CIS4020: Wireless Sensor Networks - Design and Protocol Report
VerifiedAdded on 2022/09/07
|20
|5479
|28
Report
AI Summary
This report delves into the realm of Wireless Sensor Networks (WSNs), presenting a comprehensive analysis of their design and implementation. It begins with an introduction to WSNs, emphasizing their role in data collection and environmental monitoring, and then presents a logical design for a WSN based on the requirements of the California forestry department. The report details the use of Bluetooth connections and wireless access points, providing an IPV6 subnetting scheme. It then explores various protocols essential to WSNs, including routing protocols like AODV, Dynamic Source Routing, and OLSR, as well as MAC protocols such as B-MAC and LMAC, highlighting their functionalities and advantages. Furthermore, the report considers the physical layer's role in data transmission and concludes by discussing enhanced security solutions. This report provides a valuable resource for understanding WSNs, their components, and their practical applications.

Running head: WIRELESS SENSOR NETWORKS
WIRELESS SENSOR NETWORKS
Name of the Student
Name of the University
Author Note
WIRELESS SENSOR NETWORKS
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS SENSOR NETWORKS
Table of Contents
Introduction:...............................................................................................................................2
Discussions.................................................................................................................................3
Logical Design.......................................................................................................................3
IPV6 Subnetting.....................................................................................................................4
Logical Diagram.....................................................................................................................4
Description for the Protocols.................................................................................................4
Enhanced Security Solution...................................................................................................9
Conclusion................................................................................................................................15
References................................................................................................................................16
Table of Contents
