A Detailed Analysis of Wireless Security Threats and Solutions Report
VerifiedAdded on 2023/03/20
|12
|2339
|60
Report
AI Summary
This report provides a comprehensive analysis of wireless security, focusing on threats and vulnerabilities within an IoT network. It begins by highlighting the importance of wireless security and the increasing prevalence of IoT devices. The report identifies key security threats, including vulnerabilities in WEP shared authentication, unmanaged network switches, and denial-of-service attacks, and provides real-world examples of exploitation. Attack scenarios are detailed, illustrating how these vulnerabilities can be exploited. The report then outlines proposed countermeasures and solutions, including the implementation of WPA2 encryption, managed switches, layered network design, and the use of TLS and ECC for MQTT security. Finally, it emphasizes the importance of security policies and provides example policy statements, scope, restrictions, and acceptable use guidelines to enhance overall network security.

Wireless Security
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................3
Security Threats...........................................................................................................................................3
Attack Scenario............................................................................................................................................6
WEP Threat Attack Scenarios...................................................................................................................6
Unmanaged Switch attack scenario.........................................................................................................6
Denial of service attack scenario.............................................................................................................6
Security Policies...........................................................................................................................................7
Policy Statement......................................................................................................................................7
Policy Scope.........................................................................................................................................7
Policy Restrictions................................................................................................................................7
Acceptable use....................................................................................................................................8
Regulatory framework.........................................................................................................................8
Policy Violation....................................................................................................................................8
Proposed Countermeasure(s)/Solution(s....................................................................................................8
References.................................................................................................................................................10
Introduction.................................................................................................................................................3
Security Threats...........................................................................................................................................3
Attack Scenario............................................................................................................................................6
WEP Threat Attack Scenarios...................................................................................................................6
Unmanaged Switch attack scenario.........................................................................................................6
Denial of service attack scenario.............................................................................................................6
Security Policies...........................................................................................................................................7
Policy Statement......................................................................................................................................7
Policy Scope.........................................................................................................................................7
Policy Restrictions................................................................................................................................7
Acceptable use....................................................................................................................................8
Regulatory framework.........................................................................................................................8
Policy Violation....................................................................................................................................8
Proposed Countermeasure(s)/Solution(s....................................................................................................8
References.................................................................................................................................................10

Introduction
According to (Capano, 2015), the wireless communication systems have revolutionized
data communication as it has increased efficiency and effectiveness of data transfer with high
ease of set up and maintenance. This has made it become the default choice for most people.
However, information security in the wireless system still remains a hurdle which if not well
designed, would make the whole network system vulnerable to cybersecurity attacks.
In their paper, (Apthorpe, Reisman, & Feamster, 2017) explained that the increasing
proliferation of IoT devices, despite its ease and convenience have brought with it serious
cybersecurity threats that if not address can not only lead to an information security breach but
also loss of lives.
The key goal of this report is to highlight various wireless and IoT security threats and
vulnerable from the network design, analyze the identified threats and vulnerabilities by
analyzing historical data on real-world scenarios of exploitation of such vulnerabilities in the
past and the effects they have on the organizations. The last section of the report provides key
recommendation and strategies to mitigate threats and vulnerabilities (Junior, Melo, Lu,
d’Amorim, & Prakash, 2019). This is done in terms of policies formulation and technical
mechanisms to mitigate the vulnerabilities identified by recommending an alternative solution to
the network designer (Saleh Mohamed Israeli, Melissa Sarnowski, Md Sayedul Aman, Ahmed
Abdelgawad, & Kumar Yelamarthi, 2017).
Security Threats
The following threat and vulnerabilities have been identified in from the network design.
According to (Capano, 2015), the wireless communication systems have revolutionized
data communication as it has increased efficiency and effectiveness of data transfer with high
ease of set up and maintenance. This has made it become the default choice for most people.
However, information security in the wireless system still remains a hurdle which if not well
designed, would make the whole network system vulnerable to cybersecurity attacks.
In their paper, (Apthorpe, Reisman, & Feamster, 2017) explained that the increasing
proliferation of IoT devices, despite its ease and convenience have brought with it serious
cybersecurity threats that if not address can not only lead to an information security breach but
also loss of lives.
