Wireless Networking: 802.11, VPN, WMAN Technologies and Access Methods
VerifiedAdded on 2020/03/16
|6
|986
|60
Homework Assignment
AI Summary
This document provides a comprehensive analysis of various wireless networking technologies. It begins by comparing and contrasting the physical layers of the 802.11b and 802.11a standards. The assignment then delves into client authentication using 802.11i, detailing the authentication process. It also explains the establishment of secure point-to-point communication channels using Virtual Private Networks (VPNs). Furthermore, the document explores Wireless Metropolitan Area Network (WMAN) techniques, focusing on Wi-Fi and WiMAX, and recommends WiMAX for a specific scenario. The assignment concludes by examining different multiple access methods, including Time Division Multiple Access (TDMA), Code Division Multiple Access (CDMA), and Global System for Mobile Communications (GSM), providing strengths and weaknesses for each. The solution references key sources for each topic.

Question 1
Compare and contrast the workings of physical layers for 802.11b and 802.11a wireless
standards
802.11 a 802. 11b
5 GHz frequency transmission 2.4 GHz frequency transmission
over 50 Mbps data transmission Over 10 Mbps data transmission
uses OFDM multiplexing technique uses direct sequence spread spectrum
multiplexing technique
Question 2
a) Client authentication to authentication server using 802.11i
According to (Baek, Smith, & Kotz, 2004), 802.11i authenticates a client device to a server
by following the following several procedures. Figure 1 shows the summary of the
authentication process.
i) Client device initiates a connection to a wireless network
ii) The initiation request is received by a proxy server which then establishes a virtual
link between the client device and the authentication server.
iii) The authentication server verifies itself to the client and sends a verification request
to the client device
iv) 802.11i protocol warrants that authentication between the client and server follows a
4-way handshake before a connection happens
v) If the client machine is approved by the authenticating server, the proxy server then
approves and establishes an actual port connection between the client device and
authenticating server allowing full access to the network.
Compare and contrast the workings of physical layers for 802.11b and 802.11a wireless
standards
802.11 a 802. 11b
5 GHz frequency transmission 2.4 GHz frequency transmission
over 50 Mbps data transmission Over 10 Mbps data transmission
uses OFDM multiplexing technique uses direct sequence spread spectrum
multiplexing technique
Question 2
a) Client authentication to authentication server using 802.11i
According to (Baek, Smith, & Kotz, 2004), 802.11i authenticates a client device to a server
by following the following several procedures. Figure 1 shows the summary of the
authentication process.
i) Client device initiates a connection to a wireless network
ii) The initiation request is received by a proxy server which then establishes a virtual
link between the client device and the authentication server.
iii) The authentication server verifies itself to the client and sends a verification request
to the client device
iv) 802.11i protocol warrants that authentication between the client and server follows a
4-way handshake before a connection happens
v) If the client machine is approved by the authenticating server, the proxy server then
approves and establishes an actual port connection between the client device and
authenticating server allowing full access to the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 1: Client authentication using 802.11i. Source: (Baek, Smith, & Kotz, 2004)
b) Establishing an encrypted secure point to point communication channel between on
a public network using virtual private network (VPN)
Basically, Virtual Private Network (VPN) facilities a point to point secure tunnel in a public
network. Thus, VPN enables packet transmission in such a way that a network user can send
data securely to another user as if their devices were directly connected (Pinola, 2017). VPN
facilities such communication by using tunneling protocols that include IP security, secure
socket layer, point to point protocols and layer2 tunneling protocols. When using VPN, a
client machine therefore uses any of the mentioned tunneling protocols to establish a virtual
dedicated point-to-point connection through the Internet to remote server in another network.
The remote server then receives the initiation request, authenticates the VPN client, and
allows for secure data transmission for the client machine in a public network.