Introduction:...............................................................................................................................2
Discussions.................................................................................................................................3
Logical Design.......................................................................................................................3
IPV6 Subnetting.....................................................................................................................4
Logical Diagram.....................................................................................................................4
Description for the Protocols.................................................................................................4
Enhanced Security Solution...................................................................................................9
Conclusion................................................................................................................................15
References................................................................................................................................16

2WIRELESS SENSOR NETWORKS
Introduction:
A wireless sensor network is a category of dispersed and dedicated sensors in order to
record and track the physical conditions of the environment and then organize the data that is
collected at the main location. The wireless network includes number of nodes and base
stations. These networks are utilized in order to observe environmental or physical conditions
like pressure, sound, temperature and many more and then pass data co-operatively through
the network to the central location. There are various types of protocols in the WSNs. The
protocols of the WSNs include the MAC protocols, routing protocols and the physical layer
protocols.
The report deals with an organization AMY Networks, which are a consultancy
business and the operations of the organization, is to installs, designs and operates various
types of wired and the wireless networks for the research businesses and research. The report
focuses on the network solution that will be provided by the AMY Networks. As the AMY
Networks is one of the leaders of project, the company is asked in order to answer to an
request to Tender for the network design.
Introduction:
A wireless sensor network is a category of dispersed and dedicated sensors in order to
record and track the physical conditions of the environment and then organize the data that is