The key goal of this report is to highlight various wireless and IoT security threats and
vulnerable from the network design, analyze the identified threats and vulnerabilities by
analyzing historical data on real-world scenarios of exploitation of such vulnerabilities in the
past and the effects they have on the organizations. The last section of the report provides key
recommendation and strategies to mitigate threats and vulnerabilities (Junior, Melo, Lu,
d’Amorim, & Prakash, 2019). This is done in terms of policies formulation and technical
mechanisms to mitigate the vulnerabilities identified by recommending an alternative solution to
the network designer (Saleh Mohamed Israeli, Melissa Sarnowski, Md Sayedul Aman, Ahmed
Abdelgawad, & Kumar Yelamarthi, 2017).
Security Threats
The following threat and vulnerabilities have been identified in from the network design.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

First, the WEP shared authentification methods is very vulnerable due to the shared key
authentification model used. This exposes the company to potential data theft and confidentiality
breaches. The general flow of the authentication processes in WEP shared authentication allows
an attacker to observe the negotiation between the AP and the client. The attacker can know the
plain text with its corresponding ciphertext and use the message injection mechanism to generate
a key stream and use it to request for authentification, thus in doing so, the attacker will have
gained access to the network without any form of authentification (Riahi Sfar, Natalizio, Challal,
& Chtourou, 2018).
The most documented attack on the web is the TK Maxx security breach where attackers
reportedly stole 45 million records from the corporation by sampling breaching one of the
company’s retail wireless network. It turned out TJX, the mother company of TK Maxx was still
using WEP, the highly vulnerable security in its wifi. This breach so theft of sensitive data
including over a million credit cards (Swann, 2007).
The second threat to the system is the unmanaged network switch which means all the
default setting remains the same hence can be used by an attacker to breach the IoT or another
network component. This threat is due to the vulnerabilities that exist in the OEM of the
unmanaged witches which normally uses open ports to reduce the manufacturing cost since most
of these cheap OEMs implement open port, allowing different kind of traffic to pass (McAfee,
2019). This can be exploited by a rogue employee or some external vendor who can inject
malicious code or virus into the network through the open ports hence wreaking havoc
(McLaughlin, 2008).
A most documented case of such attacks is the Bangladesh central bank data breach
where attackers broke into the central bank’s financial system which interfaces with the SWIFT
authentification model used. This exposes the company to potential data theft and confidentiality
breaches. The general flow of the authentication processes in WEP shared authentication allows
an attacker to observe the negotiation between the AP and the client. The attacker can know the
plain text with its corresponding ciphertext and use the message injection mechanism to generate
a key stream and use it to request for authentification, thus in doing so, the attacker will have
gained access to the network without any form of authentification (Riahi Sfar, Natalizio, Challal,
& Chtourou, 2018).
The most documented attack on the web is the TK Maxx security breach where attackers
reportedly stole 45 million records from the corporation by sampling breaching one of the
company’s retail wireless network. It turned out TJX, the mother company of TK Maxx was still
using WEP, the highly vulnerable security in its wifi. This breach so theft of sensitive data
including over a million credit cards (Swann, 2007).
The second threat to the system is the unmanaged network switch which means all the
default setting remains the same hence can be used by an attacker to breach the IoT or another
network component. This threat is due to the vulnerabilities that exist in the OEM of the
unmanaged witches which normally uses open ports to reduce the manufacturing cost since most
of these cheap OEMs implement open port, allowing different kind of traffic to pass (McAfee,
2019). This can be exploited by a rogue employee or some external vendor who can inject
malicious code or virus into the network through the open ports hence wreaking havoc
(McLaughlin, 2008).
A most documented case of such attacks is the Bangladesh central bank data breach
where attackers broke into the central bank’s financial system which interfaces with the SWIFT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

global payment service. This was made possible thanks to the vulnerable, cheap unmanned
switches used by the Bangladesh (Yadong Zhou, Kaiyue Chen, Junjie Zhang, Junyuan Leng, &
Yazhe Tang, 2018)
The third threat to the wireless system is is denial of service attacks which is caused by
the non layered approach to the network design making It possible for compromised computer
system to be used and flood useless traffic into the network causing the genuine users of the
network not able to access the various network resources (Ray, 2018).
Denial of service has been well documented in the past. A good example is the Sony data
breach was a well-coordinated Distributed denial of service attack on Sony servers. Such attacks
have in the past crimpled big corporation since stopping them would mean bringing down the
server offline which has serious revenues implications. It is therefore vital for organizations to
design networks that are modular, hierarchical and maintenance (Younes, 2017).
