University Networking and Communication: Wireshark Lab Assignment
VerifiedAdded on 2023/04/24
|14
|1369
|163
Practical Assignment
AI Summary
This assignment is a Wireshark lab report analyzing ICMP and IPv6 protocols. The report examines ICMP packets, including ping requests and replies, and traceroute functionality. It investigates IP addresses, source and destination ports, ICMP types and codes, and packet headers. The assignment also explores IPv6, analyzing packet headers, fragmentation, and the behavior of fields like TTL and identification across multiple ICMP messages. The student answers questions related to packet structure, constant and changing fields, and the impact of fragmentation on data transmission. The report concludes with a bibliography of relevant sources. Desklib provides a platform for students to access similar solved assignments and study resources to enhance their understanding of networking concepts.

Running head: NETWORKING AND COMMUNICATION
Networking and Communication
Name of the Student
Name of the University
Author’s Note
Networking and Communication
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
NETWORKING AND COMMUNICATION
Wireshark Lab: ICMP
1. ICMP and Ping
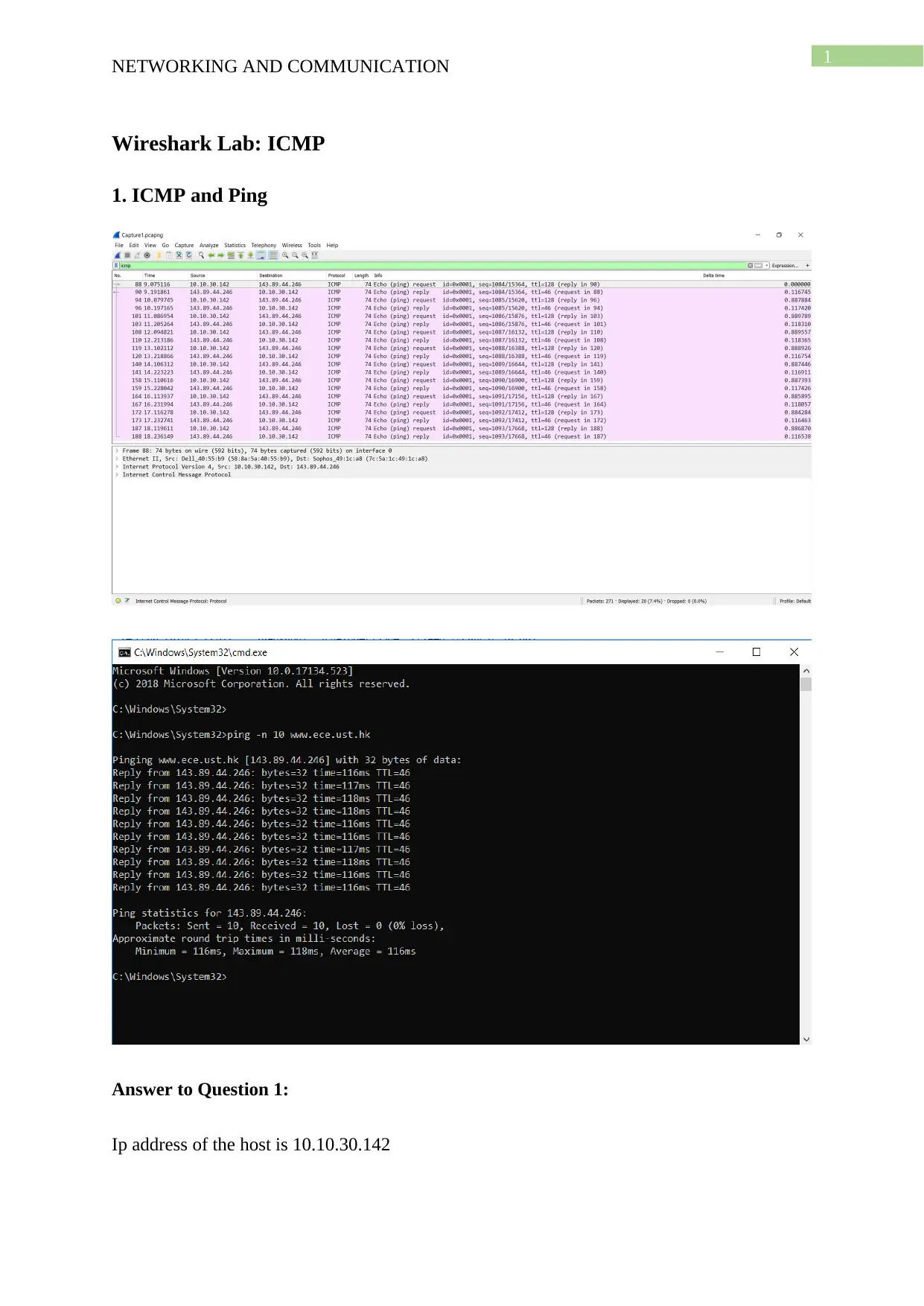
Answer to Question 1:
Ip address of the host is 10.10.30.142
NETWORKING AND COMMUNICATION
Wireshark Lab: ICMP
1. ICMP and Ping
Answer to Question 1:
Ip address of the host is 10.10.30.142
2
NETWORKING AND COMMUNICATION
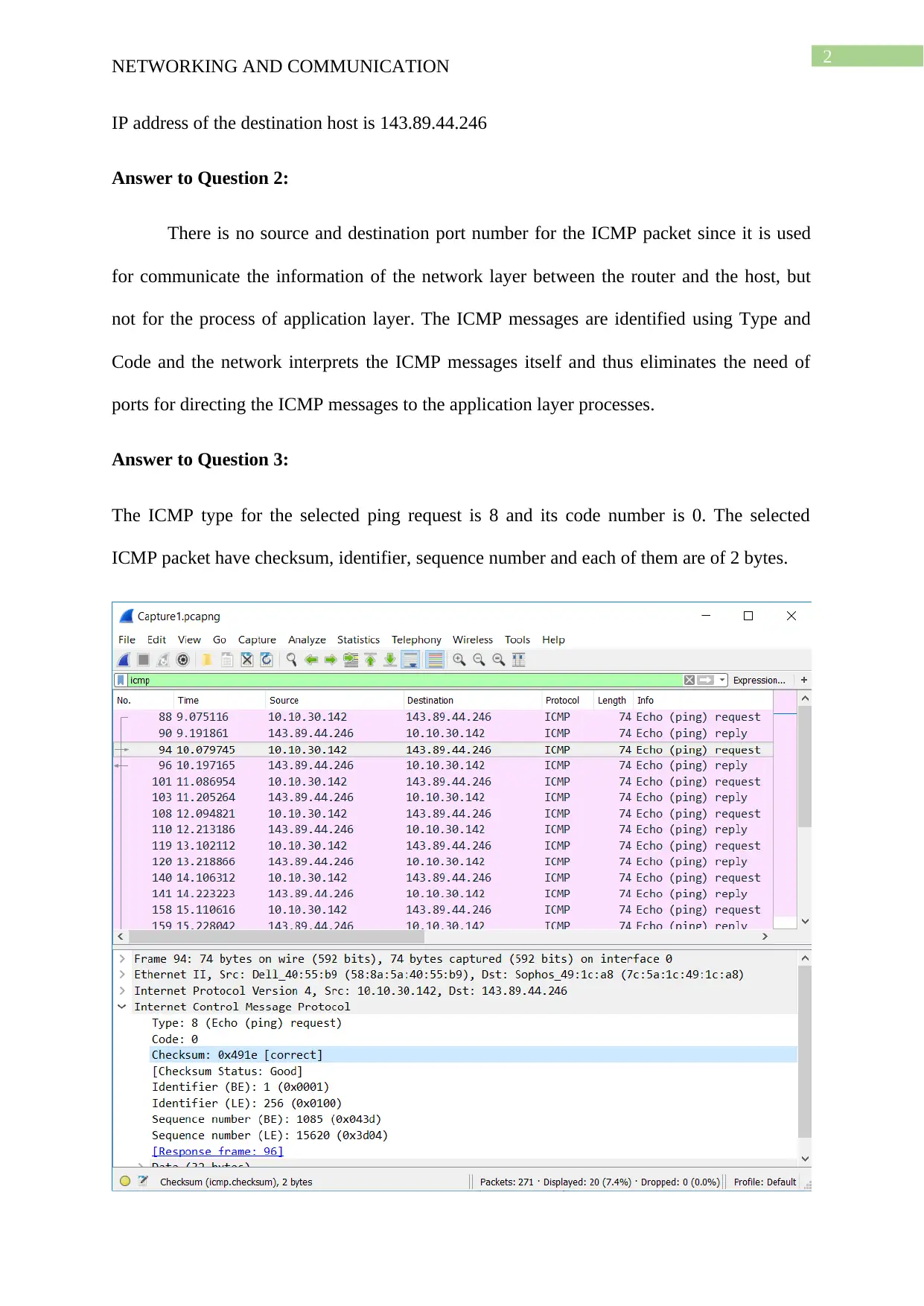
IP address of the destination host is 143.89.44.246
Answer to Question 2:
There is no source and destination port number for the ICMP packet since it is used