Question 3
Wireless Metropolitan Area Network (WMAN) techniques based on 802.16 wireless standard
and can transfer data with speeds of over 10 Mbps (Wi-ManHome, 2017). WMAN
techniques include Wireless Fidelity( Wi-Fi) and WiMAX. Both Wi-Fi and WiMAX are
different in that Wi-Fi covers shorter distances compared to WiMAX which covers longer
distances. In addition, Wi-Fi works better with LANs while WiMAX has capability to work
b) Establishing an encrypted secure point to point communication channel between on
a public network using virtual private network (VPN)
Basically, Virtual Private Network (VPN) facilities a point to point secure tunnel in a public
network. Thus, VPN enables packet transmission in such a way that a network user can send
data securely to another user as if their devices were directly connected (Pinola, 2017). VPN
facilities such communication by using tunneling protocols that include IP security, secure
socket layer, point to point protocols and layer2 tunneling protocols. When using VPN, a
client machine therefore uses any of the mentioned tunneling protocols to establish a virtual
dedicated point-to-point connection through the Internet to remote server in another network.
The remote server then receives the initiation request, authenticates the VPN client, and
allows for secure data transmission for the client machine in a public network.
Question 3
Wireless Metropolitan Area Network (WMAN) techniques based on 802.16 wireless standard
and can transfer data with speeds of over 10 Mbps (Wi-ManHome, 2017). WMAN
techniques include Wireless Fidelity( Wi-Fi) and WiMAX. Both Wi-Fi and WiMAX are
different in that Wi-Fi covers shorter distances compared to WiMAX which covers longer
distances. In addition, Wi-Fi works better with LANs while WiMAX has capability to work

with MANs. For ZeeTech, the best WMAN technology to deploy is WiMAX because of the
following reasons
i) WiMAX is easy to install and setup since it does not require much infrastructure
ii) WIMAX provides internet broadband access for data and voice transmission with
high speeds
iii) WiMAX uses strong encryption techniques such as AES and 3DES and will ensure
data security.
iv) WiMAX technology will support dedicated multipoint and point to point network
connections
Question 4
a) Time Division Multiple Access (TDMA)
TDMA facilitates multiple channel users to transmit data using a single bandwidth unit by
allotting them distinct time slots as shown in Figure 1 below.
Figure 2: Time Disvision Multiple Access. Source: (ITU, 2011)
Strengths
i) TDMA separates users in different time slots hence no signal electromagnetic
interference
ii) TDMA can be used for voice and data communication
iii) Enables less costly signal modulation
following reasons
i) WiMAX is easy to install and setup since it does not require much infrastructure
ii) WIMAX provides internet broadband access for data and voice transmission with
high speeds
iii) WiMAX uses strong encryption techniques such as AES and 3DES and will ensure
data security.
iv) WiMAX technology will support dedicated multipoint and point to point network
connections
Question 4
a) Time Division Multiple Access (TDMA)
TDMA facilitates multiple channel users to transmit data using a single bandwidth unit by
allotting them distinct time slots as shown in Figure 1 below.
Figure 2: Time Disvision Multiple Access. Source: (ITU, 2011)
Strengths
i) TDMA separates users in different time slots hence no signal electromagnetic
interference
ii) TDMA can be used for voice and data communication
iii) Enables less costly signal modulation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Weaknesses
i) It’s possible for signals to be distorted if there’s a mix up in user channels
ii) In the event of movement in the channel, pre-specified time slots for transmission
can lead to interruptions
b) Code Division Multiple Access (CDMA)
CDMA is a multiple access communication technology that utilizes of spread- spectrum
techniques as shown in Figure 2 below. CDMA does not allot channel users separate time
slots like TDMA but uses total channel bandwidth (Segan, 2017).
