireless network is increasing and the risk of
attack on the wireless network is also increasing. The wireless network is required to be
protected and it should not be accessed by unauthroised personnel because it can compromise the
security of the devices connected in the network containing personal information and sensitive
data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
WIRELESS NETWORK AND SECURITY
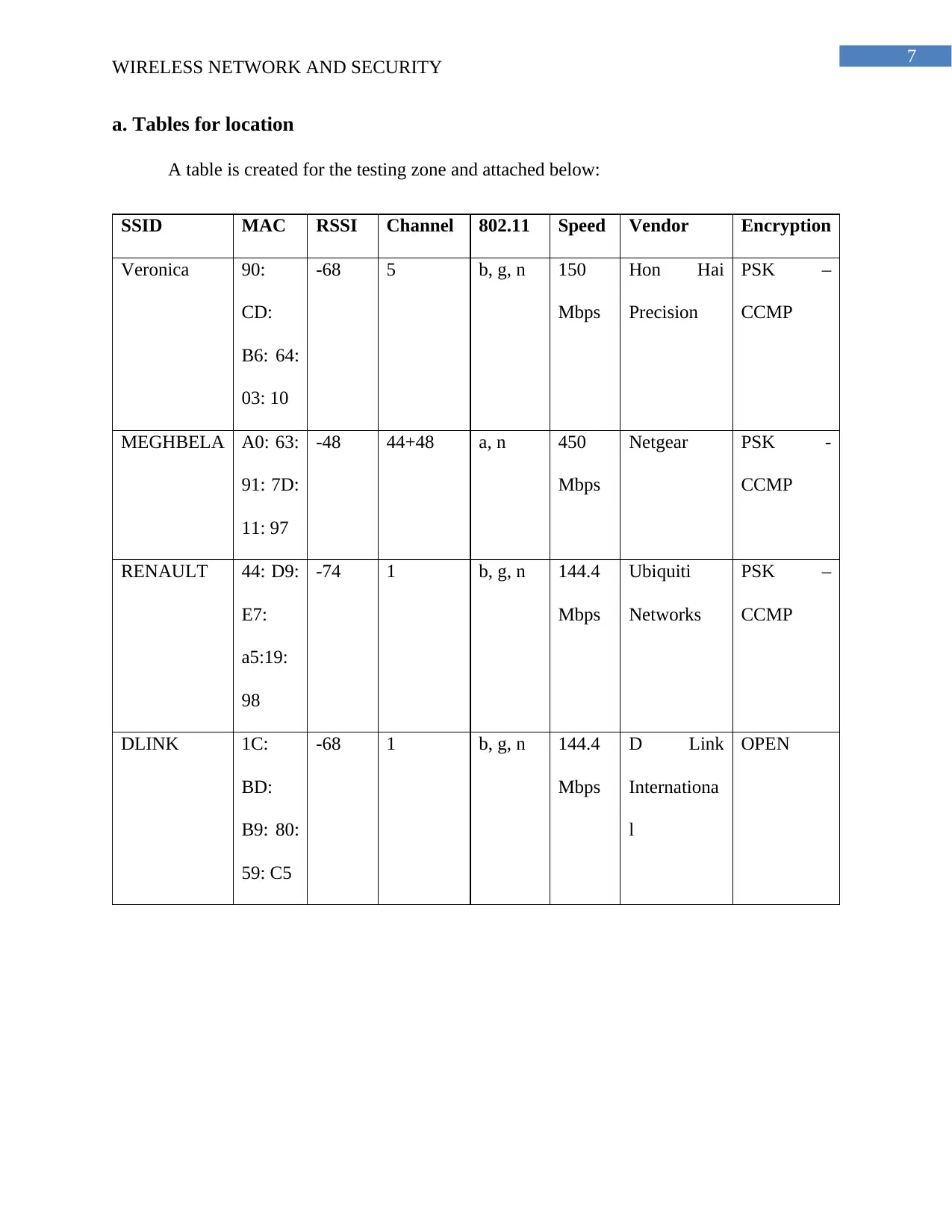
a. Tables for location
A table is created for the testing zone and attached below:
SSID MAC RSSI Channel 802.11 Speed Vendor Encryption
Veronica 90:
CD:
B6: 64:
03: 10
-68 5 b, g, n 150
Mbps
Hon Hai
Precision
PSK –
CCMP
MEGHBELA A0: 63:
91: 7D:
11: 97
-48 44+48 a, n 450
Mbps
Netgear PSK -
CCMP
RENAULT 44: D9:
E7:
a5:19:
98
-74 1 b, g, n 144.4
Mbps
Ubiquiti
Networks
PSK –
CCMP
DLINK 1C:
BD:
B9: 80:
59: C5
-68 1 b, g, n 144.4
Mbps
