Cybersecurity Incident Report on Wireless and BYOD Security Threats
VerifiedAdded on 2022/10/12
|22
|4308
|96
Report
AI Summary
This cybersecurity incident report (CIR) addresses wireless and Bring Your Own Device (BYOD) security threats within a company setting. The report begins with an executive summary highlighting passive and active attacks associated with BYOD, including eavesdropping, traffic analysis, masquerading, replay, and message modification. It then details a wireless and BYOD security plan, focusing on rogue access points, their detection, and authorized access point identification. The report applies the Cyber Kill Chain framework to improve response times to cyberattacks and discusses tracking suspicious behavior, including how to track company assets. Further, it explores identity theft and MAC spoofing in the workplace, offering preventative measures. Legal aspects of investigations are considered, including pre-investigation steps and authorization. The report also proposes a continuous improvement plan, covering Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA) networks, remote configuration management, and employee misconduct. Finally, it touches on ad hoc wireless networks, their threats, and prevention, as well as the use of SSIDs.

COMPUTER INFORMATION SYSTEM
STUDENT NAME
PROFESSOR’S NAME
DATE
STUDENT NAME
PROFESSOR’S NAME
DATE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The attacks which comes with BYOD is both passive and active attacks.The passive
attacks are the attacks whereby the person who is not authorized monitors the communication
which takes place in the WLAN. The passive attacker doesn’t alter, generate or rather disrupt the
Wireless Local Area Network Connection. In the passive attacks, it is also categorized into two
type which includes the following, (“NIST Special Publication 800-94, Guide to Intrusion
Detection and Prevention Systems”, n.d);
Eavesdropping: this is the attacker that monitors the data which is being transmitted over
the WLAN in order to get the content of the message.
Traffic Analysis: This is where the attacker just creates an intelligent platform of
monitoring the pattern at which the transmission over the WLAN is done
The active attacks are where the person who is not authorized alters, generates and disrupt
the communication over the WLAN network. In the active security threats, the following are its
sub categories;
Masquerading: this is where the attacker will impersonate as the authorized user of the
system in order to gain access to the privileges which are not authorized.
Replay: This is where the attackers’ monitors data transmission and in turn retransmits the
same data as legitimate user in the network.
Message modification: this is where the attacker recreates the original message by either
adding, changing, editing or deleting the message which was original.
The attacks which comes with BYOD is both passive and active attacks.The passive
attacks are the attacks whereby the person who is not authorized monitors the communication
which takes place in the WLAN. The passive attacker doesn’t alter, generate or rather disrupt the
Wireless Local Area Network Connection. In the passive attacks, it is also categorized into two
type which includes the following, (“NIST Special Publication 800-94, Guide to Intrusion
Detection and Prevention Systems”, n.d);
Eavesdropping: this is the attacker that monitors the data which is being transmitted over
the WLAN in order to get the content of the message.
Traffic Analysis: This is where the attacker just creates an intelligent platform of
monitoring the pattern at which the transmission over the WLAN is done
The active attacks are where the person who is not authorized alters, generates and disrupt
the communication over the WLAN network. In the active security threats, the following are its
sub categories;
Masquerading: this is where the attacker will impersonate as the authorized user of the
system in order to gain access to the privileges which are not authorized.
Replay: This is where the attackers’ monitors data transmission and in turn retransmits the
same data as legitimate user in the network.
Message modification: this is where the attacker recreates the original message by either
adding, changing, editing or deleting the message which was original.

