Computer Networking: Wireshark Lab on Ethernet and ARP Protocols
VerifiedAdded on 2022/12/02
|15
|2182
|191
Homework Assignment
AI Summary
This assignment is a comprehensive analysis of Ethernet and ARP protocols using Wireshark. The student captures and analyzes Ethernet frames, identifying source and destination addresses, frame types, and hexadecimal values. The lab explores the structure of Ethernet frames, including the frame type field, and examines the process of address resolution through ARP. The student investigates the contents of the ARP cache, analyzes ARP request and reply messages, and answers questions related to the ARP opcode field and the location of IP and Ethernet addresses within ARP messages. The assignment also includes extra credit questions that explore the implications of incorrect ARP cache entries and the default time an entry remains in the ARP cache. The student utilizes network traffic analysis to understand the underlying mechanisms of network communication, addressing concepts such as the role of routers, the behavior of ARP, and the function of various fields within Ethernet and ARP packets. The assignment demonstrates a practical understanding of network protocols and their operation.

Running head: WIRESHARK LAB
Wireshark Lab: Ethernet and ARP v7.0
Name of the Student
Name of the University
Author’s Note
Wireshark Lab: Ethernet and ARP v7.0
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
WIRESHARK LAB
Capturing and Analyzing Ethernet Frames
WIRESHARK LAB
Capturing and Analyzing Ethernet Frames

2
WIRESHARK LAB
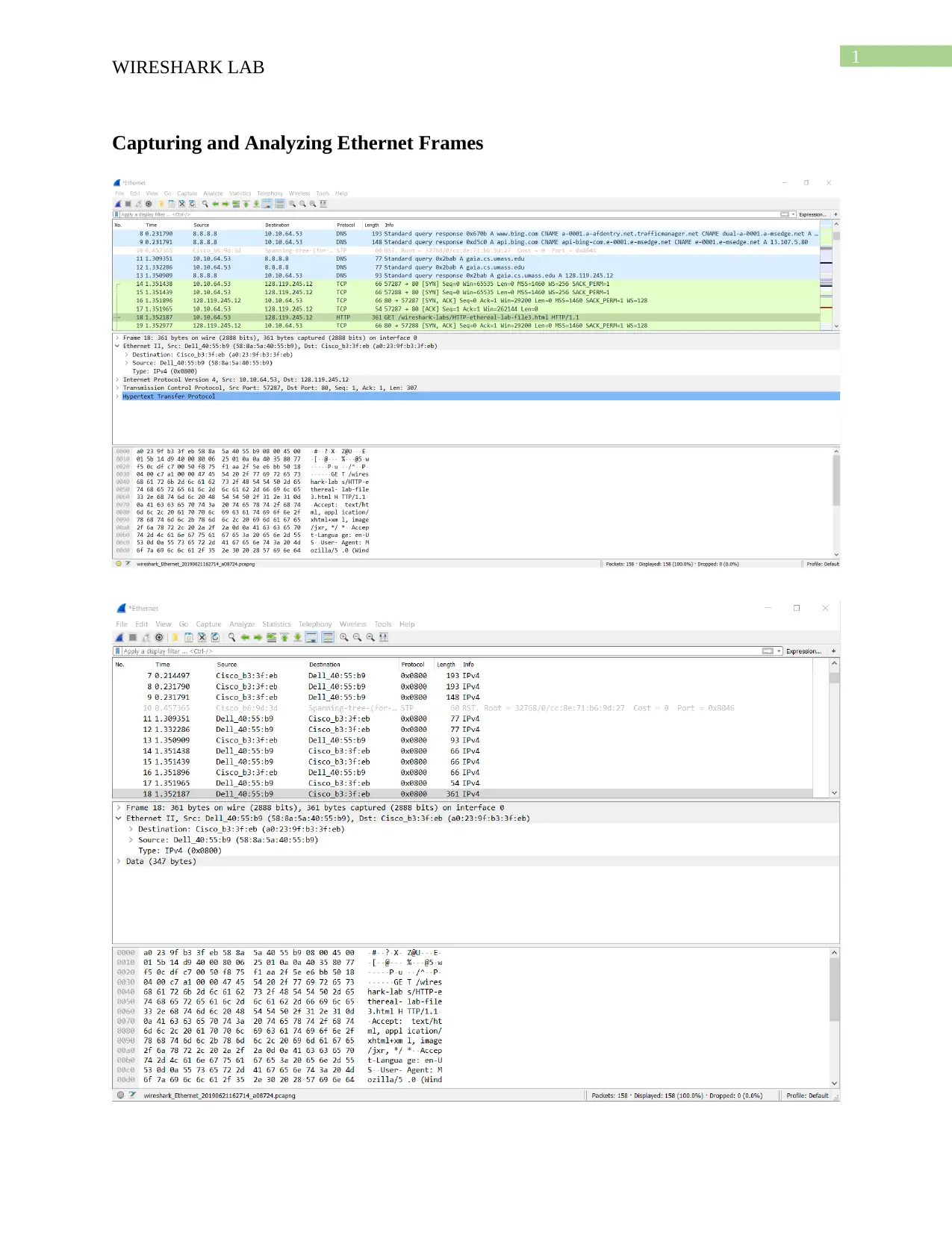
Answer to Question 1:
What is the 48-bit Ethernet address of your computer?
