WISE IT Network Enhancement Proposal: BN305 VPN Network Design
VerifiedAdded on 2023/06/04
|12
|2106
|187
Report
AI Summary
This document presents a detailed VPN network design solution, focusing on enhancing the network infrastructure for a Small to Medium Enterprise (SME). It includes an introduction to VPNs, their scopes, and limitations, followed by specific requirements for establishing a secure connection between remote locations. The solution design encompasses logical and physical aspects, network topologies (intranet and extranet VPNs), IP addressing schema, security features and policies, redundancy and failover plans, and VPN service deployment and implementation. The report also covers hardware and cabling requirements, wireless network considerations, and a bill of materials (BoM). The IP addressing and VLAN configurations are detailed, along with a failover scenario and cabling specifications, ensuring a robust and secure network environment. This paper emphasizes the importance of maintaining data security through encrypted connections and secured channels.

Running head: VIRTUAL PRIVATE NETWORK
Virtual Private Network
Name of the Student
Name of the University
Author Note
Virtual Private Network
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction................................................................................................................................2
Scopes and Limitations..............................................................................................................2
Requirements..............................................................................................................................3
Solution Design:.........................................................................................................................4
A. Logical Design.............................................................................................................4
B. Physical Design...........................................................................................................5
C. Network Topologies....................................................................................................5
D. IP addressing...............................................................................................................7
E. Security features and Policies......................................................................................8
F. Redundancy and Failover plans......................................................................................8
G. VPN service Deployment and implementation...........................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................10
Table of Contents
Introduction................................................................................................................................2
Scopes and Limitations..............................................................................................................2
Requirements..............................................................................................................................3
Solution Design:.........................................................................................................................4
A. Logical Design.............................................................................................................4
B. Physical Design...........................................................................................................5
C. Network Topologies....................................................................................................5
D. IP addressing...............................................................................................................7
E. Security features and Policies......................................................................................8
F. Redundancy and Failover plans......................................................................................8
G. VPN service Deployment and implementation...........................................................9
Conclusion..................................................................................................................................9
References................................................................................................................................10

2VIRTUAL PRIVATE NETWORK
Introduction:
The VPN or the Virtual private network can be explained as the service that helps in
establishing a secure connection between two remote locations using the public internet
services. The virtual private network helps in the process of enhancing the security services
with the use of the secure medium. The Use of the VPN is one of the most secured network
transmitting protocol that can be used, but it also have some of the major limitations. Other
than this one of the other major thing that the VPN helps in making a connection anonymous.
Hence if there is something is to be done without getting traced the same can be done using
the same. One of the other major benefit of using Virtual private networks is that, the
organisational can control the incoming and outgoing traffic of the organisation. This enables
to track all the nessecery transactions. The VPN also lets the management of the organisation
to set up different IP addresses for all the machines that are present in the organisation and
hence tracking the same also becomes very much easier.
This paper describes what virtual private network is and how these can be used for the
process of secured transmissions. This paper also describes the security issues that are related
to the VPN services. Further this paper describes the major differences between the extranet
and intranet virtual private networks. The major different kind of the IP addresses techniques
are also explained in the papers.
Scopes and Limitations
Although the VPN seems to be one of the most secured service that have been
developed but yet there are some of the major limitations in using these. This paper explains
the property that helps in the process of the ensuring and using the network security [1]. The
network design can help to understand how the data flows through the system and using the
VPN can help in the process of secured transmissions. VPN also helps in the process of
Introduction:
The VPN or the Virtual private network can be explained as the service that helps in
establishing a secure connection between two remote locations using the public internet
services. The virtual private network helps in the process of enhancing the security services
with the use of the secure medium. The Use of the VPN is one of the most secured network
transmitting protocol that can be used, but it also have some of the major limitations. Other
than this one of the other major thing that the VPN helps in making a connection anonymous.
Hence if there is something is to be done without getting traced the same can be done using
the same. One of the other major benefit of using Virtual private networks is that, the
organisational can control the incoming and outgoing traffic of the organisation. This enables
to track all the nessecery transactions. The VPN also lets the management of the organisation
to set up different IP addresses for all the machines that are present in the organisation and
hence tracking the same also becomes very much easier.
This paper describes what virtual private network is and how these can be used for the
process of secured transmissions. This paper also describes the security issues that are related
to the VPN services. Further this paper describes the major differences between the extranet
and intranet virtual private networks. The major different kind of the IP addresses techniques
are also explained in the papers.
Scopes and Limitations
Although the VPN seems to be one of the most secured service that have been
developed but yet there are some of the major limitations in using these. This paper explains
the property that helps in the process of the ensuring and using the network security [1]. The
network design can help to understand how the data flows through the system and using the
VPN can help in the process of secured transmissions. VPN also helps in the process of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3VIRTUAL PRIVATE NETWORK
encrypting information in between the computer systems and VPN servers. There are three
types of the virtual private network services that are available in present time, namely
Remote Access Virtual Private Network
Intranet Virtual Private Network
Extranet Virtual Private Network
One of the major limitation of using the Virtual private network is that it makes the internet
connection slower that the obtained speed.
