Cyber Operations Module: Wireshark Capture Analysis Portfolio
VerifiedAdded on 2022/09/06
|11
|2238
|15
Project
AI Summary
This assignment analyzes a Wireshark capture file to identify potential network attacks, specifically focusing on a DNS poisoning attack. The analysis begins with an introduction to Wireshark and its capabilities, detailing how it can be used to analyze network traffic, including identifying communicating nodes, traffic types, and network protocols. The assignment breaks down the packet capture into four parts, examining elements such as Ethernet, Internet (IP), User Datagram Protocol (UDP), and Domain Name System (DNS) to reveal the communication flow between a client and a server. The core of the analysis centers on identifying a cache poisoning attack, explaining how malicious actors exploit vulnerabilities in DNS to redirect users to incorrect websites. The assignment provides a detailed explanation of the attack, including the use of UDP port 53, which is commonly associated with DNS, and how attackers can manipulate the DNS cache to facilitate man-in-the-middle attacks. The conclusion emphasizes the importance of network security and the implementation of measures like DNSSEC to prevent such attacks.

Module Title: Cyber Operations Module Code: 7COM1069
Assignment Title: CyOps Portfolio Individual Assignment
Tutor: Stilianos Vidalis Internal Moderator: Olga Angelopoulou
Student ID Number ONLY: Year Code:
Assignment Title: CyOps Portfolio Individual Assignment
Tutor: Stilianos Vidalis Internal Moderator: Olga Angelopoulou
Student ID Number ONLY: Year Code:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Introduction
Wireshark is an ethereal network analysis tool which can be used to analyze network traffic. In the
analysis capture, information such as end communicating nodes, active nodes, type of traffic, network
protocol being used and the external sources details are revealed. In this assignment, we will be
analyzing the provided Wireshark file capture file with an aim of identifying any form attack that may
have lounged between a communications networks (Bullock & Parker, 2017).
Statistical analysis
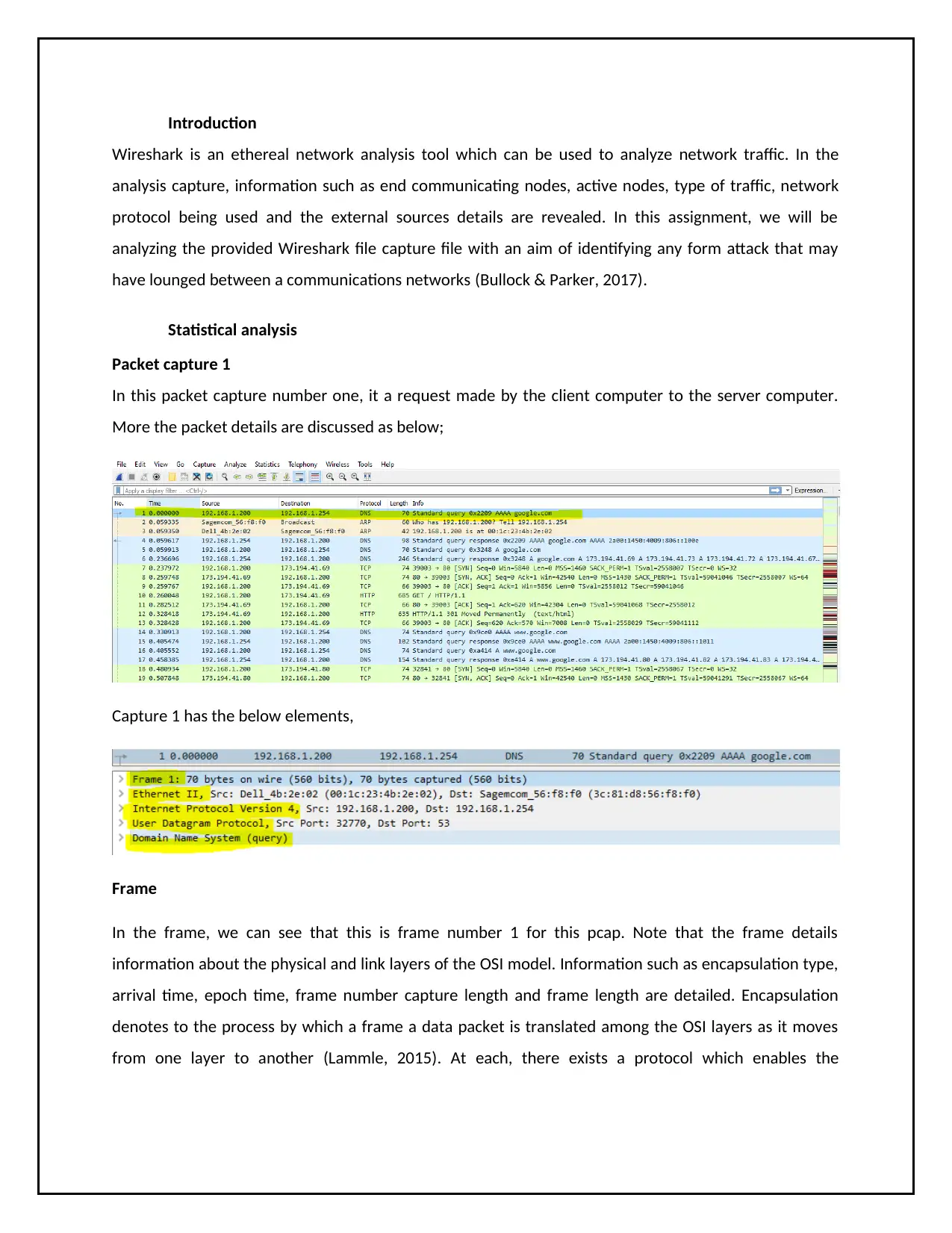
Packet capture 1
In this packet capture number one, it a request made by the client computer to the server computer.
