MIS467 Assignment 2: Wireshark Packet Analysis of Network Traffic
VerifiedAdded on 2023/04/24
|8
|1383
|199
Practical Assignment
AI Summary
This assignment analyzes network packets using Wireshark, a powerful protocol analyzer. The student captures and examines network traffic, focusing on the TCP/IP layers (physical, data link, network, transport, and application). The assignment details the steps of capturing packets, and then provides a detailed breakdown of a captured HTTP packet, illustrating the structure and contents of each layer. The analysis includes examining Ethernet headers (MAC addresses), IP addresses, TCP ports, and HTTP request details. The assignment also provides references to relevant sources. This practical exercise helps to understand the structure of network communication and troubleshooting methods. The student provides a practical demonstration of using Wireshark to analyze network traffic and interpret the data within each layer of the TCP/IP model, which is an important skill for network professionals.

Course Title:
Course Code:
Student Name:
Student Code:
Lecture Name:
Student School Affiliation:
Course Code:
Student Name:
Student Code:
Lecture Name:
Student School Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Review
Wireshark refers to a software application packet sniffer or protocol analyzer deployed for network
troubleshooting, analysis education and protocol development.
A protocol analyzer also known as packet sniffer or network analyzer is a computing software which can
cut off and log the data traffic flow going via a network. During data go back and out over a network,
protocol analyzer captures every PDU. The packet sniffer is able to decode and scrutinize its components
with respect to the suitable RFC together with supplementary specifications (Baxter, 2014).
Wireshark is decoded to distinguish structures of diverse network protocols. This gives it the capability to
present encapsulation and fields of the PDUs and give an interpretation of their meaning (Combs, 2019).