The 48 bit Ethernet address of the computer used for capturing the packet from
http://gaia.cs.umass.edu/wireshark-labs/HTTP-ethereal-lab-file3.html is given below:
Ethernet II, Src: Dell_40:55:b9 (58:8a:5a:40:55:b9)
Answer to Question 2:
What is the 48-bit destination address in the Ethernet frame? Is this the Ethernet address of
gaia.cs.umass.edu? (Hint: the answer is no). What device has this as its Ethernet address? [Note:
this is an important question, and one that students sometimes get wrong. Re-read pages 468-
469 in the text and make sure you understand the answer here.]
The 48-bit destination address in the Ethernet frame is given below:
Ethernet II, Dst: Cisco_b3:3f:eb (a0:23:9f:b3:3f:eb)
This is not the Ethernet address of gaia.cs.umass.edu.
This Ethernet address is for the next hop router.
Answer to Question 3:
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does
this correspond to?
The hexadecimal value for the two byte frame type filed is given below:
0x0800
WIRESHARK LAB
Answer to Question 1:
What is the 48-bit Ethernet address of your computer?
The 48 bit Ethernet address of the computer used for capturing the packet from
http://gaia.cs.umass.edu/wireshark-labs/HTTP-ethereal-lab-file3.html is given below:
Ethernet II, Src: Dell_40:55:b9 (58:8a:5a:40:55:b9)
Answer to Question 2:
What is the 48-bit destination address in the Ethernet frame? Is this the Ethernet address of
gaia.cs.umass.edu? (Hint: the answer is no). What device has this as its Ethernet address? [Note:
this is an important question, and one that students sometimes get wrong. Re-read pages 468-
469 in the text and make sure you understand the answer here.]
The 48-bit destination address in the Ethernet frame is given below:
Ethernet II, Dst: Cisco_b3:3f:eb (a0:23:9f:b3:3f:eb)
This is not the Ethernet address of gaia.cs.umass.edu.
This Ethernet address is for the next hop router.
Answer to Question 3:
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does
this correspond to?
The hexadecimal value for the two byte frame type filed is given below:
0x0800
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRESHARK LAB
It corresponds to IP Protocol or the upper layer protocol.
Answer to Question 4:
How many bytes from the very start of the Ethernet frame does the ASCII “G” in “GET” appear
in the Ethernet frame?
From the packet captured the Ascii G in the Get appears in the Ethernet frame with 47 bits.
Answer to Question 5:
What is the value of the Ethernet source address? Is this the address of your computer, or of
gaia.cs.umass.edu (Hint: the answer is no). What device has this as its Ethernet address?
The value of source address for Ethernet is given below:
a0:23:9f:b3:3f:eb
It is not the address of gaia.cs.umass.edu or my computer.
The captured Ethernet address is of the router interface through which the data traffic passed
over the network.
Answer to Question 6:
What is the destination address in the Ethernet frame? Is this the Ethernet address of your
computer?
WIRESHARK LAB
It corresponds to IP Protocol or the upper layer protocol.
Answer to Question 4:
How many bytes from the very start of the Ethernet frame does the ASCII “G” in “GET” appear
in the Ethernet frame?
From the packet captured the Ascii G in the Get appears in the Ethernet frame with 47 bits.