More the packet details are discussed as below;
Capture 1 has the below elements,
Frame
In the frame, we can see that this is frame number 1 for this pcap. Note that the frame details
information about the physical and link layers of the OSI model. Information such as encapsulation type,
arrival time, epoch time, frame number capture length and frame length are detailed. Encapsulation
denotes to the process by which a frame a data packet is translated among the OSI layers as it moves
from one layer to another (Lammle, 2015). At each, there exists a protocol which enables the
Wireshark is an ethereal network analysis tool which can be used to analyze network traffic. In the
analysis capture, information such as end communicating nodes, active nodes, type of traffic, network
protocol being used and the external sources details are revealed. In this assignment, we will be
analyzing the provided Wireshark file capture file with an aim of identifying any form attack that may
have lounged between a communications networks (Bullock & Parker, 2017).
Statistical analysis
Packet capture 1
In this packet capture number one, it a request made by the client computer to the server computer.
More the packet details are discussed as below;
Capture 1 has the below elements,
Frame
In the frame, we can see that this is frame number 1 for this pcap. Note that the frame details
information about the physical and link layers of the OSI model. Information such as encapsulation type,
arrival time, epoch time, frame number capture length and frame length are detailed. Encapsulation
denotes to the process by which a frame a data packet is translated among the OSI layers as it moves
from one layer to another (Lammle, 2015). At each, there exists a protocol which enables the
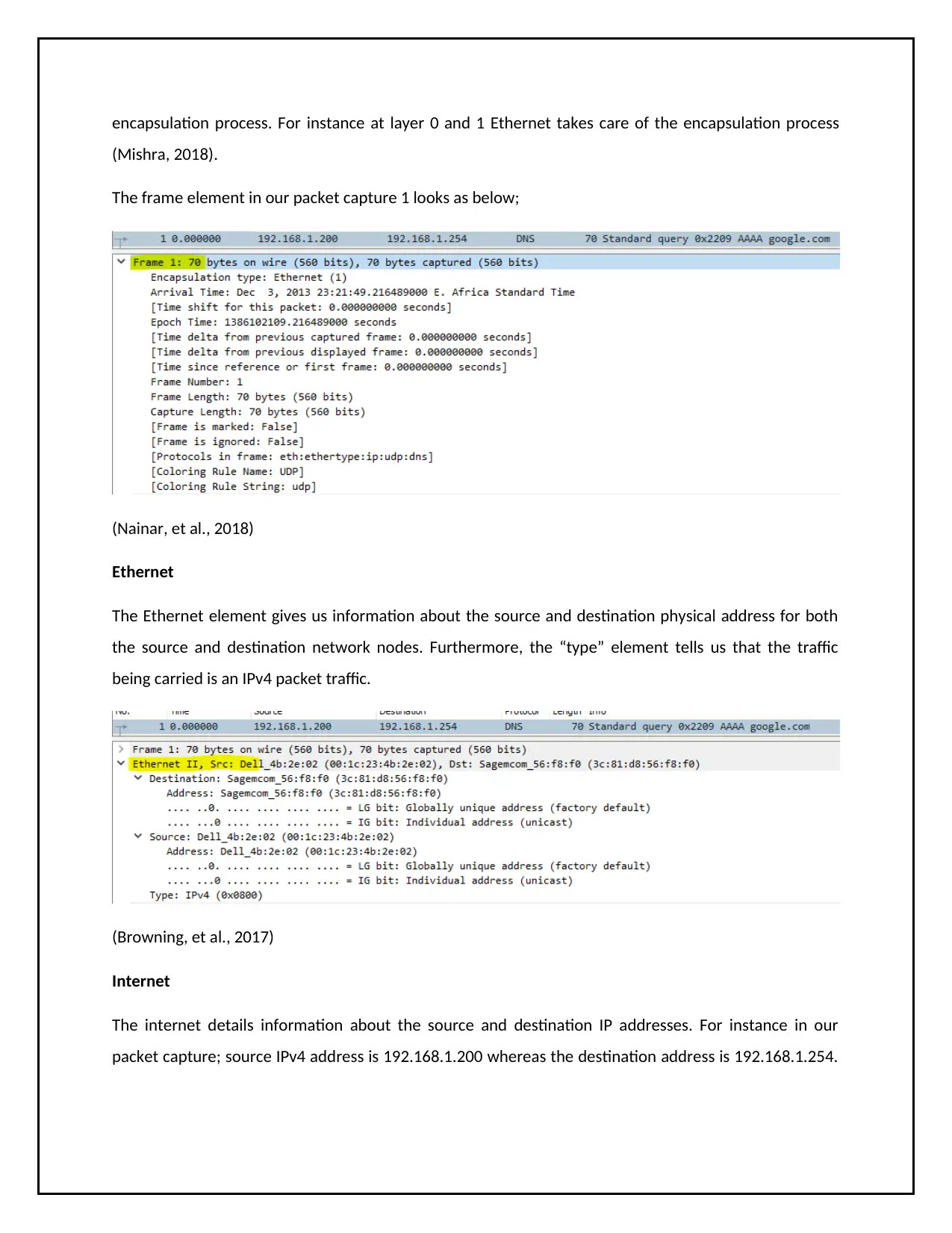
encapsulation process. For instance at layer 0 and 1 Ethernet takes care of the encapsulation process
(Mishra, 2018).