D Link
Internationa
l
OPEN
WIRELESS NETWORK AND SECURITY
a. Tables for location
A table is created for the testing zone and attached below:
SSID MAC RSSI Channel 802.11 Speed Vendor Encryption
Veronica 90:
CD:
B6: 64:
03: 10
-68 5 b, g, n 150
Mbps
Hon Hai
Precision
PSK –
CCMP
MEGHBELA A0: 63:
91: 7D:
11: 97
-48 44+48 a, n 450
Mbps
Netgear PSK -
CCMP
RENAULT 44: D9:
E7:
a5:19:
98
-74 1 b, g, n 144.4
Mbps
Ubiquiti
Networks
PSK –
CCMP
DLINK 1C:
BD:
B9: 80:
59: C5
-68 1 b, g, n 144.4
Mbps
D Link
Internationa
l
OPEN
8
WIRELESS NETWORK AND SECURITY
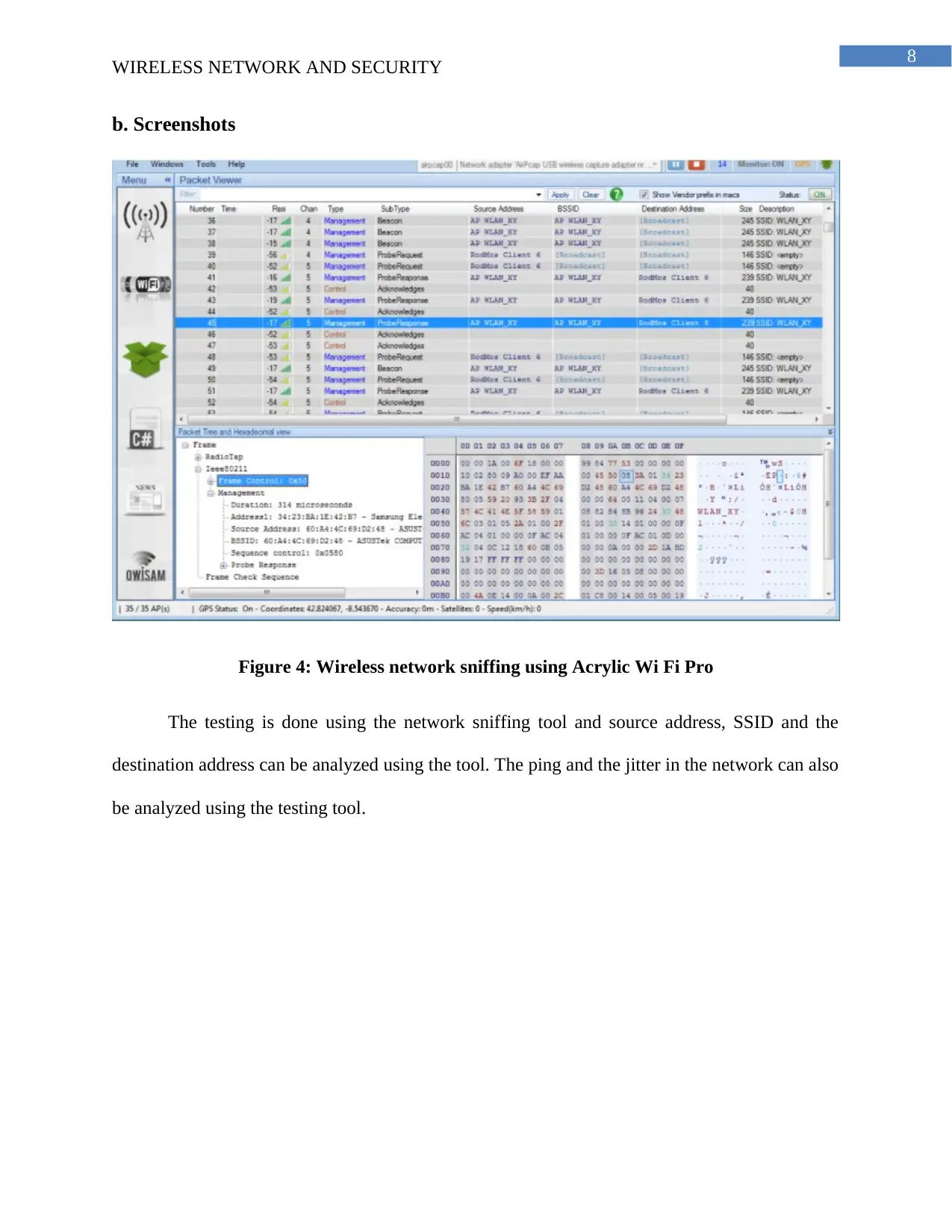
b. Screenshots
Figure 4: Wireless network sniffing using Acrylic Wi Fi Pro
The testing is done using the network sniffing tool and source address, SSID and the
destination address can be analyzed using the tool. The ping and the jitter in the network can also
be analyzed using the testing tool.