collected at the main location. The wireless network includes number of nodes and base
stations. These networks are utilized in order to observe environmental or physical conditions
like pressure, sound, temperature and many more and then pass data co-operatively through
the network to the central location. There are various types of protocols in the WSNs. The
protocols of the WSNs include the MAC protocols, routing protocols and the physical layer
protocols.
The report deals with an organization AMY Networks, which are a consultancy
business and the operations of the organization, is to installs, designs and operates various
types of wired and the wireless networks for the research businesses and research. The report
focuses on the network solution that will be provided by the AMY Networks. As the AMY
Networks is one of the leaders of project, the company is asked in order to answer to an
request to Tender for the network design.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3WIRELESS SENSOR NETWORKS
Discussions
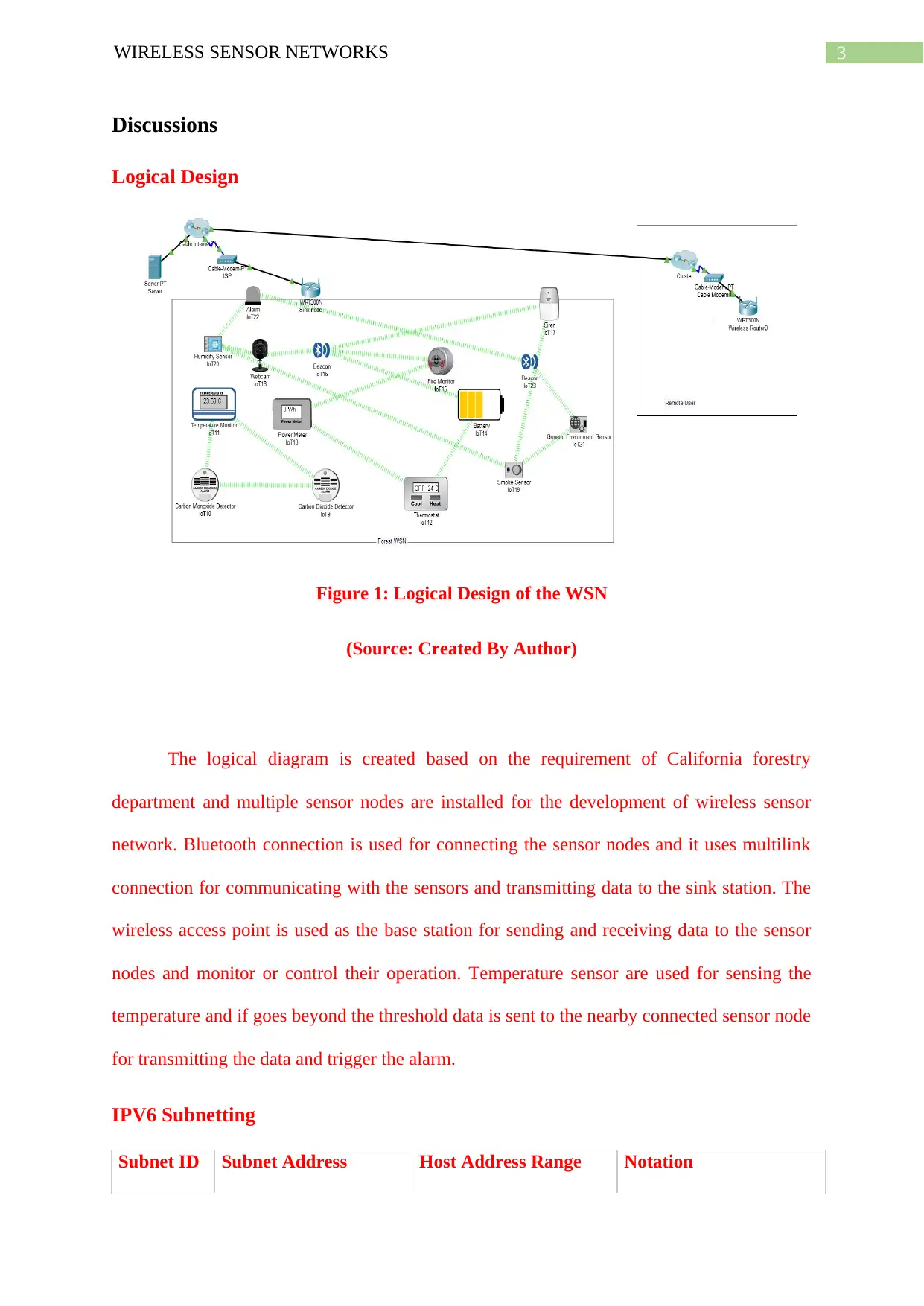
Logical Design
Figure 1: Logical Design of the WSN
(Source: Created By Author)
The logical diagram is created based on the requirement of California forestry
department and multiple sensor nodes are installed for the development of wireless sensor
network. Bluetooth connection is used for connecting the sensor nodes and it uses multilink
connection for communicating with the sensors and transmitting data to the sink station. The
wireless access point is used as the base station for sending and receiving data to the sensor
nodes and monitor or control their operation. Temperature sensor are used for sensing the
temperature and if goes beyond the threshold data is sent to the nearby connected sensor node
for transmitting the data and trigger the alarm.
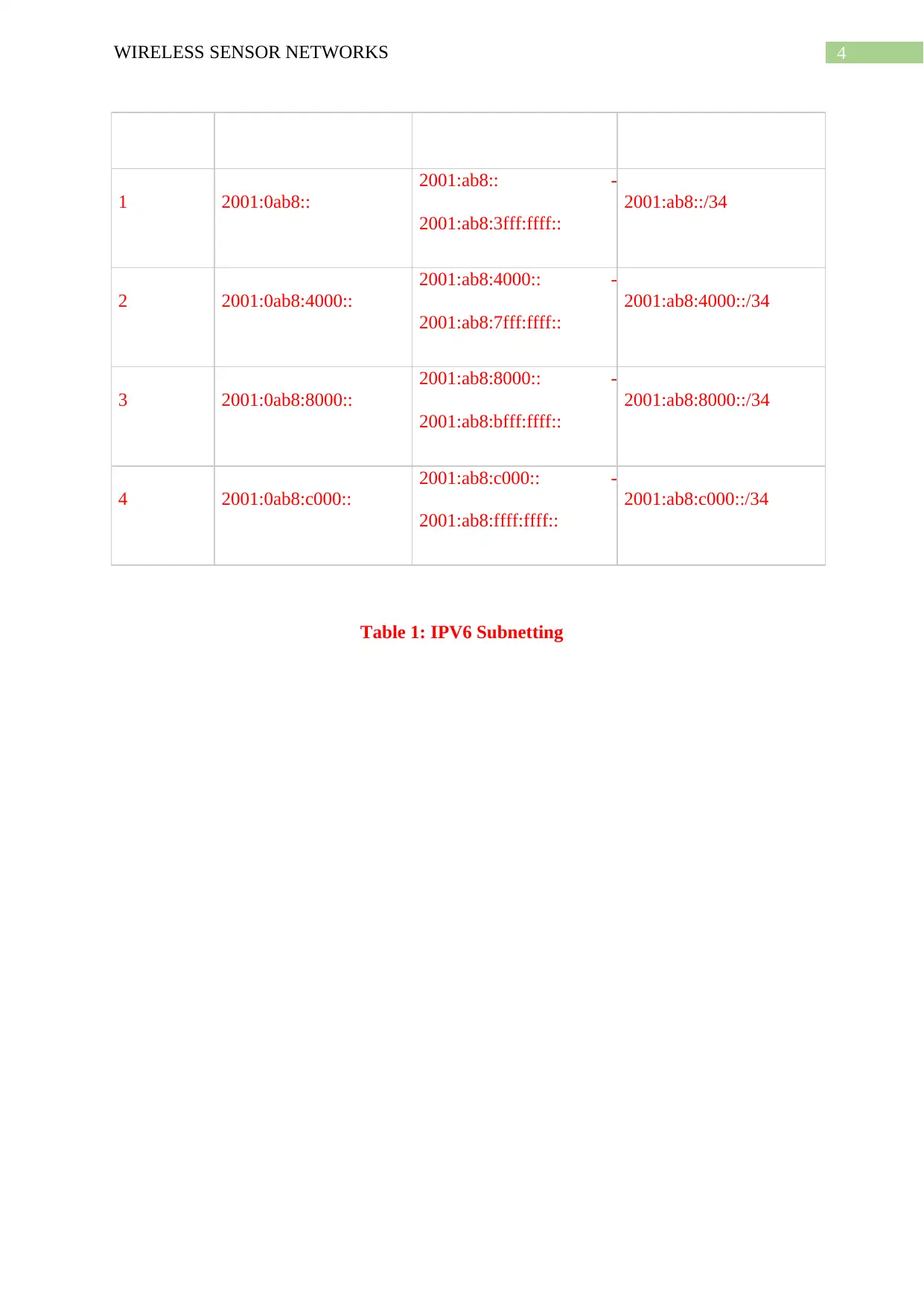
IPV6 Subnetting
Subnet ID Subnet Address Host Address Range Notation
Discussions
Logical Design
Figure 1: Logical Design of the WSN
(Source: Created By Author)
The logical diagram is created based on the requirement of California forestry
department and multiple sensor nodes are installed for the development of wireless sensor
network. Bluetooth connection is used for connecting the sensor nodes and it uses multilink
connection for communicating with the sensors and transmitting data to the sink station. The
wireless access point is used as the base station for sending and receiving data to the sensor
nodes and monitor or control their operation. Temperature sensor are used for sensing the