It should be noted that Wireshark is an imperative tool for anybody working with networks and can
deploy it in labs of CCNA courses for troubleshooting and analysis of data.
In this assignment, we are going to use the Wireshark tool to show the contents of layer 1,2,3,4 and 5
PDUs of a network.
In the steps below, we are going to perform packet capture and analysis.
Note that we are using 3.0.0 version of Wireshark.
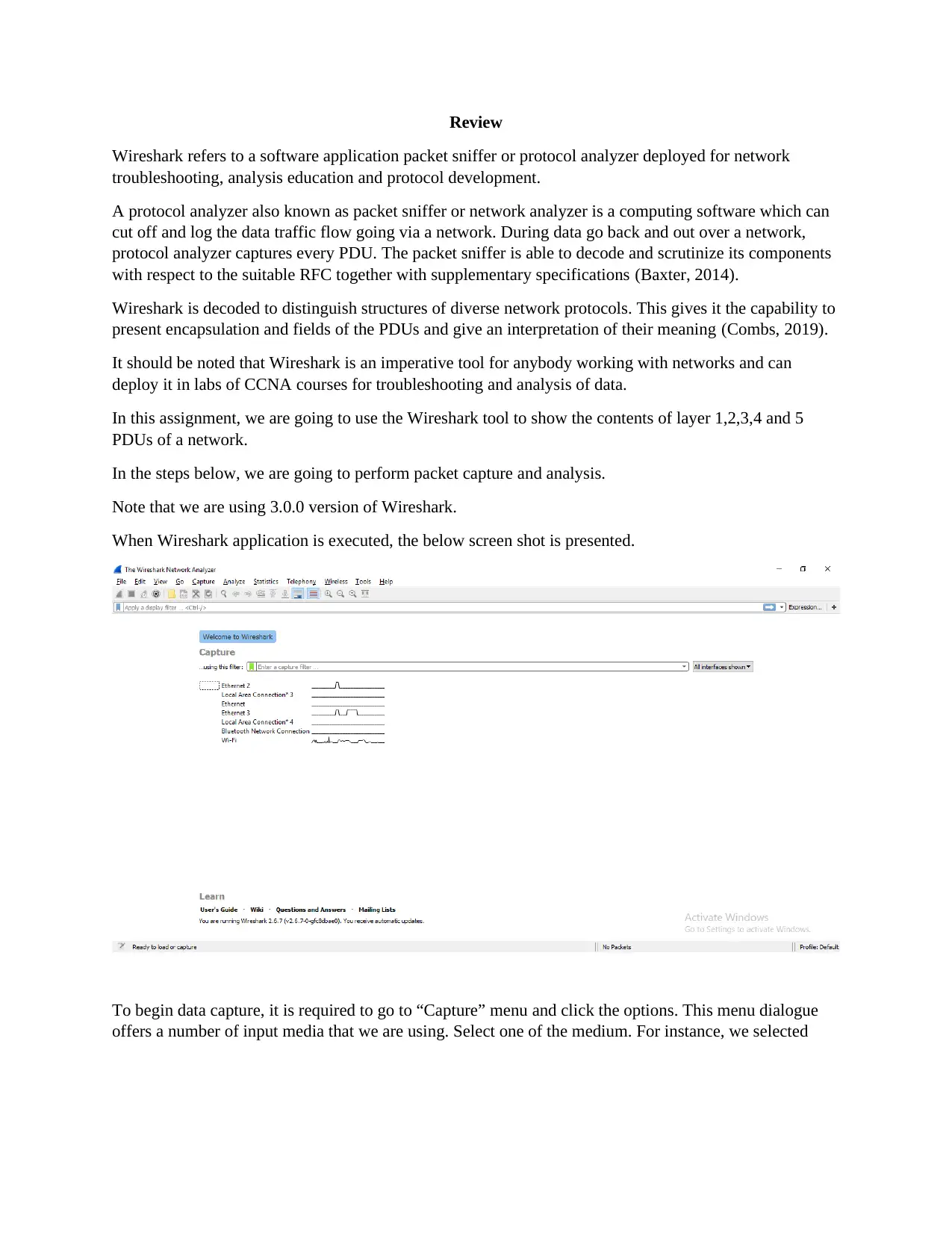
When Wireshark application is executed, the below screen shot is presented.
To begin data capture, it is required to go to “Capture” menu and click the options. This menu dialogue
offers a number of input media that we are using. Select one of the medium. For instance, we selected
Wireshark refers to a software application packet sniffer or protocol analyzer deployed for network
troubleshooting, analysis education and protocol development.
A protocol analyzer also known as packet sniffer or network analyzer is a computing software which can
cut off and log the data traffic flow going via a network. During data go back and out over a network,
protocol analyzer captures every PDU. The packet sniffer is able to decode and scrutinize its components
with respect to the suitable RFC together with supplementary specifications (Baxter, 2014).
Wireshark is decoded to distinguish structures of diverse network protocols. This gives it the capability to
present encapsulation and fields of the PDUs and give an interpretation of their meaning (Combs, 2019).
It should be noted that Wireshark is an imperative tool for anybody working with networks and can
deploy it in labs of CCNA courses for troubleshooting and analysis of data.
In this assignment, we are going to use the Wireshark tool to show the contents of layer 1,2,3,4 and 5
PDUs of a network.
In the steps below, we are going to perform packet capture and analysis.
Note that we are using 3.0.0 version of Wireshark.
When Wireshark application is executed, the below screen shot is presented.