Answer to Question 5:
What is the value of the Ethernet source address? Is this the address of your computer, or of
gaia.cs.umass.edu (Hint: the answer is no). What device has this as its Ethernet address?
The value of source address for Ethernet is given below:
a0:23:9f:b3:3f:eb
It is not the address of gaia.cs.umass.edu or my computer.
The captured Ethernet address is of the router interface through which the data traffic passed
over the network.
Answer to Question 6:
What is the destination address in the Ethernet frame? Is this the Ethernet address of your
computer?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
WIRESHARK LAB
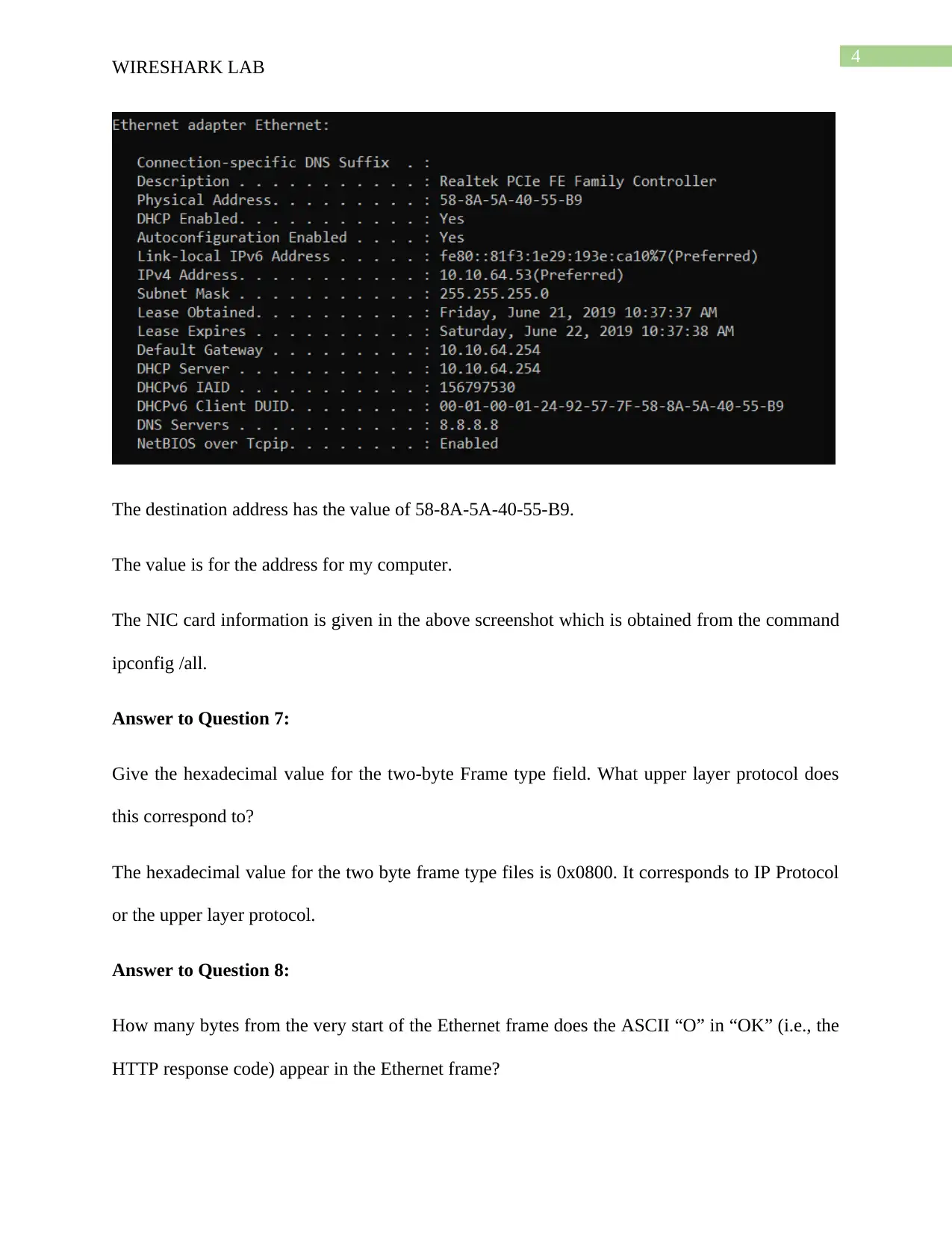
The destination address has the value of 58-8A-5A-40-55-B9.