temperature and if goes beyond the threshold data is sent to the nearby connected sensor node
for transmitting the data and trigger the alarm.
IPV6 Subnetting
Subnet ID Subnet Address Host Address Range Notation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4WIRELESS SENSOR NETWORKS
1 2001:0ab8::
2001:ab8:: -
2001:ab8:3fff:ffff::
2001:ab8::/34
2 2001:0ab8:4000::
2001:ab8:4000:: -
2001:ab8:7fff:ffff::
2001:ab8:4000::/34
3 2001:0ab8:8000::
2001:ab8:8000:: -
2001:ab8:bfff:ffff::
2001:ab8:8000::/34
4 2001:0ab8:c000::
2001:ab8:c000:: -
2001:ab8:ffff:ffff::
2001:ab8:c000::/34
Table 1: IPV6 Subnetting
1 2001:0ab8::
2001:ab8:: -
2001:ab8:3fff:ffff::
2001:ab8::/34
2 2001:0ab8:4000::
2001:ab8:4000:: -
2001:ab8:7fff:ffff::
2001:ab8:4000::/34
3 2001:0ab8:8000::
2001:ab8:8000:: -
2001:ab8:bfff:ffff::
2001:ab8:8000::/34
4 2001:0ab8:c000::
2001:ab8:c000:: -
2001:ab8:ffff:ffff::
2001:ab8:c000::/34
Table 1: IPV6 Subnetting
5WIRELESS SENSOR NETWORKS
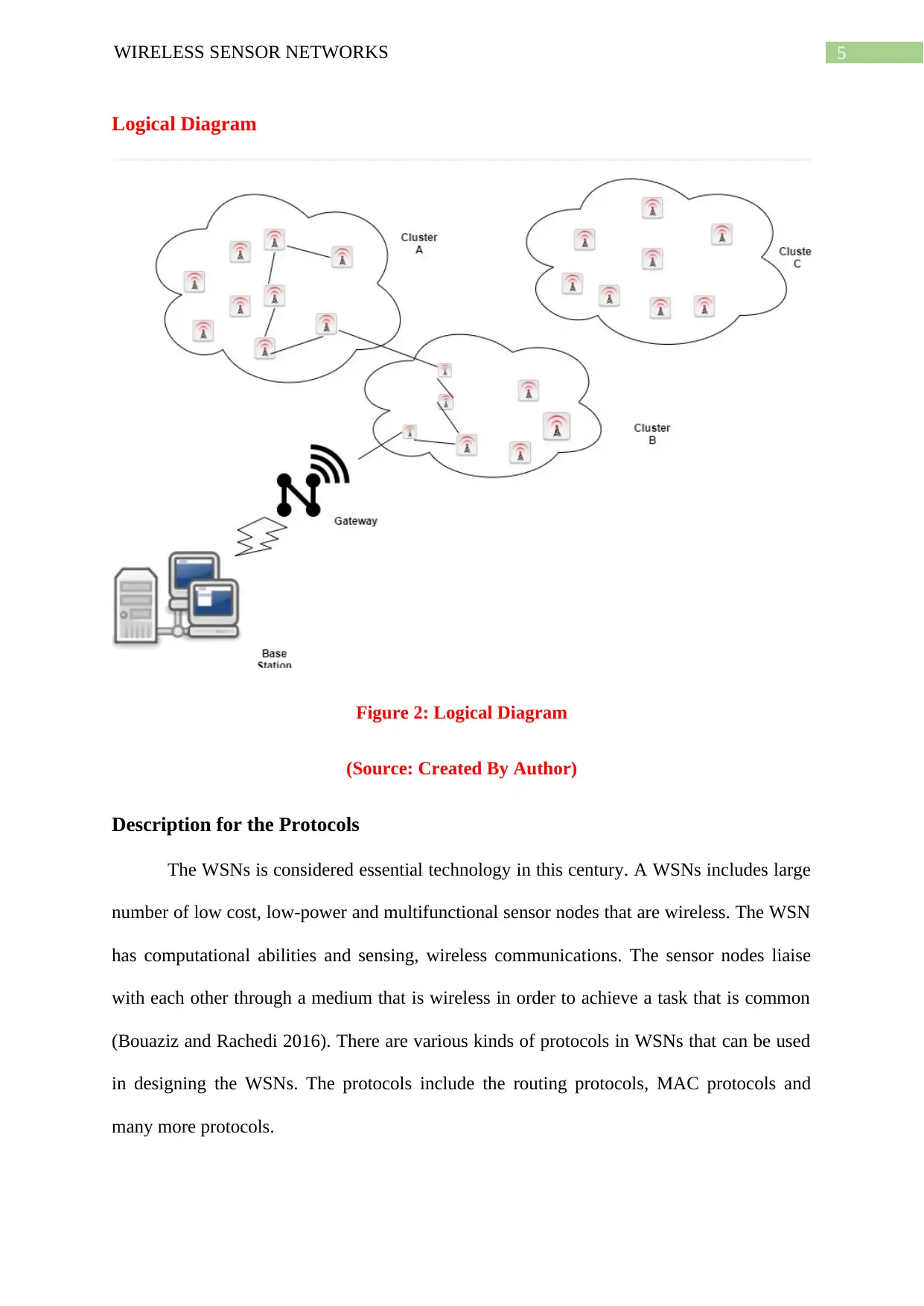
Logical Diagram
Figure 2: Logical Diagram
(Source: Created By Author)
Description for the Protocols
The WSNs is considered essential technology in this century. A WSNs includes large
number of low cost, low-power and multifunctional sensor nodes that are wireless. The WSN
has computational abilities and sensing, wireless communications. The sensor nodes liaise
with each other through a medium that is wireless in order to achieve a task that is common
(Bouaziz and Rachedi 2016). There are various kinds of protocols in WSNs that can be used
in designing the WSNs. The protocols include the routing protocols, MAC protocols and
many more protocols.
Logical Diagram
Figure 2: Logical Diagram
(Source: Created By Author)
Description for the Protocols
The WSNs is considered essential technology in this century. A WSNs includes large
number of low cost, low-power and multifunctional sensor nodes that are wireless. The WSN
has computational abilities and sensing, wireless communications. The sensor nodes liaise
with each other through a medium that is wireless in order to achieve a task that is common
(Bouaziz and Rachedi 2016). There are various kinds of protocols in WSNs that can be used
in designing the WSNs. The protocols include the routing protocols, MAC protocols and
many more protocols.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIRELESS SENSOR NETWORKS
The routing protocols that can be utilised in the design of the WSNs include AODV
(Ad-hoc on-demand distance vector routing system), Dynamic source routing and Optimized
link state routing (OLSR) (Arora, Sharma and Sachdeva 2016).