Requirements:
In order to establish a proper connection in between the remote branch and the local office
the most important need is the use of the firewall between the connections [2]. There is a
need of the hardware like the servers and the work stations. The most important thing that is
required is the internet connections. Further the VPN enabled routers and switches are
required for the process.
encrypting information in between the computer systems and VPN servers. There are three
types of the virtual private network services that are available in present time, namely
Remote Access Virtual Private Network
Intranet Virtual Private Network
Extranet Virtual Private Network
One of the major limitation of using the Virtual private network is that it makes the internet
connection slower that the obtained speed.
Requirements:
In order to establish a proper connection in between the remote branch and the local office
the most important need is the use of the firewall between the connections [2]. There is a
need of the hardware like the servers and the work stations. The most important thing that is
required is the internet connections. Further the VPN enabled routers and switches are
required for the process.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
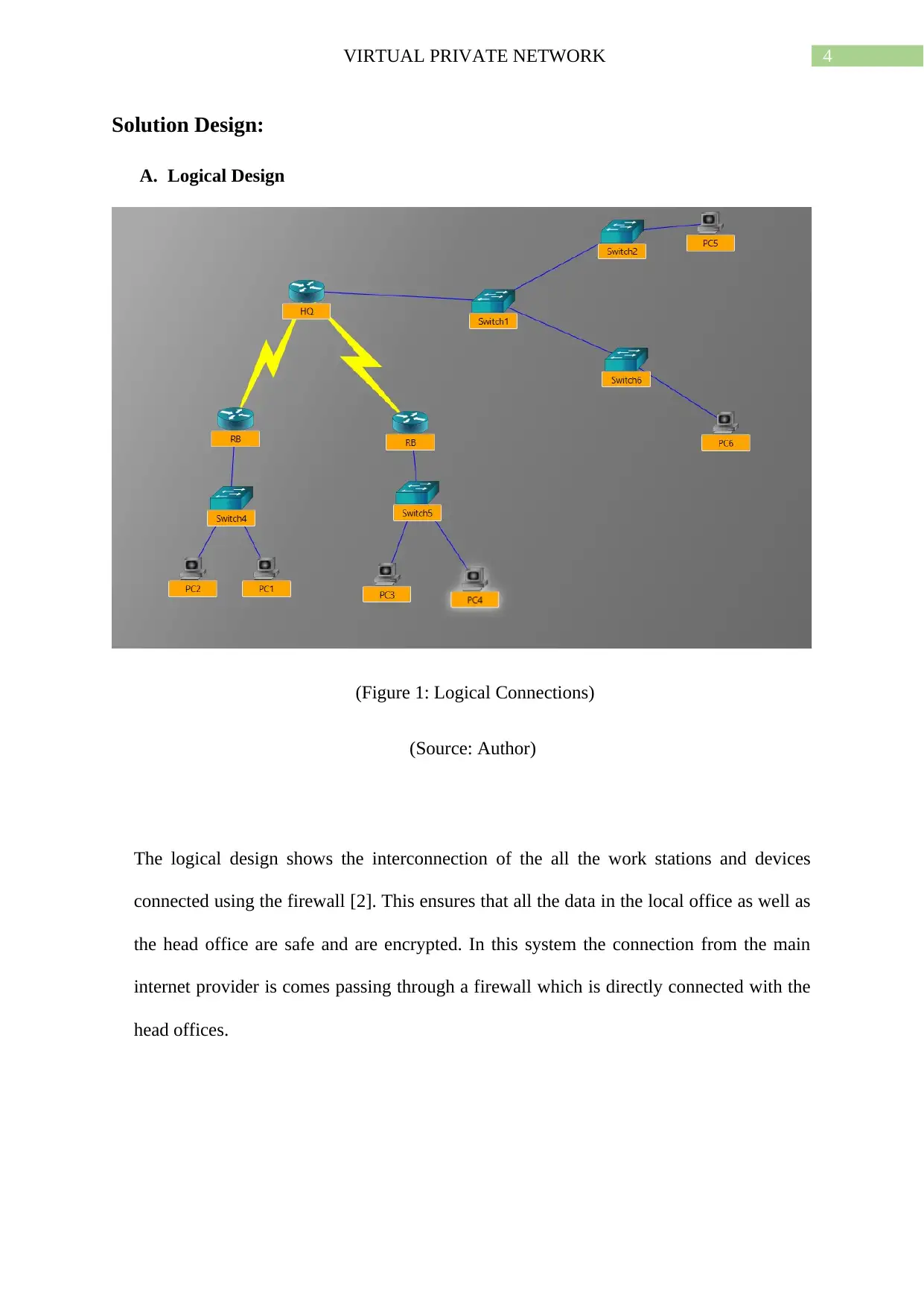
4VIRTUAL PRIVATE NETWORK
Solution Design:
A. Logical Design
(Figure 1: Logical Connections)
(Source: Author)
The logical design shows the interconnection of the all the work stations and devices
connected using the firewall [2]. This ensures that all the data in the local office as well as
the head office are safe and are encrypted. In this system the connection from the main
internet provider is comes passing through a firewall which is directly connected with the
head offices.
