University Name: Computer Networking - Wireshark SSL Lab Analysis
VerifiedAdded on 2022/11/28
|15
|2052
|219
Practical Assignment
AI Summary
This report analyzes an SSL session captured from an e-commerce site using Wireshark. The analysis focuses on SSL record types, fields, and the handshake process. The report examines the client and server hello messages, certificate details, client key exchange, and application data. A timing diagram illustrates the communication flow. The report identifies cipher suites, encryption algorithms, and session IDs. Key aspects include the pre-master secret, change cipher spec records, and encrypted handshake messages. The findings provide insights into the secure communication established between the client and server, covering encryption, key exchange, and data transmission. The report also explores the SSL version changes, and the resume of handshake processes. The report concludes that the details of the transaction are analyzed from the captured frames with the help of a timing diagram that shows the time taken for sending and receiving each of the SSL messages. The size of each of the SSL record is evaluated in terms of their fields and length. The cryptography used by the SSL can be found along with the algorithm used for the encryption. The server hello SSL record is located and the cipher suite used in the transaction is also evaluated and documented in the report. All the details such as session ID, certificate, length of the certificate and details of the client key exchange record are evaluated and documented.

Running head: WIRESHARK LAB: SSL V7.0
Wireshark Lab: SSL v7.0
Name of the Student
Name of the University
Author’s Note
Wireshark Lab: SSL v7.0
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRESHARK LAB: SSL V7.0
Table of Contents
Background......................................................................................................................................3
Request............................................................................................................................................3
Summary of Findings......................................................................................................................3
Evidence..........................................................................................................................................4
Analysis...........................................................................................................................................7
Conclusion.....................................................................................................................................12
Bibliography..................................................................................................................................13
Tables
Table 1: table for type of SSL, source and frame no.......................................................................7
Figures
FIGURE 1: SCREENSHOT OF THE PACKET CAPTURED IN WIRESHARK DEMONSTRATING
APPLICATION DATA........................................................................................................................4
FIGURE 2: SCREENSHOT OF THE CLIENT HELLO DETAILS..........................................................5
FIGURE 3: SCREENSHOT DEMONSTRATING Server HELLO DETAILS...........................................5
FIGURE 4: SCREEN DEMONSTRATING CLIENT KEY EXCHANGE RECORD..................................6
FIGURE 5: TIMING DIAGRAM BETWEEN CLIENT AND SERVER.....................................................8
WIRESHARK LAB: SSL V7.0
Table of Contents
Background......................................................................................................................................3
Request............................................................................................................................................3
Summary of Findings......................................................................................................................3
Evidence..........................................................................................................................................4
Analysis...........................................................................................................................................7
Conclusion.....................................................................................................................................12
Bibliography..................................................................................................................................13
Tables
Table 1: table for type of SSL, source and frame no.......................................................................7
Figures
FIGURE 1: SCREENSHOT OF THE PACKET CAPTURED IN WIRESHARK DEMONSTRATING
APPLICATION DATA........................................................................................................................4
FIGURE 2: SCREENSHOT OF THE CLIENT HELLO DETAILS..........................................................5
FIGURE 3: SCREENSHOT DEMONSTRATING Server HELLO DETAILS...........................................5
FIGURE 4: SCREEN DEMONSTRATING CLIENT KEY EXCHANGE RECORD..................................6
FIGURE 5: TIMING DIAGRAM BETWEEN CLIENT AND SERVER.....................................................8

2
WIRESHARK LAB: SSL V7.0
Executive Summary
The report is prepared for the analysis of the SSL session that is captured from an ecommerce
site during purchasing a product. For the capturing of the packets the filter is set to capture only
the SSL records send between the host and the server. The details of the transaction is analyzed
from the captured frames and a timing diagram is drawn demonstrating the time taken for
sending and receiving each of the SSL messages. The size of each of the SSL record is evaluated
in terms of their fields and length. The cryptography used by the SSL can be found along with
the algorithm used for the encryption. The server hello SSL record is located and the cipher suite
used in the transaction is also evaluated and documented in the report. All the details such as
session ID, certificate, length of the certificate and details of the client key exchange record are
evaluated and documented.