The AODV is a protocol that is reactive on solicitation. The AODV is developed for
the networks that are infrastructure-less Mobile. The AODV engage the methodology of on-
demand routing for the formation of route in the middle of the nodes of network. The path is
created solitary when the node of the source want packs of data that are direct and the route
that is pre-set is maintained as long as the node of the source requires (Yan, Zhou and Ding
2016). That is why the protocol of routing is known as on-demand. The AODV routing
satisfies the broadcast, unicast and the multicast routing. The routing protocols of AODV
directs the packets that are among the nodes of mobile of the ad-hoc network that is wireless
(Kumar et al 2017). The AODV allows the nodes of mobile in order to pass packets of data to
the required destination node through neighbour nodes that are not able to openly connect the
link. The material of tables of routing is switched fitfully among the nodes of neighbour and
prepared for the updates that are sudden.
The AODV protocol selects round-free and shortest path from the table of routing in
order to move the packets.
The Dynamic Source Routing is protocol of routing that is utilized in the WSN. The
Dynamic source routing can be on demand or reactive. This protocol utilizes source routing
in place of tables of routing. The routing in the protocol of DSR is split into two parts, route
maintenance and route discovery (Kafi, Othman and Badache 2017).
The node of the source will initiate a phase of route discovery and this is the stage that
consists of messages of route reply and route request. In the DSR routing, only the node of
destination will reply to the messages of route reply to the source node unlike in the AODV
The routing protocols that can be utilised in the design of the WSNs include AODV
(Ad-hoc on-demand distance vector routing system), Dynamic source routing and Optimized
link state routing (OLSR) (Arora, Sharma and Sachdeva 2016).
The AODV is a protocol that is reactive on solicitation. The AODV is developed for
the networks that are infrastructure-less Mobile. The AODV engage the methodology of on-
demand routing for the formation of route in the middle of the nodes of network. The path is
created solitary when the node of the source want packs of data that are direct and the route
that is pre-set is maintained as long as the node of the source requires (Yan, Zhou and Ding
2016). That is why the protocol of routing is known as on-demand. The AODV routing
satisfies the broadcast, unicast and the multicast routing. The routing protocols of AODV
directs the packets that are among the nodes of mobile of the ad-hoc network that is wireless
(Kumar et al 2017). The AODV allows the nodes of mobile in order to pass packets of data to
the required destination node through neighbour nodes that are not able to openly connect the
link. The material of tables of routing is switched fitfully among the nodes of neighbour and
prepared for the updates that are sudden.
The AODV protocol selects round-free and shortest path from the table of routing in
order to move the packets.
The Dynamic Source Routing is protocol of routing that is utilized in the WSN. The
Dynamic source routing can be on demand or reactive. This protocol utilizes source routing
in place of tables of routing. The routing in the protocol of DSR is split into two parts, route
maintenance and route discovery (Kafi, Othman and Badache 2017).
The node of the source will initiate a phase of route discovery and this is the stage that
consists of messages of route reply and route request. In the DSR routing, only the node of
destination will reply to the messages of route reply to the source node unlike in the AODV
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS SENSOR NETWORKS
protocol where each intermediate node would reply with the messages or route reply. The
aim of the next stage route maintenance is to keep away from flooding messages and it is
utilized for the nodes shortening between the destination and the source (Reddy and Devi
2018).
The full form of OLSR is optimized link state routing belongs to the classification of
routing protocols that are proactive and it utilizes practice that are focused on table. The main
disadvantage of OLSR is that is has a large overhead. In order to compensate this delay, the
multipoint relays are utilized in order to overcome the massive overhead. For the
transmission of data, three nodes that are adjacent are utilized as multipoint relay by each
node. No control node that is consistent is needed as every node sends it alternating (Sarkar
and Murugan 2016).
The design of the protocols of routing for the WSNs is challenging due to the
constraints of several networks. The WSNs suffer the disadvantage of several resources of
network, for example, bandwidth, energy, storage and central processing unit (Press 2016).
The communication in the WSN is alienated into quite a few layers. The medium
access control protocol tries to keep away from the collisions by disallowing two nodes that
are interfering in order to transmit at the similar time. This enables an operation of the
network that is successful. The main goals of design of the MAC protocols are to give quality
of service and high throughput. The protocols of MAC of the WSN give more priority to the
energy consumption than the requirement of quality of services (Ait Aoudia et al 2017). a
variety of protocols of MAC are created for the WSNs. The typical MAC protocols include B
MAC, X MAC, T MAC and many more such protocols. In order to increase the life of
battery, the MAC protocols execute the mechanism of active/sleep. The main object of the
WSNs is to increase the lifetime of the networks. There are two main classifications of the
protocol where each intermediate node would reply with the messages or route reply. The
aim of the next stage route maintenance is to keep away from flooding messages and it is
utilized for the nodes shortening between the destination and the source (Reddy and Devi
2018).