The value is for the address for my computer.
The NIC card information is given in the above screenshot which is obtained from the command
ipconfig /all.
Answer to Question 7:
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does
this correspond to?
The hexadecimal value for the two byte frame type files is 0x0800. It corresponds to IP Protocol
or the upper layer protocol.
Answer to Question 8:
How many bytes from the very start of the Ethernet frame does the ASCII “O” in “OK” (i.e., the
HTTP response code) appear in the Ethernet frame?
WIRESHARK LAB
The destination address has the value of 58-8A-5A-40-55-B9.
The value is for the address for my computer.
The NIC card information is given in the above screenshot which is obtained from the command
ipconfig /all.
Answer to Question 7:
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does
this correspond to?
The hexadecimal value for the two byte frame type files is 0x0800. It corresponds to IP Protocol
or the upper layer protocol.
Answer to Question 8:
How many bytes from the very start of the Ethernet frame does the ASCII “O” in “OK” (i.e., the
HTTP response code) appear in the Ethernet frame?

5
WIRESHARK LAB
From the very start of Ethernet frame the ASCII O in OK is of 58 bytes
The Address Resolution Protocol
Answer to Question 9:
Write down the contents of your computer’s ARP cache. What is the meaning of each column
value?
The Arp cache has the following content
Interface: 10.10.64.53 --- 0x7
Internet Address Physical Address Type
10.10.64.254 a0-23-9f-b3-3f-eb dynamic
224.0.0.22 01-00-5e-00-00-16 static
239.255.255.250 01-00-5e-7f-ff-fa staticontent
The meaning of the column are given below:
Internet Address – It shows the IP address
Physical Address – It demonstrates the MAC address
Type – It shows the protocol type
WIRESHARK LAB