The MQTT has the following design and implementation issues where a client can use
the constrained application protocol were the clients in the LAN1 can be commanded to send
CoAP packets to the server and use its payload to wreak havoc in the network. The open nature
of the protocol makes the MQTT very much vulnerable since it is mostly reachable via the public
IP hence can be used by an attacker to send malicious code in the network.
The temperature sensor linked directly to Ubuntu server possess some vulnerability to
the network. The custom builds of the sensors mostly don’t conform to the security standards of
IoT devices security setups. This makes is susceptible to man in the middle attacks who can use
the link to the Ubuntu server through fake authentication from the sensor.
switches used by the Bangladesh (Yadong Zhou, Kaiyue Chen, Junjie Zhang, Junyuan Leng, &
Yazhe Tang, 2018)
The third threat to the wireless system is is denial of service attacks which is caused by
the non layered approach to the network design making It possible for compromised computer
system to be used and flood useless traffic into the network causing the genuine users of the
network not able to access the various network resources (Ray, 2018).
Denial of service has been well documented in the past. A good example is the Sony data
breach was a well-coordinated Distributed denial of service attack on Sony servers. Such attacks
have in the past crimpled big corporation since stopping them would mean bringing down the
server offline which has serious revenues implications. It is therefore vital for organizations to
design networks that are modular, hierarchical and maintenance (Younes, 2017).
The MQTT has the following design and implementation issues where a client can use
the constrained application protocol were the clients in the LAN1 can be commanded to send
CoAP packets to the server and use its payload to wreak havoc in the network. The open nature
of the protocol makes the MQTT very much vulnerable since it is mostly reachable via the public
IP hence can be used by an attacker to send malicious code in the network.
The temperature sensor linked directly to Ubuntu server possess some vulnerability to
the network. The custom builds of the sensors mostly don’t conform to the security standards of
IoT devices security setups. This makes is susceptible to man in the middle attacks who can use
the link to the Ubuntu server through fake authentication from the sensor.

Attack Scenario
The identified threats can be manifested in different forms either from within the network
or from an outside threat. This section details attack vectors that can be used to exploit the
vulnerabilities and threats identified above
WEP Threat Attack Scenarios
First, the attacker can sniff the wireless traffic passing through the network and use fake
authentification message responses to gain access to the network without authorization. Once
into the network, the attacker can perform malicious activities such as the installation of
backdoor into the system, steal or install malicious software which can be used to extend the
attack
Unmanaged Switch attack scenario
The unmanaged switch can be attacked in the following scenario, the attacker can utilize
the known vulnerability of the open ports configured in the switch used in the network. Once
gained access via the open port, the attacker can use malicious software to spread lethal
computer virus that can compromise the communication and makes some resources unavailable.
Denial of service attack scenario
The nonhierarchical network set up can be attacked by denial of service in the following
scenarios, first, the attacker can remotely compromise one machine or a set of machines in the
network and use them in a coordinated fashion to flood the servers with useless traffic. This
makes the genuine user request not being processed by the servers hence making the information
assets unavailable to the authenticated and authorized users
MQTT attack scenario
The MQTT can be exploited through the distributed denial of service where an attacker
uses the open nature of the MQTT protocol which uses the public IP to launch distributed denial
The identified threats can be manifested in different forms either from within the network
or from an outside threat. This section details attack vectors that can be used to exploit the
vulnerabilities and threats identified above
WEP Threat Attack Scenarios
First, the attacker can sniff the wireless traffic passing through the network and use fake
authentification message responses to gain access to the network without authorization. Once
into the network, the attacker can perform malicious activities such as the installation of
backdoor into the system, steal or install malicious software which can be used to extend the
attack
Unmanaged Switch attack scenario
The unmanaged switch can be attacked in the following scenario, the attacker can utilize
the known vulnerability of the open ports configured in the switch used in the network. Once
gained access via the open port, the attacker can use malicious software to spread lethal
computer virus that can compromise the communication and makes some resources unavailable.