The full form of OLSR is optimized link state routing belongs to the classification of
routing protocols that are proactive and it utilizes practice that are focused on table. The main
disadvantage of OLSR is that is has a large overhead. In order to compensate this delay, the
multipoint relays are utilized in order to overcome the massive overhead. For the
transmission of data, three nodes that are adjacent are utilized as multipoint relay by each
node. No control node that is consistent is needed as every node sends it alternating (Sarkar
and Murugan 2016).
The design of the protocols of routing for the WSNs is challenging due to the
constraints of several networks. The WSNs suffer the disadvantage of several resources of
network, for example, bandwidth, energy, storage and central processing unit (Press 2016).
The communication in the WSN is alienated into quite a few layers. The medium
access control protocol tries to keep away from the collisions by disallowing two nodes that
are interfering in order to transmit at the similar time. This enables an operation of the
network that is successful. The main goals of design of the MAC protocols are to give quality
of service and high throughput. The protocols of MAC of the WSN give more priority to the
energy consumption than the requirement of quality of services (Ait Aoudia et al 2017). a
variety of protocols of MAC are created for the WSNs. The typical MAC protocols include B
MAC, X MAC, T MAC and many more such protocols. In order to increase the life of
battery, the MAC protocols execute the mechanism of active/sleep. The main object of the
WSNs is to increase the lifetime of the networks. There are two main classifications of the

8WIRELESS SENSOR NETWORKS
MAC protocols. These include the TDMA based protocol and the CSMA based protocol. The
MAC protocol that will be utilised in the WSN delivered by the company will be B MAC and
L MAC.
The full form of B MAC is Berkeley MAC, this protocol is used widely, and it is a
part of TinyOS. This MAC protocol employs listening that is low power in order to reduce
consumption of power because of inactive listening. The nodes have a period of sleep and
after the nodes wake up, they sense the medium for the preambles. If no preamble is detected,
then again the nodes go back to doze. If a preamble is disovered, the nodes stay awake and
then receive the packets of data after the preamble. If the nodes want to send a data, it first
sends a preamble so that the nodes detect it (Yadav and Yadav 2016). After the preamble, it
then sends the packets of data. There are acknowledgments that are optional as well. After the
exchange of the data packet, the nodes then go back to sleep. The preamble does not have any
information of the address. The packets of data contains the address of the recipients so all
the nodes receive the packets of data and the preamble in the communication range of the
sender and not the recipient of the packets of data that are intended. This MAC protocol will
increase the adaptability and the stability of the WSN. Therefore, the B-MAC protocol will
help the WSN of the organization in its scalability and adaptability (Han et al 2016).
The LMAC is a Mac protocol that is based on TDMA. There are transfer timeframes
of data and that are split into time slot. The number of time slot that are present in the
timeframe can be configurable according to the quantity of odes nodes that are present in the
network. Each of the nodes has its time slot and only that specific node can transmit. This
functionality saves the consumption of power, as there are no retransmissions and collisions.
A transmission is composed of a data unit and a control message. The control message
consists of some important components. These include data destination, length of the unit of
data, and the information of the occupation of the time slots. All the nodes that are present
MAC protocols. These include the TDMA based protocol and the CSMA based protocol. The
MAC protocol that will be utilised in the WSN delivered by the company will be B MAC and
L MAC.
The full form of B MAC is Berkeley MAC, this protocol is used widely, and it is a
part of TinyOS. This MAC protocol employs listening that is low power in order to reduce
consumption of power because of inactive listening. The nodes have a period of sleep and
after the nodes wake up, they sense the medium for the preambles. If no preamble is detected,
then again the nodes go back to doze. If a preamble is disovered, the nodes stay awake and
then receive the packets of data after the preamble. If the nodes want to send a data, it first
sends a preamble so that the nodes detect it (Yadav and Yadav 2016). After the preamble, it
then sends the packets of data. There are acknowledgments that are optional as well. After the
exchange of the data packet, the nodes then go back to sleep. The preamble does not have any
information of the address. The packets of data contains the address of the recipients so all
the nodes receive the packets of data and the preamble in the communication range of the
sender and not the recipient of the packets of data that are intended. This MAC protocol will
increase the adaptability and the stability of the WSN. Therefore, the B-MAC protocol will
help the WSN of the organization in its scalability and adaptability (Han et al 2016).