WIRESHARK LAB: SSL V7.0
Executive Summary
The report is prepared for the analysis of the SSL session that is captured from an ecommerce
site during purchasing a product. For the capturing of the packets the filter is set to capture only
the SSL records send between the host and the server. The details of the transaction is analyzed
from the captured frames and a timing diagram is drawn demonstrating the time taken for
sending and receiving each of the SSL messages. The size of each of the SSL record is evaluated
in terms of their fields and length. The cryptography used by the SSL can be found along with
the algorithm used for the encryption. The server hello SSL record is located and the cipher suite
used in the transaction is also evaluated and documented in the report. All the details such as
session ID, certificate, length of the certificate and details of the client key exchange record are
evaluated and documented.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
WIRESHARK LAB: SSL V7.0
Background
With the use of SSL an encrypted and secure connection is established between the client
server and the browser. In the first stage the client starts the communication by listing the SSL
version and cipher suite it can use. In return the server can see the list and pick a latest version
that can be used by the server. Using the version the server sends a message containing the
selected SSL version and cipher suite. During the server key exchange a SSL certificate is sent to
the client and the web browser of the client validates the certificate sent by the server. A list of
Root CA is stored by the web browser and which are for the third party that the web browser
trusts. After receiving the CA signature and public key is sent by the server and at the end a
server hello done message is sent. In the client key exchange unencrypted information is sent
between the server and the client.
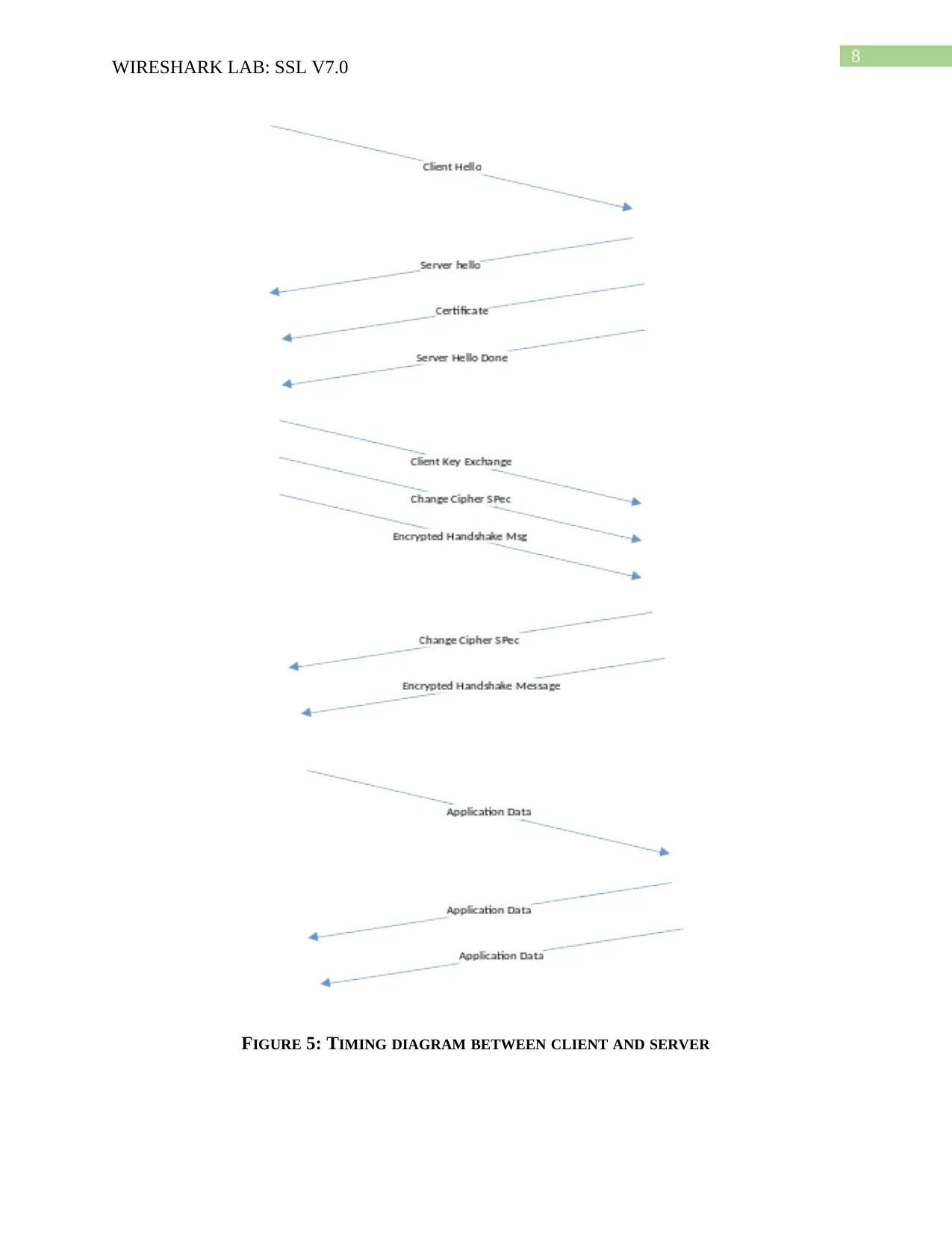
Request
Client Hello request is sent by the client and the server sends a server hello in return.
A certificate and server Hello done request is also sent by the server.
Client key exchange is sent by the client along with change cipher spec and encrypted
handshake message.
The server sends a change cipher spec message and encrypted handshake message.
An application data is sent by the client and it is returned by the server.