for communicate the information of the network layer between the router and the host, but
not for the process of application layer. The ICMP messages are identified using Type and
Code and the network interprets the ICMP messages itself and thus eliminates the need of
ports for directing the ICMP messages to the application layer processes.
Answer to Question 3:
The ICMP type for the selected ping request is 8 and its code number is 0. The selected
ICMP packet have checksum, identifier, sequence number and each of them are of 2 bytes.
NETWORKING AND COMMUNICATION
IP address of the destination host is 143.89.44.246
Answer to Question 2:
There is no source and destination port number for the ICMP packet since it is used
for communicate the information of the network layer between the router and the host, but
not for the process of application layer. The ICMP messages are identified using Type and
Code and the network interprets the ICMP messages itself and thus eliminates the need of
ports for directing the ICMP messages to the application layer processes.
Answer to Question 3:
The ICMP type for the selected ping request is 8 and its code number is 0. The selected
ICMP packet have checksum, identifier, sequence number and each of them are of 2 bytes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORKING AND COMMUNICATION
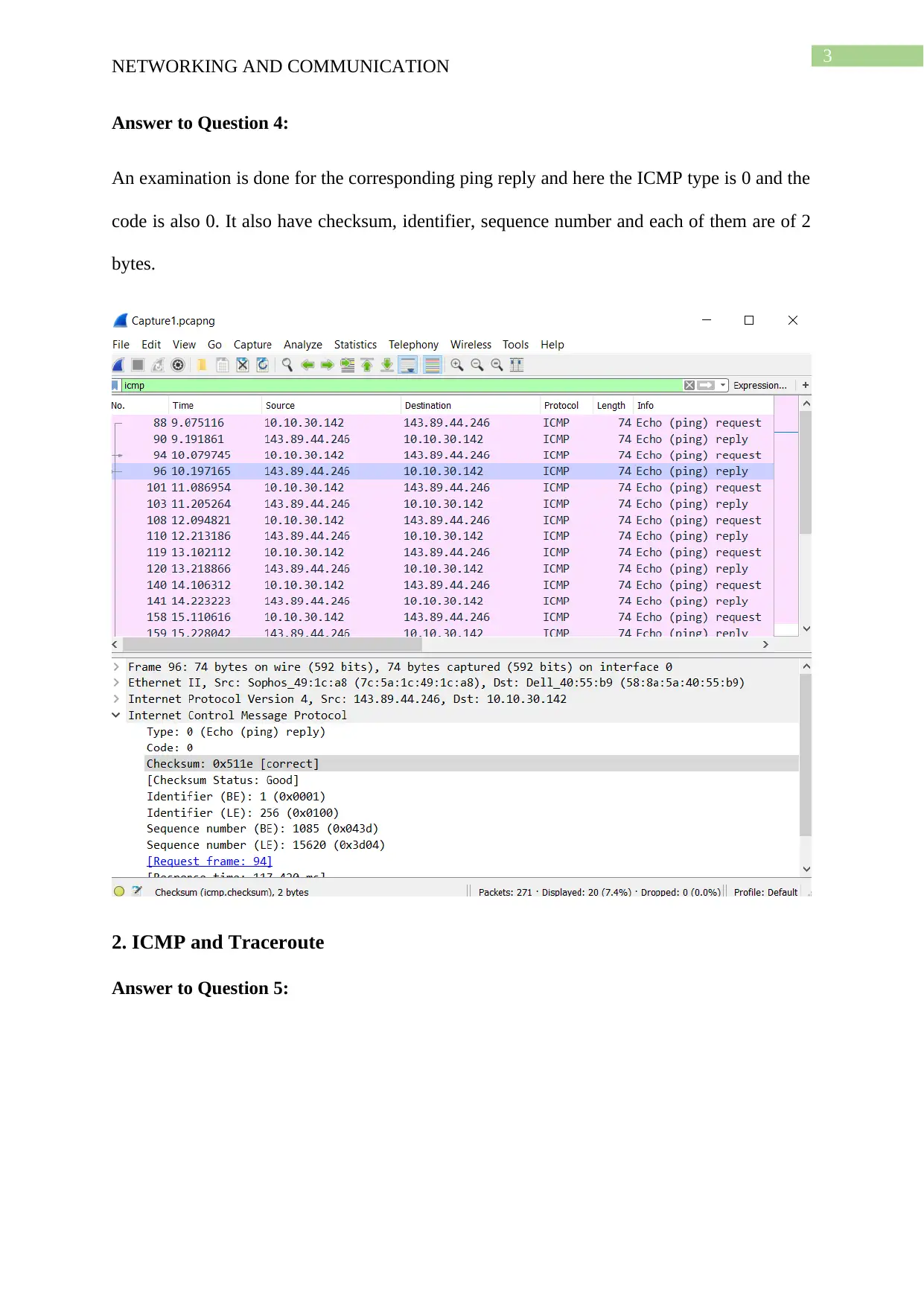
Answer to Question 4:
An examination is done for the corresponding ping reply and here the ICMP type is 0 and the
code is also 0. It also have checksum, identifier, sequence number and each of them are of 2
bytes.