To begin data capture, it is required to go to “Capture” menu and click the options. This menu dialogue
offers a number of input media that we are using. Select one of the medium. For instance, we selected
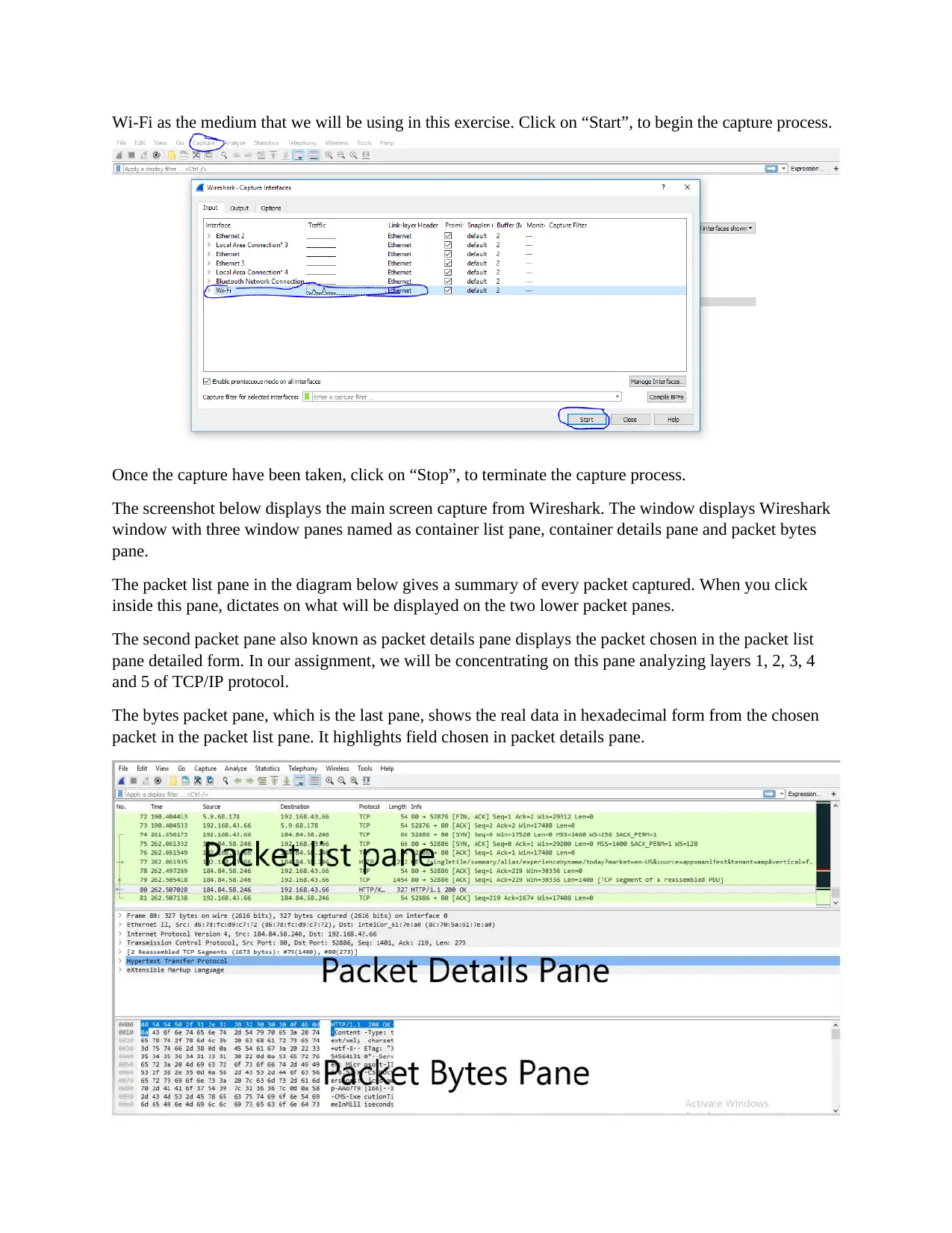
Wi-Fi as the medium that we will be using in this exercise. Click on “Start”, to begin the capture process.
Once the capture have been taken, click on “Stop”, to terminate the capture process.
The screenshot below displays the main screen capture from Wireshark. The window displays Wireshark
window with three window panes named as container list pane, container details pane and packet bytes
pane.
The packet list pane in the diagram below gives a summary of every packet captured. When you click
inside this pane, dictates on what will be displayed on the two lower packet panes.
The second packet pane also known as packet details pane displays the packet chosen in the packet list
pane detailed form. In our assignment, we will be concentrating on this pane analyzing layers 1, 2, 3, 4
and 5 of TCP/IP protocol.
The bytes packet pane, which is the last pane, shows the real data in hexadecimal form from the chosen
packet in the packet list pane. It highlights field chosen in packet details pane.
Once the capture have been taken, click on “Stop”, to terminate the capture process.