Summary of Findings
A session is generated and after receiving of the public key from the server and for
sending it to the server it encrypts with the public key. The server can only decrypt the key since
it has the private key and thus the communication is secured between client and the server. The
WIRESHARK LAB: SSL V7.0
Background
With the use of SSL an encrypted and secure connection is established between the client
server and the browser. In the first stage the client starts the communication by listing the SSL
version and cipher suite it can use. In return the server can see the list and pick a latest version
that can be used by the server. Using the version the server sends a message containing the
selected SSL version and cipher suite. During the server key exchange a SSL certificate is sent to
the client and the web browser of the client validates the certificate sent by the server. A list of
Root CA is stored by the web browser and which are for the third party that the web browser
trusts. After receiving the CA signature and public key is sent by the server and at the end a
server hello done message is sent. In the client key exchange unencrypted information is sent
between the server and the client.
Request
Client Hello request is sent by the client and the server sends a server hello in return.
A certificate and server Hello done request is also sent by the server.
Client key exchange is sent by the client along with change cipher spec and encrypted
handshake message.
The server sends a change cipher spec message and encrypted handshake message.
An application data is sent by the client and it is returned by the server.
Summary of Findings
A session is generated and after receiving of the public key from the server and for
sending it to the server it encrypts with the public key. The server can only decrypt the key since
it has the private key and thus the communication is secured between client and the server. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
WIRESHARK LAB: SSL V7.0
client and the server both sends change cipher spec message and for generating notification for
the receiving party for recording the subsequent record and protecting it from just negotiated
CiperSpec and keys. An encrypted handshake takes place between the server and the client
saying that the key information are correct.