From the very start of Ethernet frame the ASCII O in OK is of 58 bytes
The Address Resolution Protocol
Answer to Question 9:
Write down the contents of your computer’s ARP cache. What is the meaning of each column
value?
The Arp cache has the following content
Interface: 10.10.64.53 --- 0x7
Internet Address Physical Address Type
10.10.64.254 a0-23-9f-b3-3f-eb dynamic
224.0.0.22 01-00-5e-00-00-16 static
239.255.255.250 01-00-5e-7f-ff-fa staticontent
The meaning of the column are given below:
Internet Address – It shows the IP address
Physical Address – It demonstrates the MAC address
Type – It shows the protocol type
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRESHARK LAB
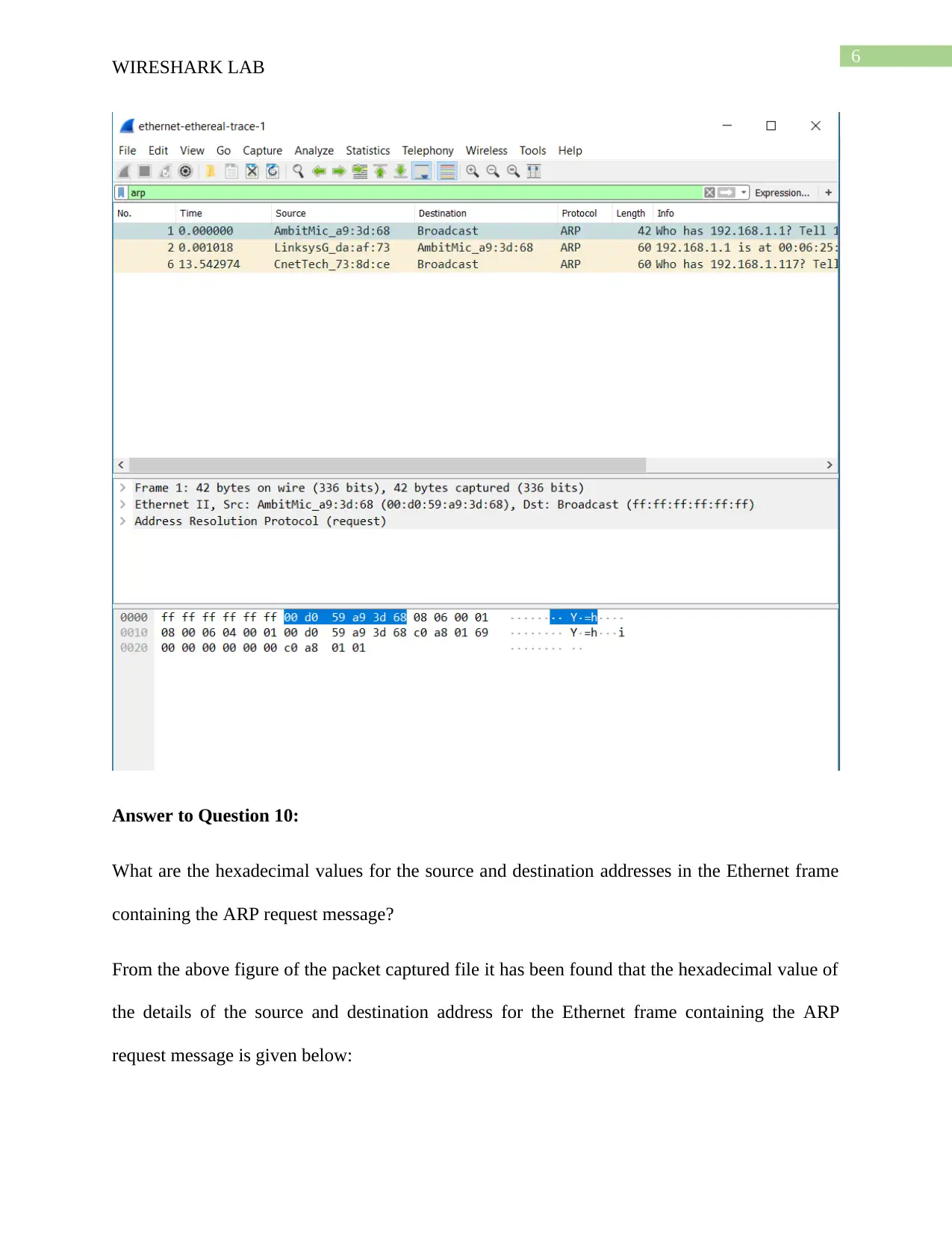
Answer to Question 10:
What are the hexadecimal values for the source and destination addresses in the Ethernet frame
containing the ARP request message?
From the above figure of the packet captured file it has been found that the hexadecimal value of
the details of the source and destination address for the Ethernet frame containing the ARP
request message is given below:
WIRESHARK LAB
Answer to Question 10:
What are the hexadecimal values for the source and destination addresses in the Ethernet frame
containing the ARP request message?
From the above figure of the packet captured file it has been found that the hexadecimal value of
the details of the source and destination address for the Ethernet frame containing the ARP
request message is given below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
WIRESHARK LAB
Ethernet II, Src: AmbitMic_a9:3d:68 (00:d0:59:a9:3d:68), Dst: Broadcast (ff:ff:ff:ff:ff:ff)
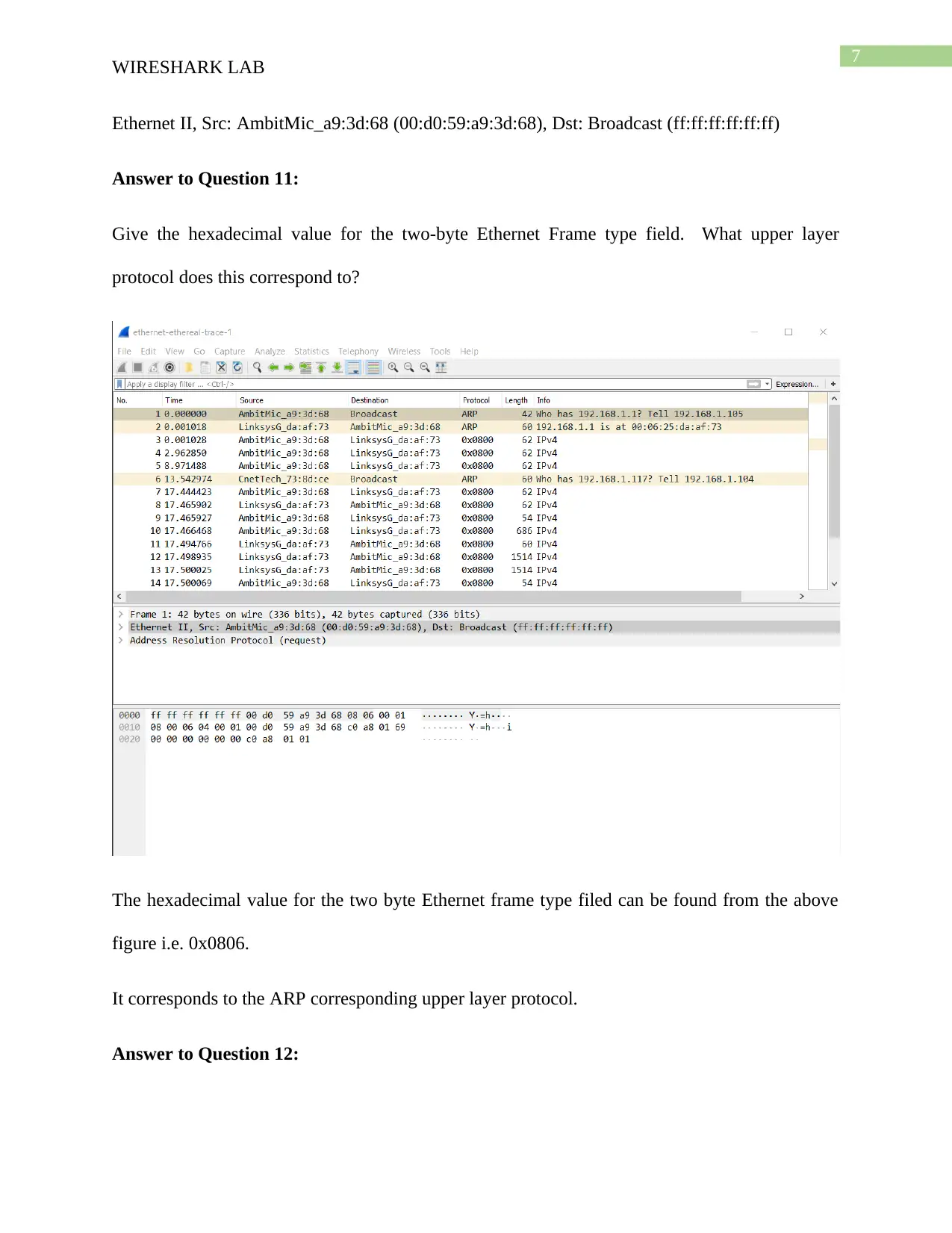
Answer to Question 11:
Give the hexadecimal value for the two-byte Ethernet Frame type field. What upper layer
protocol does this correspond to?