Solution Design:
A. Logical Design
(Figure 1: Logical Connections)
(Source: Author)
The logical design shows the interconnection of the all the work stations and devices
connected using the firewall [2]. This ensures that all the data in the local office as well as
the head office are safe and are encrypted. In this system the connection from the main
internet provider is comes passing through a firewall which is directly connected with the
head offices.
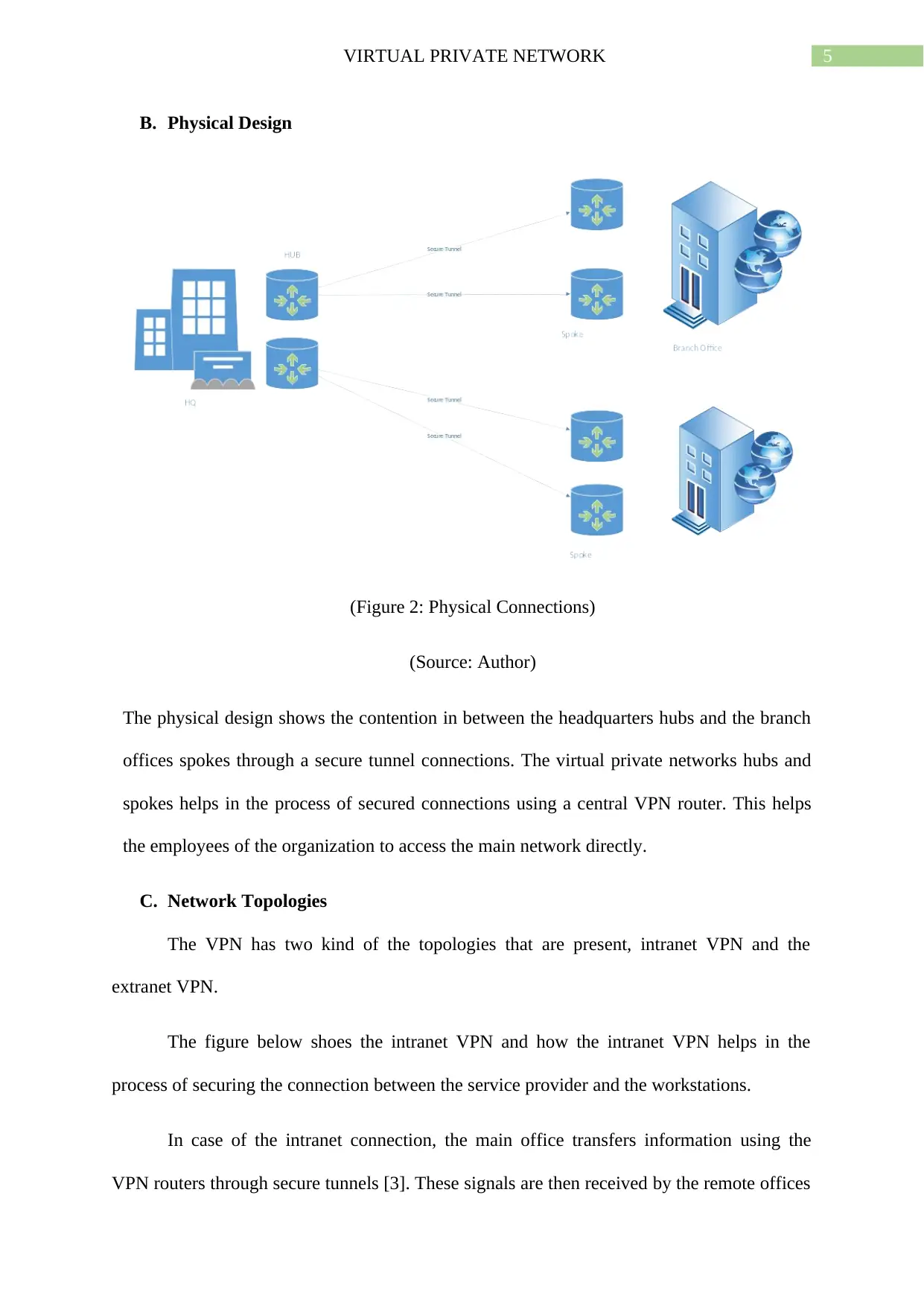
5VIRTUAL PRIVATE NETWORK
B. Physical Design
(Figure 2: Physical Connections)
(Source: Author)
The physical design shows the contention in between the headquarters hubs and the branch
offices spokes through a secure tunnel connections. The virtual private networks hubs and
spokes helps in the process of secured connections using a central VPN router. This helps
the employees of the organization to access the main network directly.