Evidence
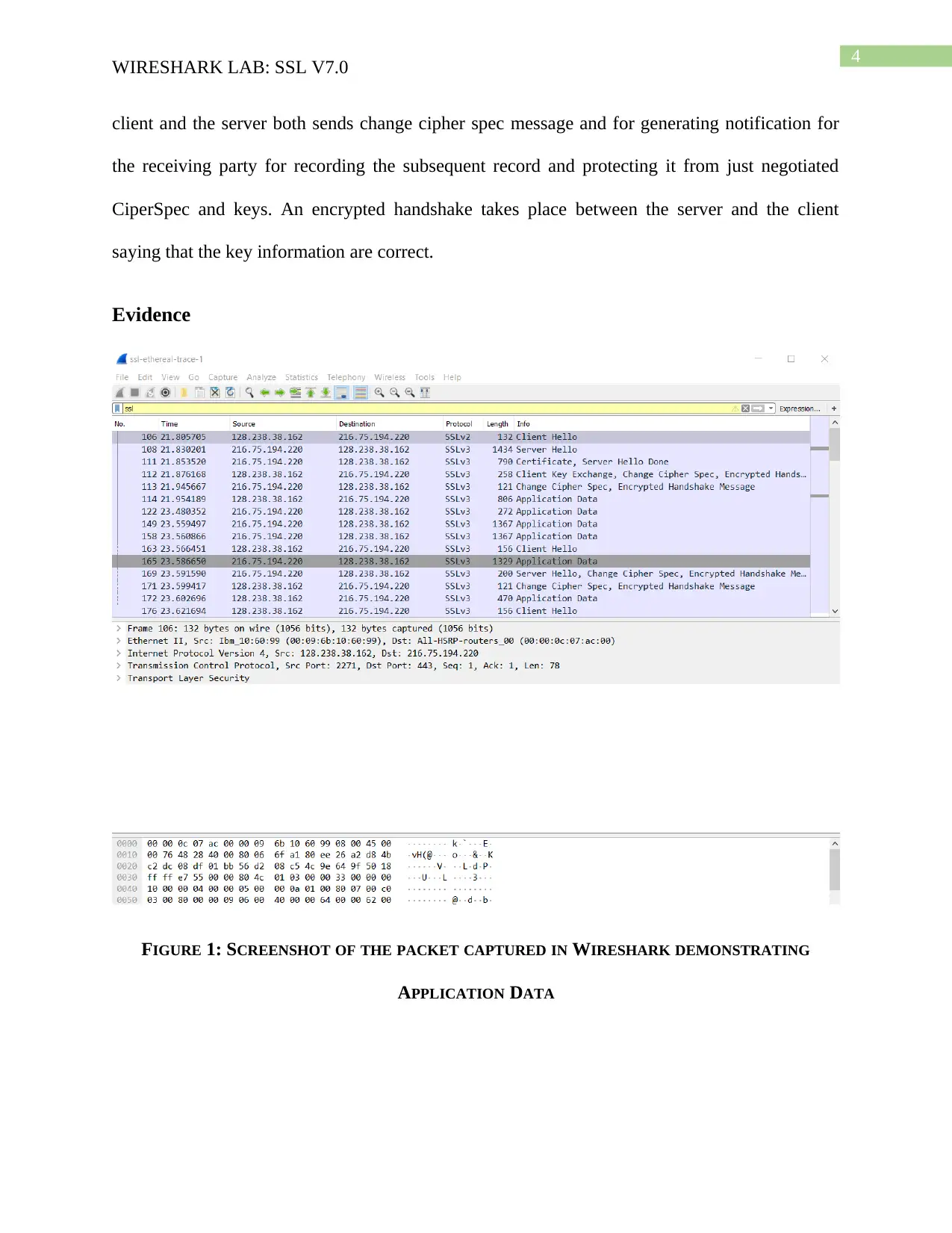
FIGURE 1: SCREENSHOT OF THE PACKET CAPTURED IN WIRESHARK DEMONSTRATING
APPLICATION DATA
WIRESHARK LAB: SSL V7.0
client and the server both sends change cipher spec message and for generating notification for
the receiving party for recording the subsequent record and protecting it from just negotiated
CiperSpec and keys. An encrypted handshake takes place between the server and the client
saying that the key information are correct.