The frame element in our packet capture 1 looks as below;
(Nainar, et al., 2018)
Ethernet
The Ethernet element gives us information about the source and destination physical address for both
the source and destination network nodes. Furthermore, the “type” element tells us that the traffic
being carried is an IPv4 packet traffic.
(Browning, et al., 2017)
Internet
The internet details information about the source and destination IP addresses. For instance in our
packet capture; source IPv4 address is 192.168.1.200 whereas the destination address is 192.168.1.254.
(Mishra, 2018).
The frame element in our packet capture 1 looks as below;
(Nainar, et al., 2018)
Ethernet
The Ethernet element gives us information about the source and destination physical address for both
the source and destination network nodes. Furthermore, the “type” element tells us that the traffic
being carried is an IPv4 packet traffic.
(Browning, et al., 2017)
Internet
The internet details information about the source and destination IP addresses. For instance in our
packet capture; source IPv4 address is 192.168.1.200 whereas the destination address is 192.168.1.254.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
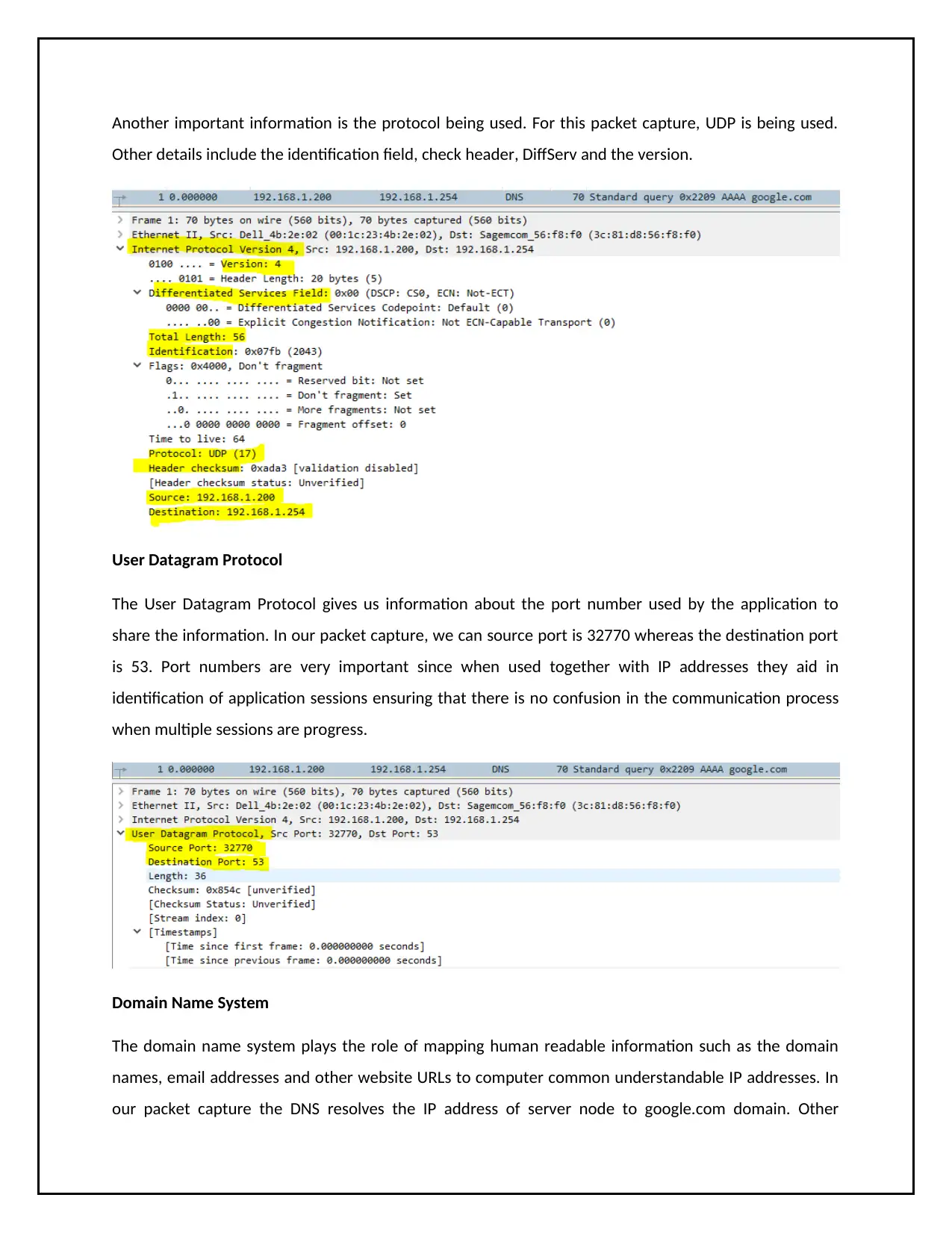
Another important information is the protocol being used. For this packet capture, UDP is being used.
Other details include the identification field, check header, DiffServ and the version.
User Datagram Protocol
The User Datagram Protocol gives us information about the port number used by the application to
share the information. In our packet capture, we can source port is 32770 whereas the destination port
is 53. Port numbers are very important since when used together with IP addresses they aid in
identification of application sessions ensuring that there is no confusion in the communication process
when multiple sessions are progress.