C. Network Topologies
The VPN has two kind of the topologies that are present, intranet VPN and the
extranet VPN.
The figure below shoes the intranet VPN and how the intranet VPN helps in the
process of securing the connection between the service provider and the workstations.
In case of the intranet connection, the main office transfers information using the
VPN routers through secure tunnels [3]. These signals are then received by the remote offices
B. Physical Design
(Figure 2: Physical Connections)
(Source: Author)
The physical design shows the contention in between the headquarters hubs and the branch
offices spokes through a secure tunnel connections. The virtual private networks hubs and
spokes helps in the process of secured connections using a central VPN router. This helps
the employees of the organization to access the main network directly.
C. Network Topologies
The VPN has two kind of the topologies that are present, intranet VPN and the
extranet VPN.
The figure below shoes the intranet VPN and how the intranet VPN helps in the
process of securing the connection between the service provider and the workstations.
In case of the intranet connection, the main office transfers information using the
VPN routers through secure tunnels [3]. These signals are then received by the remote offices
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
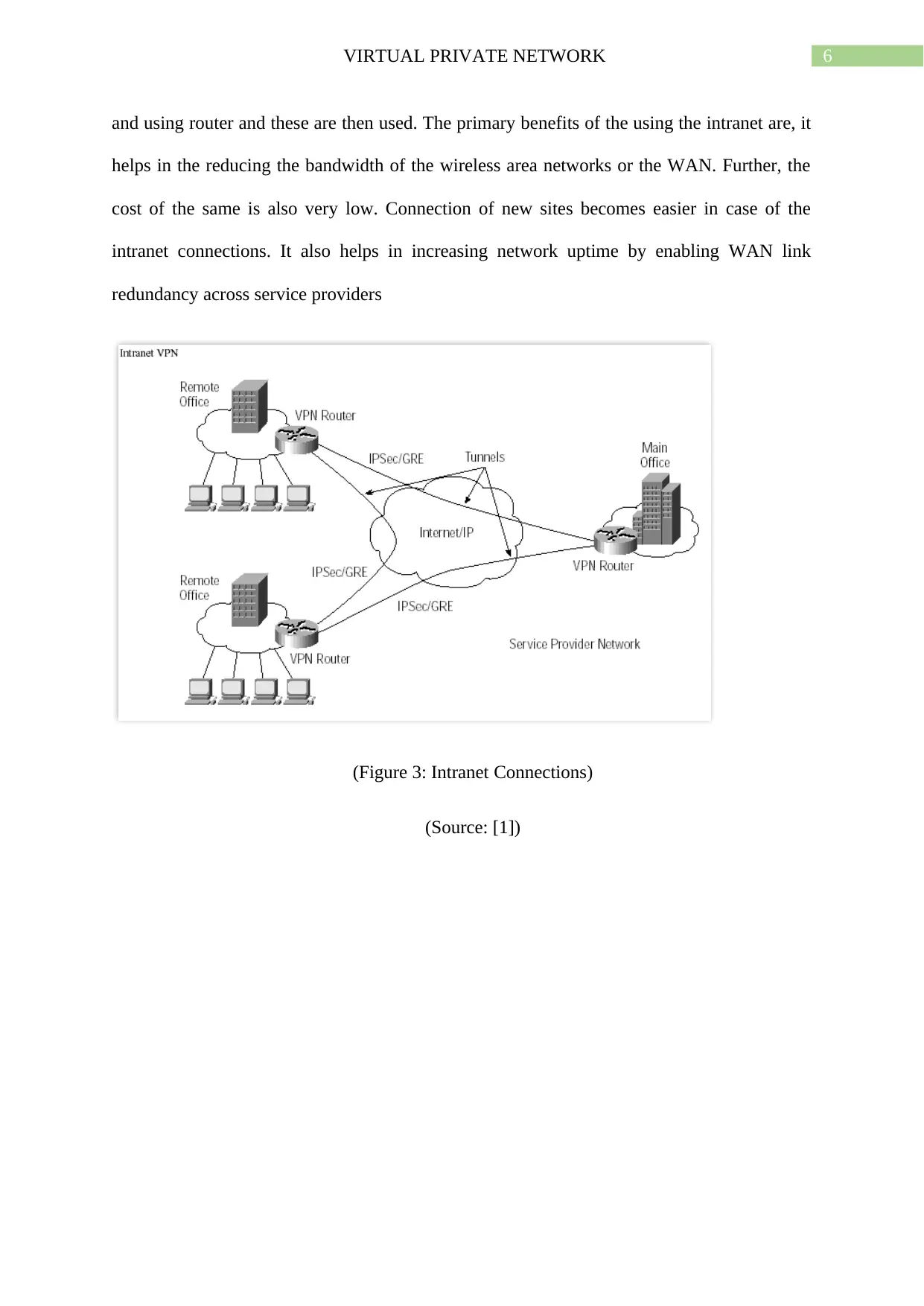
6VIRTUAL PRIVATE NETWORK
and using router and these are then used. The primary benefits of the using the intranet are, it