2. ICMP and Traceroute
Answer to Question 5:
NETWORKING AND COMMUNICATION
Answer to Question 4:
An examination is done for the corresponding ping reply and here the ICMP type is 0 and the
code is also 0. It also have checksum, identifier, sequence number and each of them are of 2
bytes.
2. ICMP and Traceroute
Answer to Question 5:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORKING AND COMMUNICATION
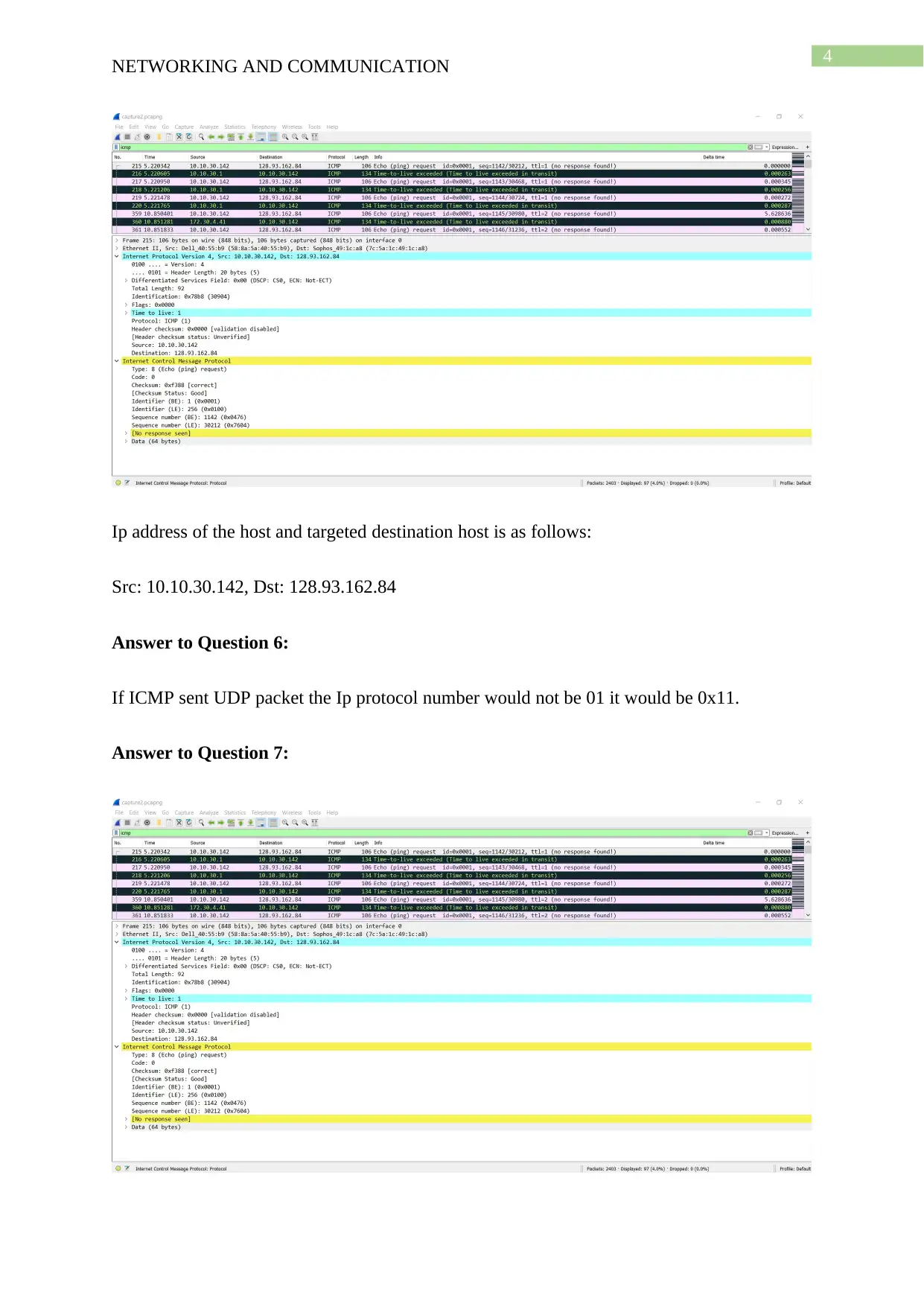
Ip address of the host and targeted destination host is as follows:
Src: 10.10.30.142, Dst: 128.93.162.84
Answer to Question 6:
If ICMP sent UDP packet the Ip protocol number would not be 01 it would be 0x11.