The screenshot below displays the main screen capture from Wireshark. The window displays Wireshark
window with three window panes named as container list pane, container details pane and packet bytes
pane.
The packet list pane in the diagram below gives a summary of every packet captured. When you click
inside this pane, dictates on what will be displayed on the two lower packet panes.
The second packet pane also known as packet details pane displays the packet chosen in the packet list
pane detailed form. In our assignment, we will be concentrating on this pane analyzing layers 1, 2, 3, 4
and 5 of TCP/IP protocol.
The bytes packet pane, which is the last pane, shows the real data in hexadecimal form from the chosen
packet in the packet list pane. It highlights field chosen in packet details pane.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

HTTP Wireshark Analyzer details
From our image above, packet number 80 is our packet of interest. TCP/IP layers below are observed in
the packet details pane i.e.
Layer 1 – Physical layer
Interface id: 0 (\Device\NPF_{A43151FE-45E3-4744-8F84-1F88AAC2ADB3})
Interface name: \Device\NPF_{A43151FE-45E3-4744-8F84-1F88AAC2ADB3}
Encapsulation type: Ethernet (1)
Arrival Time: Mar 5, 2019 06:28:28.789547000 E. Africa Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1551756508.789547000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: HTTP]
[Coloring Rule String: http || tcp.port == 80 || http2]
Layer 2 – Data-link Layer (Ethernet II)
Ethernet II, Src: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0), Dst: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
Destination: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
Address: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0)
Address: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0)
From our image above, packet number 80 is our packet of interest. TCP/IP layers below are observed in
the packet details pane i.e.
Layer 1 – Physical layer
Interface id: 0 (\Device\NPF_{A43151FE-45E3-4744-8F84-1F88AAC2ADB3})
Interface name: \Device\NPF_{A43151FE-45E3-4744-8F84-1F88AAC2ADB3}
Encapsulation type: Ethernet (1)
Arrival Time: Mar 5, 2019 06:28:28.789547000 E. Africa Standard Time
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1551756508.789547000 seconds
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.000000000 seconds]
[Time since reference or first frame: 0.000000000 seconds]
Frame Number: 1
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
[Coloring Rule Name: HTTP]
[Coloring Rule String: http || tcp.port == 80 || http2]
Layer 2 – Data-link Layer (Ethernet II)
Ethernet II, Src: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0), Dst: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
Destination: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
Address: d6:7d:fc:d9:c7:72 (d6:7d:fc:d9:c7:72)
.... ..1. .... .... .... .... = LG bit: Locally administered address (this is NOT the factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0)
Address: IntelCor_61:7e:a0 (8c:70:5a:61:7e:a0)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Layer 3 – Network Layer (Internet Protocol)
Internet Protocol Version 4, Src: 192.168.43.66, Dst: 93.184.220.29
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 52
Identification: 0x423e (16958)
Flags: 0x4000, Don't fragment
0... .... .... .... = Reserved bit: Not set
.1.. .... .... .... = Don't fragment: Set
..0. .... .... .... = More fragments: Not set
...0 0000 0000 0000 = Fragment offset: 0
Time to live: 128
Protocol: TCP (6)
Header checksum: 0x92c5 [validation disabled]
[Header checksum status: Unverified]
Source: 192.168.43.66
Destination: 93.184.220.29
Layer 4 – Transport Layer ()
Transmission Control Protocol, Src Port: 51710, Dst Port: 80, Seq: 0, Len: 0
Source Port: 51710
Destination Port: 80
[Stream index: 0]
[TCP Segment Len: 0]
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Layer 3 – Network Layer (Internet Protocol)
Internet Protocol Version 4, Src: 192.168.43.66, Dst: 93.184.220.29
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 52