WIRELESS NETWORK AND SECURITY
b. Screenshots
Figure 4: Wireless network sniffing using Acrylic Wi Fi Pro
The testing is done using the network sniffing tool and source address, SSID and the
destination address can be analyzed using the tool. The ping and the jitter in the network can also
be analyzed using the testing tool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
WIRELESS NETWORK AND SECURITY
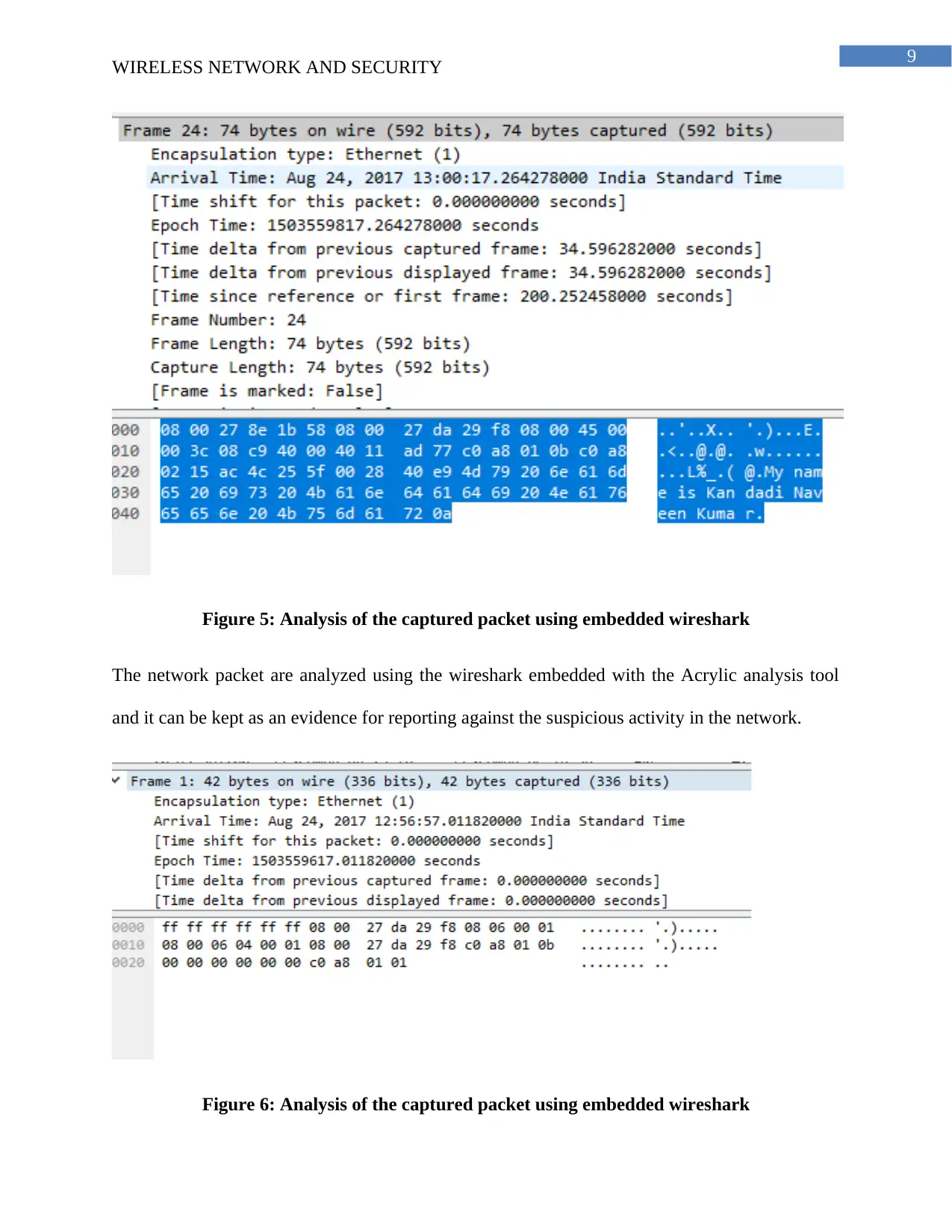
Figure 5: Analysis of the captured packet using embedded wireshark
The network packet are analyzed using the wireshark embedded with the Acrylic analysis tool
and it can be kept as an evidence for reporting against the suspicious activity in the network.