Denial of service attack scenario
The nonhierarchical network set up can be attacked by denial of service in the following
scenarios, first, the attacker can remotely compromise one machine or a set of machines in the
network and use them in a coordinated fashion to flood the servers with useless traffic. This
makes the genuine user request not being processed by the servers hence making the information
assets unavailable to the authenticated and authorized users
MQTT attack scenario
The MQTT can be exploited through the distributed denial of service where an attacker
uses the open nature of the MQTT protocol which uses the public IP to launch distributed denial
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

of service attacks onto the network. This causes the server to be busy serving useless traffic as
opposed to the client's needs
Temperature sensor
The temperature can be attack by spoofing the Ubuntu server to respond to the handshake
requirements of the temperature sensor. This can be exploited by a man in the middle attack who
can use the link to connect to Ubuntu server without any authentication or authorization
Security Policies
The administrative mechanism is key to mitigating security threats. Policy making is one
such key step to ensuring employees comply with the security mechanism of the company. The
following are key policy statements that can be used in the current section
Policy Statement
Policy Scope
This policy is applicable to all the wireless connections within the company network including
but not limited to wireless access points, wireless devices whether remotely connected or directly
connected.
Policy Restrictions
i. All the company access points must abide by the regulation provided by national
regulations
ii. All the current access points must conform to the industry standards and specification
provided by service providers
iii. All the access points must be authenticated with WPA2 encryption methods
iv. Employees are prohibited from the installation of network monitoring tools without
authorization from the network administrators
opposed to the client's needs
Temperature sensor
The temperature can be attack by spoofing the Ubuntu server to respond to the handshake
requirements of the temperature sensor. This can be exploited by a man in the middle attack who
can use the link to connect to Ubuntu server without any authentication or authorization
Security Policies
The administrative mechanism is key to mitigating security threats. Policy making is one
such key step to ensuring employees comply with the security mechanism of the company. The
following are key policy statements that can be used in the current section
Policy Statement
Policy Scope
This policy is applicable to all the wireless connections within the company network including
but not limited to wireless access points, wireless devices whether remotely connected or directly
connected.
Policy Restrictions
i. All the company access points must abide by the regulation provided by national
regulations
ii. All the current access points must conform to the industry standards and specification
provided by service providers
iii. All the access points must be authenticated with WPA2 encryption methods
iv. Employees are prohibited from the installation of network monitoring tools without
authorization from the network administrators
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

v. All the switches configured into the network must be managed switch with the latest
firmware from the vendor
Acceptable use