Domain Name System
The domain name system plays the role of mapping human readable information such as the domain
names, email addresses and other website URLs to computer common understandable IP addresses. In
our packet capture the DNS resolves the IP address of server node to google.com domain. Other
Other details include the identification field, check header, DiffServ and the version.
User Datagram Protocol
The User Datagram Protocol gives us information about the port number used by the application to
share the information. In our packet capture, we can source port is 32770 whereas the destination port
is 53. Port numbers are very important since when used together with IP addresses they aid in
identification of application sessions ensuring that there is no confusion in the communication process
when multiple sessions are progress.
Domain Name System
The domain name system plays the role of mapping human readable information such as the domain
names, email addresses and other website URLs to computer common understandable IP addresses. In
our packet capture the DNS resolves the IP address of server node to google.com domain. Other
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
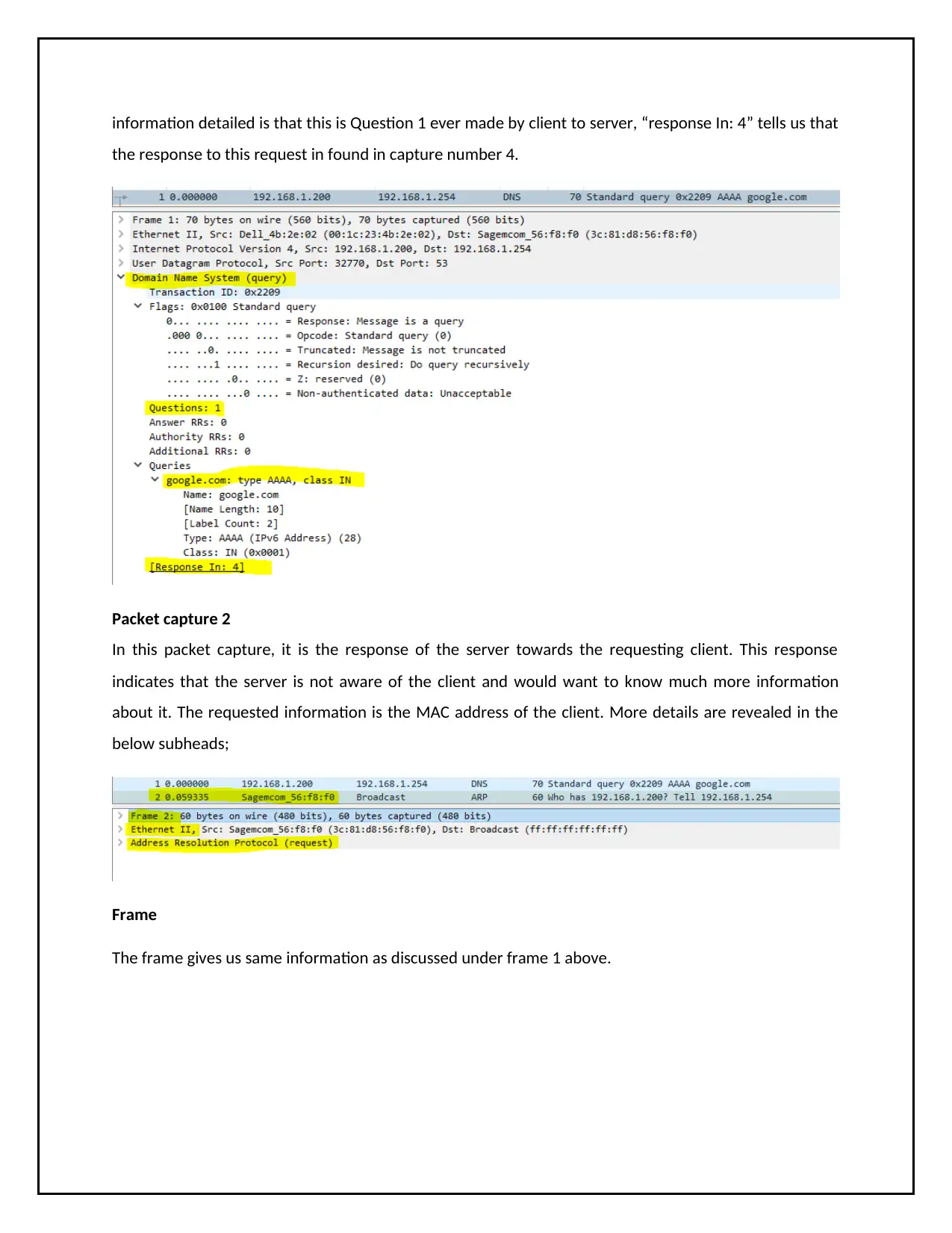
information detailed is that this is Question 1 ever made by client to server, “response In: 4” tells us that
the response to this request in found in capture number 4.
Packet capture 2
In this packet capture, it is the response of the server towards the requesting client. This response
indicates that the server is not aware of the client and would want to know much more information
about it. The requested information is the MAC address of the client. More details are revealed in the
below subheads;
Frame
The frame gives us same information as discussed under frame 1 above.
the response to this request in found in capture number 4.
Packet capture 2
In this packet capture, it is the response of the server towards the requesting client. This response
indicates that the server is not aware of the client and would want to know much more information
about it. The requested information is the MAC address of the client. More details are revealed in the
below subheads;
Frame
The frame gives us same information as discussed under frame 1 above.