helps in the reducing the bandwidth of the wireless area networks or the WAN. Further, the
cost of the same is also very low. Connection of new sites becomes easier in case of the
intranet connections. It also helps in increasing network uptime by enabling WAN link
redundancy across service providers
(Figure 3: Intranet Connections)
(Source: [1])
and using router and these are then used. The primary benefits of the using the intranet are, it
helps in the reducing the bandwidth of the wireless area networks or the WAN. Further, the
cost of the same is also very low. Connection of new sites becomes easier in case of the
intranet connections. It also helps in increasing network uptime by enabling WAN link
redundancy across service providers
(Figure 3: Intranet Connections)
(Source: [1])
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
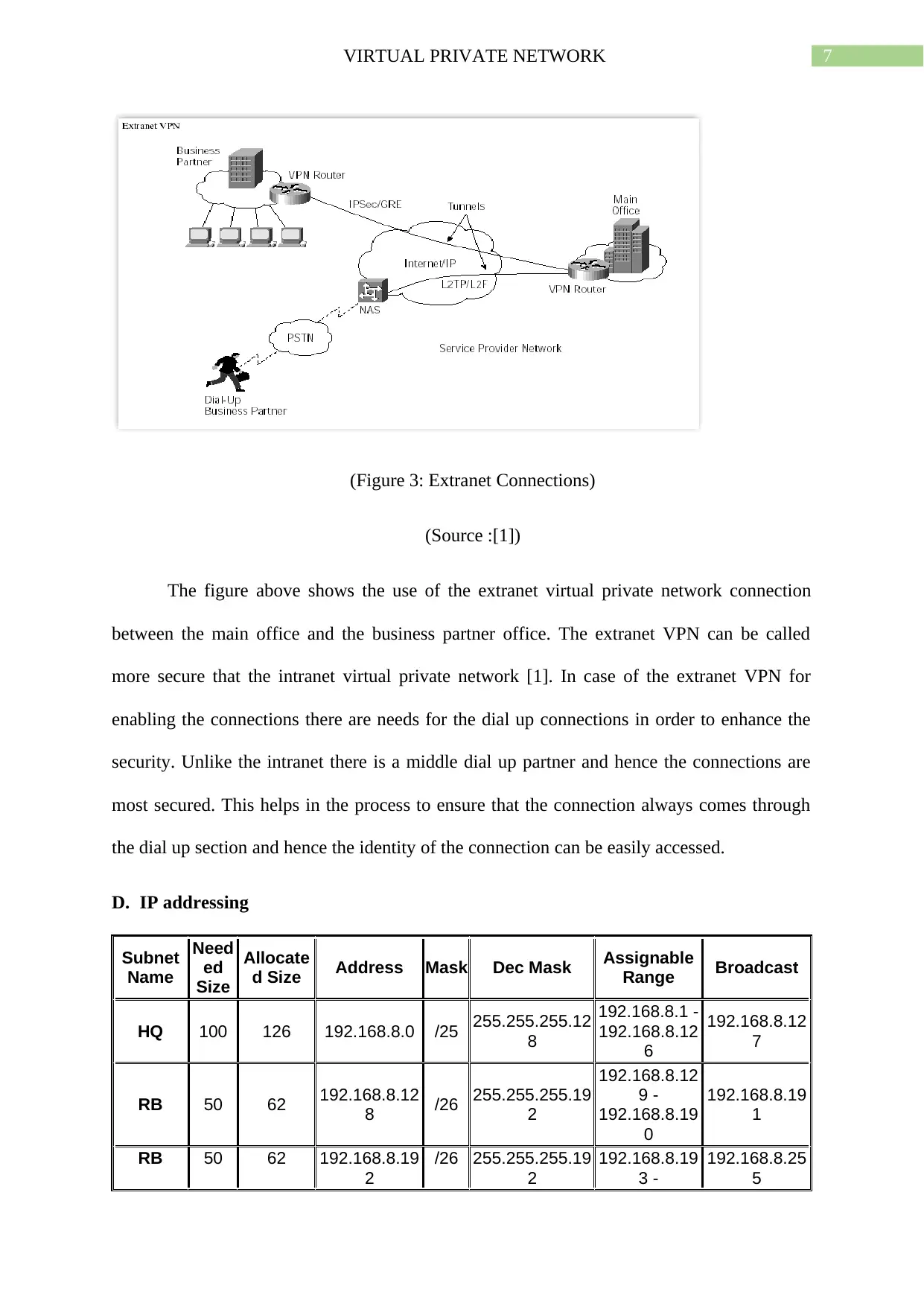
7VIRTUAL PRIVATE NETWORK
(Figure 3: Extranet Connections)
(Source :[1])
The figure above shows the use of the extranet virtual private network connection
between the main office and the business partner office. The extranet VPN can be called
more secure that the intranet virtual private network [1]. In case of the extranet VPN for
enabling the connections there are needs for the dial up connections in order to enhance the
security. Unlike the intranet there is a middle dial up partner and hence the connections are
most secured. This helps in the process to ensure that the connection always comes through
the dial up section and hence the identity of the connection can be easily accessed.