The LMAC is a Mac protocol that is based on TDMA. There are transfer timeframes
of data and that are split into time slot. The number of time slot that are present in the
timeframe can be configurable according to the quantity of odes nodes that are present in the
network. Each of the nodes has its time slot and only that specific node can transmit. This
functionality saves the consumption of power, as there are no retransmissions and collisions.
A transmission is composed of a data unit and a control message. The control message
consists of some important components. These include data destination, length of the unit of
data, and the information of the occupation of the time slots. All the nodes that are present
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9WIRELESS SENSOR NETWORKS
wake up at the start of each of the time slots. If no transmission takes place then the time slots
are assumed to be empty and the nodes again then go back to sleep (Azizi 2016). If
transmission takes place, after getting the message of control, the nodes that are not the
recipient of the messages again go back to sleep. The sender and the recipient node go to
sleep after they have sent or received the transmission. One and only one message can be
sending in each of the time slots. In the first five of the periods, the networks are set up and
no packets of data are sent. The nodes set up the networks and they claim a time slot. Then
they send a message of control to the time slot that they want to reserve. If no collisions
happen, the nodes that are present note that the time slot is asserted. If there is more than one
node and they all claim the similar time slot then collision takes place and they randomly
select another time slot that is not claimed. The advantage of this MAC protocol is that it
increases the use of the battery that implements the schedules of sleep. This protocol can be
executed very easily and the messages that are long can be shifted very efficiently utilising
the method of message passing (Kumar and Singh 2017). This MAC protocol should be
deployed in the WSN that the AMY Networks will deliver.
The primary concern for physical layer in the WSN id demodulation and modulation
of the digital data that is the reception and the transmission of the data. This task is generally
carried out by the transceivers in the nodes of the sensor. The major functionality of physical
layer is choosing of the carrier frequency, modulation and demodulation, decryption and
encryption of data and reception and communication of data. The WSNs generally work in
the bands of ISM. The most essential parameters that are to be considered in order to design
the physical layer in the WSN are:
Low power consumption
Low range of reception and transmission
Low complexity
wake up at the start of each of the time slots. If no transmission takes place then the time slots
are assumed to be empty and the nodes again then go back to sleep (Azizi 2016). If
transmission takes place, after getting the message of control, the nodes that are not the
recipient of the messages again go back to sleep. The sender and the recipient node go to
sleep after they have sent or received the transmission. One and only one message can be
sending in each of the time slots. In the first five of the periods, the networks are set up and
no packets of data are sent. The nodes set up the networks and they claim a time slot. Then
they send a message of control to the time slot that they want to reserve. If no collisions
happen, the nodes that are present note that the time slot is asserted. If there is more than one
node and they all claim the similar time slot then collision takes place and they randomly
select another time slot that is not claimed. The advantage of this MAC protocol is that it
increases the use of the battery that implements the schedules of sleep. This protocol can be
executed very easily and the messages that are long can be shifted very efficiently utilising
the method of message passing (Kumar and Singh 2017). This MAC protocol should be
deployed in the WSN that the AMY Networks will deliver.
The primary concern for physical layer in the WSN id demodulation and modulation
of the digital data that is the reception and the transmission of the data. This task is generally
carried out by the transceivers in the nodes of the sensor. The major functionality of physical
layer is choosing of the carrier frequency, modulation and demodulation, decryption and
encryption of data and reception and communication of data. The WSNs generally work in
the bands of ISM. The most essential parameters that are to be considered in order to design
the physical layer in the WSN are:
Low power consumption
Low range of reception and transmission
Low complexity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10WIRELESS SENSOR NETWORKS
Interference from the other systems that are present and that work in the similar band
High rate of data only for short duration of time and low rates of data for long duration of
time
Low cycle of duty that is most of the time the nodes of the sensor are switched off
The most challenging thing in the design of physical layer of the WSNs in to find out the
transceivers that are low cost and that will consume very less power. The schemes of
modulation that are simple and are robust in order to provide the services that are required
(Zhu, Zou and Zheng 2017).
The protocols of the WSNs have various advantages and it will help the WSNs that
the company to extend the life span of the network will supply it. The protocol of routing will
extend the lifetime of the network and maintain a good connectedness between the nodes in
the sensor networks. The replacement of battery in the sensors is feasible. This is because
most of the sensors are placed randomly in the network. The MAC protocols will also help
the WSN to amplify the lifetime of the networks by reducing the energy that is wasted by
reducing the inactive listening by making periods of listen and sleep constant and predefined.
There is also a disadvantage of this protocol. He disadvantage is that when a node lies in
between the two cluster that are awake, the nodes has to follows two various schedule and it
will consume more power (Radhappa et al 2018). The physical layer or the protocol of
physical layer of the wireless sensor network has the advantage of low cost, low consumption
of power and a good range of communication in order to upgrade the life of battery. Thus,
these protocols will help the WSNs to have a prolong lifetime of the networks.