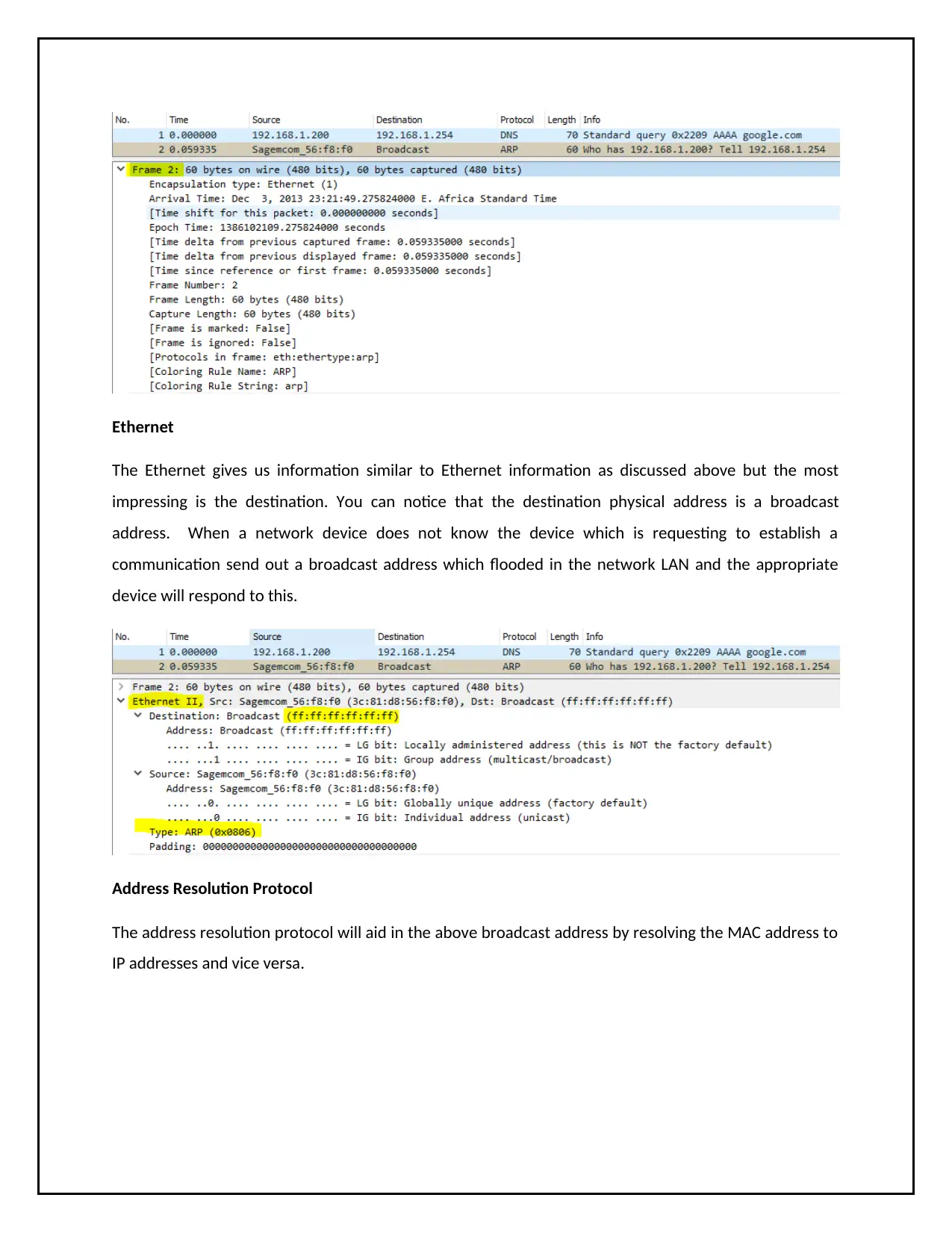
Ethernet
The Ethernet gives us information similar to Ethernet information as discussed above but the most
impressing is the destination. You can notice that the destination physical address is a broadcast
address. When a network device does not know the device which is requesting to establish a
communication send out a broadcast address which flooded in the network LAN and the appropriate
device will respond to this.
Address Resolution Protocol
The address resolution protocol will aid in the above broadcast address by resolving the MAC address to
IP addresses and vice versa.
The Ethernet gives us information similar to Ethernet information as discussed above but the most
impressing is the destination. You can notice that the destination physical address is a broadcast
address. When a network device does not know the device which is requesting to establish a
communication send out a broadcast address which flooded in the network LAN and the appropriate
device will respond to this.