Table of Contents
Executive Summary...................................................................................................................................2
Introduction................................................................................................................................................5
Wireless and BYOD Security Plan............................................................................................................5
Threats of Rogue Access Points................................................................................................................5
Detecting Rogue and authorized Access Points.......................................................................................5
Cyber Kill Chain.........................................................................................................................................5
Tracking Suspicious behavior...................................................................................................................6
How to track location of company asset..................................................................................................6
Identity Theft and MAC Spoofing in workplace........................................................................................7
How to prevent Identity Theft and MAC spoofing....................................................................................7
Legal issues for the investigation action...................................................................................................8
Pre- investigation.....................................................................................................................................8
Authorization............................................................................................................................................8
Continuous Improvement Plan...............................................................................................................10
Wired Equivalent Privacy (WEP).............................................................................................................10
Wi- Fi Protected Access Network...........................................................................................................10
Remote Configuration Management.......................................................................................................14
Removing unauthorized person from the network................................................................................14
Employee Misconduct..............................................................................................................................16
Ad Hoc wireless network........................................................................................................................16
Ad Hoc Threats and Vulnerability to the company.................................................................................17
Ad hoc threats prevention......................................................................................................................17
Self-configuring dynamic networks on open access architecture...........................................................18
SSID........................................................................................................................................................19
Conclusion.................................................................................................................................................20
References..............................................................................................................................................21
Executive Summary...................................................................................................................................2
Introduction................................................................................................................................................5
Wireless and BYOD Security Plan............................................................................................................5
Threats of Rogue Access Points................................................................................................................5
Detecting Rogue and authorized Access Points.......................................................................................5
Cyber Kill Chain.........................................................................................................................................5
Tracking Suspicious behavior...................................................................................................................6
How to track location of company asset..................................................................................................6
Identity Theft and MAC Spoofing in workplace........................................................................................7
How to prevent Identity Theft and MAC spoofing....................................................................................7
Legal issues for the investigation action...................................................................................................8
Pre- investigation.....................................................................................................................................8
Authorization............................................................................................................................................8
Continuous Improvement Plan...............................................................................................................10
Wired Equivalent Privacy (WEP).............................................................................................................10
Wi- Fi Protected Access Network...........................................................................................................10
Remote Configuration Management.......................................................................................................14
Removing unauthorized person from the network................................................................................14
Employee Misconduct..............................................................................................................................16
Ad Hoc wireless network........................................................................................................................16
Ad Hoc Threats and Vulnerability to the company.................................................................................17
Ad hoc threats prevention......................................................................................................................17
Self-configuring dynamic networks on open access architecture...........................................................18
SSID........................................................................................................................................................19
Conclusion.................................................................................................................................................20
References..............................................................................................................................................21
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table Of Figures
Figure 1: Cyber Kill Chain...........................................................................................................................6
Figure 2: Ad Hoc Network diagram...........................................................................................................16
Figure 3: SSID Name.................................................................................................................................19
Figure 4: SSID enabling and disabling.......................................................................................................20
Figure 1: Cyber Kill Chain...........................................................................................................................6
Figure 2: Ad Hoc Network diagram...........................................................................................................16
Figure 3: SSID Name.................................................................................................................................19
Figure 4: SSID enabling and disabling.......................................................................................................20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The Bring Your Own Device has come with a lot of security threats as each employee in a
company make connection using their own devices.
Wireless and BYOD Security Plan
Threats of Rogue Access Points
Rogue access points are the wireless network which has been set by the attacker with core
intentions of having unauthorized access to the main network. Rogue access point in the company
it regarded as the silent killer of the security in the company premise. The access point opens a
platform for unauthorized parties to gain access to the network system of the company. The
attacker is able of runner different type of the vulnerability scanners which enables them to attack
the system remotely without being inside the company premise (Beyah & Venkataraman, 2011).
Detecting Rogue and authorized Access Points
Rogue networks can be detected by the use of the netstumbler software where the admin
will run the software on the laptop in order to detect all the wireless networks which are available
in the broadcasting area. The software has the GPS integration which identifies the location
where the rogue access point is coming from. This is the most common way of detecting the
rogue Access Points (Beyah & Venkataraman, 2011).
Authorized access point have got identified names when the scanner is done, all the
networks will be listed and the admin will be able to know the rogue and the right access points.
The Bring Your Own Device has come with a lot of security threats as each employee in a
company make connection using their own devices.
Wireless and BYOD Security Plan
Threats of Rogue Access Points
Rogue access points are the wireless network which has been set by the attacker with core
intentions of having unauthorized access to the main network. Rogue access point in the company
it regarded as the silent killer of the security in the company premise. The access point opens a
platform for unauthorized parties to gain access to the network system of the company. The
attacker is able of runner different type of the vulnerability scanners which enables them to attack
the system remotely without being inside the company premise (Beyah & Venkataraman, 2011).
Detecting Rogue and authorized Access Points
Rogue networks can be detected by the use of the netstumbler software where the admin
will run the software on the laptop in order to detect all the wireless networks which are available
in the broadcasting area. The software has the GPS integration which identifies the location
where the rogue access point is coming from. This is the most common way of detecting the
rogue Access Points (Beyah & Venkataraman, 2011).