D. IP addressing
Subnet
Name
Need
ed
Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
HQ 100 126 192.168.8.0 /25 255.255.255.12
8
192.168.8.1 -
192.168.8.12
6
192.168.8.12
7
RB 50 62 192.168.8.12
8 /26 255.255.255.19
2
192.168.8.12
9 -
192.168.8.19
0
192.168.8.19
1
RB 50 62 192.168.8.19
2
/26 255.255.255.19
2
192.168.8.19
3 -
192.168.8.25
5
(Figure 3: Extranet Connections)
(Source :[1])
The figure above shows the use of the extranet virtual private network connection
between the main office and the business partner office. The extranet VPN can be called
more secure that the intranet virtual private network [1]. In case of the extranet VPN for
enabling the connections there are needs for the dial up connections in order to enhance the
security. Unlike the intranet there is a middle dial up partner and hence the connections are
most secured. This helps in the process to ensure that the connection always comes through
the dial up section and hence the identity of the connection can be easily accessed.
D. IP addressing
Subnet
Name
Need
ed
Size
Allocate
d Size Address Mask Dec Mask Assignable
Range Broadcast
HQ 100 126 192.168.8.0 /25 255.255.255.12
8
192.168.8.1 -
192.168.8.12
6
192.168.8.12
7
RB 50 62 192.168.8.12
8 /26 255.255.255.19
2
192.168.8.12
9 -
192.168.8.19
0
192.168.8.19
1
RB 50 62 192.168.8.19
2
/26 255.255.255.19
2
192.168.8.19
3 -
192.168.8.25
5
8VIRTUAL PRIVATE NETWORK
192.168.8.25
4
R1-ISP 2 2 192.168.9.0 /30 255.255.255.25
2
192.168.9.1 -
192.168.9.2 192.168.9.3
R1-R2 2 2 192.168.9.4 /30 255.255.255.25
2
192.168.9.5 -
192.168.9.6 192.168.9.7
R1-R3 2 2 192.168.9.8 /30 255.255.255.25
2
192.168.9.9 -
192.168.9.10 192.168.9.11
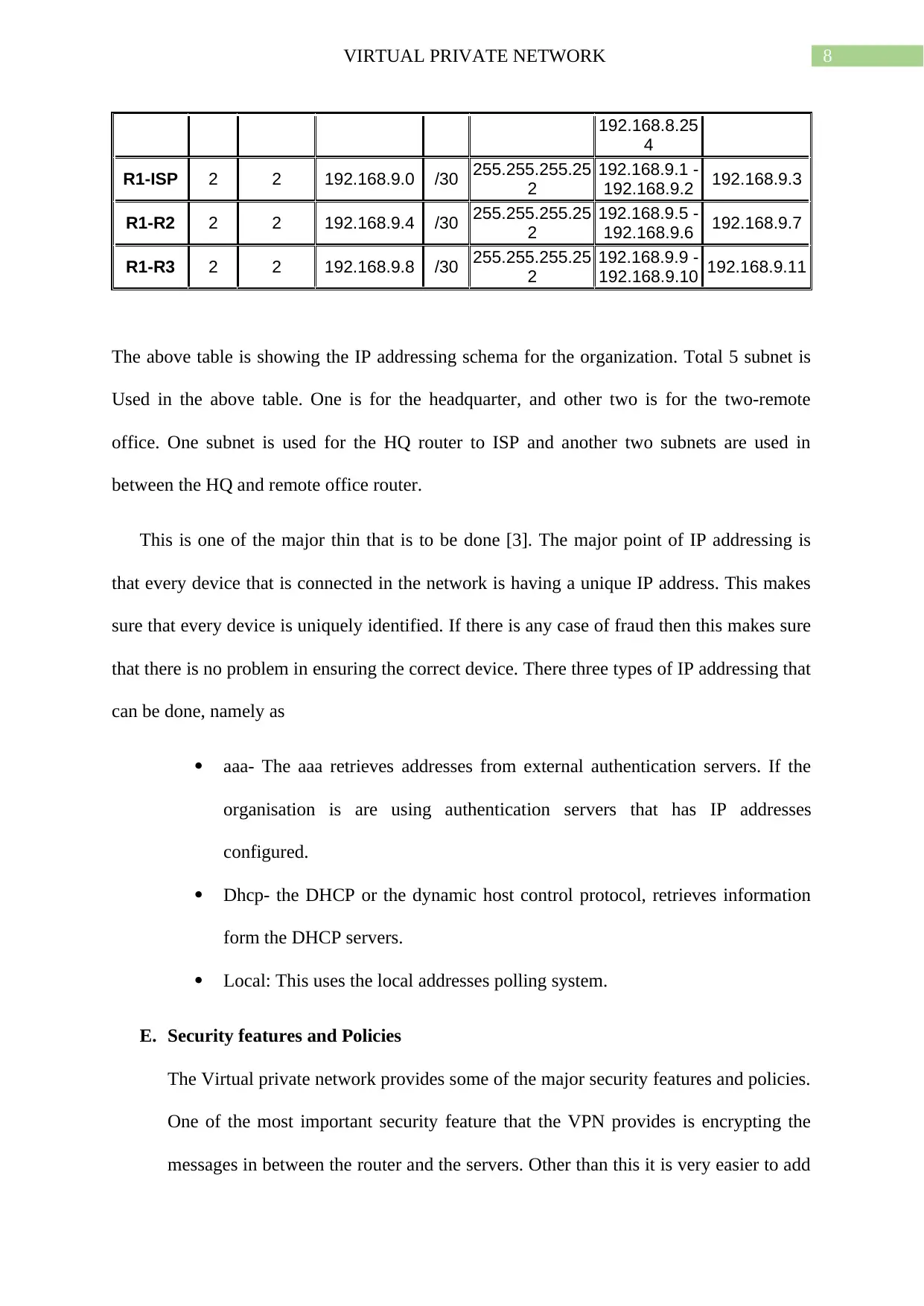
The above table is showing the IP addressing schema for the organization. Total 5 subnet is
Used in the above table. One is for the headquarter, and other two is for the two-remote
office. One subnet is used for the HQ router to ISP and another two subnets are used in
between the HQ and remote office router.