Answer to Question 7:
NETWORKING AND COMMUNICATION
Ip address of the host and targeted destination host is as follows:
Src: 10.10.30.142, Dst: 128.93.162.84
Answer to Question 6:
If ICMP sent UDP packet the Ip protocol number would not be 01 it would be 0x11.
Answer to Question 7:
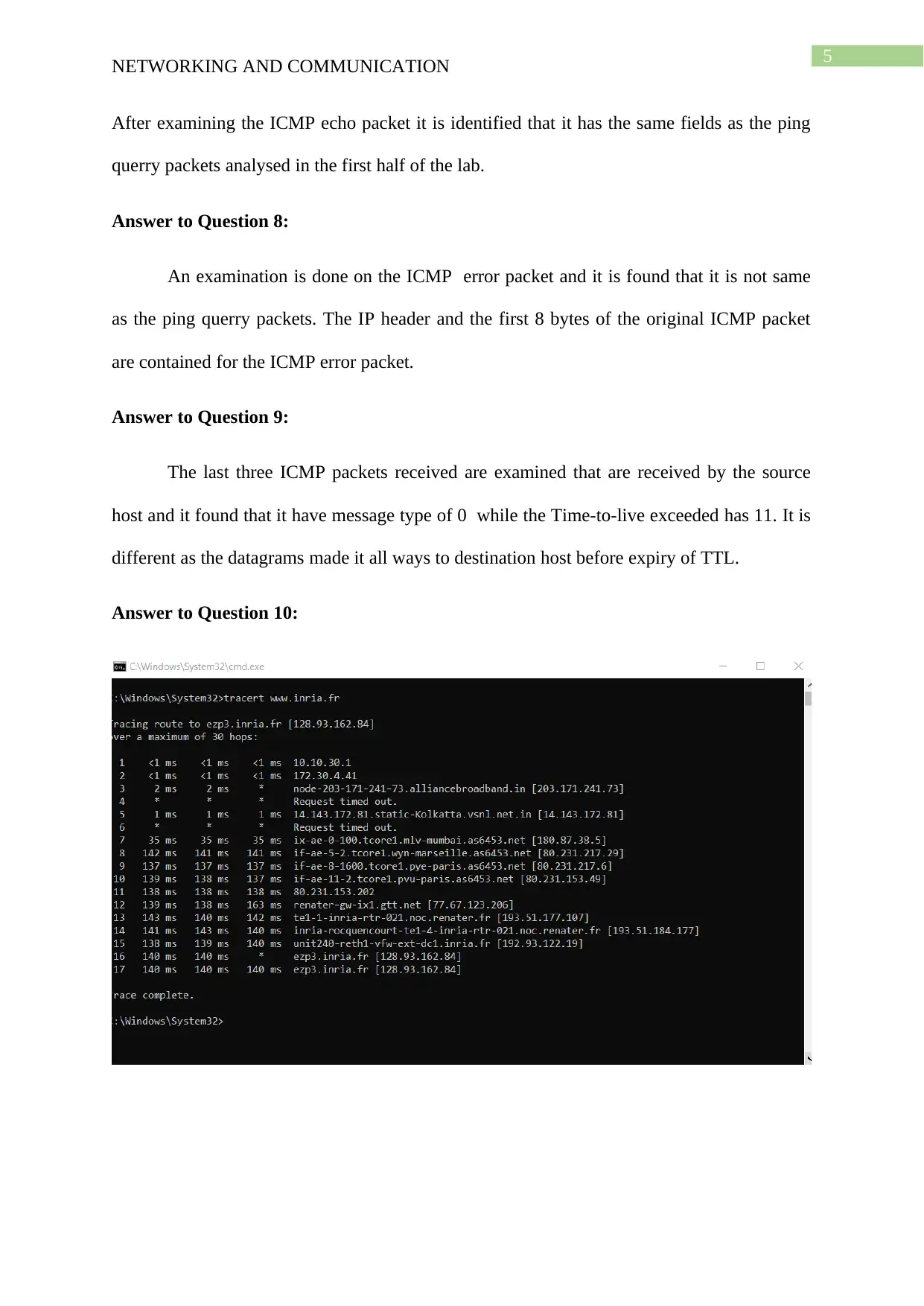
5
NETWORKING AND COMMUNICATION
After examining the ICMP echo packet it is identified that it has the same fields as the ping
querry packets analysed in the first half of the lab.
Answer to Question 8:
An examination is done on the ICMP error packet and it is found that it is not same
as the ping querry packets. The IP header and the first 8 bytes of the original ICMP packet
are contained for the ICMP error packet.
Answer to Question 9:
The last three ICMP packets received are examined that are received by the source
host and it found that it have message type of 0 while the Time-to-live exceeded has 11. It is
different as the datagrams made it all ways to destination host before expiry of TTL.
Answer to Question 10:
NETWORKING AND COMMUNICATION
After examining the ICMP echo packet it is identified that it has the same fields as the ping
querry packets analysed in the first half of the lab.
Answer to Question 8:
An examination is done on the ICMP error packet and it is found that it is not same
as the ping querry packets. The IP header and the first 8 bytes of the original ICMP packet
are contained for the ICMP error packet.
Answer to Question 9:
The last three ICMP packets received are examined that are received by the source
host and it found that it have message type of 0 while the Time-to-live exceeded has 11. It is
different as the datagrams made it all ways to destination host before expiry of TTL.