Evidence
FIGURE 1: SCREENSHOT OF THE PACKET CAPTURED IN WIRESHARK DEMONSTRATING
APPLICATION DATA
5
WIRESHARK LAB: SSL V7.0
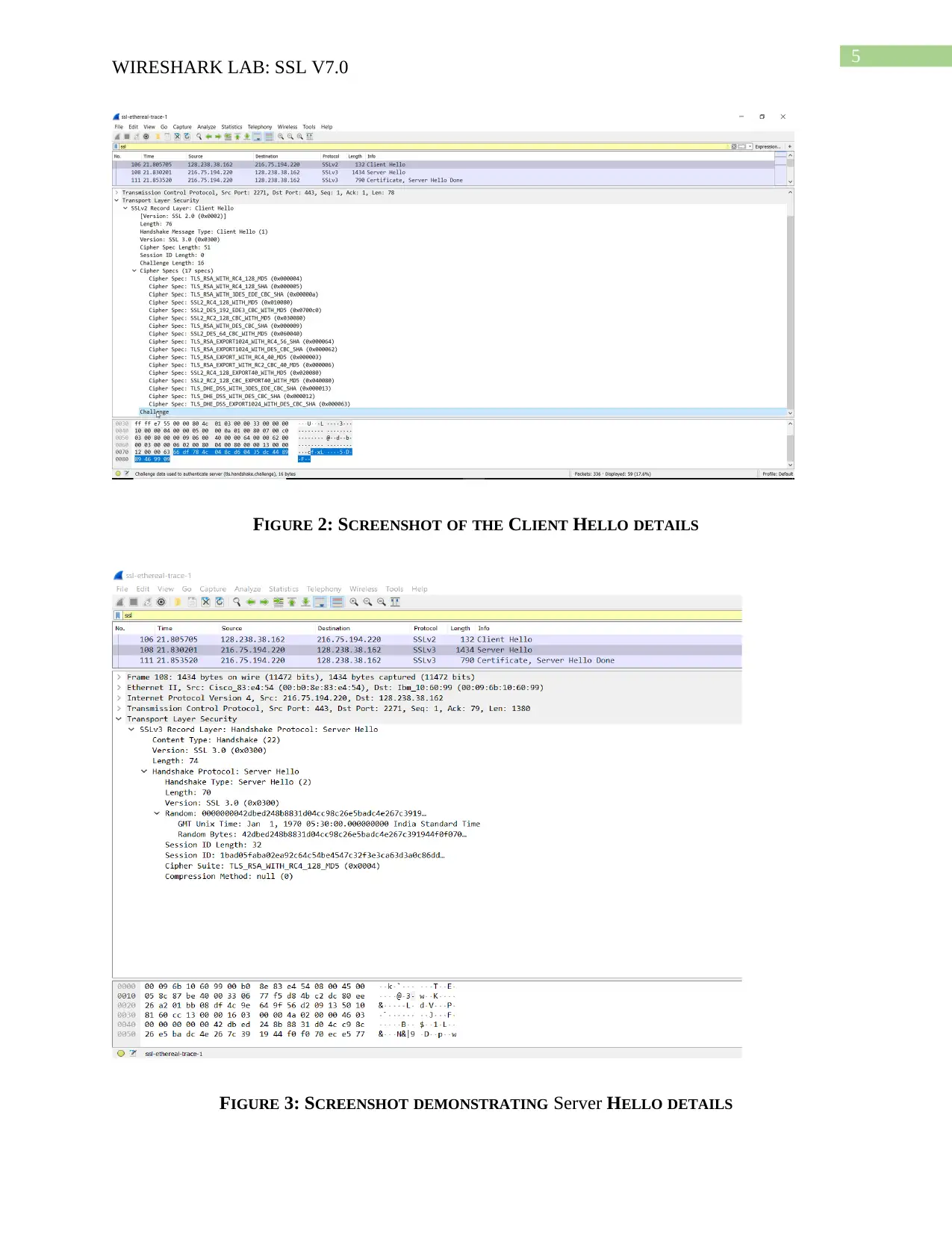
FIGURE 2: SCREENSHOT OF THE CLIENT HELLO DETAILS
FIGURE 3: SCREENSHOT DEMONSTRATING Server HELLO DETAILS
WIRESHARK LAB: SSL V7.0
FIGURE 2: SCREENSHOT OF THE CLIENT HELLO DETAILS
FIGURE 3: SCREENSHOT DEMONSTRATING Server HELLO DETAILS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRESHARK LAB: SSL V7.0
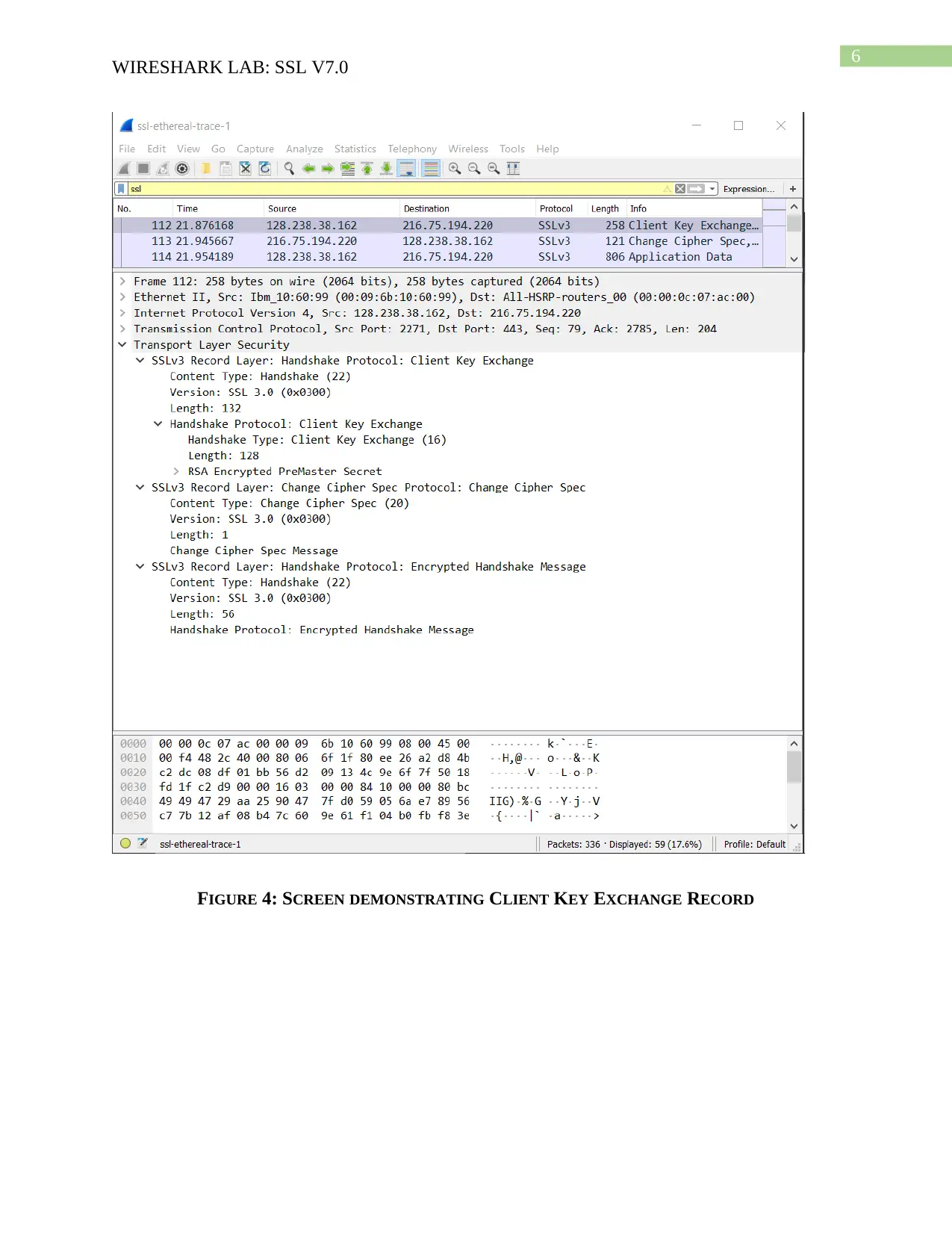
FIGURE 4: SCREEN DEMONSTRATING CLIENT KEY EXCHANGE RECORD
WIRESHARK LAB: SSL V7.0
FIGURE 4: SCREEN DEMONSTRATING CLIENT KEY EXCHANGE RECORD
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
WIRESHARK LAB: SSL V7.0
Analysis
Analysis Questions:
Answer to Question 1:
Frame No Source Count of SSL Type of SSL
106 Client 1 Client Hello
108 Server 1 Server hello
111 Server 2 Certificate Server
Hello Done
112 Client 3 Client Key Exchange
Change Cipher Spec
Encrypted Handshake
Message
113 Server 2 Application Data
114 Client 1 Application Data
122 Server 1 Application Data
127 Server 1 Application Data
Table 1: table for type of SSL, source and frame no.