Figure 3: Code Division Multiple Access. Source: (ITU, 2011)
Strengths
i) CDMA allows many users to make connections for voice and data
ii) CDMA provides high channel capacity which can facilitate many users
iii) CDMA can be used in areas where GSM channel access is impossible
Weaknesses
i) Channel interference
i) CDMA does not accommodate data roaming
ii) Limited support functionalities
i) It’s possible for signals to be distorted if there’s a mix up in user channels
ii) In the event of movement in the channel, pre-specified time slots for transmission
can lead to interruptions
b) Code Division Multiple Access (CDMA)
CDMA is a multiple access communication technology that utilizes of spread- spectrum
techniques as shown in Figure 2 below. CDMA does not allot channel users separate time
slots like TDMA but uses total channel bandwidth (Segan, 2017).
Figure 3: Code Division Multiple Access. Source: (ITU, 2011)
Strengths
i) CDMA allows many users to make connections for voice and data
ii) CDMA provides high channel capacity which can facilitate many users
iii) CDMA can be used in areas where GSM channel access is impossible
Weaknesses
i) Channel interference
i) CDMA does not accommodate data roaming
ii) Limited support functionalities
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
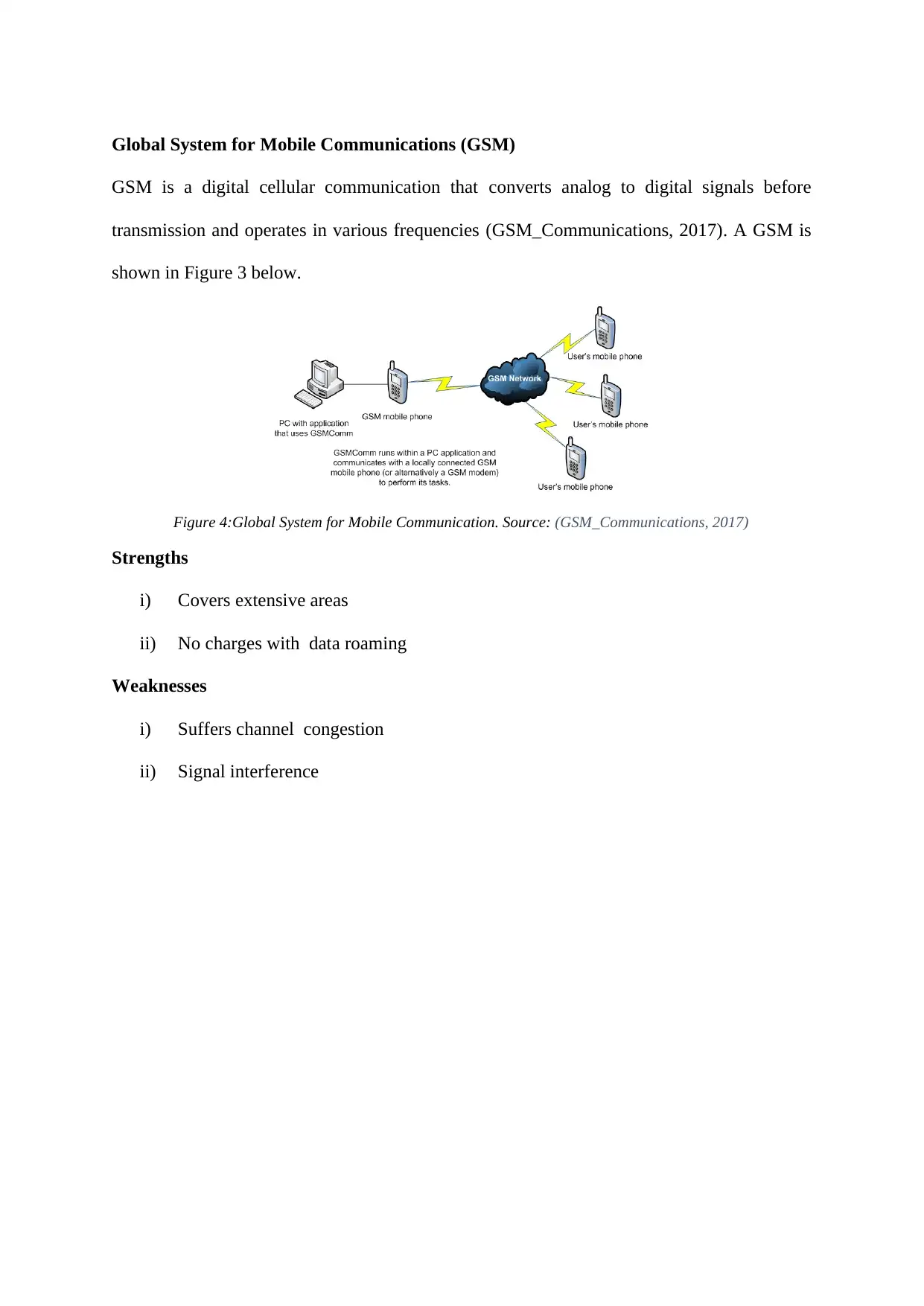
Global System for Mobile Communications (GSM)
GSM is a digital cellular communication that converts analog to digital signals before
transmission and operates in various frequencies (GSM_Communications, 2017). A GSM is
shown in Figure 3 below.