Answer to Question 10:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
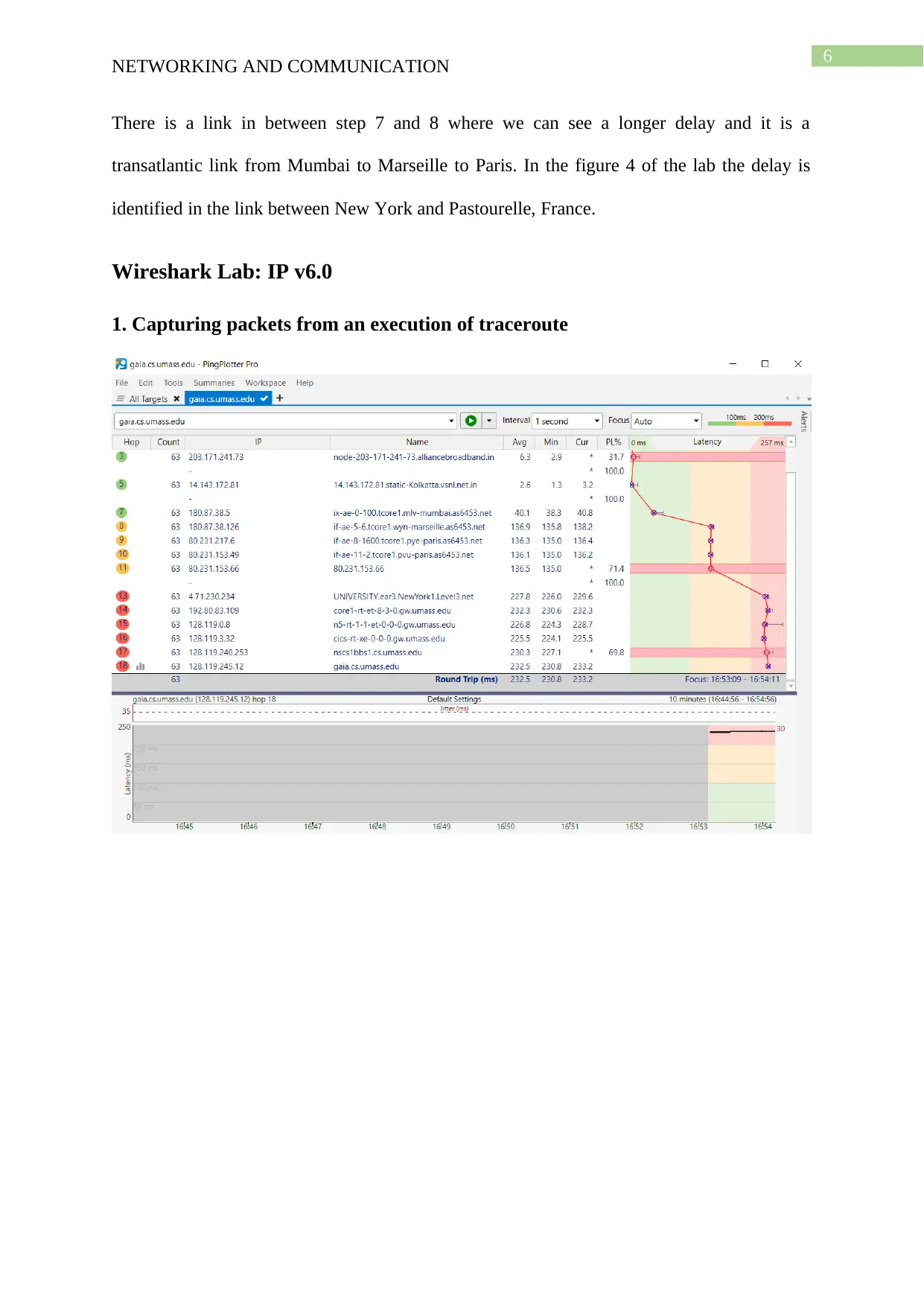
6
NETWORKING AND COMMUNICATION
There is a link in between step 7 and 8 where we can see a longer delay and it is a
transatlantic link from Mumbai to Marseille to Paris. In the figure 4 of the lab the delay is
identified in the link between New York and Pastourelle, France.
Wireshark Lab: IP v6.0
1. Capturing packets from an execution of traceroute
NETWORKING AND COMMUNICATION
There is a link in between step 7 and 8 where we can see a longer delay and it is a
transatlantic link from Mumbai to Marseille to Paris. In the figure 4 of the lab the delay is
identified in the link between New York and Pastourelle, France.
Wireshark Lab: IP v6.0
1. Capturing packets from an execution of traceroute
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
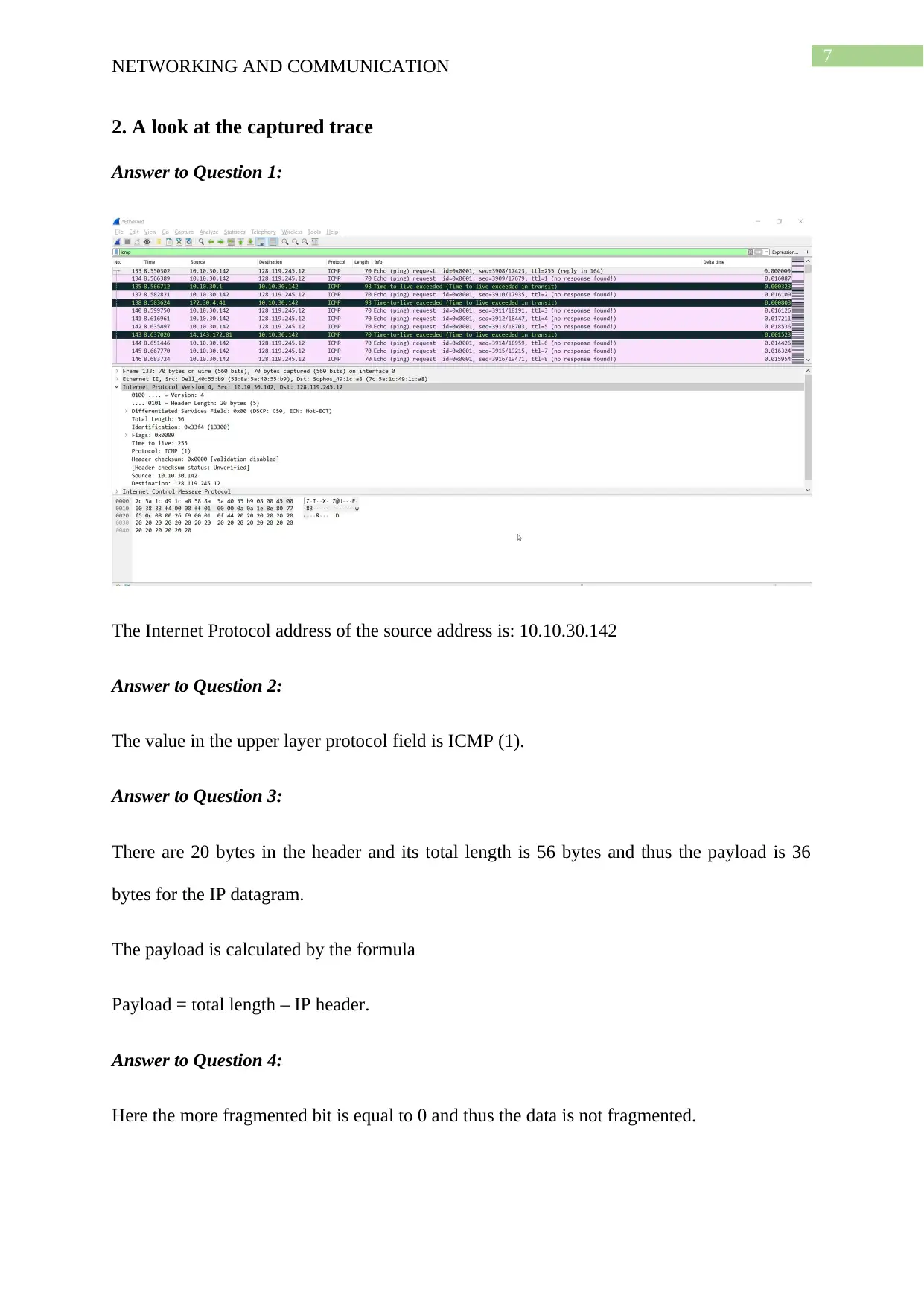
7
NETWORKING AND COMMUNICATION
2. A look at the captured trace
Answer to Question 1:
The Internet Protocol address of the source address is: 10.10.30.142
Answer to Question 2:
The value in the upper layer protocol field is ICMP (1).