This is one of the major thin that is to be done [3]. The major point of IP addressing is
that every device that is connected in the network is having a unique IP address. This makes
sure that every device is uniquely identified. If there is any case of fraud then this makes sure
that there is no problem in ensuring the correct device. There three types of IP addressing that
can be done, namely as
aaa- The aaa retrieves addresses from external authentication servers. If the
organisation is are using authentication servers that has IP addresses
configured.
Dhcp- the DHCP or the dynamic host control protocol, retrieves information
form the DHCP servers.
Local: This uses the local addresses polling system.
E. Security features and Policies
The Virtual private network provides some of the major security features and policies.
One of the most important security feature that the VPN provides is encrypting the
messages in between the router and the servers. Other than this it is very easier to add
192.168.8.25
4
R1-ISP 2 2 192.168.9.0 /30 255.255.255.25
2
192.168.9.1 -
192.168.9.2 192.168.9.3
R1-R2 2 2 192.168.9.4 /30 255.255.255.25
2
192.168.9.5 -
192.168.9.6 192.168.9.7
R1-R3 2 2 192.168.9.8 /30 255.255.255.25
2
192.168.9.9 -
192.168.9.10 192.168.9.11
The above table is showing the IP addressing schema for the organization. Total 5 subnet is
Used in the above table. One is for the headquarter, and other two is for the two-remote
office. One subnet is used for the HQ router to ISP and another two subnets are used in
between the HQ and remote office router.
This is one of the major thin that is to be done [3]. The major point of IP addressing is
that every device that is connected in the network is having a unique IP address. This makes
sure that every device is uniquely identified. If there is any case of fraud then this makes sure
that there is no problem in ensuring the correct device. There three types of IP addressing that
can be done, namely as
aaa- The aaa retrieves addresses from external authentication servers. If the
organisation is are using authentication servers that has IP addresses
configured.
Dhcp- the DHCP or the dynamic host control protocol, retrieves information
form the DHCP servers.
Local: This uses the local addresses polling system.
E. Security features and Policies
The Virtual private network provides some of the major security features and policies.
One of the most important security feature that the VPN provides is encrypting the
messages in between the router and the servers. Other than this it is very easier to add
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9VIRTUAL PRIVATE NETWORK
or remove any user from the system. Further it helps in decreasing the costs f the
telecommunications. There are three major components of the VPN, protocols,
security and applications [4]. All these helps in the process of ensuring proper and
safe interconnections. One of the other major security feature of the VPN is the
scalability feature of the VPN. The services of the virtual private networks are flexible
and are easily accessible thorough new infrastructures. IN terms of cost, a good VPN
can cost very high but this is a one time investment and service goes on for long
duration of time. Operating a virtual private network within an organization costs are
significantly lower than other types of configurations.
F. Redundancy and Failover plans
The redundant VPN tunnel helps in the process to maintain a constant
interconnection in between the HQ and the local offices. It also helps to minimize the
effect of any hardware crashes or disruptions, which in turn increases the constancy and
dependability of VPN tunnels over the Internet
In certain case if the service of the VPN fails then the first thing is to ensure that
all the communication must be stopped. Further, use of the normal connections must be
avoided in order to ensure security.
