Network Analysis and Traffic Flow - Practical Assignment Analysis
VerifiedAdded on 2022/08/26
|8
|759
|16
Practical Assignment
AI Summary
This assignment focuses on network analysis and traffic flow using Wireshark. The student conducted ping tests and traceroutes to websites like ebay.com, yahoo.com, and youtube.com, capturing the network packets using Wireshark. The analysis includes examining TCP flows, ICMP echo requests and replies, and DNS packets. Screenshots of the Wireshark output, including TCP streams and DNS packet details, are provided. The assignment also covers the sequence numbers of the packets and the hops involved in the traceroutes. The student documented the packets and traffic flow between the sender and the host, and also included a bibliography of relevant research papers. The assignment demonstrates the use of Wireshark to analyze network traffic at a microscopic level, providing insights into network protocols and data transmission.

Running head: NETWORK ANALYSIS AND TRAFFIC FLOW
Network Analysis and Traffic Flow
Name of the Student
Name of the University
Author Note
Network Analysis and Traffic Flow
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1NETWORK ANALYSIS AND TRAFFIC FLOW
Task 5
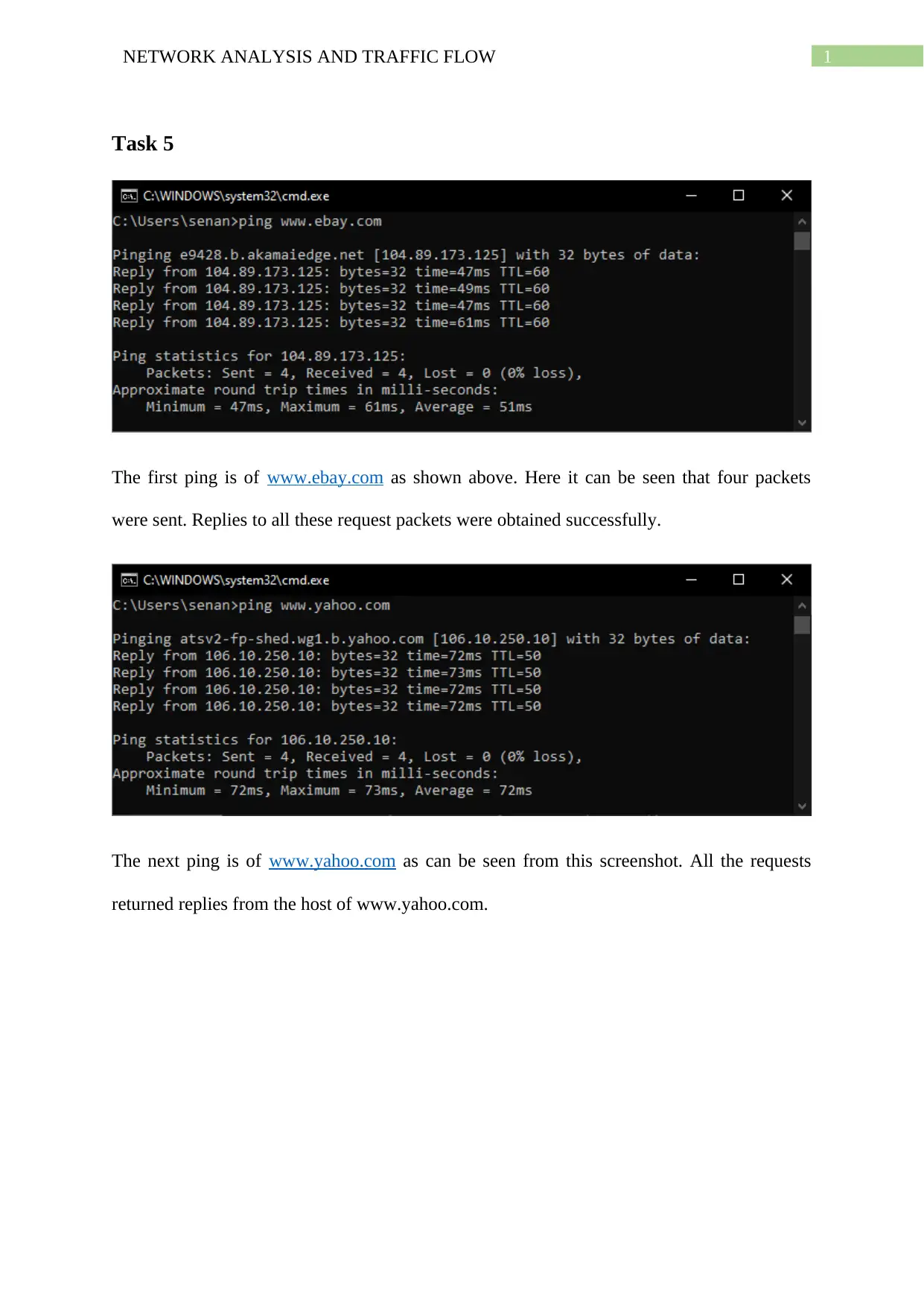
The first ping is of www.ebay.com as shown above. Here it can be seen that four packets
were sent. Replies to all these request packets were obtained successfully.