The company accepts the employees and authorized users to use the company network
resources within the scope of this policy
Regulatory framework
The company reserved the right to monitor user activities in the network and has the right
to disconnect the user who is deemed to violate the policy
Policy Violation
Any employee or contractor who violates this policy shall be subject to the disciplinary
committee which can lead to suspension of employee or contractor termination of engagement
between the employee and the company
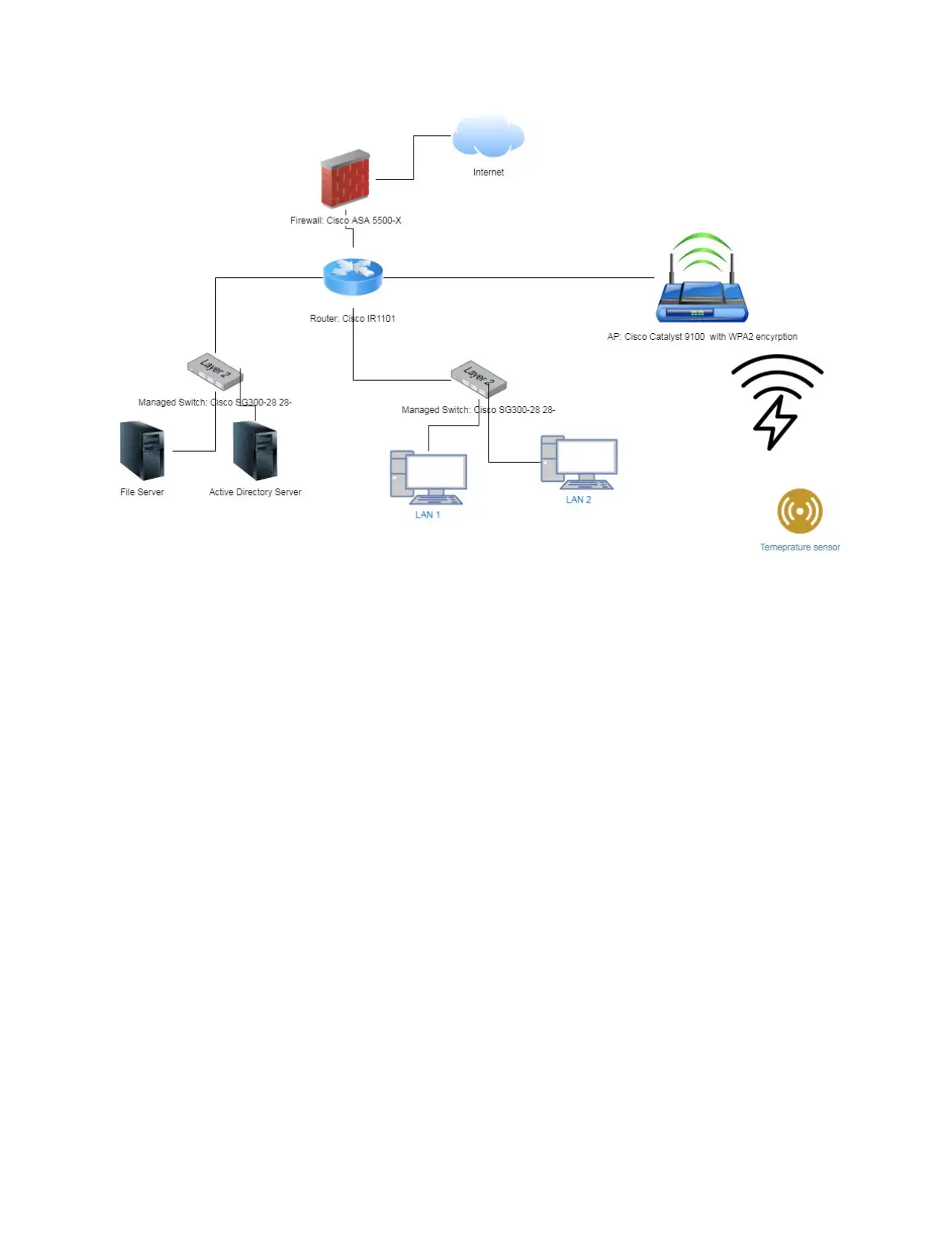
Proposed Countermeasure(s)/Solution(s)
To salvage the situation, the report suggests the following countermeasure
First, the company network should use WPS2 wifi encryption model which uses the advanced
encryption standard to encrypt the communication between the different clients and access
points. In theory, their us high computation cost to break encryption done with the AES hence
the company shall have the assurance that the communication is protected from a man in the
middle attacks. The report recommends upgrade the AP to the new Cisco Catalyst 9100 access
which is secure, build for IoT and extremely reliable (Junior et al., 2019)
firmware from the vendor
Acceptable use
The company accepts the employees and authorized users to use the company network
resources within the scope of this policy
Regulatory framework
The company reserved the right to monitor user activities in the network and has the right
to disconnect the user who is deemed to violate the policy
Policy Violation
Any employee or contractor who violates this policy shall be subject to the disciplinary
committee which can lead to suspension of employee or contractor termination of engagement
between the employee and the company
Proposed Countermeasure(s)/Solution(s)
To salvage the situation, the report suggests the following countermeasure
First, the company network should use WPS2 wifi encryption model which uses the advanced
encryption standard to encrypt the communication between the different clients and access
points. In theory, their us high computation cost to break encryption done with the AES hence
the company shall have the assurance that the communication is protected from a man in the
middle attacks. The report recommends upgrade the AP to the new Cisco Catalyst 9100 access
which is secure, build for IoT and extremely reliable (Junior et al., 2019)

Second, the issues of unmanaged switches can be mitigated by the use of Cisco
SG300-28 28-Port Gigabit Managed Switch which has the latest OEM configured to manage
current security threats. The managed switch comes with the latest firmware updates and can be
easily be upgraded to meet the industry standards.
The issue of denial of service can be mitigated by introducing routing devices
connected to the firewall which shall be used to route traffic to various LAN achieving
modularity and layered approach to network design. The switch ports would be put in different
virtual LANs to reduce the impacts of broadcast storms which can bring the whole network to a
standstill
The issue of MQTT can be mitigated by the use of TLS which enhances the security
of IoT devices in the non-constrained environment. Secondly, ECC can be implemented to
ensure data security with fewer requirements
The following diagram visual the proposed solution
SG300-28 28-Port Gigabit Managed Switch which has the latest OEM configured to manage
current security threats. The managed switch comes with the latest firmware updates and can be
easily be upgraded to meet the industry standards.