WIRESHARK LAB: SSL V7.0
Analysis
Analysis Questions:
Answer to Question 1:
Frame No Source Count of SSL Type of SSL
106 Client 1 Client Hello
108 Server 1 Server hello
111 Server 2 Certificate Server
Hello Done
112 Client 3 Client Key Exchange
Change Cipher Spec
Encrypted Handshake
Message
113 Server 2 Application Data
114 Client 1 Application Data
122 Server 1 Application Data
127 Server 1 Application Data
Table 1: table for type of SSL, source and frame no.
8
WIRESHARK LAB: SSL V7.0
FIGURE 5: TIMING DIAGRAM BETWEEN CLIENT AND SERVER
WIRESHARK LAB: SSL V7.0
FIGURE 5: TIMING DIAGRAM BETWEEN CLIENT AND SERVER
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
WIRESHARK LAB: SSL V7.0
Answer to Question 2:
Type of Content – 1 byte
Version – 2 byte
Length – 2 byte
Client Hello Record:
Answer to Question 3:
The type of content is 22 for a handshake message and has a handshake type 1, client hello.
Answer to Question 4:
Yes the client record contains a nonce which is also known as challenge and value of the
challenge in hexadecimal notation is given below:
0000 66 df 78 4c 04 8c d6 04 35 dc 44 89 89 46 99 09 f.xL....5.D..F..
Answer to Question 5:
RSA algorithm is used by the first suite for public key crypto and the RC4 is used for the
symmetric key cipher. MD5 hash algorithm is used by the ClientHello for advertising the cyber
suites.
Server Hello Record:
Answer to Question 6:
The record does specifies a chosen cipher suite and it utilizes the TSA algorithm for public key
cryptography. RC4 is used for the symmetric key cipher along with MD5 hash.
WIRESHARK LAB: SSL V7.0
Answer to Question 2:
Type of Content – 1 byte
Version – 2 byte
Length – 2 byte
Client Hello Record:
Answer to Question 3:
The type of content is 22 for a handshake message and has a handshake type 1, client hello.
Answer to Question 4:
Yes the client record contains a nonce which is also known as challenge and value of the
challenge in hexadecimal notation is given below:
0000 66 df 78 4c 04 8c d6 04 35 dc 44 89 89 46 99 09 f.xL....5.D..F..
Answer to Question 5:
RSA algorithm is used by the first suite for public key crypto and the RC4 is used for the
symmetric key cipher. MD5 hash algorithm is used by the ClientHello for advertising the cyber
suites.
Server Hello Record:
Answer to Question 6:
The record does specifies a chosen cipher suite and it utilizes the TSA algorithm for public key
cryptography. RC4 is used for the symmetric key cipher along with MD5 hash.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
WIRESHARK LAB: SSL V7.0
Answer to Question 7:
Yes a nonce is present in the record and it can be found under the random list. The length of the
nonce is 32 bits and the data has 28 bits and the time has 4 bits. It finds its application for the
prevention of replay attacks.
Answer to Question 8:
Yes a session ID is included in the record. A unique persistent identifier is provided for each of
SSL session and is sent in clear text format. The same session can be resumed by the client later
with the use of session ID that is used by the server as CleintHello.