Address Resolution Protocol
The address resolution protocol will aid in the above broadcast address by resolving the MAC address to
IP addresses and vice versa.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
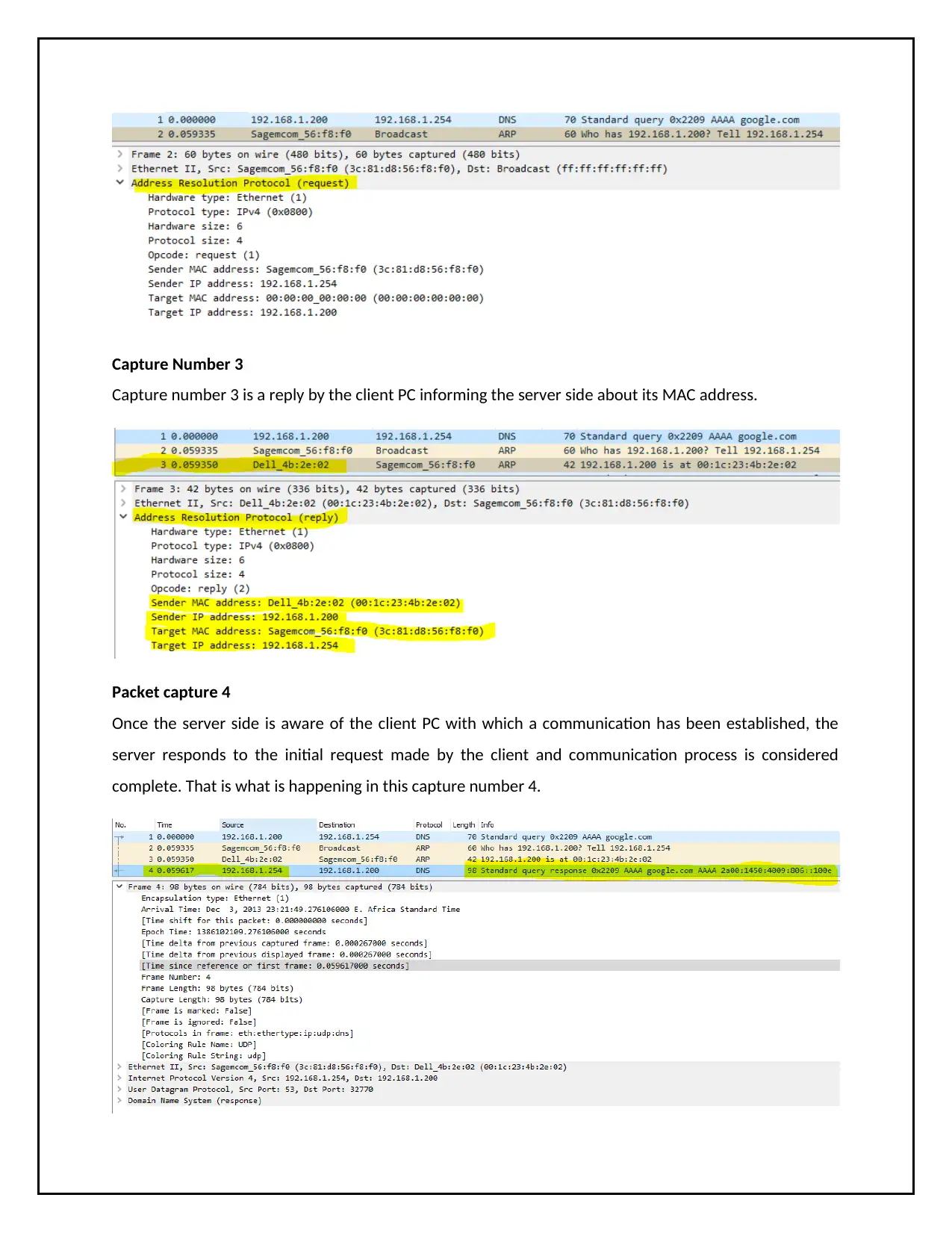
Capture Number 3
Capture number 3 is a reply by the client PC informing the server side about its MAC address.
Packet capture 4
Once the server side is aware of the client PC with which a communication has been established, the
server responds to the initial request made by the client and communication process is considered
complete. That is what is happening in this capture number 4.
Capture number 3 is a reply by the client PC informing the server side about its MAC address.
Packet capture 4
Once the server side is aware of the client PC with which a communication has been established, the
server responds to the initial request made by the client and communication process is considered
complete. That is what is happening in this capture number 4.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Activity Narrative
In this Wireshark capture file, we notice that UDP ports 53 and 32770 are being used in packet capture 1
and 4. According to the past history as observed cyber-security experts, these ports have had bad
reputation since they have been used as a point of vulnerable for systems attack. Cyber-attackers have
exploited these ports and have used them to access into unauthorized network zones.
For instance, port 53, which is used mostly Domain Name System has been used for different forms of
attacks. The most treacherous form of attack is cache poisoning which has been exploited through port
53.
Imagine that a senior high school student changing all the room numbers of their classes and sleeping
rooms so that the new the new students who do not have a clear layout of their school environment will
get a lost a through trying to identify the correct class rooms. Furthermore, you can further imagine that
inequitable room numbers are recorded in the high school directory. Obviously, the new students will
continue finding themselves in wrong classrooms until some individual will take the initiative of notifying
them and correcting them to the appropriate dorms and classrooms.
This a real analogy of DNS cache poisoning. Cache poisoning takes when wrong information is entered
into the DNS cache. A poisoned cache responds with wrong information when network users query the
wrong websites. The DNS poising is as referred to as DNS spoofing (Jajodia & Zhou, 2010). In our
analogy, the class room numbers are the IP addresses of an Internet which enable the web traffic to
reach their desired destinations. The DNS resolver is analogized to high school campus directory, when a
wrong information is kept in the directory, the traffic goes to the fault places until the cache is data is
corrected. It should be noted that having wrong information does not stop the actual websites for their
actual IP addresses (Veracode, 2016).
Since there is no known way for the DNS resolvers to authenticate the information present in their
caches, the incorrect data will remain in the cache till the TTL expires or manual removals are done.
However, there are a number of vulnerabilities which enable the DNS poisoning. Nevertheless, the
primary vulnerability is that the DNS was built for small Internet and on the basis of trust. A more
secured DNS protocol known as DNSSEC has evolved and it aims to give solutions to the challenges
posed by DNS vulnerabilities. However, this protocol has not been widely adopted in the network
environments (Dooley & Rooney, 2017).