The next ping is of www.yahoo.com as can be seen from this screenshot. All the requests
returned replies from the host of www.yahoo.com.
Task 5
The first ping is of www.ebay.com as shown above. Here it can be seen that four packets
were sent. Replies to all these request packets were obtained successfully.
The next ping is of www.yahoo.com as can be seen from this screenshot. All the requests
returned replies from the host of www.yahoo.com.
2NETWORK ANALYSIS AND TRAFFIC FLOW
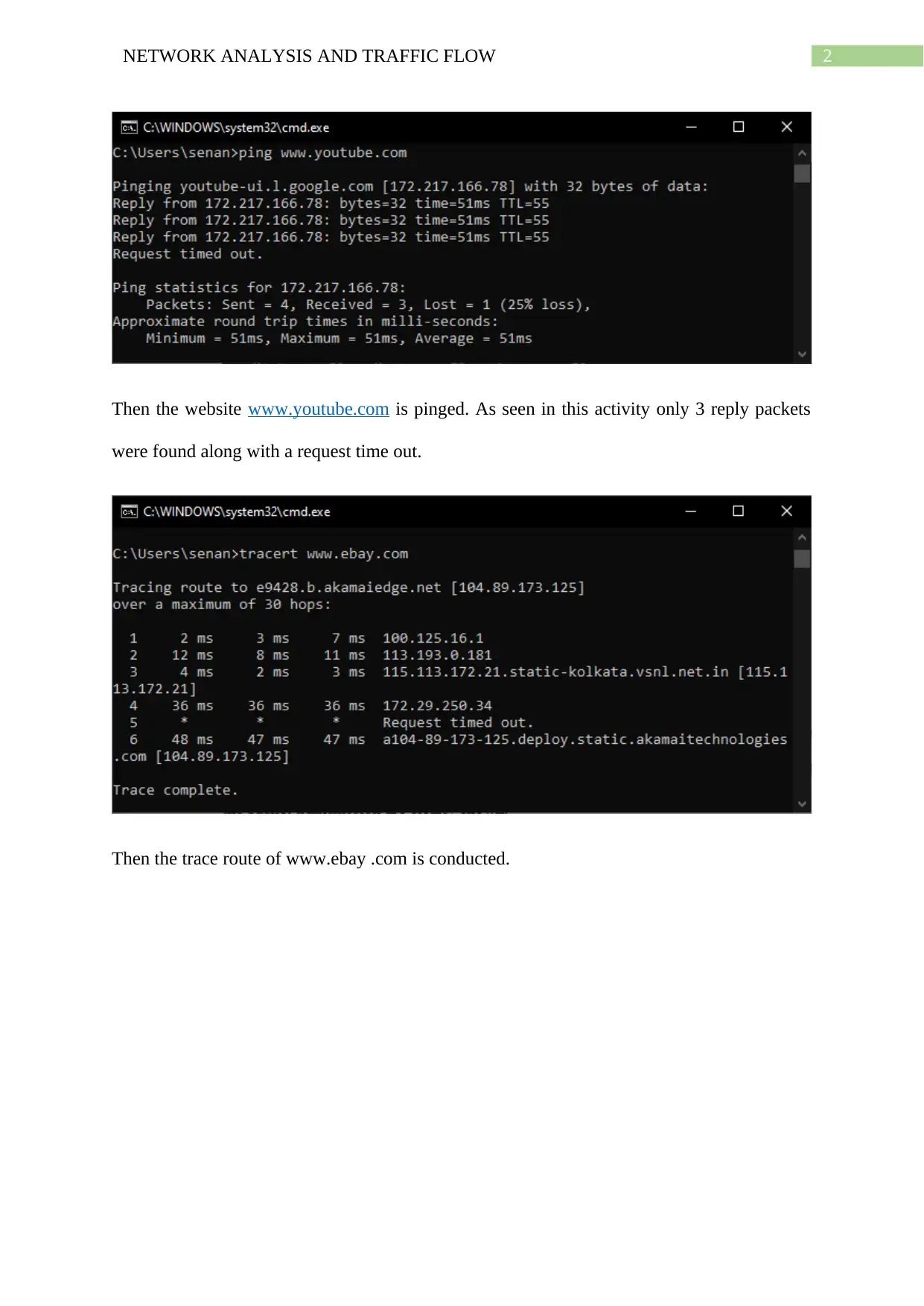
Then the website www.youtube.com is pinged. As seen in this activity only 3 reply packets
were found along with a request time out.
Then the trace route of www.ebay .com is conducted.
Then the website www.youtube.com is pinged. As seen in this activity only 3 reply packets
were found along with a request time out.
Then the trace route of www.ebay .com is conducted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3NETWORK ANALYSIS AND TRAFFIC FLOW
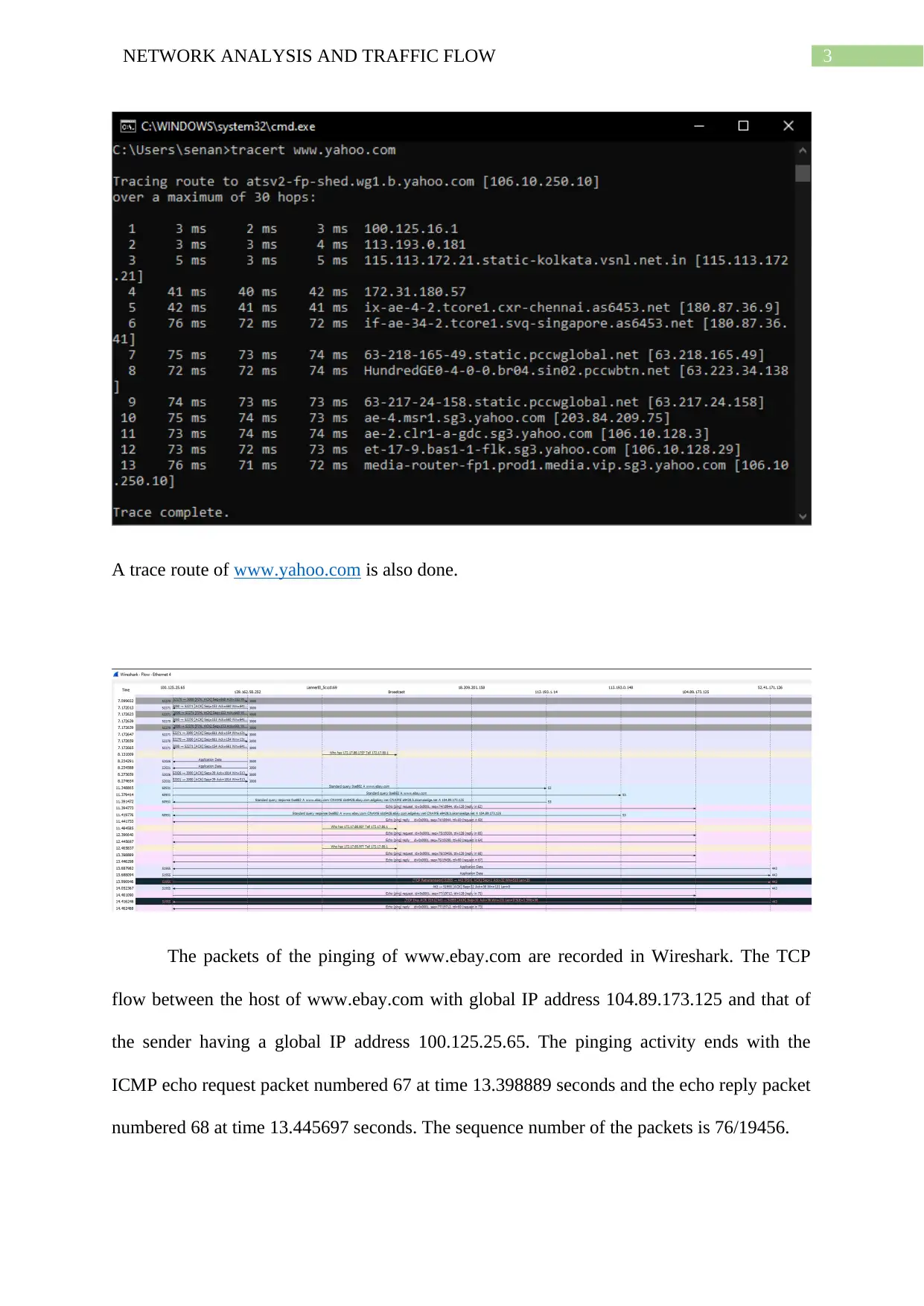
A trace route of www.yahoo.com is also done.