Figure 6: Analysis of the captured packet using embedded wireshark
WIRELESS NETWORK AND SECURITY
Figure 5: Analysis of the captured packet using embedded wireshark
The network packet are analyzed using the wireshark embedded with the Acrylic analysis tool
and it can be kept as an evidence for reporting against the suspicious activity in the network.
Figure 6: Analysis of the captured packet using embedded wireshark
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
WIRELESS NETWORK AND SECURITY
The captured frame using the packet analyzer helps to identify the source and the destination
user communicating in the wireless network.
c. Explanation of techniques applied for management and securing the network
i. Application of dual bands and its advantage
The implementation of the dual band wireless access point in the network helps to
communicate with the devices in two frequency range. The 5 Ghz channel of the dual band
network is less noisy and the thus have an increased speed of transmission. The single band
channel is affected by noise and interference and can cause loss in data and the transmission
speed may be lower in this network.
ii. Security Implication
A network penetration testing can be performed on the network for finding the flaws of
the network and secure the areas. The remote access of the network for the unauthroised user is
required to be restricted and the routers is required to be configured with EIGRP protocol for
communicating with the outside network using a secure channel [4]. The address resolution
protocol is required to be disabled on the router for reduction of the risk of discovery of the
network components.
iii. Other Aspects
Distribution of a remote access points- The access point installed in the network is
required to be placed according to the coverage area required for the business. The remote and
the relay base station is required to be connected with the main base station. Same SSID is
required to be used in the devices such that the user can remain on the same LAN.
WIRELESS NETWORK AND SECURITY
The captured frame using the packet analyzer helps to identify the source and the destination
user communicating in the wireless network.
c. Explanation of techniques applied for management and securing the network
i. Application of dual bands and its advantage
The implementation of the dual band wireless access point in the network helps to
communicate with the devices in two frequency range. The 5 Ghz channel of the dual band
network is less noisy and the thus have an increased speed of transmission. The single band
channel is affected by noise and interference and can cause loss in data and the transmission
speed may be lower in this network.
ii. Security Implication
A network penetration testing can be performed on the network for finding the flaws of
the network and secure the areas. The remote access of the network for the unauthroised user is
required to be restricted and the routers is required to be configured with EIGRP protocol for
communicating with the outside network using a secure channel [4]. The address resolution
protocol is required to be disabled on the router for reduction of the risk of discovery of the
network components.
iii. Other Aspects
Distribution of a remote access points- The access point installed in the network is
required to be placed according to the coverage area required for the business. The remote and
the relay base station is required to be connected with the main base station. Same SSID is
required to be used in the devices such that the user can remain on the same LAN.

11
WIRELESS NETWORK AND SECURITY
Security of the wireless access point- A wireless encryption algorithm is required to be
selected for securing the access point. The use of a strong algorithm reduces the risk of external
access and improves the security of the network [11].
Recording the wireless devices connected with the network- A log is required to be
maintained regarding the list of the devices connected to the wireless access point installed in the
network. An alarm can be set if any suspicious activity is noticed in the network.
Providing training to the user for securing their device- The user connecting their
wireless device is required to be awarded about securing their device because the device can be
illegally used by hackers to access the resources of the network.
Auditing the network using network analyzer tool- The logs recorded in the network is
required to be analyzed for finding any attacks performed on the network and remove the flaws
in the network.
WIRELESS NETWORK AND SECURITY
Security of the wireless access point- A wireless encryption algorithm is required to be
selected for securing the access point. The use of a strong algorithm reduces the risk of external
access and improves the security of the network [11].
Recording the wireless devices connected with the network- A log is required to be
maintained regarding the list of the devices connected to the wireless access point installed in the
network. An alarm can be set if any suspicious activity is noticed in the network.
Providing training to the user for securing their device- The user connecting their
wireless device is required to be awarded about securing their device because the device can be
illegally used by hackers to access the resources of the network.
Auditing the network using network analyzer tool- The logs recorded in the network is
required to be analyzed for finding any attacks performed on the network and remove the flaws
in the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