Answer to Question 3:
There are 20 bytes in the header and its total length is 56 bytes and thus the payload is 36
bytes for the IP datagram.
The payload is calculated by the formula
Payload = total length – IP header.
Answer to Question 4:
Here the more fragmented bit is equal to 0 and thus the data is not fragmented.
NETWORKING AND COMMUNICATION
2. A look at the captured trace
Answer to Question 1:
The Internet Protocol address of the source address is: 10.10.30.142
Answer to Question 2:
The value in the upper layer protocol field is ICMP (1).
Answer to Question 3:
There are 20 bytes in the header and its total length is 56 bytes and thus the payload is 36
bytes for the IP datagram.
The payload is calculated by the formula
Payload = total length – IP header.
Answer to Question 4:
Here the more fragmented bit is equal to 0 and thus the data is not fragmented.
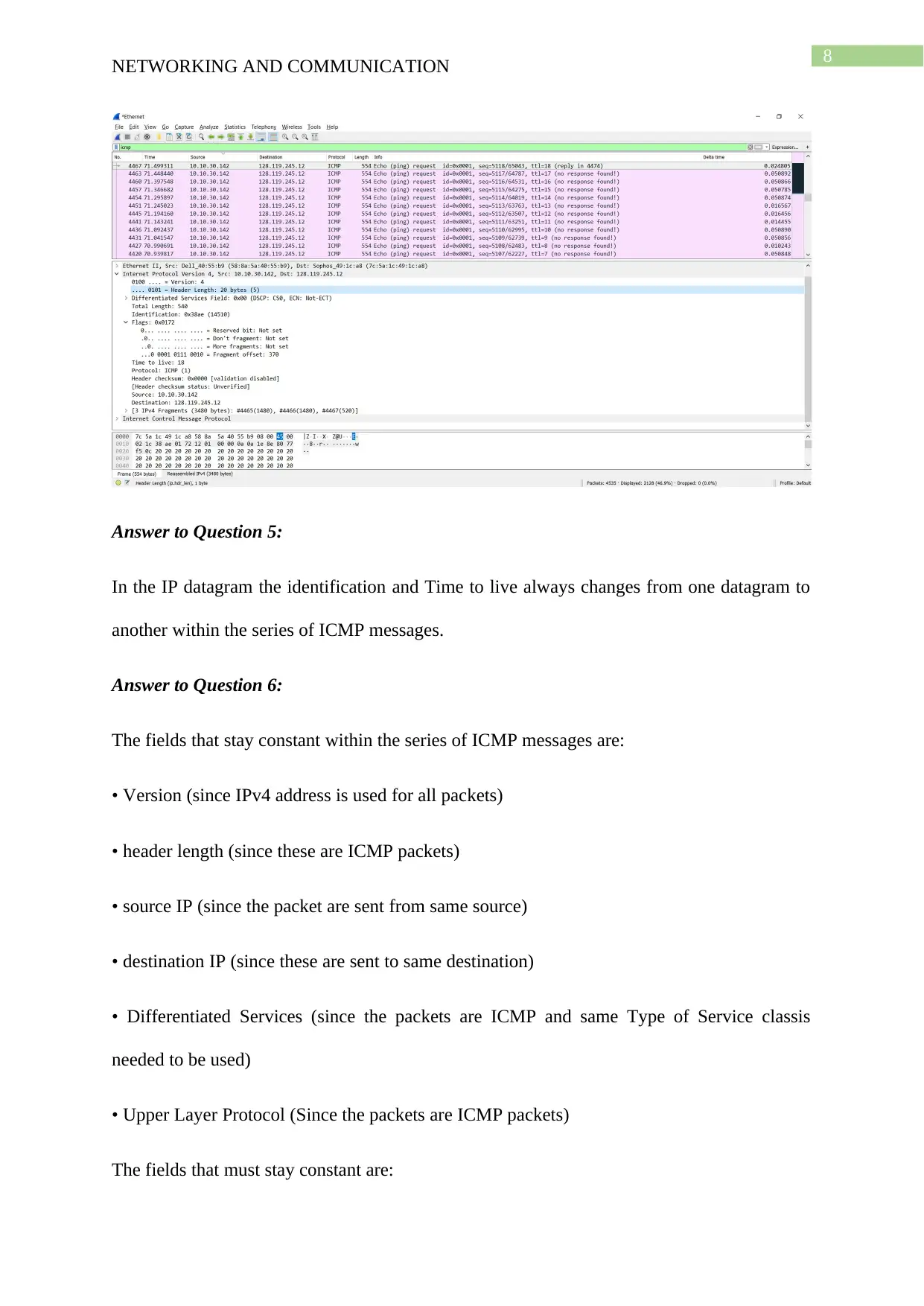
8
NETWORKING AND COMMUNICATION
Answer to Question 5:
In the IP datagram the identification and Time to live always changes from one datagram to
another within the series of ICMP messages.