The packets of the pinging of www.ebay.com are recorded in Wireshark. The TCP
flow between the host of www.ebay.com with global IP address 104.89.173.125 and that of
the sender having a global IP address 100.125.25.65. The pinging activity ends with the
ICMP echo request packet numbered 67 at time 13.398889 seconds and the echo reply packet
numbered 68 at time 13.445697 seconds. The sequence number of the packets is 76/19456.
A trace route of www.yahoo.com is also done.
The packets of the pinging of www.ebay.com are recorded in Wireshark. The TCP
flow between the host of www.ebay.com with global IP address 104.89.173.125 and that of
the sender having a global IP address 100.125.25.65. The pinging activity ends with the
ICMP echo request packet numbered 67 at time 13.398889 seconds and the echo reply packet
numbered 68 at time 13.445697 seconds. The sequence number of the packets is 76/19456.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK ANALYSIS AND TRAFFIC FLOW
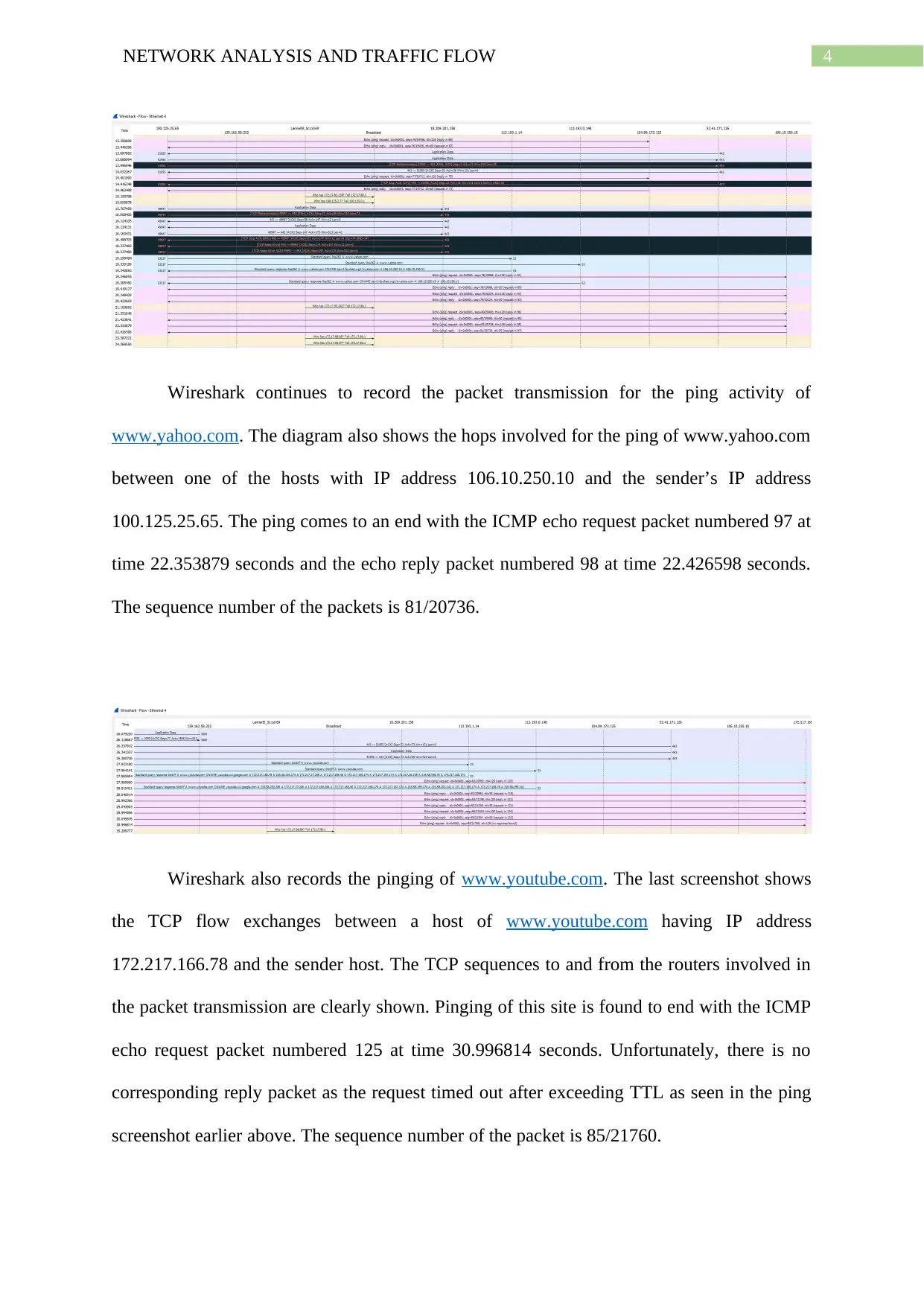