Authorized access point have got identified names when the scanner is done, all the
networks will be listed and the admin will be able to know the rogue and the right access points.
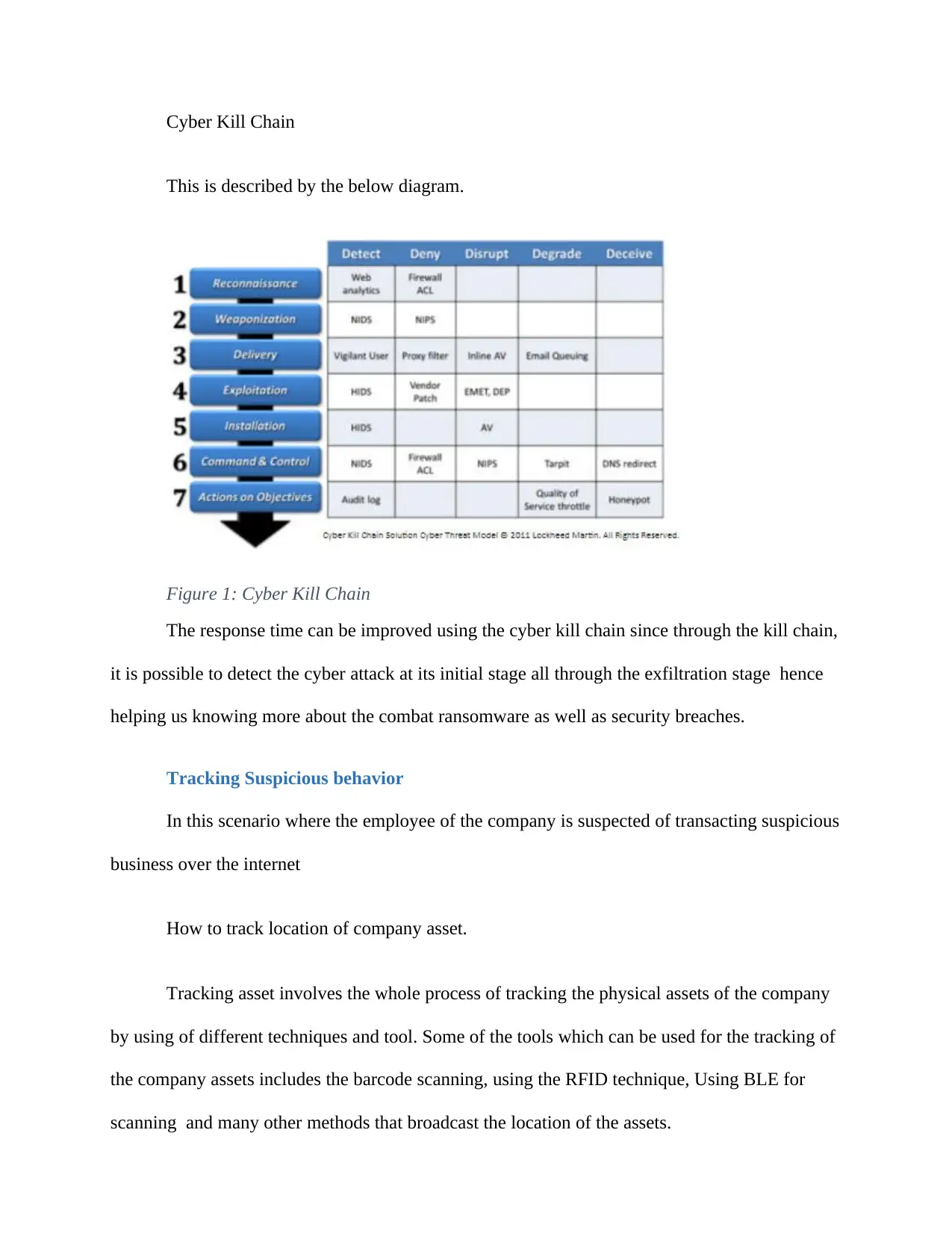
Cyber Kill Chain
This is described by the below diagram.
Figure 1: Cyber Kill Chain
The response time can be improved using the cyber kill chain since through the kill chain,
it is possible to detect the cyber attack at its initial stage all through the exfiltration stage hence
helping us knowing more about the combat ransomware as well as security breaches.
Tracking Suspicious behavior
In this scenario where the employee of the company is suspected of transacting suspicious
business over the internet
How to track location of company asset.