The issue of denial of service can be mitigated by introducing routing devices
connected to the firewall which shall be used to route traffic to various LAN achieving
modularity and layered approach to network design. The switch ports would be put in different
virtual LANs to reduce the impacts of broadcast storms which can bring the whole network to a
standstill
The issue of MQTT can be mitigated by the use of TLS which enhances the security
of IoT devices in the non-constrained environment. Secondly, ECC can be implemented to
ensure data security with fewer requirements
The following diagram visual the proposed solution
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Apthorpe, N., Reisman, D., & Feamster, N. (2017). A Smart Home is No Castle: Privacy
Vulnerabilities of Encrypted IoT Traffic.
Capano, D. E. (2015). Wireless security basics, standards. Control Engineering, (4), 34.
Junior, D. M., Melo, L., Lu, H., d’Amorim, M., & Prakash, A. (2019). Beware of the App! On
the Vulnerability Surface of Smart Devices through their Companion Apps.
McAfee. (2019, February 26). New IoT Vulnerabilities Illustrate Risks of Connected Devices.
Business Wire (English).
McLaughlin, L. (2008). How to fix 10 security threats on virtual servers Pt 2. (cover story).
NetworkWorld Asia, 4(4), 20–22.
Ray, P. p. (2018). A survey on Internet of Things architectures. Journal of King Saud University
- Computer and Information Sciences, 30(3), 291–319.
https://doi.org/10.1016/j.jksuci.2016.10.003
Riahi Sfar, A., Natalizio, E., Challal, Y., & Chtourou, Z. (2018). A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), 118–
137. https://doi.org/10.1016/j.dcan.2017.04.003
Saleh Mohamed Alnaeli, Melissa Sarnowski, Md Sayedul Aman, Ahmed Abdelgawad, & Kumar
Yelamarthi. (2017). Source Code Vulnerabilities in IoT Software Systems. Advances in
Science, Technology and Engineering Systems, (3), 1502.
https://doi.org/10.25046/aj0203188
Swann, J. (2007). BACK FROM THE BREACH. (cover story). Community Banker, 16(4), 34–
38.
Apthorpe, N., Reisman, D., & Feamster, N. (2017). A Smart Home is No Castle: Privacy
Vulnerabilities of Encrypted IoT Traffic.
Capano, D. E. (2015). Wireless security basics, standards. Control Engineering, (4), 34.
Junior, D. M., Melo, L., Lu, H., d’Amorim, M., & Prakash, A. (2019). Beware of the App! On
the Vulnerability Surface of Smart Devices through their Companion Apps.
McAfee. (2019, February 26). New IoT Vulnerabilities Illustrate Risks of Connected Devices.
Business Wire (English).
McLaughlin, L. (2008). How to fix 10 security threats on virtual servers Pt 2. (cover story).
NetworkWorld Asia, 4(4), 20–22.
Ray, P. p. (2018). A survey on Internet of Things architectures. Journal of King Saud University
- Computer and Information Sciences, 30(3), 291–319.
https://doi.org/10.1016/j.jksuci.2016.10.003
Riahi Sfar, A., Natalizio, E., Challal, Y., & Chtourou, Z. (2018). A roadmap for security
challenges in the Internet of Things. Digital Communications and Networks, 4(2), 118–
137. https://doi.org/10.1016/j.dcan.2017.04.003
Saleh Mohamed Alnaeli, Melissa Sarnowski, Md Sayedul Aman, Ahmed Abdelgawad, & Kumar
Yelamarthi. (2017). Source Code Vulnerabilities in IoT Software Systems. Advances in
Science, Technology and Engineering Systems, (3), 1502.
https://doi.org/10.25046/aj0203188
Swann, J. (2007). BACK FROM THE BREACH. (cover story). Community Banker, 16(4), 34–
38.

Yadong Zhou, Kaiyue Chen, Junjie Zhang, Junyuan Leng, & Yazhe Tang. (2018). Exploiting the
Vulnerability of Flow Table Overflow in Software-Defined Network: Attack Model,
Evaluation, and Defense. Security and Communication Networks.
https://doi.org/10.1155/2018/4760632
Younes, O. (2017). Securing ARP and DHCP for mitigating link layer attacks. Sadhana, 42(12),
2041–2053. https://doi.org/10.1007/s12046-017-0749-y
Vulnerability of Flow Table Overflow in Software-Defined Network: Attack Model,
Evaluation, and Defense. Security and Communication Networks.
https://doi.org/10.1155/2018/4760632
Younes, O. (2017). Securing ARP and DHCP for mitigating link layer attacks. Sadhana, 42(12),
2041–2053. https://doi.org/10.1007/s12046-017-0749-y
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