Wireshark continues to record the packet transmission for the ping activity of
www.yahoo.com. The diagram also shows the hops involved for the ping of www.yahoo.com
between one of the hosts with IP address 106.10.250.10 and the sender’s IP address
100.125.25.65. The ping comes to an end with the ICMP echo request packet numbered 97 at
time 22.353879 seconds and the echo reply packet numbered 98 at time 22.426598 seconds.
The sequence number of the packets is 81/20736.
Wireshark also records the pinging of www.youtube.com. The last screenshot shows
the TCP flow exchanges between a host of www.youtube.com having IP address
172.217.166.78 and the sender host. The TCP sequences to and from the routers involved in
the packet transmission are clearly shown. Pinging of this site is found to end with the ICMP
echo request packet numbered 125 at time 30.996814 seconds. Unfortunately, there is no
corresponding reply packet as the request timed out after exceeding TTL as seen in the ping
screenshot earlier above. The sequence number of the packet is 85/21760.
Wireshark continues to record the packet transmission for the ping activity of
www.yahoo.com. The diagram also shows the hops involved for the ping of www.yahoo.com
between one of the hosts with IP address 106.10.250.10 and the sender’s IP address
100.125.25.65. The ping comes to an end with the ICMP echo request packet numbered 97 at
time 22.353879 seconds and the echo reply packet numbered 98 at time 22.426598 seconds.
The sequence number of the packets is 81/20736.
Wireshark also records the pinging of www.youtube.com. The last screenshot shows
the TCP flow exchanges between a host of www.youtube.com having IP address
172.217.166.78 and the sender host. The TCP sequences to and from the routers involved in
the packet transmission are clearly shown. Pinging of this site is found to end with the ICMP
echo request packet numbered 125 at time 30.996814 seconds. Unfortunately, there is no
corresponding reply packet as the request timed out after exceeding TTL as seen in the ping
screenshot earlier above. The sequence number of the packet is 85/21760.