Tracking asset involves the whole process of tracking the physical assets of the company
by using of different techniques and tool. Some of the tools which can be used for the tracking of
the company assets includes the barcode scanning, using the RFID technique, Using BLE for
scanning and many other methods that broadcast the location of the assets.
This is described by the below diagram.
Figure 1: Cyber Kill Chain
The response time can be improved using the cyber kill chain since through the kill chain,
it is possible to detect the cyber attack at its initial stage all through the exfiltration stage hence
helping us knowing more about the combat ransomware as well as security breaches.
Tracking Suspicious behavior
In this scenario where the employee of the company is suspected of transacting suspicious
business over the internet
How to track location of company asset.
Tracking asset involves the whole process of tracking the physical assets of the company
by using of different techniques and tool. Some of the tools which can be used for the tracking of
the company assets includes the barcode scanning, using the RFID technique, Using BLE for
scanning and many other methods that broadcast the location of the assets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A company has different types of assets; hence different methods will be used for tracking
them. We have the assets which are portable and movable and other which are stationary.
Security concerns is always on the assets which are mobile and portable. In a company where
there are employees, it becomes very vital to do tracking of assets. For assets which can move or
moved from one place to another, GPS tracking technique can be used. Using this type of
tracking, the GPS device will be attached to each and every mobile assets within the company,
the device will be showing the current location of the assets in there real time basis. The general
Positioning System will be sending signals with updates on the current position and location of
the assets hence making it very possible for the company to know where there assets are exactly.
Identity Theft and MAC Spoofing in workplace
Identity theft is when an imposter stages and impersonates as someone else in the work
place. In the place where the company is employing the use of BYOD technique, identity fraud is
commonly witnessed. Since each person is able to create connection to the network and do
transactions over the network, another person can get an employees login credentials to the
system, use his/her own device to login and impersonate as the employee ("3 Ways to Spoof a
MAC Address - wikihow.tech", n.d.). Hence making transaction freely over the internet using the
security keys of another person.
MAC spoofing which is the process where the MAC address of the networked device is
altered and redirected to another device, can also happen in the company where BYOD has been
employed. This is where the attacker will just come and make changes to another person device
MAC address so that when the attacker operates the device, it will be like the other person since
the MAC address of the other person is what is active in the network ("How (and Why) to
Change Your MAC Address on Windows, Linux ...", n.d.).
them. We have the assets which are portable and movable and other which are stationary.
Security concerns is always on the assets which are mobile and portable. In a company where
there are employees, it becomes very vital to do tracking of assets. For assets which can move or
moved from one place to another, GPS tracking technique can be used. Using this type of
tracking, the GPS device will be attached to each and every mobile assets within the company,
the device will be showing the current location of the assets in there real time basis. The general
Positioning System will be sending signals with updates on the current position and location of
the assets hence making it very possible for the company to know where there assets are exactly.
Identity Theft and MAC Spoofing in workplace
Identity theft is when an imposter stages and impersonates as someone else in the work
place. In the place where the company is employing the use of BYOD technique, identity fraud is
commonly witnessed. Since each person is able to create connection to the network and do
transactions over the network, another person can get an employees login credentials to the
system, use his/her own device to login and impersonate as the employee ("3 Ways to Spoof a
MAC Address - wikihow.tech", n.d.). Hence making transaction freely over the internet using the
security keys of another person.
MAC spoofing which is the process where the MAC address of the networked device is
altered and redirected to another device, can also happen in the company where BYOD has been
employed. This is where the attacker will just come and make changes to another person device
MAC address so that when the attacker operates the device, it will be like the other person since
the MAC address of the other person is what is active in the network ("How (and Why) to
Change Your MAC Address on Windows, Linux ...", n.d.).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

How to prevent Identity Theft and MAC spoofing
Identity theft in a company which has allowed BYOD can be protected by taking into
account the following measures, this includes the following;
a. Advising the employees to guard there social security numbers for there
devices so prevent attackers and identity frauds from accessing there system.
b. Being careful while entering their login credential especially while in
public as the identity thieves are very creative, they can steal information secretly.
MAC spoofing can be prevented but encouraging the employees to configure there
devices for VPN connection in order to prevent the attackers from identifying them on a network.
Using VPN, it is very hard for the attacker to know the MAC address of another networked
device ("How to spoof a MAC address - TechRepublic", n.d.).