Figure 4:Global System for Mobile Communication. Source: (GSM_Communications, 2017)
Strengths
i) Covers extensive areas
ii) No charges with data roaming
Weaknesses
i) Suffers channel congestion
ii) Signal interference
GSM is a digital cellular communication that converts analog to digital signals before
transmission and operates in various frequencies (GSM_Communications, 2017). A GSM is
shown in Figure 3 below.
Figure 4:Global System for Mobile Communication. Source: (GSM_Communications, 2017)
Strengths
i) Covers extensive areas
ii) No charges with data roaming
Weaknesses
i) Suffers channel congestion
ii) Signal interference

References
Baek, K.-H., Smith, S. W., & Kotz, D. (2004, November). A Survey of WPA and 802.11i
RSN Authentication Protocols. Retrieved from http://www.ists.dartmouth.edu:
http://www.ists.dartmouth.edu/library/96.pdf
GSM_Communications. (2017, September 28). GSM Communication Library . Retrieved
from www.scampers.com : http://www.scampers.org/steve/sms/libraries.htm
ITU. (2011, September 29). All about the technology. Retrieved from itu.int/org:
https://www.itu.int/osg/spu/ni/3G/technology/index.html
Pinola, M. (2017, September 28). What is VPN? Retrieved from www.lifewire.com:
https://www.lifewire.com/what-is-a-vpn-2377977
Segan, S. (2017, September 28). CDMA vs. GSM: What's the Difference? Retrieved from PC
MAG: https://www.pcmag.com/article2/0,2817,2407896,00.asp
Wi-ManHome. (2017, September 29). Wireless Metropolitan Area Networks. Retrieved from
http://www.wi-man.net/: http://www.wi-man.net/
Baek, K.-H., Smith, S. W., & Kotz, D. (2004, November). A Survey of WPA and 802.11i
RSN Authentication Protocols. Retrieved from http://www.ists.dartmouth.edu:
http://www.ists.dartmouth.edu/library/96.pdf
GSM_Communications. (2017, September 28). GSM Communication Library . Retrieved
from www.scampers.com : http://www.scampers.org/steve/sms/libraries.htm
ITU. (2011, September 29). All about the technology. Retrieved from itu.int/org:
https://www.itu.int/osg/spu/ni/3G/technology/index.html
Pinola, M. (2017, September 28). What is VPN? Retrieved from www.lifewire.com:
https://www.lifewire.com/what-is-a-vpn-2377977
Segan, S. (2017, September 28). CDMA vs. GSM: What's the Difference? Retrieved from PC
MAG: https://www.pcmag.com/article2/0,2817,2407896,00.asp
Wi-ManHome. (2017, September 29). Wireless Metropolitan Area Networks. Retrieved from
http://www.wi-man.net/: http://www.wi-man.net/
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