The hexadecimal value for the two byte Ethernet frame type filed can be found from the above
figure i.e. 0x0806.
It corresponds to the ARP corresponding upper layer protocol.
Answer to Question 12:
WIRESHARK LAB
Ethernet II, Src: AmbitMic_a9:3d:68 (00:d0:59:a9:3d:68), Dst: Broadcast (ff:ff:ff:ff:ff:ff)
Answer to Question 11:
Give the hexadecimal value for the two-byte Ethernet Frame type field. What upper layer
protocol does this correspond to?
The hexadecimal value for the two byte Ethernet frame type filed can be found from the above
figure i.e. 0x0806.
It corresponds to the ARP corresponding upper layer protocol.
Answer to Question 12:

8
WIRESHARK LAB
Download the ARP specification from ftp://ftp.rfc-editor.org/in-notes/std/std37.txt. A readable,
detailed discussion of ARP is also at
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html.
a. How many bytes from the very beginning of the Ethernet frame does the ARP opcode field
begin?
From the very beginning of the Ethernet frame the ARP opcode filed begins with 20 bytes.
b. What is the value of the opcode field within the ARP-payload part of the Ethernet frame in
which an ARP request is made?
The value of opcode field within the ARP payload part of Ethernet frame where the Ethernet
frame where ARP request is made is 0x0001.
c. Does the ARP message contain the IP address of the sender?
The ARP message contain the IP address of the sender 192.168.1.105
d. Where in the ARP request does the “question” appear – the Ethernet address of the machine
whose corresponding IP address is being queried?
The ARP request in the question appears in the protocol column and the Ethernet address of the
machine is whose corresponding IP address is being queried is 00:00:00:00:00:00. The query is
for broadcasting the machine having IP address 192.168.1.105.