Identification: 0x423e (16958)
Flags: 0x4000, Don't fragment
0... .... .... .... = Reserved bit: Not set
.1.. .... .... .... = Don't fragment: Set
..0. .... .... .... = More fragments: Not set
...0 0000 0000 0000 = Fragment offset: 0
Time to live: 128
Protocol: TCP (6)
Header checksum: 0x92c5 [validation disabled]
[Header checksum status: Unverified]
Source: 192.168.43.66
Destination: 93.184.220.29
Layer 4 – Transport Layer ()
Transmission Control Protocol, Src Port: 51710, Dst Port: 80, Seq: 0, Len: 0
Source Port: 51710
Destination Port: 80
[Stream index: 0]
[TCP Segment Len: 0]

Sequence number: 0 (relative sequence number)
[Next sequence number: 0 (relative sequence number)]
Acknowledgment number: 0
1000 .... = Header Length: 32 bytes (8)
Flags: 0x002 (SYN)
Window size value: 17520
[Calculated window size: 17520]
Checksum: 0x2b07 [unverified]
[Checksum Status: Unverified]
Urgent pointer: 0
Options: (12 bytes), Maximum segment size, No-Operation (NOP), Window scale, No-Operation
(NOP), No-Operation (NOP), SACK permitted
[Timestamps]
No. Time Source Destination Protocol Length Info
2 0.042216 192.168.43.66 93.184.220.29 TCP 66 51713 → 80 [SYN] Seq=0
Win=17520 Len=0 MSS=1460 WS=256 SACK_PERM=1
Layer 5 – Session Layer
Hypertext Transfer Protocol
GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n
[Expert Info (Chat/Sequence): GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n]
[GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n]
[Severity level: Chat]
[Group: Sequence]
Request Method: GET
Request URI:
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D
[Next sequence number: 0 (relative sequence number)]
Acknowledgment number: 0
1000 .... = Header Length: 32 bytes (8)
Flags: 0x002 (SYN)
Window size value: 17520
[Calculated window size: 17520]
Checksum: 0x2b07 [unverified]
[Checksum Status: Unverified]
Urgent pointer: 0
Options: (12 bytes), Maximum segment size, No-Operation (NOP), Window scale, No-Operation
(NOP), No-Operation (NOP), SACK permitted
[Timestamps]
No. Time Source Destination Protocol Length Info
2 0.042216 192.168.43.66 93.184.220.29 TCP 66 51713 → 80 [SYN] Seq=0
Win=17520 Len=0 MSS=1460 WS=256 SACK_PERM=1
Layer 5 – Session Layer
Hypertext Transfer Protocol
GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n
[Expert Info (Chat/Sequence): GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n]
[GET
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D HTTP/1.1\r\n]
[Severity level: Chat]
[Group: Sequence]
Request Method: GET
Request URI:
/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYd
UvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Request Version: HTTP/1.1
Connection: Keep-Alive\r\n
Accept: */*\r\n
User-Agent: Microsoft-CryptoAPI/10.0\r\n
Host: ocsp.digicert.com\r\n
\r\n
[Full request URI:
http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqP
HDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D]
[HTTP request 1/2]
[Response in frame: 12]
[Next request in frame: 35]
Source Address: 93.184.220.29
Destination address: 192.168.43.66
The Ethernet type is: Ethernet II, this is highlighted in the packet details pane.
Connection: Keep-Alive\r\n
Accept: */*\r\n
User-Agent: Microsoft-CryptoAPI/10.0\r\n
Host: ocsp.digicert.com\r\n
\r\n
[Full request URI:
http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqP
HDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAMXuD70nNkGmxQ3ymnzWEA%3D]
[HTTP request 1/2]
[Response in frame: 12]
[Next request in frame: 35]
Source Address: 93.184.220.29
Destination address: 192.168.43.66
The Ethernet type is: Ethernet II, this is highlighted in the packet details pane.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Baxter, J. H. ( 2014). Wireshark Essentials. Mumbai: Packt Publishing Ltd.
Combs, G. (2019, March 5). About Wireshark. Retrieved March 5, 2019, from Wireshark:
https://www.wireshark.org/
Baxter, J. H. ( 2014). Wireshark Essentials. Mumbai: Packt Publishing Ltd.
Combs, G. (2019, March 5). About Wireshark. Retrieved March 5, 2019, from Wireshark:
https://www.wireshark.org/
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