It is not feasible to determine if MAC spoofing has taken place in the workplace since
during investigation, there was no trace of MAC spoofing which was noted as the suspicious
actions of the employee was on identify theft.
Legal issues for the investigation action
Under normal circumstances, if there is suspicion over unwarranted behavior for one of
the employees, the investigation team is free to carry out the investigation without interfering
with the confidential information of another person. As far as investigation is allowed, them there
are limited as far as protection over another persons confidential information is concerned.
Pre- investigation
Identity theft in a company which has allowed BYOD can be protected by taking into
account the following measures, this includes the following;
a. Advising the employees to guard there social security numbers for there
devices so prevent attackers and identity frauds from accessing there system.
b. Being careful while entering their login credential especially while in
public as the identity thieves are very creative, they can steal information secretly.
MAC spoofing can be prevented but encouraging the employees to configure there
devices for VPN connection in order to prevent the attackers from identifying them on a network.
Using VPN, it is very hard for the attacker to know the MAC address of another networked
device ("How to spoof a MAC address - TechRepublic", n.d.).
It is not feasible to determine if MAC spoofing has taken place in the workplace since
during investigation, there was no trace of MAC spoofing which was noted as the suspicious
actions of the employee was on identify theft.
Legal issues for the investigation action
Under normal circumstances, if there is suspicion over unwarranted behavior for one of
the employees, the investigation team is free to carry out the investigation without interfering
with the confidential information of another person. As far as investigation is allowed, them there
are limited as far as protection over another persons confidential information is concerned.
Pre- investigation

Before any kind of investigation is done, them the investigator has to be authorized to
carry out the said investigation by the legal departments in the government and the company. The
suspect has to be notified and to be given consent of the upcoming investigation over suspicious
behavior noted in the past.
Authorization
Yes, I was authorized before investigation begun. The matter was reported to the central
department and was authorized to carry on with the investigation for the same. The notification
was valid over the investigation as the person was consent of the upcoming investigation which
was to take place on his/her docket.
carry out the said investigation by the legal departments in the government and the company. The
suspect has to be notified and to be given consent of the upcoming investigation over suspicious
behavior noted in the past.
Authorization
Yes, I was authorized before investigation begun. The matter was reported to the central
department and was authorized to carry on with the investigation for the same. The notification
was valid over the investigation as the person was consent of the upcoming investigation which
was to take place on his/her docket.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Continuous Improvement Plan
Wired Equivalent Privacy (WEP)
The WEP is a protocol of security which is also specified in the standards of the Wireless
Fidelity, which is designed in order to provide the WLAN with a security level and privacy that is
compared to the Wired LAN. USING THE Wired equivalent privacy, the radio waves are
encrypted over the WLAN. This in turn gives protection to the wireless link which is vulnerable
in between the access point and the client (Mohapatra & Prakash, 2010). This type of privacy has
made it possible for the Wireless local area network to have the same type and level of security
which the Wired local area network has.
Wi- Fi Protected Access Network
This is also called WPA2, which is a standard of security for all the users of computer
based devices which is equipped with the Wireless Connection of internet. This was developed
by the Wi Fi alliance in order to give a provision of the most complex encryption of data as well
as the best authentication of the user as compared to the Wired equivalent Privacy (Eissa, Ali &
Abdel-Latif, 2013). The WPA has the personal and the enterprise mode of discretion. For the
enterprise use, the privacy makes use of the 802.1x stringent mode of authentication together
with the Extensible Authentication Protocol also abbreviated as the EAP. For the enterprise use,
the use of authentication server is required. For the personal use, the privacy makes use of the pre
shared keys in order to make is simple for the management as well as implementation among the
consumers (Eissa, Ali & Abdel-Latif, 2013). The Pre shared key is the secret key that is shared
previously just between only tow parties by the use of some connections and channels which are
Wired Equivalent Privacy (WEP)
The WEP is a protocol of security which is also specified in the standards of the Wireless
Fidelity, which is designed in order to provide the WLAN with a security level and privacy that is
compared to the Wired LAN. USING THE Wired equivalent privacy, the radio waves are
encrypted over the WLAN. This in turn gives protection to the wireless link which is vulnerable
in between the access point and the client (Mohapatra & Prakash, 2010). This type of privacy has
made it possible for the Wireless local area network to have the same type and level of security
which the Wired local area network has.