Answer to Question 6:
The fields that stay constant within the series of ICMP messages are:
• Version (since IPv4 address is used for all packets)
• header length (since these are ICMP packets)
• source IP (since the packet are sent from same source)
• destination IP (since these are sent to same destination)
• Differentiated Services (since the packets are ICMP and same Type of Service classis
needed to be used)
• Upper Layer Protocol (Since the packets are ICMP packets)
The fields that must stay constant are:
NETWORKING AND COMMUNICATION
Answer to Question 5:
In the IP datagram the identification and Time to live always changes from one datagram to
another within the series of ICMP messages.
Answer to Question 6:
The fields that stay constant within the series of ICMP messages are:
• Version (since IPv4 address is used for all packets)
• header length (since these are ICMP packets)
• source IP (since the packet are sent from same source)
• destination IP (since these are sent to same destination)
• Differentiated Services (since the packets are ICMP and same Type of Service classis
needed to be used)
• Upper Layer Protocol (Since the packets are ICMP packets)
The fields that must stay constant are:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORKING AND COMMUNICATION
• Version (Since IPv4 address is used for all packets)
• header length (since these are ICMP packets)
• source IP (since the packet are sent from same source)
• destination IP (since these are sent to same destination)
• Differentiated Services (since the packets are ICMP and same Type of Service classis
needed to be used)
• Upper Layer Protocol (Since the packets are ICMP packets)
The fields that must change are:
• Identification (IP packets should have unique ids)
• Time to live (traceroute causes increments of each subsequent packet)
• Header checksum (due to change in header)
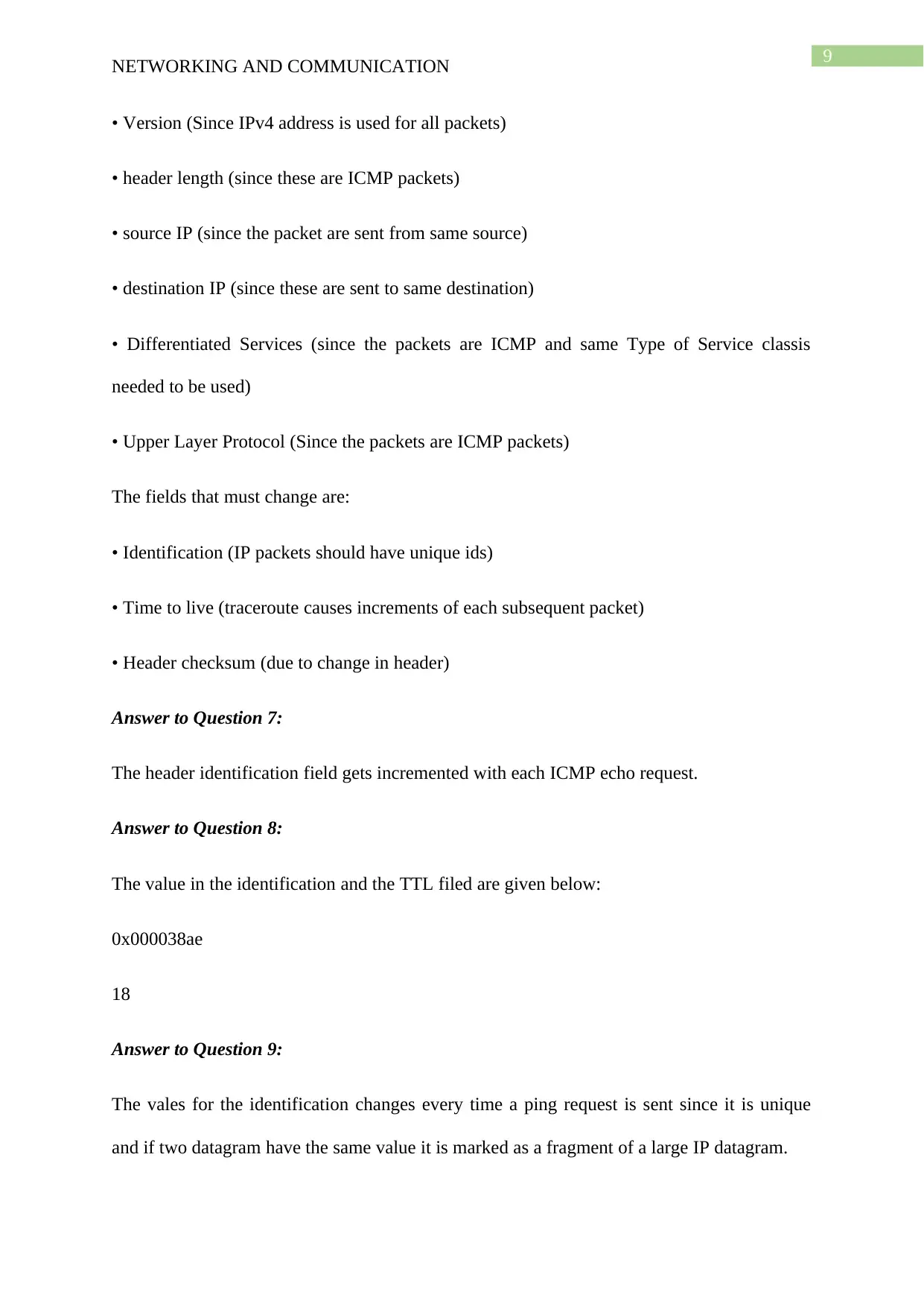
Answer to Question 7:
The header identification field gets incremented with each ICMP echo request.
Answer to Question 8:
The value in the identification and the TTL filed are given below:
0x000038ae
18
Answer to Question 9:
The vales for the identification changes every time a ping request is sent since it is unique
and if two datagram have the same value it is marked as a fragment of a large IP datagram.