5NETWORK ANALYSIS AND TRAFFIC FLOW
The traceroute of www.ebay,com is also captured by Wireshark. In this diagram, it
gets shown how the packets travel through the different hops that exists between the sender
and the host of www.ebay.com. The final packet to reach the host of www.ebay.com is the
328th packet after time 74.007544 seconds and the corresponding reply is provided by the
329th packet after time 74.055025 seconds. Sequence number of the packets is 103/26368.
Then the traceroute of www.yahoo.com is gets recorded in Wireshark. The diagram
shows that the packets transmitted during the traceroute by the sender host traverses multiple
hops before reaching the host of www.yahoo.com. The last packet to reach the host of
www.yahoo.com happens to be the 665th packet after time 113.772797 seconds and the
The traceroute of www.ebay,com is also captured by Wireshark. In this diagram, it
gets shown how the packets travel through the different hops that exists between the sender
and the host of www.ebay.com. The final packet to reach the host of www.ebay.com is the
328th packet after time 74.007544 seconds and the corresponding reply is provided by the
329th packet after time 74.055025 seconds. Sequence number of the packets is 103/26368.
Then the traceroute of www.yahoo.com is gets recorded in Wireshark. The diagram
shows that the packets transmitted during the traceroute by the sender host traverses multiple
hops before reaching the host of www.yahoo.com. The last packet to reach the host of
www.yahoo.com happens to be the 665th packet after time 113.772797 seconds and the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK ANALYSIS AND TRAFFIC FLOW
corresponding reply is received from the 666th packet after time 113.845674 seconds. The
sequence number of the packets is 142/36352. The time has been measured in seconds since
beginning of recording by the Wireshark application starting with ping of www.ebay.com.
corresponding reply is received from the 666th packet after time 113.845674 seconds. The
sequence number of the packets is 142/36352. The time has been measured in seconds since
beginning of recording by the Wireshark application starting with ping of www.ebay.com.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK ANALYSIS AND TRAFFIC FLOW
Bibliography
El Sheikh, A.Y., 2018. Evaluation of the capabilities of Wireshark as network intrusion
system. Journal of Global Research in Computer Science, 9(8), pp.01-08.
Iorliam, A., Tirunagari, S., Ho, A.T., Li, S., Waller, A. and Poh, N., 2016. " Flow Size
Difference" Can Make a Difference: Detecting Malicious TCP Network Flows Based on
Benford's Law. arXiv preprint arXiv:1609.04214.
Jamshed, M.A., Moon, Y., Kim, D., Han, D. and Park, K., 2017. mos: A reusable networking
stack for flow monitoring middleboxes. In 14th {USENIX} Symposium on Networked
Systems Design and Implementation ({NSDI} 17) (pp. 113-129).
Miravalls-Sierra, E., Muelas, D., Ramos, J., de Vergara, J.E.L., Morató, D. and Aracil, J.,
2018. Online detection of pathological TCP flows with retransmissions in high-speed
networks. Computer Communications, 127, pp.95-104.
Bibliography
El Sheikh, A.Y., 2018. Evaluation of the capabilities of Wireshark as network intrusion
system. Journal of Global Research in Computer Science, 9(8), pp.01-08.
Iorliam, A., Tirunagari, S., Ho, A.T., Li, S., Waller, A. and Poh, N., 2016. " Flow Size
Difference" Can Make a Difference: Detecting Malicious TCP Network Flows Based on
Benford's Law. arXiv preprint arXiv:1609.04214.
Jamshed, M.A., Moon, Y., Kim, D., Han, D. and Park, K., 2017. mos: A reusable networking
stack for flow monitoring middleboxes. In 14th {USENIX} Symposium on Networked
Systems Design and Implementation ({NSDI} 17) (pp. 113-129).
Miravalls-Sierra, E., Muelas, D., Ramos, J., de Vergara, J.E.L., Morató, D. and Aracil, J.,
2018. Online detection of pathological TCP flows with retransmissions in high-speed
networks. Computer Communications, 127, pp.95-104.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