Wi- Fi Protected Access Network
This is also called WPA2, which is a standard of security for all the users of computer
based devices which is equipped with the Wireless Connection of internet. This was developed
by the Wi Fi alliance in order to give a provision of the most complex encryption of data as well
as the best authentication of the user as compared to the Wired equivalent Privacy (Eissa, Ali &
Abdel-Latif, 2013). The WPA has the personal and the enterprise mode of discretion. For the
enterprise use, the privacy makes use of the 802.1x stringent mode of authentication together
with the Extensible Authentication Protocol also abbreviated as the EAP. For the enterprise use,
the use of authentication server is required. For the personal use, the privacy makes use of the pre
shared keys in order to make is simple for the management as well as implementation among the
consumers (Eissa, Ali & Abdel-Latif, 2013). The Pre shared key is the secret key that is shared
previously just between only tow parties by the use of some connections and channels which are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

very much secure just before it is used. In order to build the key from the secret shared. The
derivation key function is supposed to be used.
Wireless network are of different types, each and every wireless network has its
advantages and disadvantages. In this report, only four types of wireless networks will be
discussed. This includes the following.
a. Bluetooth
This is a wireless technology which allows the exchange of data between devices
which are fixed in nature. The range at which Bluetooth is able to create connection is a
very short distance of up to 10 meters. The Bluetooth is in the Wireless Personal Area
network category of the wireless networks.
b. Wireless Local Area Network
This is the network which creates link with two and more devices in a short
distance by the use of the wireless method of distribution by providing connection over
the access point in order for the internet to be accessed (Eissa, Ali & Abdel-Latif, 2013).
c. Wireless ad hoc network
This is also called the mesh network, this is a network which is made up of the
nodes of radio which is organized in the mesh technology. In this type of a network, every
node of the network forwards the messages in place of the other node and each and every
node perform the routing.
derivation key function is supposed to be used.
Wireless network are of different types, each and every wireless network has its
advantages and disadvantages. In this report, only four types of wireless networks will be
discussed. This includes the following.
a. Bluetooth
This is a wireless technology which allows the exchange of data between devices
which are fixed in nature. The range at which Bluetooth is able to create connection is a
very short distance of up to 10 meters. The Bluetooth is in the Wireless Personal Area
network category of the wireless networks.
b. Wireless Local Area Network
This is the network which creates link with two and more devices in a short
distance by the use of the wireless method of distribution by providing connection over
the access point in order for the internet to be accessed (Eissa, Ali & Abdel-Latif, 2013).
c. Wireless ad hoc network
This is also called the mesh network, this is a network which is made up of the
nodes of radio which is organized in the mesh technology. In this type of a network, every
node of the network forwards the messages in place of the other node and each and every
node perform the routing.

d. Wireless Metropolitan Area Network
This is the type of network which is made up of the connection of several wireless
Local Area Network put in place. It serves at least an larger area since several WLAN
have been connected together.
Advantages of the wireless network
i. This technology is very much affordable in terms of cost
ii. It does not need any extra space for its operation
iii. It does not need cable or wired connection in order to connect with other
devices
iv. This technology is very reliable and easy in terms of usage.
v. The network is fully secure as it involves the exchange of data between
only two devices.
Disadvantages of the wireless network
i. Wireless network can only serve within the shortest range of at least 10 m
to 30 meters.
ii. They are always interfered with the radio signals
iii. The rate at which data is being transferred over the wireless network is
very slow as compared to the wired network.
iv. The wireless network always has health problems that comes with it.
v. The cost of purchasing communication devices is very high.
This is the type of network which is made up of the connection of several wireless
Local Area Network put in place. It serves at least an larger area since several WLAN
have been connected together.
Advantages of the wireless network
i. This technology is very much affordable in terms of cost
ii. It does not need any extra space for its operation
iii. It does not need cable or wired connection in order to connect with other
devices
iv. This technology is very reliable and easy in terms of usage.
v. The network is fully secure as it involves the exchange of data between
only two devices.
Disadvantages of the wireless network
i. Wireless network can only serve within the shortest range of at least 10 m
to 30 meters.
ii. They are always interfered with the radio signals
iii. The rate at which data is being transferred over the wireless network is
very slow as compared to the wired network.
iv. The wireless network always has health problems that comes with it.
v. The cost of purchasing communication devices is very high.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