Answer to Question 9:
The record contains no certificate and the certificate is there for another record. A single Ethernet
frame is used by the certificate because it fits into the single Ethernet frame.
Client Key Exchange Record:
Answer to Question 10:
The client key exchange protocol is found in packet number 112 and it contains a pre-master
secret. The client and the server uses the pre-master secret for making master secret and
generation of session key for encryption and MAC. The secrets are encrypted with the use public
key of the server. The public key of the server is extracted from the certificate and it is of 128
bytes in length.
Change Cipher Spec Record (sent by client) and Encrypted Handshake Record:
Answer to Question 11:
WIRESHARK LAB: SSL V7.0
Answer to Question 7:
Yes a nonce is present in the record and it can be found under the random list. The length of the
nonce is 32 bits and the data has 28 bits and the time has 4 bits. It finds its application for the
prevention of replay attacks.
Answer to Question 8:
Yes a session ID is included in the record. A unique persistent identifier is provided for each of
SSL session and is sent in clear text format. The same session can be resumed by the client later
with the use of session ID that is used by the server as CleintHello.
Answer to Question 9:
The record contains no certificate and the certificate is there for another record. A single Ethernet
frame is used by the certificate because it fits into the single Ethernet frame.
Client Key Exchange Record:
Answer to Question 10:
The client key exchange protocol is found in packet number 112 and it contains a pre-master
secret. The client and the server uses the pre-master secret for making master secret and
generation of session key for encryption and MAC. The secrets are encrypted with the use public
key of the server. The public key of the server is extracted from the certificate and it is of 128
bytes in length.
Change Cipher Spec Record (sent by client) and Encrypted Handshake Record:
Answer to Question 11:

11
WIRESHARK LAB: SSL V7.0
Change Cipher Spec record is used for indicating the contents of SSL records that is sent by the
client to encrypt. The length of the record is 6 bytes where 5 bytes is considered for the header
and 1 byte for message segment.
Answer to Question 12:
In the encrypted handshake record the previous handshake message sent by the client are
concatenated for the MAC and sent with the server.
Answer to Question 13:
The server also sends a change cipher record by encrypting the handshake record in multiple
forms after receiving from the client. This is done since it consists concatenation of the
handshake message that are sent from server or the record would end being same.
Application Data
Answer to Question 14:
Symmetric key encryption is used for encrypting the application data during the phase of
handshake with the use of keys that are generated by the pre-master key and nonce from server
and client. The encryption key of the client is utilized for encrypting data sent between client and
server and the server encryption key is used for encrypting the data that is sent from the server
destined for the client.
Answer to Question 15:
The SSL version changes from SSLv2 in ClientHello to SSLv3 in the next message exchange.
The resume of handshake process is different from the initial because here the client does not
need Cert and thus the server does not sends it. A new nonce is needed to be sent following the
WIRESHARK LAB: SSL V7.0
Change Cipher Spec record is used for indicating the contents of SSL records that is sent by the
client to encrypt. The length of the record is 6 bytes where 5 bytes is considered for the header
and 1 byte for message segment.
Answer to Question 12:
In the encrypted handshake record the previous handshake message sent by the client are
concatenated for the MAC and sent with the server.
Answer to Question 13:
The server also sends a change cipher record by encrypting the handshake record in multiple
forms after receiving from the client. This is done since it consists concatenation of the
handshake message that are sent from server or the record would end being same.
Application Data
Answer to Question 14:
Symmetric key encryption is used for encrypting the application data during the phase of
handshake with the use of keys that are generated by the pre-master key and nonce from server
and client. The encryption key of the client is utilized for encrypting data sent between client and
server and the server encryption key is used for encrypting the data that is sent from the server
destined for the client.
Answer to Question 15:
The SSL version changes from SSLv2 in ClientHello to SSLv3 in the next message exchange.
The resume of handshake process is different from the initial because here the client does not
need Cert and thus the server does not sends it. A new nonce is needed to be sent following the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