In this Wireshark capture file, we notice that UDP ports 53 and 32770 are being used in packet capture 1
and 4. According to the past history as observed cyber-security experts, these ports have had bad
reputation since they have been used as a point of vulnerable for systems attack. Cyber-attackers have
exploited these ports and have used them to access into unauthorized network zones.
For instance, port 53, which is used mostly Domain Name System has been used for different forms of
attacks. The most treacherous form of attack is cache poisoning which has been exploited through port
53.
Imagine that a senior high school student changing all the room numbers of their classes and sleeping
rooms so that the new the new students who do not have a clear layout of their school environment will
get a lost a through trying to identify the correct class rooms. Furthermore, you can further imagine that
inequitable room numbers are recorded in the high school directory. Obviously, the new students will
continue finding themselves in wrong classrooms until some individual will take the initiative of notifying
them and correcting them to the appropriate dorms and classrooms.
This a real analogy of DNS cache poisoning. Cache poisoning takes when wrong information is entered
into the DNS cache. A poisoned cache responds with wrong information when network users query the
wrong websites. The DNS poising is as referred to as DNS spoofing (Jajodia & Zhou, 2010). In our
analogy, the class room numbers are the IP addresses of an Internet which enable the web traffic to
reach their desired destinations. The DNS resolver is analogized to high school campus directory, when a
wrong information is kept in the directory, the traffic goes to the fault places until the cache is data is
corrected. It should be noted that having wrong information does not stop the actual websites for their
actual IP addresses (Veracode, 2016).
Since there is no known way for the DNS resolvers to authenticate the information present in their
caches, the incorrect data will remain in the cache till the TTL expires or manual removals are done.
However, there are a number of vulnerabilities which enable the DNS poisoning. Nevertheless, the
primary vulnerability is that the DNS was built for small Internet and on the basis of trust. A more
secured DNS protocol known as DNSSEC has evolved and it aims to give solutions to the challenges
posed by DNS vulnerabilities. However, this protocol has not been widely adopted in the network
environments (Dooley & Rooney, 2017).

The DNS resolvers offer network client nodes IP addresses which are associated with the domain name.
That is to say that, the DNS resolvers take human-easily readable and understandable website addresses
such as google.com and it is translated to computer readable IP addresses. As soon as a network user
makes an attempt of navigating to the internet website, their OS issue out a request to DNS resolver.
The DNS resolver replies with an IP address and the internet web takes the address and will lounge the
website (Stewart, et al., 2015).
DNS caching works by the DNS resolver saving the responses to IP address requests for a particular
period of time. In such a manner, the resolver is able to respond to future request in a quicker manner
without the need to communicate with servers which are taking part in characteristic DNS resolution
process. A DNS resolver will save the replies in their cache memory provided that the destined TTL
associated has not expired.
In our packet capture scenario, we observe a query made from client computer whose IP address is
92.168.1.200. The dell client computer is offered a reply from Sagecomputer whose IP address is
192.168.1.254. This IP address resolves to be google.com. This note true because google.com has a
known IP address of 8.8.8.8. This is where the suspicion begins in our packet analysis. This implies there
is a cache poison which has taken place and is redirecting resolving incorrect IP addresses to incorrect
domain names. Cache poisoning is also known as man-in-the-middle attack.
Attack Explanation
In a cache poisoning attack, corrupted information is forced into database cache of the DNS.
Unknowingly, the DNS resolver will be forced to associate incorrect IP addresses to inappropriate
domains or computer names. Computing devices depend mostly on the DNS resolver for emails, domain
names or other websites for the DNS resolving role. When the DNS cache database which is poisoned is
queried for some information, the DNS resolver ends mapping wrong IP addresses to wrong domain
names (Lacoste & Wallace, 2014).
DNS cache poison attacks have been used in spreading of computer Trojans and worms. The man-in-the-
middle attack is a clear form of DNS cache poison. In this attack, a rogue computer sits between the
client and the server and it collects all the information from the client and it posts it to the server and it
is capable of collecting all the responses from the server and posts them to the client computer. In
either way, the rogue PC impersonates either the server or the client. This is achieved by the
That is to say that, the DNS resolvers take human-easily readable and understandable website addresses
such as google.com and it is translated to computer readable IP addresses. As soon as a network user
makes an attempt of navigating to the internet website, their OS issue out a request to DNS resolver.
The DNS resolver replies with an IP address and the internet web takes the address and will lounge the
website (Stewart, et al., 2015).
DNS caching works by the DNS resolver saving the responses to IP address requests for a particular
period of time. In such a manner, the resolver is able to respond to future request in a quicker manner
without the need to communicate with servers which are taking part in characteristic DNS resolution
process. A DNS resolver will save the replies in their cache memory provided that the destined TTL
associated has not expired.
In our packet capture scenario, we observe a query made from client computer whose IP address is
92.168.1.200. The dell client computer is offered a reply from Sagecomputer whose IP address is
192.168.1.254. This IP address resolves to be google.com. This note true because google.com has a
known IP address of 8.8.8.8. This is where the suspicion begins in our packet analysis. This implies there
is a cache poison which has taken place and is redirecting resolving incorrect IP addresses to incorrect
domain names. Cache poisoning is also known as man-in-the-middle attack.
Attack Explanation
In a cache poisoning attack, corrupted information is forced into database cache of the DNS.
