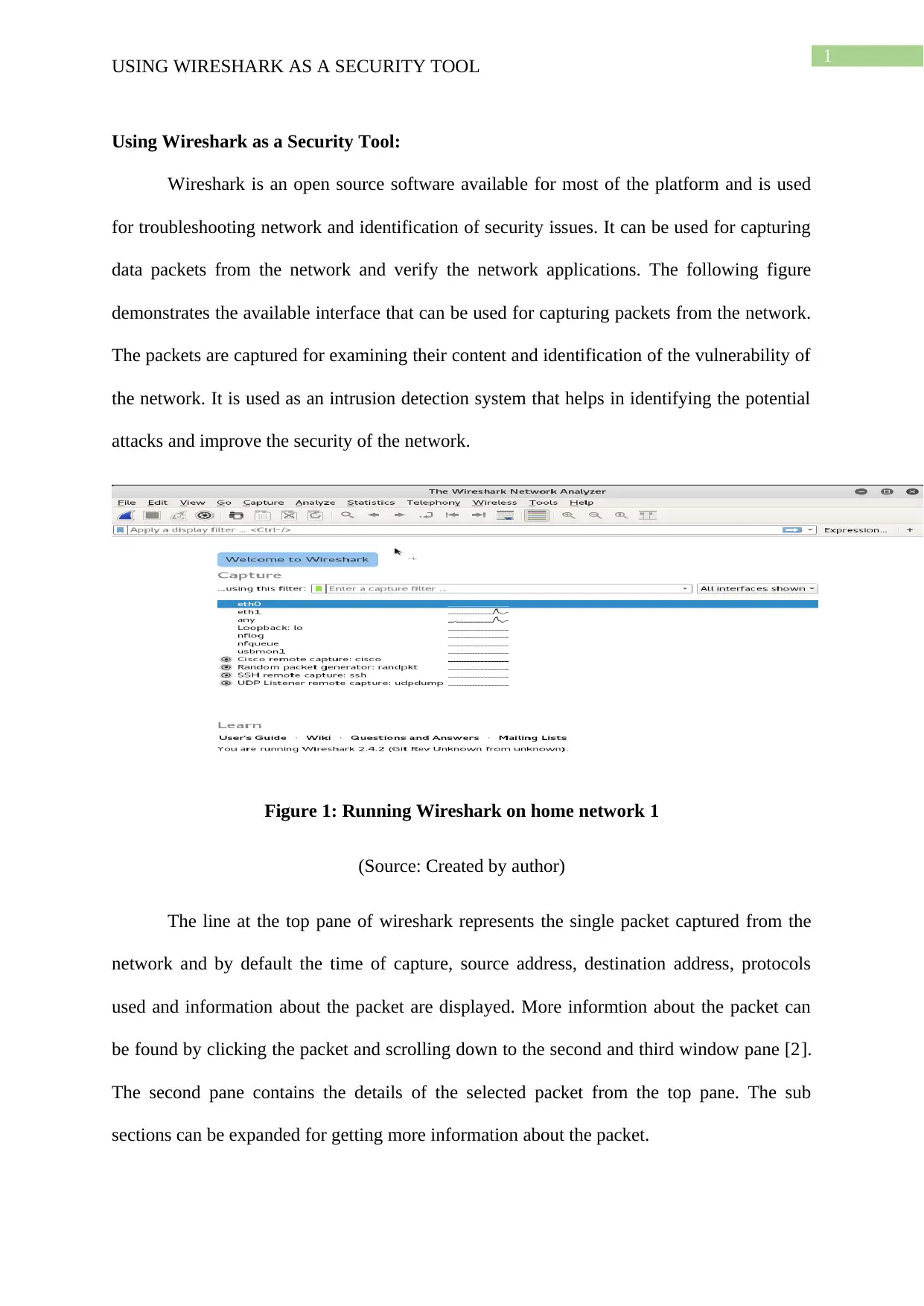
Wireshark: Security Analysis and Network Packet Inspection Report
VerifiedAdded on 2023/01/16
|4
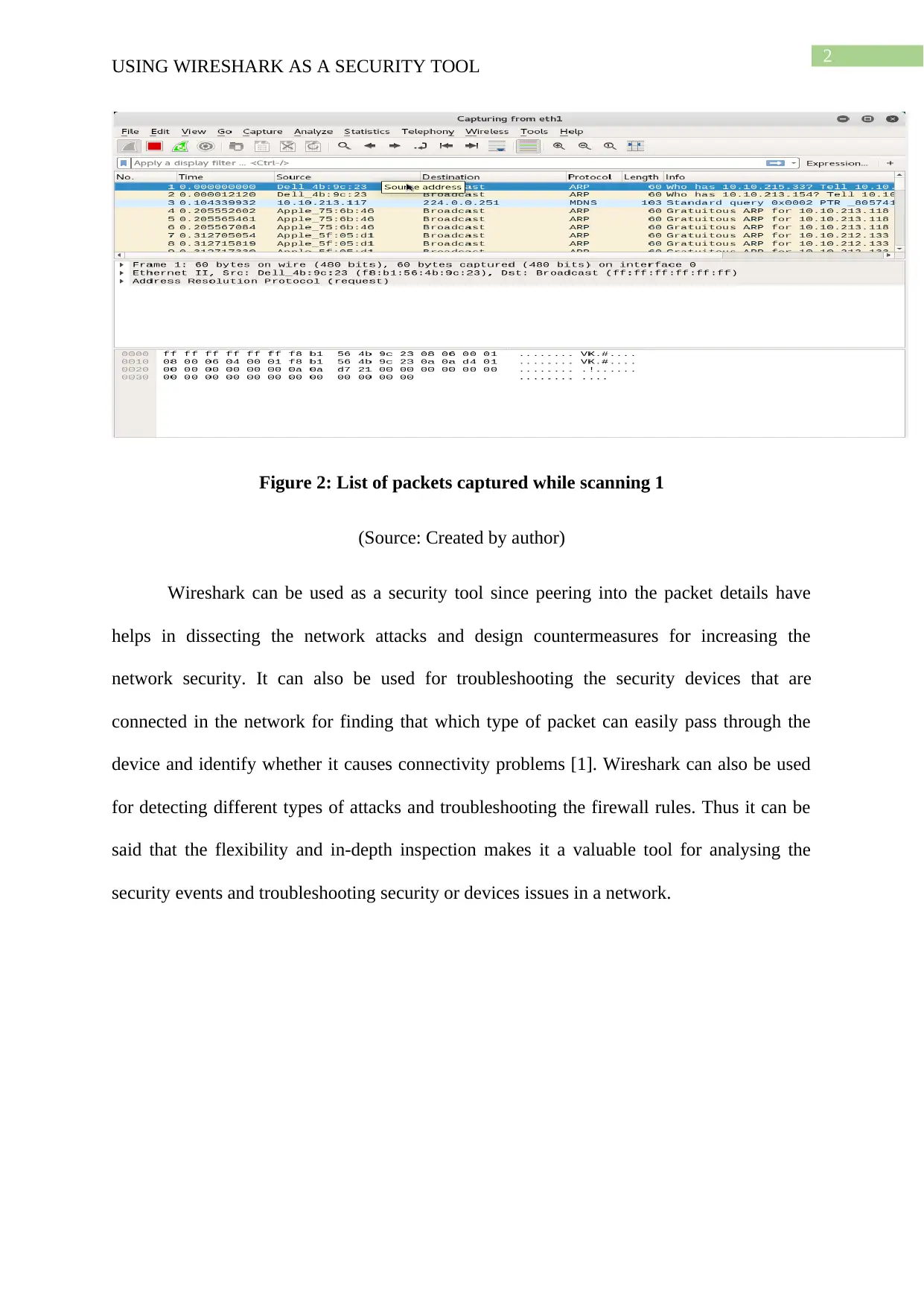
|481
|83
Report
AI Summary
This report examines Wireshark as a powerful tool for network security analysis. It details how Wireshark can be used to capture and inspect network packets, providing insights into potential security vulnerabilities and attacks. The report showcases the application of Wireshark in identifying and troubleshooting security issues, including its role in intrusion detection and firewall rule analysis. Through examples and references, the report highlights the flexibility and in-depth inspection capabilities of Wireshark, making it a valuable resource for understanding and enhancing network security. The author also provided examples of the interface and how the packets are captured and analyzed. The report concludes by emphasizing the importance of Wireshark in dissecting network attacks and designing countermeasures to improve overall network security.
1 out of 4









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)