Answer to Question 13:
Now find the ARP reply that was sent in response to the ARP request.
WIRESHARK LAB
Download the ARP specification from ftp://ftp.rfc-editor.org/in-notes/std/std37.txt. A readable,
detailed discussion of ARP is also at
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html.
a. How many bytes from the very beginning of the Ethernet frame does the ARP opcode field
begin?
From the very beginning of the Ethernet frame the ARP opcode filed begins with 20 bytes.
b. What is the value of the opcode field within the ARP-payload part of the Ethernet frame in
which an ARP request is made?
The value of opcode field within the ARP payload part of Ethernet frame where the Ethernet
frame where ARP request is made is 0x0001.
c. Does the ARP message contain the IP address of the sender?
The ARP message contain the IP address of the sender 192.168.1.105
d. Where in the ARP request does the “question” appear – the Ethernet address of the machine
whose corresponding IP address is being queried?
The ARP request in the question appears in the protocol column and the Ethernet address of the
machine is whose corresponding IP address is being queried is 00:00:00:00:00:00. The query is
for broadcasting the machine having IP address 192.168.1.105.
Answer to Question 13:
Now find the ARP reply that was sent in response to the ARP request.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
WIRESHARK LAB
a. How many bytes from the very beginning of the Ethernet frame does the ARP opcode field
begin?
From the very beginning of the Ethernet frame the ARP opcode filed begins with 20 bytes.
b. What is the value of the opcode field within the ARP-payload part of the Ethernet frame in
which an ARP response is made?
The value of opcode field within the ARP payload part of Ethernet frame where the Ethernet
frame where ARP request is made is 0x0002.
c. Where in the ARP message does the “answer” to the earlier ARP request appear – the IP
address of the machine having the Ethernet address whose corresponding IP address is being
queried?
For the ARP message answer the IP address of the sender machine is 192.168.1.1 and the
Ethernet address whose corresponding IP address is queried is 00:06:25:da:af:73.
Answer to Question 14:
What are the hexadecimal values for the source and destination addresses in the Ethernet frame
containing the ARP reply message?
The hexadecimal values for the source and destination address in Ethernet frame that contains
the ARP reply message is given below:
Ethernet II,
Src: LinksysG_da:af:73 (00:06:25:da:af:73),
Dst: AmbitMic_a9:3d:68 (00:d0:59:a9:3d:68)
WIRESHARK LAB
a. How many bytes from the very beginning of the Ethernet frame does the ARP opcode field
begin?
From the very beginning of the Ethernet frame the ARP opcode filed begins with 20 bytes.
b. What is the value of the opcode field within the ARP-payload part of the Ethernet frame in
which an ARP response is made?
The value of opcode field within the ARP payload part of Ethernet frame where the Ethernet
frame where ARP request is made is 0x0002.
c. Where in the ARP message does the “answer” to the earlier ARP request appear – the IP
address of the machine having the Ethernet address whose corresponding IP address is being
queried?
For the ARP message answer the IP address of the sender machine is 192.168.1.1 and the
Ethernet address whose corresponding IP address is queried is 00:06:25:da:af:73.
Answer to Question 14:
What are the hexadecimal values for the source and destination addresses in the Ethernet frame
containing the ARP reply message?
The hexadecimal values for the source and destination address in Ethernet frame that contains
the ARP reply message is given below:
Ethernet II,
Src: LinksysG_da:af:73 (00:06:25:da:af:73),
Dst: AmbitMic_a9:3d:68 (00:d0:59:a9:3d:68)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
WIRESHARK LAB
Answer to Question 15:
Open the ethernet-ethereal-trace-1 trace file in
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip. The first and second ARP packets
in this trace correspond to an ARP request sent by the computer running Wireshark, and the ARP
reply sent to the computer running Wireshark by the computer with the ARP-requested Ethernet
address. But there is yet another computer on this network, as indicated by packet 6 – another
ARP request. Why is there no ARP reply (sent in response to the ARP request in packet 6) in the
packet trace?
Since a broadcast ARP request is made and the reply of the ARP is not a broadcast the reply is
sent to the computer directly which have requested.
Extra Credit:
Ex-1 The arp command:
arp -s InetAddr EtherAddr
allows you to manually add an entry to the ARP cache that resolves the IP address InetAddr to
the physical address EtherAddr. What would happen if, when you manually added an entry, you
entered the correct IP address, but the wrong Ethernet address for that remote interface?