Unknowingly, the DNS resolver will be forced to associate incorrect IP addresses to inappropriate
domains or computer names. Computing devices depend mostly on the DNS resolver for emails, domain
names or other websites for the DNS resolving role. When the DNS cache database which is poisoned is
queried for some information, the DNS resolver ends mapping wrong IP addresses to wrong domain
names (Lacoste & Wallace, 2014).
DNS cache poison attacks have been used in spreading of computer Trojans and worms. The man-in-the-
middle attack is a clear form of DNS cache poison. In this attack, a rogue computer sits between the
client and the server and it collects all the information from the client and it posts it to the server and it
is capable of collecting all the responses from the server and posts them to the client computer. In
either way, the rogue PC impersonates either the server or the client. This is achieved by the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

vulnerability of the DNS protocol and port 53 which are easy to exploit by the attackers (Teare, et al.,
2015).
Conclusion
Conclusively, we have to accept the fact that our computer systems are vulnerable to either logical or
physical attacks. It is the role of the network administrators to ensure that their network environments
are secured against either forms of attack. Logical attack is the most difficult to prevent. However, there
must be away in which this kind of attack can be stopped from interfering with the web traffic. For
instance, for DNS poisoning, DNSSEC has to be impressed. This protocol verifies the DNS information
origin and integrity. The DNS was never designed with such a form of verification. This opens up for DNS
cache poisoning.
2015).
Conclusion
Conclusively, we have to accept the fact that our computer systems are vulnerable to either logical or
physical attacks. It is the role of the network administrators to ensure that their network environments
are secured against either forms of attack. Logical attack is the most difficult to prevent. However, there
must be away in which this kind of attack can be stopped from interfering with the web traffic. For
instance, for DNS poisoning, DNSSEC has to be impressed. This protocol verifies the DNS information
origin and integrity. The DNS was never designed with such a form of verification. This opens up for DNS
cache poisoning.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Browning, P. W., Tafa, F., Gheorghe, D. & Barinic, D., 2017. Cisco CCNA Simplified: Your Complete Guide
to Passing the Cisco CCNA Routing and Switching Exam. 3 ed. Northampton: Reality Press Ltd.
Bullock, J. & Parker, J. T., 2017. Wireshark for Security Professionals: Using Wireshark and the Metasploit
Framework. 3rd ed. Hoboken: Wiley.
Dooley, M. & Rooney, ., 2017. DNS Security Management. Hoboken: John Wiley & Sons.
Jajodia, S. & Zhou, ., 2010. Security and Privacy in Communication Networks. 6th ed. Springer: New York
City.
Lacoste, R. & Wallace, K., 2014. DNS Snooping. 4th ed. Indianapolis: Cisco Press.
Lammle, T., 2015. CCNA Routing and Switching Complete Study Guide Exam 100-105, Exam 200-105,
Exam 200-125. 2 ed. Indianapolis: Ciscopress.
Mishra, C., 2018. Wireshark 2 Quick Start Guide Secure your network through protocol analysis. 4th ed.
New York City: Appress.
Nainar, N. K., Ramdoss, Y. & Orzach, Y., 2018. Network Analysis Using Wireshark 2 Cookbook: Practical
recipes to analyze and secure your network using Wireshark 2. 2nd ed. Birmingham: Packt Publishing .
Stewart, J. M., Chapple, . & Gibson, ., 2015. CISSP (ISC)2 Certified Information Systems Security
Professional Official. 3rd ed. Hoboken: John Wiley & Sons.
Teare, D. et al., 2015. CCNP Routing and Switching Foundation Learning Guide Library. Indianapolis:
Cisco Press.
Veracode, 2016. CACHE POISONING ATTACK. [Online]
Available at: https://www.veracode.com/security/cache-poisoning
[Accessed 20 December 2019].
Browning, P. W., Tafa, F., Gheorghe, D. & Barinic, D., 2017. Cisco CCNA Simplified: Your Complete Guide
to Passing the Cisco CCNA Routing and Switching Exam. 3 ed. Northampton: Reality Press Ltd.
Bullock, J. & Parker, J. T., 2017. Wireshark for Security Professionals: Using Wireshark and the Metasploit
Framework. 3rd ed. Hoboken: Wiley.
Dooley, M. & Rooney, ., 2017. DNS Security Management. Hoboken: John Wiley & Sons.
Jajodia, S. & Zhou, ., 2010. Security and Privacy in Communication Networks. 6th ed. Springer: New York
City.
Lacoste, R. & Wallace, K., 2014. DNS Snooping. 4th ed. Indianapolis: Cisco Press.
Lammle, T., 2015. CCNA Routing and Switching Complete Study Guide Exam 100-105, Exam 200-105,
Exam 200-125. 2 ed. Indianapolis: Ciscopress.
Mishra, C., 2018. Wireshark 2 Quick Start Guide Secure your network through protocol analysis. 4th ed.
New York City: Appress.
Nainar, N. K., Ramdoss, Y. & Orzach, Y., 2018. Network Analysis Using Wireshark 2 Cookbook: Practical
recipes to analyze and secure your network using Wireshark 2. 2nd ed. Birmingham: Packt Publishing .
Stewart, J. M., Chapple, . & Gibson, ., 2015. CISSP (ISC)2 Certified Information Systems Security
Professional Official. 3rd ed. Hoboken: John Wiley & Sons.
Teare, D. et al., 2015. CCNP Routing and Switching Foundation Learning Guide Library. Indianapolis:
Cisco Press.
Veracode, 2016. CACHE POISONING ATTACK. [Online]
Available at: https://www.veracode.com/security/cache-poisoning
[Accessed 20 December 2019].
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