NETWORKING AND COMMUNICATION
• Version (Since IPv4 address is used for all packets)
• header length (since these are ICMP packets)
• source IP (since the packet are sent from same source)
• destination IP (since these are sent to same destination)
• Differentiated Services (since the packets are ICMP and same Type of Service classis
needed to be used)
• Upper Layer Protocol (Since the packets are ICMP packets)
The fields that must change are:
• Identification (IP packets should have unique ids)
• Time to live (traceroute causes increments of each subsequent packet)
• Header checksum (due to change in header)
Answer to Question 7:
The header identification field gets incremented with each ICMP echo request.
Answer to Question 8:
The value in the identification and the TTL filed are given below:
0x000038ae
18
Answer to Question 9:
The vales for the identification changes every time a ping request is sent since it is unique
and if two datagram have the same value it is marked as a fragment of a large IP datagram.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORKING AND COMMUNICATION
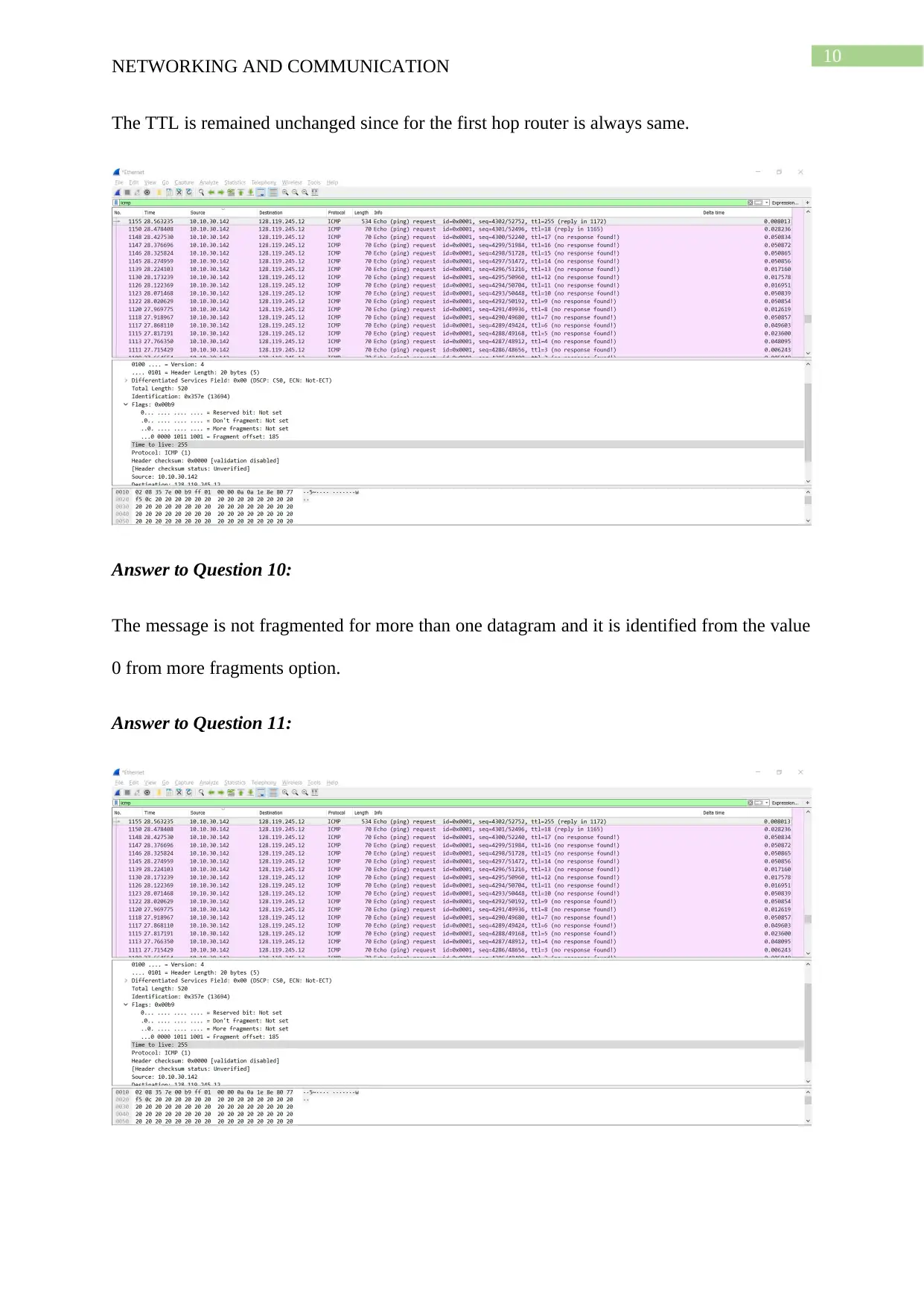
The TTL is remained unchanged since for the first hop router is always same.
Answer to Question 10:
The message is not fragmented for more than one datagram and it is identified from the value
0 from more fragments option.
Answer to Question 11:
NETWORKING AND COMMUNICATION
The TTL is remained unchanged since for the first hop router is always same.
Answer to Question 10:
The message is not fragmented for more than one datagram and it is identified from the value
0 from more fragments option.
Answer to Question 11:

11
NETWORKING AND COMMUNICATION
The flag bits for more fragments is not set and it indicates that the data fragments has not
been fragmented.
The first datagram has a total length of 534 bytes including the header.
Answer to Question 12:
Since the fragment offset is 185 it is confirmed that it has an offset and it is the last fragment
since the value of more fragment size is not set.
Answer to Question 13:
The field IP header changes between the fragments such as total length, flogs, fragment offset
and checksum.
Answer to Question 14:
3 fragments are created from the original datagram when Packet Size in pingplotter si set to
3500.
Answer to Question 15:
NETWORKING AND COMMUNICATION
The flag bits for more fragments is not set and it indicates that the data fragments has not
been fragmented.
The first datagram has a total length of 534 bytes including the header.
Answer to Question 12:
Since the fragment offset is 185 it is confirmed that it has an offset and it is the last fragment
since the value of more fragment size is not set.
Answer to Question 13:
The field IP header changes between the fragments such as total length, flogs, fragment offset
and checksum.
Answer to Question 14:
3 fragments are created from the original datagram when Packet Size in pingplotter si set to
3500.
Answer to Question 15:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