Enhanced Security Solution
There are various layers in the WSNs that will provide enhanced security solutions to the
organization. The project is to implement 1500 specially made battery operated wireless
Interference from the other systems that are present and that work in the similar band
High rate of data only for short duration of time and low rates of data for long duration of
time
Low cycle of duty that is most of the time the nodes of the sensor are switched off
The most challenging thing in the design of physical layer of the WSNs in to find out the
transceivers that are low cost and that will consume very less power. The schemes of
modulation that are simple and are robust in order to provide the services that are required
(Zhu, Zou and Zheng 2017).
The protocols of the WSNs have various advantages and it will help the WSNs that
the company to extend the life span of the network will supply it. The protocol of routing will
extend the lifetime of the network and maintain a good connectedness between the nodes in
the sensor networks. The replacement of battery in the sensors is feasible. This is because
most of the sensors are placed randomly in the network. The MAC protocols will also help
the WSN to amplify the lifetime of the networks by reducing the energy that is wasted by
reducing the inactive listening by making periods of listen and sleep constant and predefined.
There is also a disadvantage of this protocol. He disadvantage is that when a node lies in
between the two cluster that are awake, the nodes has to follows two various schedule and it
will consume more power (Radhappa et al 2018). The physical layer or the protocol of
physical layer of the wireless sensor network has the advantage of low cost, low consumption
of power and a good range of communication in order to upgrade the life of battery. Thus,
these protocols will help the WSNs to have a prolong lifetime of the networks.
Enhanced Security Solution
There are various layers in the WSNs that will provide enhanced security solutions to the
organization. The project is to implement 1500 specially made battery operated wireless

11WIRELESS SENSOR NETWORKS
sensors. The sensors must function on a globally companionable ISM band with series spread
spectrum that is direct. The various layers in the WSNs include the Network Layer, Mac
Layer, Physical layer and security.
Network Layer
The Network layer in the WSNs is one of the most researched topics in the WSNs. Many
algorithms and protocols of routing have been proposed through the Wireless Sensor
Network’s development. The major aim of the protocols of routing is well-organized delivery
of information between the sink and the sensors. The consumption of energy is one of the
primary concerns in the creation of any protocols of routing for the WSNs (Kocakulak and
Butun 2017). Due to the incomplete assets of energy of the nodes of sensors, the data those
are present required to be delivered in a manner that is energy-efficient. Hence, there are
many routing metrics that are conventional should be enquired conventionally and new
routing metrics that are enery-efficient for the WSNs.
The WSNs includes many numbers of nodes. The requirement to watch the physical
phenomena in detail can also need a high-density implementation of these nodes. The great
numbers of nodes that are present prevent the information that is global of the topology of
network from being acquired at each of the nodes. Therefore, the protocols that are fully
distributed that operate with very less knowledge of the topology of the network. The local
information exchange should be limited in order to upgrade the efficiency of energy of the
network (Pritchard, Hancke and Abu-Mahfouz 2017).
The large number of nodes of sensor in a network prevents the addresses that are unique
from getting assigned to each of the nodes. While the schemes of local addressing can be
used in order to facilitate communication between the neighbours. The routing protocols that
are based on address are not feasible due to large overhead needed to utilise the distinct
sensors. The sensors must function on a globally companionable ISM band with series spread
spectrum that is direct. The various layers in the WSNs include the Network Layer, Mac
Layer, Physical layer and security.
Network Layer
The Network layer in the WSNs is one of the most researched topics in the WSNs. Many
algorithms and protocols of routing have been proposed through the Wireless Sensor
Network’s development. The major aim of the protocols of routing is well-organized delivery
of information between the sink and the sensors. The consumption of energy is one of the
primary concerns in the creation of any protocols of routing for the WSNs (Kocakulak and
Butun 2017). Due to the incomplete assets of energy of the nodes of sensors, the data those
are present required to be delivered in a manner that is energy-efficient. Hence, there are
many routing metrics that are conventional should be enquired conventionally and new
routing metrics that are enery-efficient for the WSNs.
The WSNs includes many numbers of nodes. The requirement to watch the physical
phenomena in detail can also need a high-density implementation of these nodes. The great
numbers of nodes that are present prevent the information that is global of the topology of
network from being acquired at each of the nodes. Therefore, the protocols that are fully
distributed that operate with very less knowledge of the topology of the network. The local
information exchange should be limited in order to upgrade the efficiency of energy of the
network (Pritchard, Hancke and Abu-Mahfouz 2017).
The large number of nodes of sensor in a network prevents the addresses that are unique
from getting assigned to each of the nodes. While the schemes of local addressing can be
used in order to facilitate communication between the neighbours. The routing protocols that
are based on address are not feasible due to large overhead needed to utilise the distinct
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