G. VPN service Deployment and implementation
As explained the VPN service helps in the process of ensuing that the
interconnection of two offices in a secured manner [5]. In order to properly implement the
VPN service there are needs to ensure that the main connection between the two offices
are connected through the firewall. This ensures that there is always a redundant
connection in between the main office and the local offices. The use of the VPN enables
or remove any user from the system. Further it helps in decreasing the costs f the
telecommunications. There are three major components of the VPN, protocols,
security and applications [4]. All these helps in the process of ensuring proper and
safe interconnections. One of the other major security feature of the VPN is the
scalability feature of the VPN. The services of the virtual private networks are flexible
and are easily accessible thorough new infrastructures. IN terms of cost, a good VPN
can cost very high but this is a one time investment and service goes on for long
duration of time. Operating a virtual private network within an organization costs are
significantly lower than other types of configurations.
F. Redundancy and Failover plans
The redundant VPN tunnel helps in the process to maintain a constant
interconnection in between the HQ and the local offices. It also helps to minimize the
effect of any hardware crashes or disruptions, which in turn increases the constancy and
dependability of VPN tunnels over the Internet
In certain case if the service of the VPN fails then the first thing is to ensure that
all the communication must be stopped. Further, use of the normal connections must be
avoided in order to ensure security.
G. VPN service Deployment and implementation
As explained the VPN service helps in the process of ensuing that the
interconnection of two offices in a secured manner [5]. In order to properly implement the
VPN service there are needs to ensure that the main connection between the two offices
are connected through the firewall. This ensures that there is always a redundant
connection in between the main office and the local offices. The use of the VPN enables
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10VIRTUAL PRIVATE NETWORK
the access of the internet using a secured channels. The use of hubs and spokes makes it
easier to properly access these information.
Conclusion
Thus concluding the topic it can be said that the use of the virtual private network
helps in the process of securing the servers of an organisation and helps in maintaining data
security. The virtual private network helps in the process of enhancing the security services
with the use of the secure medium. Further it can be said that the use of the VPN service
helps in the process to ensure that the connections are always encrypted so that data cannot be
overridden while using a VPN. The use of the extranet virtual private network can help in
further making the services more secured. The dial up process of the extranet service makes
the connections more secured and are more highly encrypted.
the access of the internet using a secured channels. The use of hubs and spokes makes it
easier to properly access these information.
Conclusion
Thus concluding the topic it can be said that the use of the virtual private network
helps in the process of securing the servers of an organisation and helps in maintaining data
security. The virtual private network helps in the process of enhancing the security services
with the use of the secure medium. Further it can be said that the use of the VPN service
helps in the process to ensure that the connections are always encrypted so that data cannot be
overridden while using a VPN. The use of the extranet virtual private network can help in
further making the services more secured. The dial up process of the extranet service makes
the connections more secured and are more highly encrypted.

11VIRTUAL PRIVATE NETWORK
References:
[1] Sinha, Sanjib. "Virtual Private Network or VPN." In Beginning Ethical Hacking with
Python, pp. 185-189. Apress, Berkeley, CA, 2017.
[2] Raeespour, Akram Kargar, and Ahmed Moosajee Patel. "Design and Evaluation of a
Virtual Private Network Architecture for Collaborating Specialist Users." Asia-Pacific
Journal of Information Technology and Multimedia 5, no. 1 (2016).
[3] Jangid, Manoj, and Prakriti Trivedi. "Improve Performance of Successive Ratio for
Virtual Private Network." In Computational Intelligence and Communication Networks
(CICN), 2016 8th International Conference on, pp. 97-101. IEEE, 2016.
[4] Nurcahyaningsih, Shinta, Rendy Munadi, Sofia Naning Hertiana, and Taufik Hasan.
"Transport Solution Based on Layer 3 MPLS-Virtual Private Network to Support IP
Connectivity in Long Term Evolution Mobile Back-Haul." Advanced Science Letters 20, no.
2 (2014): 386-390.
[5] Lodi, Andrea, and Ahmad Moradi. "Experiments on virtual private network design with
concave capacity costs." Optimization Letters 12, no. 5 (2018): 945-957.
References:
[1] Sinha, Sanjib. "Virtual Private Network or VPN." In Beginning Ethical Hacking with
Python, pp. 185-189. Apress, Berkeley, CA, 2017.
[2] Raeespour, Akram Kargar, and Ahmed Moosajee Patel. "Design and Evaluation of a
Virtual Private Network Architecture for Collaborating Specialist Users." Asia-Pacific
Journal of Information Technology and Multimedia 5, no. 1 (2016).
[3] Jangid, Manoj, and Prakriti Trivedi. "Improve Performance of Successive Ratio for
Virtual Private Network." In Computational Intelligence and Communication Networks
(CICN), 2016 8th International Conference on, pp. 97-101. IEEE, 2016.
[4] Nurcahyaningsih, Shinta, Rendy Munadi, Sofia Naning Hertiana, and Taufik Hasan.
"Transport Solution Based on Layer 3 MPLS-Virtual Private Network to Support IP
Connectivity in Long Term Evolution Mobile Back-Haul." Advanced Science Letters 20, no.
2 (2014): 386-390.
[5] Lodi, Andrea, and Ahmad Moradi. "Experiments on virtual private network design with
concave capacity costs." Optimization Letters 12, no. 5 (2018): 945-957.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