In case of manually adding an entry and entering the correct IP address but with wrong Ethernet
address for the remote interface a request time out would be displayed when the web server is
tried to ping from the source machine. This is because the ICMP packet would not reach the
destination web server. If the web server is tried to reach to be accessed via the port 80 the also
the connection could not be established. For establishing the connection the arp cache is needed
to be cleared.
WIRESHARK LAB
Answer to Question 15:
Open the ethernet-ethereal-trace-1 trace file in
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip. The first and second ARP packets
in this trace correspond to an ARP request sent by the computer running Wireshark, and the ARP
reply sent to the computer running Wireshark by the computer with the ARP-requested Ethernet
address. But there is yet another computer on this network, as indicated by packet 6 – another
ARP request. Why is there no ARP reply (sent in response to the ARP request in packet 6) in the
packet trace?
Since a broadcast ARP request is made and the reply of the ARP is not a broadcast the reply is
sent to the computer directly which have requested.
Extra Credit:
Ex-1 The arp command:
arp -s InetAddr EtherAddr
allows you to manually add an entry to the ARP cache that resolves the IP address InetAddr to
the physical address EtherAddr. What would happen if, when you manually added an entry, you
entered the correct IP address, but the wrong Ethernet address for that remote interface?
In case of manually adding an entry and entering the correct IP address but with wrong Ethernet
address for the remote interface a request time out would be displayed when the web server is
tried to ping from the source machine. This is because the ICMP packet would not reach the
destination web server. If the web server is tried to reach to be accessed via the port 80 the also
the connection could not be established. For establishing the connection the arp cache is needed
to be cleared.

11
WIRESHARK LAB
Ex-2
What is the default amount of time that an entry remains in your ARP cache before being
removed. You can determine this empirically (by monitoring the cache contents) or by looking
this up in your operation system documentation. Indicate how/where you determined this value.
In Windows 10 implementation of TCP/IP stack, a neighbor cache entry is created for the host
and there are no entries matched with the neighbor cache. For the IPv4 the ARP cache entry can
be considered as an example for the neighbor cache entry and after successfully entering the
neighbor cache the entry is changed to Reachable state after analyzing the conditions. If the state
is found to be Reachable then the Windows 10 host does not sends the ARP request in the
network.
Thus it can be concluded that the windows 10 host utilize the information present in the cache. If
the entry in the arp table is not used and it stay in the Reachable state for a longer period than the
Reachable time the state is changed to Stale state. In case if an entry is in the stale state the
windows 10 host sends an ARP request for reaching the destination address.
For the calculation of the Reachable time the following formula is used:
Reachable Time = BaseReachable Time × (A random value between
MIN_RANDOM_FACTOR and MAX_RANDOM_FACTOR)
The following calculated result is obtained from the RFC:
Base Reachable Time – 30,000 ms
MIN_RANDOM_Factor – 0.5
MAX_RANDOM_FACTOR – 1.5
WIRESHARK LAB
Ex-2
What is the default amount of time that an entry remains in your ARP cache before being
removed. You can determine this empirically (by monitoring the cache contents) or by looking
this up in your operation system documentation. Indicate how/where you determined this value.
In Windows 10 implementation of TCP/IP stack, a neighbor cache entry is created for the host
and there are no entries matched with the neighbor cache. For the IPv4 the ARP cache entry can
be considered as an example for the neighbor cache entry and after successfully entering the
neighbor cache the entry is changed to Reachable state after analyzing the conditions. If the state
is found to be Reachable then the Windows 10 host does not sends the ARP request in the
network.
Thus it can be concluded that the windows 10 host utilize the information present in the cache. If
the entry in the arp table is not used and it stay in the Reachable state for a longer period than the
Reachable time the state is changed to Stale state. In case if an entry is in the stale state the
windows 10 host sends an ARP request for reaching the destination address.
For the calculation of the Reachable time the following formula is used:
Reachable Time = BaseReachable Time × (A random value between
MIN_RANDOM_FACTOR and MAX_RANDOM_FACTOR)
The following calculated result is obtained from the RFC:
Base Reachable Time – 30,000 ms
MIN_RANDOM_Factor – 0.5
MAX_RANDOM_FACTOR – 1.5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



